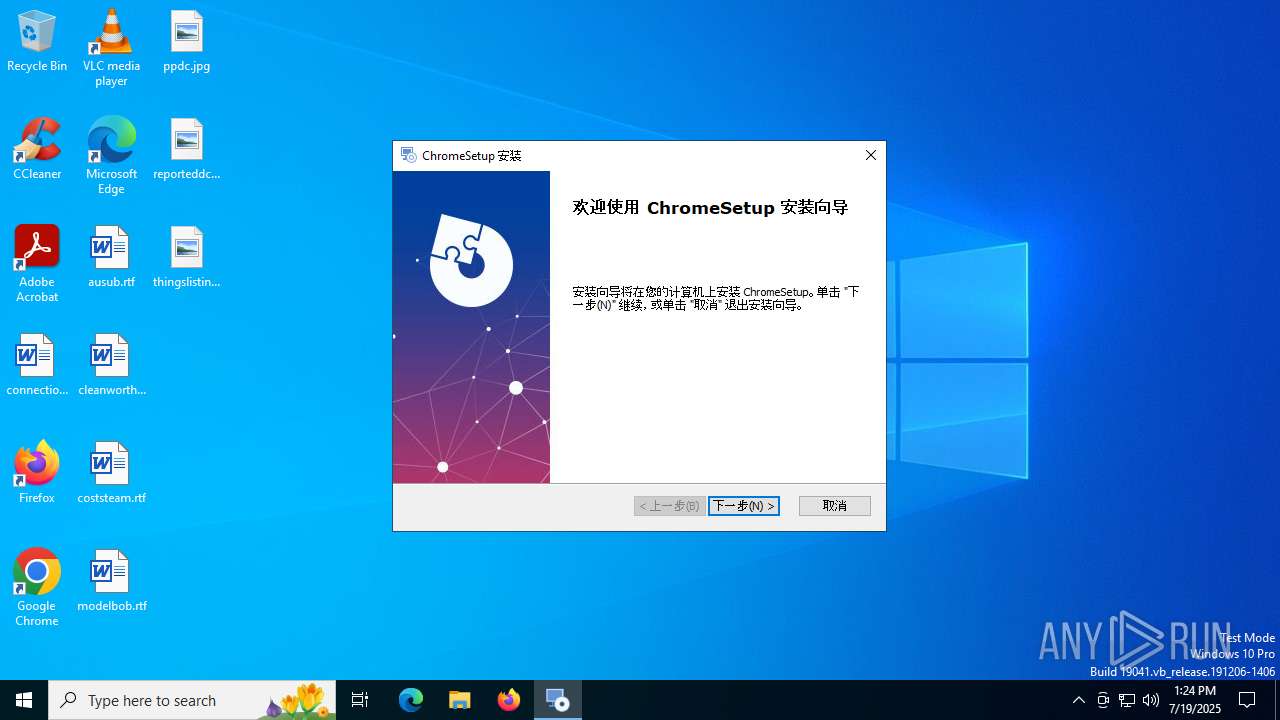
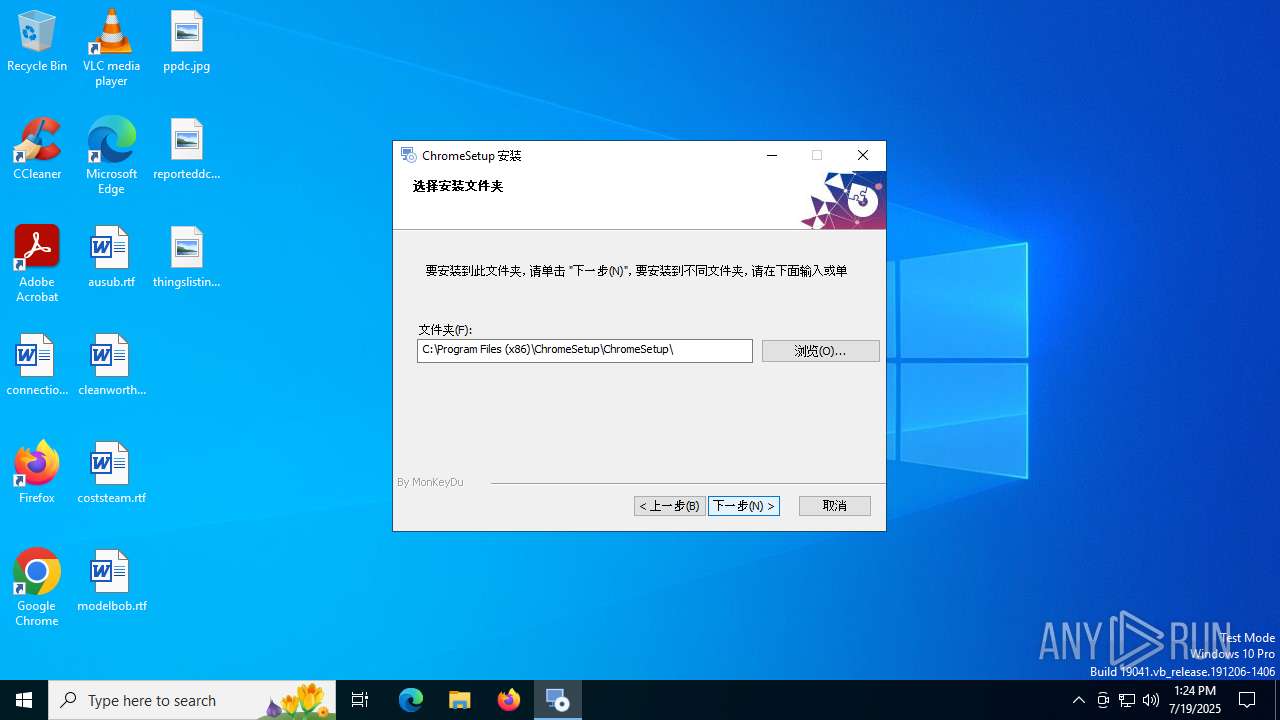
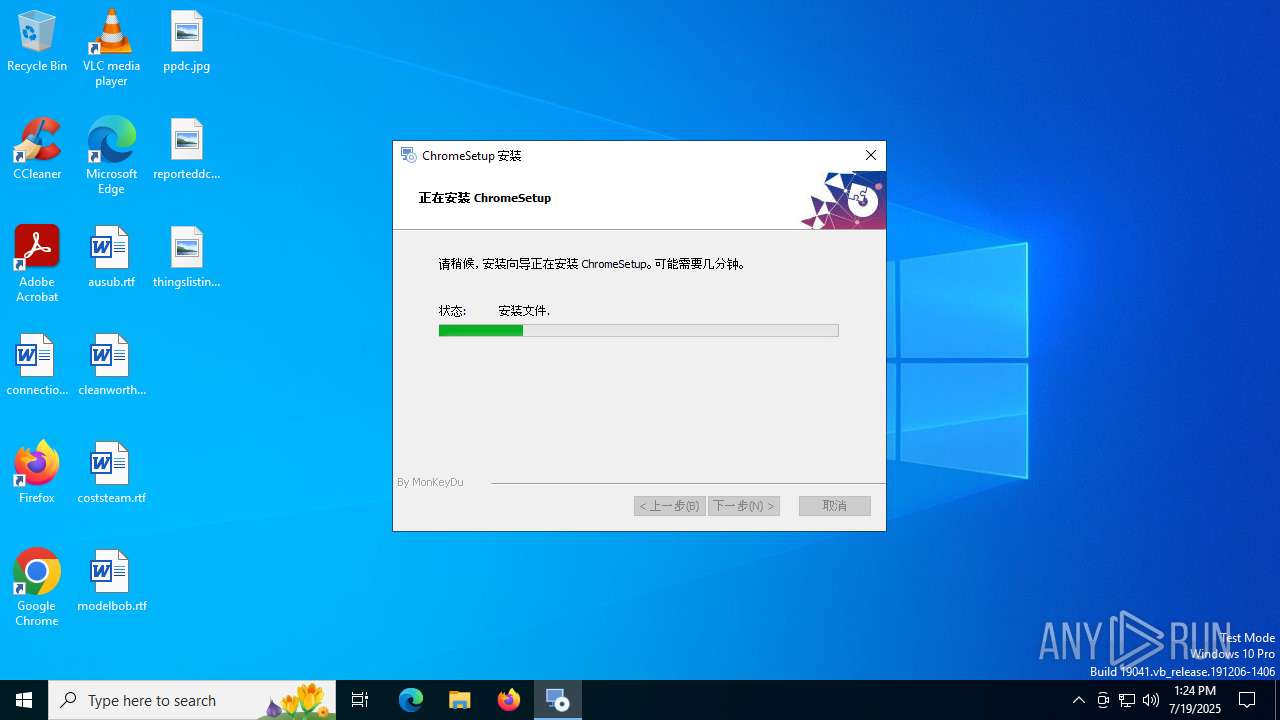
| File name: | ChromeSetup.exe |
| Full analysis: | https://app.any.run/tasks/c22645e7-bbbf-49ca-9dfa-971df6ee8661 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | July 19, 2025, 13:24:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 7678BA7092C658FB4AD3908852277184 |
| SHA1: | 98079EA87D017ADD7DC8F17FF96D81065316220E |
| SHA256: | 43130DF9D6C99E0D01470A57E0A21215A9AFBB1C9B191E1B86FCB046316DE6D1 |
| SSDEEP: | 196608:9fAnutgO2U4HC0X1AsRvR8fOO/89ypfADT:JAnutgxU4i0SsRvRzO/89aoDT |
MALICIOUS
SILVERFOX has been detected
- msiexec.exe (PID: 2292)
Changes the autorun value in the registry
- appdata.exe (PID: 72)
- appdata.exe (PID: 1244)
- appdata.exe (PID: 5496)
- setup.exe (PID: 6840)
UAC/LUA settings modification
- appdata.exe (PID: 1244)
Connects to the CnC server
- appdata.exe (PID: 1244)
SILVERFOX has been detected (SURICATA)
- appdata.exe (PID: 1244)
SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- ChromeSetup.exe (PID: 1392)
Executable content was dropped or overwritten
- ChromeSetup.exe (PID: 1392)
- updater.exe (PID: 5884)
- updater.exe (PID: 2432)
- 138.0.7204.158_chrome_installer_uncompressed.exe (PID: 4160)
- setup.exe (PID: 6840)
Application launched itself
- ChromeSetup.exe (PID: 1392)
- updater.exe (PID: 5884)
- cmd.exe (PID: 3620)
- updater.exe (PID: 2432)
- updater.exe (PID: 4544)
- appdata.exe (PID: 72)
- appdata.exe (PID: 1244)
- setup.exe (PID: 6840)
- setup.exe (PID: 6140)
Reads security settings of Internet Explorer
- ChromeSetup.exe (PID: 1392)
- msiexec.exe (PID: 3628)
- updater.exe (PID: 5884)
- ShellExperienceHost.exe (PID: 5528)
Reads the Windows owner or organization settings
- ChromeSetup.exe (PID: 1392)
- msiexec.exe (PID: 2292)
Executing commands from a ".bat" file
- msiexec.exe (PID: 3628)
- cmd.exe (PID: 3620)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3620)
- msiexec.exe (PID: 3628)
There is functionality for taking screenshot (YARA)
- ChromeSetup.exe (PID: 1392)
Detects AdvancedInstaller (YARA)
- ChromeSetup.exe (PID: 1392)
Executes as Windows Service
- updater.exe (PID: 2432)
- updater.exe (PID: 4544)
Executes application which crashes
- appdata.exe (PID: 72)
Connects to unusual port
- appdata.exe (PID: 1244)
Process drops legitimate windows executable
- ChromeSetup.exe (PID: 1392)
Contacting a server suspected of hosting an CnC
- appdata.exe (PID: 1244)
Searches for installed software
- setup.exe (PID: 6840)
Creates a software uninstall entry
- setup.exe (PID: 6840)
INFO
Creates files or folders in the user directory
- ChromeSetup.exe (PID: 1392)
- updater.exe (PID: 5884)
- WerFault.exe (PID: 6820)
The sample compiled with chinese language support
- ChromeSetup.exe (PID: 1392)
- msiexec.exe (PID: 2292)
Create files in a temporary directory
- ChromeSetup.exe (PID: 1392)
- ChromeSetup.exe (PID: 5724)
- updater.exe (PID: 5884)
Reads Environment values
- msiexec.exe (PID: 3628)
- ChromeSetup.exe (PID: 1392)
- msiexec.exe (PID: 1660)
Checks supported languages
- ChromeSetup.exe (PID: 1324)
- ChromeSetup.exe (PID: 1392)
- msiexec.exe (PID: 2292)
- msiexec.exe (PID: 1660)
- appdata.exe (PID: 72)
- ChromeSetup.exe (PID: 5724)
- updater.exe (PID: 5884)
- updater.exe (PID: 4692)
- updater.exe (PID: 2432)
- updater.exe (PID: 5988)
- updater.exe (PID: 4892)
- updater.exe (PID: 4544)
- appdata.exe (PID: 1244)
- appdata.exe (PID: 5496)
- ShellExperienceHost.exe (PID: 5528)
- msiexec.exe (PID: 3628)
- 138.0.7204.158_chrome_installer_uncompressed.exe (PID: 4160)
- setup.exe (PID: 6840)
- setup.exe (PID: 1828)
- setup.exe (PID: 6140)
- setup.exe (PID: 7132)
- elevation_service.exe (PID: 2324)
Reads the computer name
- msiexec.exe (PID: 3628)
- msiexec.exe (PID: 1660)
- ChromeSetup.exe (PID: 5724)
- updater.exe (PID: 5884)
- updater.exe (PID: 2432)
- updater.exe (PID: 4544)
- appdata.exe (PID: 72)
- appdata.exe (PID: 1244)
- ShellExperienceHost.exe (PID: 5528)
- ChromeSetup.exe (PID: 1392)
- msiexec.exe (PID: 2292)
- appdata.exe (PID: 5496)
- 138.0.7204.158_chrome_installer_uncompressed.exe (PID: 4160)
- setup.exe (PID: 6840)
- setup.exe (PID: 6140)
- elevation_service.exe (PID: 2324)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2292)
The sample compiled with english language support
- msiexec.exe (PID: 2292)
- updater.exe (PID: 5884)
- updater.exe (PID: 2432)
- ChromeSetup.exe (PID: 1392)
- 138.0.7204.158_chrome_installer_uncompressed.exe (PID: 4160)
- setup.exe (PID: 6840)
Creates a software uninstall entry
- msiexec.exe (PID: 2292)
Process checks computer location settings
- msiexec.exe (PID: 3628)
- ChromeSetup.exe (PID: 1392)
Creates files in the program directory
- updater.exe (PID: 4692)
- updater.exe (PID: 5884)
- updater.exe (PID: 2432)
- appdata.exe (PID: 1244)
- updater.exe (PID: 4544)
- setup.exe (PID: 6840)
- setup.exe (PID: 6140)
Process checks whether UAC notifications are on
- updater.exe (PID: 5884)
- updater.exe (PID: 2432)
- updater.exe (PID: 4544)
- appdata.exe (PID: 1244)
Reads the software policy settings
- updater.exe (PID: 5884)
- updater.exe (PID: 4544)
- WerFault.exe (PID: 6820)
Reads the machine GUID from the registry
- updater.exe (PID: 5884)
Checks proxy server information
- updater.exe (PID: 5884)
- WerFault.exe (PID: 6820)
Launching a file from a Registry key
- appdata.exe (PID: 72)
- appdata.exe (PID: 5496)
- appdata.exe (PID: 1244)
- setup.exe (PID: 6840)
Manual execution by a user
- chrome.exe (PID: 2040)
Application launched itself
- chrome.exe (PID: 2040)
Executes as Windows Service
- elevation_service.exe (PID: 2324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:05:31 13:15:01+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 2484736 |
| InitializedDataSize: | 948224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d6f94 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.0.0 |
| ProductVersionNumber: | 11.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| CompanyName: | ChromeSetup |
| FileDescription: | ChromeSetup Installer |
| FileVersion: | 11.0.0 |
| InternalName: | ChromeSetup |
| LegalCopyright: | Copyright (C) 2025 ChromeSetup |
| OriginalFileName: | ChromeSetup.exe |
| ProductName: | ChromeSetup |
| ProductVersion: | 11.0.0 |
Total processes
185
Monitored processes
44
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | appdata.exe | C:\ProgramData\appdata\appdata.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 酷狗音乐动态壁纸播放器(WebGL) Exit code: 3221225477 Version: 1.0.0.141 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=138.0.7204.158 --initial-client-data=0x220,0x224,0x228,0x208,0x22c,0x7ffc431b96e8,0x7ffc431b96f4,0x7ffc431b9700 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 138.0.7204.158 Modules
| |||||||||||||||
| 1148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-pre-read-main-dll --force-high-res-timeticks=disabled --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2032,i,17647067089505178164,1613429678796346635,262144 --variations-seed-version --mojo-platform-channel-handle=2028 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 138.0.7204.158 Modules
| |||||||||||||||
| 1244 | "C:\ProgramData\appdata\appdata.exe" --a --watch=0 | C:\ProgramData\appdata\appdata.exe | appdata.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 酷狗音乐动态壁纸播放器(WebGL) Version: 1.0.0.141 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Local\Temp\ChromeSetup.exe" /i "C:\Users\admin\AppData\Roaming\ChromeSetup\ChromeSetup 11.0.0\install\0B216C5\ChromeSetup.msi" AI_EUIMSI=1 APPDIR="C:\Program Files (x86)\ChromeSetup\ChromeSetup" SECONDSEQUENCE="1" CLIENTPROCESSID="1392" CHAINERUIPROCESSID="1392Chainer" ACTION="INSTALL" EXECUTEACTION="INSTALL" CLIENTUILEVEL="0" ADDLOCAL="MainFeature" PRIMARYFOLDER="APPDIR" ROOTDRIVE="C:\" AI_SETUPEXEPATH="C:\Users\admin\AppData\Local\Temp\ChromeSetup.exe" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp\" EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1752929853 " AI_SETUPEXEPATH_ORIGINAL="C:\Users\admin\AppData\Local\Temp\ChromeSetup.exe" TARGETDIR="C:\" AI_INSTALL="1" ARPSIZE=31380 AiProductCode={65C9AD67-092B-4C8E-AC7A-9C5CB0B216C5} FASTOEM=1 /qn | C:\Users\admin\AppData\Local\Temp\ChromeSetup.exe | ChromeSetup.exe | ||||||||||||
User: admin Company: ChromeSetup Integrity Level: HIGH Description: ChromeSetup Installer Exit code: 0 Version: 11.0.0 Modules
| |||||||||||||||
| 1392 | "C:\Users\admin\AppData\Local\Temp\ChromeSetup.exe" | C:\Users\admin\AppData\Local\Temp\ChromeSetup.exe | explorer.exe | ||||||||||||
User: admin Company: ChromeSetup Integrity Level: MEDIUM Description: ChromeSetup Installer Exit code: 0 Version: 11.0.0 Modules
| |||||||||||||||
| 1660 | C:\Windows\syswow64\MsiExec.exe -Embedding A4C891D71885BE9EB1B528CC950F12CD | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=2032,i,17647067089505178164,1613429678796346635,262144 --variations-seed-version --mojo-platform-channel-handle=1812 /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 138.0.7204.158 Modules
| |||||||||||||||
| 1828 | C:\WINDOWS\SystemTemp\chrome_Unpacker_BeginUnzipping4544_552069456\CR_ED307.tmp\setup.exe --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\WINDOWS\SystemTemp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=138.0.7204.158 --initial-client-data=0x2a0,0x2a4,0x2a8,0x27c,0x2ac,0x7ff791d025a0,0x7ff791d025ac,0x7ff791d025b8 | C:\Windows\SystemTemp\chrome_Unpacker_BeginUnzipping4544_552069456\CR_ED307.tmp\setup.exe | — | setup.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Installer Exit code: 0 Version: 138.0.7204.158 Modules
| |||||||||||||||
| 1880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 705
Read events
12 389
Write events
290
Delete events
26
Modification events
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: F4080000B74D437CB0F8DB01 | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: F2A832BA5A17A1B71E92407BE3843E282C9FBAF675F273C27F6A849467D1BC5D | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | LocalPackage |
Value: C:\WINDOWS\Installer\18f7bb.msi | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | AuthorizedCDFPrefix |
Value: | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | Comments |
Value: 此 Installer 数据库包含了安装 ChromeSetup 所需的逻辑和数据。 | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | Contact |
Value: | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | DisplayVersion |
Value: 11.0.0 | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | HelpLink |
Value: | |||
| (PID) Process: | (2292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\76DA9C56B290E8C4CAA7C9C50B2B615C\InstallProperties |
| Operation: | write | Name: | HelpTelephone |
Value: | |||
Executable files
41
Suspicious files
94
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Roaming\ChromeSetup\ChromeSetup 11.0.0\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\shiDB28.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\MSIDC57.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\MSIDBF5.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Roaming\ChromeSetup\ChromeSetup 11.0.0\install\0B216C5\ChromeSetup.msi | executable | |
MD5:9C2E4A1C4AA7D2CDC8F4DA6633D17A10 | SHA256:59A6833BF81127B9DD632AF49446D30349C16C8F680E4EB41150E466955BCC3B | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\MSIDC16.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1392\exclamic | image | |
MD5:3FBB7DDBC13EDF109E3ACAA7A4A69A4E | SHA256:F8429073C7A83377AD754824B0B81040D68F8C1350A82FF4DCCF8BC4BF31F177 | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1392\New | image | |
MD5:1E80DE80CEFEE55D7CFDA0DF2EDCF3B2 | SHA256:4E64F4E40D8CBFF082B37186C831AF4B49E3131C62C00A0CF53E0A6E7E24AC2B | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\MSIDC17.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1392 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1392\insticon | image | |
MD5:EAC3781BA9FB0502D6F16253EB67B2B4 | SHA256:F864E8640C98B65C6C1B9B66A850661E8397ED6E66B06F4424396275488AF1BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
46
DNS requests
49
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5884 | updater.exe | GET | 200 | 142.250.186.131:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
4544 | updater.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/%7B8a69d345-d564-463c-aff1-a69d9e530f96%7D/3f2b7bd6ef00d6154123f47afe3a30d1c6656ba876cec51c1b93b11a60ef01c7 | unknown | — | — | whitelisted |
5884 | updater.exe | GET | 200 | 142.250.186.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5884 | updater.exe | GET | 200 | 172.217.18.99:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCECdz283NVEpjCi5UeCEUBvs%3D | unknown | — | — | whitelisted |
6820 | WerFault.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6820 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
504 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2232 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
828 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4544 | updater.exe | 142.250.185.195:443 | update.googleapis.com | GOOGLE | US | whitelisted |
5884 | updater.exe | 142.250.186.110:443 | dl.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
c.pki.goog |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
o.pki.goog |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1244 | appdata.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 25 |
1244 | appdata.exe | Malware Command and Control Activity Detected | ET MALWARE Winos4.0 Framework CnC Login Message |
1244 | appdata.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Keep-Alive Client Packet |
1244 | appdata.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Keep-Alive Client Packet |
1244 | appdata.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Keep-Alive Client Packet |
1816 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
1816 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
1244 | appdata.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Keep-Alive Client Packet |
Process | Message |
|---|---|
chrome.exe | I0000 00:00:1752931543.150722 2848 voice_transcription.cc:58] Registering VoiceTranscriptionCapability
|