| File name: | 3 |
| Full analysis: | https://app.any.run/tasks/53413081-098c-4d19-8ed7-50147714d6ba |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 15, 2019, 13:36:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
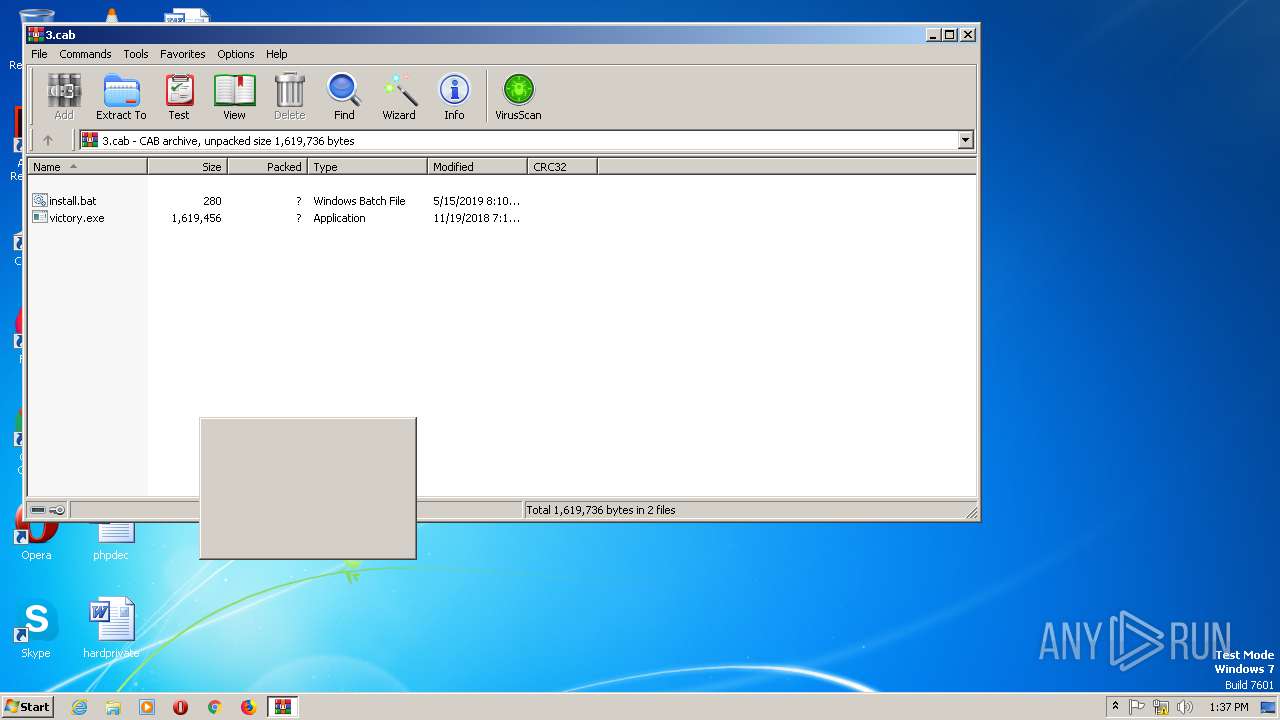
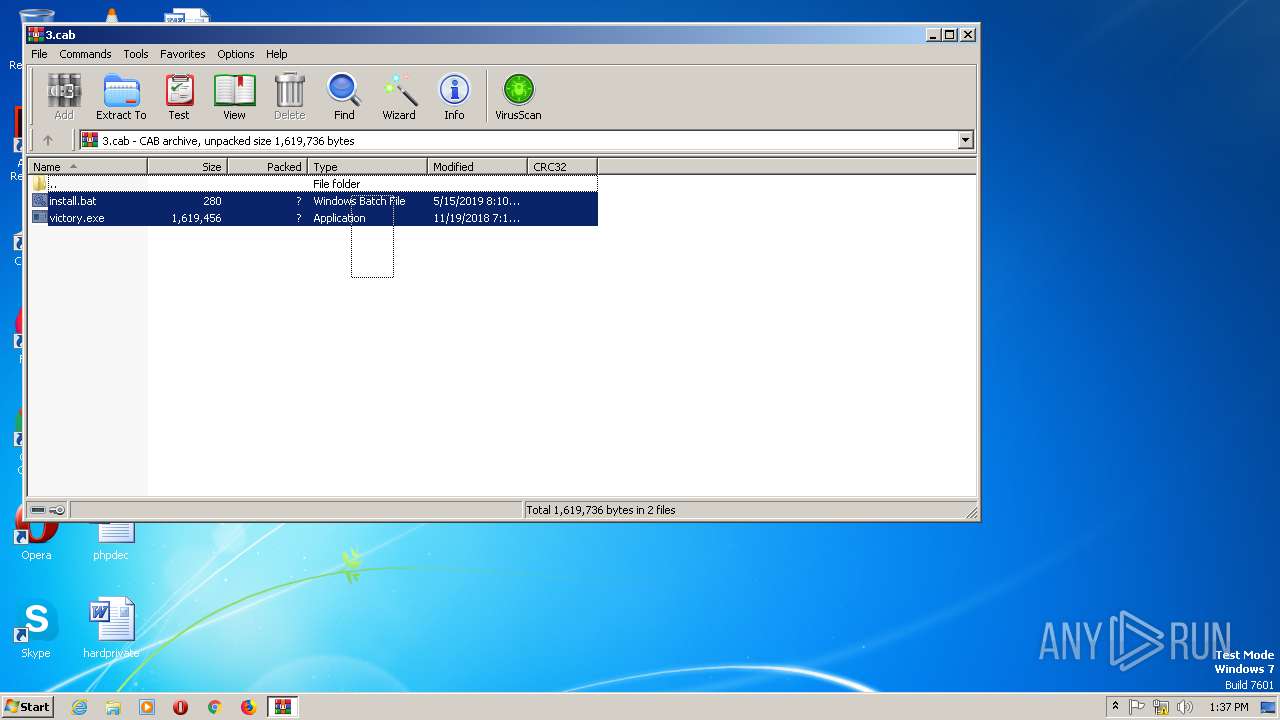
| File info: | Microsoft Cabinet archive data, 827079 bytes, 2 files |
| MD5: | 0CAA12C4EA3BF9802337985740021038 |
| SHA1: | 9DB0DC442CD268BF14ACEDBD86BEE9AA7F3A0699 |
| SHA256: | 4472D902F9EFA717E2AC112D7FF039DC027E59872B4A26F9041D2A56CB7CB98C |
| SSDEEP: | 12288:XPt5cjD6hGi780IiO0FG6aoa8LmNl70V29rF8+TrqJ8VHFTsls9+y444Ek+WU:XPtfTNOQG6aLFJ9+KqIFn9+b7U |
MALICIOUS
Application was dropped or rewritten from another process
- victory.exe (PID: 2864)
- victory.exe (PID: 2352)
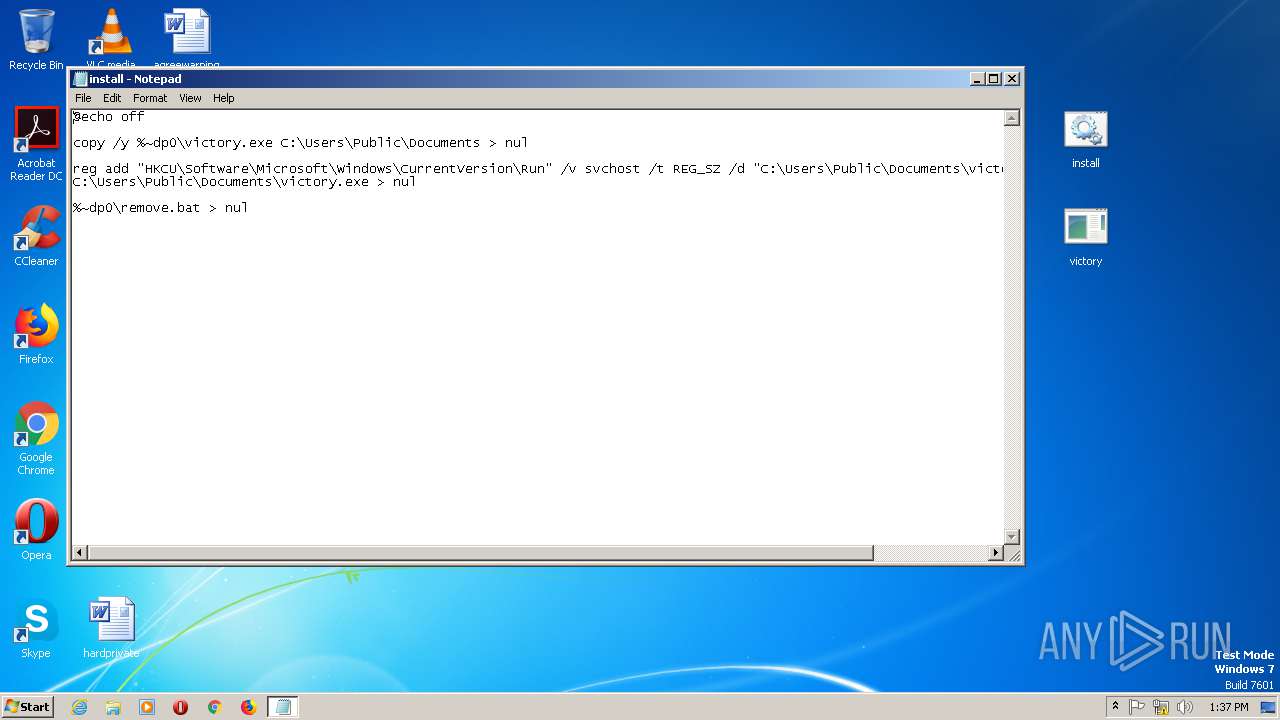
Changes the autorun value in the registry
- reg.exe (PID: 2824)
AMADEY was detected
- victory.exe (PID: 2352)
Connects to CnC server
- victory.exe (PID: 2352)
SUSPICIOUS
Reads the machine GUID from the registry
- WinRAR.exe (PID: 2912)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2060)
Executable content was dropped or overwritten
- cmd.exe (PID: 2060)
Application launched itself
- victory.exe (PID: 2864)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
38
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2060 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\install.bat" " | C:\Windows\system32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2240 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\install.bat | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2352 | "C:\Users\Public\Documents\victory.exe" | C:\Users\Public\Documents\victory.exe | victory.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2824 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v svchost /t REG_SZ /d "C:\Users\Public\Documents\victory.exe" /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2864 | C:\Users\Public\Documents\victory.exe | C:\Users\Public\Documents\victory.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2912 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\3.cab" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
394
Read events
355
Write events
39
Delete events
0
Modification events
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\65\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\3.cab | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\65\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1600000016000000D60300000B020000 | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2912.45169\install.bat | — | |
MD5:— | SHA256:— | |||
| 2912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2912.45169\victory.exe | — | |
MD5:— | SHA256:— | |||
| 2864 | victory.exe | C:\Users\admin\AppData\Local\Temp\Liebert.bmp | — | |
MD5:— | SHA256:— | |||
| 2060 | cmd.exe | C:\Users\Public\Documents\victory.exe | executable | |
MD5:— | SHA256:— | |||
| 2352 | victory.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\K78MRVB5\suspendedpage[1].htm | html | |
MD5:— | SHA256:— | |||
| 2352 | victory.exe | C:\Users\admin\AppData\Local\Temp\sp.exe | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
4
DNS requests
2
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2352 | victory.exe | GET | 200 | 188.241.39.220:80 | http://fighiting1013.org/cgi-sys/suspendedpage.cgi | GB | html | 4.01 Kb | malicious |
2352 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | — | — | malicious |
2352 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 50 b | malicious |
2352 | victory.exe | GET | 302 | 188.241.39.220:80 | http://fighiting1013.org/2/sp.exe | GB | html | 593 b | malicious |
2352 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 6 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2352 | victory.exe | 104.243.41.186:80 | charley-online.com | Choopa, LLC | US | suspicious |
2352 | victory.exe | 188.241.39.220:80 | fighiting1013.org | Hydra Communications Ltd | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
charley-online.com |
| malicious |
fighiting1013.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2352 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2352 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2352 | victory.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
2352 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2352 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2 ETPRO signatures available at the full report