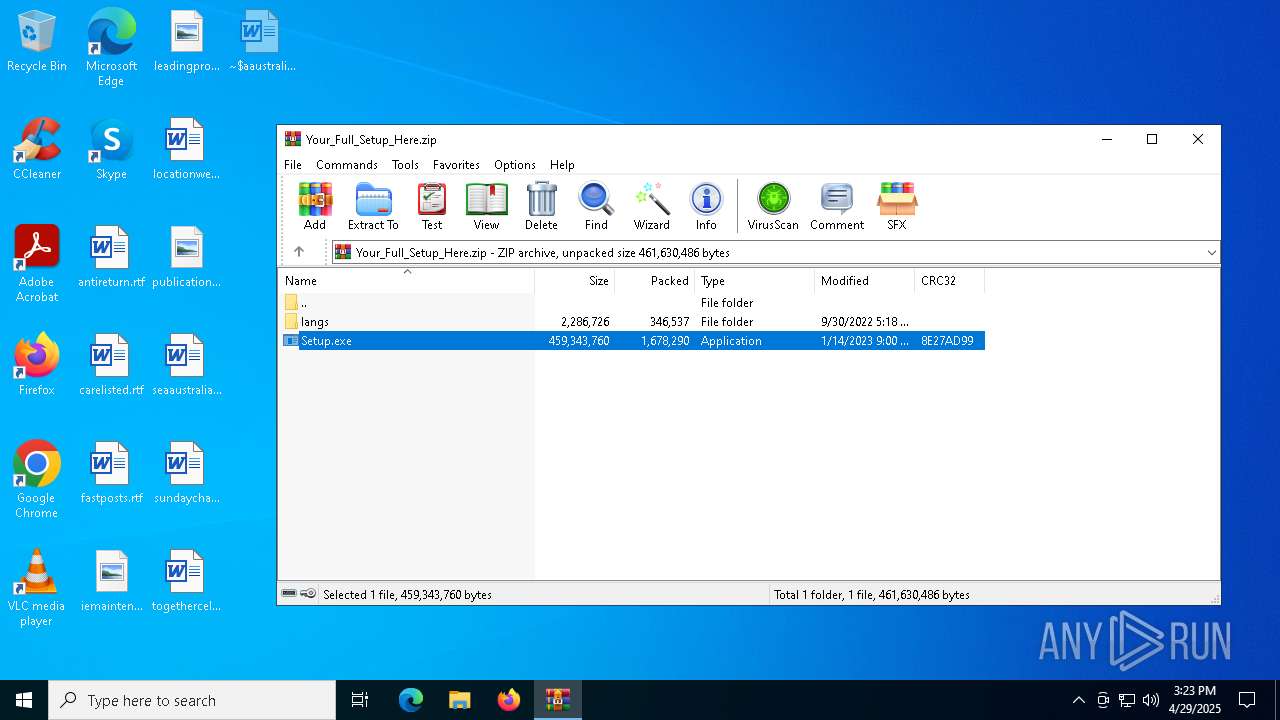
| File name: | Your_Full_Setup_Here.zip |
| Full analysis: | https://app.any.run/tasks/82213edb-1b26-4be5-9cca-8b400fffc113 |
| Verdict: | Malicious activity |
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | April 29, 2025, 15:20:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 3C0015F9BDC6A78CC683CE22DAF90487 |
| SHA1: | E351954C925A0F3BFAF944E9DBACD10D0918C388 |
| SHA256: | 42E8AADCE8780643C1BC9CFA59D466ECD0ABB555467CD210C383FA62FB562B49 |
| SSDEEP: | 98304:RzCic78jntzssZQbFUkeplthkrnX+/OOK5DY95ABFpBsPW4:LYW8y |
MALICIOUS
RACCOON has been detected (SURICATA)
- Setup.exe (PID: 2420)
Connects to the CnC server
- Setup.exe (PID: 2420)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4812)
- Setup.exe (PID: 2420)
Application launched itself
- Setup.exe (PID: 4120)
Connects to the server without a host name
- Setup.exe (PID: 2420)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 4812)
INFO
Manual execution by a user
- WINWORD.EXE (PID: 6564)
- WINWORD.EXE (PID: 6960)
Checks supported languages
- Setup.exe (PID: 4120)
- Setup.exe (PID: 2420)
Reads the machine GUID from the registry
- Setup.exe (PID: 4120)
- Setup.exe (PID: 2420)
Reads the computer name
- Setup.exe (PID: 4120)
- Setup.exe (PID: 2420)
Checks proxy server information
- Setup.exe (PID: 2420)
- slui.exe (PID: 6584)
Reads the software policy settings
- slui.exe (PID: 1272)
- slui.exe (PID: 6584)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 732)
- WinRAR.exe (PID: 4812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:09:30 22:48:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | langs/ |
Total processes
149
Monitored processes
13
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Laptop Simulator Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3300 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\dummy\DESKTOP-JGLLJLD-20190323-1136.log | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "DAA6951F-C41D-442B-A0EE-63338C859045" "154C0989-4F21-4AF4-9E41-0EC8175F0D19" "6564" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 4120 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Laptop Simulator Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4200 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4812 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Your_Full_Setup_Here.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Laptop Simulator Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6248 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "C738843B-2B00-4430-9F90-90D948D04CC1" "315087B5-AADB-440C-9682-F7FD014E1C10" "6960" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
38 161
Read events
37 938
Write events
171
Delete events
52
Modification events
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Your_Full_Setup_Here.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
0
Suspicious files
31
Text files
26
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\Danish.ini | text | |
MD5:5F50B22DE0EFB245CD3B8F2FB50A6D3D | SHA256:59DF77A75ACA7C0A8574F6D4B5BE5632908C4FEA8634F4748E36FF6FEE40E317 | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\Hungarian.ini | text | |
MD5:7591DF7FAE4342CBC7A0706E1B28E87B | SHA256:FE9997629D296908247A2E82DA6C369E2EA7EB4C87B12FC7C8D3ECB3E6FC320D | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\English.ini | text | |
MD5:525CE1C02CA53F9C63CB697ED3AAE899 | SHA256:0F9D467F6BB6F682C0D1351B26038950C73720F2BFC0741EC1C7BFAB2046D75F | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Your_Full_Setup_Here\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\Kazakh.ini | text | |
MD5:FE2B5687F2DE60CB55629FD7F0CA9A21 | SHA256:1FDE00989B3BAEB67E6B1F8654CD2FC7216A40A4C5A5A9A64D03D47EE95E76BE | |||
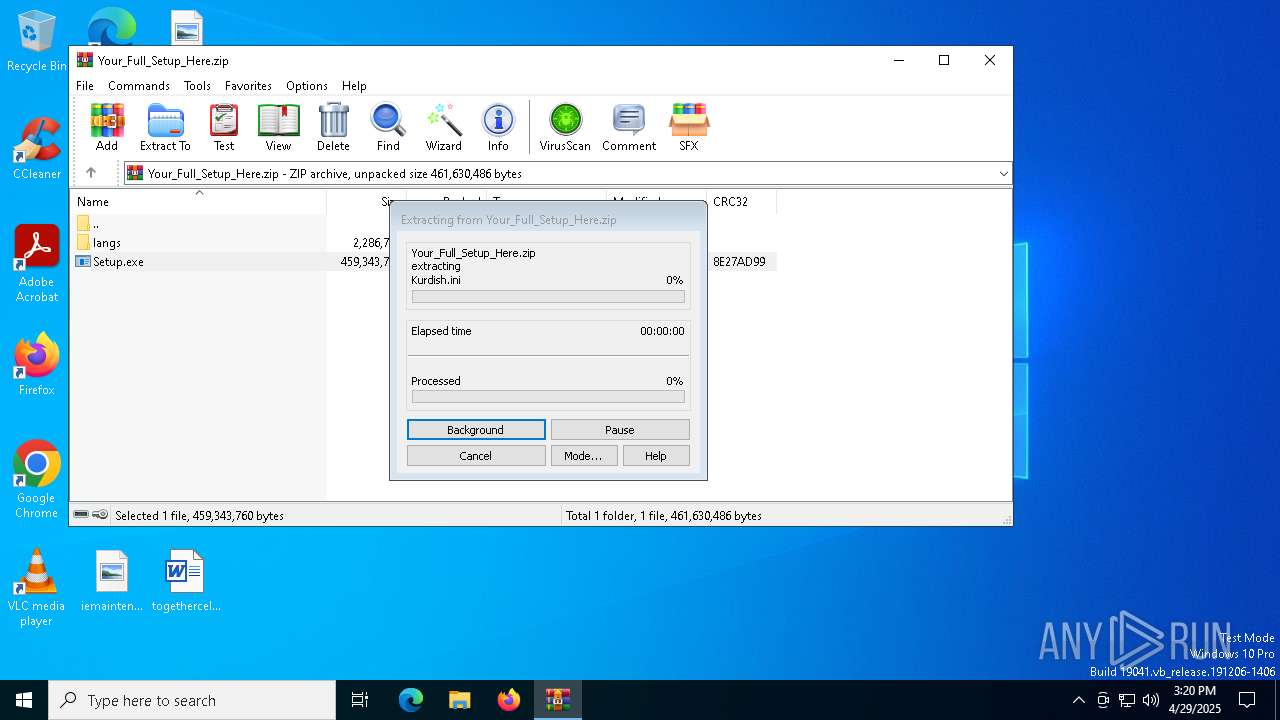
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\Kurdish.ini | text | |
MD5:AF61B416403963D653F5008AABA82E03 | SHA256:94AC43CB7EB95277DB44616A53B23E9174415377B4B3B98A1BDFC98D06A40A4B | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\Korean.ini | text | |
MD5:EFAE0C78BE2ABE2920C78B9D4785AB45 | SHA256:AD556989F6E4A683D9668E41D2D7175B7B46847C2EEF26188B9075FC600D0132 | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\TradChinese.ini | text | |
MD5:DC01555F89E044192A9AD584B62E41A7 | SHA256:EB8FC39F2551834010F3748D81E5F842A1B4E27ADB87E425B764BB9152B55CB1 | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.34463\langs\SimpChinese.ini | text | |
MD5:7AAD044A68D89D8BB5A202F8BC69D87C | SHA256:1BFA864F7012E64F5C1656FC5636EA29E87E2A45B5EB2C31A3B20643FDD8AD4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
62
DNS requests
24
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2420 | Setup.exe | POST | 404 | 83.217.11.11:80 | http://83.217.11.11/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6564 | WINWORD.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6564 | WINWORD.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6564 | WINWORD.EXE | 23.48.23.62:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
2420 | Setup.exe | 83.217.11.11:80 | — | Okay-Telecom Ltd. | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2420 | Setup.exe | A Network Trojan was detected | ET MALWARE Win32/RecordBreaker CnC Checkin M1 |
2420 | Setup.exe | A Network Trojan was detected | ET MALWARE Win32/RecordBreaker - Observed UA M5 (23591) |