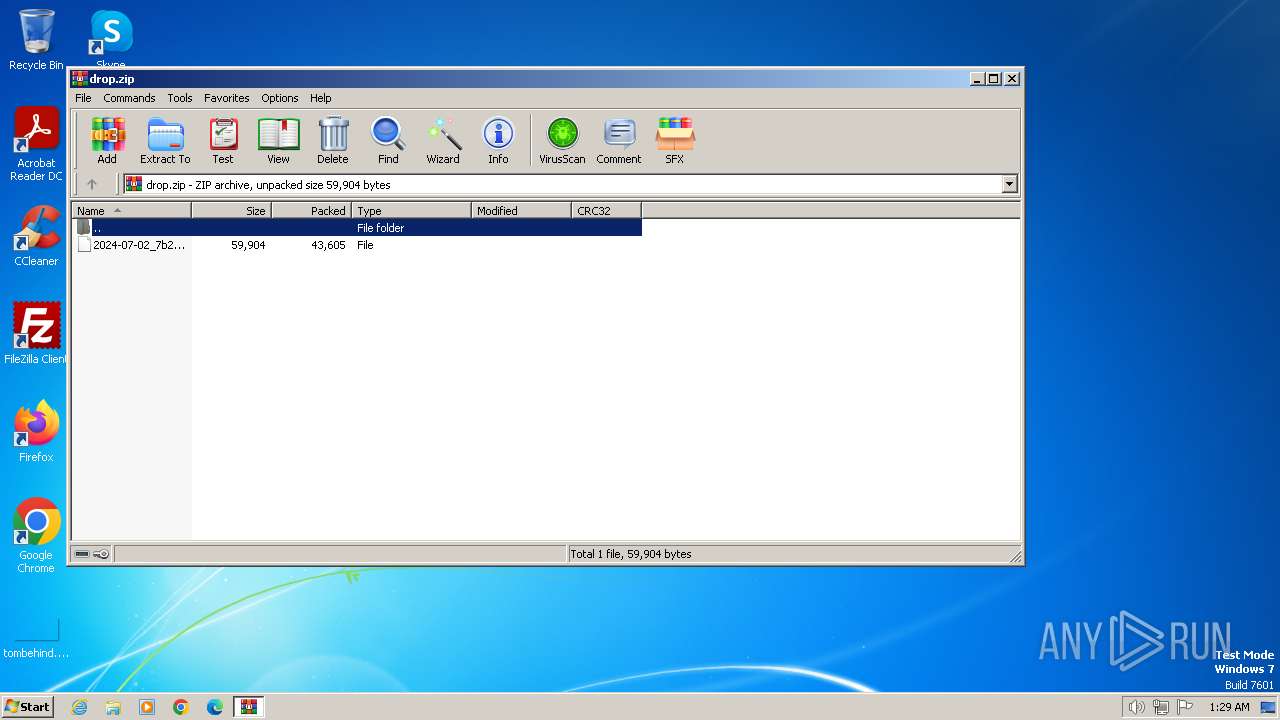
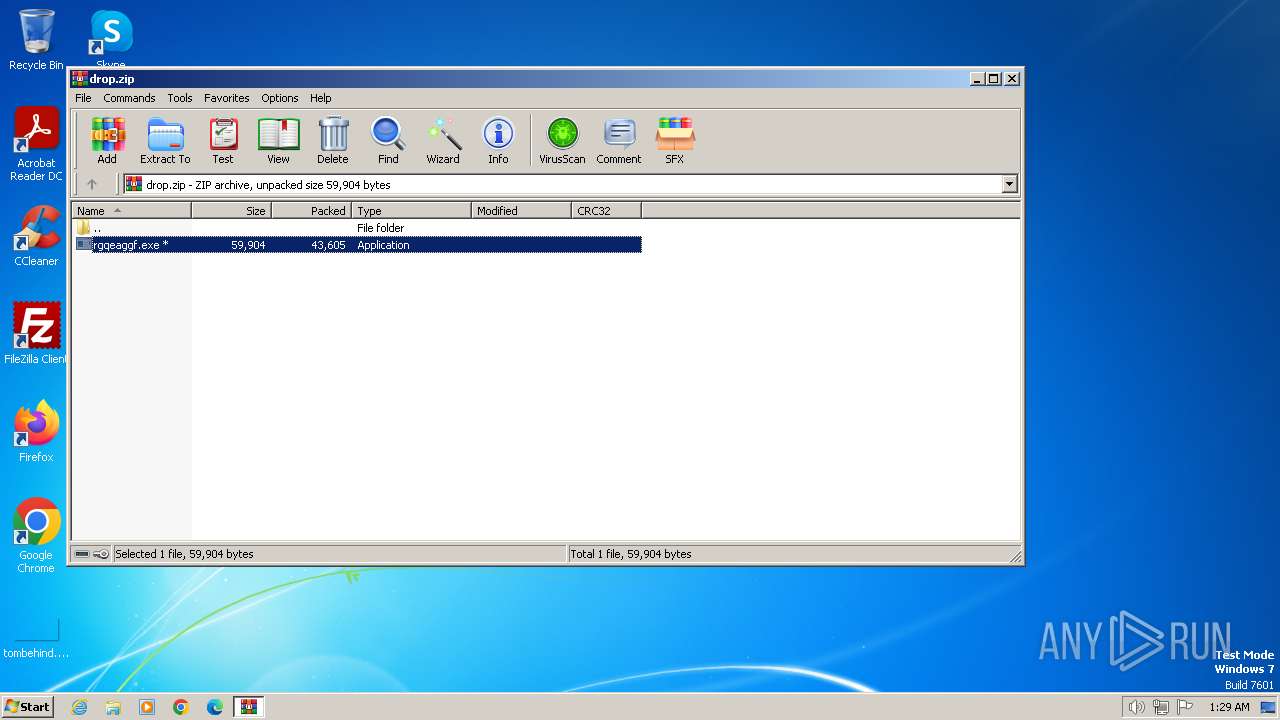
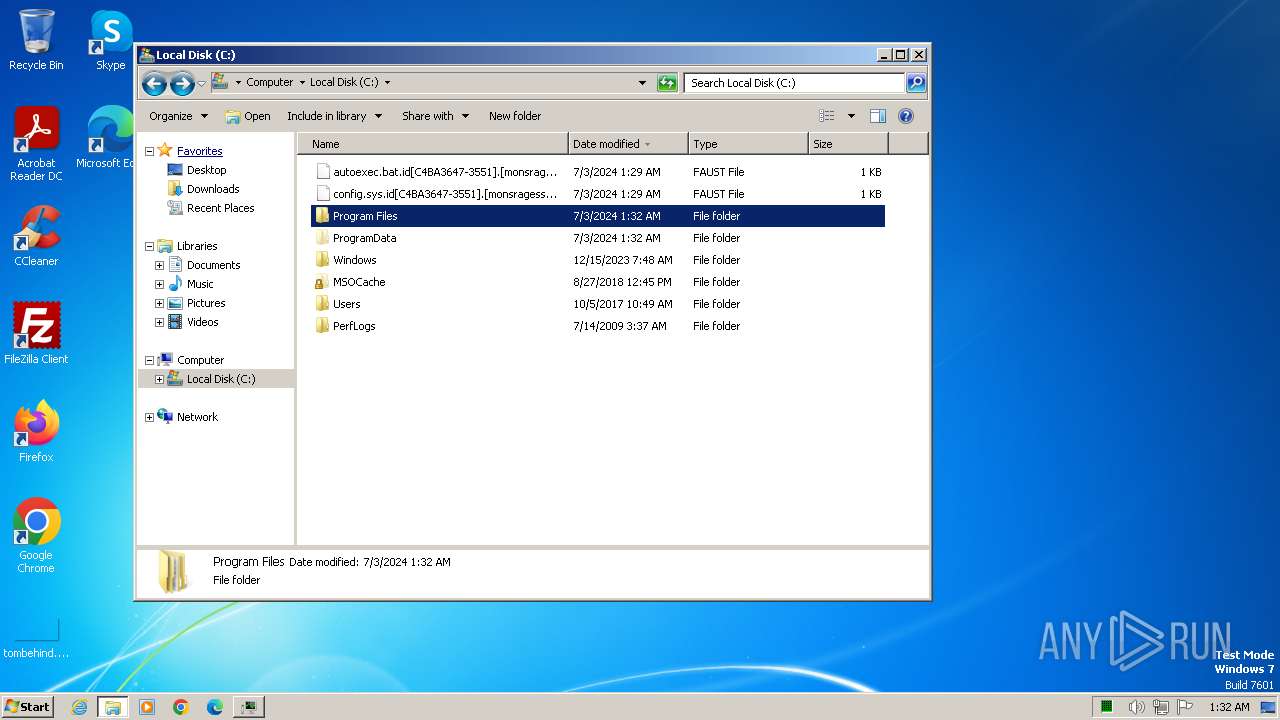
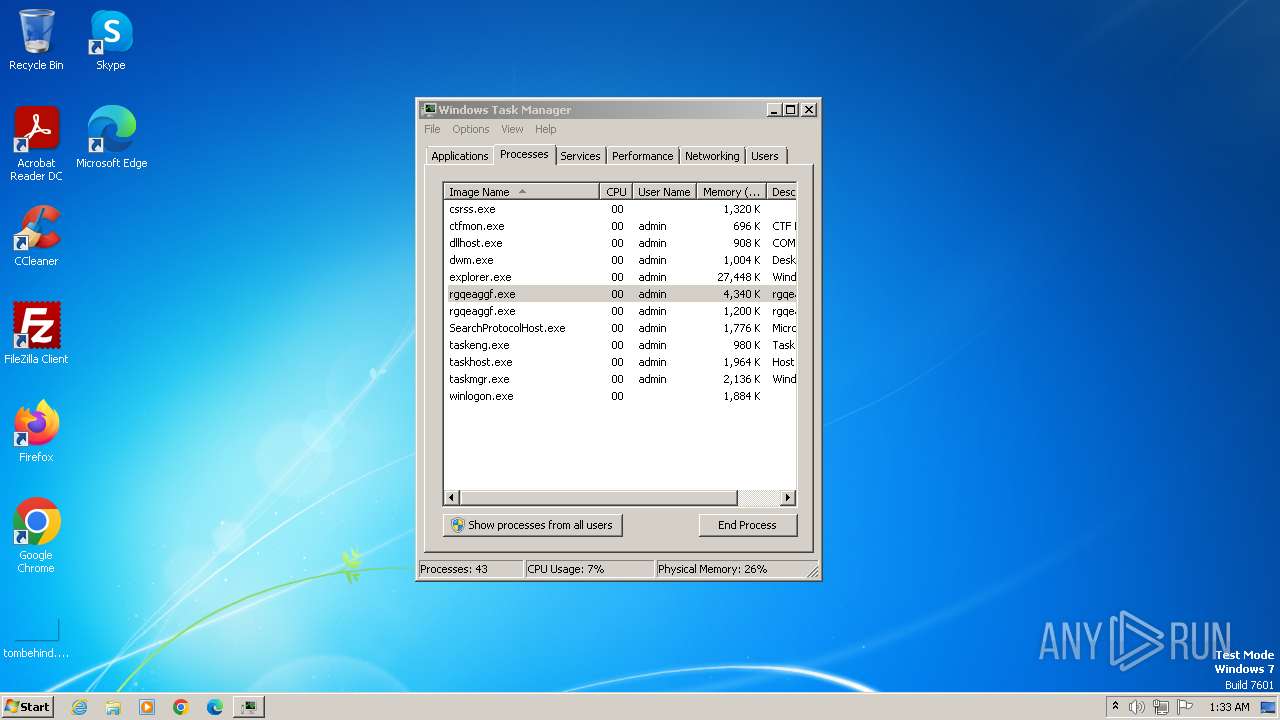
| File name: | drop.zip |
| Full analysis: | https://app.any.run/tasks/de564f27-c65d-43a2-978b-072025cec1bc |
| Verdict: | Malicious activity |
| Threats: | Phobos is a ransomware that locks or encrypts files to demand a ransom. It uses AES encryption with different extensions, which leaves no chance to recover the infected files. |
| Analysis date: | July 03, 2024, 00:29:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 4A5609D14690CEEFD17E99B3E6803DA1 |
| SHA1: | 9616AED734433A129159B70941246018BE86C1F8 |
| SHA256: | 4956F865B02D7B030CF027FD13FA5BD9030291AC017DC43A5858616A1FED68AB |
| SSDEEP: | 768:G5tLlhAbiG7+2H83/b2v09uaNZyU5EbEic4FiwGKjTIyNyKEvEhU2I/pCmO:QRKbDcvJtD5X1+phLI/7O |
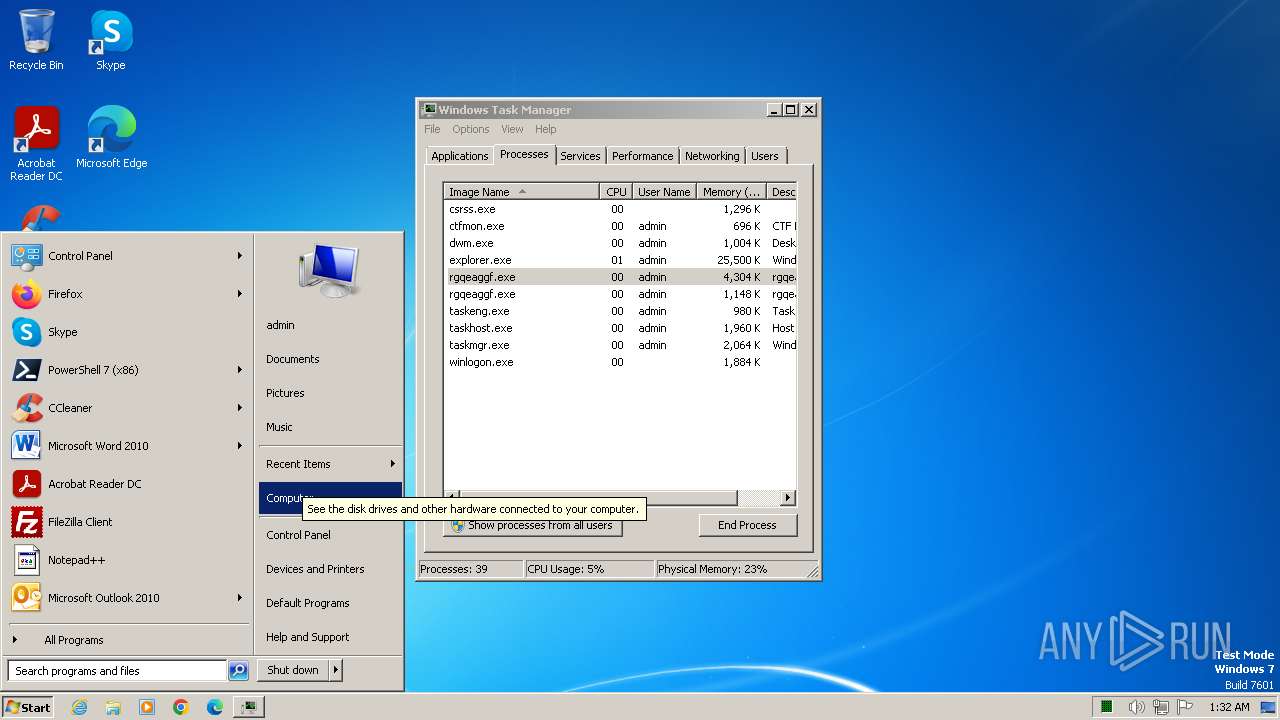
MALICIOUS
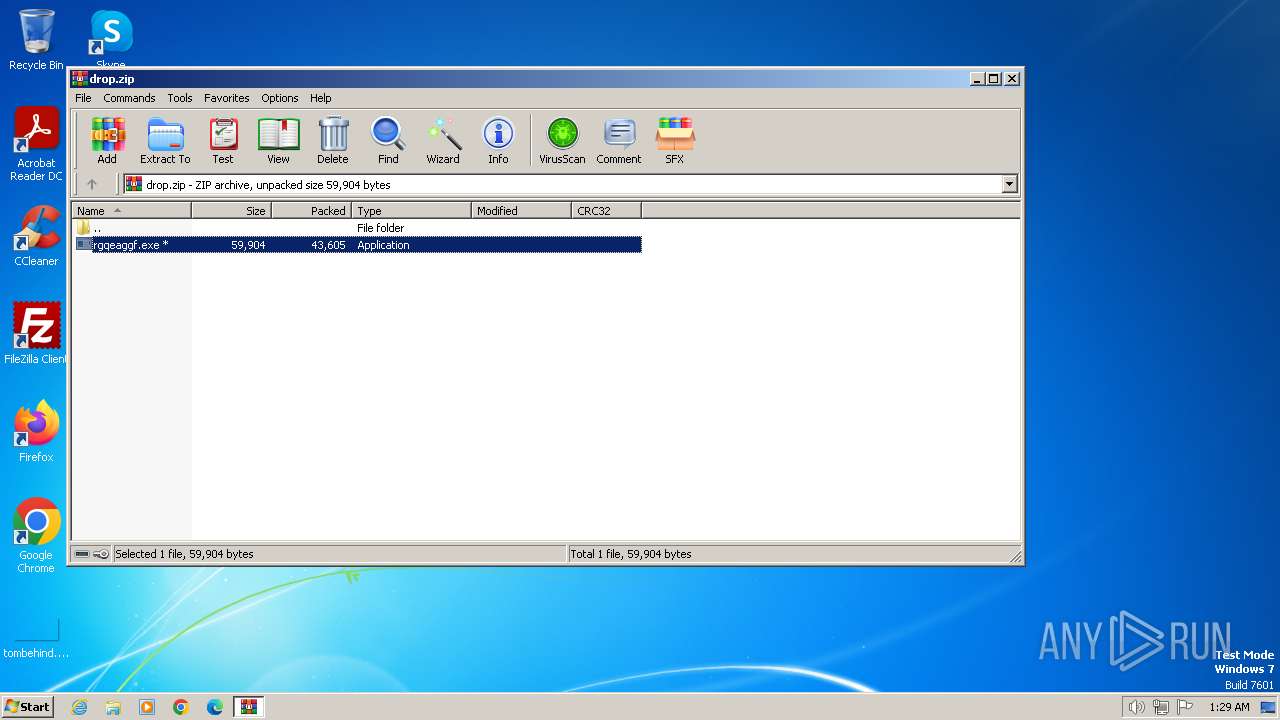
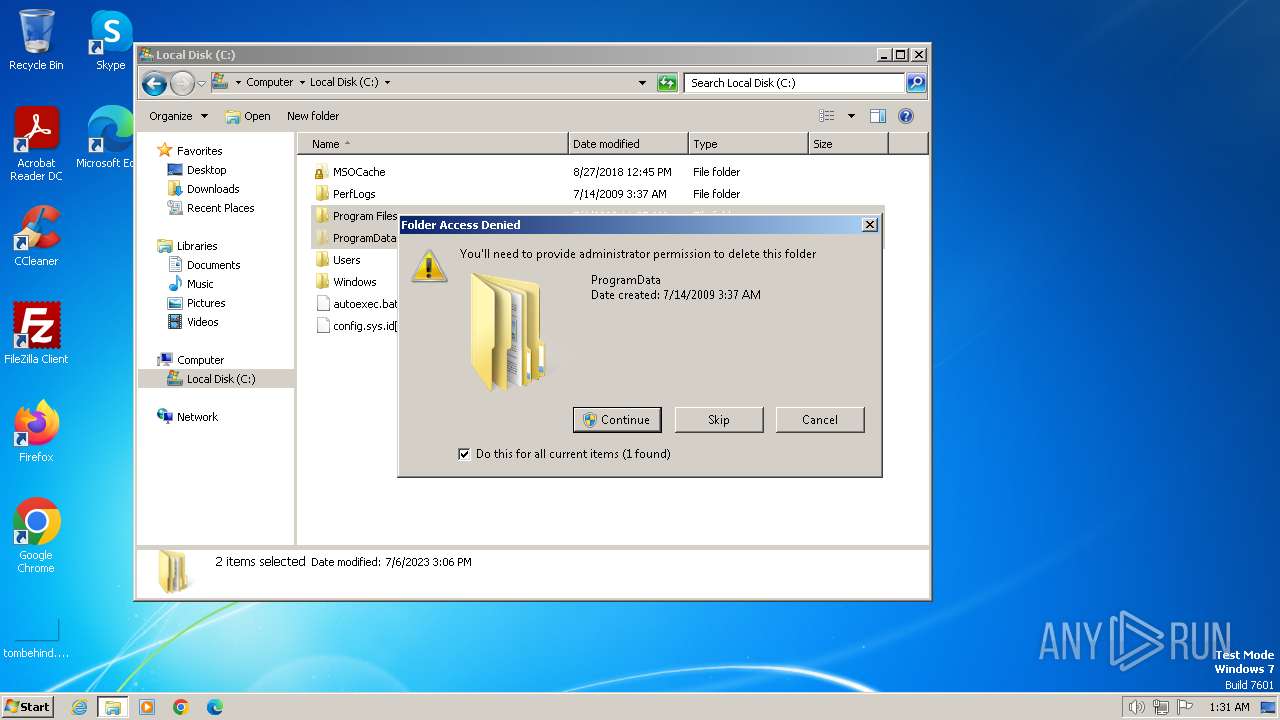
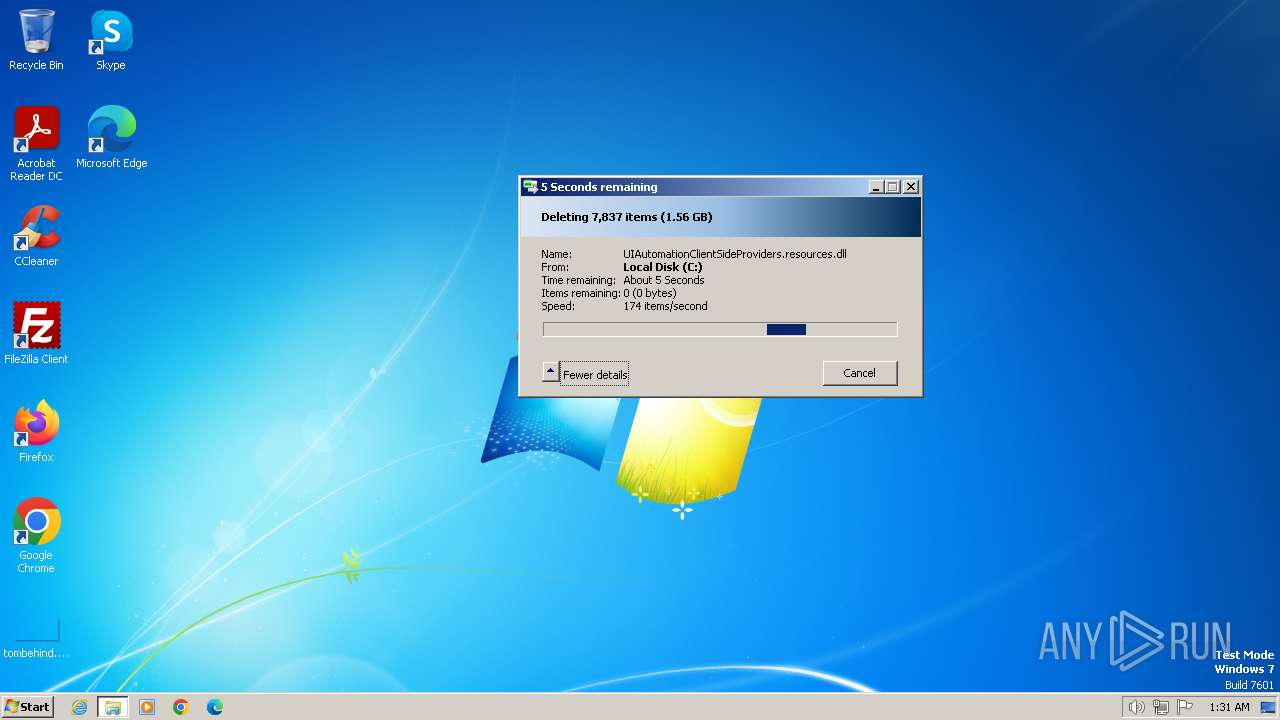
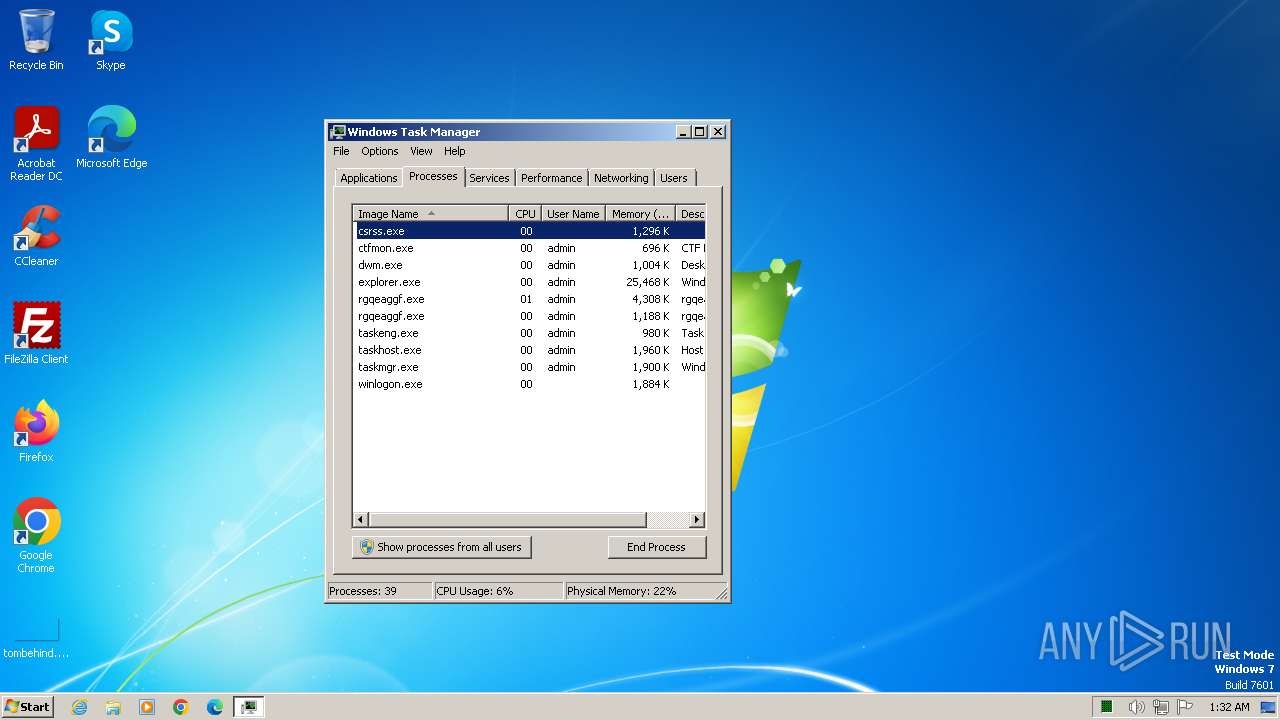
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3380)
- rgqeaggf.exe (PID: 2944)
Changes the autorun value in the registry
- rgqeaggf.exe (PID: 2944)
- rgqeaggf.exe (PID: 3432)
PHOBOS has been detected
- rgqeaggf.exe (PID: 2944)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 2348)
Create files in the Startup directory
- rgqeaggf.exe (PID: 2944)
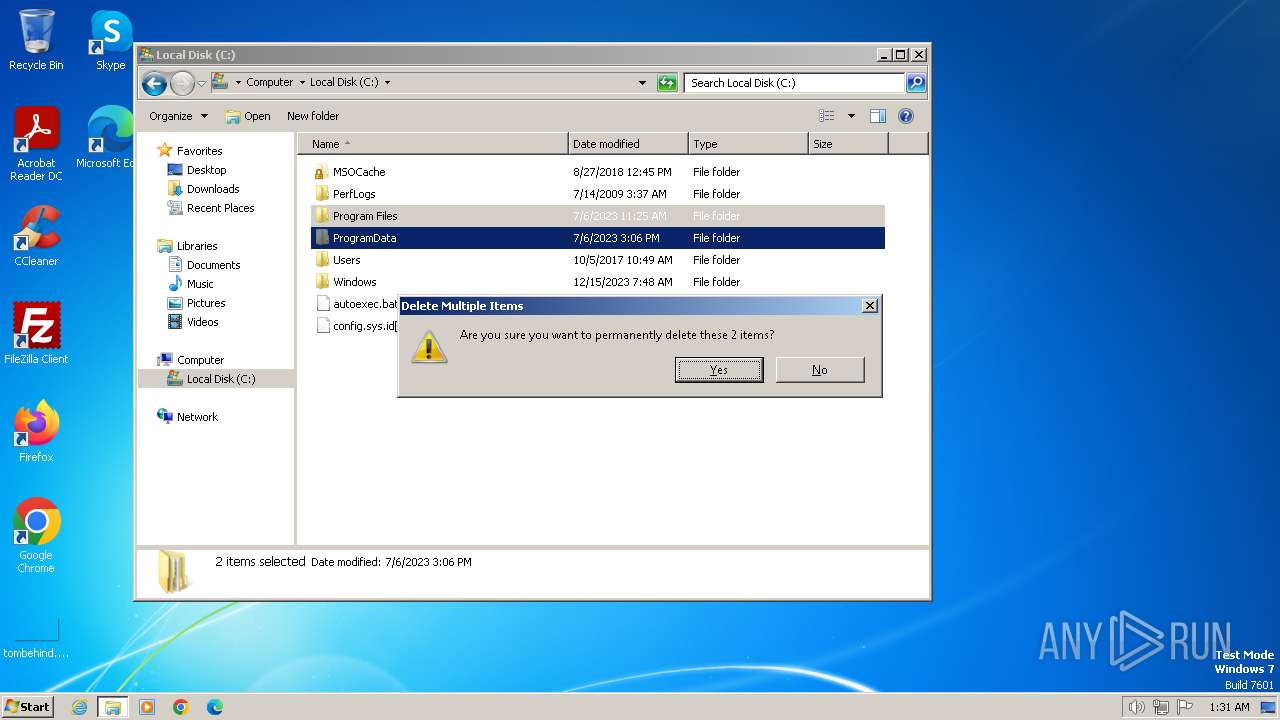
Deletes shadow copies
- cmd.exe (PID: 2348)
Actions looks like stealing of personal data
- SearchIndexer.exe (PID: 3192)
- rgqeaggf.exe (PID: 2944)
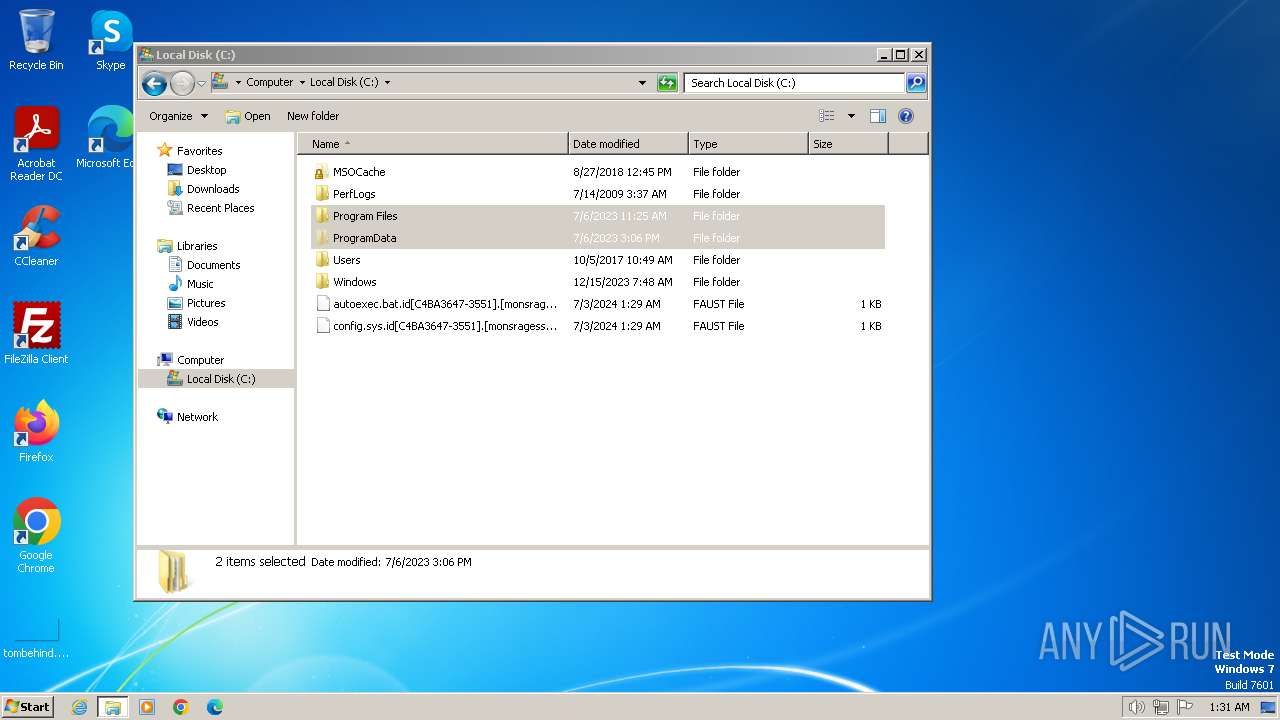
Renames files like ransomware
- rgqeaggf.exe (PID: 2944)
Modifies files in the Chrome extension folder
- rgqeaggf.exe (PID: 2944)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3380)
- rgqeaggf.exe (PID: 3252)
Application launched itself
- rgqeaggf.exe (PID: 3432)
- rgqeaggf.exe (PID: 3252)
Reads the Internet Settings
- rgqeaggf.exe (PID: 3252)
- WMIC.exe (PID: 2536)
- SearchProtocolHost.exe (PID: 2252)
Starts CMD.EXE for commands execution
- rgqeaggf.exe (PID: 2944)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2076)
Executes as Windows Service
- VSSVC.exe (PID: 3360)
- vds.exe (PID: 4040)
- wbengine.exe (PID: 3316)
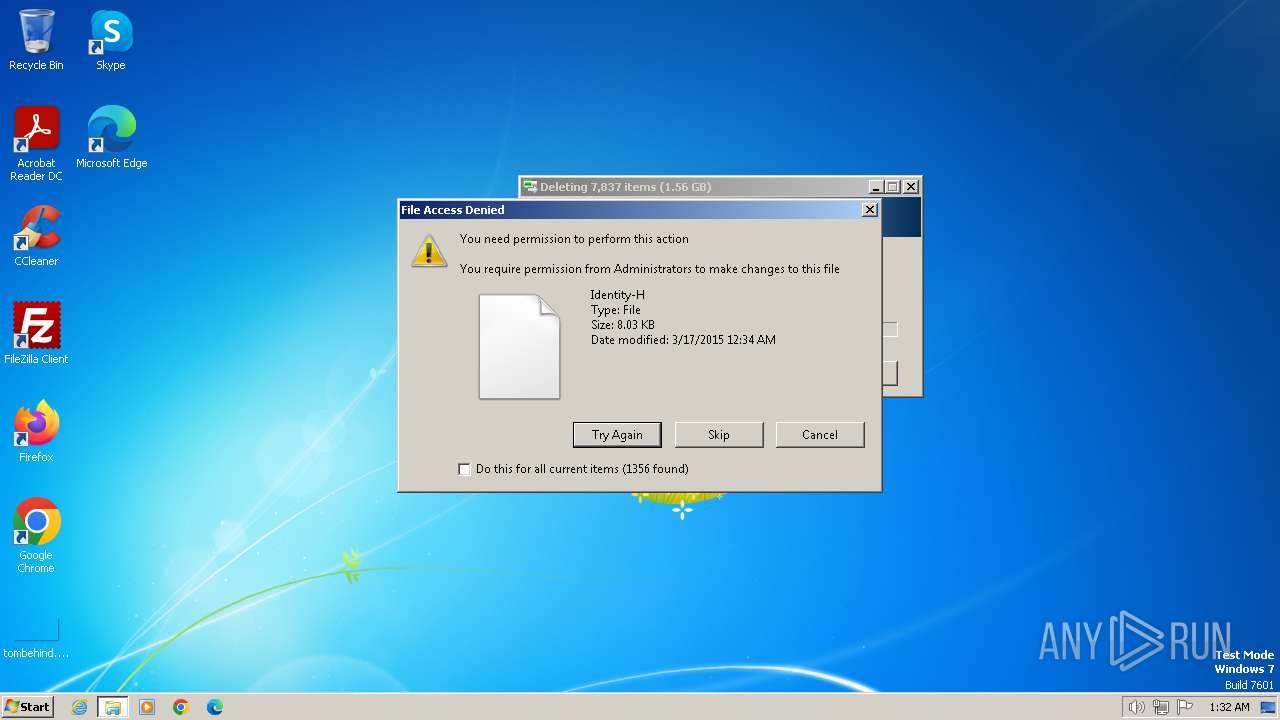
Executable content was dropped or overwritten
- rgqeaggf.exe (PID: 2944)
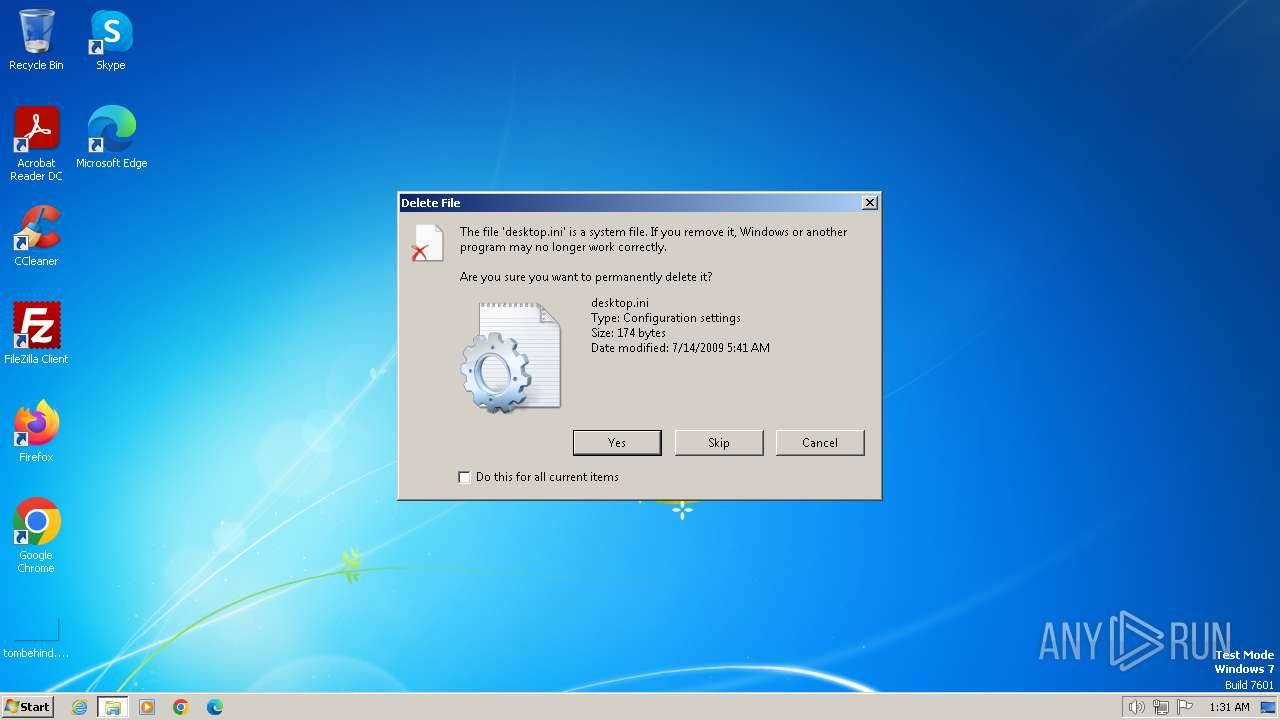
Write to the desktop.ini file (may be used to cloak folders)
- rgqeaggf.exe (PID: 2944)
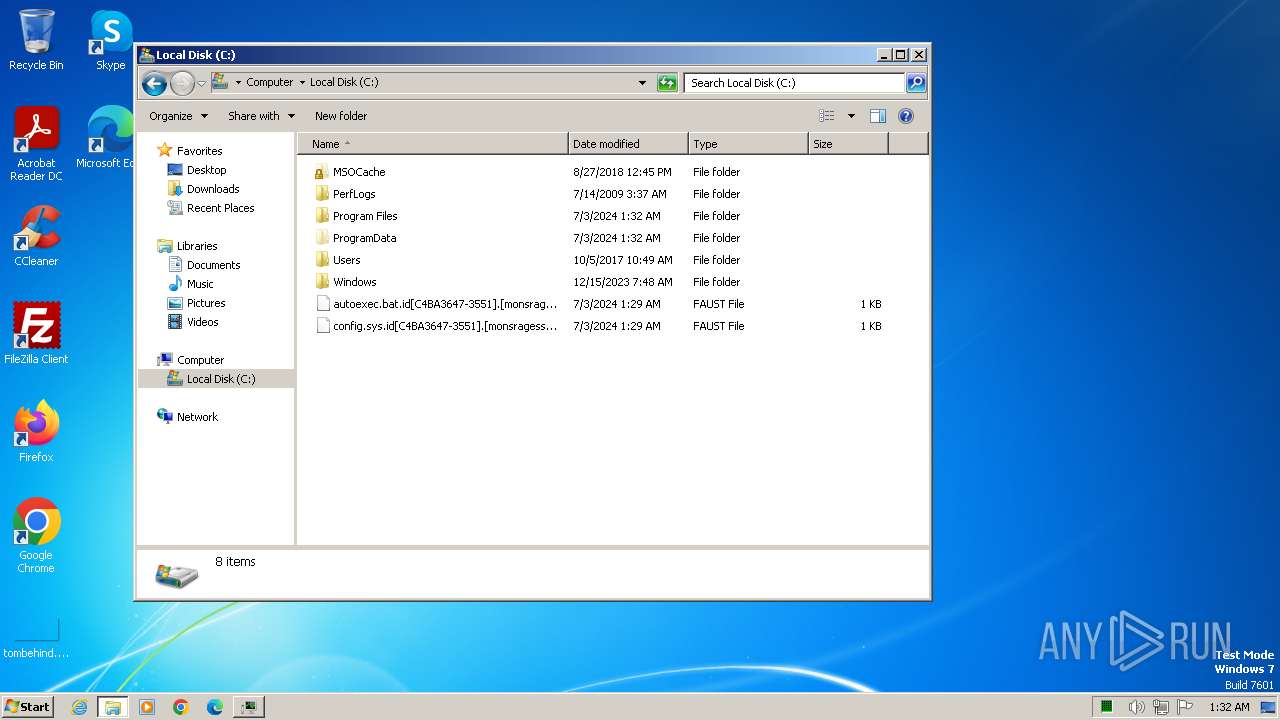
Creates file in the systems drive root
- rgqeaggf.exe (PID: 2944)
Process drops legitimate windows executable
- rgqeaggf.exe (PID: 2944)
Reads browser cookies
- rgqeaggf.exe (PID: 2944)
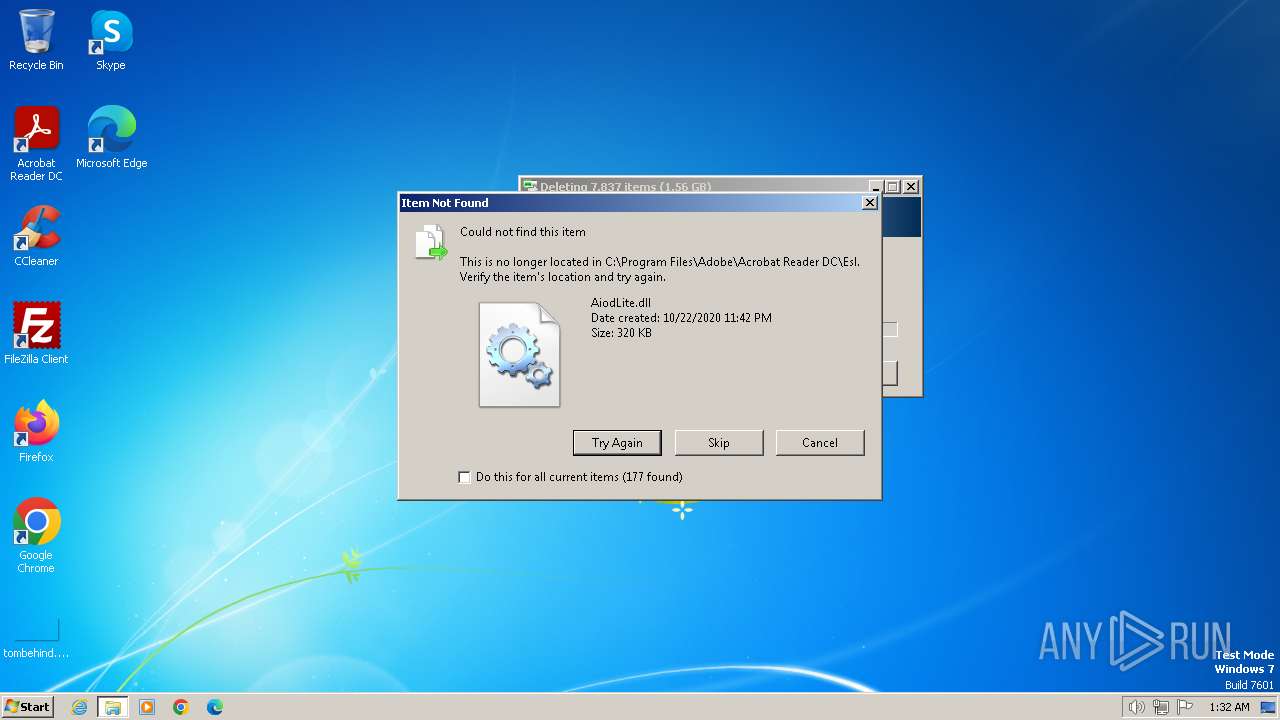
The process creates files with name similar to system file names
- rgqeaggf.exe (PID: 2944)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3380)
Checks supported languages
- rgqeaggf.exe (PID: 3432)
- rgqeaggf.exe (PID: 3252)
- rgqeaggf.exe (PID: 2944)
- wmpnscfg.exe (PID: 2312)
Reads the computer name
- rgqeaggf.exe (PID: 3252)
- rgqeaggf.exe (PID: 3432)
- rgqeaggf.exe (PID: 2944)
- wmpnscfg.exe (PID: 2312)
Creates files or folders in the user directory
- rgqeaggf.exe (PID: 2944)
Creates files in the program directory
- rgqeaggf.exe (PID: 2944)
- SearchIndexer.exe (PID: 3340)
- SearchIndexer.exe (PID: 3192)
Manual execution by a user
- taskmgr.exe (PID: 1816)
- wmpnscfg.exe (PID: 2312)
Executes as Windows Service
- SearchIndexer.exe (PID: 3192)
- SearchIndexer.exe (PID: 3340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 43605 |
| ZipUncompressedSize: | 59904 |
| ZipFileName: | 2024-07-02_7b23d3e6e6528012c98dda612c3dc821_phobos |
Total processes
78
Monitored processes
25
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | bcdedit /set {default} recoveryenabled no | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 996 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2076 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | rgqeaggf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2252 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | rgqeaggf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2384 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2424 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2536 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
32 279
Read events
30 317
Write events
1 735
Delete events
227
Modification events
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\drop.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
173
Suspicious files
5 956
Text files
14
Unknown types
373
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
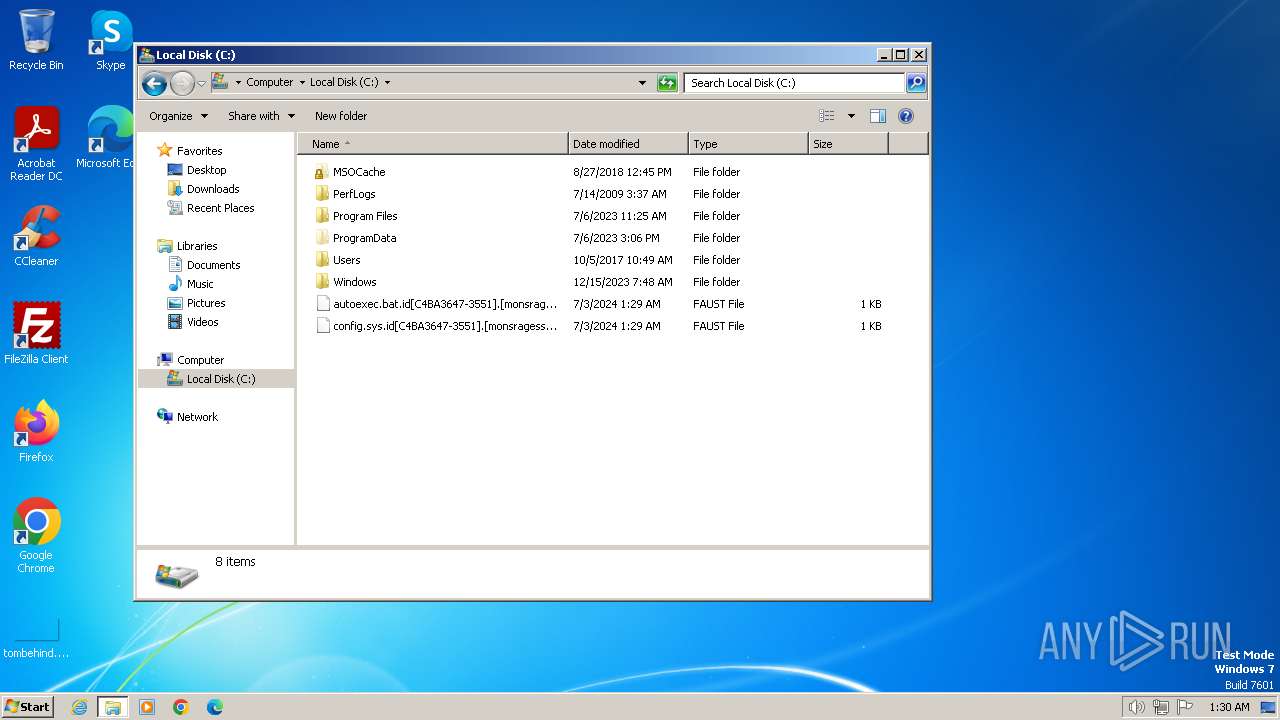
| 2944 | rgqeaggf.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3551].[monsragessparo@mail.com].faust | — | |
MD5:— | SHA256:— | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3380.36328\rgqeaggf.exe | executable | |
MD5:7B23D3E6E6528012C98DDA612C3DC821 | SHA256:F1E2B5685035903FCA89CD8F05B7B5CA922A1B23F9587CFA6DB938CF59A9C15D | |||
| 2944 | rgqeaggf.exe | C:\programdata\microsoft\windows\start menu\programs\startup\rgqeaggf.exe | executable | |
MD5:7B23D3E6E6528012C98DDA612C3DC821 | SHA256:F1E2B5685035903FCA89CD8F05B7B5CA922A1B23F9587CFA6DB938CF59A9C15D | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\drop.zip | compressed | |
MD5:8B49A4131EC052D2C2A4C2CB0FF8159C | SHA256:DFF84B09A4101072548E04783351E6F8540C721F6DE95B8209CB4E3B96090227 | |||
| 2944 | rgqeaggf.exe | C:\Users\admin\AppData\Local\rgqeaggf.exe | executable | |
MD5:7B23D3E6E6528012C98DDA612C3DC821 | SHA256:F1E2B5685035903FCA89CD8F05B7B5CA922A1B23F9587CFA6DB938CF59A9C15D | |||
| 2944 | rgqeaggf.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini | abr | |
MD5:5F54D1240735D46980B776AF554F44D3 | SHA256:2C80619D7E7C58257293CDA3A878C13E5856F4E06F6F90601276F7B9179C9E07 | |||
| 2944 | rgqeaggf.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3551].[monsragessparo@mail.com].faust | — | |
MD5:— | SHA256:— | |||
| 2944 | rgqeaggf.exe | C:\users\admin\appdata\roaming\microsoft\windows\start menu\programs\startup\rgqeaggf.exe | executable | |
MD5:7B23D3E6E6528012C98DDA612C3DC821 | SHA256:F1E2B5685035903FCA89CD8F05B7B5CA922A1B23F9587CFA6DB938CF59A9C15D | |||
| 2944 | rgqeaggf.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini.id[C4BA3647-3551].[monsragessparo@mail.com].faust | binary | |
MD5:DE6C06BCA486BB17E30838D03709A57F | SHA256:1D661F592A9D90D612E972D810C4613B5106FDE2B33E0D55157DFC2D198C0BC1 | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_3380.36279 | compressed | |
MD5:8B49A4131EC052D2C2A4C2CB0FF8159C | SHA256:DFF84B09A4101072548E04783351E6F8540C721F6DE95B8209CB4E3B96090227 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |