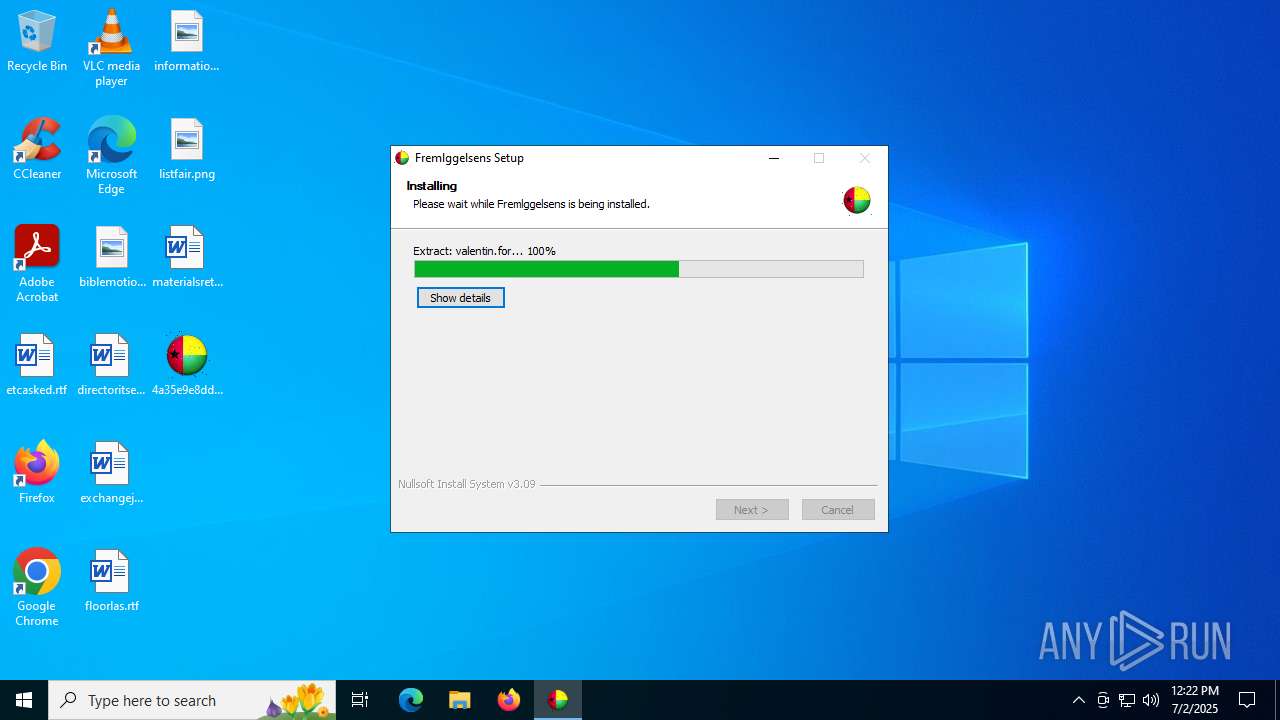
| File name: | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902 |
| Full analysis: | https://app.any.run/tasks/d3e568b1-7e84-48b9-b0a7-ab15312966b6 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | July 02, 2025, 12:22:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | B9A630AFF8ACAA7FE1D6E56BA7CA1B42 |
| SHA1: | 5446C648A82D72990172A2E45C294D9ABDF1F7B9 |
| SHA256: | 4A35E9E8DDD64D9B37D11C6BB166D12B59E7C2D1B77FC0D87CF2EE2AE8165902 |
| SSDEEP: | 49152:Iso0YRfqCQnKY5gjwsyy5fW36sjNkAbMdGgfwY59GJS5GEUbRq33D9h54UwNgggY:IsYRNQnKY5gj7Z2MrrwJS5ibMhL4UwdL |
MALICIOUS
Executing a file with an untrusted certificate
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
GULOADER SHELLCODE has been detected (YARA)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
GULOADER has been detected (YARA)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
SNAKEKEYLOGGER has been detected (SURICATA)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Actions looks like stealing of personal data
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Steals credentials from Web Browsers
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
The process creates files with name similar to system file names
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
There is functionality for taking screenshot (YARA)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Executable content was dropped or overwritten
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
Application launched itself
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
Reads security settings of Internet Explorer
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Checks for external IP
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
- svchost.exe (PID: 2200)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
The process verifies whether the antivirus software is installed
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
INFO
Reads the computer name
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
The sample compiled with english language support
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
Checks supported languages
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Creates files or folders in the user directory
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
Create files in a temporary directory
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 6208)
Checks proxy server information
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
- slui.exe (PID: 760)
Reads the machine GUID from the registry
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Reads the software policy settings
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
- slui.exe (PID: 760)
Disables trace logs
- 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe (PID: 5240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:02 02:09:39+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x34fc |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.4.0.0 |
| ProductVersionNumber: | 2.4.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | opblandes sociallovens |
| CompanyName: | cryptology flagets |
| FileDescription: | klyster |
| FileVersion: | 2.4.0.0 |
| LegalTrademarks: | snuggerie |
| OriginalFileName: | phrasings hardtacks.exe |
Total processes
133
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | "C:\Users\admin\Desktop\4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe" | C:\Users\admin\Desktop\4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | ||||||||||||
User: admin Company: cryptology flagets Integrity Level: MEDIUM Description: klyster Version: 2.4.0.0 Modules
| |||||||||||||||
| 6208 | "C:\Users\admin\Desktop\4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe" | C:\Users\admin\Desktop\4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | explorer.exe | ||||||||||||
User: admin Company: cryptology flagets Integrity Level: MEDIUM Description: klyster Exit code: 0 Version: 2.4.0.0 Modules
| |||||||||||||||
Total events
8 824
Read events
7 919
Write events
905
Delete events
0
Modification events
| (PID) Process: | (6208) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_CURRENT_USER\flidens\Wingerne\Posteringtekst |
| Operation: | write | Name: | omoplatoscopy |
Value: 7CB332 | |||
| (PID) Process: | (6208) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_CURRENT_USER\Stiftelsesfester\asylretten |
| Operation: | write | Name: | indiction |
Value: FFF6CC0F | |||
| (PID) Process: | (6208) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_CURRENT_USER\commandingness\Uninstall\Stackers185\Archbishop |
| Operation: | write | Name: | unshattered |
Value: 1 | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5240) 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
2
Suspicious files
2
Text files
18
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\hyperlustrousness.skr | — | |
MD5:— | SHA256:— | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\nongraduation.int | — | |
MD5:— | SHA256:— | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Inferential\Bajonetfatningernes.jpg | image | |
MD5:F59865EE0FECAA882F3BB592D6F8767A | SHA256:63ECBCB3B9CFF11154107CE1C8D516FBDC692DCD0CB4D297728A205E71CD56F8 | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\alkitran.jpg | image | |
MD5:BCDB06211140120BA45EAC66AE4F761E | SHA256:BB3964204BAA3AEF9F29EF0AA145737B9622F228141B64ECE95482C631D2D2DD | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\valentin.for | — | |
MD5:— | SHA256:— | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\handwrote.txt | text | |
MD5:BC6D942F32EDE43E594BCD18D785580E | SHA256:BC59F76A202FE6082E78CBABDEE292529F129F7C4B4BF7AD6E571D3FD4092B8C | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\bloodsucker.ini | text | |
MD5:86089CDC7B589CAB26B69076D01AD84C | SHA256:55C9E0D8B86980598B1AF749FE4BA4FE56EF768A2472CB44E48812522D768491 | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\Gylpene161.ini | text | |
MD5:8CB5328ED492801FA6295ECBD232D250 | SHA256:6FD8FD4D7C89718DA327E922DDCD5DF4F20B8A3086B9BE04695CC16B850A60E8 | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\Microhistology.ini | text | |
MD5:F000478142AAF6B19CEF8406934AE0FE | SHA256:7F52510571E6060DF62A878194C9B403512BBD85FA3AFE0BEBBDD20EC1D98B02 | |||
| 6208 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Pizzazz221\Reproduktiv\Sensationspresser\enegangens.ini | text | |
MD5:891ACC88AC77AFC8DE3B45FBFECA0196 | SHA256:D614A135FAA507BF56D650E47D2B6B2665E0C6865B847C8950D067602D8DD313 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
28
DNS requests
14
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2276 | RUXIMICS.exe | GET | 200 | 23.216.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2276 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 303 | 142.250.184.206:443 | https://drive.google.com/uc?export=download&id=1JBgajAlA4RQiyos2JaOZEmMWNmHIAV6w | unknown | — | — | unknown |
— | — | GET | 200 | 142.250.74.193:443 | https://drive.usercontent.google.com/download?id=1JBgajAlA4RQiyos2JaOZEmMWNmHIAV6w&export=download | unknown | binary | 269 Kb | whitelisted |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | GET | 200 | 132.226.247.73:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | GET | 200 | 132.226.247.73:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2276 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2276 | RUXIMICS.exe | 23.216.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2276 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
drive.google.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
checkip.dyndns.org |
| whitelisted |
reallyfreegeoip.org |
| malicious |
api.telegram.org |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET DYN_DNS External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Misc activity | ET INFO External IP Lookup Service Domain (reallyfreegeoip .org) in TLS SNI |
2200 | svchost.exe | Misc activity | ET INFO External IP Address Lookup Domain in DNS Lookup (reallyfreegeoip .org) |
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Address Lookup Domain (reallyfreegeoip .org) |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5240 | 4a35e9e8ddd64d9b37d11c6bb166d12b59e7c2d1b77fc0d87cf2ee2ae8165902.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |