| File name: | setup_patched.exe |
| Full analysis: | https://app.any.run/tasks/d36296d1-44d4-45fe-9c28-c30f92b0fc12 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 29, 2025, 11:26:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | D1029500FE27A9BA17363E58C3708855 |
| SHA1: | 134FC4F004D775E03E8A781B60F0B082941CE622 |
| SHA256: | 42F4479C89C128D436008B43F53C259257500C7A1E77DA4C89162096BB772D5D |
| SSDEEP: | 98304:EFiMnJ+NwfnPOhNjgZscCED/KaFhrSwpt+NBlP875DfGhrNjBt8Ij4qW4bJdTwn6:yqrWnf0nrN |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
Connects to the CnC server
- svchost.exe (PID: 2196)
- ping.com (PID: 7416)
LUMMA has been detected (YARA)
- setup_patched.exe (PID: 7716)
LUMMA mutex has been found
- setup_patched.exe (PID: 7716)
Steals credentials from Web Browsers
- setup_patched.exe (PID: 7716)
Actions looks like stealing of personal data
- setup_patched.exe (PID: 7716)
Executing a file with an untrusted certificate
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
- EA0VB1WQ461JCROBYA70L0Z7RDOGCEM.exe (PID: 4920)
- shark.exe (PID: 6676)
Known privilege escalation attack
- dllhost.exe (PID: 5892)
Changes the autorun value in the registry
- reg.exe (PID: 7668)
AMADEY has been detected (YARA)
- ping.com (PID: 7416)
HIJACKLOADER has been detected (YARA)
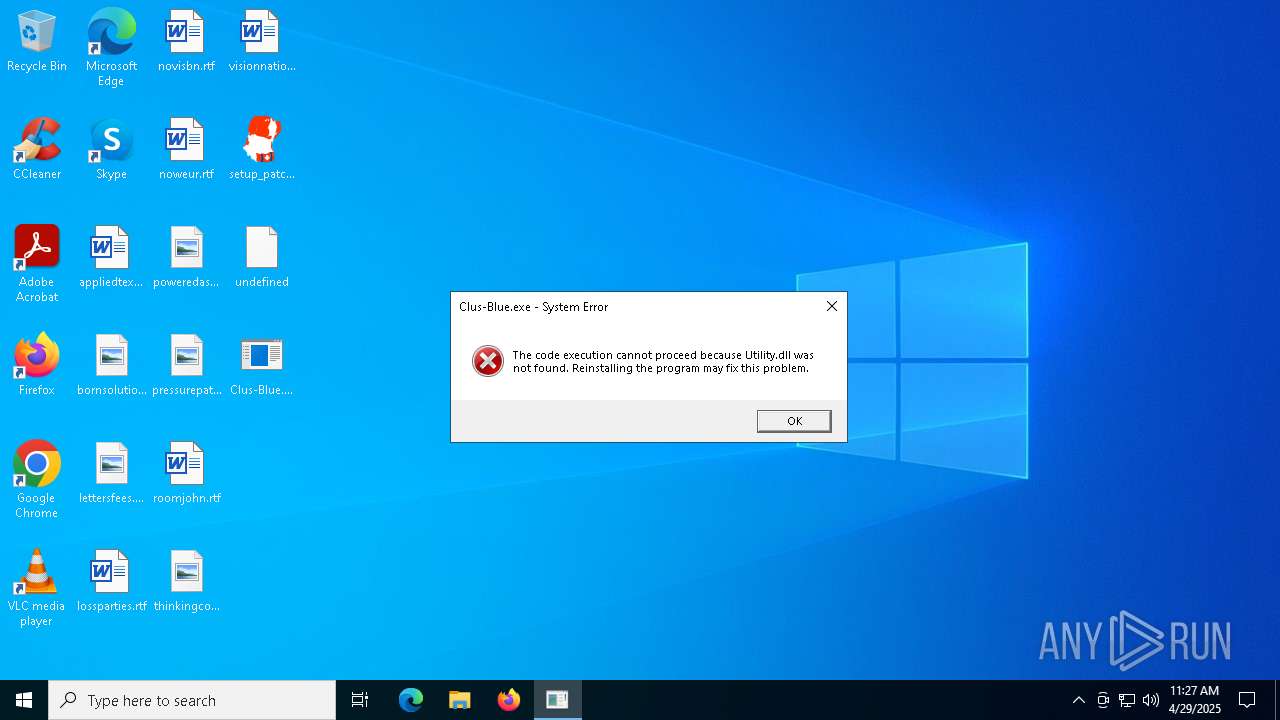
- Clus-Blue.exe (PID: 4408)
AMADEY has been detected (SURICATA)
- ping.com (PID: 7416)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- ping.com (PID: 7416)
Executable content was dropped or overwritten
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8144)
- Clus-Blue.exe (PID: 8164)
- Clus-Blue.exe (PID: 4408)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
Searches for installed software
- setup_patched.exe (PID: 7716)
The process drops C-runtime libraries
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8144)
Process drops legitimate windows executable
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8144)
Starts itself from another location
- Clus-Blue.exe (PID: 8144)
Executes application which crashes
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
- shark.exe (PID: 6676)
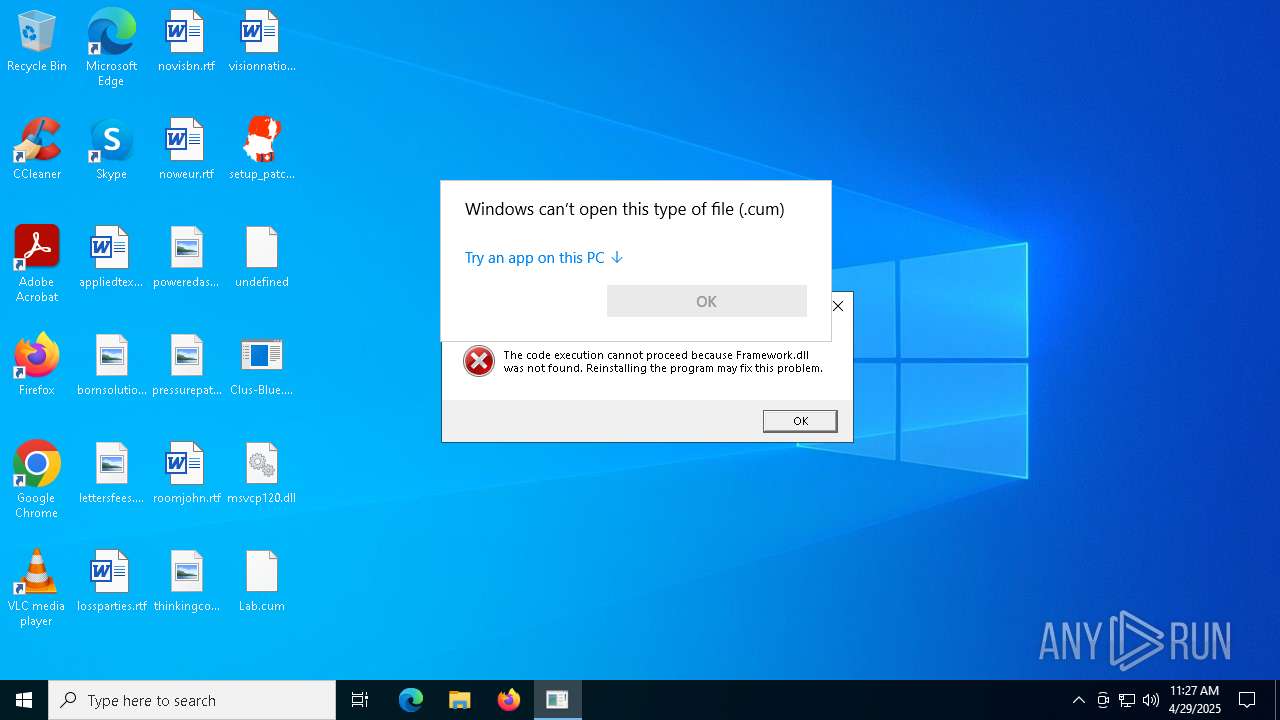
Starts application with an unusual extension
- Clus-Blue.exe (PID: 4408)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7472)
There is functionality for taking screenshot (YARA)
- Clus-Blue.exe (PID: 4408)
- ping.com (PID: 7416)
There is functionality for enable RDP (YARA)
- ping.com (PID: 7416)
Starts CMD.EXE for commands execution
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
Connects to unusual port
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
Reads security settings of Internet Explorer
- ping.com (PID: 7416)
INFO
The sample compiled with english language support
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8144)
Reads the computer name
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8144)
- Clus-Blue.exe (PID: 8164)
- EA0VB1WQ461JCROBYA70L0Z7RDOGCEM.exe (PID: 4920)
- 360Tray.exe (PID: 7256)
- Clus-Blue.exe (PID: 4408)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
- ping.com (PID: 7416)
- 360Tray.exe (PID: 5384)
Checks supported languages
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8144)
- Clus-Blue.exe (PID: 8164)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
- 360Tray.exe (PID: 7256)
- Clus-Blue.exe (PID: 4408)
- EA0VB1WQ461JCROBYA70L0Z7RDOGCEM.exe (PID: 4920)
- ping.com (PID: 7416)
- shark.exe (PID: 6676)
- 360Tray.exe (PID: 5384)
Reads the machine GUID from the registry
- setup_patched.exe (PID: 7716)
- 360Tray.exe (PID: 7256)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
Reads the software policy settings
- setup_patched.exe (PID: 7716)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
- slui.exe (PID: 6456)
Create files in a temporary directory
- setup_patched.exe (PID: 7716)
- Clus-Blue.exe (PID: 8164)
- Clus-Blue.exe (PID: 4408)
Creates files in the program directory
- Clus-Blue.exe (PID: 8144)
- Clus-Blue.exe (PID: 8164)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
The sample compiled with chinese language support
- Clus-Blue.exe (PID: 8164)
Manual execution by a user
- Clus-Blue.exe (PID: 864)
- OpenWith.exe (PID: 6656)
- OpenWith.exe (PID: 4428)
- shark.exe (PID: 6676)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6656)
- OpenWith.exe (PID: 4428)
Compiled with Borland Delphi (YARA)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
- shark.exe (PID: 6676)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5892)
Drops encrypted JS script (Microsoft Script Encoder)
- TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe (PID: 1760)
Auto-launch of the file from Registry key
- reg.exe (PID: 7668)
Checks proxy server information
- slui.exe (PID: 6456)
- ping.com (PID: 7416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(7416) ping.com
C2tackleoutplayed.com
URLhttp://tackleoutplayed.com/yLC6Ya9ut5bfTA/index.php
Version5.34
Options
Drop directoryf7d1e9b9a5
Drop namenudwee.exe
Strings (125)S-%lu-
og:
clip.dll
ProgramData\
shell32.dll
<c>
vs:
Programs
&&
VideoID
ESET
av:
\App
0000043f
Doctor Web
:::
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
------
rundll32.exe
f7d1e9b9a5
00000422
0123456789
st=s
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
msi
ar:
GetNativeSystemInfo
Norton
-%lu
Sophos
zip
SOFTWARE\Microsoft\Windows NT\CurrentVersion
"
Content-Type: application/octet-stream
|
+++
nudwee.exe
" && ren
pc:
#
d1
cmd /C RMDIR /s/q
Bitdefender
Comodo
<d>
Kaspersky Lab
DefaultSettings.YResolution
Main
-executionpolicy remotesigned -File "
&& Exit"
ProductName
&unit=
2022
Panda Security
=
Rem
cmd
\0000
id:
sd:
--
/quiet
rundll32
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%-lu
random
GET
"taskkill /f /im "
Content-Disposition: form-data; name="data"; filename="
00000423
5.34
2016
?scr=1
ComputerName
Keyboard Layout\Preload
Powershell.exe
POST
http://
AVAST Software
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
ps1
DefaultSettings.XResolution
Startup
CurrentBuild
tackleoutplayed.com
e3
cred.dll|clip.dll|
------
WinDefender
wb
https://
Avira
2025
" && timeout 1 && del
cred.dll
un:
SYSTEM\ControlSet001\Services\BasicDisplay\Video
rb
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e1
lv:
shutdown -s -t 0
/k
/yLC6Ya9ut5bfTA/index.php
e2
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
exe
%USERPROFILE%
-unicode-
r=
.jpg
dll
Content-Type: multipart/form-data; boundary=----
2019
bi:
\
"
kernel32.dll
os:
abcdefghijklmnopqrstuvwxyz0123456789-_
dm:
AVG
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (53.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (35.5) |
| .exe | | | Win32 Executable (generic) (5.8) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:03:21 14:29:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 13606400 |
| InitializedDataSize: | 7665152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x36e935 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.8.708.689 |
| ProductVersionNumber: | 7.8.708.689 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Restorer Ultimate |
| CompanyName: | BitMart Inc. |
| FileDescription: | Restorer Ultimate |
| FileVersion: | 7, 8, 708, 689 |
| InternalName: | Restorer Ultimate |
| LegalCopyright: | Copyright (c) 2000-2013 BitMart Inc. |
| LegalTrademarks: | Copyright (c) 2000-2013 BitMart Inc. |
| OriginalFileName: | Restorer Ultimate.exe |
| ProductName: | Restorer Ultimate |
| ProductVersion: | 7, 8, 708, 689 |
Total processes
171
Monitored processes
34
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1760 -s 616 | C:\Windows\SysWOW64\WerFault.exe | — | TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Users\admin\Desktop\Clus-Blue.exe" | C:\Users\admin\Desktop\Clus-Blue.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 1240 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6676 -s 540 | C:\Windows\SysWOW64\WerFault.exe | — | shark.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\AppData\Local\Temp\TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe" | C:\Users\admin\AppData\Local\Temp\TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe | setup_patched.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 5.3.0.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1760 -s 596 | C:\Windows\SysWOW64\WerFault.exe | — | TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4112 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1760 -s 660 | C:\Windows\SysWOW64\WerFault.exe | — | TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6676 -s 156 | C:\Windows\SysWOW64\WerFault.exe | — | shark.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | "C:\ProgramData\Fidl\Clus-Blue.exe" | C:\ProgramData\Fidl\Clus-Blue.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4428 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\Kingfrae.srze | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 677
Read events
16 672
Write events
5
Delete events
0
Modification events
| (PID) Process: | (5892) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7668) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | shark |
Value: C:\ProgramData\shark.exe | |||
| (PID) Process: | (7416) ping.com | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7416) ping.com | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7416) ping.com | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
31
Suspicious files
9
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\Qt5Xml.dll | executable | |
MD5:EFEE87118A310EDB82A7A6AEEBAEC1C1 | SHA256:0A6D4E2FB47E8DB1D35EA70D66D40097469CBF61979FD10AA2BEB44A6CA06324 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\Framework.dll | executable | |
MD5:2207332818329E3CE4E5E020BA1B1F04 | SHA256:C554A0BD610BA0B10D8D92BB588FC86893B59985E4ED9316D340781C482FCAA2 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\Utility.dll | executable | |
MD5:48B0445F21B92190B1E199AD31F89CBC | SHA256:3094FB377E55EF2DEAE50B6C350EA2B6D37FD098D75CD3F874E5AF705A5BB3E8 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\Qt5Widgets.dll | executable | |
MD5:2BD07ACEF2FFD5AD8388B714D4F81995 | SHA256:250C3717663E4AB3CE50E4A53BC532BF0C0850D2917773DD7E482E733081A1A1 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\Qt5Gui.dll | executable | |
MD5:72AC63E9E9F015D6471DDE58297A4FC6 | SHA256:6B8A49B6B37D69213762C8F2C8A9970014364F4055F08A850D27C0343FBE00DE | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\msvcp120.dll | executable | |
MD5:EDEF53778EAAFE476EE523BE5C2AB67F | SHA256:92FAEDD18A29E1BD2DD27A1D805EA5AA3E73B954A625AF45A74F49D49506D20F | |||
| 8144 | Clus-Blue.exe | C:\ProgramData\Fidl\Clus-Blue.exe | executable | |
MD5:20BC61AA222AA74059F4D42872A76EB5 | SHA256:B1465F5CE1D0F83EF9B6086C81D8788B50C09BD329374BD3D04DC61807551435 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\libssl-1_1-x64.dll | executable | |
MD5:2574E9E3159CD45194EAC2591EADC73A | SHA256:2D7208FAE6767F5F01664448F4EA89C8009F75DB4C20FECDEA508A498A6A1223 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\libcrypto-1_1-x64.dll | executable | |
MD5:CF1DF078FA02C3F20A613FF9FACEEE46 | SHA256:0897F6EF6C7875F64ED82AD83473FD8EA119CFEAA959B0AB2B2F981C1DA7C679 | |||
| 7716 | setup_patched.exe | C:\Users\admin\AppData\Local\Temp\PD07FWUX4M0OBAY4OQSNOPU82I9SJK\Clus-Blue.exe | executable | |
MD5:20BC61AA222AA74059F4D42872A76EB5 | SHA256:B1465F5CE1D0F83EF9B6086C81D8788B50C09BD329374BD3D04DC61807551435 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
63
DNS requests
24
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
8024 | SIHClient.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.165.164.15:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.31.69:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7716 | setup_patched.exe | 23.197.130.99:443 | steamcommunity.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
techcastlev.live |
| malicious |
longitudde.digital |
| malicious |
hemispherexz.top |
| malicious |
equatorf.run |
| malicious |
latitudert.live |
| malicious |
climatologfy.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (equatorf .run) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (latitudert .live) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (climatologfy .top) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (longitudde .digital) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (hemispherexz .top) |
2196 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES DNS Query to Commonly Actor Abused Online Service (data-seed-prebsc-2-s1 .binance .org) |
1760 | TK1ZV41VVMC89YNDU53NY1GMLHIEV.exe | Misc activity | ET TA_ABUSED_SERVICES Observed Commonly Actor Abused Online Service Domain (data-seed-prebsc-2-s1 .binance .org in TLS SNI) |
7416 | ping.com | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7416 | ping.com | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |