| URL: | https://click-west.acuityplatform.com/Adserver/landing?etoken=MHZGKHKMAIKQOEHgAMMDY1MDQ3NDE5MDg2Bw49-KU0Dih0IgIOMM8GAw4-13R4Djvt0wEOPfikCg49-KBZDj34pg0AJDA2NjdCMkY5Mjg3Ny1BMDdCLUFCRDQtMkQzNy02MzA2NzVBNgkOPfiIBAAAAAA3G8_KBQAAAAAofqIVRAABMAwABjkwMDY1MQsAAAAANin9cAgAJUIyNDI5NUY5Qzc0M0ItQzgzQS0wRjE0LTYxMTAtQTBFQzFDMTN7AAJuZRwACDE5ZjFiYmI2GwALNTRiNzBmYjJjODEaDj34pkMOPfinTwADQVNVUAACTElRAAdPR0FDSUhDUwAFOTI2MDZSAAAAADYq_oArAAEwLAAAJw49-KEoDj34pCkOPfimSQAMNjgyMjYzMzU2ODU4Kg49-KYtDj34pi4OPfimPQAlQjI0Mjk1RjlDNzQzQi1DODNBLTBGMTQtNjExMC1BMEVDMUMxM2QOPfijZQ49-KdiDj34pmMOPeNMPwABMDcAADgAADUACzU0YjcwZmIyYzgxDw49-KYVVrhPIhbWMDofGA49-KYZDj34phIOPfinEwABMBAOPfinTAAKOTIwLXJkYi1hbE0AJjI4OTYxMzkyNjEwNzFfMjk2OTIyNDQ1MTA3MV85MjAtcmRiLWFsVA4-13RLAAoxMDAtZGliLWFsWw49-KJVDj34p10OPdSYXg49zXhfDj1xiGAOP5XIYQ48mDR5DjyJ6X8OPfikZgAXOTAwNjUxOmVjYTJmNjgxYjMwNDI2ZDVqAAY5MjU3OTFnAAAAADYqrfpoAAAAADYq_ulpAAAAADYq_ulsCyNf2N8uXul6K2xiqWsAAAAAG0KrLXUAAAGMGnSmrG4ACzUxLDIxLDYyLDMycQ49-KVyAAAAADYq_ul3AA==&jk=&landingUrl=https://jaherkhabar.com?2Fus/?&utm_source=acuityads&utm_medium=display&utm_campaign=23&utm_term=NOOFR&dclid=%edclid |
| Full analysis: | https://app.any.run/tasks/a4f3cb17-b329-45dc-9c2f-80e8b804acf1 |
| Verdict: | Malicious activity |
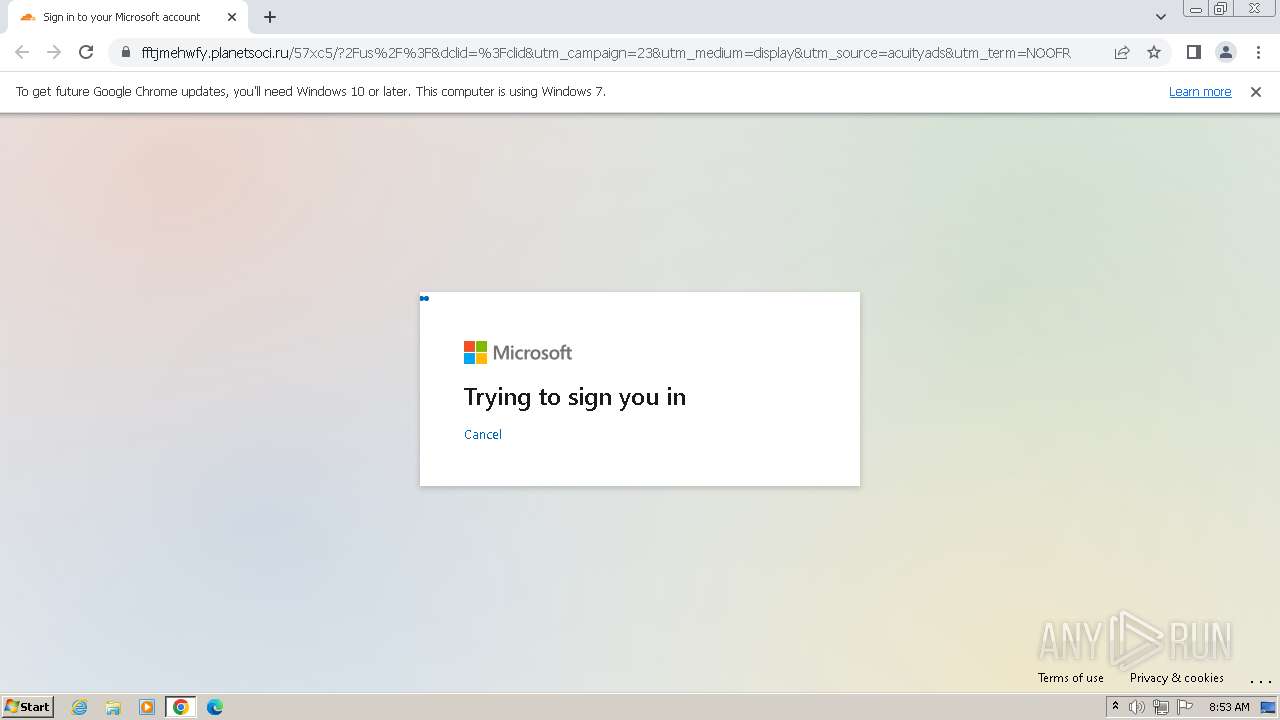
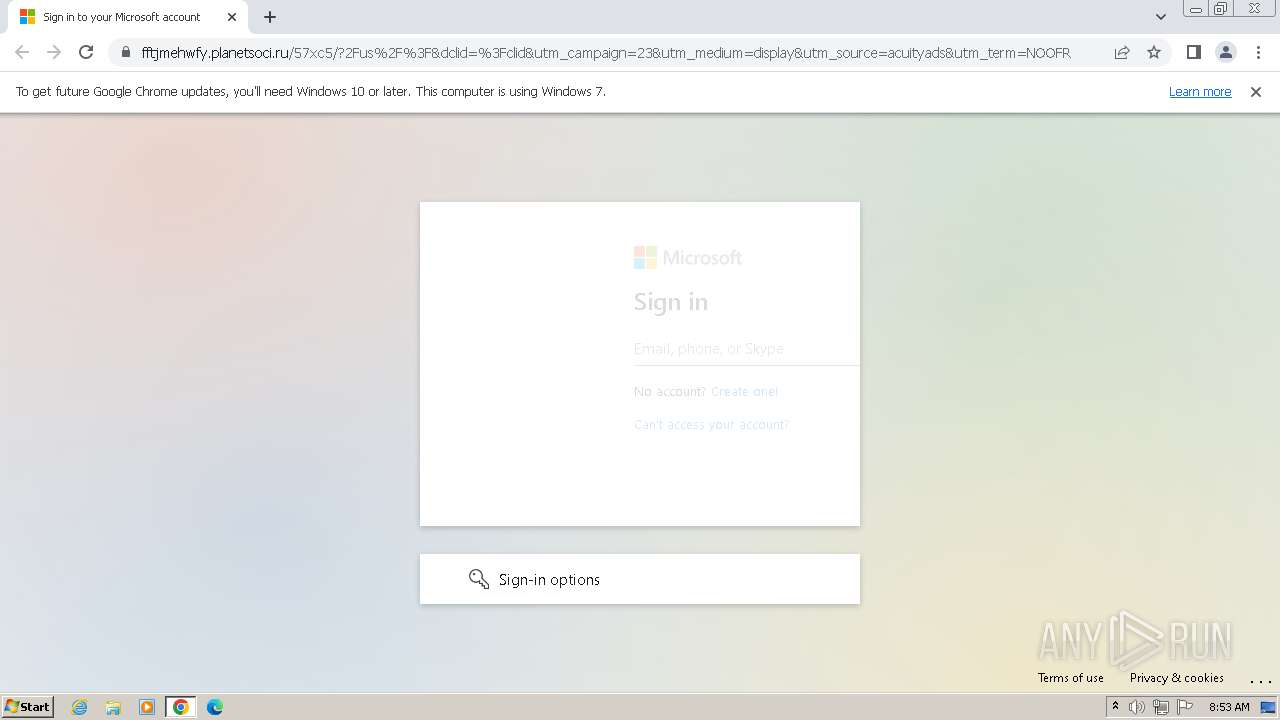
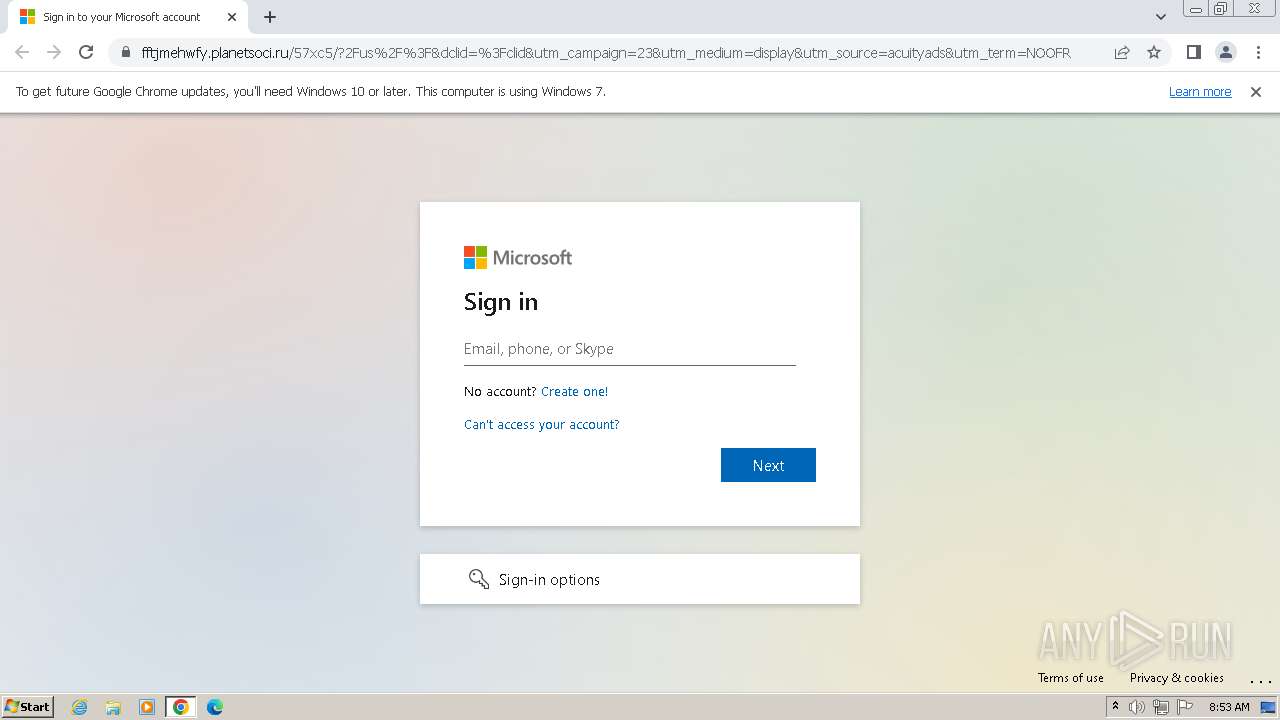
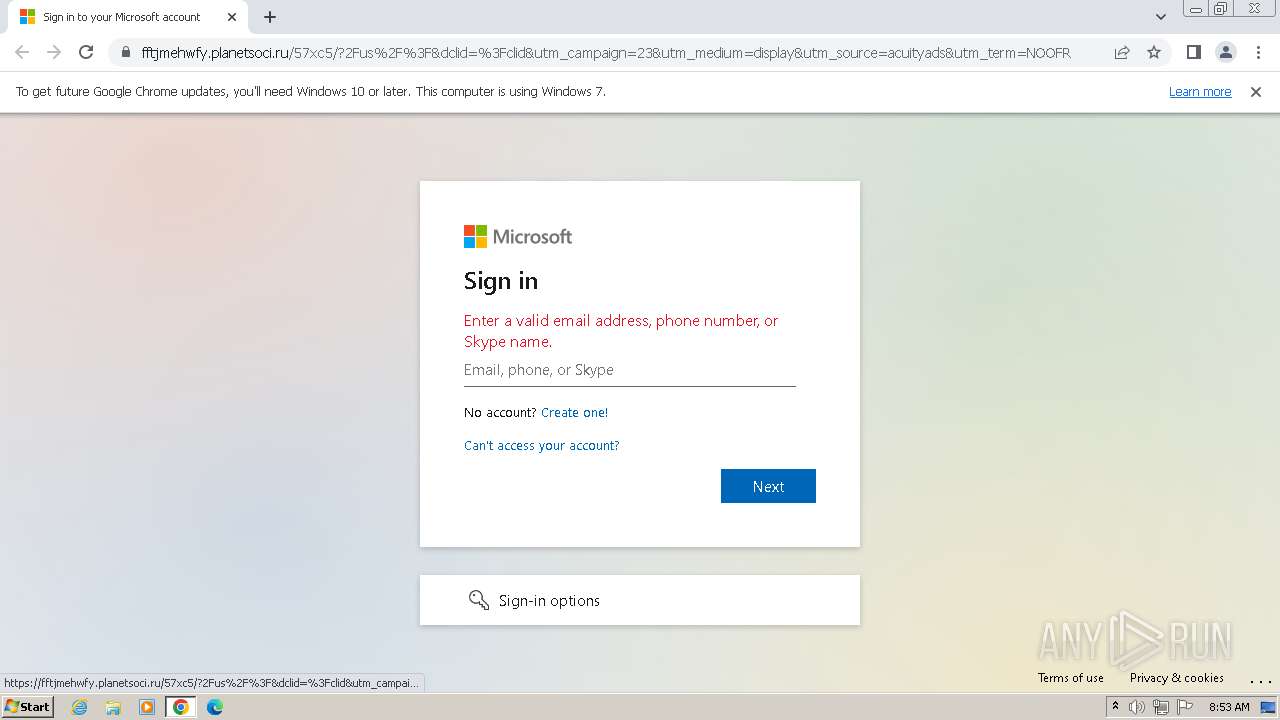
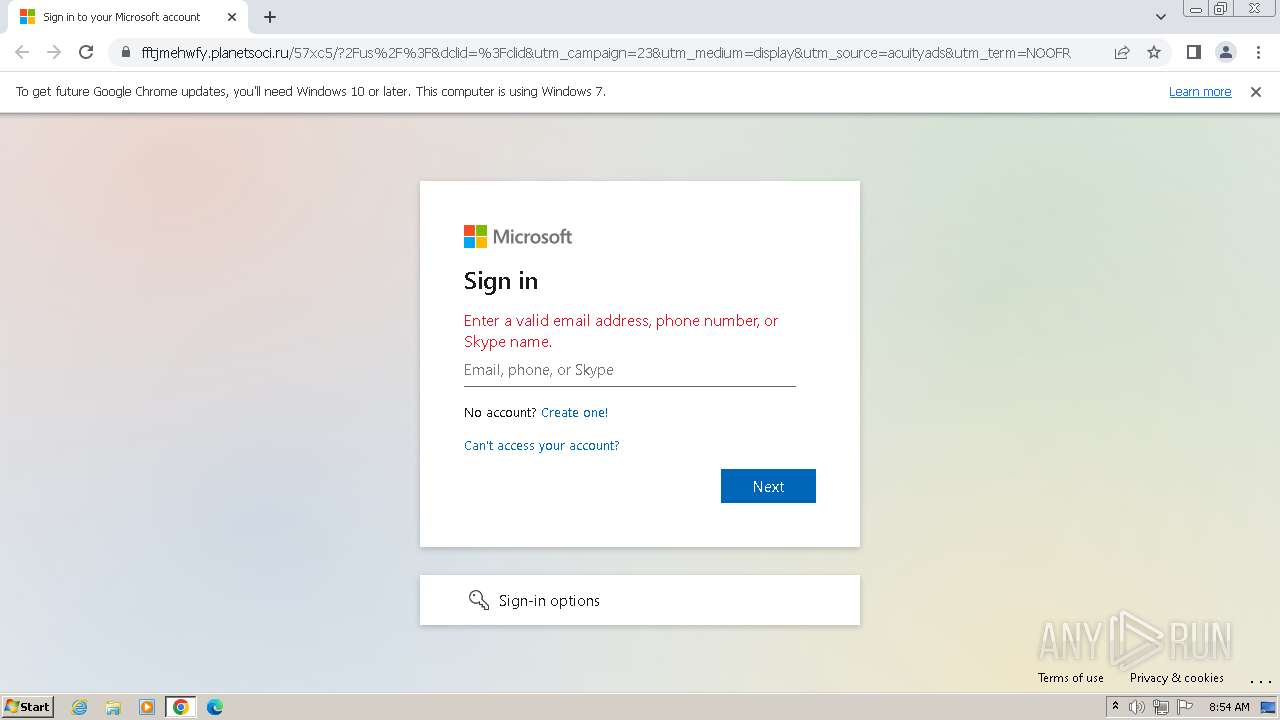
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | December 05, 2023, 08:53:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0D9E94A07C751A2AA32BA06808C1A6D6 |
| SHA1: | 22B193CB02D5949D4776B6B53B7286E192946C3A |
| SHA256: | 46AD8611557F72CDE19E8FE6FB86529C9912CA29B3F8FC4A6D2A53146FFF2F24 |
| SSDEEP: | 24:2UzQb2mI9A++0vR4eytiQ+9kcv0fZ/hBOuFT788rx:XUTI9A+Rp4BtovMfNhBFTwc |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 2544)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 3264)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3588)
- wmpnscfg.exe (PID: 2500)
Reads the computer name
- wmpnscfg.exe (PID: 3588)
- wmpnscfg.exe (PID: 2500)
Manual execution by a user
- wmpnscfg.exe (PID: 3588)
- wmpnscfg.exe (PID: 2500)
The process uses the downloaded file
- chrome.exe (PID: 120)
- chrome.exe (PID: 2128)
- chrome.exe (PID: 2092)
Drops the executable file immediately after the start
- chrome.exe (PID: 3264)
Application launched itself
- chrome.exe (PID: 3264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
59
Monitored processes
23
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2216 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2868 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3816 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1108 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3188 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6a7a8b38,0x6a7a8b48,0x6a7a8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2020 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3732 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2532 --field-trial-handle=1072,i,16256236338557957976,17839864497561954147,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2500 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 849
Read events
3 763
Write events
86
Delete events
0
Modification events
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (3264) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
1
Suspicious files
57
Text files
22
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF21004d.TMP | — | |
MD5:— | SHA256:— | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF21005d.TMP | text | |
MD5:513218482935B0D388C0A990D868387A | SHA256:8E39CBAAF4AACC3A01AFA74EA8C30FB24FE69A22B8B30728AFB1614FD68809D9 | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8175FB7046E977DAAD01289080C116EF | SHA256:19E403B4BEF7D83DD425AB6A54DE943D244A16E5EA121DEC91C417608AEAACB7 | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF210ffd.TMP | — | |
MD5:— | SHA256:— | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\73e89252-4086-4c2c-948d-dc39a5695ed7.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3264 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\optimization_guide_hint_cache_store\LOG.old~RF211d2c.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
30
DNS requests
34
Threats
6
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2544 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3264 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2544 | chrome.exe | 69.90.133.56:443 | click-west.acuityplatform.com | COGECO-PEER1 | US | unknown |
2544 | chrome.exe | 77.91.124.250:443 | jaherkhabar.com | Foton Telecom CJSC | RU | unknown |
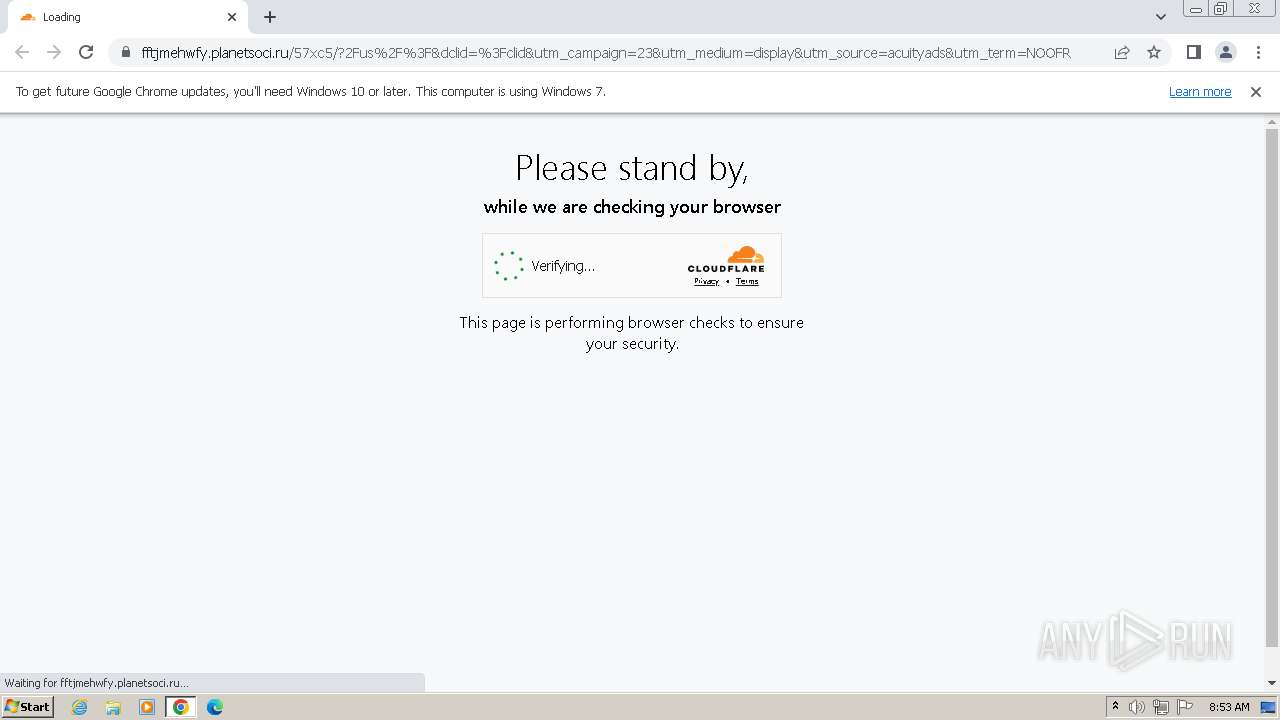
2544 | chrome.exe | 172.67.217.173:443 | fftjmehwfy.planetsoci.ru | CLOUDFLARENET | US | unknown |
2544 | chrome.exe | 151.101.130.137:443 | code.jquery.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
click-west.acuityplatform.com |
| unknown |
jaherkhabar.com |
| unknown |
fftjmehwfy.planetsoci.ru |
| unknown |
code.jquery.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
www.google.com |
| whitelisted |
cdn.socket.io |
| shared |
optimizationguide-pa.googleapis.com |
| whitelisted |
aadcdn.msftauth.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2544 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
2544 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2544 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain chain detected (Tycoon 2FA) |
2544 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Client-Server Socket.IO CDN communication (cdn.socket .io) |
2544 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2544 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |