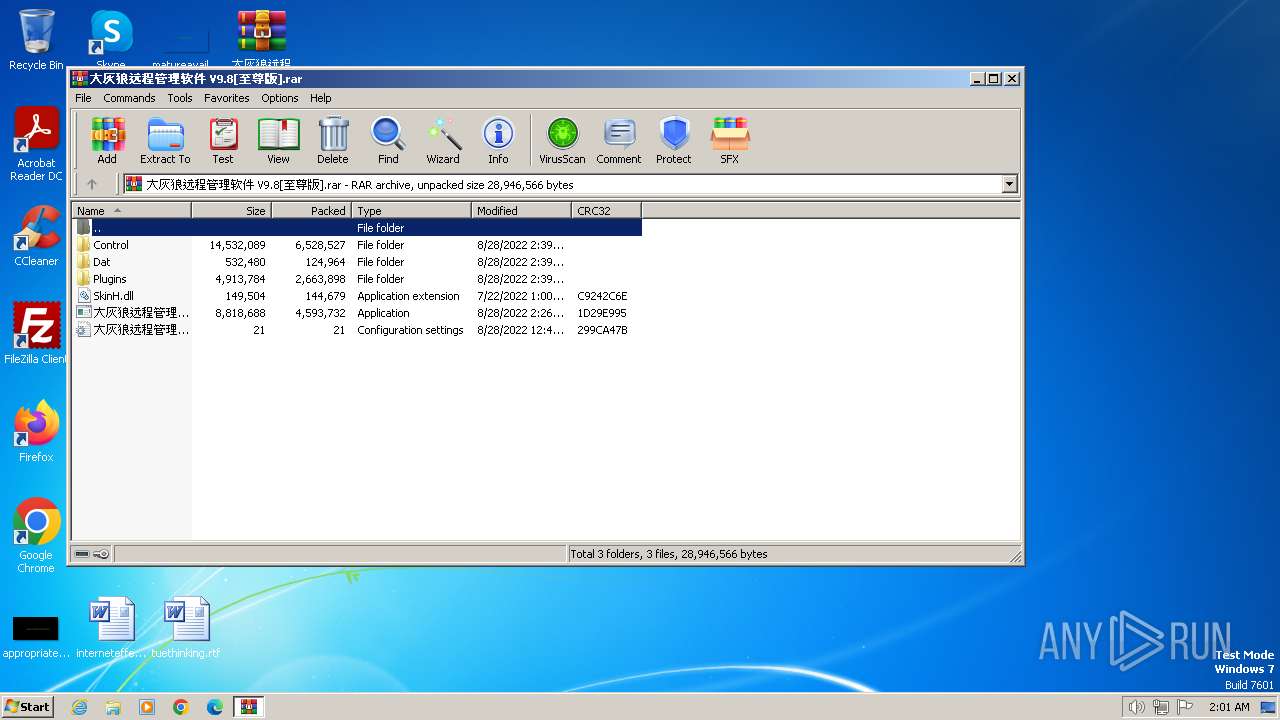
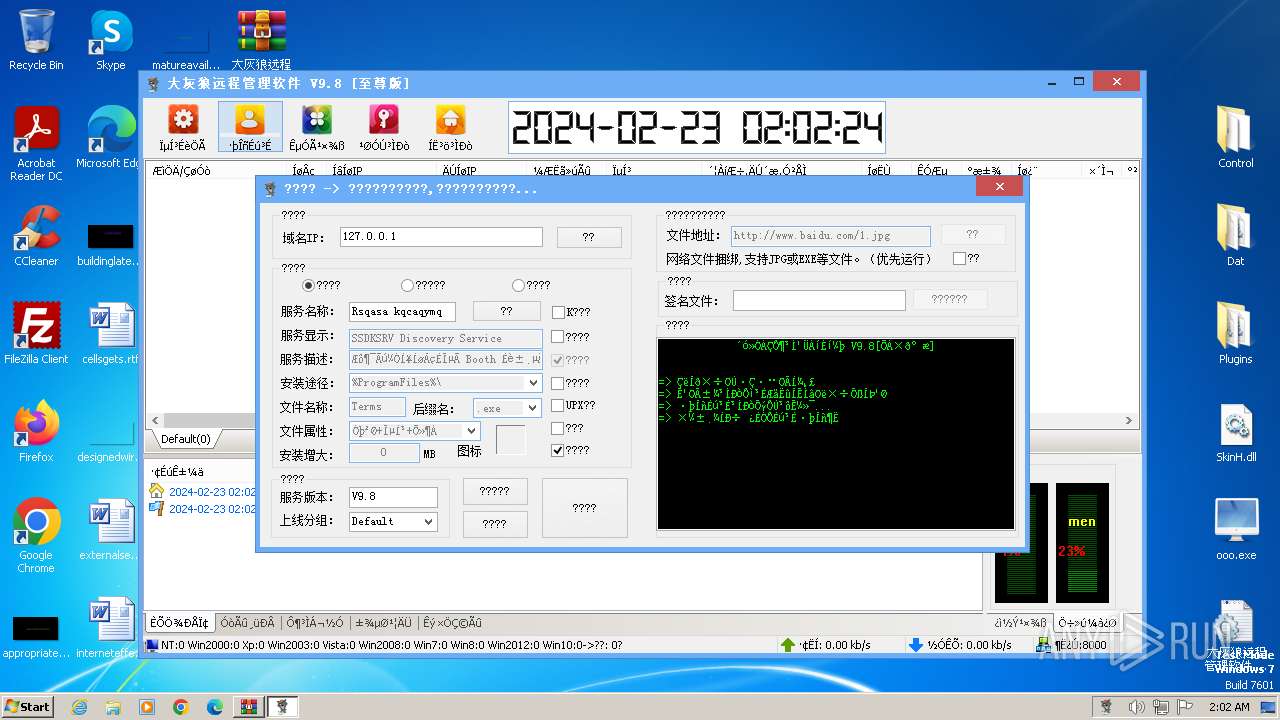
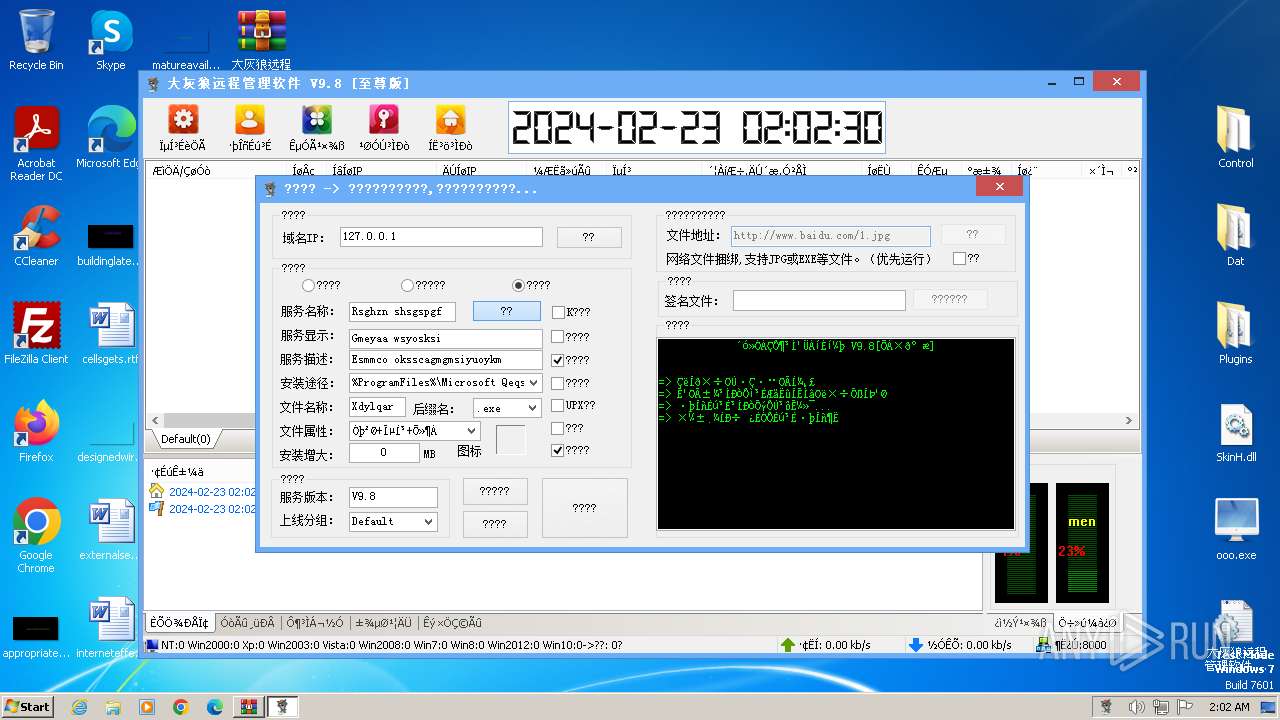
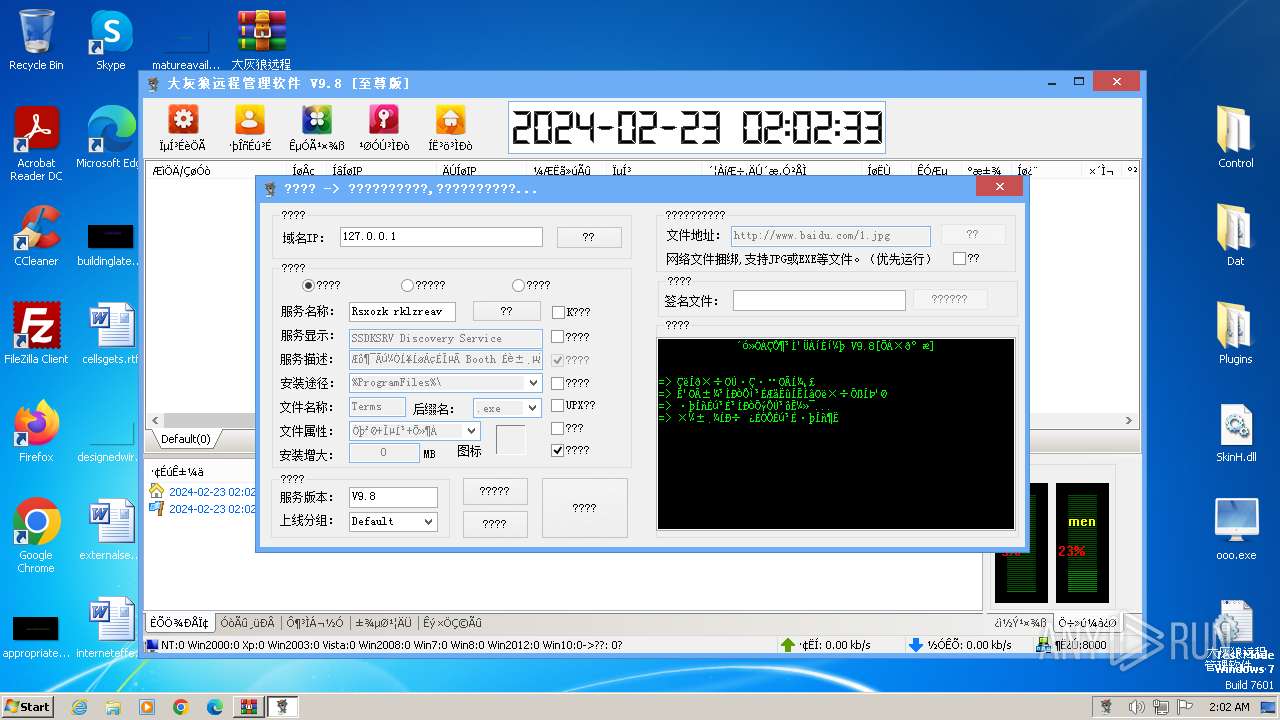
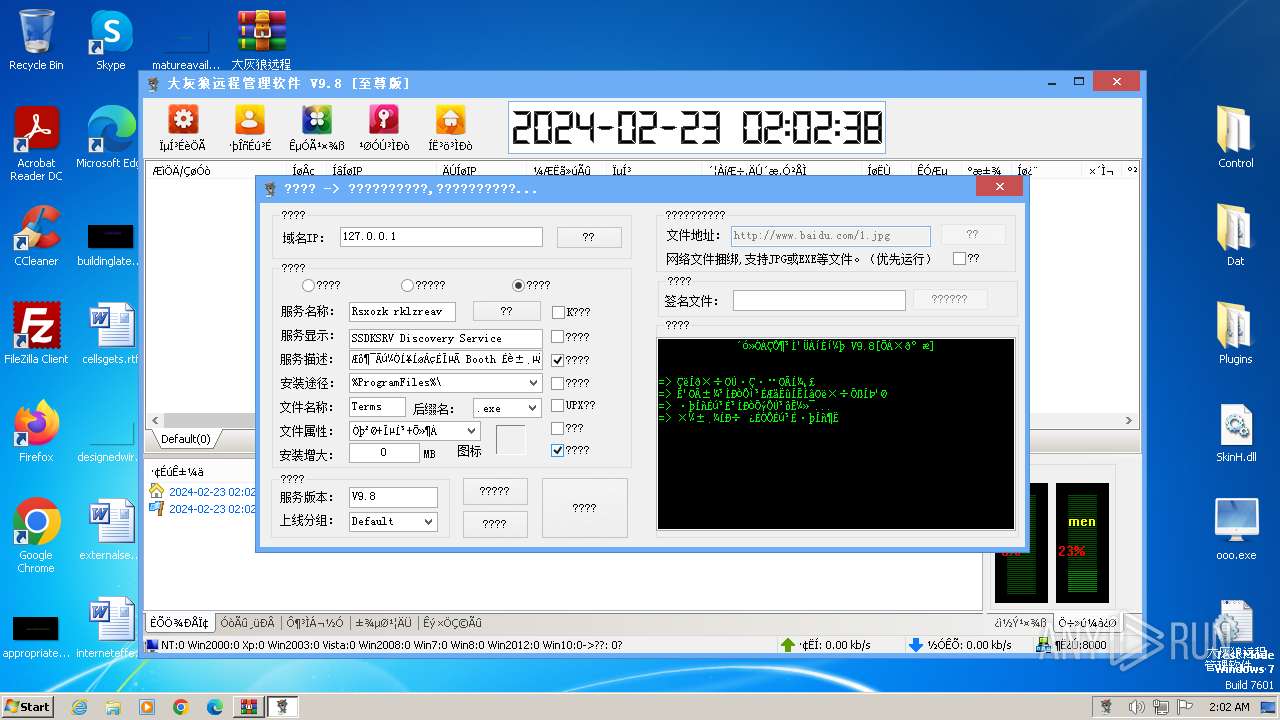
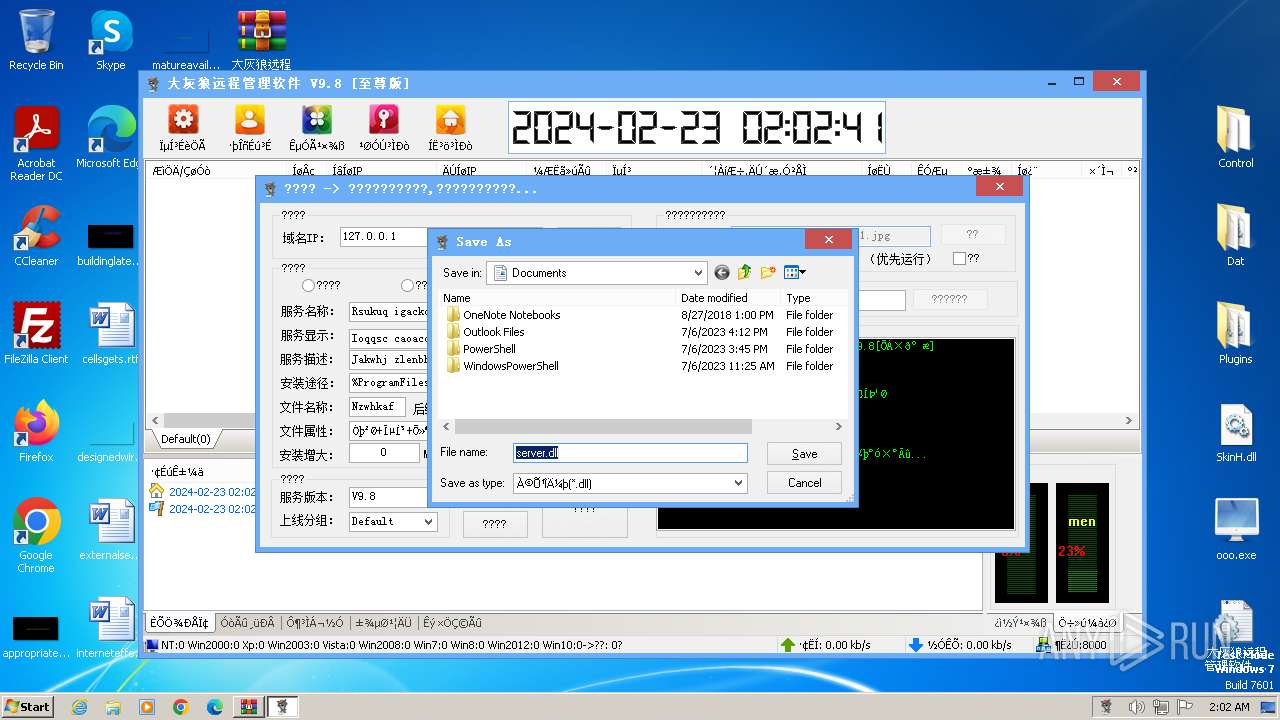
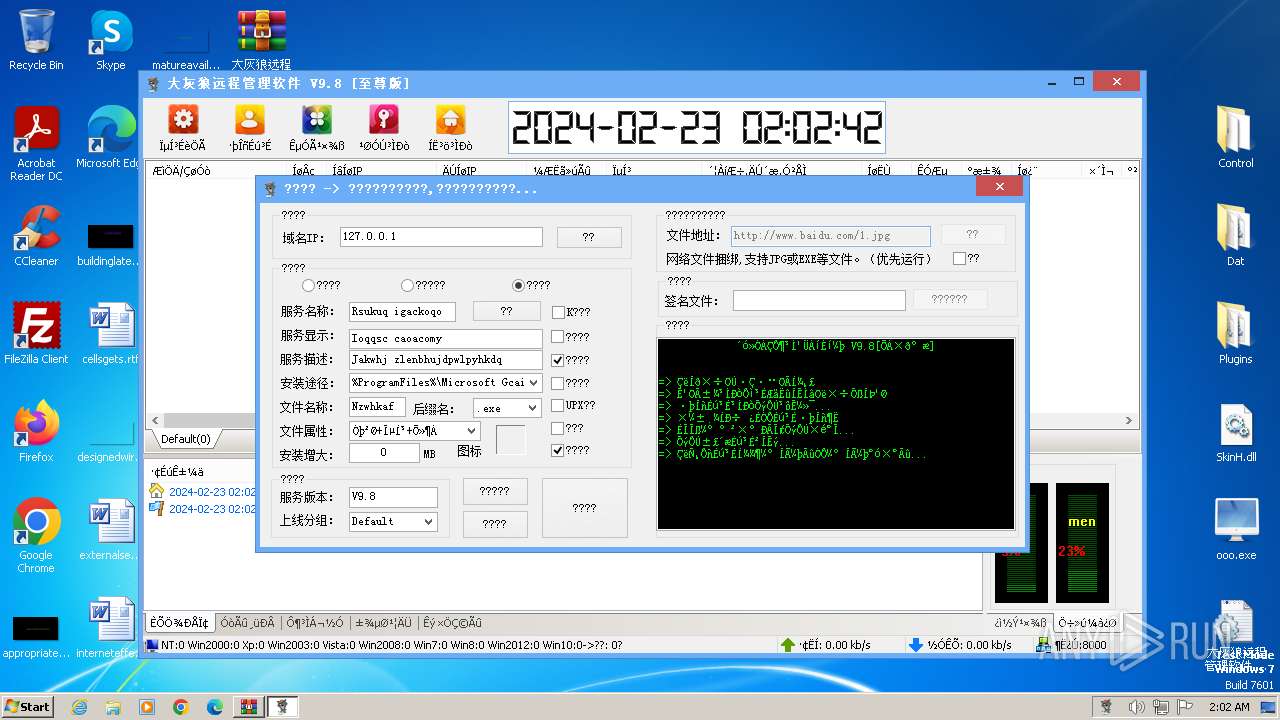
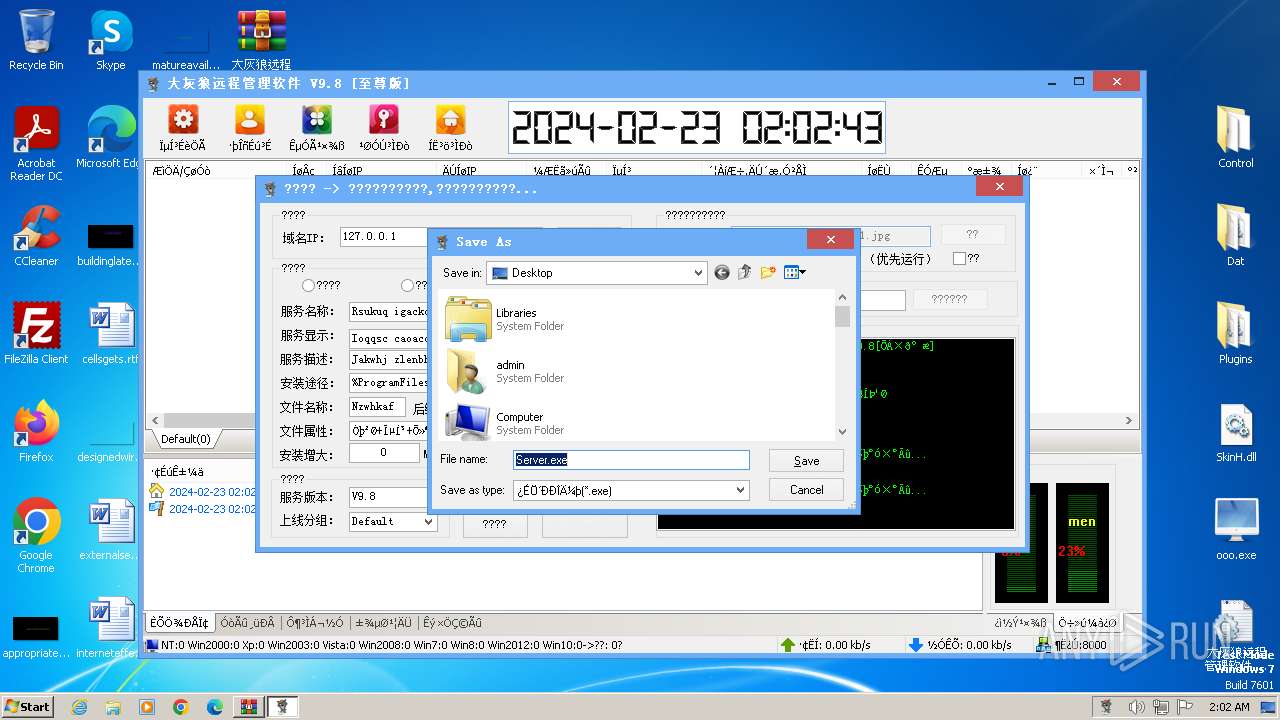
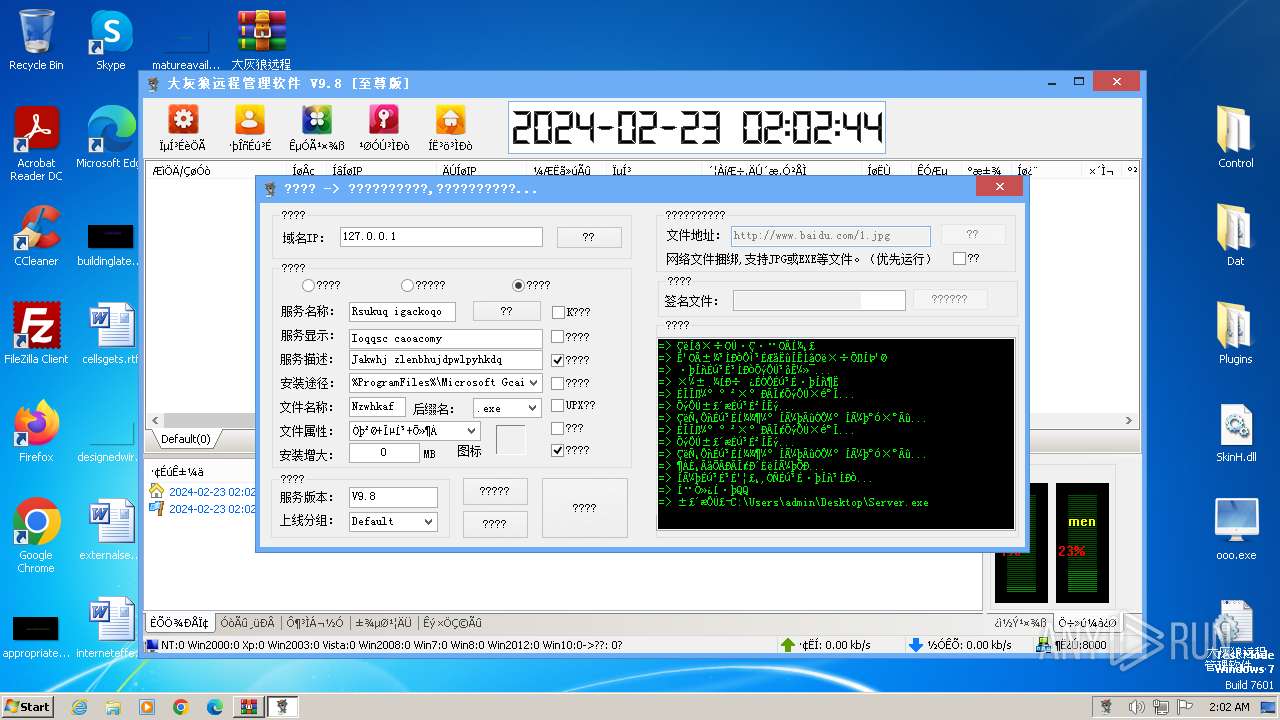
| File name: | 大灰狼远程管理软件 V9.8[至尊版].rar |
| Full analysis: | https://app.any.run/tasks/737894fe-70d0-401b-8a78-f84936372b04 |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | February 23, 2024, 02:01:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DABC8A095DB954B67EA981847FAD67B4 |
| SHA1: | 199158B063F3BD47DB61CEB2067C614676A1A3AF |
| SHA256: | 43DCAAE265A607F71A7E5D4239DEA7FBB8E92BE400919D474F30B58770DCE84B |
| SSDEEP: | 98304:3lwfqMzbrY7zFGp4ShJM7wFfU6oMjl+BwoH8rLc8KDei+ffwH/gNtGVKvVlS/V6z:hLSaIF6U2Uj+d57oH7g+8Xjmv7i0D7 |
MALICIOUS
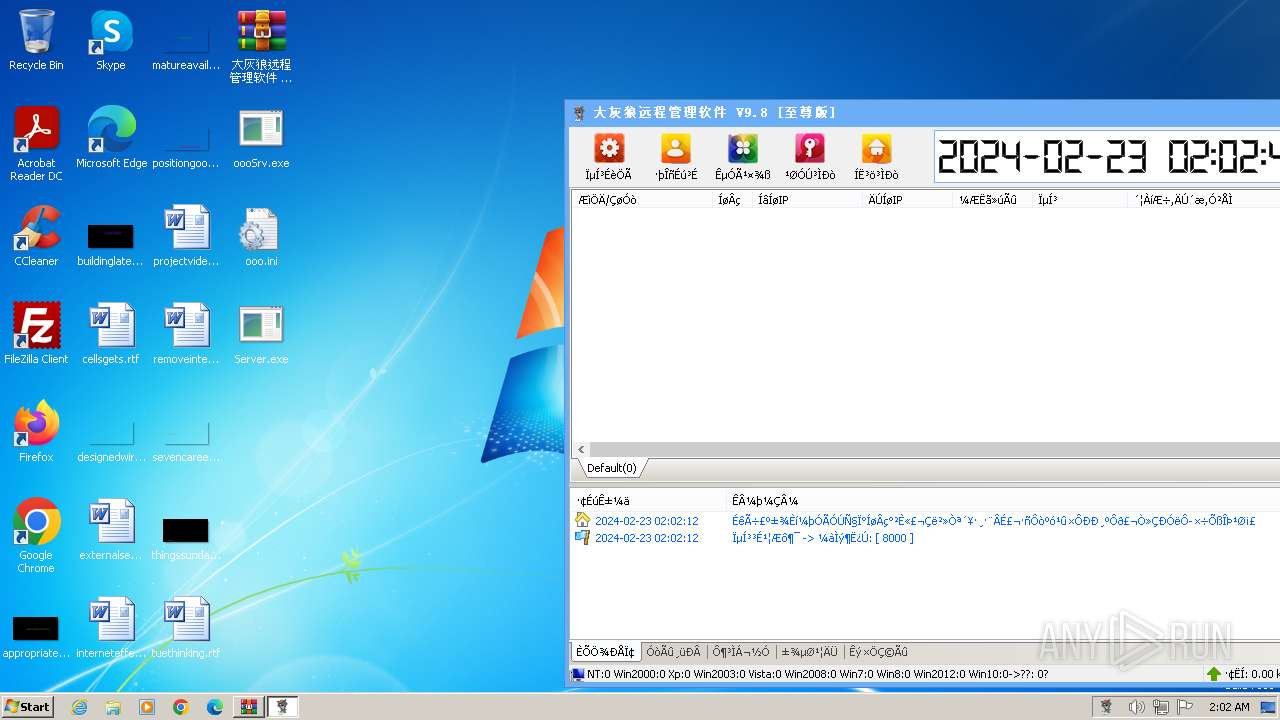
Drops the executable file immediately after the start
- oooSrv.exe (PID: 2580)
- WinRAR.exe (PID: 2044)
- ooo.exe (PID: 1696)
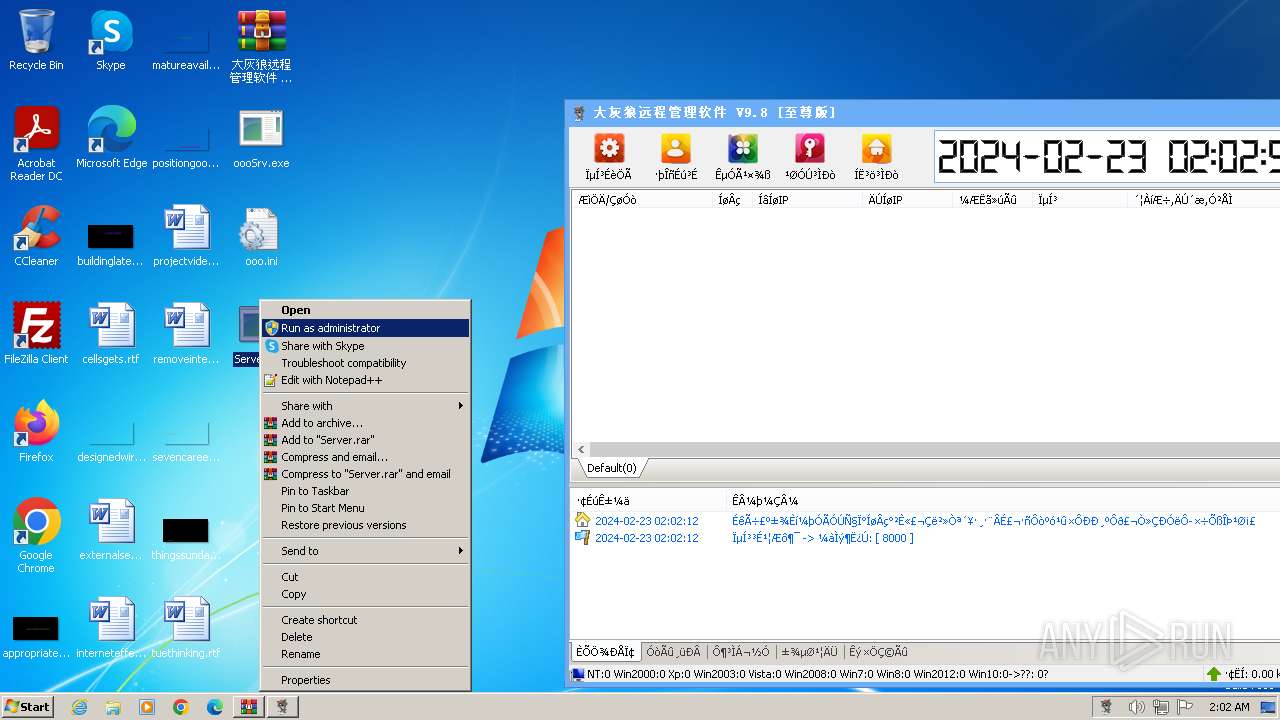
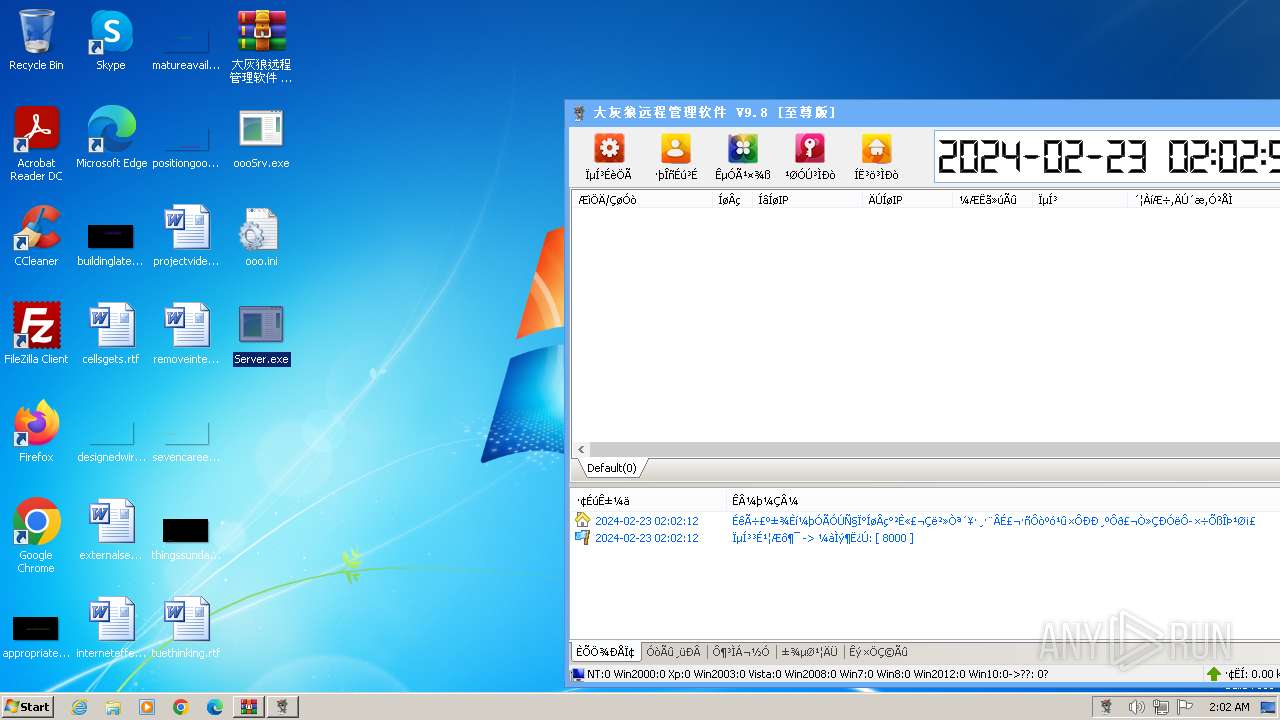
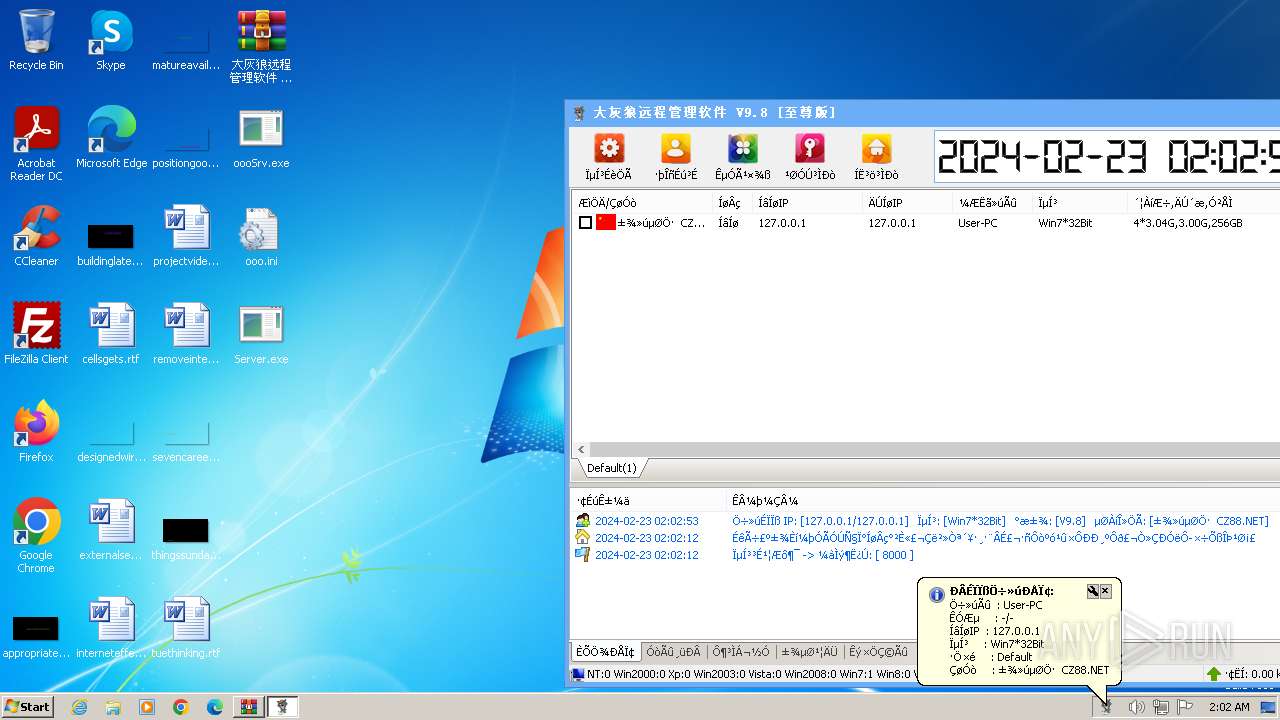
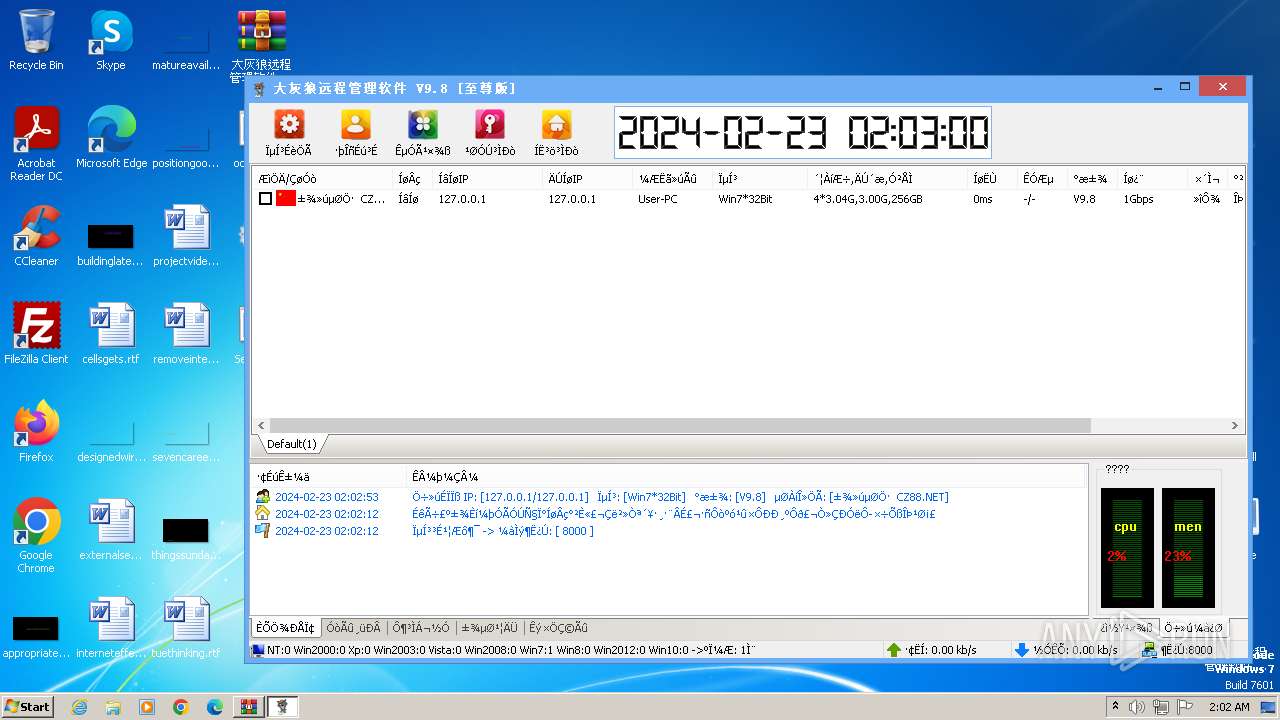
- Server.exe (PID: 3540)
- Nzwhkaf.exe (PID: 492)
Signature: RAMNIT has been detected
- DesktopLayer.exe (PID: 2860)
- iexplore.exe (PID: 3092)
- ooo.exe (PID: 1696)
- oooSrv.exe (PID: 2580)
- Server.exe (PID: 3540)
- Nzwhkaf.exe (PID: 492)
- NzwhkafSrv.exe (PID: 2576)
- iexplore.exe (PID: 1848)
- Nzwhkaf.exe (PID: 1624)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 3092)
- iexplore.exe (PID: 1848)
RAMNIT has been detected (SURICATA)
- iexplore.exe (PID: 3092)
- iexplore.exe (PID: 1848)
Connects to the CnC server
- iexplore.exe (PID: 3092)
- iexplore.exe (PID: 1848)
NITOL has been detected (YARA)
- Server.exe (PID: 3540)
SUSPICIOUS
Executable content was dropped or overwritten
- ooo.exe (PID: 1696)
- oooSrv.exe (PID: 2580)
- Server.exe (PID: 3540)
- Nzwhkaf.exe (PID: 492)
Starts itself from another location
- oooSrv.exe (PID: 2580)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2044)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 2044)
Reads the Internet Settings
- ooo.exe (PID: 1696)
Reads security settings of Internet Explorer
- ooo.exe (PID: 1696)
Process requests binary or script from the Internet
- ooo.exe (PID: 1696)
Checks for external IP
- ooo.exe (PID: 1696)
Executes as Windows Service
- Nzwhkaf.exe (PID: 492)
Creates or modifies Windows services
- Server.exe (PID: 3540)
Application launched itself
- Nzwhkaf.exe (PID: 492)
Connects to unusual port
- Server.exe (PID: 3540)
INFO
Checks supported languages
- oooSrv.exe (PID: 2580)
- DesktopLayer.exe (PID: 2860)
- ooo.exe (PID: 1696)
- Server.exe (PID: 3540)
- Nzwhkaf.exe (PID: 492)
- NzwhkafSrv.exe (PID: 2576)
- Nzwhkaf.exe (PID: 1624)
Creates files in the program directory
- oooSrv.exe (PID: 2580)
- iexplore.exe (PID: 3092)
- Server.exe (PID: 3540)
- Nzwhkaf.exe (PID: 492)
- NzwhkafSrv.exe (PID: 2576)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2044)
Manual execution by a user
- ooo.exe (PID: 1696)
- Server.exe (PID: 3540)
Reads the computer name
- ooo.exe (PID: 1696)
- Server.exe (PID: 3540)
- Nzwhkaf.exe (PID: 492)
- Nzwhkaf.exe (PID: 1624)
Reads the machine GUID from the registry
- ooo.exe (PID: 1696)
Checks proxy server information
- ooo.exe (PID: 1696)
Creates files or folders in the user directory
- ooo.exe (PID: 1696)
Reads CPU info
- Server.exe (PID: 3540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
57
Monitored processes
10
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "C:\Program Files\Microsoft Gcaiys\Nzwhkaf.exe" | C:\Program Files\Microsoft Gcaiys\Nzwhkaf.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1624 | "C:\Program Files\Microsoft Gcaiys\Nzwhkaf.exe" Win7 | C:\Program Files\Microsoft Gcaiys\Nzwhkaf.exe | Nzwhkaf.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\Desktop\ooo.exe" | C:\Users\admin\Desktop\ooo.exe | explorer.exe | ||||||||||||
User: admin Company: 客服QQ:295589399 Integrity Level: HIGH Description: Dhl Microsoft 基础类应用程序 Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | NzwhkafSrv.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\大灰狼远程管理软件 V9.8[至尊版].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2576 | "C:\Program Files\Microsoft Gcaiys\NzwhkafSrv.exe" | C:\Program Files\Microsoft Gcaiys\NzwhkafSrv.exe | — | Nzwhkaf.exe | |||||||||||
User: SYSTEM Company: SOFTWIN S.R.L. Integrity Level: SYSTEM Description: BitDefender Management Console Exit code: 0 Version: 106.42.73.61 Modules
| |||||||||||||||
| 2580 | C:\Users\admin\Desktop\oooSrv.exe | C:\Users\admin\Desktop\oooSrv.exe | ooo.exe | ||||||||||||
User: admin Company: SOFTWIN S.R.L. Integrity Level: HIGH Description: BitDefender Management Console Exit code: 0 Version: 106.42.73.61 Modules
| |||||||||||||||
| 2860 | "C:\Program Files\Microsoft\DesktopLayer.exe" | C:\Program Files\Microsoft\DesktopLayer.exe | — | oooSrv.exe | |||||||||||
User: admin Company: SOFTWIN S.R.L. Integrity Level: HIGH Description: BitDefender Management Console Exit code: 0 Version: 106.42.73.61 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | DesktopLayer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3540 | "C:\Users\admin\Desktop\Server.exe" | C:\Users\admin\Desktop\Server.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 086
Read events
8 979
Write events
92
Delete events
15
Modification events
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\大灰狼远程管理软件 V9.8[至尊版].rar | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
31
Suspicious files
0
Text files
26
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Control\QQwry.dat | — | |
MD5:— | SHA256:— | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Control\mstscax.dll | executable | |
MD5:1CD3B0AD1044B86514232E8FE33F9679 | SHA256:A5CE588A32564C7C65CAAB7E11EE644DB6B14B71F1E15BD03165467402B2EE20 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Control\FTPServer.exe | executable | |
MD5:C8FE8C3BABDDCD6C4401903947B265DD | SHA256:E1301690A5C10493FF6C7C59FD6BA7CDA2EDF0D7418CF613D7810D6118764AC0 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Plugins\C_CHAT.h | text | |
MD5:2286EBBA205B77E0CAA922997629A359 | SHA256:0354A0C31578149DB6A5A23101EA0B1C8C8727BE772BCEDA598E85161C72B200 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Plugins\C_SCREEN1.h | text | |
MD5:720254D57BA61F15436CD216B03FA7CF | SHA256:44530DA9DE5F79781F7B391C7A01CCF06E926C9BBD0D8ABFC23EC780880D4DB9 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Plugins\C_PROXYMAP.h | text | |
MD5:4655D21C85F90E9102299BAA81EC33CD | SHA256:A2B5445EDF773EE31ED61D0280CEECEA01E245E33048227714FA75739F05819E | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Plugins\AnyFileToByte.exe | executable | |
MD5:FF83181FDFF4572E4D21D3273B02E9F2 | SHA256:A87637DB46B2076A44CA7399EB4D87A2FE0113147AA403B3B9C8AC7D365432F1 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Control\hfs.exe | executable | |
MD5:E262FEE29CBA27AD3D67C5FD09966307 | SHA256:9652D3A0B9A0EA28755F5F65D67359140C5653AB017E68E6A8A68919E1BD07B6 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Control\mstsc.exe | executable | |
MD5:C8906AA6F3D3609A97D6E33D570662A3 | SHA256:2D74B6C313A7D36EAEFB5B39FE295B29E057C1F3485D505290FC4B0D86050200 | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.20078\Control\upx.exe | executable | |
MD5:153A7003F42108044122BA0AEB34A202 | SHA256:C96F0BCF5DD5B9BABB431970D627BFA25673AFE1720E658755DBDAE9EE7F0A84 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
5
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1696 | ooo.exe | GET | 200 | 14.29.101.169:80 | http://whois.pconline.com.cn/ipJson.jsp | unknown | text | 199 b | unknown |
1696 | ooo.exe | GET | 302 | 103.235.46.245:80 | http://api.map.baidu.com/telematics/v3/ | unknown | — | — | unknown |
1696 | ooo.exe | GET | 200 | 103.235.46.40:80 | http://www.baidu.com/error.html | unknown | html | 14.9 Kb | unknown |
1696 | ooo.exe | GET | 302 | 103.235.46.245:80 | http://api.map.baidu.com/telematics/v3/weather?location=&&output=json&&ak=DC8048985ecf4db39f22016f18226a1c | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3092 | iexplore.exe | 216.58.206.46:80 | — | GOOGLE | US | whitelisted |
3092 | iexplore.exe | 34.175.230.209:443 | fget-career.com | GOOGLE-CLOUD-PLATFORM | ES | unknown |
1696 | ooo.exe | 14.29.101.169:80 | whois.pconline.com.cn | Chinanet | CN | unknown |
1696 | ooo.exe | 103.235.46.245:80 | api.map.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | unknown |
1696 | ooo.exe | 103.235.46.40:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | unknown |
1848 | iexplore.exe | 34.175.230.209:443 | fget-career.com | GOOGLE-CLOUD-PLATFORM | ES | unknown |
1848 | iexplore.exe | 216.58.206.46:80 | — | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fget-career.com |
| malicious |
whois.pconline.com.cn |
| malicious |
api.map.baidu.com |
| unknown |
www.baidu.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1696 | ooo.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup (whois .pconline .com .cn) |
3092 | iexplore.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Ramnit Checkin |
3092 | iexplore.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Ramnit Checkin |
1848 | iexplore.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Ramnit Checkin |
1848 | iexplore.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Ramnit Checkin |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
ooo.exe | 12345 |
Server.exe | ½øÈë¼ÓÔØWinMain |
Nzwhkaf.exe | ½øÈë¼ÓÔØWinMain |
Nzwhkaf.exe | ½øÈë¼ÓÔØWinMain |