| File name: | 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe |
| Full analysis: | https://app.any.run/tasks/441d90a4-8705-4303-9b11-ba302339dc23 |
| Verdict: | Malicious activity |
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | May 15, 2025, 11:33:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | AE3D912081D1ED9E0E103290D2AA14A5 |
| SHA1: | CA0B14020A16A418E9480D557C7F6F009210F3D7 |
| SHA256: | 4954B1413717C7E81AD5E75F68B9EBA2F4BC5E30B2647B7725828170A0988EFA |
| SSDEEP: | 1536:UWLUqPsuGc+kfq9o86XLX3ixLklrvmPzYxAfcwBgpGWshaqFcQRbHF4q:U9mfq9o86TSdklyrRcyusNzNHB |
MALICIOUS
Disables task manager
- svchost.exe (PID: 7356)
Changes the autorun value in the registry
- svchost.exe (PID: 7356)
Deletes shadow copies
- cmd.exe (PID: 7776)
- cmd.exe (PID: 6244)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 8104)
RANSOMWARE has been detected
- svchost.exe (PID: 7356)
Modifies files in the Chrome extension folder
- svchost.exe (PID: 7356)
CHAOS has been detected (YARA)
- svchost.exe (PID: 7356)
Create files in the Startup directory
- svchost.exe (PID: 7356)
SUSPICIOUS
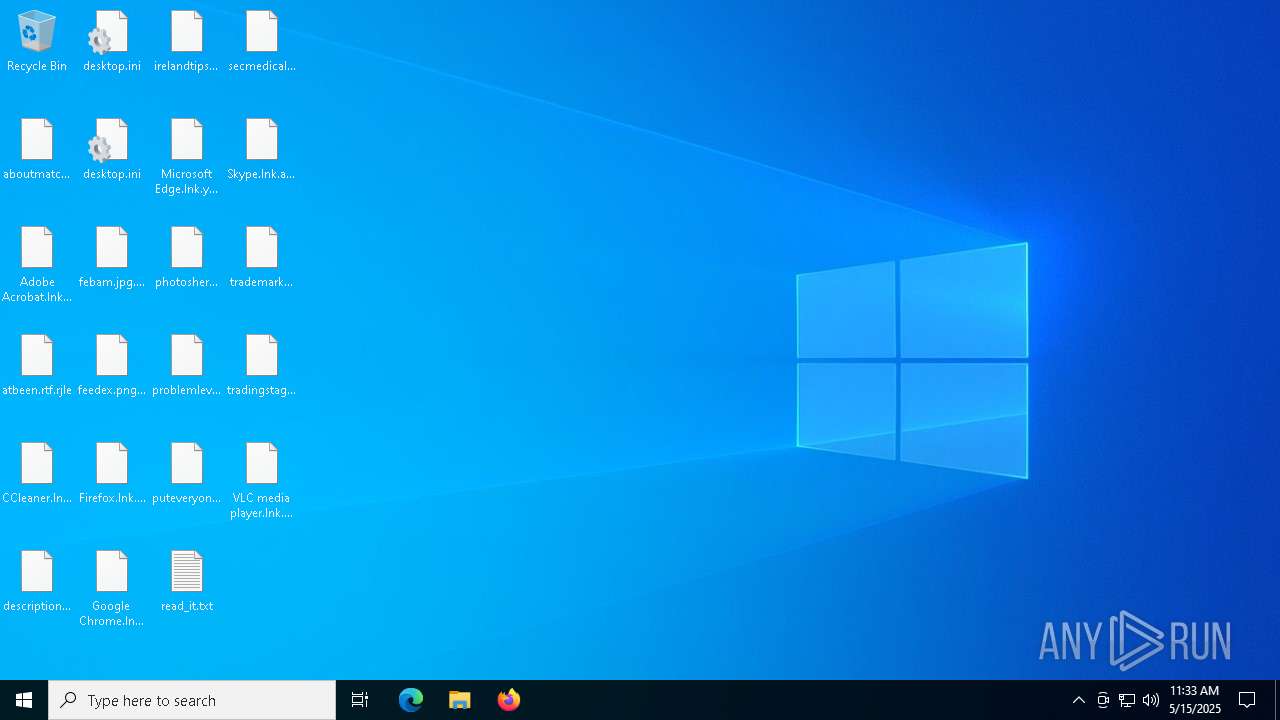
Executable content was dropped or overwritten
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
Reads security settings of Internet Explorer
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
- svchost.exe (PID: 7356)
Reads the date of Windows installation
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
- svchost.exe (PID: 7356)
Starts itself from another location
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
Executes as Windows Service
- wbengine.exe (PID: 4620)
- vds.exe (PID: 5720)
- VSSVC.exe (PID: 7860)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 7356)
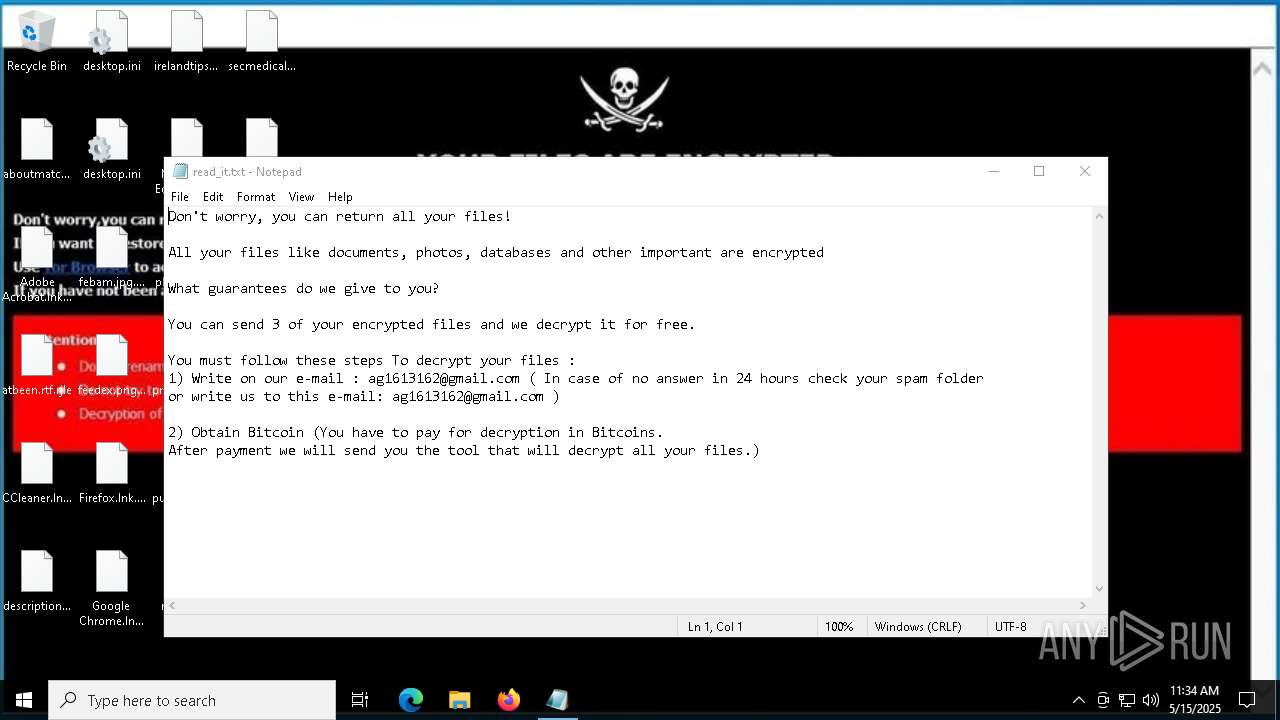
Start notepad (likely ransomware note)
- svchost.exe (PID: 7356)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 7356)
INFO
Checks supported languages
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
- svchost.exe (PID: 7356)
Reads the machine GUID from the registry
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
- svchost.exe (PID: 7356)
Reads the computer name
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
- svchost.exe (PID: 7356)
Process checks computer location settings
- 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe (PID: 6108)
- svchost.exe (PID: 7356)
Creates files in the program directory
- svchost.exe (PID: 7356)
Creates files or folders in the user directory
- svchost.exe (PID: 7356)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7972)
- notepad.exe (PID: 7448)
Reads Microsoft Office registry keys
- svchost.exe (PID: 7356)
Create files in a temporary directory
- svchost.exe (PID: 7356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:01 16:32:07+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 71168 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1356e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | ransomeware.exe |
| LegalCopyright: | |
| OriginalFileName: | ransomeware.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
152
Monitored processes
20
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | "C:\WINDOWS\system32\wbengine.exe" | C:\Windows\System32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5544 | wbadmin delete catalog -quiet | C:\Windows\System32\wbadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6036 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6108 | "C:\Users\admin\AppData\Local\Temp\4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe" | C:\Users\admin\AppData\Local\Temp\4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 6244 | "C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7144 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7356 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
5 098
Read events
5 061
Write events
19
Delete events
18
Modification events
| (PID) Process: | (7356) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateTask |
Value: C:\Users\admin\AppData\Roaming\svchost.exe | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Boot\Loader.efi | |||
| (PID) Process: | (8160) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{a5a30fa2-3d06-4e9f-b5f4-a01df9d1fcba}\Description |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
564
Text files
872
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7356 | svchost.exe | C:\$WinREAgent\RollbackInfo.ini.tvuq | binary | |
MD5:AA364D57A3565DCE6A3002BA23C697BF | SHA256:920B11C34B1D967E5A9C412DDAF7C662D7E4F1755D7770C72A215925C5E59257 | |||
| 6108 | 4954b1413717c7e81ad5e75f68b9eba2f4bc5e30b2647b7725828170a0988efa.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:AE3D912081D1ED9E0E103290D2AA14A5 | SHA256:4954B1413717C7E81AD5E75F68B9EBA2F4BC5E30B2647B7725828170A0988EFA | |||
| 7356 | svchost.exe | C:\$WinREAgent\Backup\read_it.txt | text | |
MD5:4C78BE4A1A58FD1A9C578EC2764088B0 | SHA256:41AF7386CF53609D4CED48C1F69E23FB9AC5C5973F97E4288D871EAFB6B93F83 | |||
| 7356 | svchost.exe | C:\$WinREAgent\Rollback.xml | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 7356 | svchost.exe | C:\$WinREAgent\Backup\location.txt.cx87 | binary | |
MD5:27C90711E297E3CD9926A76F2A080FC0 | SHA256:4E0A1825A8E5AD4D1022CAD59B8F4B8FC94F9BBF678CE3A621F7C173A35B40FD | |||
| 7356 | svchost.exe | C:\$WinREAgent\Backup\location.txt | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 7356 | svchost.exe | C:\found.000\dir0001.chk\WmiApRpl.ini.jjmz | binary | |
MD5:24BA97F12D1A711EB6E9B980C69BB52E | SHA256:B1B992EFBCFFF37034D32B6FE3458644C1C786E564FBB3E56928938A2DD0BC0E | |||
| 7356 | svchost.exe | C:\$WinREAgent\Backup\ReAgent.xml | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 7356 | svchost.exe | C:\found.000\dir0001.chk\WmiApRpl.ini | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 7356 | svchost.exe | C:\$WinREAgent\Rollback.xml.8p9v | binary | |
MD5:9C05111DD3FA902E8440F40632A0983D | SHA256:4041F22346AECF986B48535F48B442D78AC4AB99345AEE867F6CA3108F77CB48 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.18.190.71:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7444 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7444 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5556 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.18.190.71:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7444 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |