| File name: | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe |
| Full analysis: | https://app.any.run/tasks/1658f0a2-8014-427c-9a71-69cab1dff87d |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | December 05, 2023, 04:08:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 15BC4D1C91DA5D491756D4C4CFA96F8E |
| SHA1: | D1A0A6F32D9A41FF76FE2A0FF3EF084334B949D6 |
| SHA256: | 456480580B48923A2771689CF8EE2240D1A98F5C1633671260BDC203CE5A8EDD |
| SSDEEP: | 98304:JC8vTnwoelpJoyWvyY/Cr0/WB55Mhr/vYrFmGA7Az2qeRVcW4fsCGLycWMMXXYrC:bxQbgX |
MALICIOUS
Drops the executable file immediately after the start
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
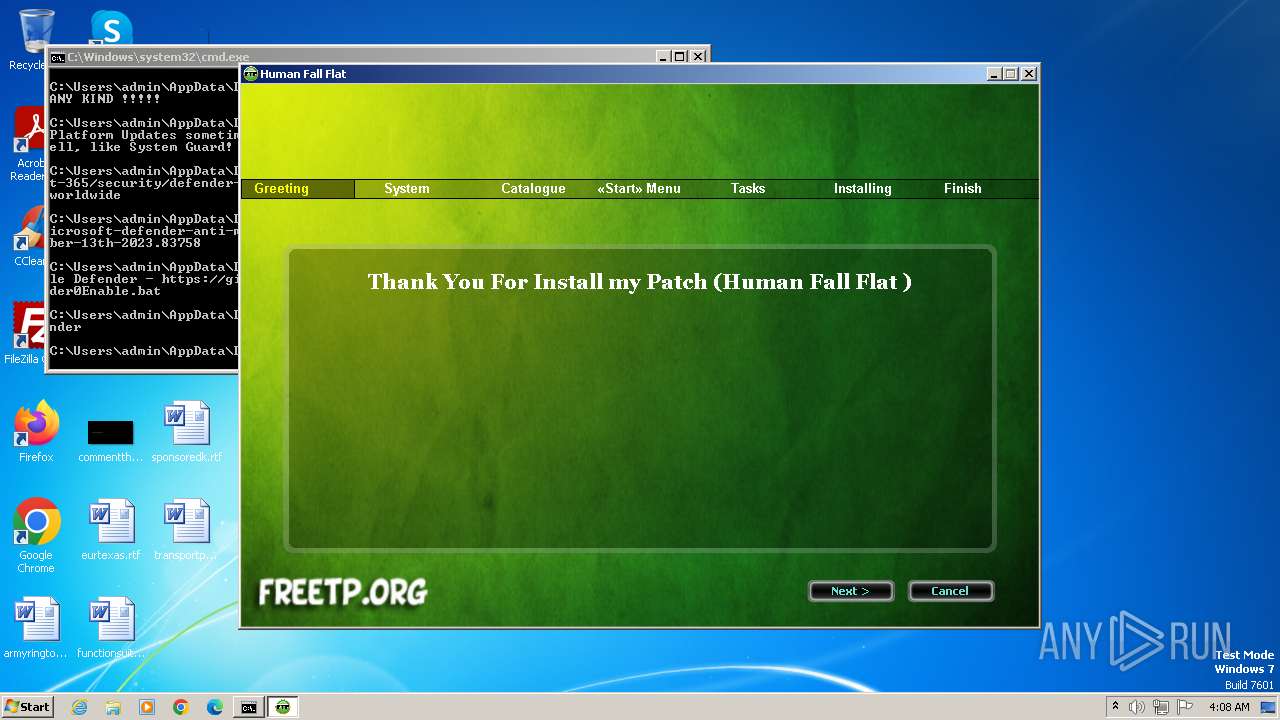
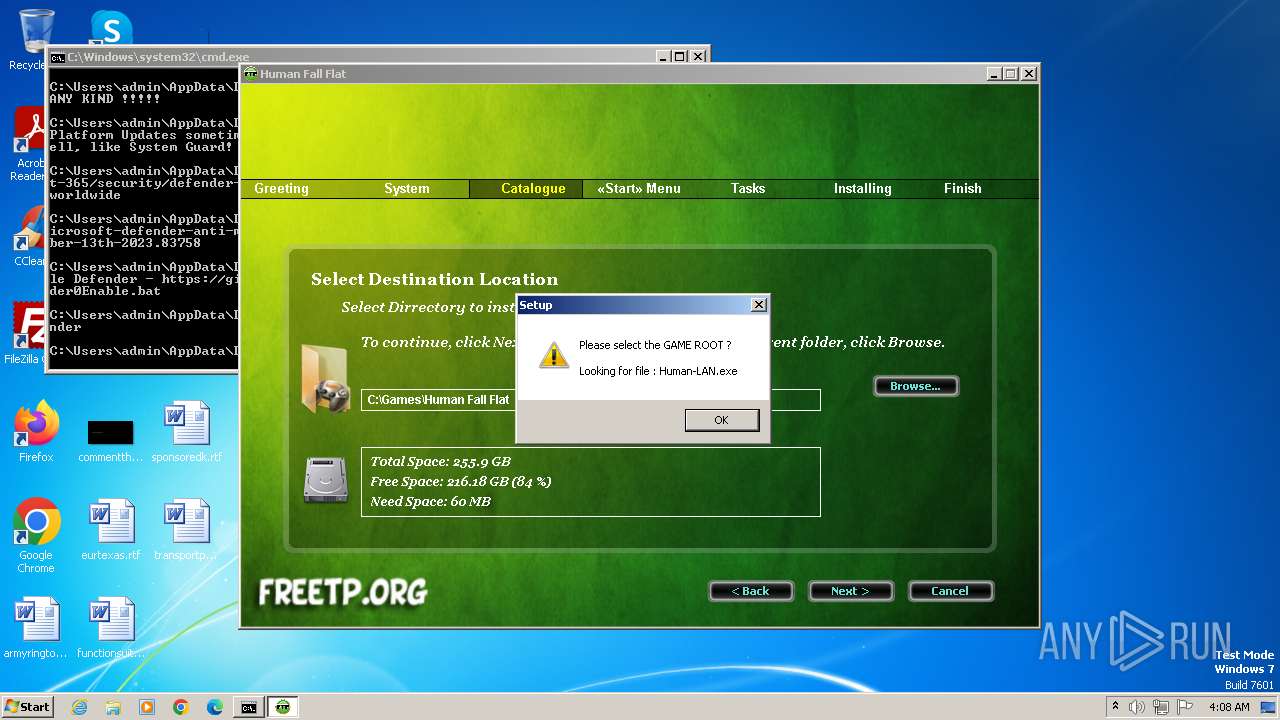
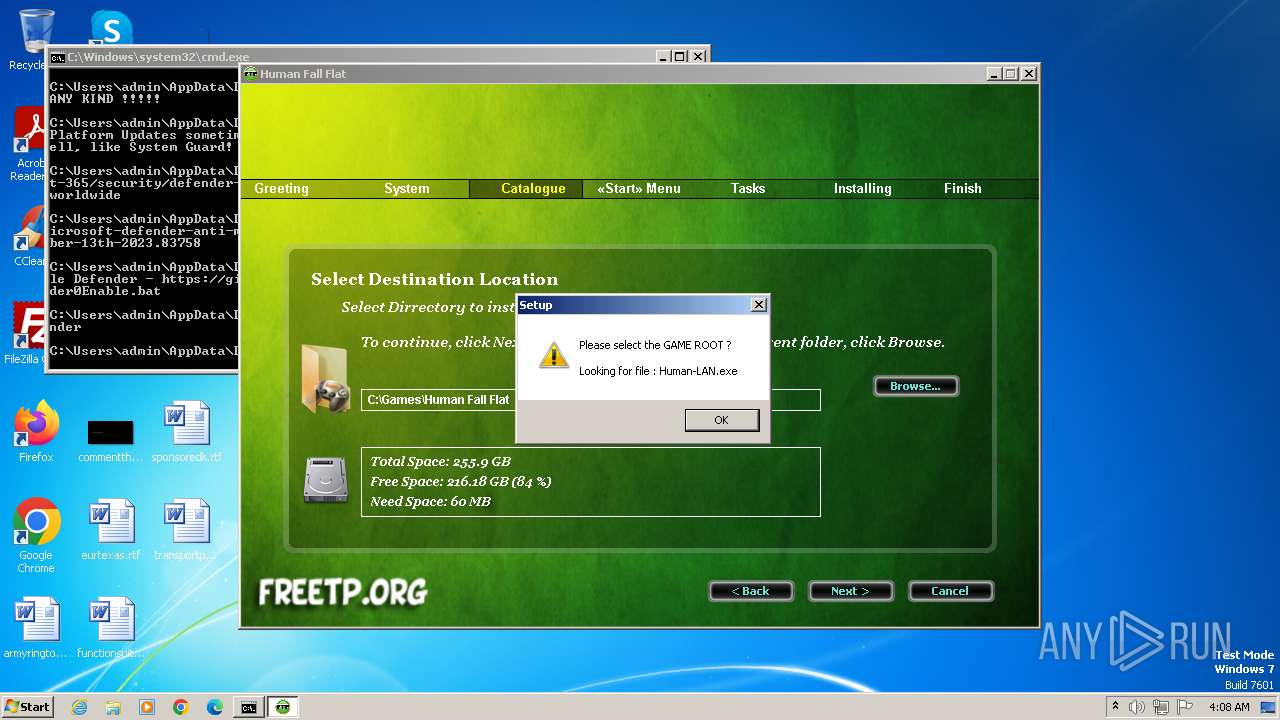
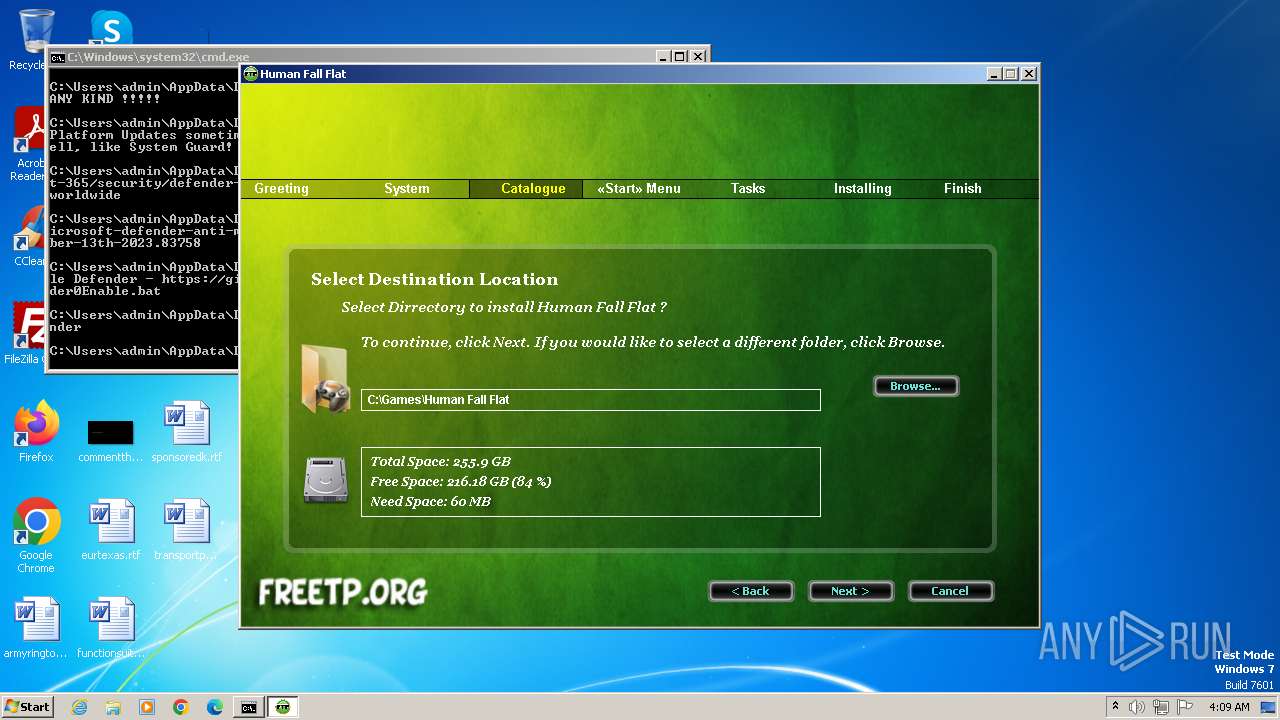
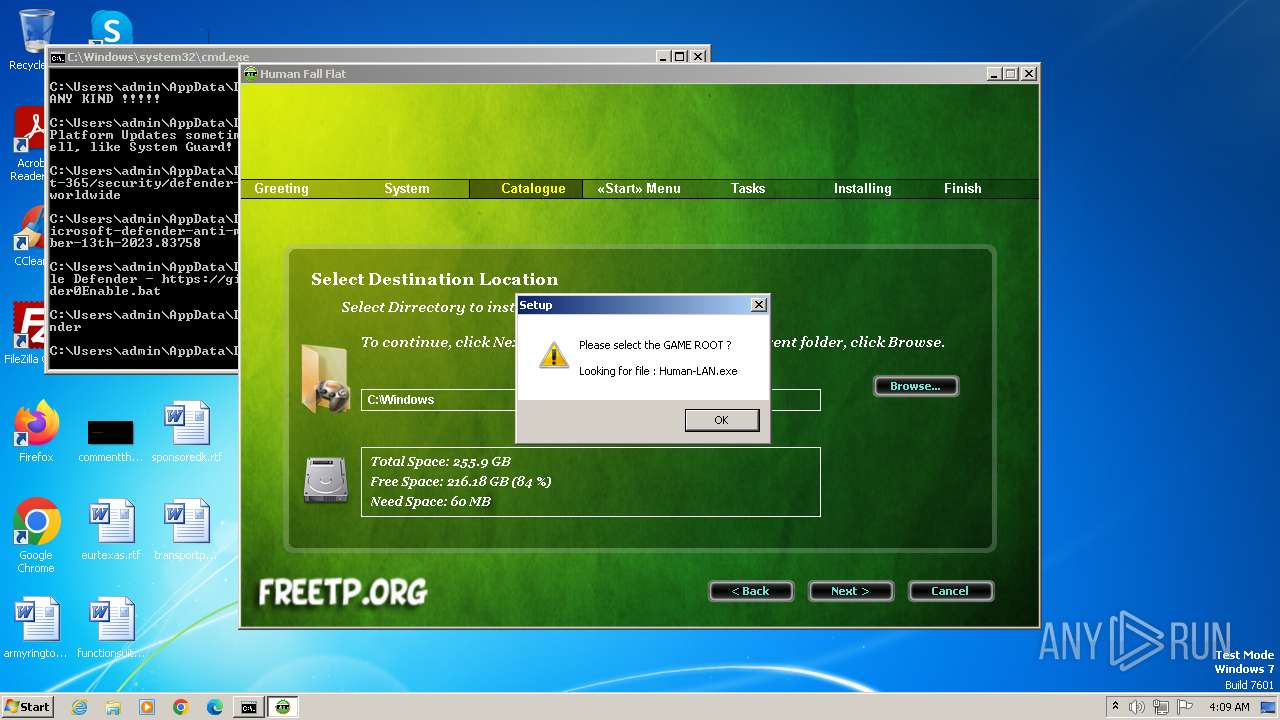
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe (PID: 2084)
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
NJRAT has been detected (SURICATA)
- stub.exe (PID: 3872)
Connects to the CnC server
- stub.exe (PID: 3872)
SUSPICIOUS
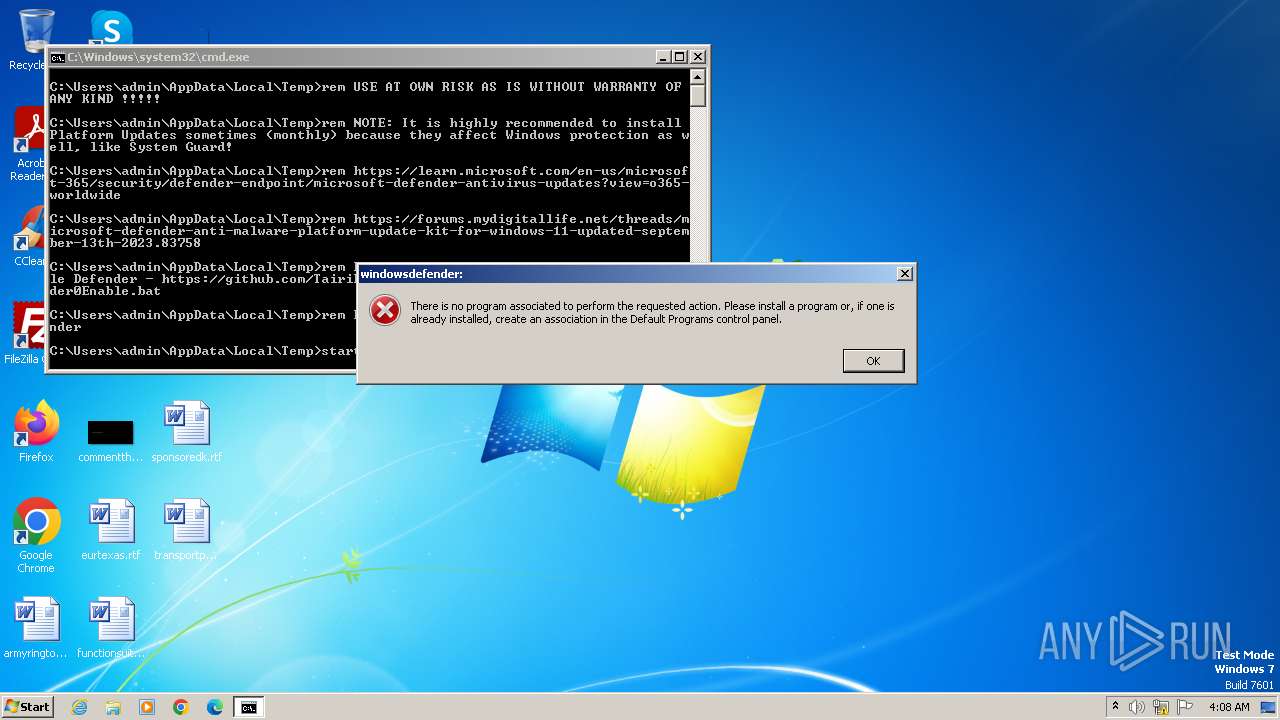
Starts CMD.EXE for commands execution
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
Reads the Internet Settings
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
- cmd.exe (PID: 3672)
- stub.exe (PID: 3872)
Executing commands from a ".bat" file
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
Found strings related to reading or modifying Windows Defender settings
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
Process drops legitimate windows executable
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
Reads the Windows owner or organization settings
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
Reads settings of System Certificates
- stub.exe (PID: 3872)
Connects to unusual port
- stub.exe (PID: 3872)
INFO
Reads the machine GUID from the registry
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
- stub.exe (PID: 3872)
Checks supported languages
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
- stub.exe (PID: 3872)
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe (PID: 2084)
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
- wmpnscfg.exe (PID: 2868)
Reads the computer name
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
- stub.exe (PID: 3872)
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
- wmpnscfg.exe (PID: 2868)
Create files in a temporary directory
- 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe (PID: 2412)
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe (PID: 2084)
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
Reads Environment values
- stub.exe (PID: 3872)
Manual execution by a user
- wmpnscfg.exe (PID: 2868)
Reads product name
- stub.exe (PID: 3872)
Reads CPU info
- [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp (PID: 1344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:30 15:37:51+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 3353600 |
| InitializedDataSize: | 57344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x334afe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
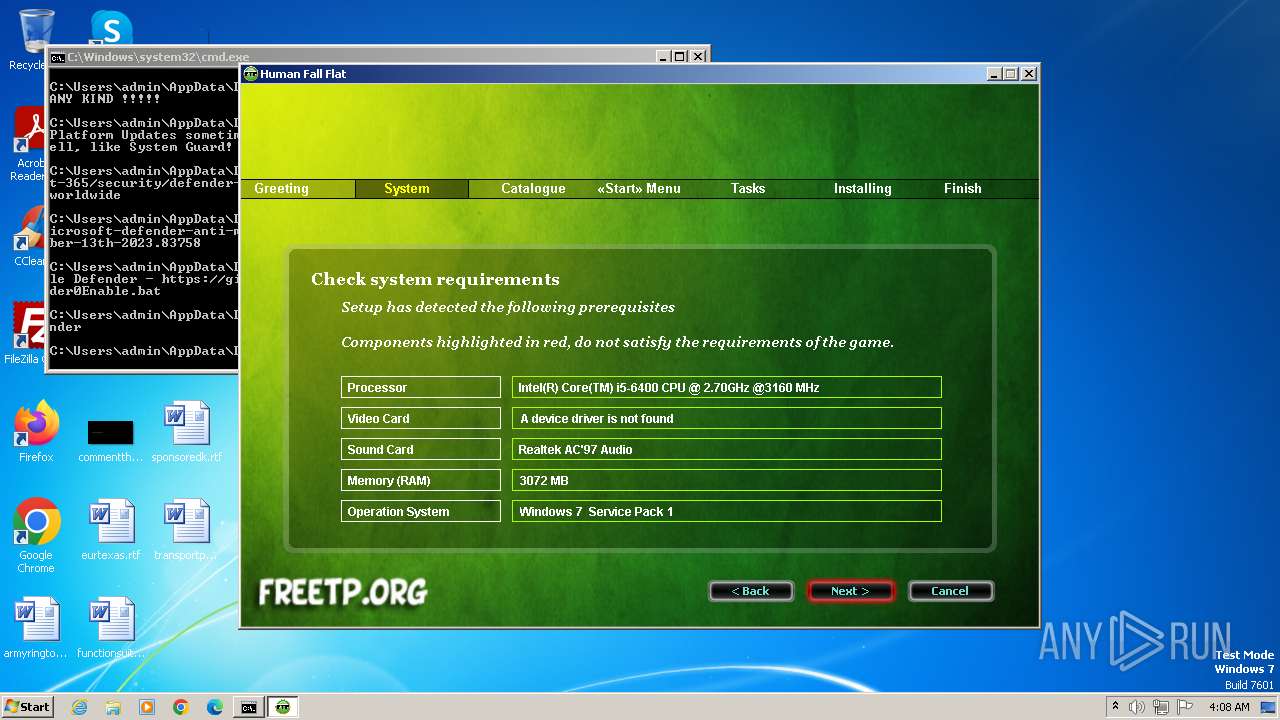
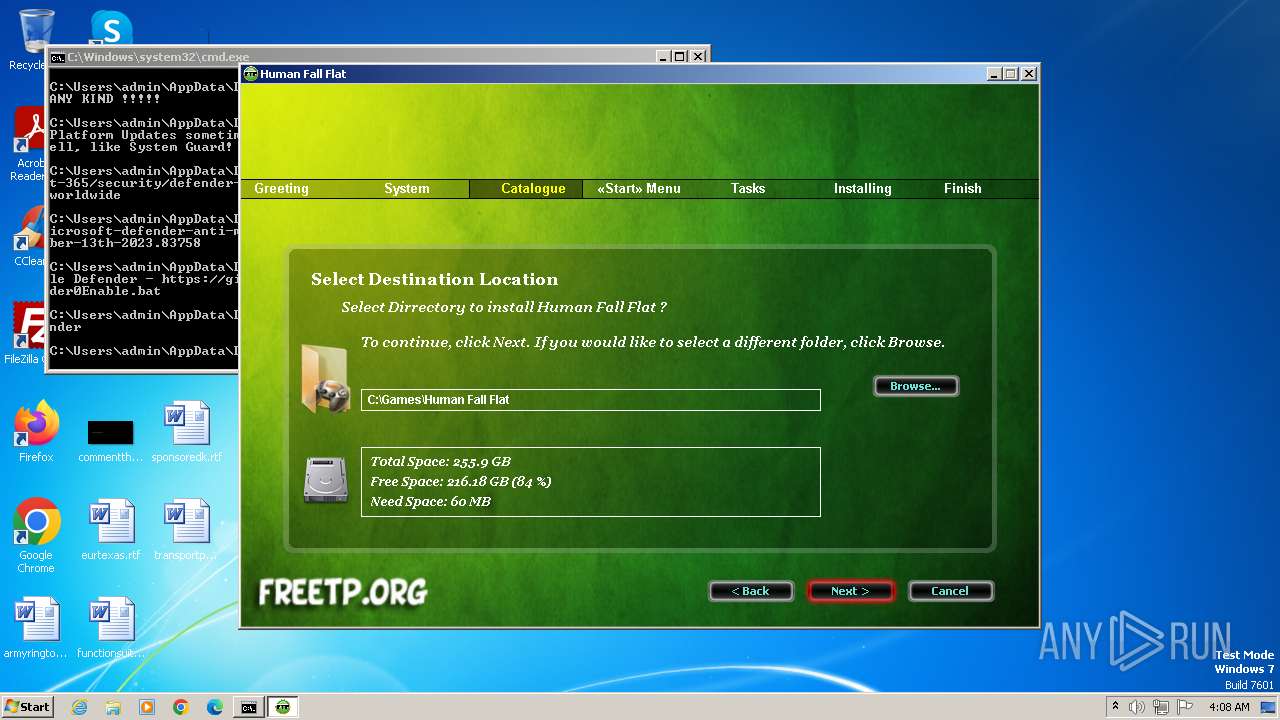
| CompanyName: | FreeTP.Org - Human Fall Flat Multiplayer Fix |
| FileDescription: | Human Fall Flat |
| FileVersion: | 0.0.0.0 |
| InternalName: | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe |
| LegalCopyright: | |
| OriginalFileName: | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe |
| ProductName: | Human Fall Flat |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
46
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1344 | "C:\Users\admin\AppData\Local\Temp\is-MVDGT.tmp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp" /SL5="$26013A,2865322,190464,C:\Users\admin\AppData\Local\Temp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe" | C:\Users\admin\AppData\Local\Temp\is-MVDGT.tmp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | — | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe" | C:\Users\admin\AppData\Local\Temp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | ||||||||||||
User: admin Company: FreeTP.Org - Human Fall Flat Multiplayer Fix Integrity Level: HIGH Description: Human Fall Flat Exit code: 0 Version: Modules
| |||||||||||||||
| 2412 | "C:\Users\admin\AppData\Local\Temp\456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe" | C:\Users\admin\AppData\Local\Temp\456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | — | explorer.exe | |||||||||||
User: admin Company: FreeTP.Org - Human Fall Flat Multiplayer Fix Integrity Level: MEDIUM Description: Human Fall Flat Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\AppData\Local\Temp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe" | C:\Users\admin\AppData\Local\Temp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe | — | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | |||||||||||
User: admin Company: FreeTP.Org - Human Fall Flat Multiplayer Fix Integrity Level: MEDIUM Description: Human Fall Flat Exit code: 3221226540 Version: Modules
| |||||||||||||||
| 2868 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3672 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Microsoft Defender Disable.bat" " | C:\Windows\System32\cmd.exe | — | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3872 | "C:\Users\admin\AppData\Local\Temp\stub.exe" | C:\Users\admin\AppData\Local\Temp\stub.exe | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
4 976
Read events
4 955
Write events
21
Delete events
0
Modification events
| (PID) Process: | (2412) 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2412) 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2412) 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2412) 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3872) stub.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1344) [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: flashplayer32ax_xa_install.exe | |||
Executable files
7
Suspicious files
0
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2412 | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | C:\Users\admin\AppData\Local\Temp\stub.exe | executable | |
MD5:C0E9C050A999C46528AC1E176CF0A00D | SHA256:9CC01229BCC1D0D2619CE65B13BD737449700DC892B1D19C7839A5A7F3C262C9 | |||
| 2412 | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | C:\Users\admin\AppData\Local\Temp\Microsoft Defender Disable.bat | text | |
MD5:4F79C754E9958D1AEE7EE1BF0F620C16 | SHA256:2A089B08617195FB30B10A1B3E2C0EDA45BC49A31CCA7B9680F08E8631A0092C | |||
| 1344 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | C:\Users\admin\AppData\Local\Temp\is-O86JS.tmp\innocallback.dll | executable | |
MD5:1C55AE5EF9980E3B1028447DA6105C75 | SHA256:6AFA2D104BE6EFE3D9A2AB96DBB75DB31565DAD64DD0B791E402ECC25529809F | |||
| 2412 | 456480580b48923a2771689cf8ee2240d1a98f5c1633671260bdc203ce5a8edd.exe | C:\Users\admin\AppData\Local\Temp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe | executable | |
MD5:592B233A631AA9684102991684B906EF | SHA256:81878356F5A813A3004C1BCCCCE453AA1F38BD1C37523F4878ED619D0AC7F456 | |||
| 1344 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | C:\Users\admin\AppData\Local\Temp\is-O86JS.tmp\get_hw_caps.dll | executable | |
MD5:2E35D2894DF3B691DBD8E0D4F4C84EFC | SHA256:869079BA362CBC560D673DB290248EC2AA075A74F22A82D90621F1118F8E1C4D | |||
| 2084 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.exe | C:\Users\admin\AppData\Local\Temp\is-MVDGT.tmp\[FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | executable | |
MD5:17FAC68C3018078E9BEDC9D58D02423B | SHA256:C87BD5D9698EB981EE384BAA08305E7B94769E0CF3C1BBC97D11AAB096013417 | |||
| 1344 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | C:\Users\admin\AppData\Local\Temp\is-O86JS.tmp\botva2.dll | executable | |
MD5:295832FA6400CB3407CFE84B06785531 | SHA256:13E372C4D843603096F33603915C3F25D0E0D4475001C33CE5263BFCD1760784 | |||
| 1344 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | C:\Users\admin\AppData\Local\Temp\is-O86JS.tmp\StatusPanel2.png | image | |
MD5:567FE80CE090119956DF8CC152930CF2 | SHA256:6B4B64CFA24B8B040B8F6CEB3553007609B0C3D46B7202ACC7FB6D0CB8603986 | |||
| 1344 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | C:\Users\admin\AppData\Local\Temp\is-O86JS.tmp\WizardImage.jpg | image | |
MD5:B91658597F15D7F689C86F5A2E7824BD | SHA256:B3CDA6AB45AD5AA6A0A5F700D2C8987B3C1C1EBDA63165D9BD5A566B24DCBD84 | |||
| 1344 | [FreeTP.Org]Human-Fall-Flat-Multiplayer-Fix-Online-v4.tmp | C:\Users\admin\AppData\Local\Temp\is-O86JS.tmp\GroupFolder.png | image | |
MD5:D2018CFAB20B6385A80EF24100267CAC | SHA256:90649334D9D905558E337C6FD329624201BB0BE037EE67F7555E5ADA8CE49C96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
3
Threats
14
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3872 | stub.exe | 104.20.67.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
3872 | stub.exe | 18.192.31.165:17987 | 0.tcp.eu.ngrok.io | AMAZON-02 | DE | malicious |
3872 | stub.exe | 3.125.223.134:17987 | 0.tcp.eu.ngrok.io | AMAZON-02 | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
0.tcp.eu.ngrok.io |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DNS Query to a *.ngrok domain (ngrok.io) |
3872 | stub.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
3872 | stub.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
1080 | svchost.exe | Misc activity | ET INFO DNS Query to a *.ngrok domain (ngrok.io) |
3872 | stub.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
9 ETPRO signatures available at the full report