| File name: | strings2.exe |
| Full analysis: | https://app.any.run/tasks/64bdbeeb-9186-4f70-bfee-562d28290984 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 04, 2025, 13:32:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 6FAF652806018BBD36CFEED1CDF198AE |
| SHA1: | DF186AB88C4E0EA2FF5D5477B2077EC628C42D18 |
| SHA256: | 488EE4E5457EDE812FEAFE470BE88C88069ADA5F09C5607036BA70493AB2146A |
| SSDEEP: | 12288:F0Fmj0Fm80FmO0FmNAagKOn+7pOTxGqdij7UN0tTrQOrf0b/yGonQ:F0Mj0M80MO0MNAaglqOTaV370bXonQ |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2200)
Steals credentials from Web Browsers
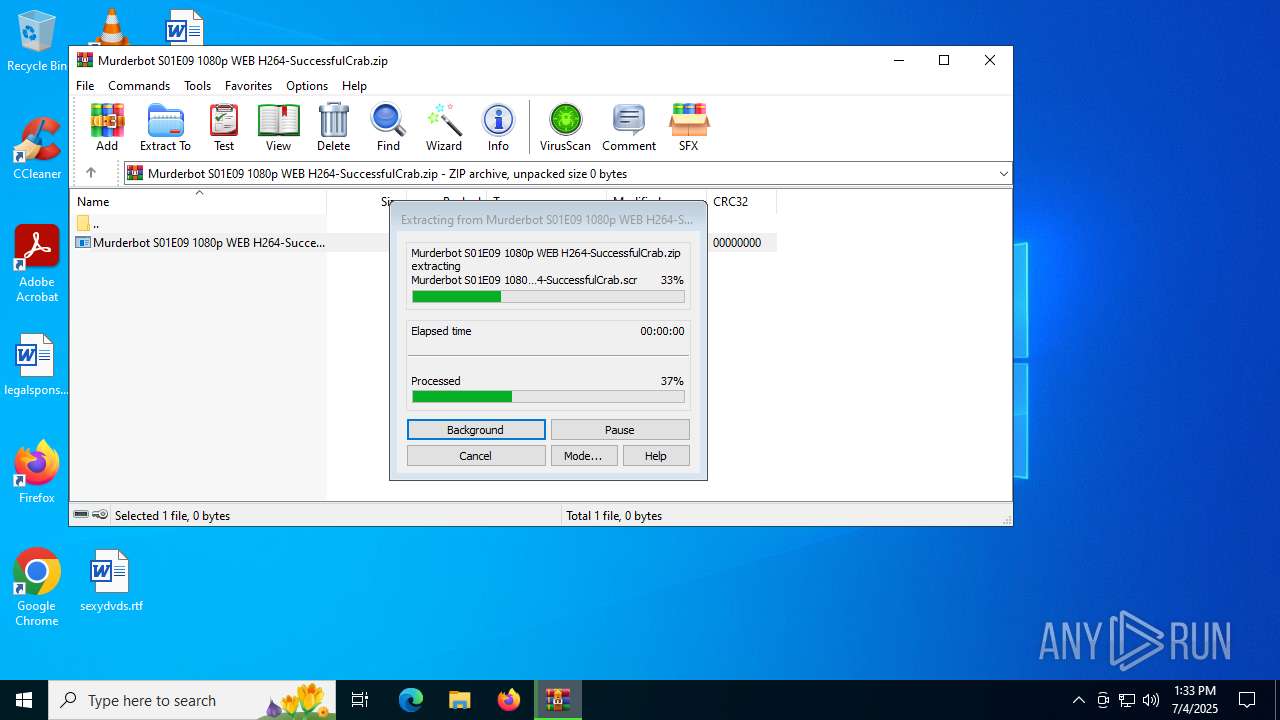
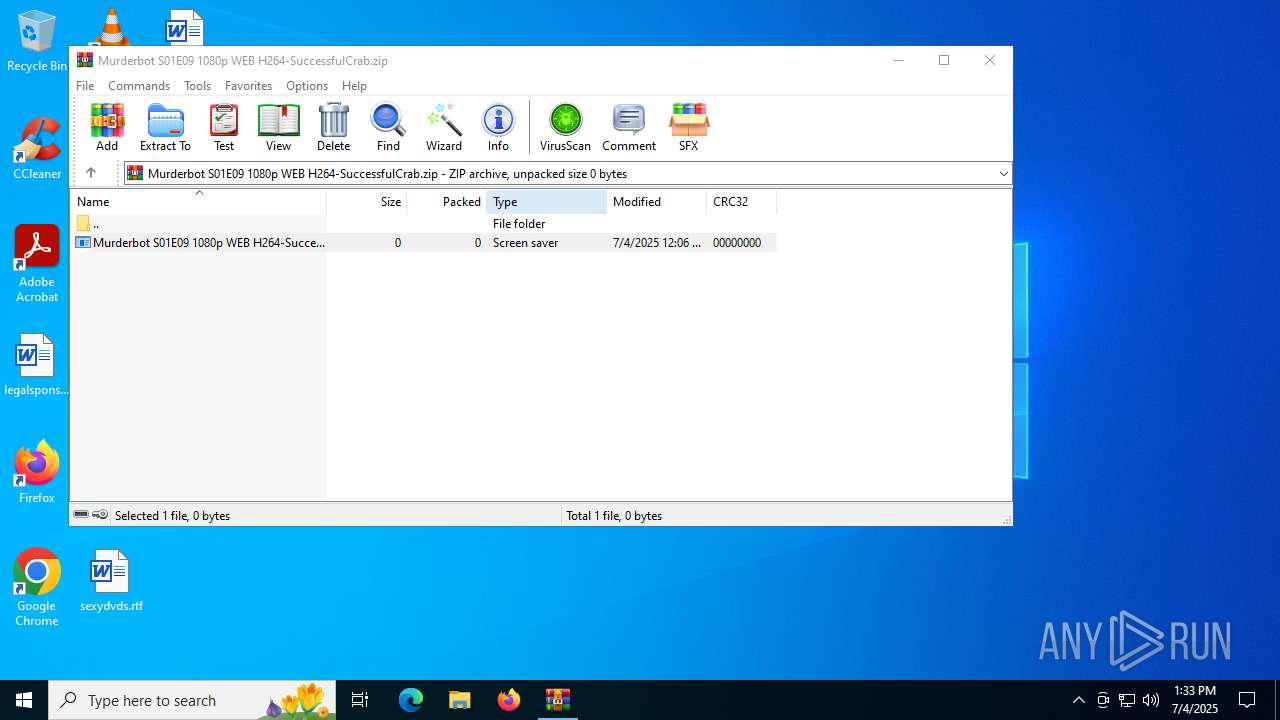
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
Actions looks like stealing of personal data
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
LUMMA mutex has been found
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
- svchost.exe (PID: 2200)
There is functionality for taking screenshot (YARA)
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
INFO
Checks supported languages
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
- strings2.exe (PID: 7052)
Reads the machine GUID from the registry
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
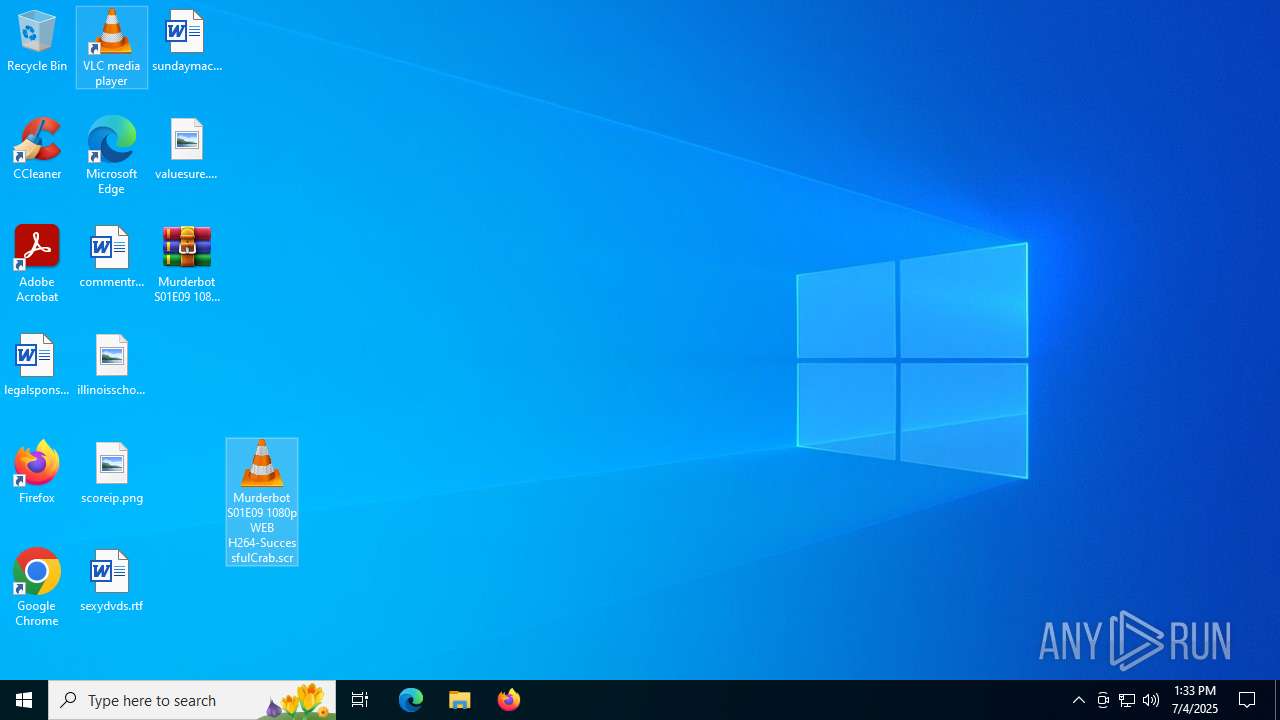
Manual execution by a user
- WinRAR.exe (PID: 3944)
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
Reads the software policy settings
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
- slui.exe (PID: 2528)
Application launched itself
- chrome.exe (PID: 6896)
- chrome.exe (PID: 5708)
- chrome.exe (PID: 1660)
- chrome.exe (PID: 2512)
- msedge.exe (PID: 1520)
- msedge.exe (PID: 6896)
- msedge.exe (PID: 3820)
- msedge.exe (PID: 4800)
- msedge.exe (PID: 2288)
- msedge.exe (PID: 3820)
Checks proxy server information
- slui.exe (PID: 2528)
Reads the computer name
- Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr (PID: 4644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:05:30 04:50:06+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 830976 |
| InitializedDataSize: | 220160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x77250 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (Canadian) |
| CharacterSet: | Unicode |
| CompanyName: | Geoff McDonald |
| FileDescription: | Strings2: Extract strings from binary content. |
| FileVersion: | 2.0.0.0 |
| InternalName: | strings2.exe |
| LegalCopyright: | Copyright (C) 2022 |
| OriginalFileName: | strings2.exe |
| ProductName: | Strings2 |
| ProductVersion: | 2.0.0.0 |
Total processes
206
Monitored processes
68
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4224,i,16271295082382355502,2677314205078075556,262144 --variations-seed-version --mojo-platform-channel-handle=4944 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=4504,i,8367311046057491603,4410019074047558083,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4648 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x220,0x224,0x228,0x1fc,0x22c,0x7ffc44c8fff8,0x7ffc44c90004,0x7ffc44c90010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 728 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=3820,i,531766720811290388,3361270675215073019,262144 --variations-seed-version --mojo-platform-channel-handle=3740 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 756 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3612,i,531766720811290388,3361270675215073019,262144 --variations-seed-version --mojo-platform-channel-handle=3628 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5020,i,17815550044937556252,10940199015555623491,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5036 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --instant-process --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3708,i,9175663473080842670,12452175507151939651,262144 --variations-seed-version --mojo-platform-channel-handle=3776 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1688 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3216,i,5108016858778416732,1744256063120275622,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3248 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
22 190
Read events
22 119
Write events
71
Delete events
0
Modification events
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Murderbot S01E09 1080p WEB H264-SuccessfulCrab.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
30
Suspicious files
283
Text files
201
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3944.30100\Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF1809ee.TMP | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1809ee.TMP | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1809fd.TMP | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF1809fd.TMP | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1809fd.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
194
DNS requests
166
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6876 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5900 | chrome.exe | GET | 200 | 142.250.185.206:80 | http://clients2.google.com/time/1/current?cup2key=8:yVqc11aPRaW-dp0V4ODPCGOdn0nwX5vP_U6d6X2SPnE&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2648 | chrome.exe | GET | 200 | 142.250.185.206:80 | http://clients2.google.com/time/1/current?cup2key=8:cLe3JKe1V30avwFXX2Rgyo7Szko7Y93kZBdsnAImmao&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6376 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:7D_6G00jPOqFJkYstLnXQDMZn5UcI7E0CkySCQFwCWU&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6936 | chrome.exe | GET | 200 | 142.250.185.206:80 | http://clients2.google.com/time/1/current?cup2key=8:ddj1SVBjyAgJEwKV4SGnH23a6H3mqQj1NN6d_WNKYNQ&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4916 | chrome.exe | GET | 200 | 142.250.185.206:80 | http://clients2.google.com/time/1/current?cup2key=8:P_kiYmGpPsNA1v8FAQEAfUwhg2NPMnVNZ_GegqS6TMk&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6980 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:FbXkxantwnWYPdxQM6Yw2jgGodcFQ9M3cXklBZFbONM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6368 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6876 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (unurew .xyz) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (pacwpw .xyz) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (trsuv .xyz) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (comkxjs .xyz) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | MALWARE [ANY.RUN] Win32/Lumma CnC related domain (comkxjs .xyz) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | MALWARE [ANY.RUN] Win32/Lumma CnC related domain (pacwpw .xyz) |
4644 | Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | Not Suspicious Traffic | ET INFO OpenSSL Demo CA - Internet Widgits Pty (O) |
4644 | Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (trsuv .xyz) in TLS SNI |
4644 | Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (trsuv .xyz) in TLS SNI |
4644 | Murderbot S01E09 1080p WEB H264-SuccessfulCrab.scr | Not Suspicious Traffic | ET INFO OpenSSL Demo CA - Internet Widgits Pty (O) |