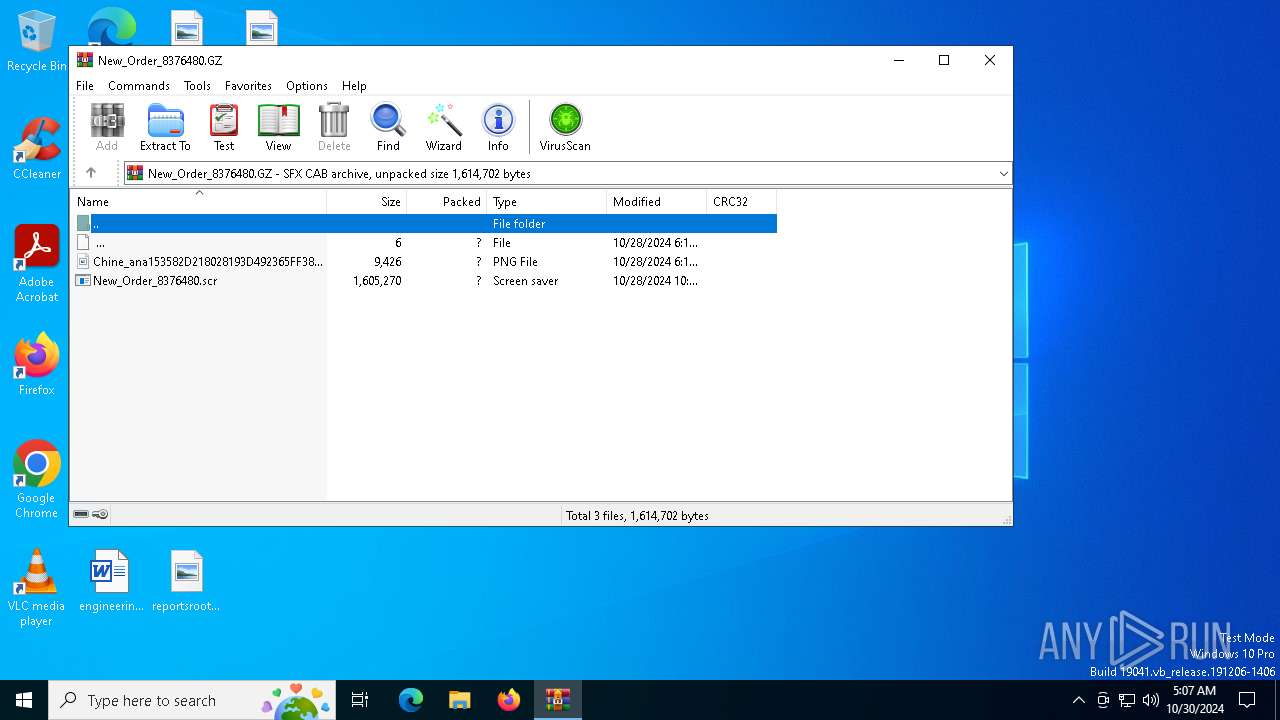
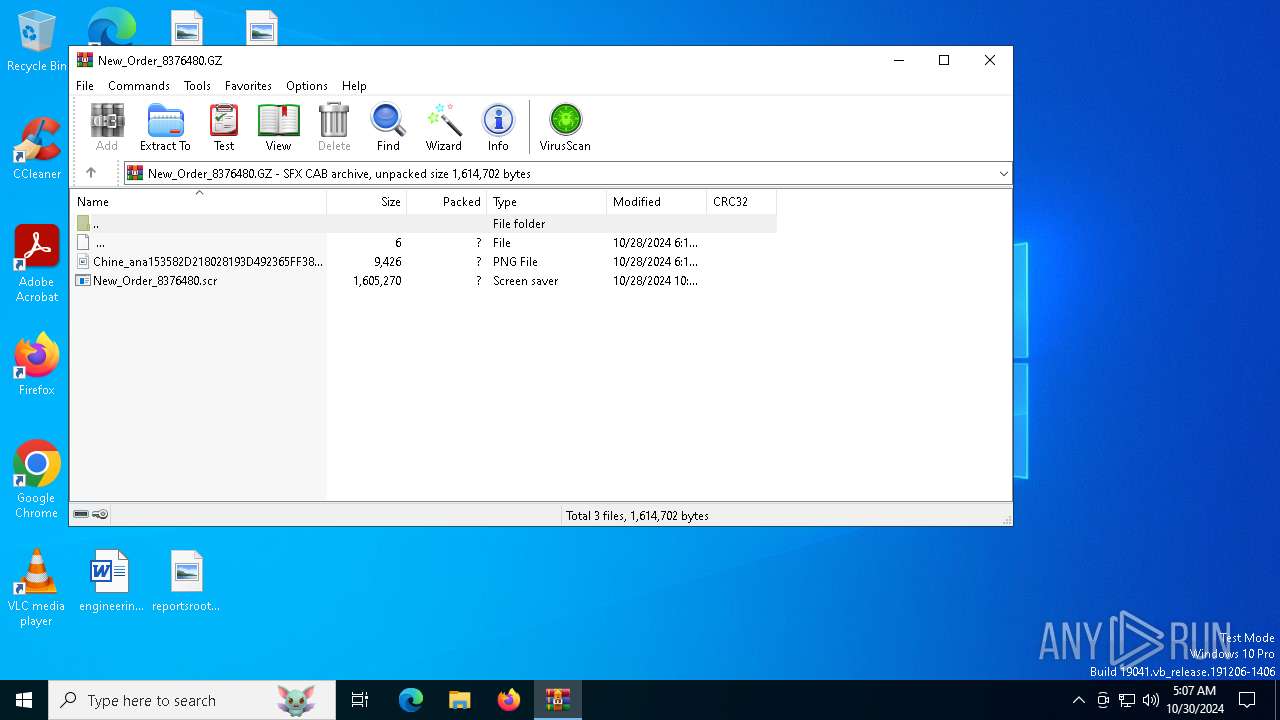
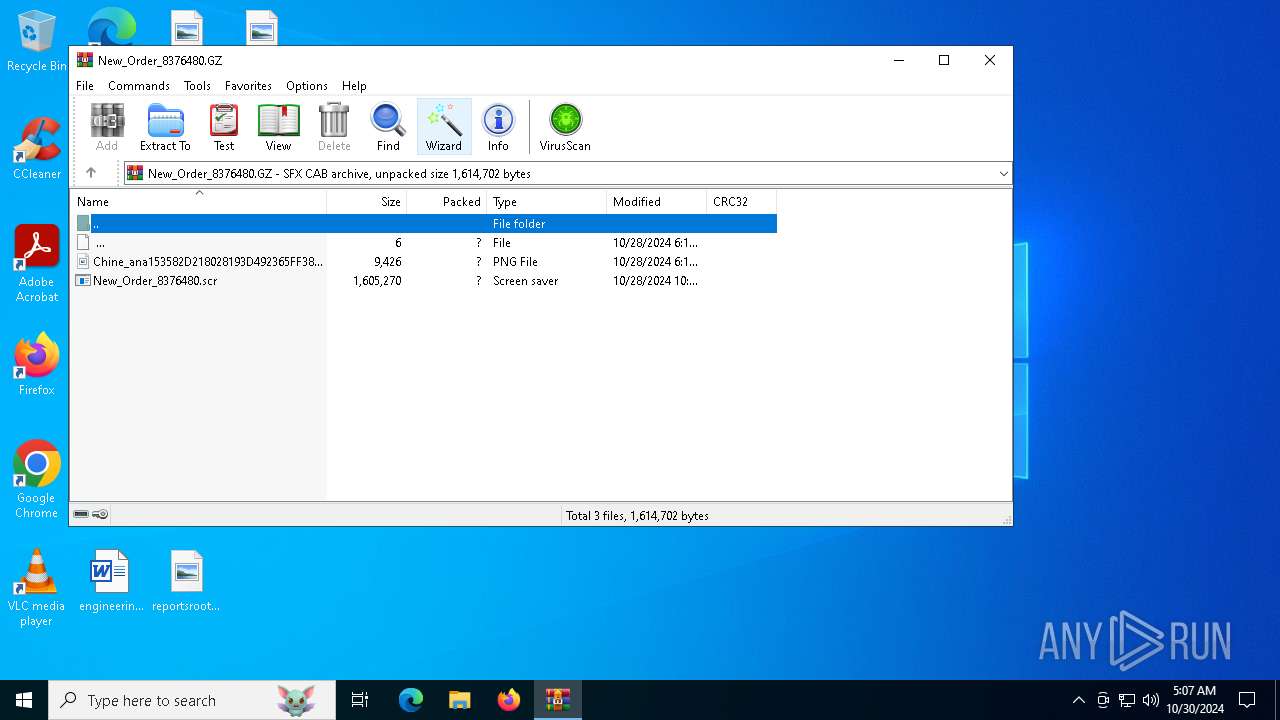
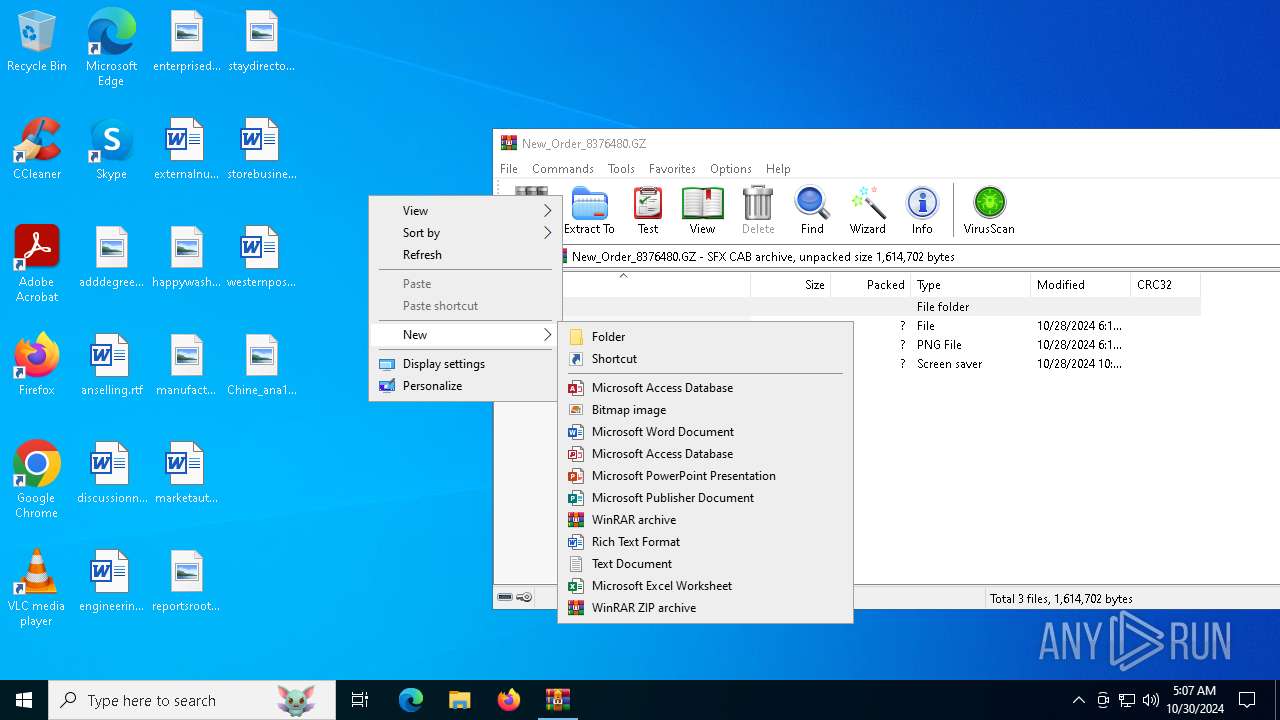
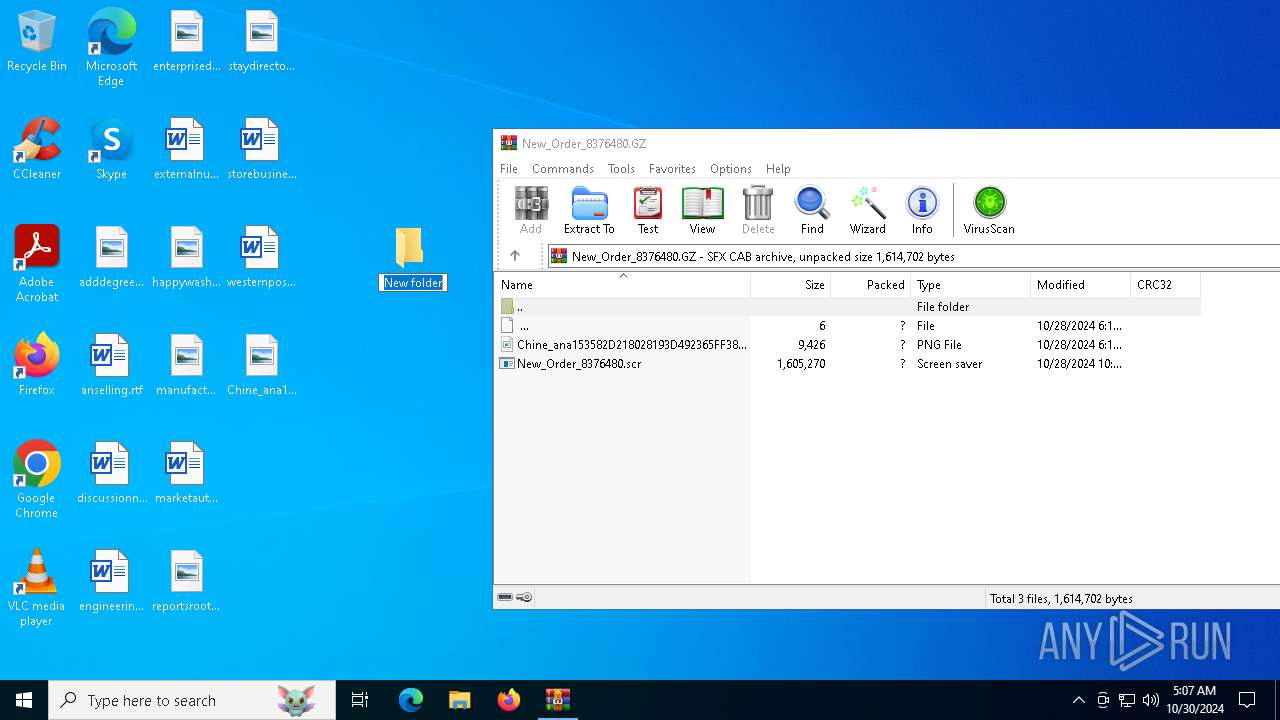
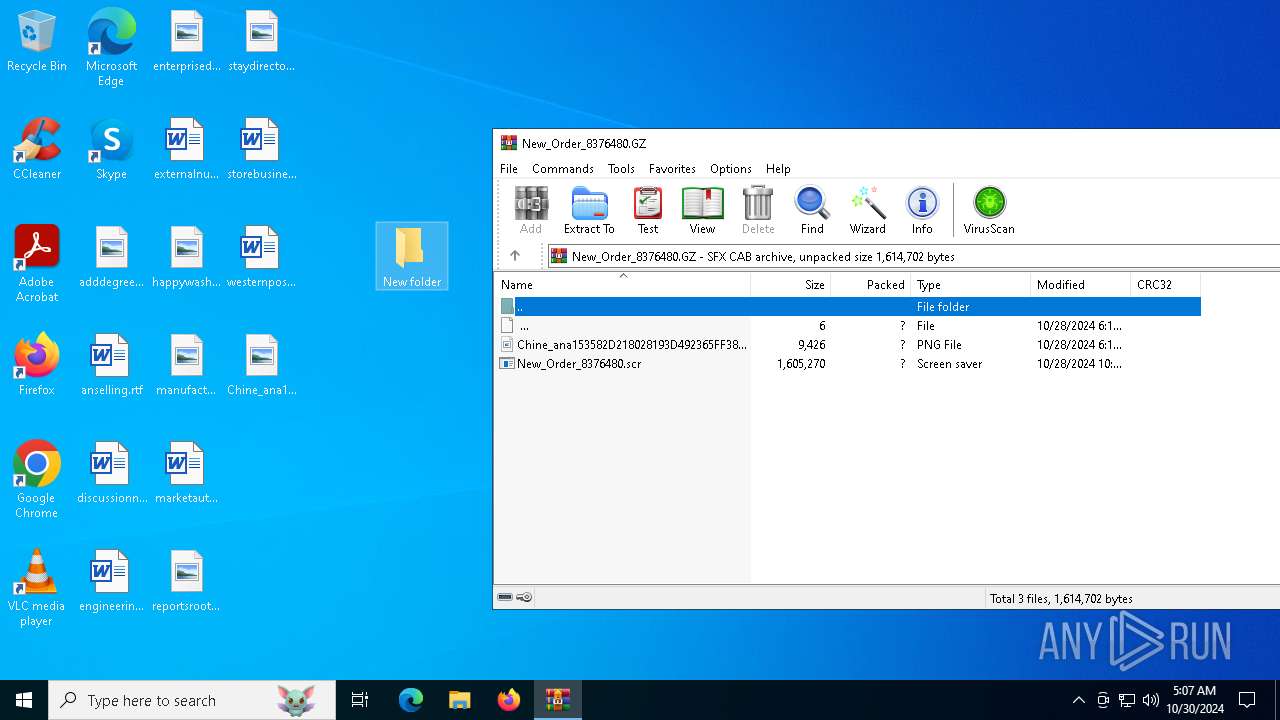
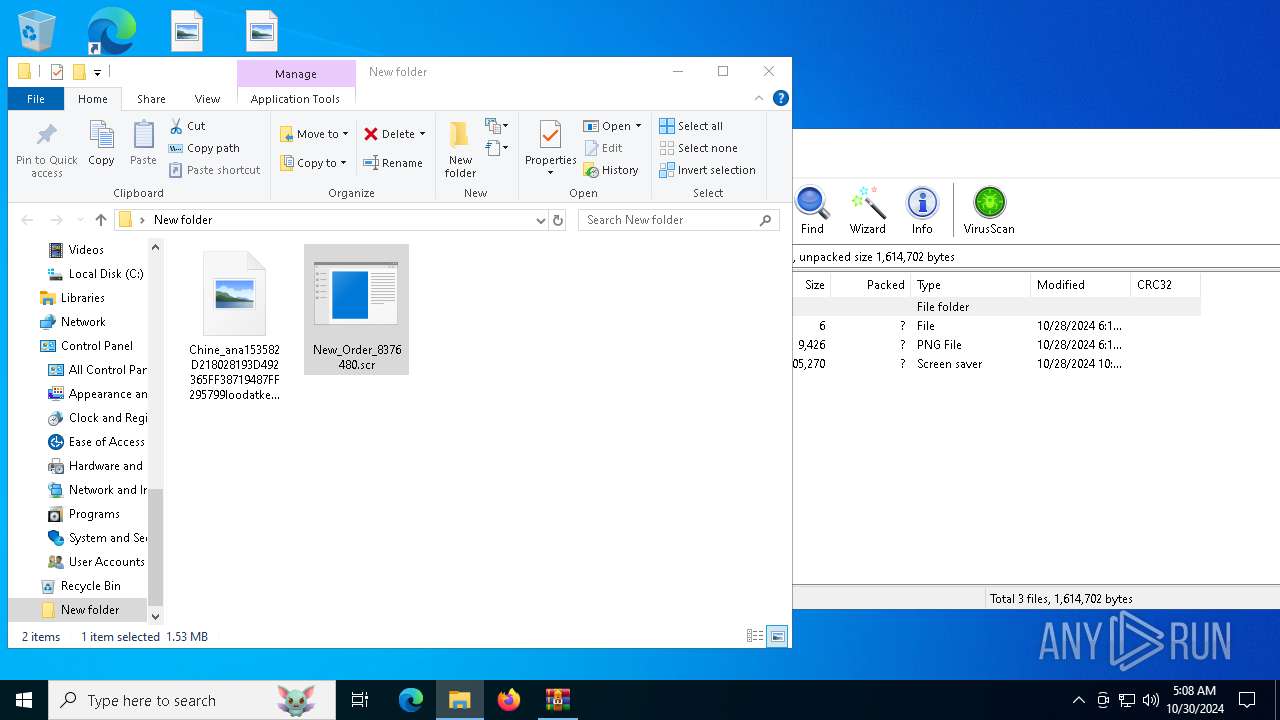
| File name: | New_Order_8376480.GZ |
| Full analysis: | https://app.any.run/tasks/fbceee7b-9221-4bdd-8a47-437e1d56b95d |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | October 30, 2024, 05:07:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 5B9924D878D739E8DEE30926D05E701F |
| SHA1: | 76AD69F5D5D1AA4824A3091B358C8E9FBFA8E3A2 |
| SHA256: | 43B9F2F9513A0DB40AA5D2AC2FF68ACF8CB90460742D83B88748E5FED45E758C |
| SSDEEP: | 24576:FqqqZHzyBkVgw2rGZvlNPkis/4WvcY8aLl0pfpaikLJp:FqqqZHzyBkVgw2rGZv3Pkis/4WvcY8aB |
MALICIOUS
Connects to the CnC server
- wab.exe (PID: 1580)
AGENTTESLA has been detected (SURICATA)
- wab.exe (PID: 1580)
Uses Task Scheduler to run other applications
- wab.exe (PID: 1580)
XWORM has been detected (SURICATA)
- wab.exe (PID: 1580)
SNAKEKEYLOGGER has been detected (SURICATA)
- wab.exe (PID: 1580)
Adds path to the Windows Defender exclusion list
- wab.exe (PID: 1580)
SUSPICIOUS
Executes application which crashes
- New_Order_8376480.scr (PID: 6888)
Executable content was dropped or overwritten
- wab.exe (PID: 1580)
Process drops legitimate windows executable
- wab.exe (PID: 1580)
Connects to unusual port
- wab.exe (PID: 1580)
Contacting a server suspected of hosting an CnC
- wab.exe (PID: 1580)
The process connected to a server suspected of theft
- wab.exe (PID: 1580)
Checks for external IP
- wab.exe (PID: 1580)
- svchost.exe (PID: 2172)
Connects to SMTP port
- wab.exe (PID: 1580)
Starts POWERSHELL.EXE for commands execution
- wab.exe (PID: 1580)
The process executes via Task Scheduler
- XClient.exe (PID: 3524)
- XClient.exe (PID: 528)
- XClient.exe (PID: 3604)
- XClient.exe (PID: 6216)
Script adds exclusion path to Windows Defender
- wab.exe (PID: 1580)
Starts itself from another location
- wab.exe (PID: 1580)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4828)
Manual execution by a user
- New_Order_8376480.scr (PID: 6888)
.NET Reactor protector has been detected
- wab.exe (PID: 1580)
Attempt to transmit an email message via SMTP
- wab.exe (PID: 1580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
153
Monitored processes
19
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Users\admin\AppData\Roaming\XClient.exe" | C:\Users\admin\AppData\Roaming\XClient.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | "C:\Program Files (x86)\Windows Mail\wab.exe" | C:\Program Files (x86)\Windows Mail\wab.exe | New_Order_8376480.scr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | "C:\Users\admin\AppData\Roaming\XClient.exe" | C:\Users\admin\AppData\Roaming\XClient.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3604 | "C:\Users\admin\AppData\Roaming\XClient.exe" | C:\Users\admin\AppData\Roaming\XClient.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "C:\Users\admin\AppData\Roaming\ACCApi\apihost.exe" | C:\Users\admin\AppData\Roaming\ACCApi\apihost.exe | — | wab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4828 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\New_Order_8376480.GZ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 271
Read events
14 218
Write events
28
Delete events
25
Modification events
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New_Order_8376480.GZ | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (4828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
2
Suspicious files
8
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7148 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_New_Order_837648_66e5fbbf8cc1be19e06ffab5c977529751026a1_c09ff8e5_c05b3574-e00c-4246-afef-03df4f44ebbc\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7148 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\New_Order_8376480.scr.6888.dmp | — | |
MD5:— | SHA256:— | |||
| 1580 | wab.exe | C:\Users\admin\AppData\Roaming\ACCApi\apihost.exe | — | |
MD5:— | SHA256:— | |||
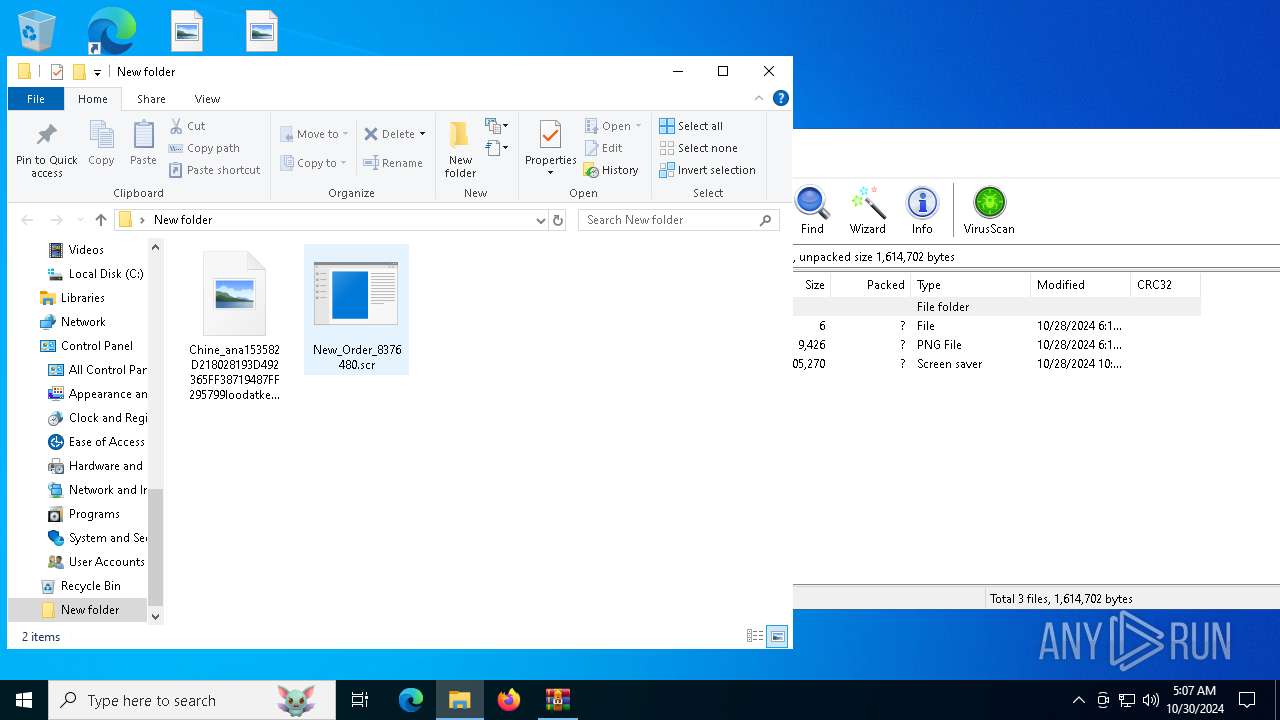
| 4828 | WinRAR.exe | C:\Users\admin\Desktop\New folder\New_Order_8376480.scr | executable | |
MD5:0A3235126FFDFE6E847946D2EB23C03E | SHA256:F17A45C8B3AC9ADF1A66DFA1B27E62E433ADFAABCD36BA52DEAC1E7C00699F47 | |||
| 4828 | WinRAR.exe | C:\Users\admin\Desktop\Chine_ana153582D218028193D492365FF38719487FF295799loodatke.PNG | image | |
MD5:DC156637AEBF04336700A9BC71C78AAD | SHA256:E739A88AC8FB4FEFA998F8DBF4402A8D7A22EB079EDD05BEE412C4D4C99014EB | |||
| 1580 | wab.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\XClient.lnk | binary | |
MD5:1CF23A62FA5361139A2CD96752A97DF3 | SHA256:BC59342C811069CA5BFA6A890DB55B0F4D44C5F9371169ADD619E75EA165979D | |||
| 7148 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9D30.tmp.xml | xml | |
MD5:B734A135A04C42F9EF22BE4ADAB271C9 | SHA256:F3FDBAA804B89B3D7F43AC4B24EA8D0782302EC6492FD86352CDB4EF0A128FDA | |||
| 5984 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pigkkw0e.rd2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7148 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9D10.tmp.WERInternalMetadata.xml | xml | |
MD5:A0050878A295FB9C4D3FF878BDBB64D1 | SHA256:95C78A3B77B1639847D20053F238AAD3B8DAE2AE2C8EBB65E66D8DBE9D63A5EA | |||
| 7148 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:F0CF5B1794ECA7CD73F9C020DAAB8EF2 | SHA256:2AF00EDCE7EF3266897E52DC81E8DE3B7A079028C0F1F96EAFF9E38AD342F617 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
56
DNS requests
29
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
884 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
528 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
528 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7148 | WerFault.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7148 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1580 | wab.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2660 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 2.23.209.177:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
816 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1580 | wab.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm TCP Packet |
2172 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1580 | wab.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1580 | wab.exe | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
1580 | wab.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Exfiltration via SMTP (AgentTesla) |
1580 | wab.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
1580 | wab.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
1580 | wab.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - checkip.dyndns.org |
1580 | wab.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
10 ETPRO signatures available at the full report