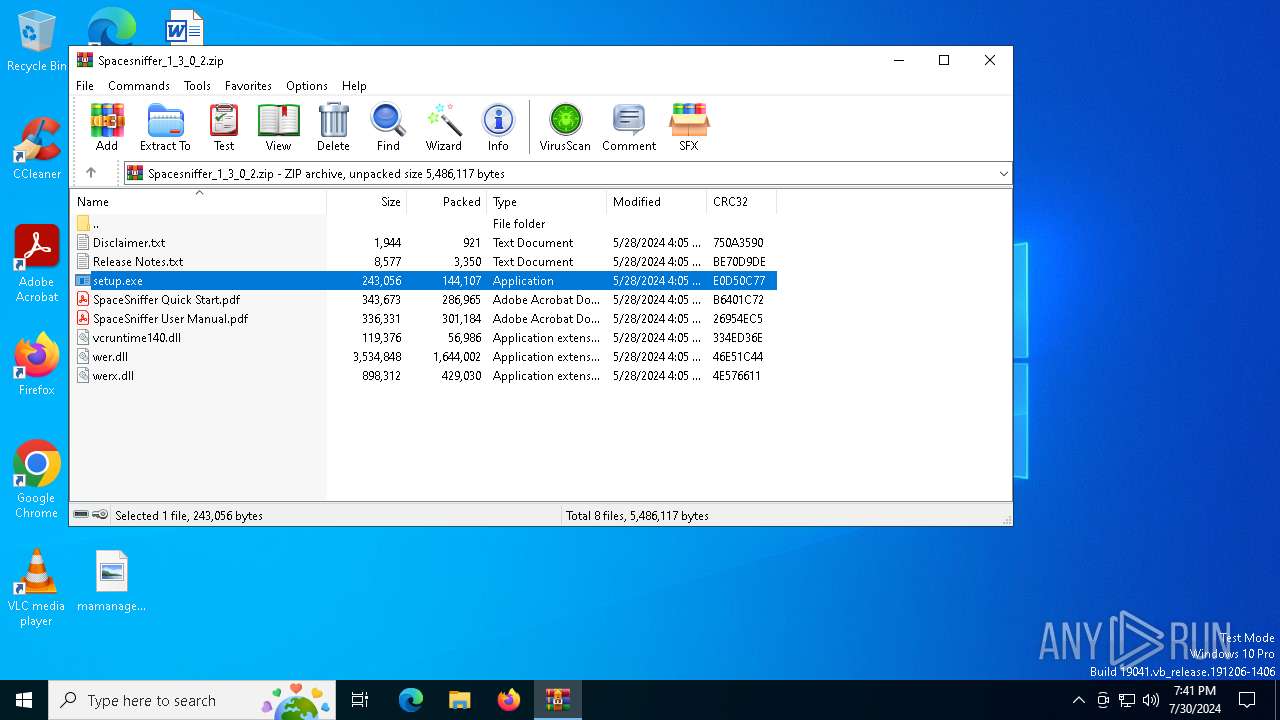
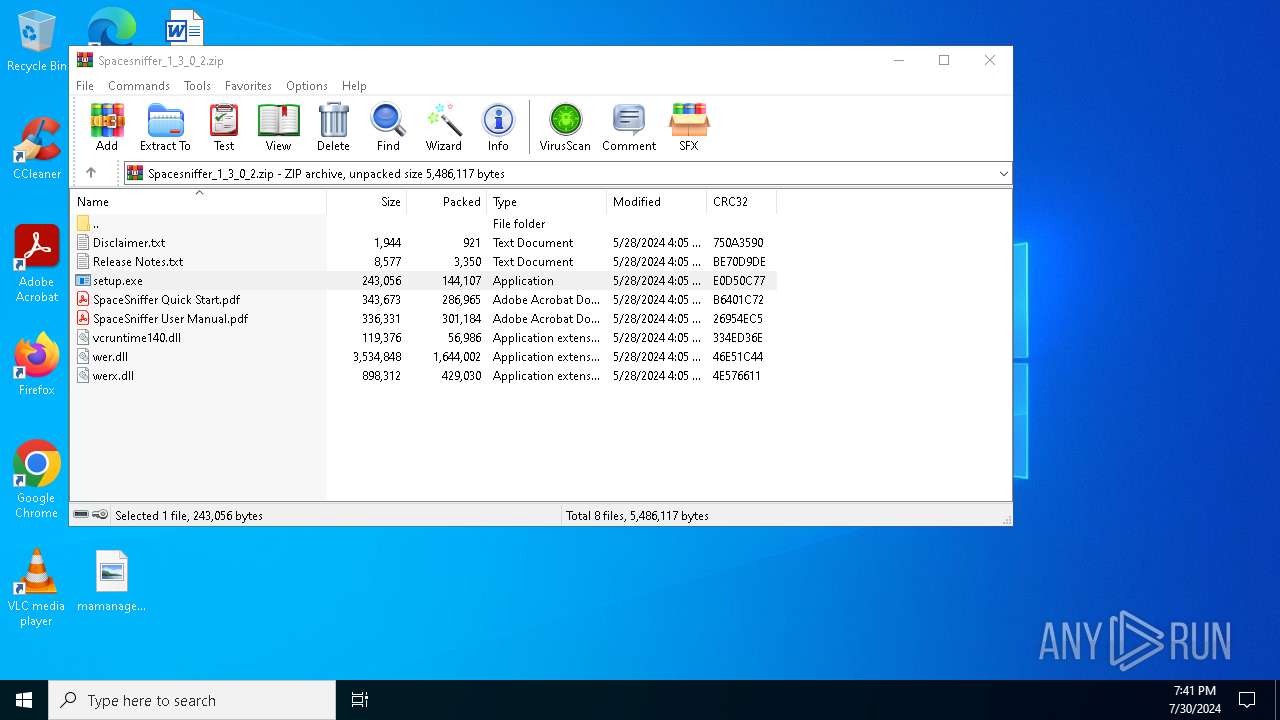
| File name: | Spacesniffer_1_3_0_2.zip |
| Full analysis: | https://app.any.run/tasks/67342c79-4c8a-47d4-ad1a-093b7dc599ff |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | July 30, 2024, 19:40:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 568EBCF0898B13319D440C44AFADAF79 |
| SHA1: | 052D81D5E11F36BA017A9D66F1E5B542AF55C009 |
| SHA256: | 47D1957D069B598672DDAF83FECDB55E079F236804C1DCE973496526FEB15E9D |
| SSDEEP: | 98304:TyWVEa30gP44Sfefn1ln3c6+x1qLCV8cCq1CgspC8A0UHOZAk4reiqxFXBusIwT9:5VWE6+ |
MALICIOUS
Drops the executable file immediately after the start
- setup.exe (PID: 7036)
- WinRAR.exe (PID: 6364)
COBALTSTRIKE has been detected (YARA)
- setup.exe (PID: 7036)
- sihost.exe (PID: 6076)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6364)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6364)
- StartMenuExperienceHost.exe (PID: 2472)
Starts a Microsoft application from unusual location
- setup.exe (PID: 7036)
Executable content was dropped or overwritten
- setup.exe (PID: 7036)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 2472)
- SearchApp.exe (PID: 372)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6364)
Reads security settings of Internet Explorer
- explorer.exe (PID: 888)
Checks supported languages
- setup.exe (PID: 7036)
- SpaceSniffer.exe (PID: 6828)
- StartMenuExperienceHost.exe (PID: 2472)
- TextInputHost.exe (PID: 6268)
- SearchApp.exe (PID: 372)
Reads the computer name
- SpaceSniffer.exe (PID: 6828)
- StartMenuExperienceHost.exe (PID: 2472)
- TextInputHost.exe (PID: 6268)
- SearchApp.exe (PID: 372)
Reads Microsoft Office registry keys
- explorer.exe (PID: 888)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 2472)
- SearchApp.exe (PID: 372)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 372)
Checks proxy server information
- SearchApp.exe (PID: 372)
- explorer.exe (PID: 888)
- slui.exe (PID: 5304)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 372)
Reads the software policy settings
- SearchApp.exe (PID: 372)
- slui.exe (PID: 5304)
Reads Environment values
- SearchApp.exe (PID: 372)
Creates files in the program directory
- setup.exe (PID: 7036)
Creates files or folders in the user directory
- explorer.exe (PID: 888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CobalStrike
(PID) Process(7036) setup.exe
C2 (1)91.92.250.70/broadcast
BeaconTypeHTTPS
Port10443
SleepTime15500
MaxGetSize13982519
Jitter15
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCKCx0TqxEL7f794xRtav1937lV
DGtM4Lqsp0H4tnh87+nsCuqL4povSjRESckHfjoduBm1pNrZScCOHgu3B56PH2ts
Yjc3rCXMO/R4xvln2vMRVRLkKXs5QjW2Fw+q4cC/KNaerhSjVRA7eUKXVSzCAVD8
RGh8oQIuJa/kUNdkPQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\gpupdate.exe
Spawnto_x64%windir%\sysnative\gpupdate.exe
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark1158277545
bStageCleanupTrue
bCFGCautionTrue
UserAgentMozilla/5.0 (Macintosh; Intel Mac OS X 14_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
HttpPostUri/1/events/com.amazon.csm.csa.prod
Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 1 bytes at the end, Remove 194 bytes from the beginning, Base64 decode
HttpGet_Metadata
ConstHeaders (8)Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Origin: https://www.amazon.com
Referer: https://www.amazon.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Te: trailers
SessionId (2)base64
header: x-amzn-RequestId
HttpPost_Metadata
ConstHeaders (2)Accept: */*
Origin: https://www.amazon.com
SessionId (2)base64url
header: x-amz-rid
Output (5)base64url
prepend: {"events":[{"data":{"schemaId":"csa.VideoInteractions.1","application":"Retail:Prod:,"requestId":"MBFV82TTQV2JNBKJJ50B","title":"Amazon.com. Spend less. Smile more.","subPageType":"desktop","session":{"id":"133-9905055-2677266"},"video":{"id":"
append: "
append: "playerMode":"INLINE","videoRequestId":"MBFV82TTQV2JNBKJJ50B","isAudioOn":"false","player":"IVS","event":"NONE"}}}}]}
print
bUsesCookies0000
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXFalse
bProcInject_UseRWXFalse
bProcInject_MinAllocSize8092
ProcInject_PrependAppend_x866687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00..
ProcInject_PrependAppend_x646687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00..
ProcInject_Stub5462f8cce537c664d9b20f4f03cc8339
ProcInject_AllocationMethodNtMapViewOfSection
(PID) Process(6076) sihost.exe
C2 (1)91.92.250.70/broadcast
BeaconTypeHTTPS
Port10443
SleepTime15500
MaxGetSize13982519
Jitter15
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCKCx0TqxEL7f794xRtav1937lV
DGtM4Lqsp0H4tnh87+nsCuqL4povSjRESckHfjoduBm1pNrZScCOHgu3B56PH2ts
Yjc3rCXMO/R4xvln2vMRVRLkKXs5QjW2Fw+q4cC/KNaerhSjVRA7eUKXVSzCAVD8
RGh8oQIuJa/kUNdkPQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\gpupdate.exe
Spawnto_x64%windir%\sysnative\gpupdate.exe
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark1158277545
bStageCleanupTrue
bCFGCautionTrue
UserAgentMozilla/5.0 (Macintosh; Intel Mac OS X 14_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
HttpPostUri/1/events/com.amazon.csm.csa.prod
Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 1 bytes at the end, Remove 194 bytes from the beginning, Base64 decode
HttpGet_Metadata
ConstHeaders (8)Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Origin: https://www.amazon.com
Referer: https://www.amazon.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Te: trailers
SessionId (2)base64
header: x-amzn-RequestId
HttpPost_Metadata
ConstHeaders (2)Accept: */*
Origin: https://www.amazon.com
SessionId (2)base64url
header: x-amz-rid
Output (5)base64url
prepend: {"events":[{"data":{"schemaId":"csa.VideoInteractions.1","application":"Retail:Prod:,"requestId":"MBFV82TTQV2JNBKJJ50B","title":"Amazon.com. Spend less. Smile more.","subPageType":"desktop","session":{"id":"133-9905055-2677266"},"video":{"id":"
append: "
append: "playerMode":"INLINE","videoRequestId":"MBFV82TTQV2JNBKJJ50B","isAudioOn":"false","player":"IVS","event":"NONE"}}}}]}
print
bUsesCookies0000
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXFalse
bProcInject_UseRWXFalse
bProcInject_MinAllocSize8092
ProcInject_PrependAppend_x866687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00..
ProcInject_PrependAppend_x646687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00..
ProcInject_Stub5462f8cce537c664d9b20f4f03cc8339
ProcInject_AllocationMethodNtMapViewOfSection
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:28 09:05:20 |
| ZipCRC: | 0x750a3590 |
| ZipCompressedSize: | 921 |
| ZipUncompressedSize: | 1944 |
| ZipFileName: | Disclaimer.txt |
Total processes
157
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | explorer.exe /LOADSAVEDWINDOWS | C:\Windows\explorer.exe | — | sihost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2472 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3704 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5304 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6076 | \??\C:\Windows\System32\sihost.exe | C:\Windows\System32\sihost.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Shell Infrastructure Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
CobalStrike(PID) Process(6076) sihost.exe C2 (1)91.92.250.70/broadcast BeaconTypeHTTPS Port10443 SleepTime15500 MaxGetSize13982519 Jitter15 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCKCx0TqxEL7f794xRtav1937lV
DGtM4Lqsp0H4tnh87+nsCuqL4povSjRESckHfjoduBm1pNrZScCOHgu3B56PH2ts
Yjc3rCXMO/R4xvln2vMRVRLkKXs5QjW2Fw+q4cC/KNaerhSjVRA7eUKXVSzCAVD8
RGh8oQIuJa/kUNdkPQIDAQAB
-----END PUBLIC KEY----- DNS_strategyround-robin DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86%windir%\syswow64\gpupdate.exe Spawnto_x64%windir%\sysnative\gpupdate.exe CryptoScheme0 HttpGet_VerbGET HttpPost_VerbPOST HttpPostChunk0 Watermark1158277545 bStageCleanupTrue bCFGCautionTrue UserAgentMozilla/5.0 (Macintosh; Intel Mac OS X 14_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36 HttpPostUri/1/events/com.amazon.csm.csa.prod Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 1 bytes at the end, Remove 194 bytes from the beginning, Base64 decode HttpGet_Metadata ConstHeaders (8)Accept: application/json, text/plain, */* Accept-Language: en-US,en;q=0.5 Origin: https://www.amazon.com Referer: https://www.amazon.com Sec-Fetch-Dest: empty Sec-Fetch-Mode: cors Sec-Fetch-Site: cross-site Te: trailers SessionId (2)base64 header: x-amzn-RequestId HttpPost_Metadata ConstHeaders (2)Accept: */* Origin: https://www.amazon.com SessionId (2)base64url header: x-amz-rid Output (5)base64url prepend: {"events":[{"data":{"schemaId":"csa.VideoInteractions.1","application":"Retail:Prod:,"requestId":"MBFV82TTQV2JNBKJJ50B","title":"Amazon.com. Spend less. Smile more.","subPageType":"desktop","session":{"id":"133-9905055-2677266"},"video":{"id":" append: " append: "playerMode":"INLINE","videoRequestId":"MBFV82TTQV2JNBKJJ50B","isAudioOn":"false","player":"IVS","event":"NONE"}}}}]} print bUsesCookies0000 Proxy_BehaviorUse IE settings tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXFalse bProcInject_UseRWXFalse bProcInject_MinAllocSize8092 ProcInject_PrependAppend_x866687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00.. ProcInject_PrependAppend_x646687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00.. ProcInject_Stub5462f8cce537c664d9b20f4f03cc8339 ProcInject_AllocationMethodNtMapViewOfSection | |||||||||||||||
| 6268 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6364 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Spacesniffer_1_3_0_2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6828 | C:\Users\Public\Downloads\SpaceSniffer.exe | — | setup.exe | ||||||||||||
User: admin Company: Uderzo Software e Consulenza Informatica Integrity Level: MEDIUM Description: Disk space analysis tool Exit code: 0 Version: 1.3.0.2 Modules
| |||||||||||||||
| 7036 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 2147942487 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
CobalStrike(PID) Process(7036) setup.exe C2 (1)91.92.250.70/broadcast BeaconTypeHTTPS Port10443 SleepTime15500 MaxGetSize13982519 Jitter15 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCKCx0TqxEL7f794xRtav1937lV
DGtM4Lqsp0H4tnh87+nsCuqL4povSjRESckHfjoduBm1pNrZScCOHgu3B56PH2ts
Yjc3rCXMO/R4xvln2vMRVRLkKXs5QjW2Fw+q4cC/KNaerhSjVRA7eUKXVSzCAVD8
RGh8oQIuJa/kUNdkPQIDAQAB
-----END PUBLIC KEY----- DNS_strategyround-robin DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86%windir%\syswow64\gpupdate.exe Spawnto_x64%windir%\sysnative\gpupdate.exe CryptoScheme0 HttpGet_VerbGET HttpPost_VerbPOST HttpPostChunk0 Watermark1158277545 bStageCleanupTrue bCFGCautionTrue UserAgentMozilla/5.0 (Macintosh; Intel Mac OS X 14_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36 HttpPostUri/1/events/com.amazon.csm.csa.prod Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 1 bytes at the end, Remove 194 bytes from the beginning, Base64 decode HttpGet_Metadata ConstHeaders (8)Accept: application/json, text/plain, */* Accept-Language: en-US,en;q=0.5 Origin: https://www.amazon.com Referer: https://www.amazon.com Sec-Fetch-Dest: empty Sec-Fetch-Mode: cors Sec-Fetch-Site: cross-site Te: trailers SessionId (2)base64 header: x-amzn-RequestId HttpPost_Metadata ConstHeaders (2)Accept: */* Origin: https://www.amazon.com SessionId (2)base64url header: x-amz-rid Output (5)base64url prepend: {"events":[{"data":{"schemaId":"csa.VideoInteractions.1","application":"Retail:Prod:,"requestId":"MBFV82TTQV2JNBKJJ50B","title":"Amazon.com. Spend less. Smile more.","subPageType":"desktop","session":{"id":"133-9905055-2677266"},"video":{"id":" append: " append: "playerMode":"INLINE","videoRequestId":"MBFV82TTQV2JNBKJJ50B","isAudioOn":"false","player":"IVS","event":"NONE"}}}}]} print bUsesCookies0000 Proxy_BehaviorUse IE settings tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXFalse bProcInject_UseRWXFalse bProcInject_MinAllocSize8092 ProcInject_PrependAppend_x866687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00.. ProcInject_PrependAppend_x646687c944456687d287db49484c400f1f00434287d24766900f1f0400660f1f040040416687db87c990460f1f000f1f00.. ProcInject_Stub5462f8cce537c664d9b20f4f03cc8339 ProcInject_AllocationMethodNtMapViewOfSection | |||||||||||||||
Total events
44 569
Read events
44 291
Write events
255
Delete events
23
Modification events
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Spacesniffer_1_3_0_2.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
50
Text files
264
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 372 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | der | |
MD5:836D92C831135FFE10D7C33FC0C3FE66 | SHA256:BC7E6EB403F7FF1A2DD37814D4455A399951F876F476F79E10D265079EDD597E | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\Release Notes.txt | text | |
MD5:46FEB3FF3CAED4B53B508DB39664B52E | SHA256:1E3E232CAC8757FBFA45DF3D6288860C0CE7F3425BD3CBAF051510B8928B28AA | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\Disclaimer.txt | text | |
MD5:9BE250E513AEB89502B35F21C0FBF0C4 | SHA256:AC88CF90B4E7643F27EA762D1643CC58D631DC021135BF9B4F02C43A2242894B | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\SpaceSniffer Quick Start.pdf | ||
MD5:7CAA1C6249587B32273517DD53D34979 | SHA256:4D60EBEB8176692FA259A81C8A69622002D272CD13B79E14451980E031E74B79 | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\vcruntime140.dll | executable | |
MD5:699DD61122D91E80ABDFCC396CE0EC10 | SHA256:F843CD00D9AFF9A902DD7C98D6137639A10BD84904D81A085C28A3B29F8223C1 | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\SpaceSniffer User Manual.pdf | ||
MD5:3D1F422D948C87957A56A23593818A8D | SHA256:9EF8CF15B269454E4443FC7F99AA7A582DBD98CE108A45485B3BCF3BD437286C | |||
| 372 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\58\CYGXBN1kkA_ojDY5vKbCoG4Zy0E[1].css | text | |
MD5:DF25912CCFEE50A9E57BC97B4D05B5C0 | SHA256:3CA3D1262A62E919C72A641F7491B38769CFB8149704E69CB6C960836DD9C6F8 | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\werx.dll | executable | |
MD5:0A0CD54859A60630714A076934111E7C | SHA256:C91552FCD8829E182B620D29B333ED5187296F9612F79815F87267A2817823F9 | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6364.27780\setup.exe | executable | |
MD5:0A9EE8F50EF336B422521E133F6CC751 | SHA256:4A135F60A5193F543D452C9D01E98546C44680E7BDF6C043E8837B1DFEAE3875 | |||
| 7036 | setup.exe | C:\Users\Public\Downloads\SpaceSniffer.exe | executable | |
MD5:B310E7335EAE66A533E985B377E81612 | SHA256:FC0629D450F8A57BC93E1BA1CDEF0BFF49C1A4CF0725C2A1F52116FD67D9FE8E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
56
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4584 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
372 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4128 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.122.215.72:443 | — | Akamai International B.V. | DE | unknown |
5900 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 131.253.33.254:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3188 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |