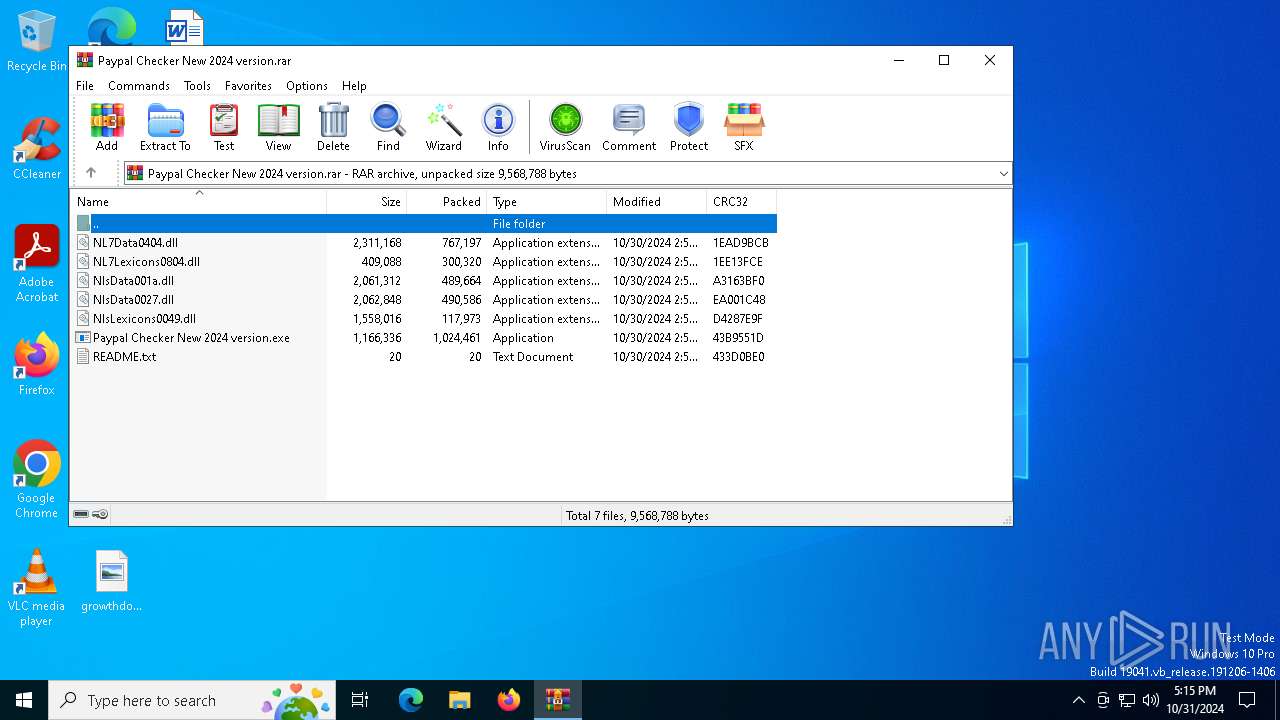
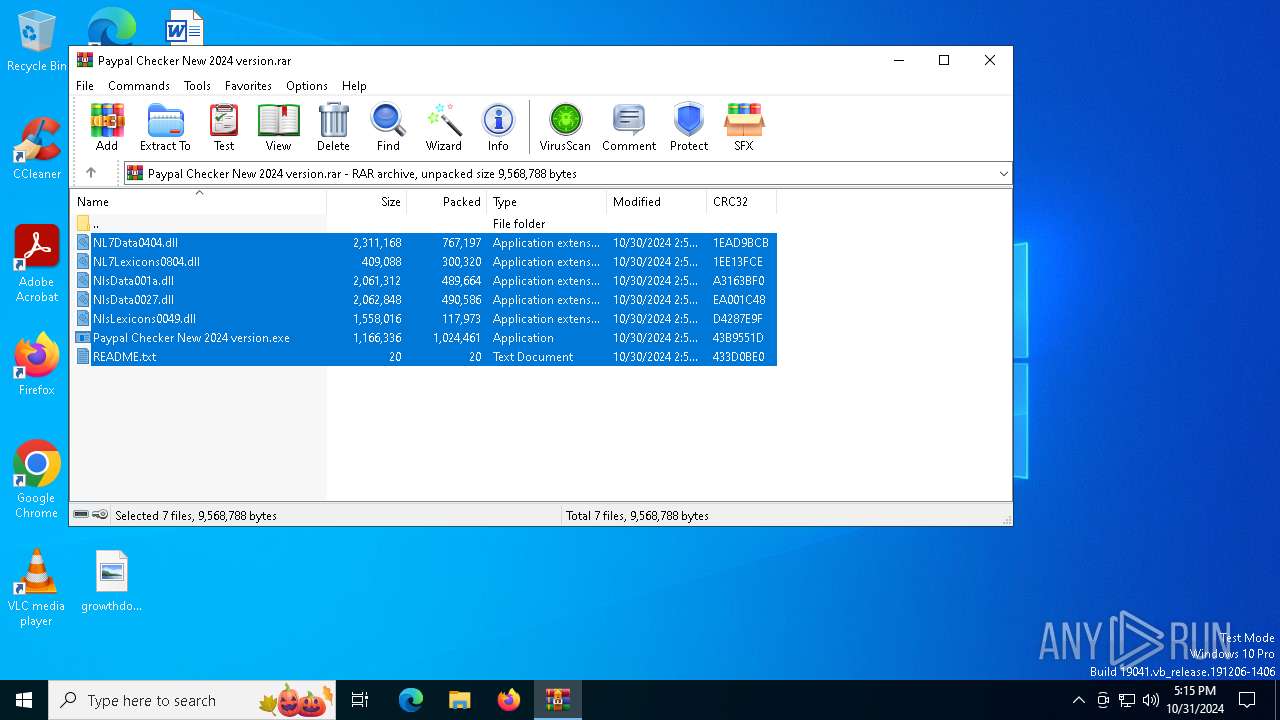
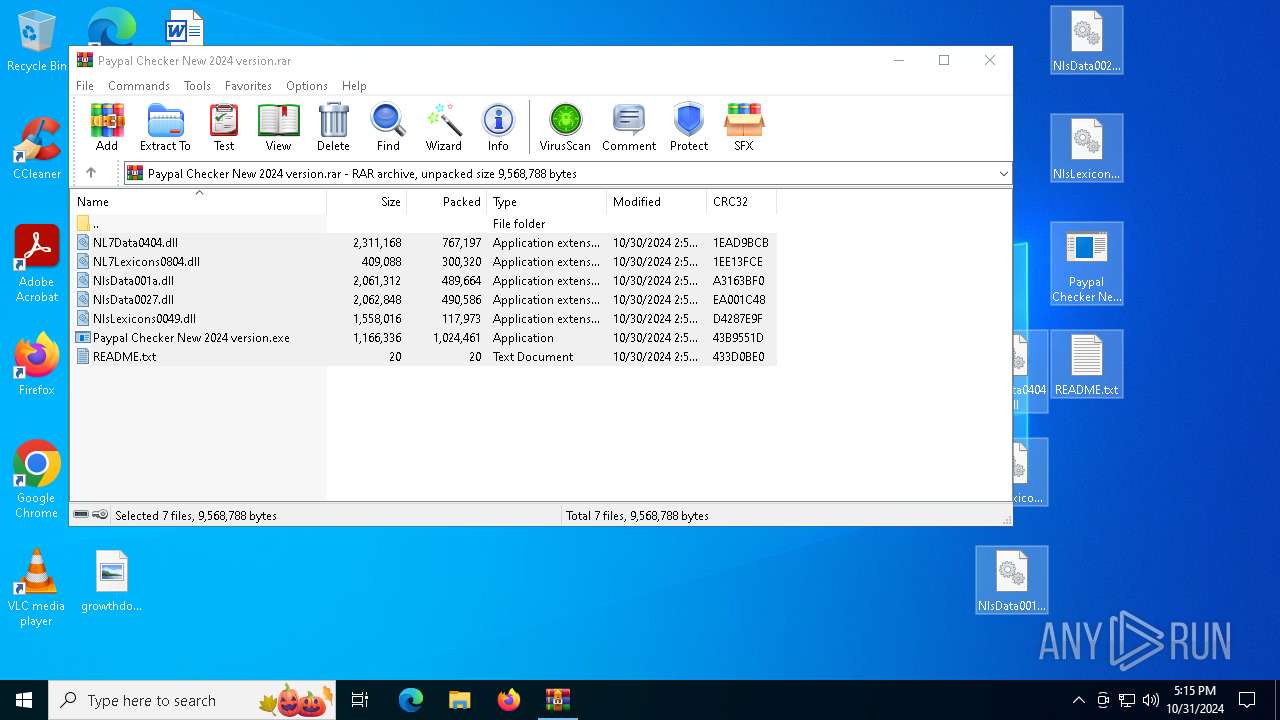
| File name: | Paypal Checker New 2024 version.rar |
| Full analysis: | https://app.any.run/tasks/4e6c3023-0c90-4c91-a05e-54638a829686 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 31, 2024, 17:14:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CE89266D589FC52E395F1A596571AED2 |
| SHA1: | 1DDB8372130B4CB8EF38BB90DD9478F69A216790 |
| SHA256: | 45EF548F451F98FA4B6C3BEA6D5C74A80292B0A8239E2D2210DA503726374835 |
| SSDEEP: | 98304:bIWrNlSVOBOGCEEuHdZMYW4DrzFehjVNfggalm56rMjWSv5hVA1LEuFYIqWUzs+q:DHIZla |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2172)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
- rtKNzonlBa.exe (PID: 3832)
Stealers network behavior
- rtKNzonlBa.exe (PID: 3832)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1576)
Executes application which crashes
- Paypal Checker New 2024 version.exe (PID: 300)
- rtKNzonlBa.exe (PID: 7144)
Application launched itself
- rtKNzonlBa.exe (PID: 7144)
- Paypal Checker New 2024 version.exe (PID: 300)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
- rtKNzonlBa.exe (PID: 3832)
Executable content was dropped or overwritten
- bUULV4cfU7.exe (PID: 5976)
- Paypal Checker New 2024 version.exe (PID: 5948)
INFO
Manual execution by a user
- Paypal Checker New 2024 version.exe (PID: 300)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1024461 |
| UncompressedSize: | 1166336 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Paypal Checker New 2024 version.exe |
Total processes
135
Monitored processes
11
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\Desktop\Paypal Checker New 2024 version.exe" | C:\Users\admin\Desktop\Paypal Checker New 2024 version.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 616 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7144 -s 336 | C:\Windows\SysWOW64\WerFault.exe | rtKNzonlBa.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Paypal Checker New 2024 version.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2380 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 300 -s 280 | C:\Windows\SysWOW64\WerFault.exe | Paypal Checker New 2024 version.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | "C:\Users\admin\AppData\Roaming\rtKNzonlBa.exe" | C:\Users\admin\AppData\Roaming\rtKNzonlBa.exe | rtKNzonlBa.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Paypal Checker New 2024 version.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5948 | "C:\Users\admin\Desktop\Paypal Checker New 2024 version.exe" | C:\Users\admin\Desktop\Paypal Checker New 2024 version.exe | Paypal Checker New 2024 version.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5976 | "C:\Users\admin\AppData\Roaming\bUULV4cfU7.exe" | C:\Users\admin\AppData\Roaming\bUULV4cfU7.exe | Paypal Checker New 2024 version.exe | ||||||||||||
User: admin Company: Microsoft Windows Integrity Level: MEDIUM Description: system32 Version: 15.6.13.6 Modules
| |||||||||||||||
| 6192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rtKNzonlBa.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 628
Read events
8 622
Write events
6
Delete events
0
Modification events
| (PID) Process: | (1576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Paypal Checker New 2024 version.rar | |||
| (PID) Process: | (1576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
8
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2380 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Paypal Checker N_9deed480613c815ec9c25a84c6828c3e34825a_edebd1dd_effef0ea-c9e4-4c6a-8eb8-18eca942ef2d\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2380 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1989.tmp.xml | xml | |
MD5:4E64B434F39DE6C1C40426E21BDE37FF | SHA256:8CFD440D25AE45A381BB392251B23A74B878784D0E5FBCDBC45245EAFE6E891F | |||
| 1576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1576.22112\README.txt | text | |
MD5:229BFB07694F123E2CB4986F47100A62 | SHA256:8DF26B1F550C80646F01D25B8AAFCABB1342BBB2BE1CD335CDB8D254BE8C4090 | |||
| 616 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_rtKNzonlBa.exe_17bbd65e7bf9821afc6da046fb50e3c4143daaba_063a1f78_949c896b-17e9-486a-80ba-0132b5a35719\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1576.22112\Paypal Checker New 2024 version.exe | executable | |
MD5:2ABFF13CFDBB439B7BD63D3BE7727689 | SHA256:61AEEB5A4A82B1083D1378EEFDB77AB7D30FC0B89566E6400387DEBAEDD64C37 | |||
| 2380 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER18DB.tmp.dmp | binary | |
MD5:1302798BED575B30DD14C1EA0C30252A | SHA256:62D38EF01067005A771E5FFAA2B5E0923EDE8061D8C2E7DB722452E548BEFECA | |||
| 5976 | bUULV4cfU7.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost.exe | executable | |
MD5:5AFB8CE4DD3923219BD69BD7B5168D91 | SHA256:F727BBA8D917FA3F129D71745E0741A8511F940B1A6817FF5130AA2F3AE85C79 | |||
| 2380 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Paypal Checker New 2024 version.exe.300.dmp | binary | |
MD5:5A6BD2F79E0C88436B7B692A72F86F75 | SHA256:59A73E71C6A22660674B7763CC26CCCA3862A3BA80293A95FC58F21734266C81 | |||
| 2380 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:8800716E0FCE81542EBA9097EE7C7181 | SHA256:02C8BD3FC85704C3A57F101B63278D33F86EE73907DAFC3519B263BA58C42DFD | |||
| 616 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER21D4.tmp.dmp | dmp | |
MD5:1640EFB9F92772AAA9D5A5CDCA95A8C7 | SHA256:51F846E173D56A90762F88D0687E79C5DEE2B6465618E9B0EE1A6F7A8FCD10AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
49
DNS requests
25
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2380 | WerFault.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7080 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2380 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4292 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.184:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (servicedny .site) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (seallysl .site) |
3832 | rtKNzonlBa.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (goalyfeastz .site in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (opposezmny .site) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (goalyfeastz .site) |
3832 | rtKNzonlBa.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
3832 | rtKNzonlBa.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (goalyfeastz .site in TLS SNI) |
3832 | rtKNzonlBa.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (goalyfeastz .site in TLS SNI) |
3832 | rtKNzonlBa.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (goalyfeastz .site in TLS SNI) |
3832 | rtKNzonlBa.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (goalyfeastz .site in TLS SNI) |