| File name: | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe |
| Full analysis: | https://app.any.run/tasks/357320c2-5726-4da6-a8d4-177def1b84b6 |
| Verdict: | Malicious activity |
| Threats: | NetSupport RAT is a malicious adaptation of the legitimate NetSupport Manager, a remote access tool used for IT support, which cybercriminals exploit to gain unauthorized control over systems. It has gained significant traction due to its sophisticated evasion techniques, widespread distribution campaigns, and the challenge it poses to security professionals who must distinguish between legitimate and malicious uses of the underlying software. |
| Analysis date: | January 30, 2024, 19:21:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 553AC66062429D5A0423D4B286E53C31 |
| SHA1: | 0ACEA7BCAEA5C8A9A4E19232E3CA114863AA6968 |
| SHA256: | 428D51259AD927C58EA5ABB9ECA6E0DCE4FEE5D97E20F78ABBA194C8C4FAADFD |
| SSDEEP: | 12288:eRsTcbkyoo5SRla8yQoigLC7ZORW8+7j3NQzY88PhBVj:eRccbkyB5SRQ8yQoBLCVORWZ7j3N0Q |
MALICIOUS
Creates a writable file in the system directory
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
Drops the executable file immediately after the start
- drvinst.exe (PID: 2472)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 624)
NETSUPPORT has been detected (SURICATA)
- client32.exe (PID: 2308)
Actions looks like stealing of personal data
- client32.exe (PID: 2480)
SUSPICIOUS
Reads settings of System Certificates
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
Reads the Internet Settings
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
Adds/modifies Windows certificates
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
- winst64.exe (PID: 2644)
Creates files in the driver directory
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
Checks Windows Trust Settings
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
Drops a system driver (possible attempt to evade defenses)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
Executable content was dropped or overwritten
- drvinst.exe (PID: 2472)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 624)
Reads the Windows owner or organization settings
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
The process executes VB scripts
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
The process downloads a VBScript from the remote host
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
Connects to unusual port
- client32.exe (PID: 2308)
INFO
Checks supported languages
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
- client32.exe (PID: 2480)
- client32.exe (PID: 2308)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
- client32.exe (PID: 1748)
Drops the executable file immediately after the start
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
Reads the computer name
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
- client32.exe (PID: 2480)
- client32.exe (PID: 2308)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
- client32.exe (PID: 1748)
Reads the machine GUID from the registry
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 624)
- client32.exe (PID: 2308)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 2480)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
Reads Environment values
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
Create files in a temporary directory
- 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe (PID: 312)
- winst64.exe (PID: 2644)
Drop NetSupport executable file
- drvinst.exe (PID: 2472)
- winst64.exe (PID: 2644)
- drvinst.exe (PID: 624)
Executes as Windows Service
- client32.exe (PID: 2308)
Creates files in the program directory
- client32.exe (PID: 2308)
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
Application launched itself
- client32.exe (PID: 2308)
Reads Windows Product ID
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
Reads CPU info
- client32.exe (PID: 2480)
- client32.exe (PID: 2296)
- client32.exe (PID: 2328)
- client32.exe (PID: 284)
- client32.exe (PID: 2000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:01:03 19:43:20+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 460288 |
| InitializedDataSize: | 184320 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x725ae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.0 |
| ProductVersionNumber: | 1.0.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Configurator |
| CompanyName: | - |
| FileDescription: | Configurator |
| FileVersion: | 1.0.1.0 |
| InternalName: | Configurator.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | Configurator.exe |
| ProductName: | Configurator |
| ProductVersion: | 1.0.1.0 |
| AssemblyVersion: | 1.0.1.0 |
Total processes
82
Monitored processes
24
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files (x86)\NetSupport\NetSupport Manager\client32.exe" * /VistaUI | C:\Program Files (x86)\NetSupport\NetSupport Manager\client32.exe | client32.exe | ||||||||||||
User: SYSTEM Company: NetSupport Ltd Integrity Level: SYSTEM Description: NetSupport Client Application Exit code: 9 Version: V14.02 Modules
| |||||||||||||||
| 312 | "C:\Users\admin\AppData\Local\Temp\428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe" | C:\Users\admin\AppData\Local\Temp\428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Configurator Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 624 | DrvInst.exe "2" "211" "ROOT\DISPLAY\0000" "C:\Windows\INF\oem4.inf" "gdihook5.inf:gdihook5.Mfg.NTamd64:gdihook5:11.11.0.704:pci_gdihook5_hwid" "6d3d268df" "0000000000000570" "00000000000005D8" "00000000000005DC" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | "cscript.exe" C:\Windows\system32\Printing_Admin_Scripts\en-US\prnport.vbs -a -r NSM001 -h 127.0.0.1 -o raw -n 49169 | C:\Windows\SysWOW64\cscript.exe | — | client32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 892 | "cscript.exe" C:\Windows\system32\Printing_Admin_Scripts\en-US\prnport.vbs -d -r NSM001 | C:\Windows\SysWOW64\cscript.exe | — | client32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 892 | "cscript.exe" C:\Windows\system32\Printing_Admin_Scripts\en-US\prnport.vbs -d -r NSM001 | C:\Windows\SysWOW64\cscript.exe | — | client32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1748 | "C:\Program Files (x86)\NetSupport\NetSupport Manager\client32.exe" * /VistaUI | C:\Program Files (x86)\NetSupport\NetSupport Manager\client32.exe | — | client32.exe | |||||||||||
User: SYSTEM Company: NetSupport Ltd Integrity Level: SYSTEM Description: NetSupport Client Application Exit code: 0 Version: V14.02 Modules
| |||||||||||||||
| 1808 | "cscript.exe" C:\Windows\system32\Printing_Admin_Scripts\en-US\prnport.vbs -d -r NSM001 | C:\Windows\SysWOW64\cscript.exe | — | client32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1928 | "cscript.exe" C:\Windows\system32\Printing_Admin_Scripts\en-US\prnport.vbs -a -r NSM001 -h 127.0.0.1 -o raw -n 49166 | C:\Windows\SysWOW64\cscript.exe | — | client32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2000 | "C:\Program Files (x86)\NetSupport\NetSupport Manager\client32.exe" * /VistaUI | C:\Program Files (x86)\NetSupport\NetSupport Manager\client32.exe | client32.exe | ||||||||||||
User: SYSTEM Company: NetSupport Ltd Integrity Level: SYSTEM Description: NetSupport Client Application Exit code: 9 Version: V14.02 Modules
| |||||||||||||||
Total events
84 652
Read events
84 577
Write events
74
Delete events
1
Modification events
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA2030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3491D00000001000000100000002E0D6875874A44C820912E85E964CFDB140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B40B000000010000001C0000005300650063007400690067006F002000280041004100410029000000620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF453000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000497904B0EB8719AC47B0BC11519B74D00F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B0601050507030853000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF40B000000010000001C0000005300650063007400690067006F002000280041004100410029000000140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B41D00000001000000100000002E0D6875874A44C820912E85E964CFDB030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3491900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA2200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (312) 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2644) winst64.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2644) winst64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2644) winst64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD2000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
Executable files
19
Suspicious files
28
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | C:\Users\admin\AppData\Local\Temp\sgzyltd0.dge\4lexaita.vmf | — | |
MD5:— | SHA256:— | |||
| 312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | C:\Users\admin\AppData\Local\Temp\sgzyltd0.dge\DotNetZip-2kmimyak.tmp | — | |
MD5:— | SHA256:— | |||
| 312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | C:\Users\admin\AppData\Local\Temp\sgzyltd0.dge\whopper.msi | — | |
MD5:— | SHA256:— | |||
| 2472 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{4a44d450-2fb4-7230-d961-5b60f584697f}\x64\SETEA7E.tmp | executable | |
MD5:52B88EB20BEB3B34A692A4CAE0FF2196 | SHA256:2B675E9C27D3FB01CB9DF2583B380DE8DC8C0D5BBBE18AF458F90B47C6D62B03 | |||
| 312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | C:\Users\admin\AppData\Local\Temp\sgzyltd0.dge\DotNetZip-cyngwq5d.tmp | text | |
MD5:F21C50AA6DC247C7B4284B61E76C525F | SHA256:587A341B24EAB5E18FF78169D9BA5DC15181FC4390B801CD2C7F549440A4D24A | |||
| 312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | C:\Users\admin\AppData\Local\Temp\sgzyltd0.dge\NSM.lic | text | |
MD5:D2C2217861F5535686409D80A0867F6F | SHA256:AF9C79CF3AF6A7E969208DA78DFCFAC54D6F956545B46F434D0E447CFF94807B | |||
| 312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | C:\Users\admin\AppData\Local\Temp\sgzyltd0.dge\DotNetZip-mdfci3x4.tmp | text | |
MD5:D2C2217861F5535686409D80A0867F6F | SHA256:AF9C79CF3AF6A7E969208DA78DFCFAC54D6F956545B46F434D0E447CFF94807B | |||
| 2644 | winst64.exe | C:\Windows\system32\drivers\pcisys.sys | executable | |
MD5:84DEE0F25FE97868071202065DAB63BB | SHA256:DE5ACE5C2A02AFB01A90BA39B305A8F3C783883012432D22912910EAD44AD60A | |||
| 2644 | winst64.exe | C:\Users\admin\AppData\Local\Temp\{7fdf3548-90f3-7ed6-d753-d531305bb446}\x64\SETEA10.tmp | executable | |
MD5:52B88EB20BEB3B34A692A4CAE0FF2196 | SHA256:2B675E9C27D3FB01CB9DF2583B380DE8DC8C0D5BBBE18AF458F90B47C6D62B03 | |||
| 2644 | winst64.exe | C:\Windows\system32\clhook4.dll | executable | |
MD5:38935DB0DD061269B7D79A1D287E750C | SHA256:5A7E162064982B196F646DC3F4C4A5CC50858DA13BCFBA268F8BA0A6D9ABB741 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
11
DNS requests
5
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2216 | msiexec.exe | GET | 200 | 23.48.23.31:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a32568fd1e7f5a7a | unknown | compressed | 65.2 Kb | unknown |
2308 | client32.exe | GET | 404 | 172.67.68.212:80 | http://geo.netsupportsoftware.com/location/loca.asp | unknown | html | 315 b | unknown |
2308 | client32.exe | GET | 404 | 172.67.68.212:80 | http://geo.netsupportsoftware.com/location/loca.asp | unknown | html | 315 b | unknown |
2308 | client32.exe | GET | 404 | 172.67.68.212:80 | http://geo.netsupportsoftware.com/location/loca.asp | unknown | html | 315 b | unknown |
2308 | client32.exe | GET | 101 | 51.195.145.91:2533 | http://51.195.145.91:2533/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
312 | 428d51259ad927c58ea5abb9eca6e0dce4fee5d97e20f78abba194c8c4faadfd.exe | 198.187.29.22:443 | niklomertie.shop | NAMECHEAP-NET | US | unknown |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
2216 | msiexec.exe | 23.48.23.31:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2308 | client32.exe | 172.67.68.212:80 | geo.netsupportsoftware.com | CLOUDFLARENET | US | unknown |
2308 | client32.exe | 51.195.145.91:2533 | zmezzw.duckdns.org | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
niklomertie.shop |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
geo.netsupportsoftware.com |
| unknown |
zmezzw.duckdns.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2308 | client32.exe | Potential Corporate Privacy Violation | ET POLICY NetSupport GeoLocation Lookup Request |
2308 | client32.exe | Potential Corporate Privacy Violation | ET POLICY NetSupport GeoLocation Lookup Request |
2308 | client32.exe | Potential Corporate Privacy Violation | ET POLICY NetSupport GeoLocation Lookup Request |
352 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
352 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
352 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
352 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2308 | client32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Websocket update request to external network |
Process | Message |
|---|---|
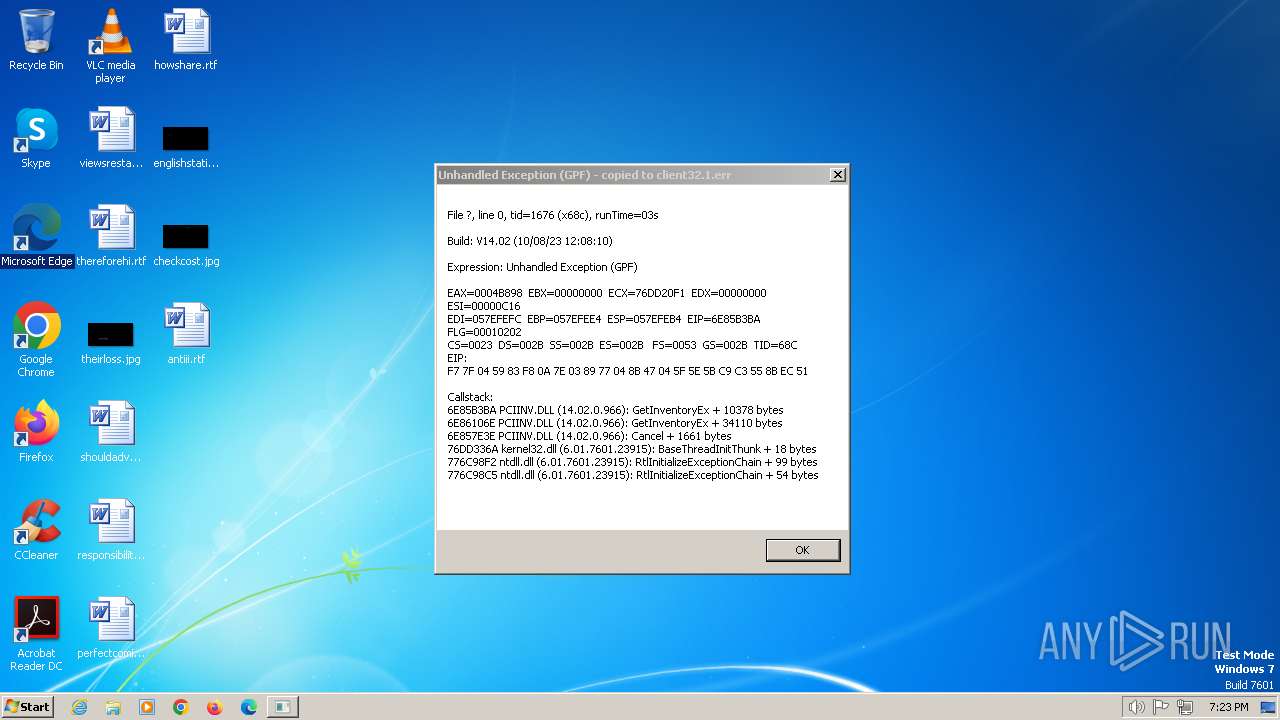
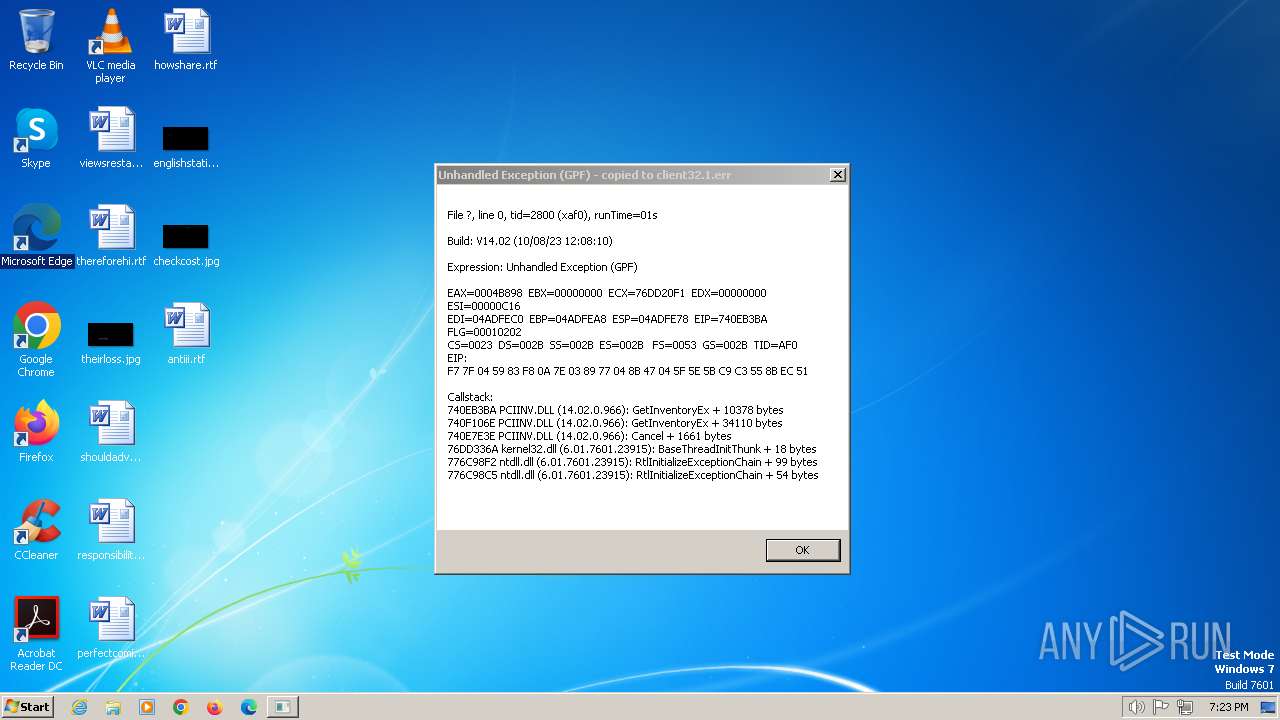
client32.exe | Exception caught at 6e85b3ba. Trying minidump.
|
client32.exe | EAX=0004B898 EBX=00000000 ECX=76DD20F1 EDX=00000000 ESI=00000C16
EDI=057EFEFC EBP=057EFEE4 ESP=057EFEB4 EIP=6E85B3BA FLG=00010202
CS=0023 DS=002B SS=002B ES=002B FS=0053 GS=002B TID=68C
EIP:
F7 7F 04 59 83 F8 0A 7E 03 89 77 04 8B 47 04 5F 5E 5B C9 C3 55 8B EC 51
Callstack:
6E85B3BA PCIINV.DLL (14.02.0.966): GetInventoryEx + 10378 bytes
6E86106E PCIINV.DLL (14.02.0.966): GetInventoryEx + 34110 bytes
6E857E3E PCIINV.DLL (14.02.0.966): Cancel + 1661 bytes
76DD336A kernel32.dll (6.01.7601.23915): BaseThreadInitThunk + 18 bytes
776C98F2 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 99 bytes
776C98C5 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 54 bytes
|
client32.exe | Assert, tid=68c thread=, tid=1676 (x68c), runTime=03s exp=EAX=0004B898 EBX=00000000 ECX=76DD20F1 EDX=00000000 ESI=00000C16
EDI=057EFEFC EBP=057EFEE4 ESP=057EFEB4 EIP=6E85B3BA FLG=00010202
CS=0023 DS=002B SS=002B ES=002B FS=0053 GS=002B TID=68C
EIP:
F7 7F 04 59 83 F8 0A 7E 03 89 77 04 8B 47 04 5F 5E 5B C9 C3 55 8B EC 51
Callstack:
6E85B3BA PCIINV.DLL (14.02.0.966): GetInventoryEx + 10378 bytes
6E86106E PCIINV.DLL (14.02.0.966): GetInventoryEx + 34110 bytes
6E857E3E PCIINV.DLL (14.02.0.966): Cancel + 1661 bytes
76DD336A kernel32.dll (6.01.7601.23915): BaseThreadInitThunk + 18 bytes
776C98F2 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 99 bytes
776C98C5 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 54 bytes
@ ?:0
|
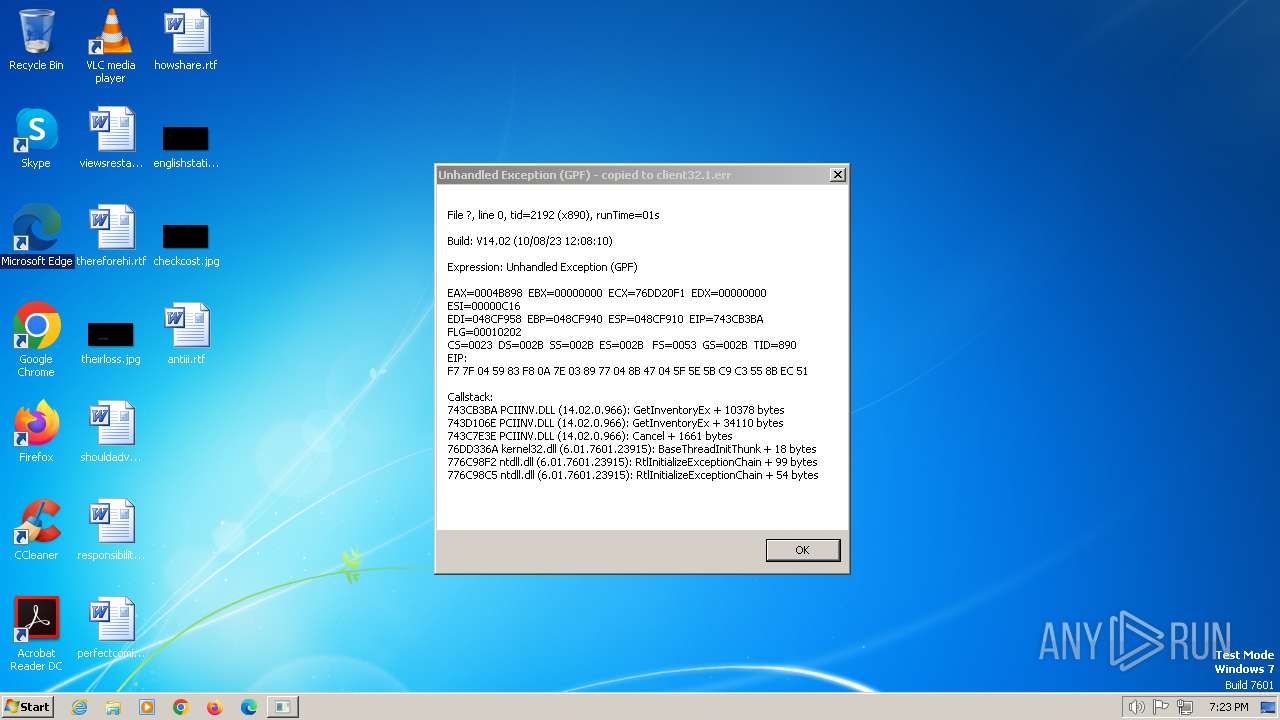
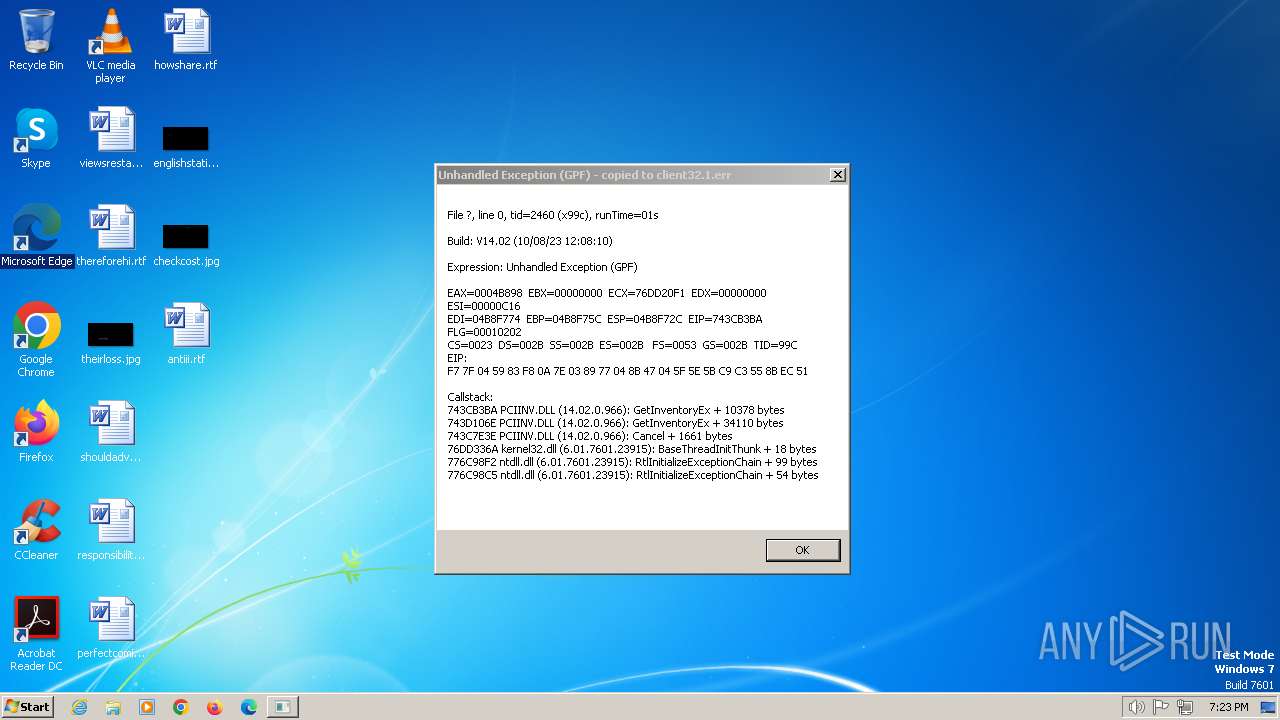
client32.exe | Exception caught at 743cb3ba. Trying minidump.
|
client32.exe | EAX=0004B898 EBX=00000000 ECX=76DD20F1 EDX=00000000 ESI=00000C16
EDI=048CF958 EBP=048CF940 ESP=048CF910 EIP=743CB3BA FLG=00010202
CS=0023 DS=002B SS=002B ES=002B FS=0053 GS=002B TID=890
EIP:
F7 7F 04 59 83 F8 0A 7E 03 89 77 04 8B 47 04 5F 5E 5B C9 C3 55 8B EC 51
Callstack:
743CB3BA PCIINV.DLL (14.02.0.966): GetInventoryEx + 10378 bytes
743D106E PCIINV.DLL (14.02.0.966): GetInventoryEx + 34110 bytes
743C7E3E PCIINV.DLL (14.02.0.966): Cancel + 1661 bytes
76DD336A kernel32.dll (6.01.7601.23915): BaseThreadInitThunk + 18 bytes
776C98F2 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 99 bytes
776C98C5 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 54 bytes
|
client32.exe | Assert, tid=890 thread=, tid=2192 (x890), runTime=01s exp=EAX=0004B898 EBX=00000000 ECX=76DD20F1 EDX=00000000 ESI=00000C16
EDI=048CF958 EBP=048CF940 ESP=048CF910 EIP=743CB3BA FLG=00010202
CS=0023 DS=002B SS=002B ES=002B FS=0053 GS=002B TID=890
EIP:
F7 7F 04 59 83 F8 0A 7E 03 89 77 04 8B 47 04 5F 5E 5B C9 C3 55 8B EC 51
Callstack:
743CB3BA PCIINV.DLL (14.02.0.966): GetInventoryEx + 10378 bytes
743D106E PCIINV.DLL (14.02.0.966): GetInventoryEx + 34110 bytes
743C7E3E PCIINV.DLL (14.02.0.966): Cancel + 1661 bytes
76DD336A kernel32.dll (6.01.7601.23915): BaseThreadInitThunk + 18 bytes
776C98F2 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 99 bytes
776C98C5 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 54 bytes
@ ?:0
|
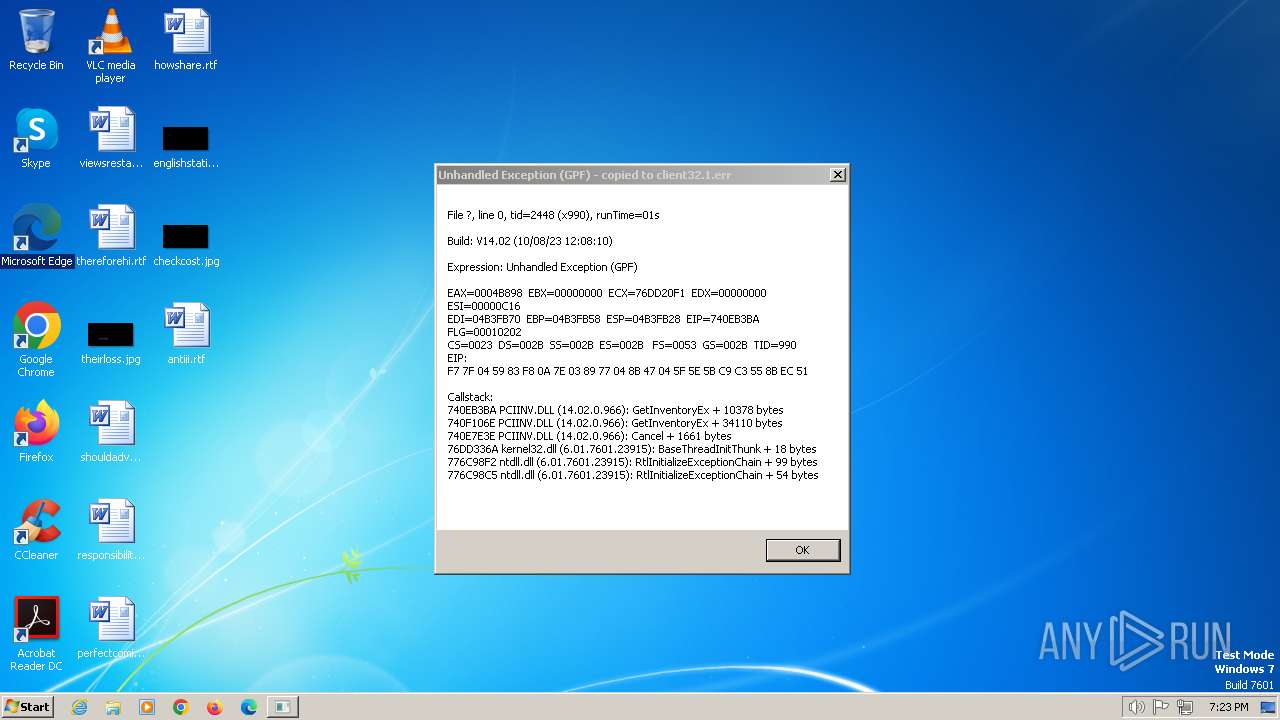
client32.exe | Exception caught at 740eb3ba. Trying minidump.
|
client32.exe | EAX=0004B898 EBX=00000000 ECX=76DD20F1 EDX=00000000 ESI=00000C16
EDI=04B3FB70 EBP=04B3FB58 ESP=04B3FB28 EIP=740EB3BA FLG=00010202
CS=0023 DS=002B SS=002B ES=002B FS=0053 GS=002B TID=990
EIP:
F7 7F 04 59 83 F8 0A 7E 03 89 77 04 8B 47 04 5F 5E 5B C9 C3 55 8B EC 51
Callstack:
740EB3BA PCIINV.DLL (14.02.0.966): GetInventoryEx + 10378 bytes
740F106E PCIINV.DLL (14.02.0.966): GetInventoryEx + 34110 bytes
740E7E3E PCIINV.DLL (14.02.0.966): Cancel + 1661 bytes
76DD336A kernel32.dll (6.01.7601.23915): BaseThreadInitThunk + 18 bytes
776C98F2 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 99 bytes
776C98C5 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 54 bytes
|
client32.exe | Assert, tid=990 thread=, tid=2448 (x990), runTime=01s exp=EAX=0004B898 EBX=00000000 ECX=76DD20F1 EDX=00000000 ESI=00000C16
EDI=04B3FB70 EBP=04B3FB58 ESP=04B3FB28 EIP=740EB3BA FLG=00010202
CS=0023 DS=002B SS=002B ES=002B FS=0053 GS=002B TID=990
EIP:
F7 7F 04 59 83 F8 0A 7E 03 89 77 04 8B 47 04 5F 5E 5B C9 C3 55 8B EC 51
Callstack:
740EB3BA PCIINV.DLL (14.02.0.966): GetInventoryEx + 10378 bytes
740F106E PCIINV.DLL (14.02.0.966): GetInventoryEx + 34110 bytes
740E7E3E PCIINV.DLL (14.02.0.966): Cancel + 1661 bytes
76DD336A kernel32.dll (6.01.7601.23915): BaseThreadInitThunk + 18 bytes
776C98F2 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 99 bytes
776C98C5 ntdll.dll (6.01.7601.23915): RtlInitializeExceptionChain + 54 bytes
@ ?:0
|
client32.exe | Exception caught at 743cb3ba. Trying minidump.
|