| File name: | OSE.EXE |
| Full analysis: | https://app.any.run/tasks/0cf71eee-4c80-440b-8832-d61b8ad86e51 |
| Verdict: | Malicious activity |
| Threats: | Raspberry Robin is a trojan that primarily spreads through infected USB drives and exploits legitimate Windows commands. This malware is known for its advanced obfuscation techniques, anti-debugging mechanisms, and ability to gain persistence on infected systems. Raspberry Robin often communicates with command-and-control servers over the TOR network and can download additional malicious payloads. |
| Analysis date: | December 08, 2024, 14:56:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 02ADE94C4B5BD3295D775A6D48A968C2 |
| SHA1: | 4848ED0A67705E086035FADA76F70C8F220DCD65 |
| SHA256: | 46D89DAE47B8F048E11DC2D4EF6B0C74A6175C948B5407589F4CB97A06E92B0D |
| SSDEEP: | 3072:9kd8W2W7OEBGG6sJcNXN098OMAFD62dalDqHVjt88o4SIh+HGnYW+v/1pegCATvf:9z5uc0cNXK8OMAFvdH88o41hcfPBrBs |
MALICIOUS
Deletes shadow copies
- jxQjSb4C:bin (PID: 6972)
RASPBERRYROBIN has been detected (YARA)
- elevation_service.exe (PID: 448)
SUSPICIOUS
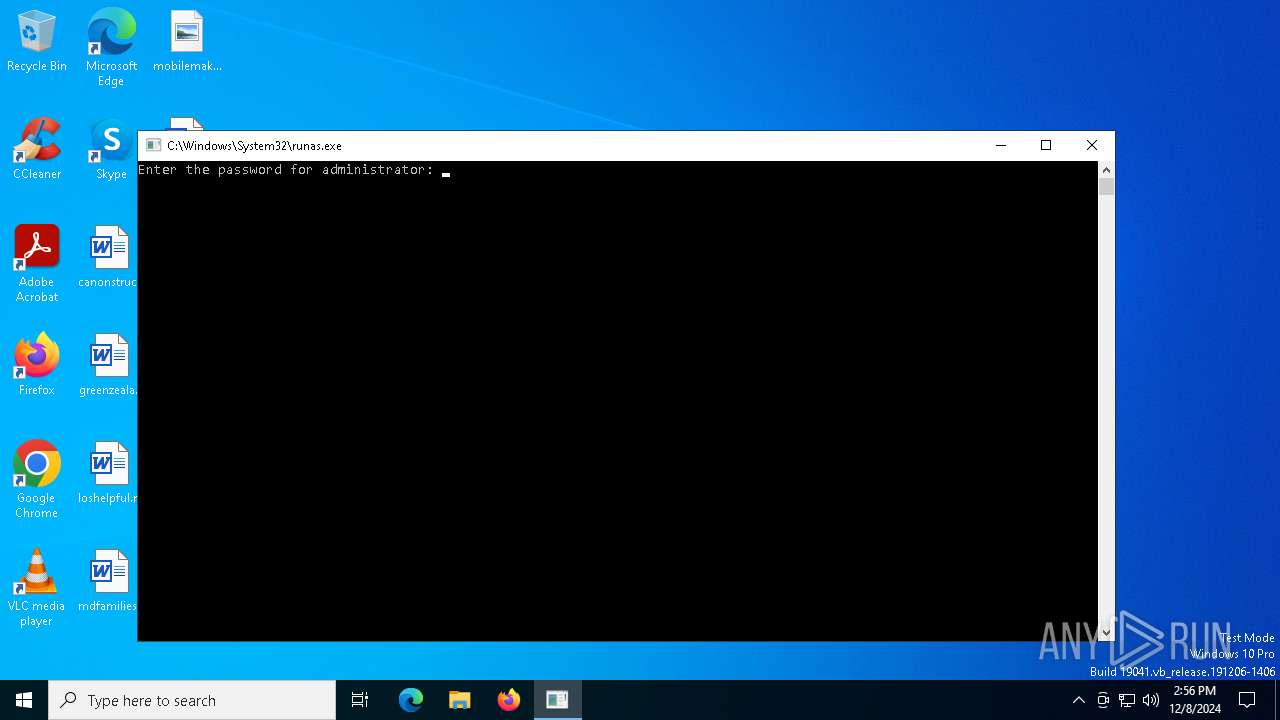
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 4052)
Executable content was dropped or overwritten
- OSE.EXE.exe (PID: 6932)
- jxQjSb4C:bin (PID: 6972)
Detected use of alternative data streams (AltDS)
- OSE.EXE.exe (PID: 6932)
- jxQjSb4C:bin (PID: 6972)
- elevation_service.exe (PID: 448)
- LL6ZL8~1:bin (PID: 2612)
Starts itself from another location
- OSE.EXE.exe (PID: 6932)
- elevation_service.exe (PID: 448)
Starts application with an unusual extension
- OSE.EXE.exe (PID: 6932)
- elevation_service.exe (PID: 448)
Executes as Windows Service
- VSSVC.exe (PID: 7060)
- wbengine.exe (PID: 2828)
Takes ownership (TAKEOWN.EXE)
- jxQjSb4C:bin (PID: 6972)
Uses ICACLS.EXE to modify access control lists
- jxQjSb4C:bin (PID: 6972)
Creates or modifies Windows services
- jxQjSb4C:bin (PID: 6972)
Process drops legitimate windows executable
- jxQjSb4C:bin (PID: 6972)
- elevation_service.exe (PID: 448)
Executes application which crashes
- wbengine.exe (PID: 2828)
Creates file in the systems drive root
- elevation_service.exe (PID: 448)
Uses pipe srvsvc via SMB (transferring data)
- net.exe (PID: 7124)
- net.exe (PID: 3816)
The process drops C-runtime libraries
- elevation_service.exe (PID: 448)
Process uses ARP to discover network configuration
- LL6ZL8~1:bin (PID: 2612)
Uses NSLOOKUP.EXE to check DNS info
- LL6ZL8~1:bin (PID: 2612)
Starts NET.EXE for network exploration
- LL6ZL8~1:bin (PID: 2612)
INFO
Reads the machine GUID from the registry
- OSE.EXE.exe (PID: 6932)
- jxQjSb4C:bin (PID: 6972)
- LL6ZL8~1:bin (PID: 2612)
Checks supported languages
- OSE.EXE.exe (PID: 6932)
- jxQjSb4C:bin (PID: 6972)
- wbengine.exe (PID: 2828)
- elevation_service.exe (PID: 448)
- LL6ZL8~1:bin (PID: 2612)
Process checks whether UAC notifications are on
- OSE.EXE.exe (PID: 6932)
- jxQjSb4C:bin (PID: 6972)
- elevation_service.exe (PID: 448)
- LL6ZL8~1:bin (PID: 2612)
Reads the computer name
- OSE.EXE.exe (PID: 6932)
- jxQjSb4C:bin (PID: 6972)
- elevation_service.exe (PID: 448)
- LL6ZL8~1:bin (PID: 2612)
Creates files in the program directory
- jxQjSb4C:bin (PID: 6972)
Executes as Windows Service
- elevation_service.exe (PID: 448)
Creates files or folders in the user directory
- elevation_service.exe (PID: 448)
Manual execution by a user
- WINWORD.EXE (PID: 1140)
Drops encrypted VBS script (Microsoft Script Encoder)
- WINWORD.EXE (PID: 1140)
The process uses the downloaded file
- WINWORD.EXE (PID: 1140)
Sends debugging messages
- WINWORD.EXE (PID: 1140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2004:07:24 01:47:17+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 77824 |
| InitializedDataSize: | - |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2d92 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.19 |
| ProductVersionNumber: | 2.1.0.19 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Unknown (1C09) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Microgaming |
| FileDescription: | IGFX Encryption Handler |
| FileVersion: | 2, 1, 0, 19 |
| InternalName: | IEncrypt |
| LegalCopyright: | Copyright © Microgaming 2002 |
| LegalTrademarks: | - |
| OriginalFileName: | IEncrypt.dll |
| PrivateBuild: | - |
| ProductName: | Microgaming Encryption Handler |
| ProductVersion: | 2, 1, 0, 19 |
| SpecialBuild: | - |
Total processes
171
Monitored processes
37
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\elevation_service.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\elevation_service.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microgaming Integrity Level: SYSTEM Description: IGFX Encryption Handler Version: 2, 1, 0, 19 Modules
| |||||||||||||||
| 1140 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\photostructure.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "18A07214-00DA-4DE5-B528-26CAEA89CE26" "093018BC-857A-4B5A-8E1E-ECC9A126B2EA" "1140" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 1704 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | C:\Users\admin\AppData\Roaming\\LL6ZL8~1:bin | C:\Users\admin\AppData\Roaming\LL6ZL8~1:bin | — | elevation_service.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2828 | C:\WINDOWS\system32\wbengine.exe | C:\Windows\System32\wbengine.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microgaming Integrity Level: SYSTEM Description: IGFX Encryption Handler Exit code: 255 Version: 2, 1, 0, 19 Modules
| |||||||||||||||
| 3140 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2828 -s 320 | C:\Windows\SysWOW64\WerFault.exe | wbengine.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3816 | C:\WINDOWS\system32\net.exe view mdns.mcast.net | C:\Windows\System32\net.exe | — | LL6ZL8~1:bin | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\OSE.EXE.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
75 232
Read events
74 933
Write events
274
Delete events
25
Modification events
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | RequiredPrivileges |
Value: SeTcbPrivilege | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | RequiredPrivileges |
Value: SeImpersonatePrivilege | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | ObjectName |
Value: LocalSystem | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | ObjectName |
Value: localSystem | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | DependOnService |
Value: rpcss | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | DependOnService |
Value: | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | ImagePath |
Value: "C:\WINDOWS\system32\wbengine.exe" | |||
| (PID) Process: | (6972) jxQjSb4C:bin | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | ImagePath |
Value: C:\WINDOWS\system32\wbengine.exe | |||
| (PID) Process: | (3140) WerFault.exe | Key: | \REGISTRY\A\{1050d1cf-2bf3-1f94-66d2-b616305f1e21}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (3140) WerFault.exe | Key: | \REGISTRY\A\{1050d1cf-2bf3-1f94-66d2-b616305f1e21}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
82
Suspicious files
473
Text files
4 090
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6932 | OSE.EXE.exe | C:\jxQjSb4C | — | |
MD5:— | SHA256:— | |||
| 3140 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_wbengine.exe_c640629829cc7fc6214f7fad154253b5a16e52_ce08e760_c24f52bd-e56e-4fd3-b769-fb7c592948e6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 448 | elevation_service.exe | C:\Users\admin\AppData\Roaming\LL6ZL8~1 | — | |
MD5:— | SHA256:— | |||
| 3140 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | hiv | |
MD5:1C473574F6FB80D57B2120D3DFD94C11 | SHA256:533C48AAA24B91C3D1416724E59C4C6C0601ED97A9453E13CC39A82404E07F6C | |||
| 3140 | WerFault.exe | C:\Windows\SysWOW64\config\systemprofile\AppData\Local\CrashDumps\wbengine.exe.2828.dmp | binary | |
MD5:348E67A6ED4E1211365FA8DBD6933FE9 | SHA256:1A2E1A34C787D060062656A24F9FDA1C7D46B1F1ABA48E91EAC8DDA2186A78D0 | |||
| 6972 | jxQjSb4C:bin | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\elevation_service.exe | executable | |
MD5:02ADE94C4B5BD3295D775A6D48A968C2 | SHA256:46D89DAE47B8F048E11DC2D4EF6B0C74A6175C948B5407589F4CB97A06E92B0D | |||
| 6972 | jxQjSb4C:bin | C:\Windows\System32\wbengine.exe | executable | |
MD5:02ADE94C4B5BD3295D775A6D48A968C2 | SHA256:46D89DAE47B8F048E11DC2D4EF6B0C74A6175C948B5407589F4CB97A06E92B0D | |||
| 6932 | OSE.EXE.exe | C:\jxQjSb4C:bin | executable | |
MD5:02ADE94C4B5BD3295D775A6D48A968C2 | SHA256:46D89DAE47B8F048E11DC2D4EF6B0C74A6175C948B5407589F4CB97A06E92B0D | |||
| 3140 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER7C76.tmp.dmp | binary | |
MD5:AFA3F3CC08E925F643CD2159EB26C736 | SHA256:8592000F6D8A7C75EA2BB29875AA4A0254F083CD7EF48237FA171BD7B857E2B8 | |||
| 6972 | jxQjSb4C:bin | C:\Users\Administrator\AppData\Local\Temp\srr78EC.tmp | text | |
MD5:E028C8417DD1F4A1BBEBE990687F60BE | SHA256:AD1745FB0662B3217F3D8E591FC3476278766709A185B43BDEA26C966071A6C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
43
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5340 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5340 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
748 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6548 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1140 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6548 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5340 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5340 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.40:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|