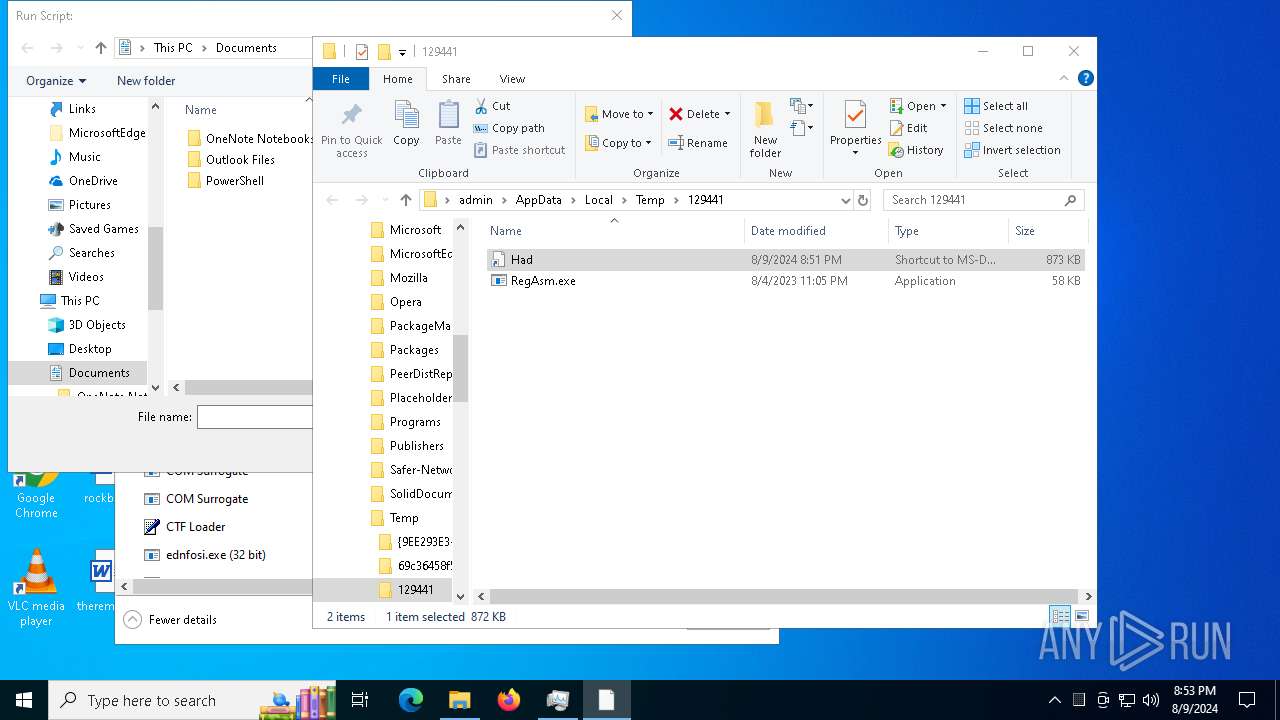
| File name: | SmLAztxc1o8yfogkJXrRjbDt.exe |
| Full analysis: | https://app.any.run/tasks/40ab98fa-2b87-4a82-88e7-39e7c96ab332 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 09, 2024, 20:50:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A386741A24F6DD80F0A87A8AF51C37C7 |
| SHA1: | 51DD4F9A6BA686E40123E6200B292534FE15B529 |
| SHA256: | 4410E6509EF90E0B6D680E04C05552C0CF8729C40D3CBB6FFD39126D022D3A11 |
| SSDEEP: | 98304:QStEC335r1M0pqbp1q4JPvgKeqp6IcloFwG1hKL6SPSTcm1qbUOOYo4OHppFKU3/:L3DD3bXnhWpcC8 |
MALICIOUS
AMADEY has been detected (SURICATA)
- ednfosi.exe (PID: 6488)
Connects to the CnC server
- ednfosi.exe (PID: 6488)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 6896)
- findstr.exe (PID: 7012)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6212)
- cmd.exe (PID: 3176)
Create files in the Startup directory
- cmd.exe (PID: 2852)
- cmd.exe (PID: 3032)
- InstallUtil.exe (PID: 7220)
AMADEY has been detected (YARA)
- ednfosi.exe (PID: 6488)
DARKTORTILLA has been detected (YARA)
- VLC3.exe (PID: 752)
Actions looks like stealing of personal data
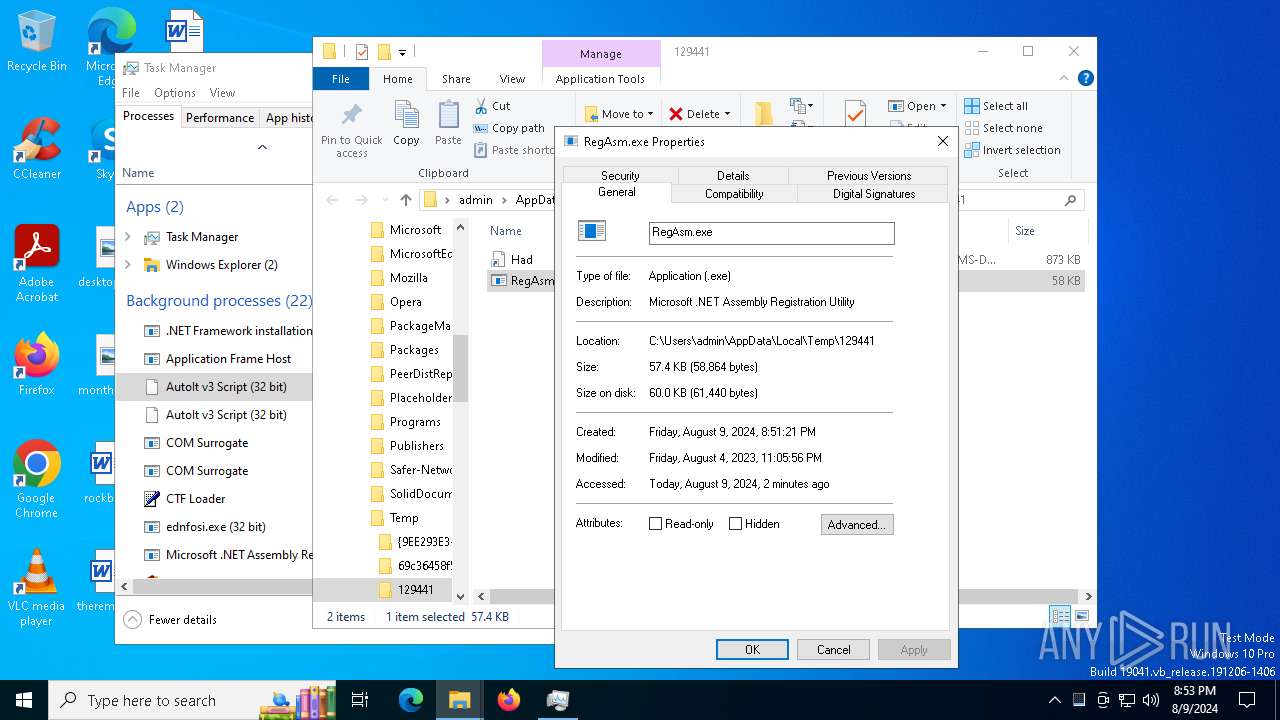
- RegAsm.exe (PID: 7536)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
ASYNCRAT has been detected (SURICATA)
- RegAsm.exe (PID: 7536)
PURECRYPTER has been detected (SURICATA)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
PUREHVNC has been detected (YARA)
- RegAsm.exe (PID: 7536)
Stealers network behavior
- RegAsm.exe (PID: 7916)
PURELOGS has been detected (SURICATA)
- RegAsm.exe (PID: 7916)
Scans artifacts that could help determine the target
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 8000)
SUSPICIOUS
Executable content was dropped or overwritten
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- cmd.exe (PID: 6772)
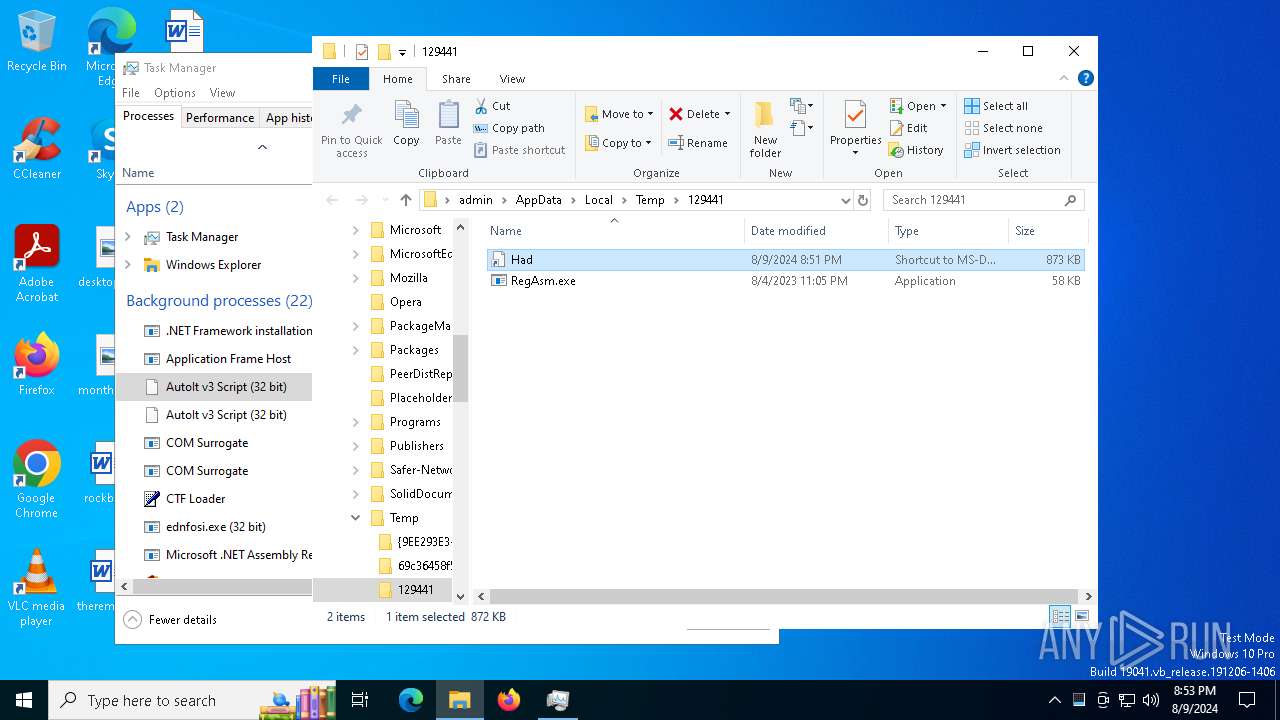
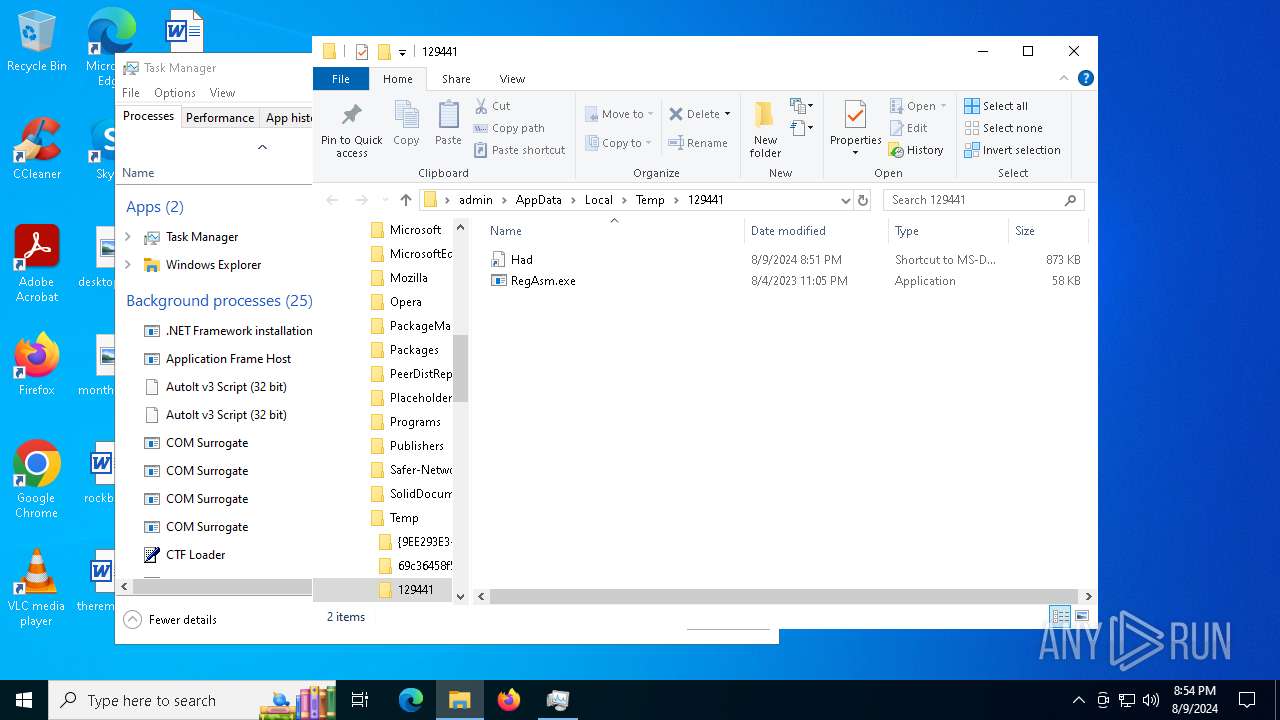
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
Drops the executable file immediately after the start
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- ReadilyAccompanied.exe (PID: 6732)
- cmd.exe (PID: 6772)
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
Checks Windows Trust Settings
- ednfosi.exe (PID: 6488)
Reads security settings of Internet Explorer
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- ReadilyAccompanied.exe (PID: 6732)
- InstallUtil.exe (PID: 7220)
- Had.pif (PID: 6276)
Reads the date of Windows installation
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- ReadilyAccompanied.exe (PID: 6732)
- InstallUtil.exe (PID: 7220)
Starts itself from another location
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
The process executes via Task Scheduler
- ednfosi.exe (PID: 6576)
- ednfosi.exe (PID: 7012)
- ednfosi.exe (PID: 4772)
- ednfosi.exe (PID: 6788)
- ednfosi.exe (PID: 6388)
Contacting a server suspected of hosting an CnC
- ednfosi.exe (PID: 6488)
- RegAsm.exe (PID: 7536)
Executing commands from ".cmd" file
- ReadilyAccompanied.exe (PID: 6732)
Get information on the list of running processes
- cmd.exe (PID: 6772)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6772)
Application launched itself
- cmd.exe (PID: 6772)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6772)
- ReadilyAccompanied.exe (PID: 6732)
- explorer.exe (PID: 4552)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 6772)
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
The executable file from the user directory is run by the CMD process
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
Starts application with an unusual extension
- cmd.exe (PID: 6772)
- explorer.exe (PID: 4552)
The process creates files with name similar to system file names
- Had.pif (PID: 7124)
Process drops legitimate windows executable
- Had.pif (PID: 7124)
Connects to unusual port
- RegAsm.exe (PID: 7536)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
Starts a Microsoft application from unusual location
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 7536)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
INFO
Checks supported languages
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- ednfosi.exe (PID: 6576)
- ReadilyAccompanied.exe (PID: 6732)
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
- VLC3.exe (PID: 752)
- RegAsm.exe (PID: 7536)
- InstallUtil.exe (PID: 7220)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- ednfosi.exe (PID: 4772)
- Had.pif (PID: 6276)
- ednfosi.exe (PID: 7012)
- RegAsm.exe (PID: 8000)
- ednfosi.exe (PID: 6788)
- ednfosi.exe (PID: 6388)
- RegAsm.exe (PID: 1964)
Process checks computer location settings
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- ReadilyAccompanied.exe (PID: 6732)
- InstallUtil.exe (PID: 7220)
Reads the computer name
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ReadilyAccompanied.exe (PID: 6732)
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
- VLC3.exe (PID: 752)
- RegAsm.exe (PID: 7536)
- ednfosi.exe (PID: 6488)
- InstallUtil.exe (PID: 7220)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- Had.pif (PID: 6276)
- RegAsm.exe (PID: 1964)
Create files in a temporary directory
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- ReadilyAccompanied.exe (PID: 6732)
- Had.pif (PID: 7124)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
Reads Environment values
- SmLAztxc1o8yfogkJXrRjbDt.exe (PID: 6432)
- ednfosi.exe (PID: 6488)
- RegAsm.exe (PID: 7536)
- InstallUtil.exe (PID: 7220)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
Checks proxy server information
- ednfosi.exe (PID: 6488)
- InstallUtil.exe (PID: 7220)
- explorer.exe (PID: 4552)
Reads the software policy settings
- ednfosi.exe (PID: 6488)
- RegAsm.exe (PID: 7536)
- InstallUtil.exe (PID: 7220)
- explorer.exe (PID: 4552)
Reads mouse settings
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
- Had.pif (PID: 6276)
Creates files or folders in the user directory
- Had.pif (PID: 7124)
- Had.pif (PID: 7164)
- explorer.exe (PID: 4552)
- ednfosi.exe (PID: 6488)
- InstallUtil.exe (PID: 7220)
Manual execution by a user
- cmd.exe (PID: 2852)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 6212)
- cmd.exe (PID: 3032)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 7536)
- RegAsm.exe (PID: 2272)
- Taskmgr.exe (PID: 2572)
- Taskmgr.exe (PID: 4280)
Reads the machine GUID from the registry
- VLC3.exe (PID: 752)
- RegAsm.exe (PID: 7536)
- InstallUtil.exe (PID: 7220)
- ednfosi.exe (PID: 6488)
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
Disables trace logs
- InstallUtil.exe (PID: 7220)
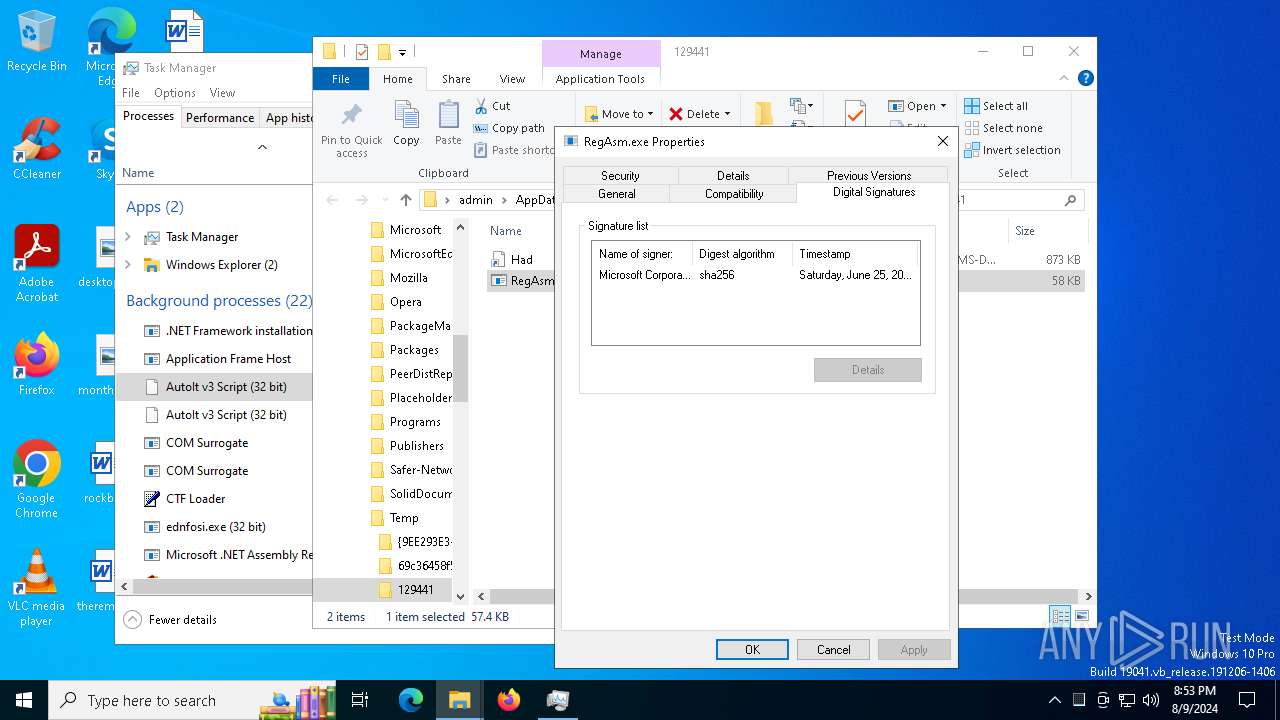
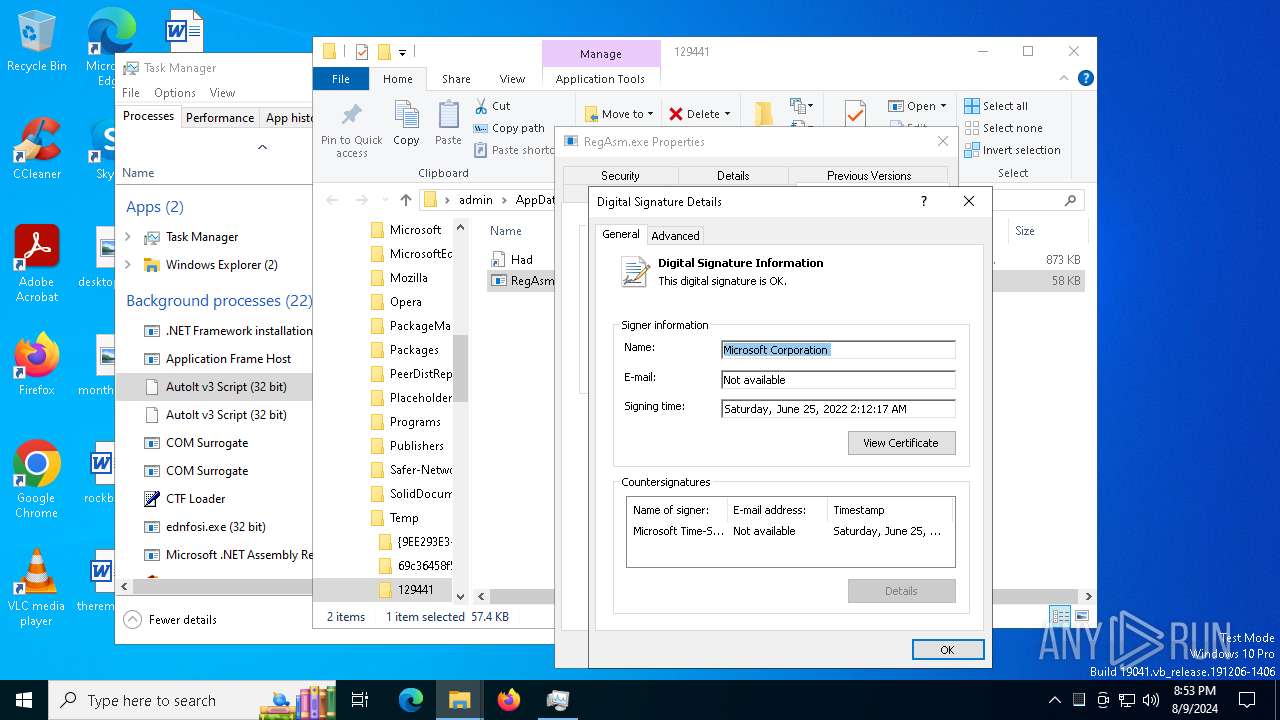
.NET Reactor protector has been detected
- RegAsm.exe (PID: 7536)
- RegAsm.exe (PID: 2272)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 1964)
Reads Microsoft Office registry keys
- RegAsm.exe (PID: 7916)
- RegAsm.exe (PID: 2272)
- explorer.exe (PID: 4552)
- RegAsm.exe (PID: 8000)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 2572)
- explorer.exe (PID: 4552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(6488) ednfosi.exe
C2api.garageserviceoperation.com
URLhttp://api.garageserviceoperation.com/CoreOPT/index.php
Version4.41
Options
Drop directory69c36458f5
Drop nameednfosi.exe
Strings (119)AVG
69c36458f5
\App
0123456789
SOFTWARE\Microsoft\Windows NT\CurrentVersion
os:
r=
zip
cmd /C RMDIR /s/q
/CoreOPT/index.php
Bitdefender
dm:
360TotalSecurity
-executionpolicy remotesigned -File "
.jpg
S-%lu-
POST
ESET
abcdefghijklmnopqrstuvwxyz0123456789-_
&&
2022
shutdown -s -t 0
/Plugins/
Content-Disposition: form-data; name="data"; filename="
un:
--
/quiet
ProductName
Comodo
cmd
Kaspersky Lab
"taskkill /f /im "
+++
|
:::
e1
"
random
GET
bi:
=
wb
"
Content-Type: application/octet-stream
-%lu
2019
kernel32.dll
\0000
pc:
shell32.dll
Startup
ComputerName
av:
ar:
lv:
DefaultSettings.XResolution
Avira
&unit=
AVAST Software
%USERPROFILE%
exe
-unicode-
2016
e0
id:
DefaultSettings.YResolution
vs:
%-lu
/k
Powershell.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
#
rundll32.exe
Sophos
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
CurrentBuild
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
<d>
https://
Content-Type: application/x-www-form-urlencoded
VideoID
d1
Main
cred.dll
rb
Doctor Web
4.41
http://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ProgramData\
msi
Norton
&& Exit"
cred.dll|clip.dll|
Panda Security
\
og:
" && ren
GetNativeSystemInfo
rundll32
api.garageserviceoperation.com
st=s
e2
<c>
Programs
Content-Type: multipart/form-data; boundary=----
Rem
?scr=1
sd:
------
------
SYSTEM\ControlSet001\Services\BasicDisplay\Video
dll
clip.dll
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
" && timeout 1 && del
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ednfosi.exe
ps1
WinDefender
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:08:07 12:47:37+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 321024 |
| InitializedDataSize: | 117248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x60e275 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
181
Monitored processes
43
Malicious processes
11
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Users\admin\AppData\Local\Temp\1000056001\VLC3.exe" | C:\Users\admin\AppData\Local\Temp\1000056001\VLC3.exe | ednfosi.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1860 | schtasks.exe /create /tn "Dpi" /tr "wscript //B 'C:\Users\admin\AppData\Local\DataSynergy Technologies LLC\VirtuoSync.js'" /sc minute /mo 5 /F | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | C:\Users\admin\AppData\Local\Temp\129441\RegAsm.exe | C:\Users\admin\AppData\Local\Temp\129441\RegAsm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2272 | C:\Users\admin\AppData\Local\Temp\129441\RegAsm.exe | C:\Users\admin\AppData\Local\Temp\129441\RegAsm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | cmd /k echo [InternetShortcut] > "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VirtuoSync.url" & echo URL="C:\Users\admin\AppData\Local\DataSynergy Technologies LLC\VirtuoSync.js" >> "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VirtuoSync.url" & exit | C:\Windows\SysWOW64\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | cmd /k echo [InternetShortcut] > "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VirtuoSync11.url" & echo URL="C:\Users\admin\AppData\Local\DataSynergy Technologies LLC11\VirtuoSync.js" >> "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VirtuoSync11.url" & exit | C:\Windows\SysWOW64\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
79 675
Read events
79 504
Write events
165
Delete events
6
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (6432) SmLAztxc1o8yfogkJXrRjbDt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6432) SmLAztxc1o8yfogkJXrRjbDt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6432) SmLAztxc1o8yfogkJXrRjbDt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6432) SmLAztxc1o8yfogkJXrRjbDt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6488) ednfosi.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6488) ednfosi.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6488) ednfosi.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6488) ednfosi.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6488) ednfosi.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
10
Suspicious files
110
Text files
10
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4552 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6488 | ednfosi.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:51883DF11BA0F75D2AAD9E88EBD057DC | SHA256:1CC443E507D740FEDC646DCA7116EEAD8084ED9B7C70ABBB34281DD1E7DBBA10 | |||
| 6432 | SmLAztxc1o8yfogkJXrRjbDt.exe | C:\Windows\Tasks\ednfosi.job | binary | |
MD5:5F1BBF4E57D4FF6C7E3E9703032402C7 | SHA256:E7B0818628DBBDB6359A4F281D55D9BE43662E4D2DC6C61A3A21B7339F51185C | |||
| 6488 | ednfosi.exe | C:\Users\admin\AppData\Local\Temp\1000055001\ReadilyAccompanied.exe | executable | |
MD5:9C557C498C29E5D37016400CF0899AC6 | SHA256:DCE64DE620B212280D3C6AE529C51A9CE4DEE56588B30899AB22ECF6C1474F4A | |||
| 6488 | ednfosi.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C351DA027D36327B234E51E60978368C | binary | |
MD5:F7FEFD8E0FB4057013D4D3E20E625220 | SHA256:B466721C480D9897453694DC44928836CBD8E3D1531B5B273DBDFB755F94C787 | |||
| 6488 | ednfosi.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C351DA027D36327B234E51E60978368C | der | |
MD5:8C03FCA02E2FC8BAE9E29AEABDEEA7C9 | SHA256:997E8D08195D42BA0BED2162A93E16D7FD42E5A47D44D3334D485EFDA001A124 | |||
| 6488 | ednfosi.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:C230AEA800CBDA62DF63052973D78649 | SHA256:5DDF1CB320A0C45491F91E5FD4866E8E91AA60DF9C60873F9C9DD86ADDFDC145 | |||
| 6488 | ednfosi.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\ReadilyAccompanied[1].exe | executable | |
MD5:9C557C498C29E5D37016400CF0899AC6 | SHA256:DCE64DE620B212280D3C6AE529C51A9CE4DEE56588B30899AB22ECF6C1474F4A | |||
| 6732 | ReadilyAccompanied.exe | C:\Users\admin\AppData\Local\Temp\Nest | binary | |
MD5:6CBEAA318088F9F592B54554973D9C34 | SHA256:3B4708043D7618CFDA75FD75B75757DA43189B057F944E1A2965349EE073BA25 | |||
| 6732 | ReadilyAccompanied.exe | C:\Users\admin\AppData\Local\Temp\Vocals | binary | |
MD5:A1B4F39A0003231772886911B191C2D4 | SHA256:F6996FB2F118F3F3C2EE2C2FF36CF93A2E3E63A5A860D0DE11C1DCE37EB198C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
67
DNS requests
32
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6488 | ednfosi.exe | POST | 200 | 185.208.158.115:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
6488 | ednfosi.exe | POST | 200 | 185.208.158.115:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
— | — | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
6488 | ednfosi.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQChefxDqizHp%2BUDESVkPX%2B3 | unknown | — | — | whitelisted |
6488 | ednfosi.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
6488 | ednfosi.exe | POST | 200 | 185.208.158.115:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
6488 | ednfosi.exe | POST | 200 | 185.208.158.115:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4168 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6180 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4484 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1184 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6488 | ednfosi.exe | 185.208.158.115:80 | api.garageserviceoperation.com | — | US | unknown |
6488 | ednfosi.exe | 162.0.209.124:443 | helleaa.com | NAMECHEAP-NET | US | unknown |
6488 | ednfosi.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
6488 | ednfosi.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.garageserviceoperation.com |
| malicious |
helleaa.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
fTklZVzzlysZHeldfzSjVCiKTVtL.fTklZVzzlysZHeldfzSjVCiKTVtL |
| unknown |
umGPgIUKlmbxKNhoefdnUvgjrV.umGPgIUKlmbxKNhoefdnUvgjrV |
| unknown |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6488 | ednfosi.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
6488 | ednfosi.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6488 | ednfosi.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M2 |
6488 | ednfosi.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M2 |
7536 | RegAsm.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 25 |
7536 | RegAsm.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
7916 | RegAsm.exe | A Network Trojan was detected | LOADER [ANY.RUN] PureLogs Download Attempt (LOAD) |
7536 | RegAsm.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
2272 | RegAsm.exe | A Network Trojan was detected | LOADER [ANY.RUN] PureLogs Download Attempt (LOAD) |
2 ETPRO signatures available at the full report