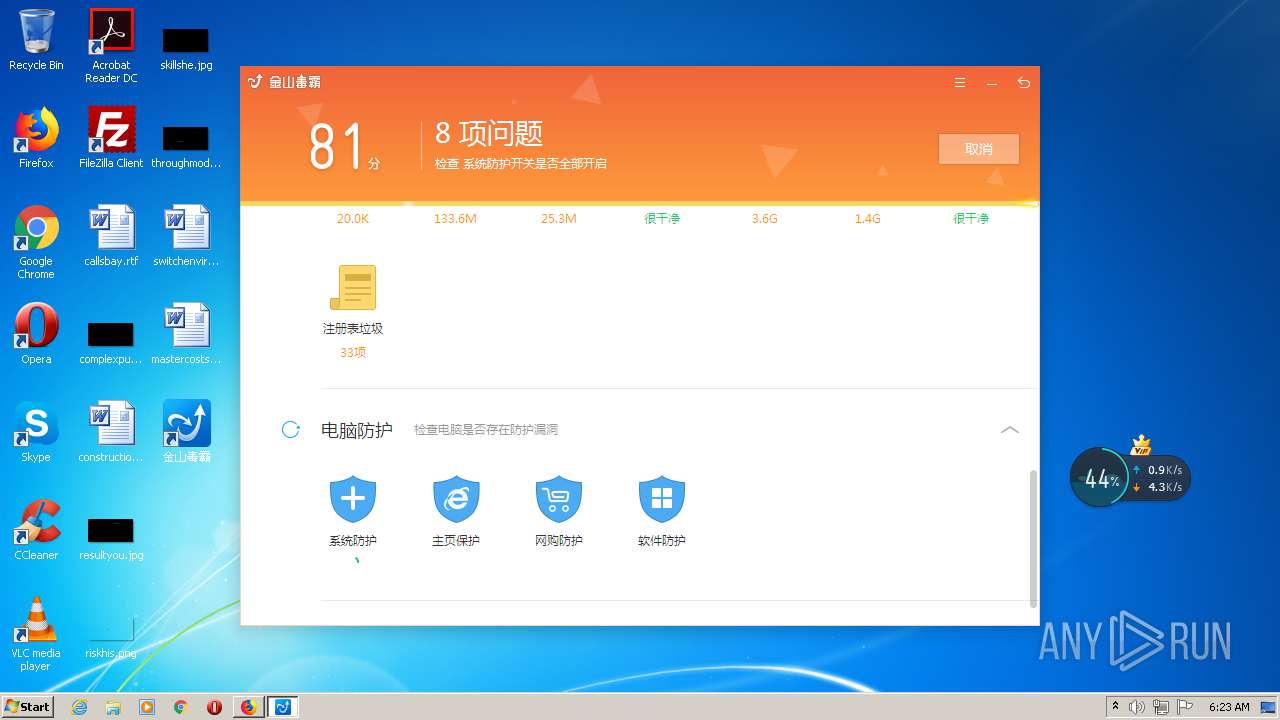
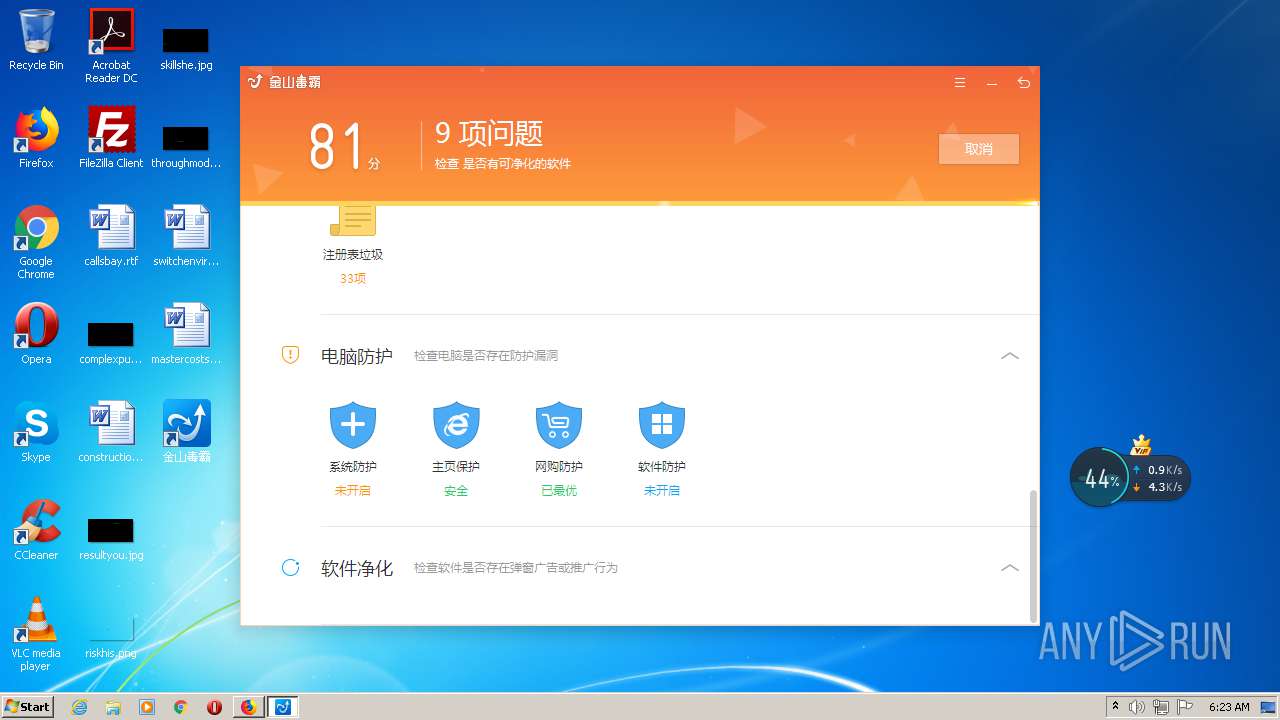
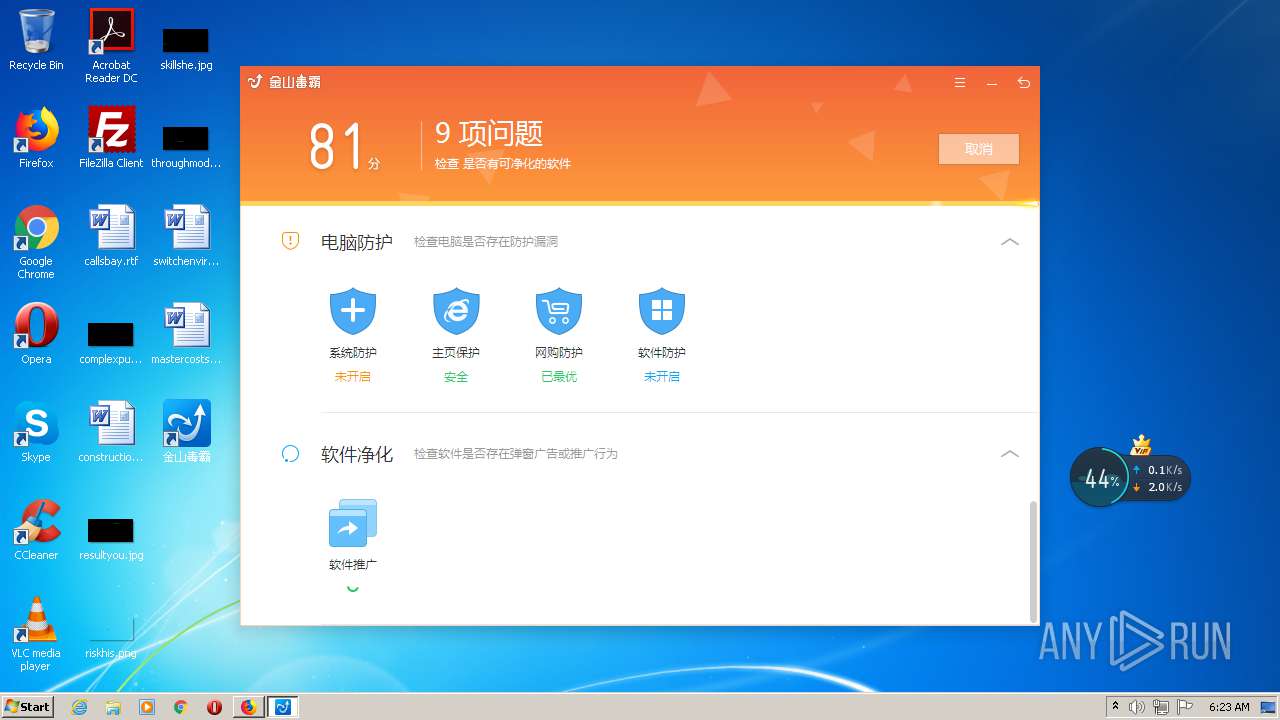
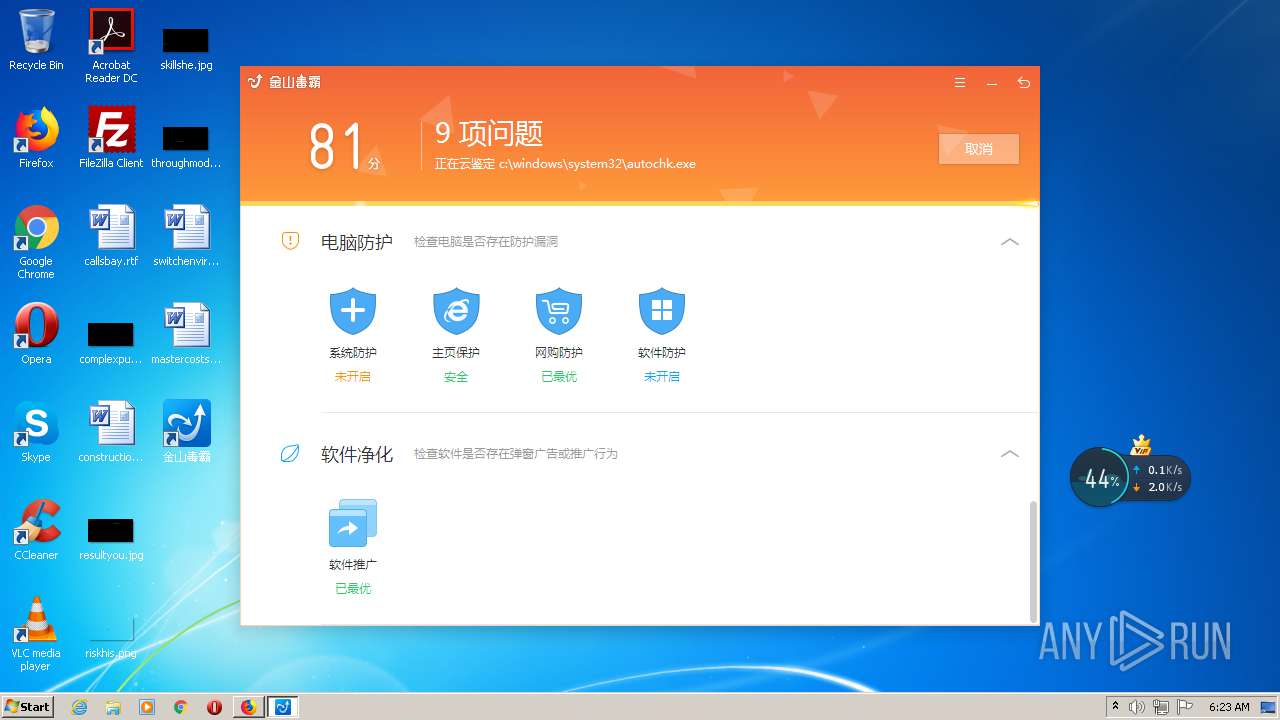
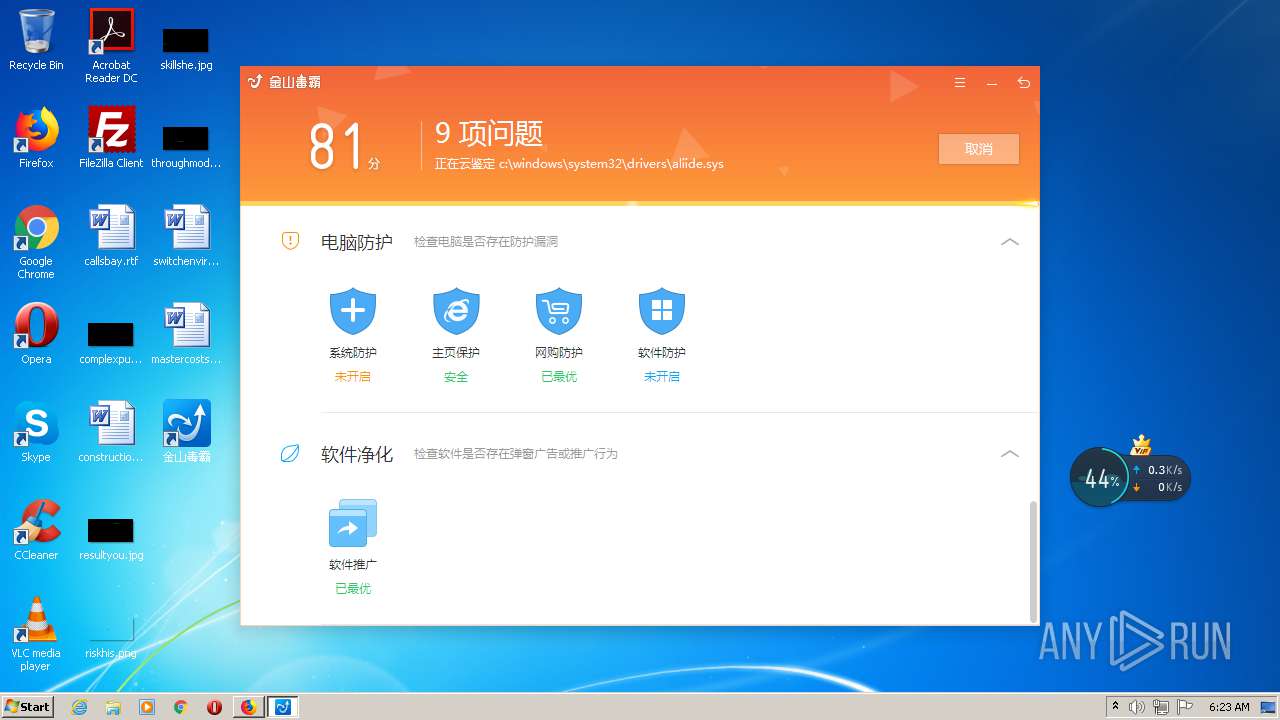
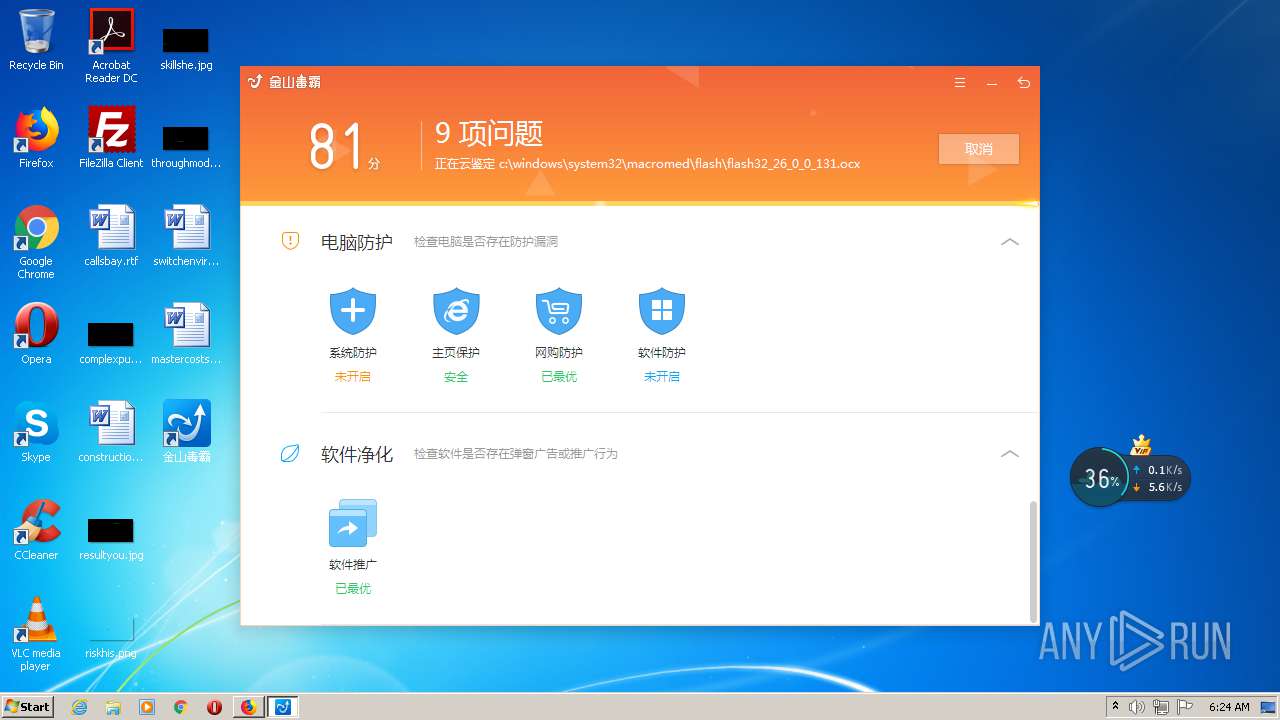
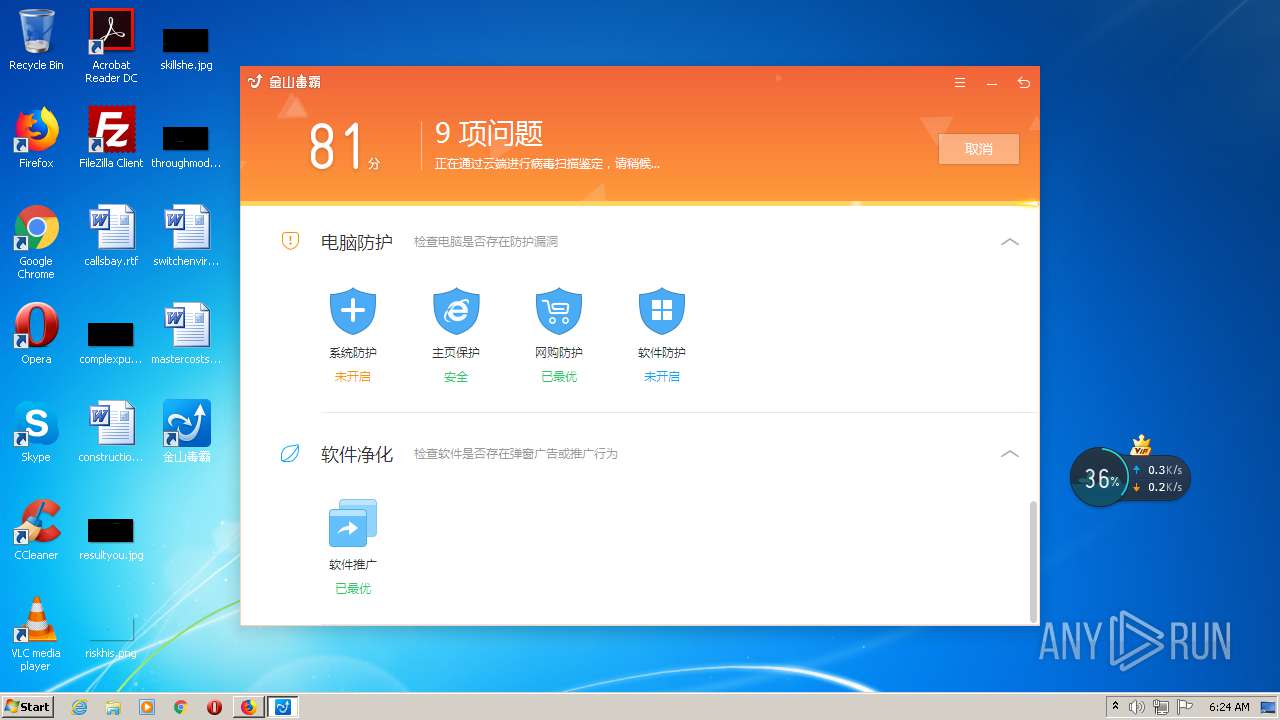
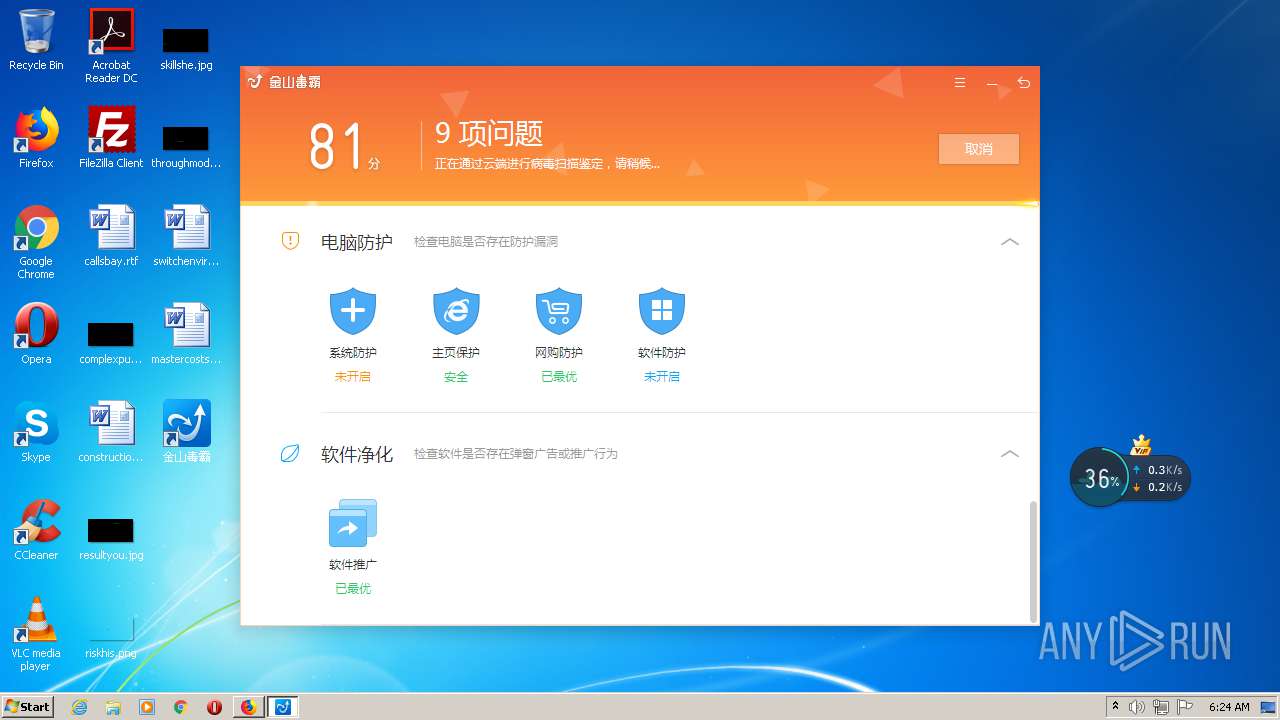
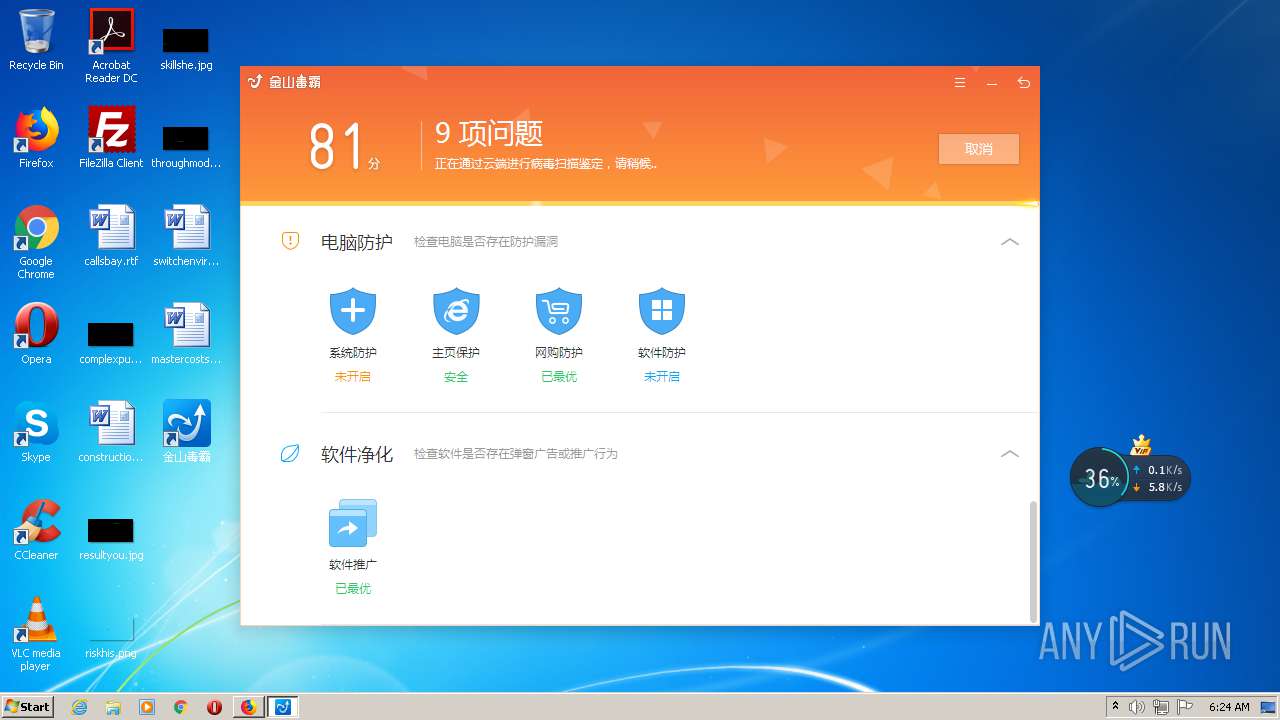
| URL: | http://www.duba.net/ |
| Full analysis: | https://app.any.run/tasks/4a7a9700-aa99-4437-8135-bbf70529b835 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | June 20, 2020, 05:20:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D74F162F0842875E6E714ED82833589E |
| SHA1: | D3FA23A1906C58391233071FE447DD7585591D4B |
| SHA256: | 4664DFD5F2D2A1044FC5072808856DF6D5769D95B71CFBFC12C3134DEC798271 |
| SSDEEP: | 3:N1KJS4xIs:Cc4+s |
MALICIOUS
Application was dropped or rewritten from another process
- dubaperf_2020051901.exe (PID: 2076)
- dubaperf_2020051901.exe (PID: 2988)
- kxetray.exe (PID: 3416)
- kxescore.exe (PID: 3768)
- kxescore.exe (PID: 2696)
- kxecenter.exe (PID: 3376)
- kavlog2.exe (PID: 1688)
- kxecenter.exe (PID: 2372)
- ksoftmgr.exe (PID: 2732)
- kxemain.exe (PID: 4084)
- kscan.exe (PID: 5296)
- kxetray.exe (PID: 4992)
- kslaunch.exe (PID: 6068)
- kfloatmain.exe (PID: 4600)
Connects to CnC server
- dubaperf_2020051901.exe (PID: 2988)
Downloads executable files from the Internet
- firefox.exe (PID: 3892)
Changes the autorun value in the registry
- dubaperf_2020051901.exe (PID: 2988)
Loads dropped or rewritten executable
- kxescore.exe (PID: 3768)
- kxetray.exe (PID: 3416)
- kavlog2.exe (PID: 1688)
- ksoftmgr.exe (PID: 2732)
- dubaperf_2020051901.exe (PID: 2988)
- kxecenter.exe (PID: 2372)
- kxecenter.exe (PID: 3376)
- kxemain.exe (PID: 4084)
- kxescore.exe (PID: 2696)
- kscan.exe (PID: 5296)
- kxetray.exe (PID: 4992)
- explorer.exe (PID: 468)
- kfloatmain.exe (PID: 4600)
Actions looks like stealing of personal data
- explorer.exe (PID: 468)
- kxetray.exe (PID: 3416)
- kxescore.exe (PID: 2696)
- kxemain.exe (PID: 4084)
- kscan.exe (PID: 5296)
Changes settings of System certificates
- kxemain.exe (PID: 4084)
- kxetray.exe (PID: 3416)
- kxescore.exe (PID: 2696)
Loads the Task Scheduler DLL interface
- kxemain.exe (PID: 4084)
Loads the Task Scheduler COM API
- kxescore.exe (PID: 2696)
- kscan.exe (PID: 5296)
- kxemain.exe (PID: 4084)
SUSPICIOUS
Creates a software uninstall entry
- dubaperf_2020051901.exe (PID: 2988)
- kxetray.exe (PID: 3416)
Creates files in the driver directory
- dubaperf_2020051901.exe (PID: 2988)
- kxescore.exe (PID: 2696)
- kscan.exe (PID: 5296)
Creates files in the Windows directory
- dubaperf_2020051901.exe (PID: 2988)
- kavlog2.exe (PID: 1688)
- kxescore.exe (PID: 2696)
- kscan.exe (PID: 5296)
Removes files from Windows directory
- dubaperf_2020051901.exe (PID: 2988)
- kxescore.exe (PID: 2696)
- kscan.exe (PID: 5296)
- kxemain.exe (PID: 4084)
Creates files in the program directory
- firefox.exe (PID: 3892)
- kxescore.exe (PID: 3768)
- dubaperf_2020051901.exe (PID: 2988)
- kxecenter.exe (PID: 2372)
- kxecenter.exe (PID: 3376)
- kxetray.exe (PID: 3416)
- kxescore.exe (PID: 2696)
- kxemain.exe (PID: 4084)
- kxetray.exe (PID: 4992)
- kscan.exe (PID: 5296)
- kfloatmain.exe (PID: 4600)
- SearchIndexer.exe (PID: 4212)
Executable content was dropped or overwritten
- firefox.exe (PID: 3892)
- dubaperf_2020051901.exe (PID: 2988)
- kxemain.exe (PID: 4084)
- kxescore.exe (PID: 2696)
Creates COM task schedule object
- dubaperf_2020051901.exe (PID: 2988)
- kxescore.exe (PID: 2696)
Executed as Windows Service
- kxescore.exe (PID: 2696)
- SearchIndexer.exe (PID: 4212)
Writes to a desktop.ini file (may be used to cloak folders)
- dubaperf_2020051901.exe (PID: 2988)
- kxescore.exe (PID: 2696)
Reads internet explorer settings
- ksoftmgr.exe (PID: 2732)
Creates files in the user directory
- kxetray.exe (PID: 3416)
- kxemain.exe (PID: 4084)
Creates or modifies windows services
- kxemain.exe (PID: 4084)
- kxecenter.exe (PID: 3376)
- kxescore.exe (PID: 2696)
- kfloatmain.exe (PID: 4600)
Low-level read access rights to disk partition
- dubaperf_2020051901.exe (PID: 2988)
Connects to server without host name
- kxemain.exe (PID: 4084)
- kxescore.exe (PID: 2696)
- kscan.exe (PID: 5296)
- kfloatmain.exe (PID: 4600)
- kxetray.exe (PID: 3416)
Searches for installed software
- kxemain.exe (PID: 4084)
- kxetray.exe (PID: 3416)
Adds / modifies Windows certificates
- kxemain.exe (PID: 4084)
- kxetray.exe (PID: 3416)
- kxescore.exe (PID: 2696)
Reads Internet Cache Settings
- ksoftmgr.exe (PID: 2732)
Loads DLL from Mozilla Firefox
- kscan.exe (PID: 5296)
INFO
Application launched itself
- firefox.exe (PID: 2836)
- firefox.exe (PID: 3892)
Reads Internet Cache Settings
- firefox.exe (PID: 3892)
Reads CPU info
- firefox.exe (PID: 3892)
Reads settings of System Certificates
- firefox.exe (PID: 3892)
- kxescore.exe (PID: 2696)
- kxetray.exe (PID: 3416)
- kxemain.exe (PID: 4084)
- kscan.exe (PID: 5296)
Creates files in the user directory
- firefox.exe (PID: 3892)
Dropped object may contain Bitcoin addresses
- dubaperf_2020051901.exe (PID: 2988)
Reads the hosts file
- kscan.exe (PID: 5296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
64
Monitored processes
25
Malicious processes
16
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1688 | "c:\program files\kingsoft\kingsoft antivirus\kavlog2.exe" -install | c:\program files\kingsoft\kingsoft antivirus\kavlog2.exe | dubaperf_2020051901.exe | ||||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: KXEngine KeventLog3 Exit code: 0 Version: 2018,06,14,20609 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\Downloads\dubaperf_2020051901.exe" | C:\Users\admin\Downloads\dubaperf_2020051901.exe | — | firefox.exe | |||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: MEDIUM Description: Kingsoft Security - 安装程序 Exit code: 3221226540 Version: 2020,03,31,24203 Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3892.20.549686900\1195446996" -childID 3 -isForBrowser -prefsHandle 3912 -prefMapHandle 3916 -prefsLen 6785 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3892 "\\.\pipe\gecko-crash-server-pipe.3892" 3920 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3892.13.1965863260\1559940349" -childID 2 -isForBrowser -prefsHandle 2924 -prefMapHandle 2928 -prefsLen 5997 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3892 "\\.\pipe\gecko-crash-server-pipe.3892" 2932 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2372 | "c:\program files\kingsoft\kingsoft antivirus\kxecenter.exe" (null) | c:\program files\kingsoft\kingsoft antivirus\kxecenter.exe | — | kxetray.exe | |||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Security - kxecenter Exit code: 4294967295 Version: 2020,05,14,44 Modules
| |||||||||||||||
| 2696 | "c:\program files\kingsoft\kingsoft antivirus\kxescore.exe" /service kxescore | c:\program files\kingsoft\kingsoft antivirus\kxescore.exe | services.exe | ||||||||||||
User: SYSTEM Company: Kingsoft Corporation Integrity Level: SYSTEM Description: Kingsoft Security - 防御服务 Exit code: 0 Version: 2020,02,28,23821 Modules
| |||||||||||||||
| 2732 | "c:\program files\kingsoft\kingsoft antivirus\ksoftmgr.exe" -preload | c:\program files\kingsoft\kingsoft antivirus\ksoftmgr.exe | dubaperf_2020051901.exe | ||||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Security - 软件管家 Exit code: 0 Version: 2020,03,04,23930 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Mozilla Firefox\firefox.exe" "http://www.duba.net/" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2988 | "C:\Users\admin\Downloads\dubaperf_2020051901.exe" | C:\Users\admin\Downloads\dubaperf_2020051901.exe | firefox.exe | ||||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Security - 安装程序 Exit code: 1 Version: 2020,03,31,24203 Modules
| |||||||||||||||
Total events
8 413
Read events
6 068
Write events
2 230
Delete events
115
Modification events
| (PID) Process: | (2836) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: CEA00B0300000000 | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: CFA00B0300000000 | |||
| (PID) Process: | (468) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 00000000090000000E000000CC190500000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF605D425CD146D50100000000 | |||
| (PID) Process: | (468) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000004200000054000000C8ED25000B0000001A00000057BE0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000010000024E9ED017990C577B8006900000069000010000050E9ED01C4F6C4770000690000000000580269000002690064E9ED016C19C5770D00000000026900580269002CEBED0128EBED01000008009786217614E8ED0114EAED01D8E9ED0115E1C077C7670800FEFFFFFF8B8DC477108BC47701000000010000000000000004EAED01CCE9ED01E8E9ED012C8AC375010000000000000004EAED013F8AC375ED1805AB000000006CEFED0102000000FFFFFFFF0000000000000000000000000000E96FACE9ED01485F9B0050EEED01B514C5754D7B2BDFFEFFFFFF3F8AC375A36CC375A589C375651F05AB6CEFED0111000000483D3200403D32006CEFED017CEA0000C05704AB2CEAED018291D2767CEAED01EC430000FC5704AB40EAED01B69CD276F04311024C06000058EAED01603F110264EAED01789CD2763691D27611000000483D3200403D320000EBED01803F1102D0EA0000BC5704AB80EAED018291D276D0EAED0184EAED012795D27600000000EC431102ACEAED01CD94D276EC43110258EBED01603F1102E194D27600000000603F110258EBED01B4EAED010B0000001A00000057BE0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000010000024E9ED017990C577B8006900000069000010000050E9ED01C4F6C4770000690000000000580269000002690064E9ED016C19C5770D00000000026900580269002CEBED0128EBED01000008009786217614E8ED0114EAED01D8E9ED0115E1C077C7670800FEFFFFFF8B8DC477108BC47701000000010000000000000004EAED01CCE9ED01E8E9ED012C8AC375010000000000000004EAED013F8AC375ED1805AB000000006CEFED0102000000FFFFFFFF0000000000000000000000000000E96FACE9ED01485F9B0050EEED01B514C5754D7B2BDFFEFFFFFF3F8AC375A36CC375A589C375651F05AB6CEFED0111000000483D3200403D32006CEFED017CEA0000C05704AB2CEAED018291D2767CEAED01EC430000FC5704AB40EAED01B69CD276F04311024C06000058EAED01603F110264EAED01789CD2763691D27611000000483D3200403D320000EBED01803F1102D0EA0000BC5704AB80EAED018291D276D0EAED0184EAED012795D27600000000EC431102ACEAED01CD94D276EC43110258EBED01603F1102E194D27600000000603F110258EBED01B4EAED010B0000001A00000057BE0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000010000024E9ED017990C577B8006900000069000010000050E9ED01C4F6C4770000690000000000580269000002690064E9ED016C19C5770D00000000026900580269002CEBED0128EBED01000008009786217614E8ED0114EAED01D8E9ED0115E1C077C7670800FEFFFFFF8B8DC477108BC47701000000010000000000000004EAED01CCE9ED01E8E9ED012C8AC375010000000000000004EAED013F8AC375ED1805AB000000006CEFED0102000000FFFFFFFF0000000000000000000000000000E96FACE9ED01485F9B0050EEED01B514C5754D7B2BDFFEFFFFFF3F8AC375A36CC375A589C375651F05AB6CEFED0111000000483D3200403D32006CEFED017CEA0000C05704AB2CEAED018291D2767CEAED01EC430000FC5704AB40EAED01B69CD276F04311024C06000058EAED01603F110264EAED01789CD2763691D27611000000483D3200403D320000EBED01803F1102D0EA0000BC5704AB80EAED018291D276D0EAED0184EAED012795D27600000000EC431102ACEAED01CD94D276EC43110258EBED01603F1102E194D27600000000603F110258EBED01B4EAED01 | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (3892) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
Executable files
239
Suspicious files
582
Text files
710
Unknown types
86
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4 | jsonlz4 | |
MD5:— | SHA256:— | |||
| 3892 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\base-track-digest256.sbstore | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
411
TCP/UDP connections
437
DNS requests
162
Threats
330
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3892 | firefox.exe | GET | — | 222.186.16.238:80 | http://act.cmcmcdn.com/js/k/infoc.b.min.js | CN | — | — | suspicious |
3892 | firefox.exe | GET | — | 222.186.16.238:80 | http://dh1.cmcmcdn.com/duba/d/e/7/5/7/de7571d8c371adb22aae157310b6a637.png | CN | — | — | malicious |
3892 | firefox.exe | GET | — | 222.186.16.238:80 | http://dh1.cmcmcdn.com/duba/9/3/4/f/a/934fa0104b23eade3cba28e169672f6f.png | CN | — | — | malicious |
3892 | firefox.exe | GET | — | 222.186.16.238:80 | http://dh1.cmcmcdn.com/duba/5/a/1/3/0/5a13045f60ead4b4b955d756d3b0e922.png | CN | — | — | malicious |
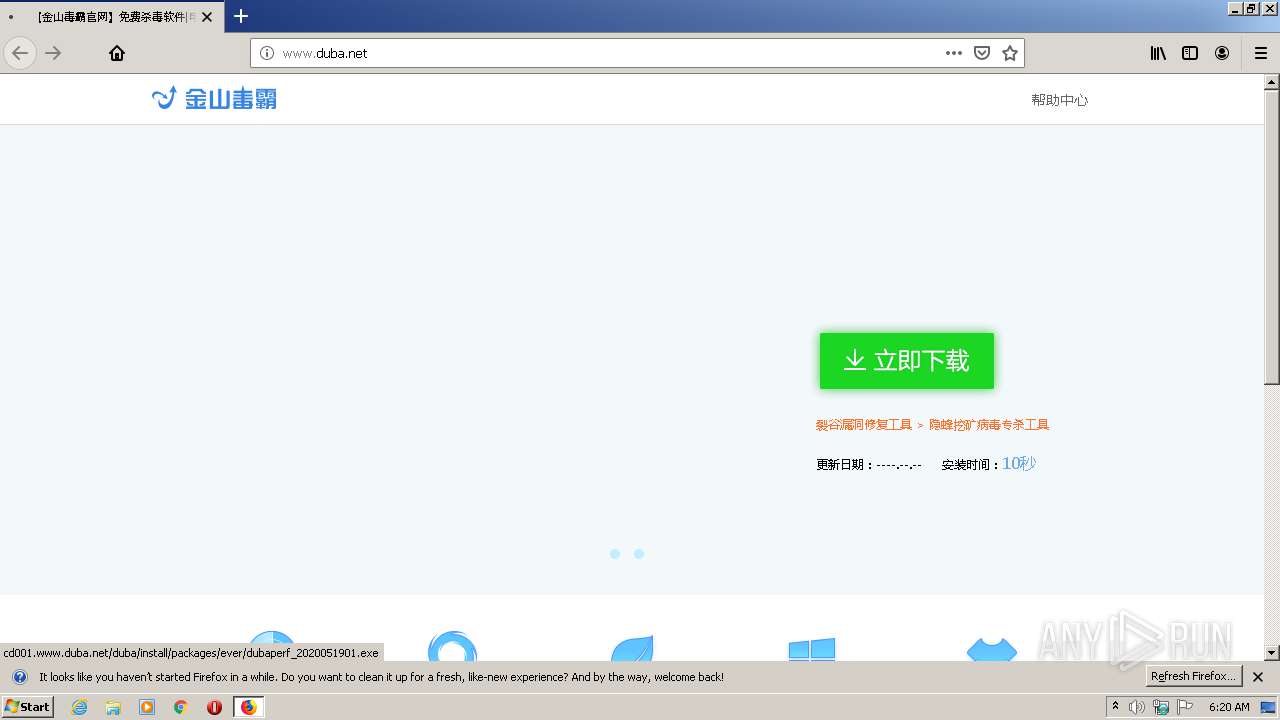
3892 | firefox.exe | GET | 200 | 218.24.18.21:80 | http://www.duba.net/js/jss/jquery.js | CN | text | 24.1 Kb | malicious |
3892 | firefox.exe | GET | 200 | 218.24.18.21:80 | http://www.duba.net/css/indexS.css?v=20200401 | CN | text | 3.97 Kb | malicious |
3892 | firefox.exe | GET | 200 | 218.24.18.21:80 | http://www.duba.net/ | CN | html | 4.08 Kb | malicious |
3892 | firefox.exe | GET | 200 | 218.24.18.21:80 | http://www.duba.net/js/jss/dialog.min.js | CN | text | 1.54 Kb | malicious |
3892 | firefox.exe | GET | 200 | 218.24.18.21:80 | http://www.duba.net/images/20161227/newdb-zbtn.png | CN | image | 12.3 Kb | malicious |
3892 | firefox.exe | GET | 200 | 218.24.18.21:80 | http://www.duba.net/images/20161227/all.png | CN | image | 11.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3892 | firefox.exe | 2.16.107.58:80 | detectportal.firefox.com | Akamai International B.V. | — | suspicious |
3892 | firefox.exe | 218.24.18.21:80 | www.duba.net | CHINA UNICOM China169 Backbone | CN | suspicious |
3892 | firefox.exe | 52.41.191.52:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3892 | firefox.exe | 202.173.15.148:80 | kxlogo.knet.cn | KNET Techonlogy (BeiJing) Co.,Ltd. | CN | unknown |
3892 | firefox.exe | 222.186.16.238:80 | dh1.cmcmcdn.com | AS Number for CHINANET jiangsu province backbone | CN | unknown |
3892 | firefox.exe | 103.235.46.191:80 | hm.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | suspicious |
3892 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3892 | firefox.exe | 143.204.94.64:443 | snippets.cdn.mozilla.net | — | US | malicious |
3892 | firefox.exe | 13.224.198.15:443 | firefox.settings.services.mozilla.com | — | US | unknown |
3892 | firefox.exe | 58.49.180.1:80 | www.ijinshan.com | No.31,Jin-rong Street | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
www.duba.net |
| malicious |
a1089.dscd.akamai.net |
| whitelisted |
zliebao.v.bsgslb.cn |
| suspicious |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
dh1.cmcmcdn.com |
| malicious |
www.ijinshan.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3892 | firefox.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
2988 | dubaperf_2020051901.exe | Misc activity | ADWARE [PTsecurity] PUP.Win32/KingSoft.E (antivirus) |
2988 | dubaperf_2020051901.exe | Misc activity | ADWARE [PTsecurity] PUP.Win32/KingSoft.E |
2988 | dubaperf_2020051901.exe | Misc activity | ADWARE [PTsecurity] PUP.Win32/KingSoft.E |
2988 | dubaperf_2020051901.exe | Potentially Bad Traffic | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2988 | dubaperf_2020051901.exe | Misc activity | ADWARE [PTsecurity] W32/Kingsoft Checkin |
2988 | dubaperf_2020051901.exe | Misc activity | ADWARE [PTsecurity] W32/Kingsoft Response |
2988 | dubaperf_2020051901.exe | Misc activity | ADWARE [PTsecurity] PUP.Win32/KingSoft.E |
130 ETPRO signatures available at the full report
Process | Message |
|---|---|
dubaperf_2020051901.exe | 06:21:58|~03400| [KAVMENU] reg_duba_32bit |
kavlog2.exe | _tWinMain End. |
kxescore.exe | c:\program files\kingsoft\kingsoft antivirus\ksapi.dll |
kxescore.exe | c:\program files\kingsoft\kingsoft antivirus\ksapi.dll |
kxetray.exe | c:\program files\kingsoft\kingsoft antivirus\ksapi.dll |
kxetray.exe | c:\program files\kingsoft\kingsoft antivirus\ksapi.dll |
kxemain.exe | c:\program files\kingsoft\kingsoft antivirus\ksapi.dll |
kxemain.exe | c:\program files\kingsoft\kingsoft antivirus\ksapi.dll |
kxetray.exe | g_recent_newskin:false -- print
|
kxetray.exe | SqBallShowOptionChange:3 -- print
|