| File name: | ea97169151c8fc8189ceba9290b41823 |
| Full analysis: | https://app.any.run/tasks/f0203f07-4631-4b8a-a55e-2b5e586812f8 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 04, 2024, 20:28:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | news or mail, ASCII text, with CRLF line terminators |
| MD5: | EA97169151C8FC8189CEBA9290B41823 |
| SHA1: | 1E3E612917CEED5F04301D4CB89281488FD1DEF1 |
| SHA256: | 45444397552D1C7A1A5D95A6C438AC582D7B5FF0CD790D92DA4B3BA3AE0AD7ED |
| SSDEEP: | 3072:V3EiAH63QYDDNsh8vfuvwm3O4OInAKqLySxO:26gYDnnowMO4pn69O |
MALICIOUS
Unusual execution from MS Outlook
- OUTLOOK.EXE (PID: 4876)
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 4876)
- CasPol.exe (PID: 6448)
Steals credentials from Web Browsers
- CasPol.exe (PID: 6448)
AGENTTESLA has been detected (YARA)
- CasPol.exe (PID: 6448)
Actions looks like stealing of personal data
- CasPol.exe (PID: 6448)
SUSPICIOUS
Checks for external IP
- CasPol.exe (PID: 6448)
Process drops legitimate windows executable
- CasPol.exe (PID: 6448)
Executable content was dropped or overwritten
- CasPol.exe (PID: 6448)
Connects to FTP
- CasPol.exe (PID: 6448)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2500)
- OUTLOOK.EXE (PID: 4876)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2500)
Checks supported languages
- QUOTATION#00913.exe (PID: 6464)
- CasPol.exe (PID: 6448)
Reads the computer name
- QUOTATION#00913.exe (PID: 6464)
- CasPol.exe (PID: 6448)
Manual execution by a user
- QUOTATION#00913.exe (PID: 6464)
Reads the machine GUID from the registry
- QUOTATION#00913.exe (PID: 6464)
- CasPol.exe (PID: 6448)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2500)
Reads Environment values
- CasPol.exe (PID: 6448)
Creates files or folders in the user directory
- QUOTATION#00913.exe (PID: 6464)
- CasPol.exe (PID: 6448)
Reads the software policy settings
- CasPol.exe (PID: 6448)
Checks proxy server information
- CasPol.exe (PID: 6448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 2) (100) |
|---|
Total processes
135
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2500 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\4LK8LWEW\QUOTATION#00913.gz" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4876 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\ea97169151c8fc8189ceba9290b41823.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5256 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "D7427929-BA1F-45D5-9279-F5311DA4A9A4" "E98F390F-DAF1-4B13-BB6A-1B21FA8E037B" "4876" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6448 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe | QUOTATION#00913.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework CAS Policy Manager Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6464 | "C:\Users\admin\Desktop\QUOTATION#00913.exe" | C:\Users\admin\Desktop\QUOTATION#00913.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Project322024 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
14 506
Read events
14 236
Write events
143
Delete events
127
Modification events
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E04000000000000000400000000000000 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 1 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 1 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 1 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 1 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 1 | |||
| (PID) Process: | (4876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 1 | |||
Executable files
2
Suspicious files
14
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4876 | OUTLOOK.EXE | C:\USERS\ADMIN\DOCUMENTS\OUTLOOK FILES\OUTLOOK1.PST | — | |
MD5:— | SHA256:— | |||
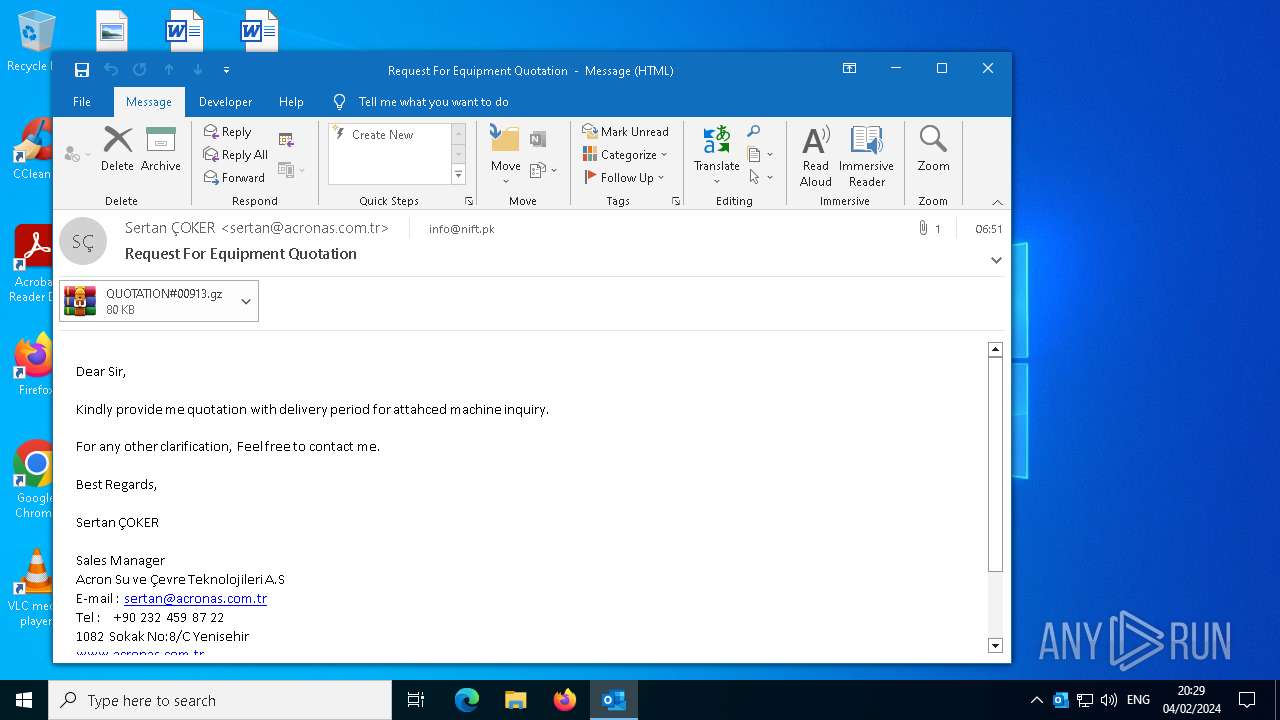
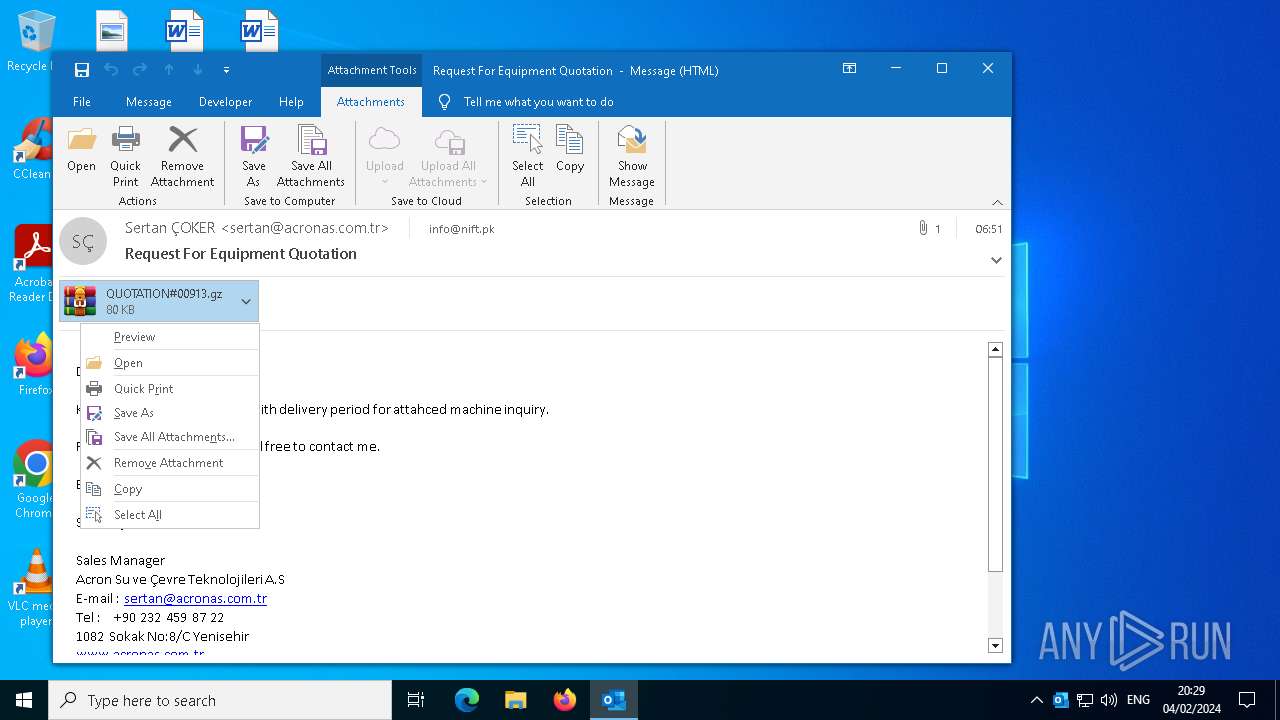
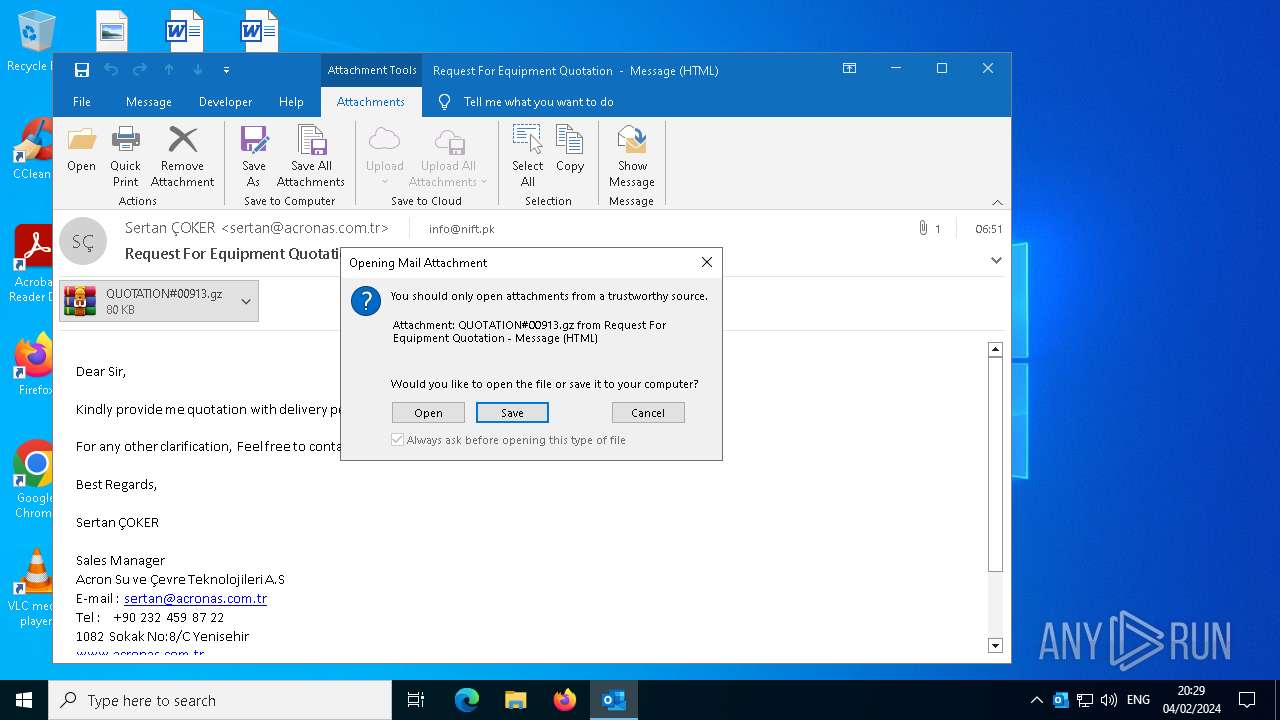
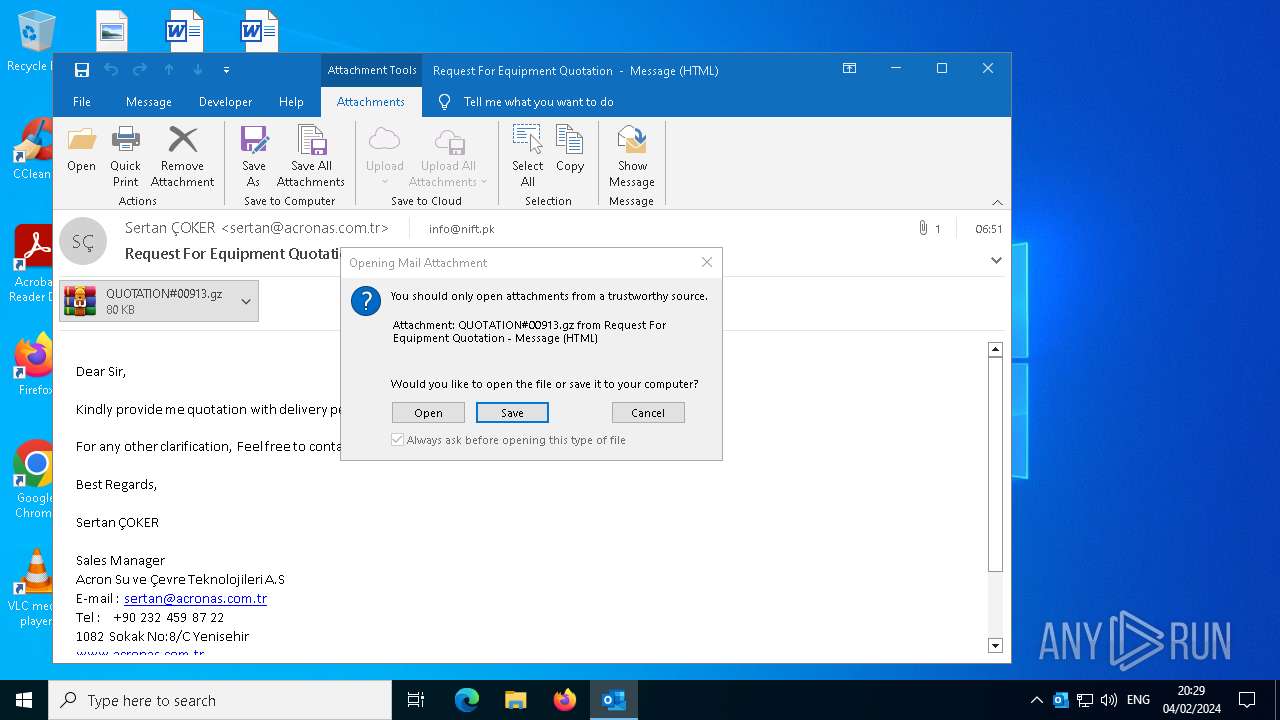
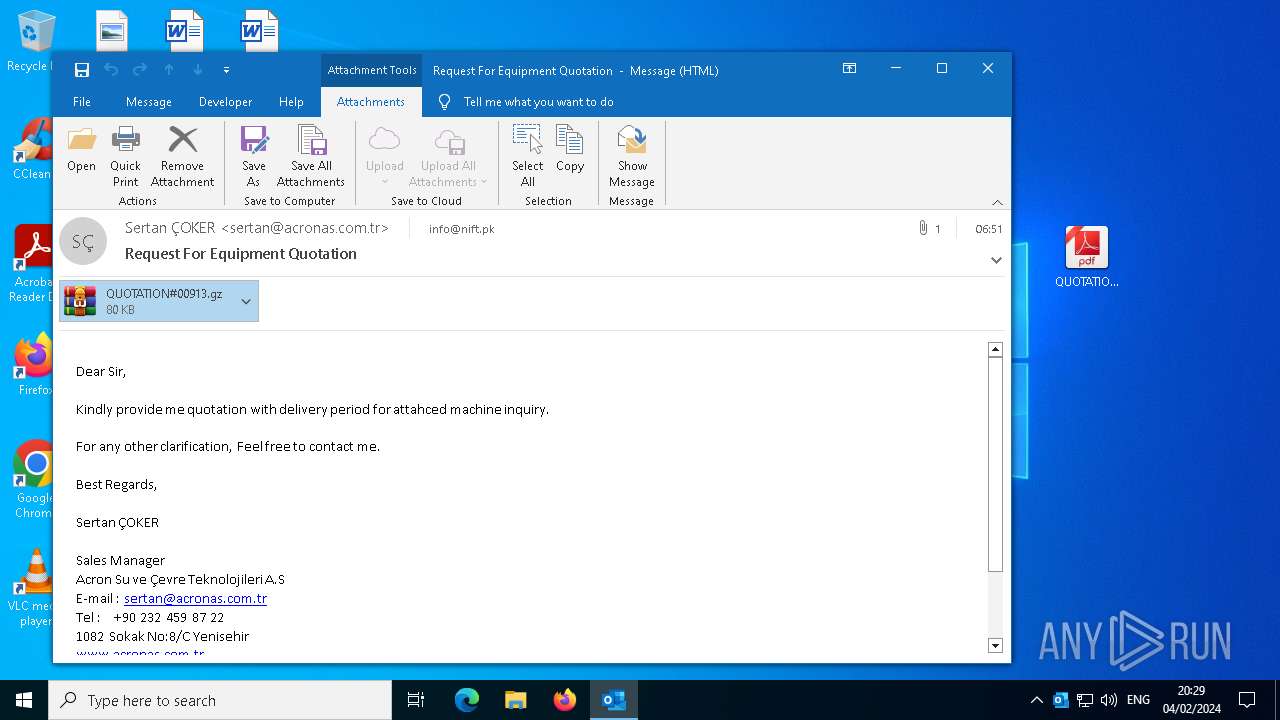
| 4876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\4LK8LWEW\QUOTATION#00913.gz | compressed | |
MD5:1F46757CFD9B2958DD614A0470DA5417 | SHA256:291E7CA64F60D55CF36C8B4A87090FCCE0388F3041317702F3411B81C867CADD | |||
| 4876 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:4E5A6AA5DB46737394BF05E59D9D9F78 | SHA256:20A8C7388F200B8F233BC7E1FC35EFE39AB6D259ECE8832E4A59B6C793C6CD0F | |||
| 4876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\4LK8LWEW\QUOTATION#00913 (002).gz:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 4876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:6D4DE3C5917BAA7B9B0C272974B2FD4E | SHA256:EA295E017CCCD7A740EE9B7BFED3CC7C0FBBE82C991C26C051F8B3F549AB2F14 | |||
| 2500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2500.6604\QUOTATION#00913.exe | executable | |
MD5:35A3EA67F40367A4C8B136666CB048AC | SHA256:0538FB78E9459CA726B08C4DE952BCAD3E397C0C019318A52A7495E1C3E802F3 | |||
| 4876 | OUTLOOK.EXE | C:\USERS\ADMIN\APPDATA\ROAMING\MICROSOFT\OUTLOOK\OUTLOOK.SRS | binary | |
MD5:50CC0985482AAB14381ED441DA516762 | SHA256:CDA5B36A3A874195BD9DB4742DD917B95854926E042C77EAAC60FECC9F65654B | |||
| 2500 | WinRAR.exe | C:\Users\admin\AppData\Roaming\WinRAR\version.dat | binary | |
MD5:AB37DF48BDF29DD49200215B1662BB53 | SHA256:7B579D5A10D7F6E74AADE0319F13896DC97E20F54C73C0D76AD807B511146E4E | |||
| 4876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{9E0DE90A-4ED9-4FC8-8445-B31441FB599A}.tmp | binary | |
MD5:830FBF83999E052538EAF156AB6ECB17 | SHA256:D5098A2CEAE815DB29CD53C76F85240C95DC4D2E3FEDDD71D628617064C29869 | |||
| 4876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\4LK8LWEW\QUOTATION#00913 (002).gz | compressed | |
MD5:1F46757CFD9B2958DD614A0470DA5417 | SHA256:291E7CA64F60D55CF36C8B4A87090FCCE0388F3041317702F3411B81C867CADD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
17
DNS requests
15
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6092 | svchost.exe | GET | 206 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/78c34df8-0979-4065-b0a1-02478ab0702c?P1=1707508673&P2=404&P3=2&P4=aXTGA3%2fPYhWUShHMO2Cs1q1zD1krSxjcKsG2KJePAW3sWIWC4Q8iRvuyYsKJ6xYEs1%2bl72a31ISIaWy8VzseWQ%3d%3d | unknown | binary | 37.0 Kb | unknown |
6492 | msedge.exe | GET | 302 | 88.221.169.152:443 | https://go.microsoft.com/fwlink/?linkid=2133855&bucket=15 | unknown | — | — | unknown |
6092 | svchost.exe | GET | 206 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | binary | 1.09 Kb | unknown |
6092 | svchost.exe | HEAD | 200 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | — | — | unknown |
6092 | svchost.exe | GET | 206 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | binary | 3.95 Kb | unknown |
6092 | svchost.exe | GET | 206 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | binary | 1.01 Kb | unknown |
6464 | QUOTATION#00913.exe | GET | 200 | 188.114.97.3:80 | http://vitalikcreatedethereumtobethenewworldorderscurrency.shop/get/65bf1cc95973d6923329b22f | unknown | html | 1.12 Mb | unknown |
6092 | svchost.exe | GET | 206 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | binary | 6.37 Kb | unknown |
6092 | svchost.exe | GET | 206 | 104.103.72.50:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | binary | 9.81 Kb | unknown |
6492 | msedge.exe | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/111.0.1661.62?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig%2CEdgeDomainActions&osname=win&client=edge&channel=stable&scpfull=0&scpguard=0&scpfre=0&scpver=0&osarch=x86_64&osver=10.0.19044&wu=1&devicefamily=desktop&uma=0&sessionid=13&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245 | unknown | binary | 81.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4876 | OUTLOOK.EXE | 13.89.178.26:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6492 | msedge.exe | 2.19.230.153:443 | go.microsoft.com | AKAMAI-AS | FR | unknown |
6492 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
6092 | svchost.exe | 104.103.72.50:80 | msedge.b.tlu.dl.delivery.mp.microsoft.com | Akamai International B.V. | AT | unknown |
6464 | QUOTATION#00913.exe | 188.114.97.3:80 | vitalikcreatedethereumtobethenewworldorderscurrency.shop | CLOUDFLARENET | NL | unknown |
6448 | CasPol.exe | 64.185.227.156:443 | api.ipify.org | WEBNX | US | unknown |
6448 | CasPol.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
6448 | CasPol.exe | 192.254.225.136:21 | ftp.ercolina-usa.com | UNIFIEDLAYER-AS-1 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
self.events.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
vitalikcreatedethereumtobethenewworldorderscurrency.shop |
| unknown |
api.ipify.org |
| shared |
ip-api.com |
| shared |
ftp.ercolina-usa.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2136 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6448 | CasPol.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
6448 | CasPol.exe | Potential Corporate Privacy Violation | ET POLICY Possible IP Check api.ipify.org |
6448 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
6448 | CasPol.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6448 | CasPol.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2 ETPRO signatures available at the full report