| File name: | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe |
| Full analysis: | https://app.any.run/tasks/f49edbbf-af77-4cb2-adaa-0e1813bb22a1 |
| Verdict: | Malicious activity |
| Threats: | Maze is ransomware — a malware type that encrypts the victim’s files and restores the data in exchange for a ransom payment. One of the most distinguishable features of Maze is that it is one of the first malware of the kind to publicly release stolen data. |
| Analysis date: | May 30, 2025, 15:44:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 910509A686DF19980EB53DA607DCEDDC |
| SHA1: | F93539C26A99A46C85C40ABCB0B3AAEB98C86DED |
| SHA256: | 485DA83D711D4F9B1F968C7C7E62B30A9987E7CC5A961E5B92A4AB9FCB11611D |
| SSDEEP: | 12288:k1kfxfDVLmX9GbGypH3wl69qKX1L8jH2aF0jJx66dibr5OVSUqARshrDPDizxyrO:SkfxLwtNxzi8AloCxlmja |
MALICIOUS
MAZE has been detected (YARA)
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
MAZE mutex has been found
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
RANSOMWARE has been detected
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Create files in the Startup directory
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Writes a file to the Word startup folder
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
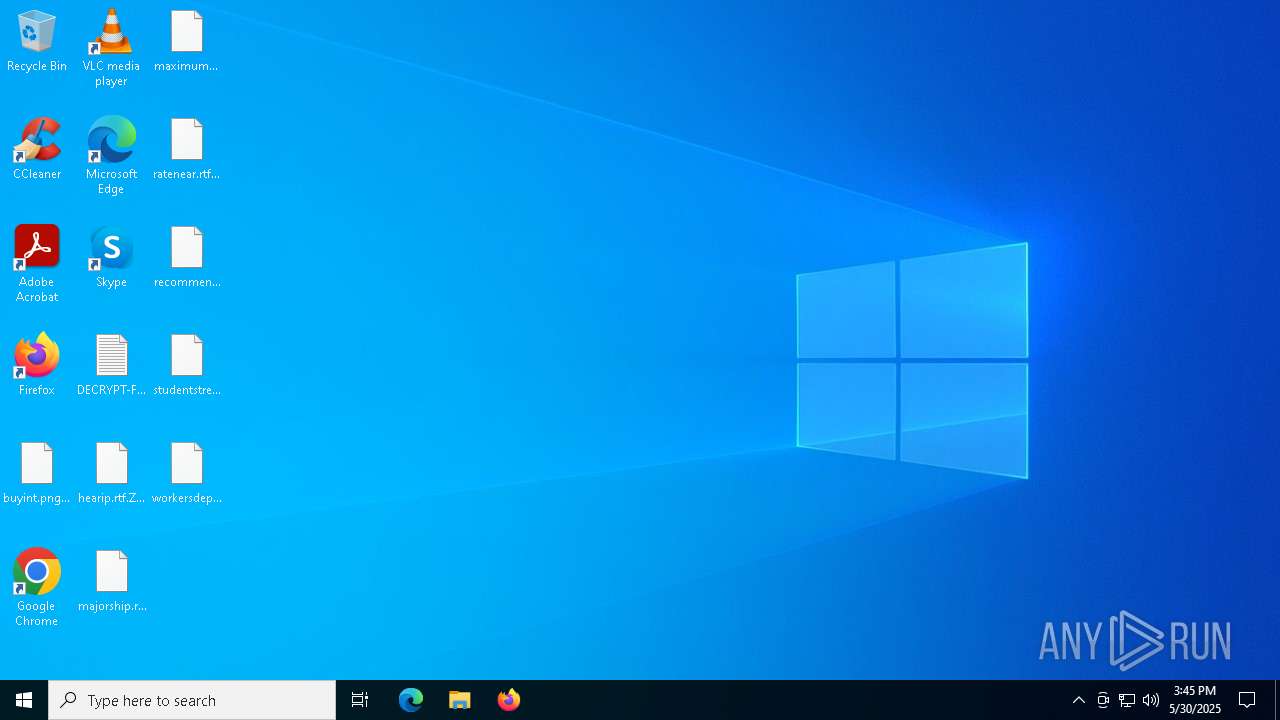
Renames files like ransomware
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Deletes shadow copies
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
SUSPICIOUS
Creates file in the systems drive root
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Reads security settings of Internet Explorer
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
INFO
Reads the computer name
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Checks supported languages
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Creates files in the program directory
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Reads the machine GUID from the registry
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Creates files or folders in the user directory
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Launch of the file from Startup directory
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Checks proxy server information
- 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe (PID: 6476)
Reads the software policy settings
- slui.exe (PID: 3828)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:28 13:29:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 240640 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x219e0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
128
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 716 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3828 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | "C:\Users\admin\AppData\Local\Temp\485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe" | C:\Users\admin\AppData\Local\Temp\485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7824 | "C:\vbii\yyw\..\..\WINDOWS\ogcct\..\system32\hkrqd\lfs\rvlo\..\..\..\wbem\hw\l\..\..\wmic.exe" shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7928 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 238
Read events
1 235
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6476) 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6476) 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6476) 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
774
Text files
336
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\AppData\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\AppData\Roaming\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\.ms-ad\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\BOOTNXT.3nNf | binary | |
MD5:038DCDDC46F7BEC0E113663E517AF970 | SHA256:021F6FAB498549EE40352BA50025021D3F66E4B15B34DB1361A9473842A3F5BD | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\bootTel.dat.3nNf | binary | |
MD5:E69D6BC81CBC0EC4B58FE6FD55AC85FC | SHA256:8C5DC4DFBD82BB37716411A5DE5B8ED5921493FAEC68F5488D4DDF7500368DBD | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\AppData\Local\VirtualStore\BOOTNXT | binary | |
MD5:038DCDDC46F7BEC0E113663E517AF970 | SHA256:021F6FAB498549EE40352BA50025021D3F66E4B15B34DB1361A9473842A3F5BD | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
| 6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | C:\Users\admin\AppData\Local\VirtualStore\DECRYPT-FILES.txt | text | |
MD5:7E5E05A6EED1B06D7EFE961871FB5EB2 | SHA256:F5E10C682E03C97F87129FA624C1E6139C58488788E4399133BAB08D11BB8DB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5216 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5216 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3760 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8000 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3760 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6476 | 485da83d711d4f9b1f968c7c7e62b30a9987e7cc5a961e5b92a4ab9fcb11611d.exe | 91.218.114.4:80 | — | Hostkey B.v. | RU | malicious |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |