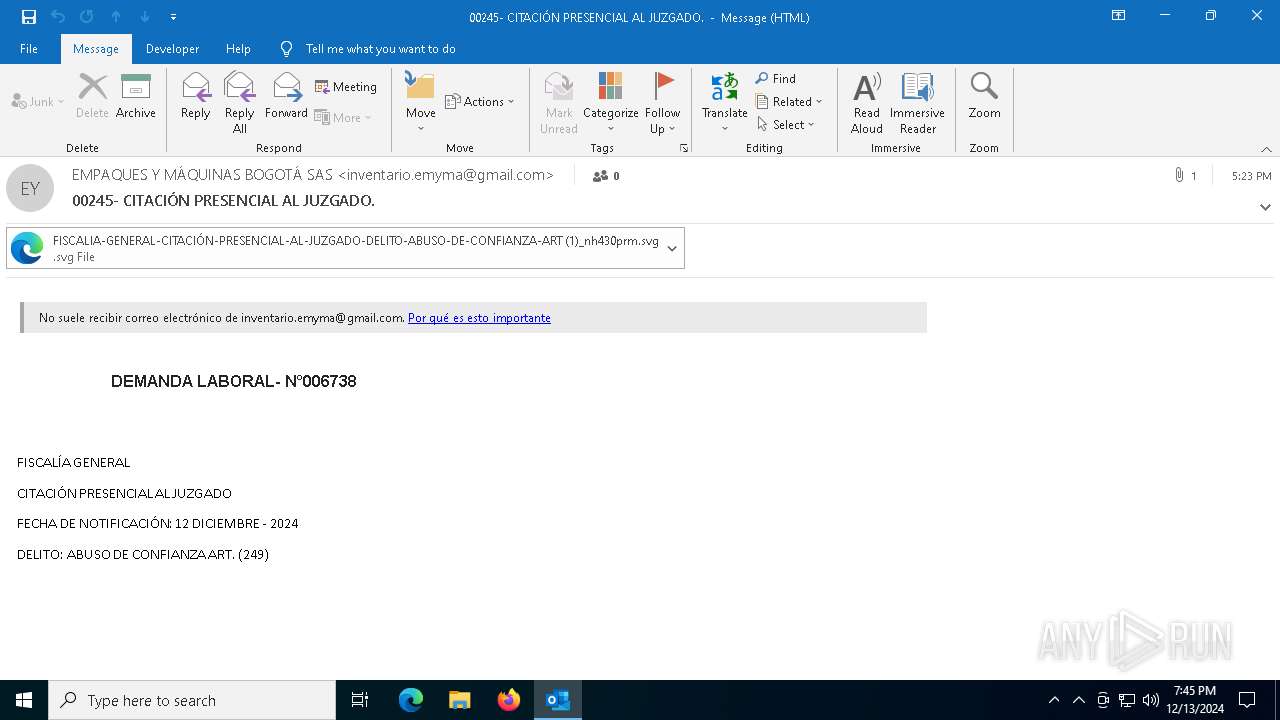
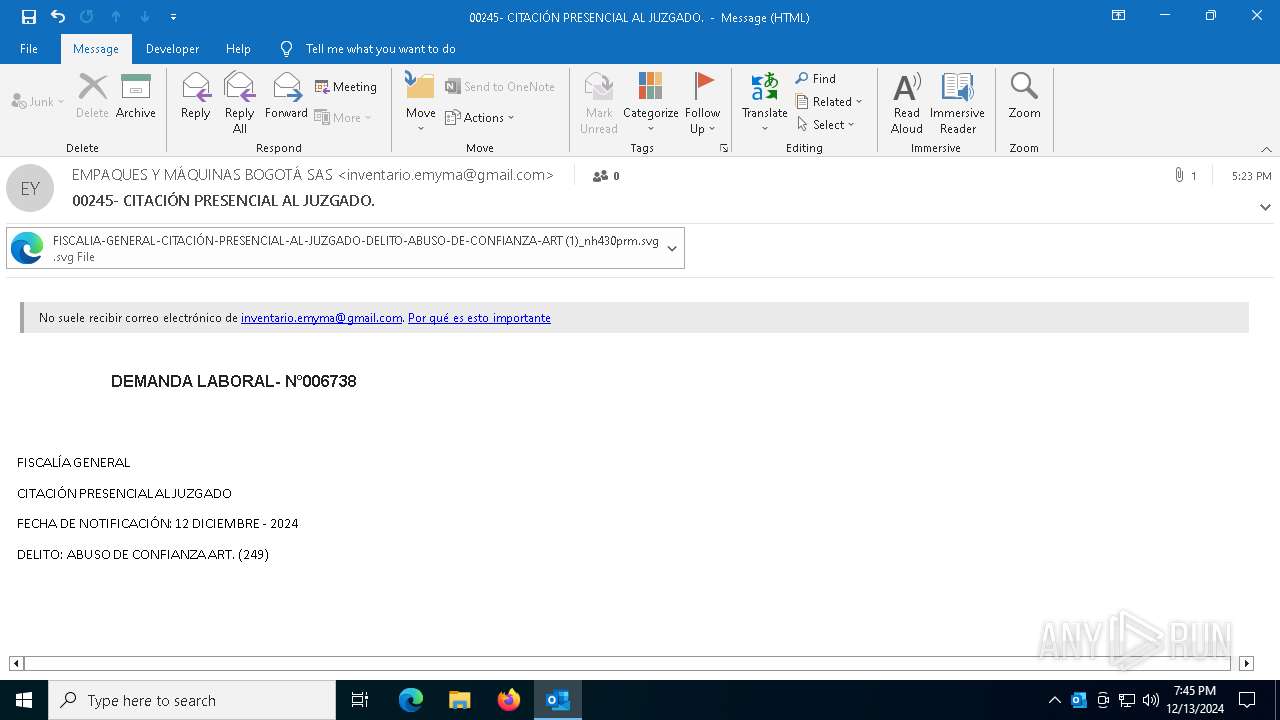
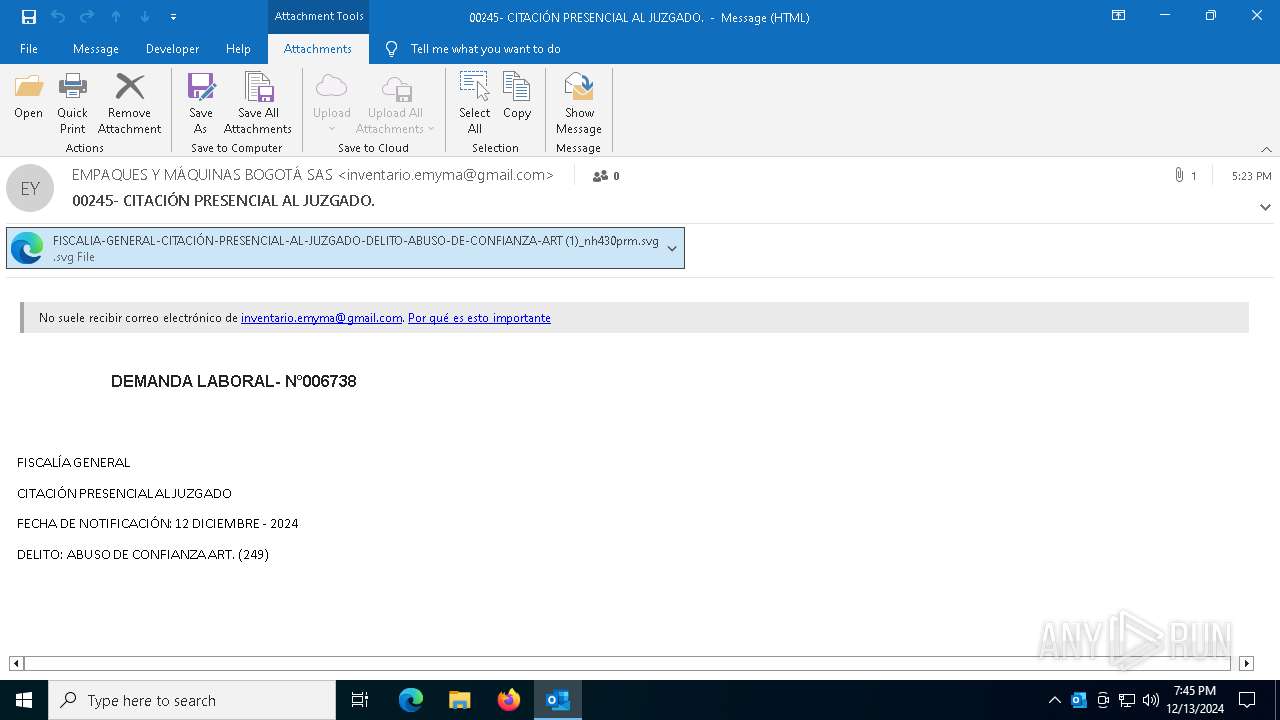
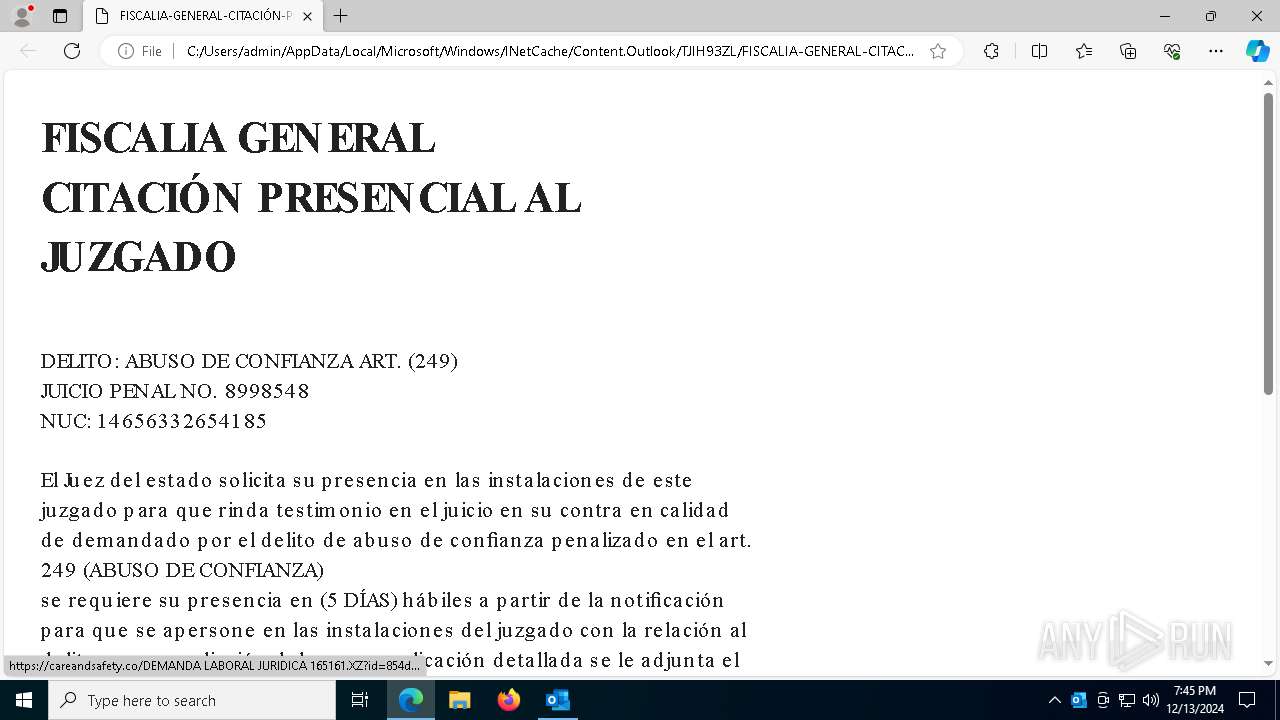
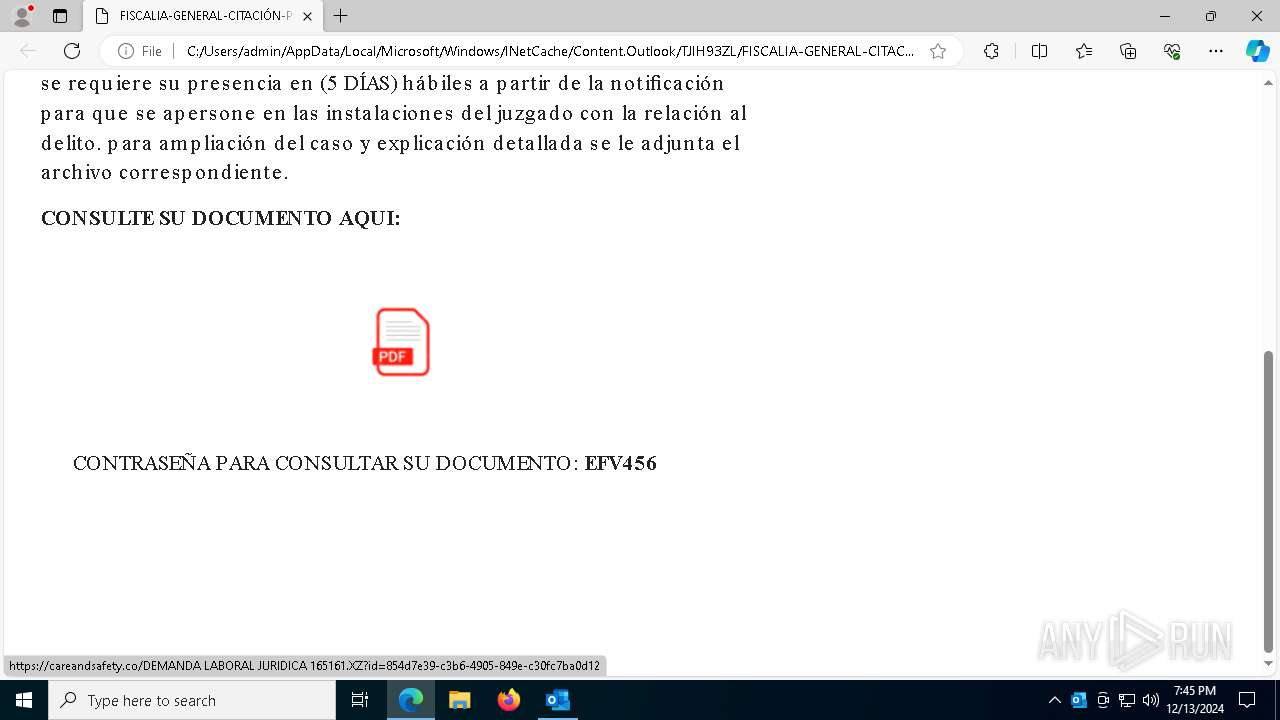
| File name: | 00245- CITACIÓN PRESENCIAL AL JUZGADO..msg |
| Full analysis: | https://app.any.run/tasks/1a6c81d0-dbef-4a2e-b565-d1b7959ed299 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | December 13, 2024, 19:45:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | BC8C4447795CDB9AF8C983B5DEEF4E40 |
| SHA1: | 7E4C689FF261D752561D850866540BC944BDBAFF |
| SHA256: | 42238633A6D9E524AB37E435E8C52A953B0B53E3F9763FD0CD9FA71643EAF341 |
| SSDEEP: | 1536:1fBPrqWLRFWAWRYiwWdATmd4WBartTWNtvML3kf/6aFp/ML3kf/6aFpV:1fZryPPASd4a25aU5a |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 7316)
- dllhost.exe (PID: 7036)
- dllhost.exe (PID: 7456)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 8168)
- cmd.exe (PID: 1612)
REMCOS has been detected
- svchost.exe (PID: 8140)
Connects to the CnC server
- svchost.exe (PID: 8140)
REMCOS mutex has been found
- svchost.exe (PID: 8140)
REMCOS has been detected (SURICATA)
- svchost.exe (PID: 8140)
Deletes a file (SCRIPT)
- wscript.exe (PID: 7552)
Actions looks like stealing of personal data
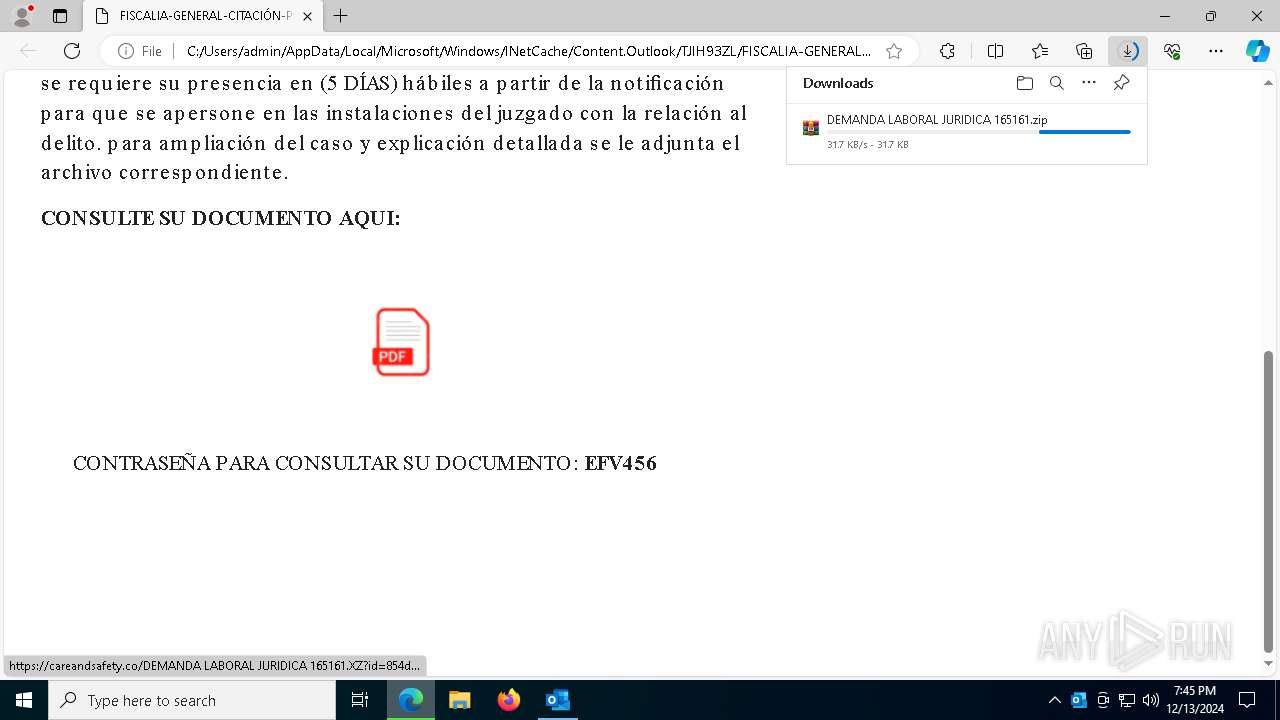
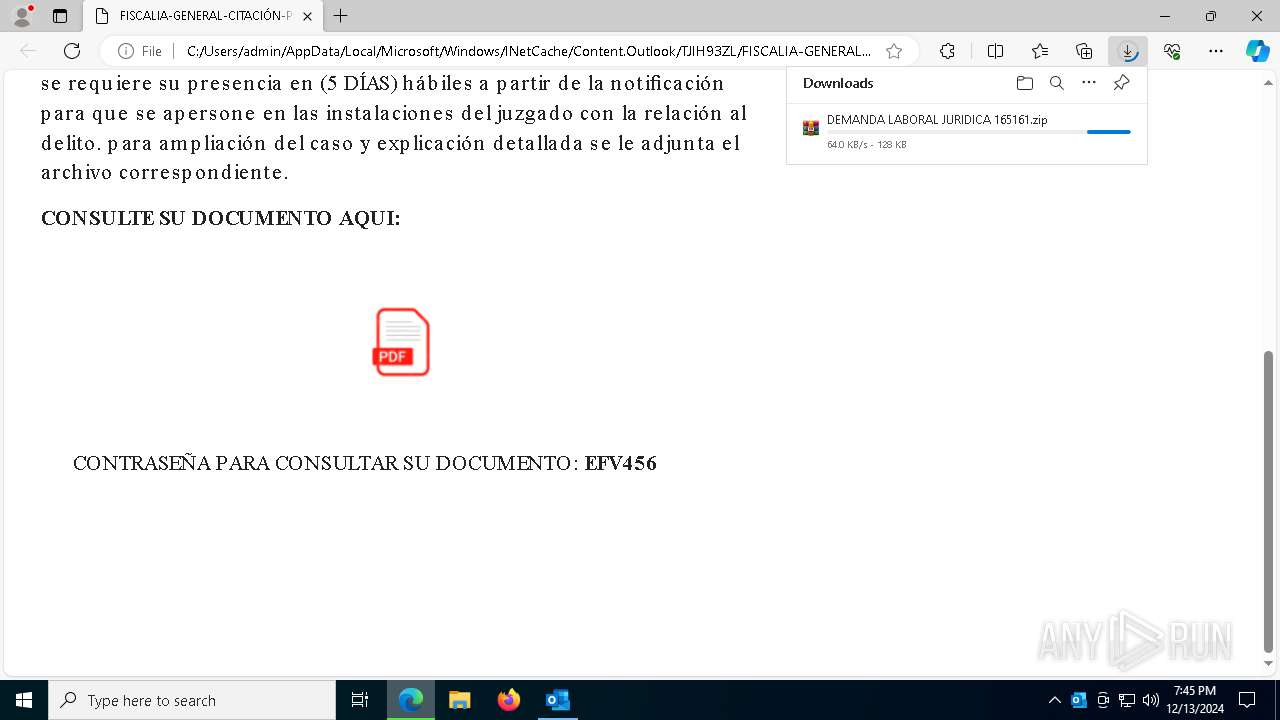
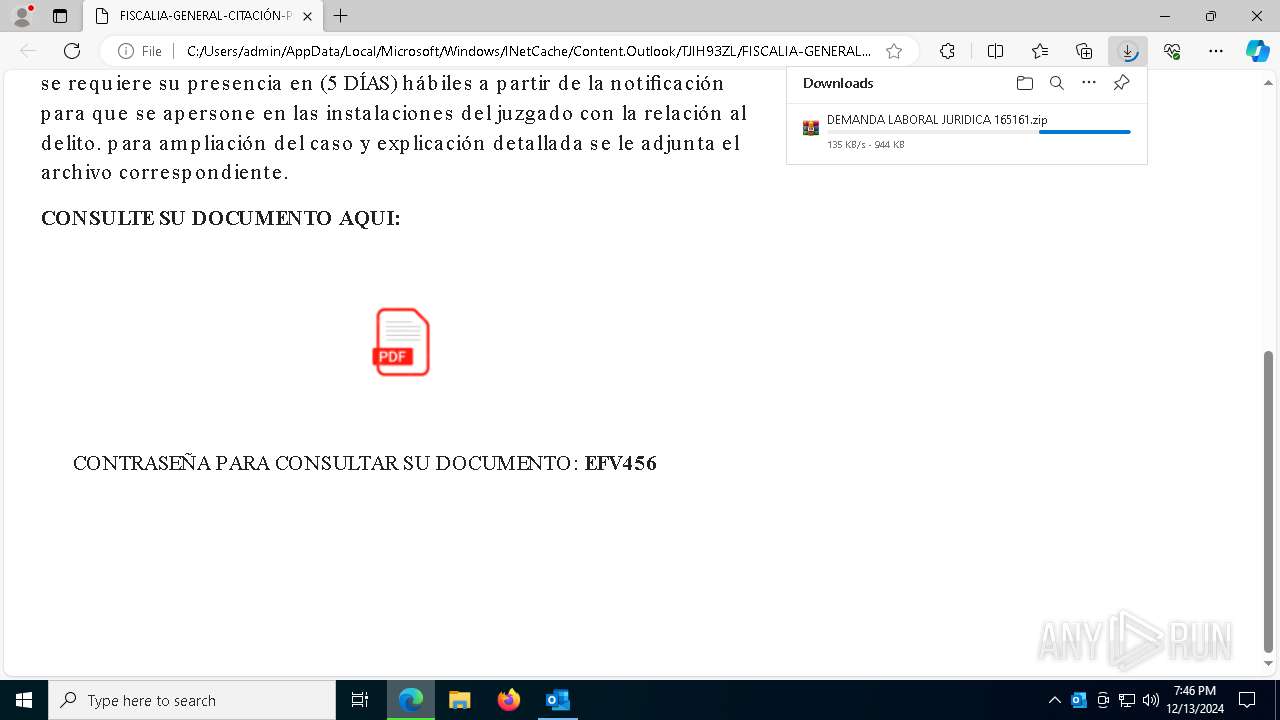
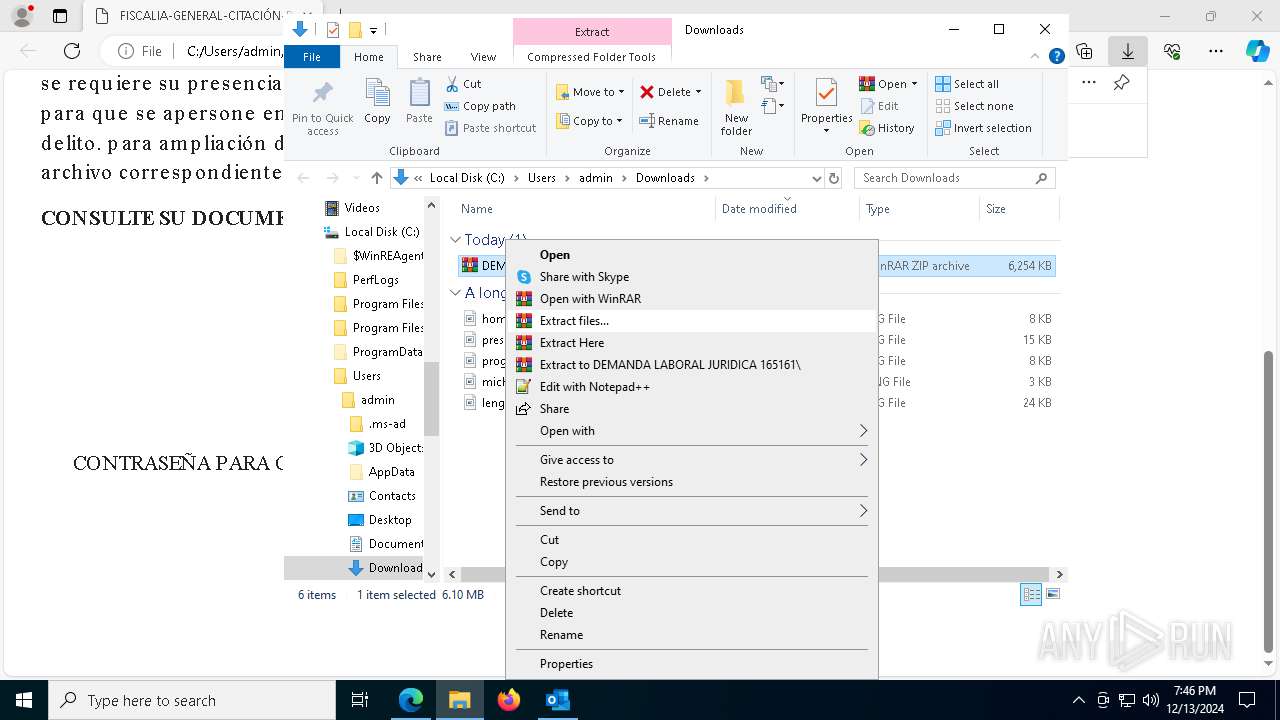
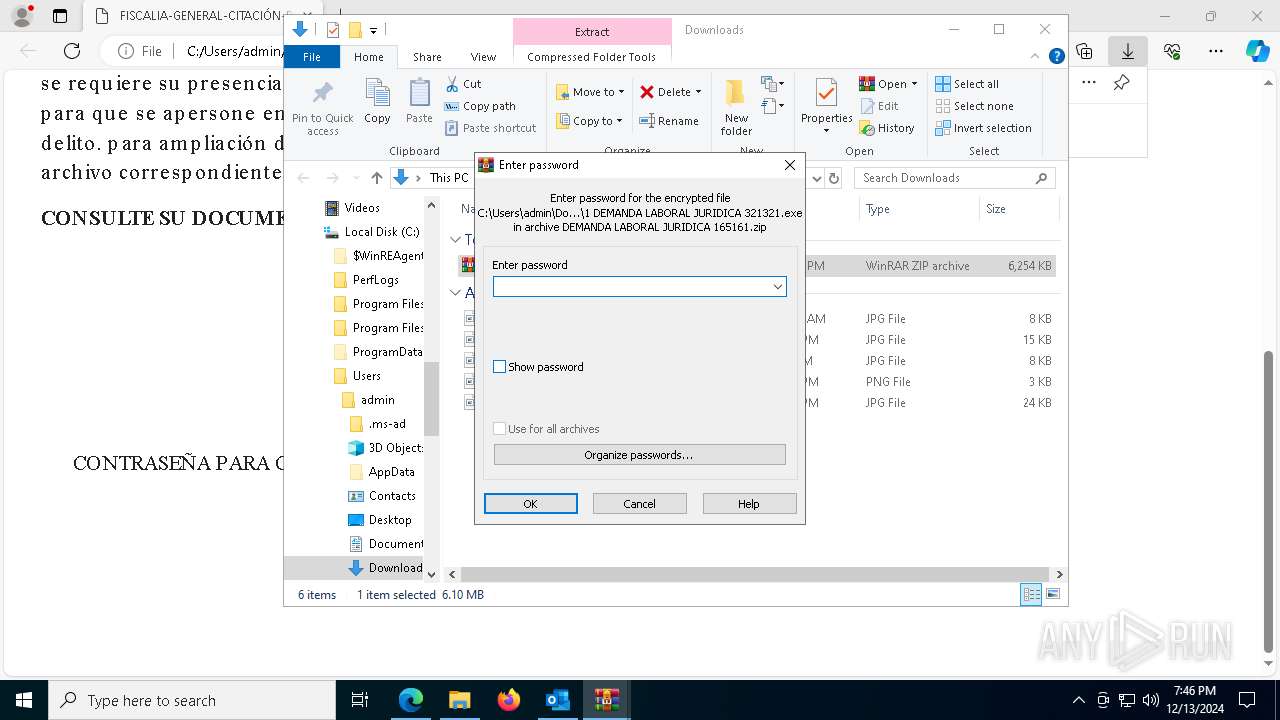
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
SUSPICIOUS
Executable content was dropped or overwritten
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 7976)
Drops a system driver (possible attempt to evade defenses)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
Starts CMD.EXE for commands execution
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 5076)
The process verifies whether the antivirus software is installed
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 8140)
Checks for external IP
- svchost.exe (PID: 8140)
Connects to unusual port
- svchost.exe (PID: 8140)
Executes application which crashes
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 5076)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
Reads security settings of Internet Explorer
- svchost.exe (PID: 8140)
The process executes VB scripts
- svchost.exe (PID: 8140)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 7552)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7552)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7552)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 6496)
Checks supported languages
- identity_helper.exe (PID: 7280)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 7976)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 8044)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4952)
Reads Environment values
- identity_helper.exe (PID: 7280)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 6496)
- msedge.exe (PID: 7488)
- dllhost.exe (PID: 7316)
- WinRAR.exe (PID: 4980)
- dllhost.exe (PID: 7036)
- svchost.exe (PID: 8140)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4980)
Manual execution by a user
- WinRAR.exe (PID: 4980)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 8044)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 7976)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4952)
Application launched itself
- msedge.exe (PID: 4264)
Reads the computer name
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 7976)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
- identity_helper.exe (PID: 7280)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 8044)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4952)
Reads the machine GUID from the registry
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 7976)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 8044)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7316)
- dllhost.exe (PID: 7036)
Checks transactions between databases Windows and Oracle
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 7976)
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 8044)
The sample compiled with english language support
- 1 DEMANDA LABORAL JURIDICA 321321.exe (PID: 4740)
Creates files or folders in the user directory
- WerFault.exe (PID: 7764)
Create files in a temporary directory
- svchost.exe (PID: 8140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
190
Monitored processes
56
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | C:\WINDOWS\system32\cmd.exe /c schtasks /create /tn "G7EJdZoaViCVgUwk" /tr "C:\Users\admin\AppData\Roaming\1 DEMANDA LABORAL JURIDICA 321321.exe" /sc onlogon /rl highest /f | C:\Windows\System32\cmd.exe | 1 DEMANDA LABORAL JURIDICA 321321.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1864 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6920 --field-trial-handle=2156,i,11116530524964629024,13592891096636963236,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | schtasks /create /tn "G7EJdZoaViCVgUwk" /tr "C:\Users\admin\AppData\Roaming\1 DEMANDA LABORAL JURIDICA 321321.exe" /sc onlogon /rl highest /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2736 | C:\WINDOWS\system32\WerFault.exe -u -p 4740 -s 640 | C:\Windows\System32\WerFault.exe | 1 DEMANDA LABORAL JURIDICA 321321.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "35E731D3-352E-4220-AD62-6A50959F6BB2" "17B87359-2593-44CE-A451-A69C1A232DBF" "6496" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3848 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2220 --field-trial-handle=2156,i,11116530524964629024,13592891096636963236,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4264 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\TJIH93ZL\FISCALIA-GENERAL-CITACIÓN-PRESENCIAL-AL-JUZGADO-DELITO-ABUSO-DE-CONFIANZA-ART (1)_nh430prm.svg | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
27 198
Read events
25 964
Write events
1 085
Delete events
149
Modification events
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6496 |
| Operation: | write | Name: | 0 |
Value: 0B0E1016D1B24460945D428651D9666DE079C423004689F2EDA3F9B2D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511E032D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
10
Suspicious files
97
Text files
47
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6496 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:E852B2CD62D4C9846683F00CB9554D0A | SHA256:A92663025367C8776AB2E9D7C1BED2E01263B898B03EA0473EF6B121875B04C3 | |||
| 6496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_9A335D0F23714847A572CC75B30F6500.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 6496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\D6B018A8-30D3-493C-B9BC-7CF8CE2199EC | xml | |
MD5:3017BE7E08F0F62745C49D7549D5346B | SHA256:BCD7536D515942CA95C9990700A36B30DF82BB8DAA7160E0C76A8A1D70D898E7 | |||
| 6496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\TJIH93ZL\FISCALIA-GENERAL-CITACIÓN-PRESENCIAL-AL-JUZGADO-DELITO-ABUSO-DE-CONFIANZA-ART (1)_nh430prm.svg:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 6496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:2B2A11D1F3F41555687553B7648A5834 | SHA256:35F999D6059ED8F98B5D5C17A38567A25F24DADA2D6D4F2683C24464D009200F | |||
| 4264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:C7E2197BAE099B13BBB3ADEB1433487D | SHA256:3460EEAF45D581DD43A6E4E17AF8102DDAFF5AEAA88B10099527CF85211629E9 | |||
| 4264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13908b.TMP | — | |
MD5:— | SHA256:— | |||
| 4264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13908b.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
77
DNS requests
67
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.123:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6496 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7908 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1734558356&P2=404&P3=2&P4=Q12%2f0zMWTSqlzJ3wEFyZYcdR4aIjFQKgoWIA%2fiPyimYwmI8WbOWlE3SOrFz6N%2bL71PKRMVcM%2fwdHxGgnfcVyog%3d%3d | unknown | — | — | whitelisted |
6700 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8016 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7908 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1734558356&P2=404&P3=2&P4=Q12%2f0zMWTSqlzJ3wEFyZYcdR4aIjFQKgoWIA%2fiPyimYwmI8WbOWlE3SOrFz6N%2bL71PKRMVcM%2fwdHxGgnfcVyog%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
900 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.123:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.215.121.133:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.215.121.133:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.21.110.139:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6496 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.kozow .com Domain |
8140 | svchost.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
8140 | svchost.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
— | — | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
1 ETPRO signatures available at the full report