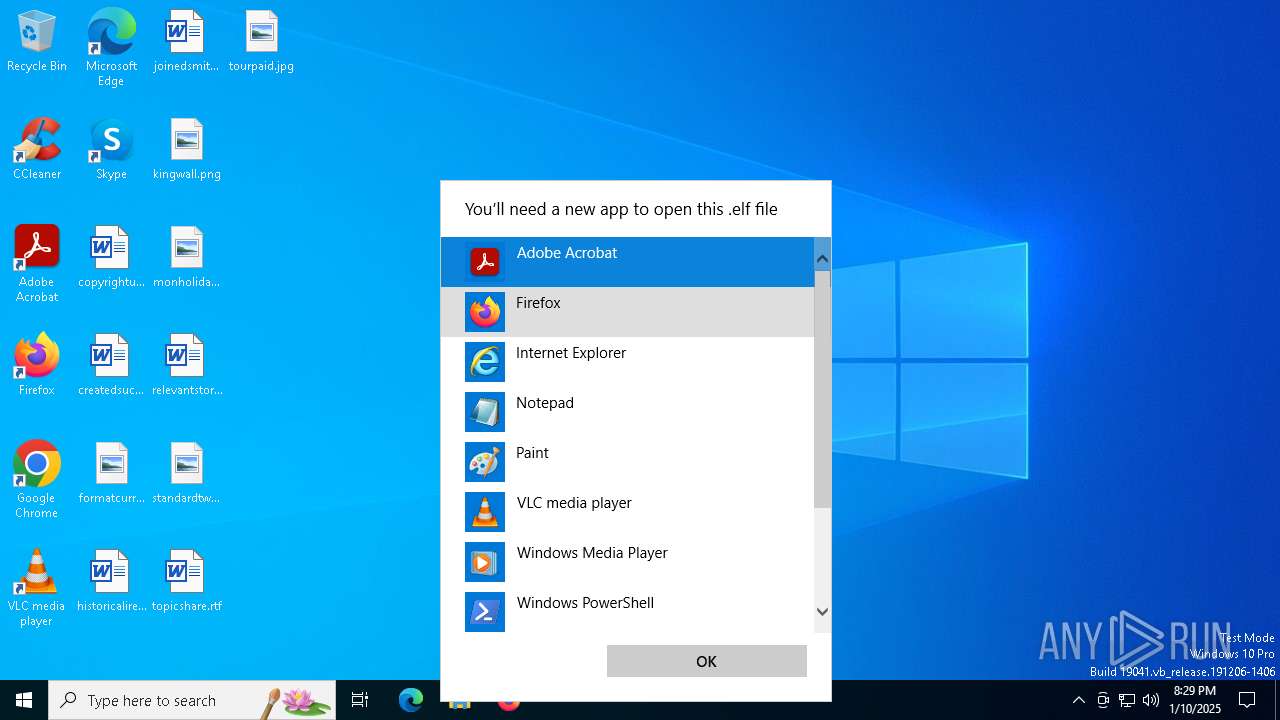
| File name: | 48f3923c4a5434675a38008a4dc75aed93a0b751b35070fc09d1a271923e8852.elf |
| Full analysis: | https://app.any.run/tasks/923f0e56-7031-45ea-8f54-16e3efddf1bd |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | January 10, 2025, 20:29:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-executable |
| File info: | ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, stripped |
| MD5: | BA4C87BB28F2537300B633B56DD6336C |
| SHA1: | F7E761C2282E0AC8A1E2EC3333B6646FEAFF3F9D |
| SHA256: | 48F3923C4A5434675A38008A4DC75AED93A0B751B35070FC09D1A271923E8852 |
| SSDEEP: | 1536:MRczFjv1OwrqkXwlRU66804OsG4Ic/4hxV+NDo5t:Mqt9qkXwlR70Df4Ic/4heNDo5 |
MALICIOUS
BOTNET has been found (auto)
- OpenWith.exe (PID: 4724)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .o | | | ELF Executable and Linkable format (generic) (100) |
|---|
EXIF
EXE
| CPUArchitecture: | 32 bit |
|---|---|
| CPUByteOrder: | Little endian |
| ObjectFileType: | Executable file |
| CPUType: | Arm (up to Armv7/AArch32) |
Total processes
124
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4724 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\AppData\Local\Temp\48f3923c4a5434675a38008a4dc75aed93a0b751b35070fc09d1a271923e8852.elf | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
649
Read events
649
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
15
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 184.51.252.63:443 | www.bing.com | Akamai International B.V. | SE | whitelisted |
2160 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | whitelisted |
— | — | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |