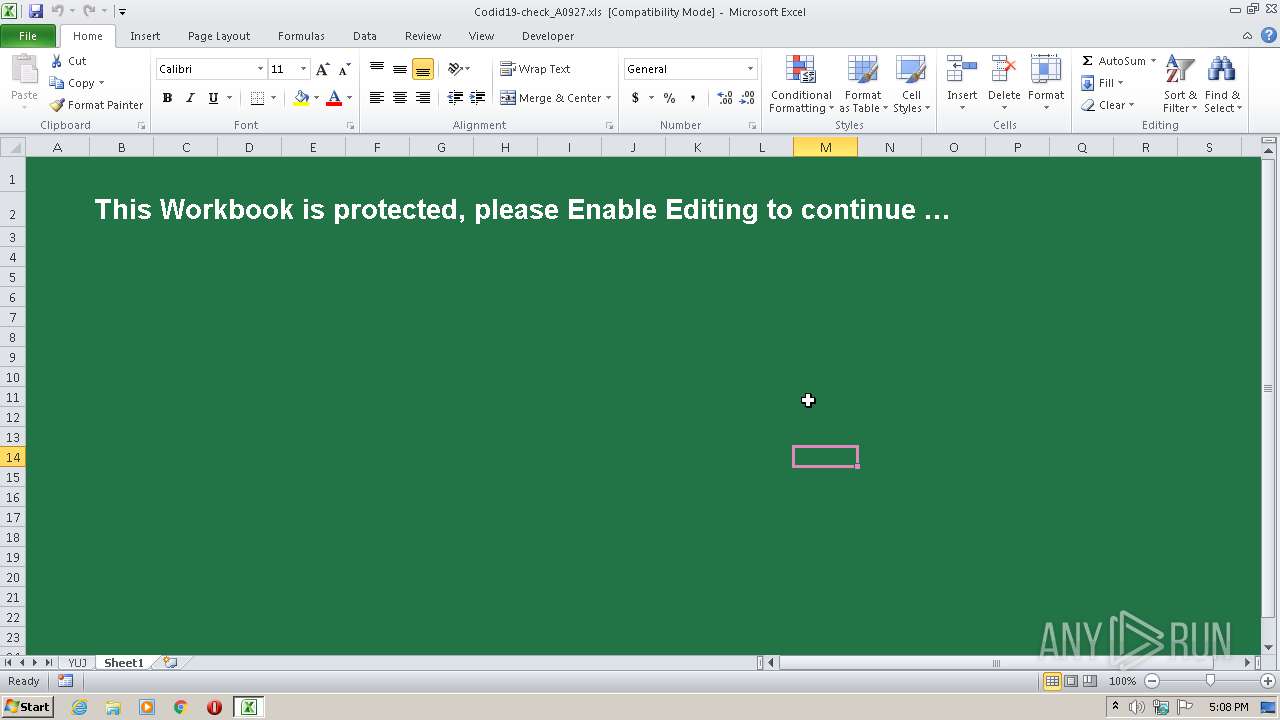
| File name: | Codid19-check_A0927.xls |
| Full analysis: | https://app.any.run/tasks/aba3722a-b373-4dae-8273-8730fb40cdbe |
| Verdict: | Malicious activity |
| Threats: | TrickBot is an advanced banking trojan that attackers can use to steal payment credentials from the victims. It can redirect the victim to a fake banking cabinet and retrieve credentials typed in on the webpage. |
| Analysis date: | June 24, 2020, 16:07:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Mon Jun 22 17:20:38 2020, Last Saved Time/Date: Wed Jun 24 15:43:47 2020, Security: 0 |
| MD5: | 10F8BAC6C273C1D96BBAECF6EEB60B62 |
| SHA1: | BF6B425519BBF5D94AE683C614F1DE34B822330B |
| SHA256: | 47561B4E949041EFF0A0F4693C59C81726591779FE21183AE9185B5EB6A69847 |
| SSDEEP: | 3072:Uk3hOdsylKlgryzc4bNhZFGzE+cL4LgldAIlJdqjZYyc0k3BIhS2NR+w:Uk3hOdsylKlgryzc4bNhZF+E+W4LgldE |
MALICIOUS
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 2092)
Loads dropped or rewritten executable
- rundll32.exe (PID: 700)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2092)
Application was dropped or rewritten from another process
- rundll32.exe (PID: 700)
Loads the Task Scheduler COM API
- rundll32.exe (PID: 700)
TRICKBOT was detected
- rundll32.exe (PID: 700)
Actions looks like stealing of personal data
- rundll32.exe (PID: 700)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- EXCEL.EXE (PID: 2092)
Executable content was dropped or overwritten
- rundll32.exe (PID: 700)
Creates files in the user directory
- rundll32.exe (PID: 700)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 2092)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2092)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 2092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2020:06:22 16:20:38 |
| ModifyDate: | 2020:06:24 14:43:47 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
35
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Windows\System32\rundll32.exe" C:\fkVOVzN\McgiazP\oIDrXgh.dll,DllRegisterServer | C:\Windows\System32\rundll32.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
647
Read events
593
Write events
43
Delete events
11
Modification events
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | c2> |
Value: 63323E002C080000010000000000000000000000 | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2092) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2092 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR8A43.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2092 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\M7T7KRW2.txt | — | |
MD5:— | SHA256:— | |||
| 2092 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\7A6YV7BX.txt | text | |
MD5:— | SHA256:— | |||
| 2092 | EXCEL.EXE | C:\fkVOVzN\McgiazP\oIDrXgh.dll | executable | |
MD5:— | SHA256:— | |||
| 700 | rundll32.exe | C:\Users\admin\AppData\Roaming\DoorBell\revocations.txt | text | |
MD5:— | SHA256:— | |||
| 2092 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\update[1].dll | executable | |
MD5:— | SHA256:— | |||
| 700 | rundll32.exe | C:\Users\admin\AppData\Roaming\DoorBell\dlrundll32ru.dog | executable | |
MD5:51138BEEA3E2C21EC44D0932C71762A8 | SHA256:5AD3C37E6F2B9DB3EE8B5AEEDC474645DE90C66E3D95F8620C48102F1EBA4124 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2092 | EXCEL.EXE | 81.16.141.208:80 | — | — | — | suspicious |
700 | rundll32.exe | 91.235.129.20:443 | — | ITL Company | NL | suspicious |
2092 | EXCEL.EXE | 23.95.231.200:80 | — | ColoCrossing | US | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
2092 | EXCEL.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
2092 | EXCEL.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
2092 | EXCEL.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2092 | EXCEL.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |