| File name: | 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe |
| Full analysis: | https://app.any.run/tasks/8ae08534-48b2-4dc6-ac5c-b46c391ae0ae |
| Verdict: | Malicious activity |
| Threats: | GCleaner is a type of malware loader that has the capability to deliver numerous malicious software programs, which differ based on the location of the targeted victim. This malware is commonly spread through fraudulent websites that advertise free PC optimization tools |
| Analysis date: | August 01, 2025, 04:38:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 9D896D5131C143727CD241F55D51BAFD |
| SHA1: | C5A7A56CCE10ADC1F21AE5DAE30945345787885E |
| SHA256: | 46E562E1967E51D3BAAC23012260C37F4999937FC319EC3868FB832EF0A7E374 |
| SSDEEP: | 98304:M/f8u23l6iLEe5vY5am5DkTTfgXn1Og71h7Ag1iUrBpvBYANUAqQAtcDwe97A50h:FkBOa |
MALICIOUS
GCLEANER has been detected (YARA)
- svchost015.exe (PID: 6492)
LUMMA has been found (auto)
- svchost015.exe (PID: 6492)
LUMMA mutex has been found
- tviwTDgLQOO.exe (PID: 2296)
- MUSWsS12rwt.exe (PID: 6368)
Actions looks like stealing of personal data
- tviwTDgLQOO.exe (PID: 2296)
Steals credentials from Web Browsers
- tviwTDgLQOO.exe (PID: 2296)
SUSPICIOUS
Executable content was dropped or overwritten
- 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe (PID: 6656)
- svchost015.exe (PID: 6492)
- 6BLxsOUpv6L.exe (PID: 2388)
- shPLP1rDI.exe (PID: 7056)
- ERRSPzEwUVO1.exe (PID: 6812)
- ExJQKVva3.exe (PID: 2728)
Reads security settings of Internet Explorer
- svchost015.exe (PID: 6492)
There is functionality for taking screenshot (YARA)
- svchost015.exe (PID: 6492)
- kLPjwNpfzy.exe (PID: 5188)
- Market.com (PID: 1468)
- ARLPL5txvrsO.exe (PID: 1128)
- Market.com (PID: 6472)
- tviwTDgLQOO.exe (PID: 2296)
- Market.com (PID: 4544)
- MUSWsS12rwt.exe (PID: 6368)
- Market.com (PID: 2708)
Connects to the server without a host name
- svchost015.exe (PID: 6492)
Get information on the list of running processes
- cmd.exe (PID: 6240)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 5140)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6240)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 5140)
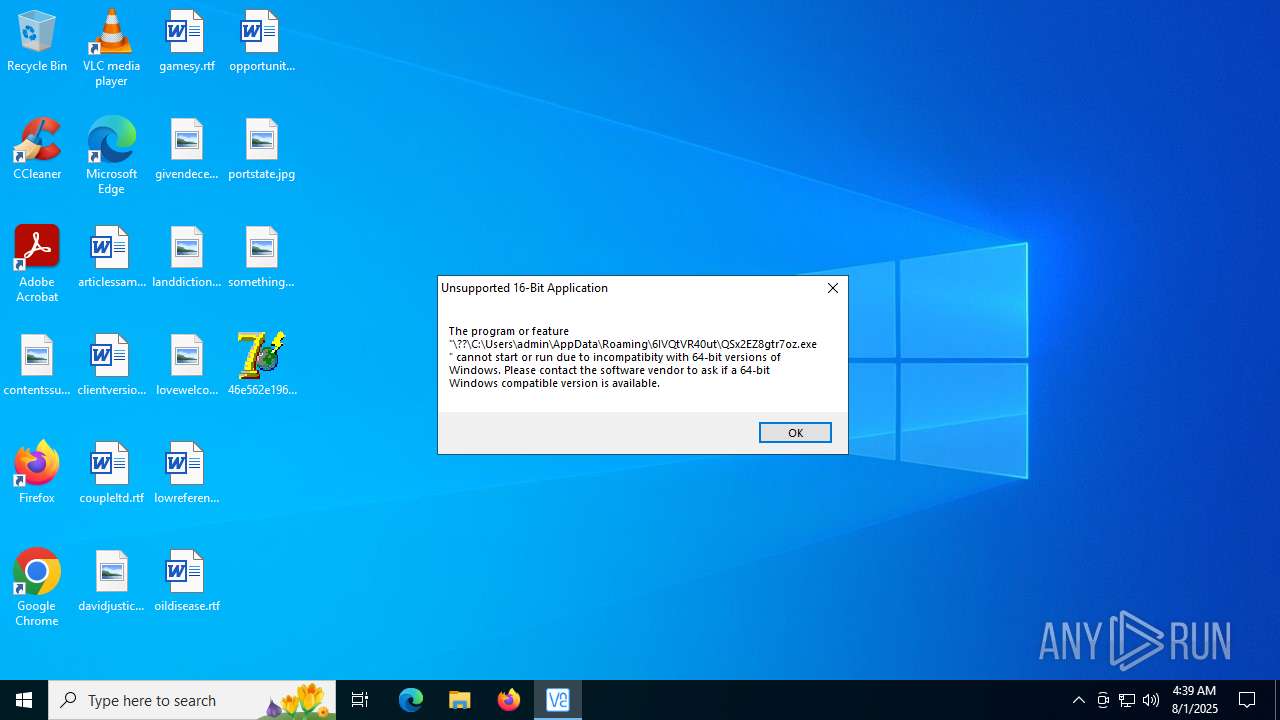
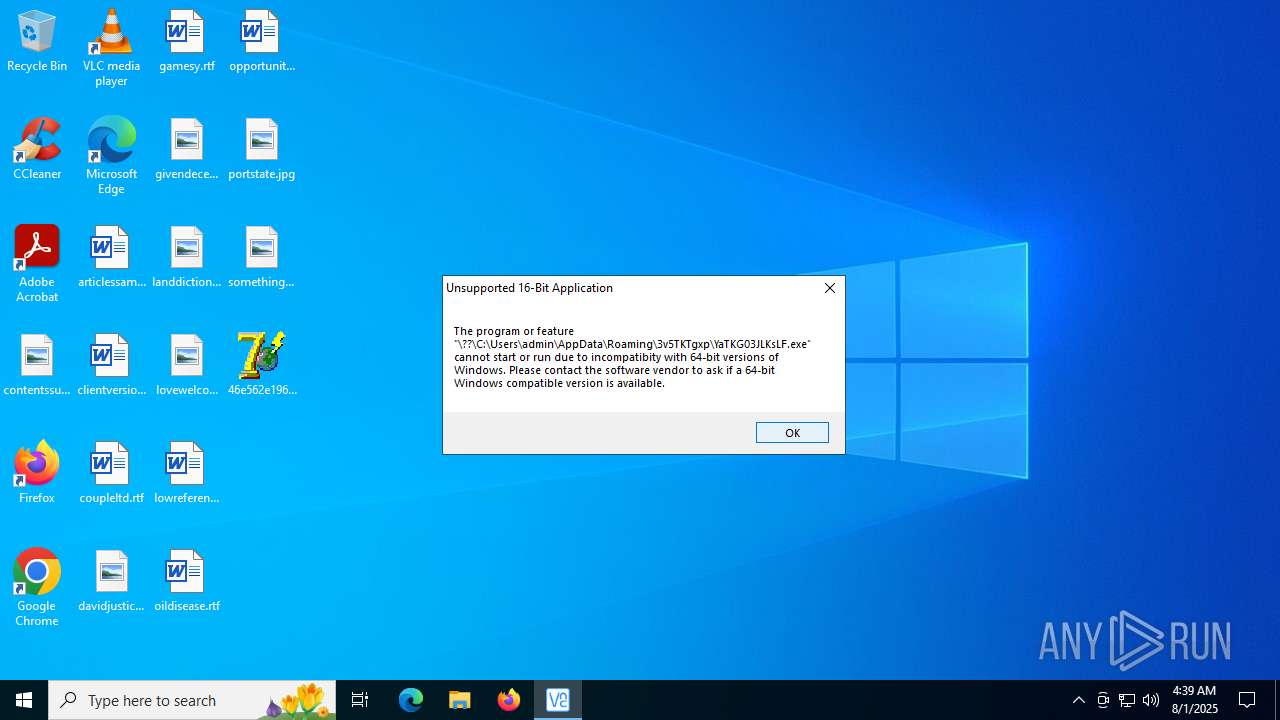
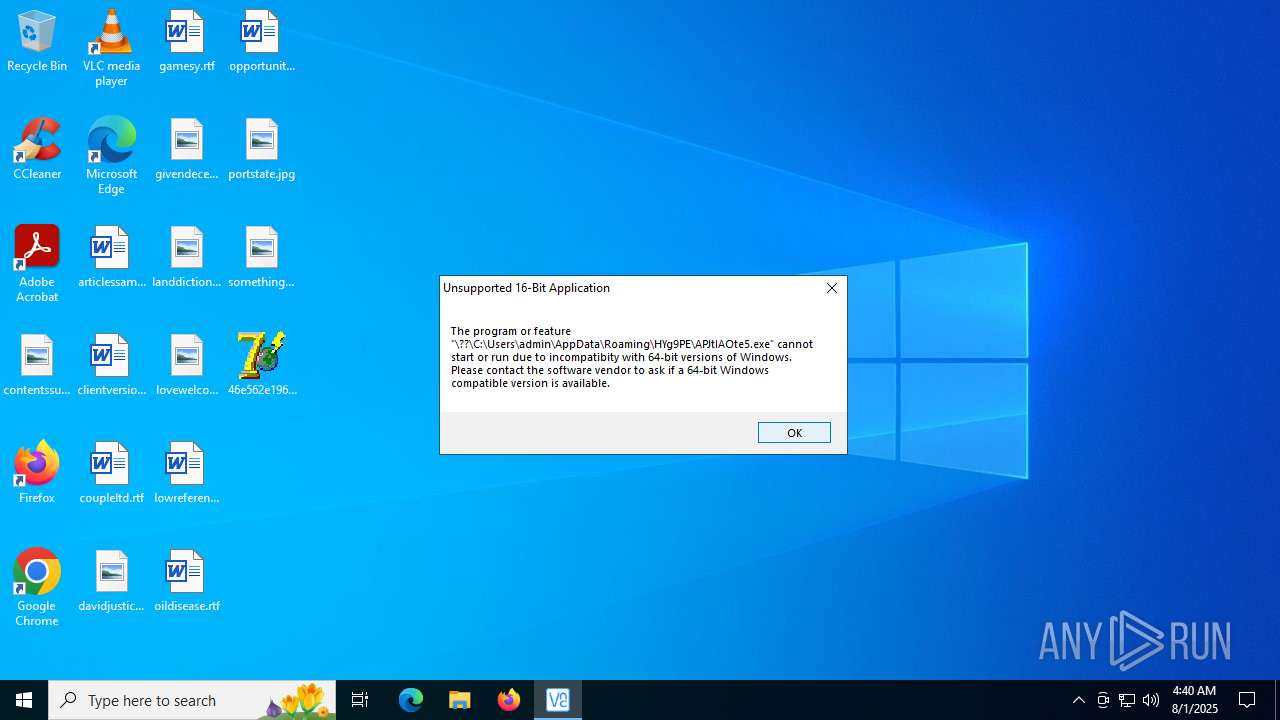
Starts application with an unusual extension
- cmd.exe (PID: 6240)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 5140)
Starts CMD.EXE for commands execution
- 6BLxsOUpv6L.exe (PID: 2388)
- shPLP1rDI.exe (PID: 7056)
- ERRSPzEwUVO1.exe (PID: 6812)
- ExJQKVva3.exe (PID: 2728)
Starts the AutoIt3 executable file
- cmd.exe (PID: 6240)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 5140)
The executable file from the user directory is run by the CMD process
- Market.com (PID: 1468)
- Market.com (PID: 6472)
- Market.com (PID: 4544)
- Market.com (PID: 2708)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6240)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 5140)
Executing commands from ".cmd" file
- 6BLxsOUpv6L.exe (PID: 2388)
- shPLP1rDI.exe (PID: 7056)
- ERRSPzEwUVO1.exe (PID: 6812)
- ExJQKVva3.exe (PID: 2728)
Searches for installed software
- tviwTDgLQOO.exe (PID: 2296)
INFO
The sample compiled with english language support
- 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe (PID: 6656)
- svchost015.exe (PID: 6492)
Checks supported languages
- 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe (PID: 6656)
- svchost015.exe (PID: 6492)
- kLPjwNpfzy.exe (PID: 5188)
- J6m0a0P9zu.exe (PID: 3896)
- 6BLxsOUpv6L.exe (PID: 2388)
- Market.com (PID: 1468)
- extrac32.exe (PID: 5724)
- ARLPL5txvrsO.exe (PID: 1128)
- 4vUeUpIyk.exe (PID: 6236)
- shPLP1rDI.exe (PID: 7056)
- extrac32.exe (PID: 6764)
- tviwTDgLQOO.exe (PID: 2296)
- Market.com (PID: 6472)
- wLqAp8rMUP.exe (PID: 1180)
- ERRSPzEwUVO1.exe (PID: 6812)
- Market.com (PID: 4544)
- extrac32.exe (PID: 4400)
- MUSWsS12rwt.exe (PID: 6368)
- ExJQKVva3.exe (PID: 2728)
- Q0vtvWBVLc.exe (PID: 7044)
- extrac32.exe (PID: 5988)
- Market.com (PID: 2708)
Create files in a temporary directory
- 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe (PID: 6656)
- extrac32.exe (PID: 5724)
- 6BLxsOUpv6L.exe (PID: 2388)
- shPLP1rDI.exe (PID: 7056)
- extrac32.exe (PID: 6764)
- ERRSPzEwUVO1.exe (PID: 6812)
- extrac32.exe (PID: 4400)
- ExJQKVva3.exe (PID: 2728)
- extrac32.exe (PID: 5988)
- svchost015.exe (PID: 6492)
Reads the computer name
- svchost015.exe (PID: 6492)
- kLPjwNpfzy.exe (PID: 5188)
- extrac32.exe (PID: 5724)
- Market.com (PID: 1468)
- ARLPL5txvrsO.exe (PID: 1128)
- extrac32.exe (PID: 6764)
- Market.com (PID: 6472)
- tviwTDgLQOO.exe (PID: 2296)
- extrac32.exe (PID: 4400)
- Market.com (PID: 4544)
- MUSWsS12rwt.exe (PID: 6368)
- extrac32.exe (PID: 5988)
- Market.com (PID: 2708)
Checks proxy server information
- svchost015.exe (PID: 6492)
- slui.exe (PID: 4172)
Reads the machine GUID from the registry
- svchost015.exe (PID: 6492)
- kLPjwNpfzy.exe (PID: 5188)
- ARLPL5txvrsO.exe (PID: 1128)
- Market.com (PID: 1468)
- Market.com (PID: 6472)
- tviwTDgLQOO.exe (PID: 2296)
- Market.com (PID: 4544)
- MUSWsS12rwt.exe (PID: 6368)
- Market.com (PID: 2708)
Reads the software policy settings
- svchost015.exe (PID: 6492)
- kLPjwNpfzy.exe (PID: 5188)
- ARLPL5txvrsO.exe (PID: 1128)
- Market.com (PID: 1468)
- tviwTDgLQOO.exe (PID: 2296)
- Market.com (PID: 6472)
- Market.com (PID: 4544)
- MUSWsS12rwt.exe (PID: 6368)
- slui.exe (PID: 4172)
- Market.com (PID: 2708)
Creates files or folders in the user directory
- svchost015.exe (PID: 6492)
Reads mouse settings
- Market.com (PID: 1468)
- Market.com (PID: 6472)
- Market.com (PID: 4544)
- Market.com (PID: 2708)
Process checks computer location settings
- svchost015.exe (PID: 6492)
Application launched itself
- chrome.exe (PID: 2348)
- chrome.exe (PID: 5352)
- chrome.exe (PID: 3620)
- chrome.exe (PID: 7032)
- msedge.exe (PID: 2040)
- msedge.exe (PID: 3740)
- msedge.exe (PID: 5528)
- msedge.exe (PID: 4216)
- msedge.exe (PID: 5080)
- chrome.exe (PID: 1232)
- chrome.exe (PID: 3100)
- chrome.exe (PID: 4916)
- msedge.exe (PID: 7104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 376832 |
| InitializedDataSize: | 2981376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5cee0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
284
Monitored processes
148
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2044,i,10185319715461863332,15031215815062211617,262144 --variations-seed-version --mojo-platform-channel-handle=2040 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4928,i,10185319715461863332,15031215815062211617,262144 --variations-seed-version --mojo-platform-channel-handle=4936 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 472 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | ping localhost -n 5 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x220,0x224,0x228,0x1fc,0x22c,0x7ffc4531fff8,0x7ffc45320004,0x7ffc45320010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5196,i,12628232165323429787,3831760266667909592,262144 --variations-seed-version --mojo-platform-channel-handle=5212 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3016,i,16417957255298412154,15196800234162956191,262144 --variations-seed-version --mojo-platform-channel-handle=2884 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3720,i,885389866950982003,16130765049755559226,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3888 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
62 210
Read events
62 143
Write events
67
Delete events
0
Modification events
| (PID) Process: | (6492) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6492) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6492) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2348) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2348) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2348) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2348) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2348) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5352) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5352) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
25
Suspicious files
129
Text files
252
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6492 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\success[1].htm | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 6492 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\info[1].htm | text | |
MD5:FE9B08252F126DDFCB87FB82F9CC7677 | SHA256:E63E7EBE4C2DB7E61FFC71AF0675E870BCDE0A9D8916E5B3BE0CB252478030BF | |||
| 6492 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\text[1] | text | |
MD5:BAA7F7522A9F7B5ABD72F16BAF6CED5D | SHA256:F6616341C37EBD423B881D7C43D0726E809476AA928DEF87AE3A3424E0213ADC | |||
| 6656 | 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe | C:\Users\admin\AppData\Local\Temp\svcEDC6.tmp | executable | |
MD5:AD387E34F627CBF0E4920439D0ED80A5 | SHA256:410070FEE996ADD03214A3A4AEA30F343A6F8BAED1A7385295F28432760340D1 | |||
| 6656 | 46e562e1967e51d3baac23012260c37f4999937fc319ec3868fb832ef0a7e374.bin.exe | C:\Users\admin\AppData\Local\Temp\svchost015.exe | executable | |
MD5:CEEAE1523C3864B719E820B75BF728AA | SHA256:4E04E2FB20A9C6846B5D693EA67098214F77737F4F1F3DF5F0C78594650E7F71 | |||
| 6492 | svchost015.exe | C:\Users\admin\AppData\Roaming\60p38h\6BLxsOUpv6L.exe | executable | |
MD5:E1C980E16F677AAF740440ADC882639F | SHA256:4F74C9436D6E306FEE66BC786F8A4C373A7D268A60E14C51FAD83B0C17E9FAAA | |||
| 2388 | 6BLxsOUpv6L.exe | C:\Users\admin\AppData\Local\Temp\Manchester.adts | binary | |
MD5:BE2850535A13D17D5BDF66A2353C2ECB | SHA256:F9F238F5282D9AC1843DC034EF5BEA5DD4BCC9A151E5DD74382C16C81F8D2546 | |||
| 2388 | 6BLxsOUpv6L.exe | C:\Users\admin\AppData\Local\Temp\Merchandise.adts | binary | |
MD5:4590282C5C07D9485E60FD06606A0A0F | SHA256:A6967878E90F686A86CDCEB3C81A1223BCC57950E136580880096D99D7720EDE | |||
| 2388 | 6BLxsOUpv6L.exe | C:\Users\admin\AppData\Local\Temp\Revised.adts | binary | |
MD5:93E0009AB418B5AE8583D447B8B7F32E | SHA256:22EED5EB198FCE477C65B6A92441917134A20B3FF71A24B9D199C96C53DCA4FC | |||
| 6492 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\TWO[1].file | executable | |
MD5:E1C980E16F677AAF740440ADC882639F | SHA256:4F74C9436D6E306FEE66BC786F8A4C373A7D268A60E14C51FAD83B0C17E9FAAA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
327
TCP/UDP connections
339
DNS requests
212
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 400 | 20.190.159.129:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.0:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.71:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.1:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 142.250.186.65:443 | https://drive.usercontent.google.com/download?id=1YBVIDkZgygNfUU2rbJXXCYdrzay5rMdY&export=download&authuser=0&confirm=t | unknown | text | 13 b | whitelisted |
— | — | POST | 400 | 40.126.31.3:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1944 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1944 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
yikpspbi.my |
| malicious |
mastwin.in |
| malicious |