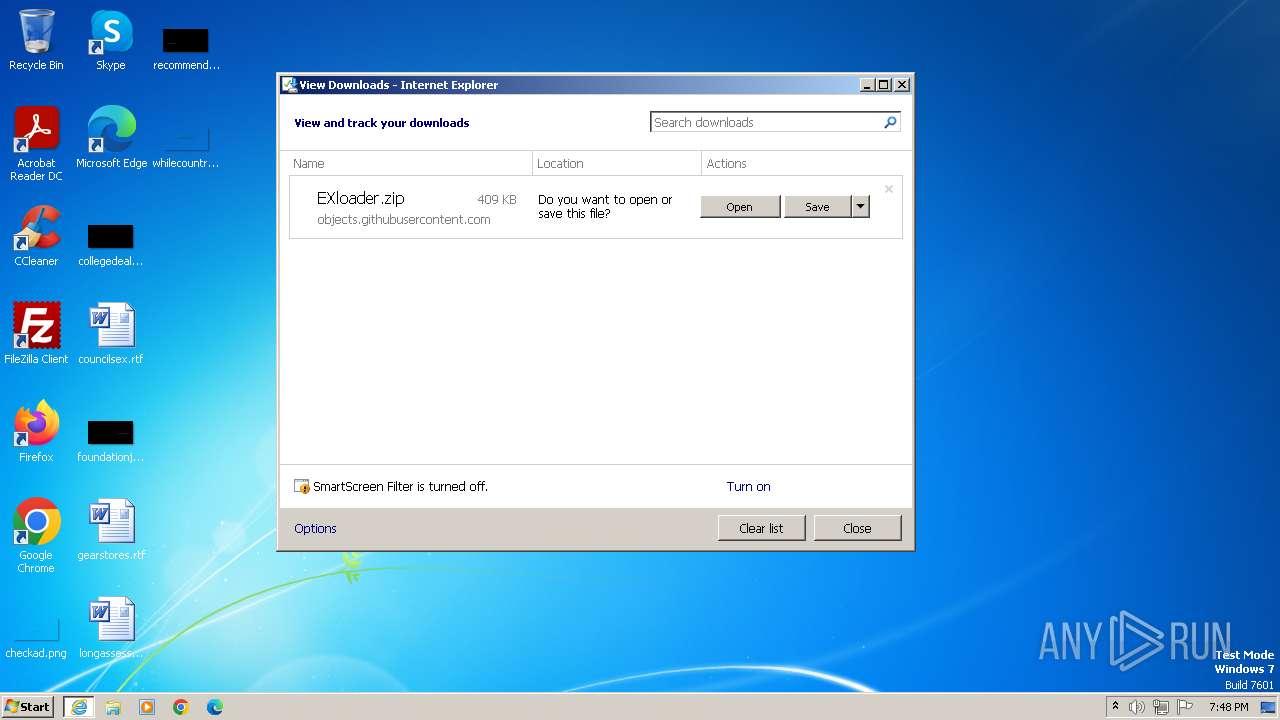
| URL: | https://github.com/BubblesMC/pubg-hacks/releases/download/hack/EXloader.zip |
| Full analysis: | https://app.any.run/tasks/a8f3a69e-9c2a-40b9-b1d5-cb326c566509 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | December 05, 2023, 19:47:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 708E73797FF662941181CC429941EE19 |
| SHA1: | 3E4D04EA366D76C7DF3CBC388ADECFF36B28B135 |
| SHA256: | 4960405A56A8764FA4B99CB7C305094BE3B7F1A22CC982999849BEE3F4308A29 |
| SSDEEP: | 3:N8tEdA5omOONEZ6KkC4P2XrU:2um57OiEZ6KKb |
MALICIOUS
Connects to the CnC server
- Launcher.exe (PID: 3140)
REDLINE has been detected (SURICATA)
- Launcher.exe (PID: 3140)
Steals credentials from Web Browsers
- Launcher.exe (PID: 3140)
Actions looks like stealing of personal data
- Launcher.exe (PID: 3140)
REDLINE has been detected (YARA)
- Launcher.exe (PID: 3140)
SUSPICIOUS
Connects to unusual port
- Launcher.exe (PID: 3140)
Reads browser cookies
- Launcher.exe (PID: 3140)
Searches for installed software
- Launcher.exe (PID: 3140)
INFO
Application launched itself
- iexplore.exe (PID: 2144)
Manual execution by a user
- wmpnscfg.exe (PID: 2908)
- Launcher.exe (PID: 3140)
Reads the computer name
- wmpnscfg.exe (PID: 2908)
- Launcher.exe (PID: 3140)
Checks supported languages
- wmpnscfg.exe (PID: 2908)
- Launcher.exe (PID: 3140)
The process uses the downloaded file
- WinRAR.exe (PID: 1560)
- iexplore.exe (PID: 2144)
Reads the machine GUID from the registry
- Launcher.exe (PID: 3140)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1560)
Reads Environment values
- Launcher.exe (PID: 3140)
Reads product name
- Launcher.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3140) Launcher.exe
C2 (1)45.15.156.142:33597
Botnet@SunLank
Options
ErrorMessage
Keys
XorOnsetting
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1560 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\EXloader.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2144 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/BubblesMC/pubg-hacks/releases/download/hack/EXloader.zip" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\Desktop\EXloader\Launcher.exe" | C:\Users\admin\Desktop\EXloader\Launcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
RedLine(PID) Process(3140) Launcher.exe C2 (1)45.15.156.142:33597 Botnet@SunLank Options ErrorMessage Keys XorOnsetting | |||||||||||||||
Total events
12 864
Read events
12 788
Write events
57
Delete events
19
Modification events
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
8
Suspicious files
22
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2144 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD1D22EB0563EA2EF.TMP | binary | |
MD5:B6C2C98554228937A4806DE860A698F7 | SHA256:583FB046F48C3AF70AF16BBA176AF253C4658FB03A9DBD0808323EDF480ECF47 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:33047B917E01D146E1BD43C23E51B801 | SHA256:90219216F3E958E658DB35C5EE140C624828E362CBD9AFD371C36000F80EE9C8 | |||
| 2144 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\EXloader.zip.o9a0h0s.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:0C617190C71F8AEE48CADB867B670837 | SHA256:00BE8D61C2DD58BFBB2B4918F961FF5D5370E9896C076A4548F24DA13AB163BD | |||
| 1560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1560.17562\EXloader\loader.dll | executable | |
MD5:F188F5741CF4BAF89B994B2F114D9BB5 | SHA256:B361203044BB95332B51A36D2527F64BB72CF2B445B250804083A8403C0BA88F | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:0DD6CDC70921478464E0696891EE79D3 | SHA256:B463CE1C456C2441261B9426BEEE99C77D04395EC831E469E20C3698906B8AF7 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\EXloader.zip.o9a0h0s.partial | compressed | |
MD5:B4B47E3D90590CFB02EEBA9723597701 | SHA256:F1457F32A554CA487DA6601C6F6FE17D4E3D59DB87DD238D0A2649779D9B9CBB | |||
| 1560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1560.17562\EXloader\locales\service-2023-09-21-184358.log | binary | |
MD5:CE1BB99B04EED6C7B257F40B303ACD75 | SHA256:D722277BAA73F0D1178CD9EE4A9143627F1349D6F6D8095E3BD45DB9DE19F652 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\EXloader[1].zip | compressed | |
MD5:35E05822E8406882510EBE2AFE96DA27 | SHA256:19E8A7AE4D3669EAF4FF289F2417DEEE20FB8B5616A3239A925B7893AEE27E74 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:619BD70B5EE2826AF6777A48C01E4125 | SHA256:1636C121C568C37E56FBC3A461639EAF4D9F3ADB6F7124F5FAEA334B8910F8D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
14
DNS requests
6
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1584 | iexplore.exe | GET | 200 | 23.50.131.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7c0985578a653cb5 | unknown | compressed | 4.66 Kb | unknown |
1584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
1584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 313 b | unknown |
1584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 173.222.108.179:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?59b8873ffc666c10 | unknown | compressed | 65.2 Kb | unknown |
1584 | iexplore.exe | GET | 200 | 23.50.131.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0b7725d384a0a9d4 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1584 | iexplore.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1584 | iexplore.exe | 23.50.131.199:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1584 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1584 | iexplore.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
3140 | Launcher.exe | 45.15.156.142:33597 | — | Galaxy LLC | RU | malicious |
1080 | svchost.exe | 173.222.108.179:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3140 | Launcher.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer Family Related (MC-NMF Authorization) |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC - Id1Response |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer Family Activity (Response) |
3140 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3140 | Launcher.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
3140 | Launcher.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |