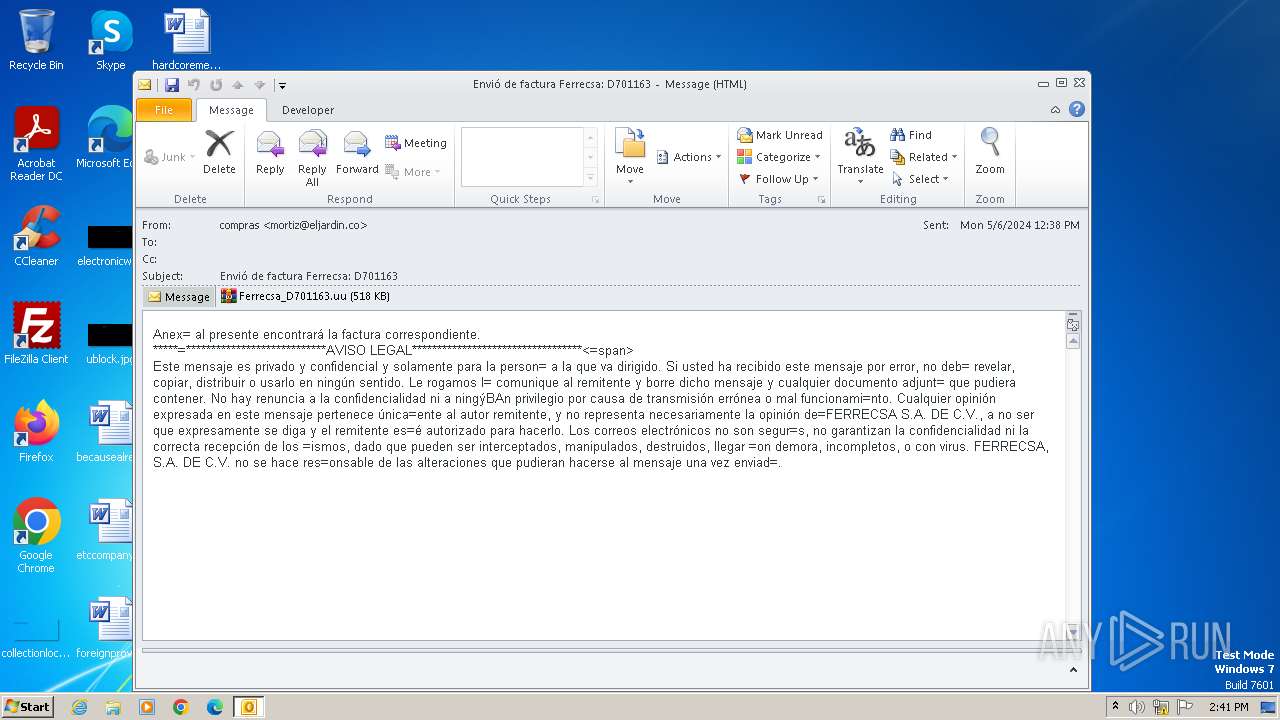
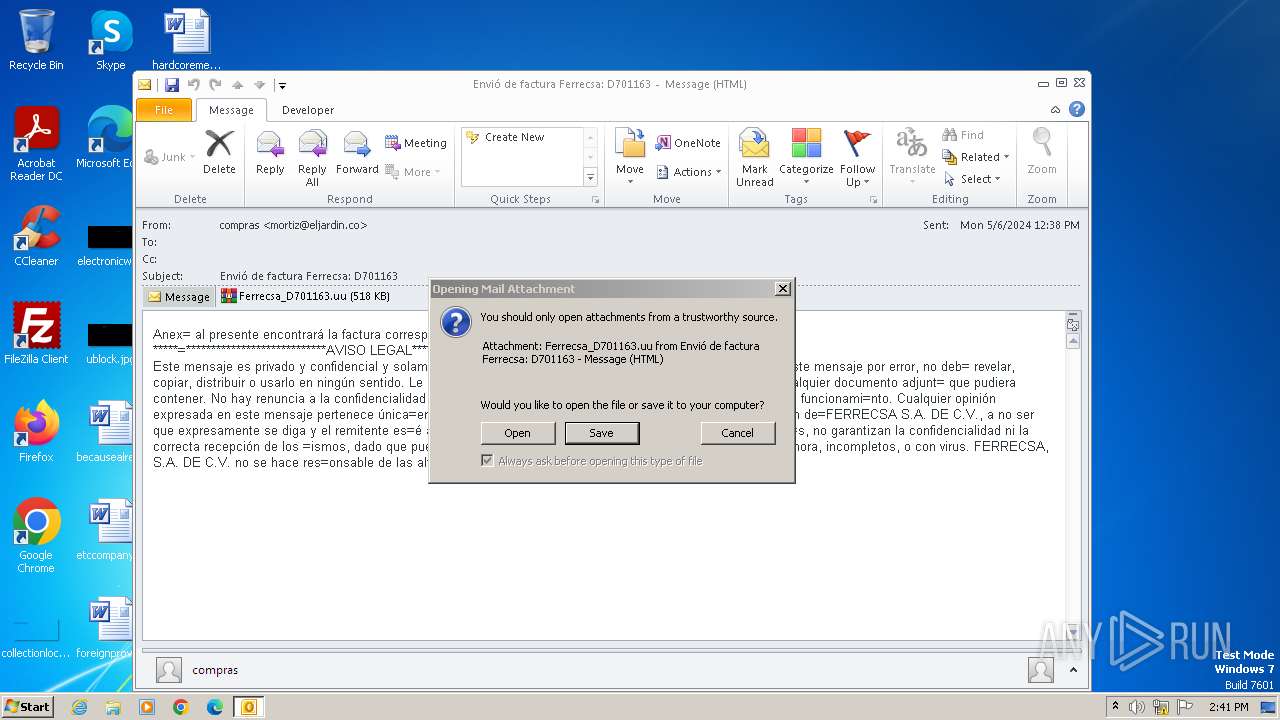
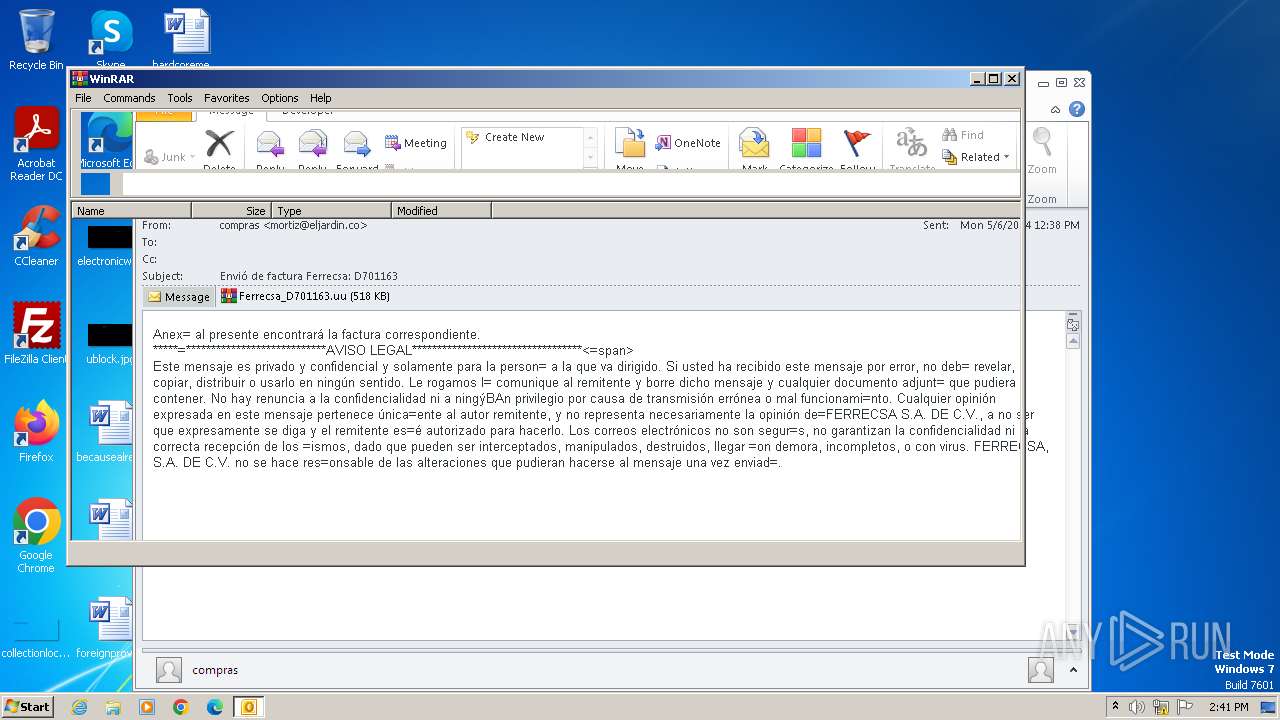
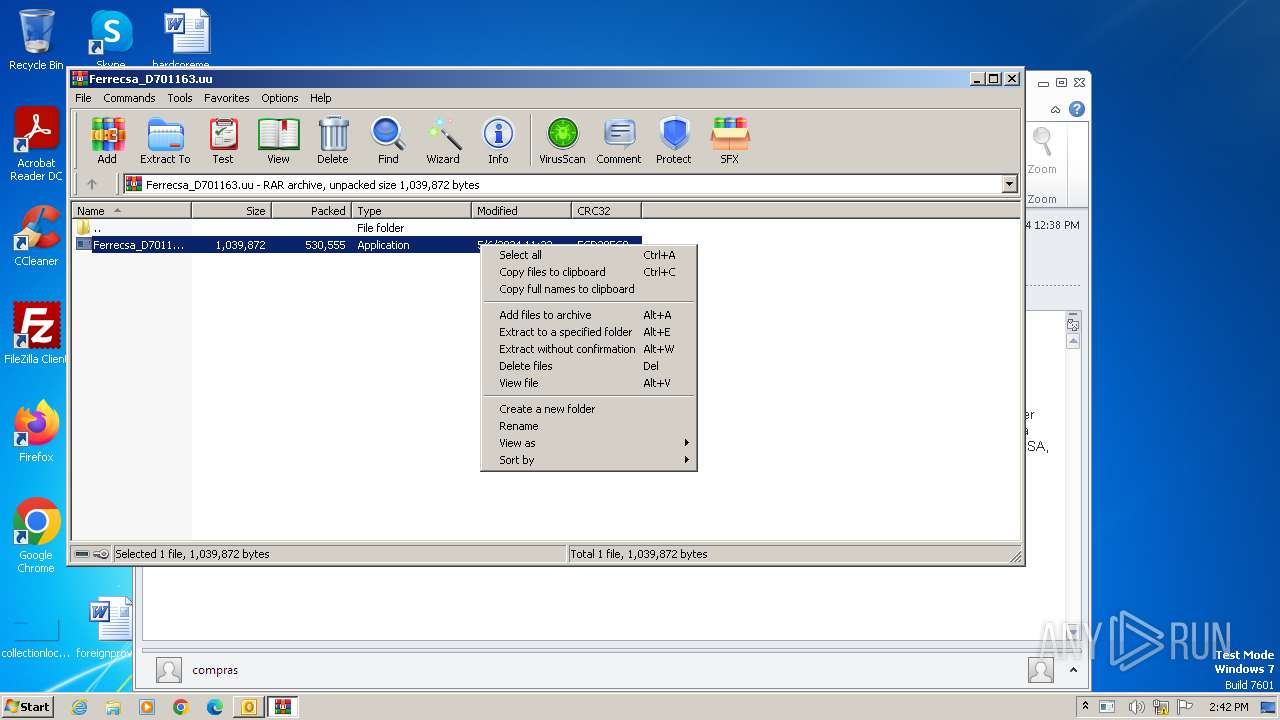
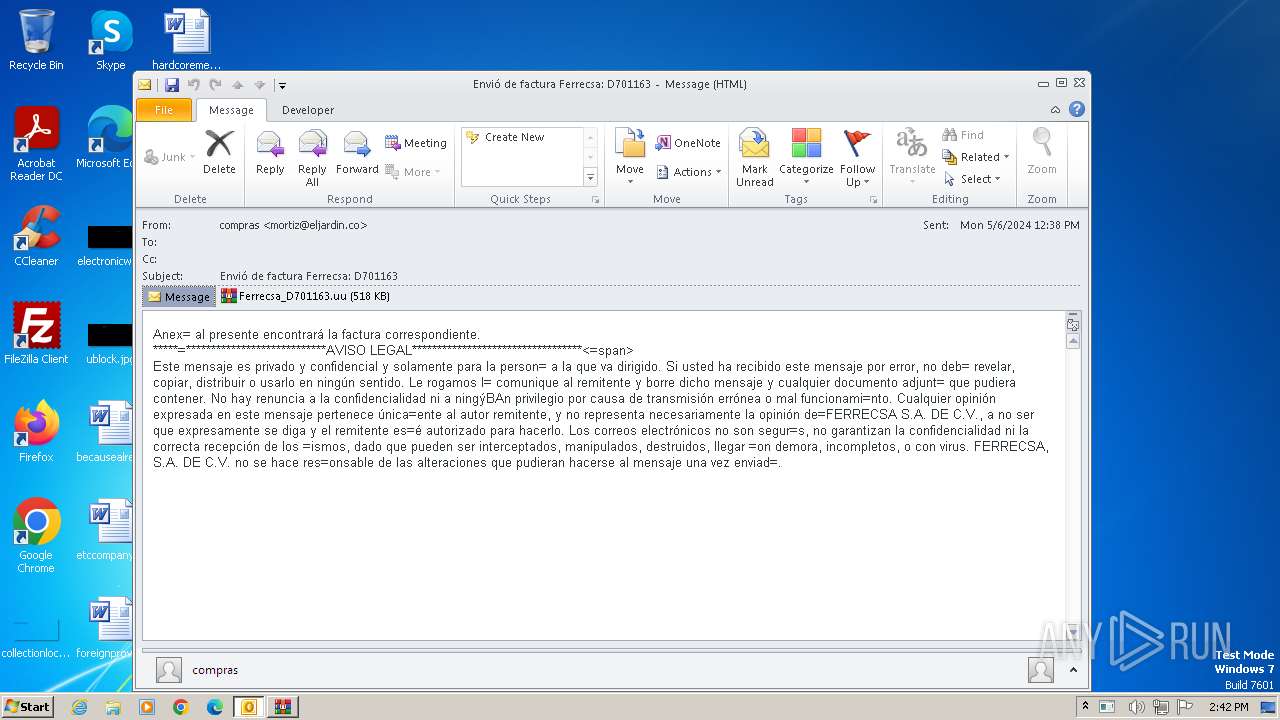
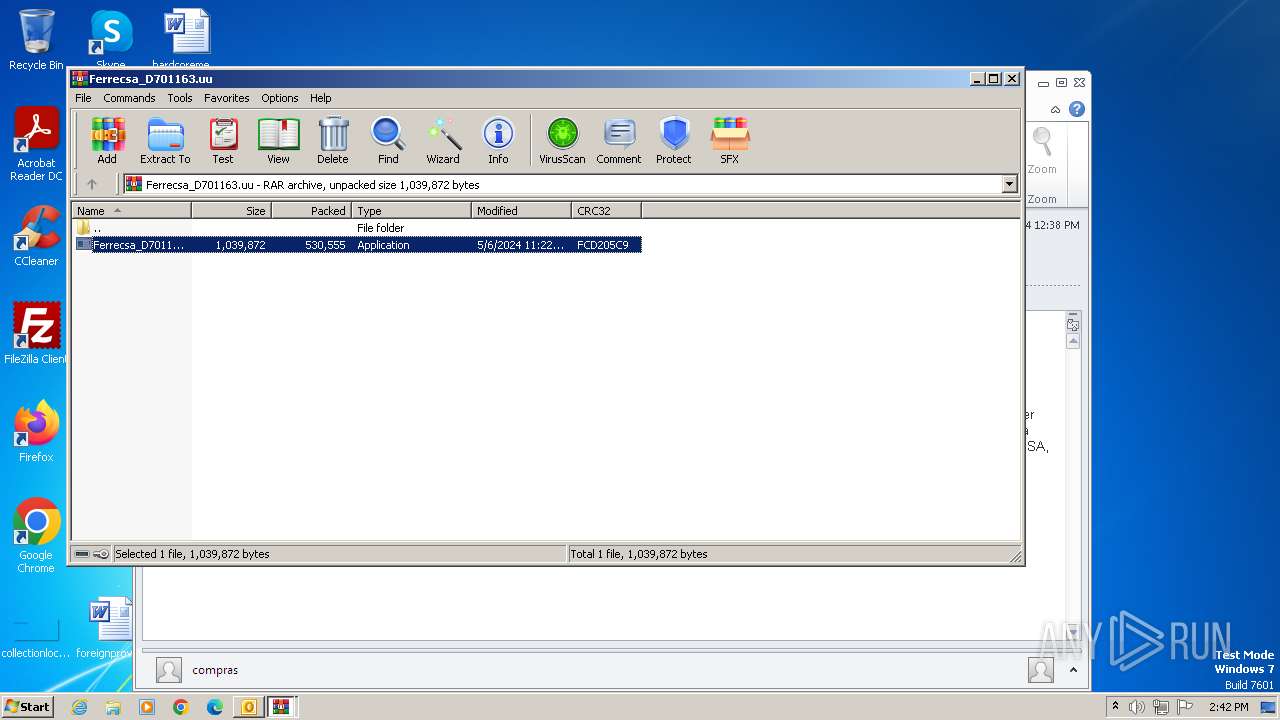
| File name: | ForwardedMessage.eml |
| Full analysis: | https://app.any.run/tasks/80628382-66e0-4347-bbd7-6e56f351e820 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 06, 2024, 13:41:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text |
| MD5: | 0BE9FF6B02275AD38C88FC31E8B30C49 |
| SHA1: | DEAC0F480D32A1200EE92ECE09D3085E2A780251 |
| SHA256: | 41D4720EFC5286DCC59AE5856C88559DEBB3F7E8D22C9CE86B1B439F4B2A40F7 |
| SSDEEP: | 12288:KYlk7cduOTMs+DsO13aWvtghwIhOhMPoejJw9BaLST:5k79s+z3zyhwTeq1T |
MALICIOUS
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 3988)
Unusual execution from MS Outlook
- OUTLOOK.EXE (PID: 3988)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 1588)
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 1588)
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2960)
Connects to the CnC server
- RegSvcs.exe (PID: 2552)
AGENTTESLA has been detected (SURICATA)
- RegSvcs.exe (PID: 2552)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1056)
- WinRAR.exe (PID: 1644)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 1588)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
Connects to FTP
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
Reads the Internet Settings
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
Connects to unusual port
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
INFO
Checks supported languages
- Ferrecsa_D701163.exe (PID: 1592)
- RegSvcs.exe (PID: 1588)
- Ferrecsa_D701163.exe (PID: 1552)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2336)
- Ferrecsa_D701163.exe (PID: 1820)
- Ferrecsa_D701163.exe (PID: 856)
- Ferrecsa_D701163.exe (PID: 1576)
- RegSvcs.exe (PID: 1408)
- RegSvcs.exe (PID: 2560)
- wmpnscfg.exe (PID: 1468)
- RegSvcs.exe (PID: 2396)
- Ferrecsa_D701163.exe (PID: 2420)
- Ferrecsa_D701163.exe (PID: 2876)
- RegSvcs.exe (PID: 2552)
- Ferrecsa_D701163.exe (PID: 2860)
- RegSvcs.exe (PID: 2960)
Reads the computer name
- Ferrecsa_D701163.exe (PID: 1592)
- RegSvcs.exe (PID: 1588)
- Ferrecsa_D701163.exe (PID: 1552)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2336)
- Ferrecsa_D701163.exe (PID: 1820)
- wmpnscfg.exe (PID: 1468)
- Ferrecsa_D701163.exe (PID: 856)
- Ferrecsa_D701163.exe (PID: 1576)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 1408)
- RegSvcs.exe (PID: 2396)
- Ferrecsa_D701163.exe (PID: 2420)
- Ferrecsa_D701163.exe (PID: 2876)
- RegSvcs.exe (PID: 2552)
- Ferrecsa_D701163.exe (PID: 2860)
- RegSvcs.exe (PID: 2960)
Reads mouse settings
- Ferrecsa_D701163.exe (PID: 1592)
- Ferrecsa_D701163.exe (PID: 1552)
- Ferrecsa_D701163.exe (PID: 1820)
- Ferrecsa_D701163.exe (PID: 856)
- Ferrecsa_D701163.exe (PID: 1576)
- Ferrecsa_D701163.exe (PID: 2420)
- Ferrecsa_D701163.exe (PID: 2860)
- Ferrecsa_D701163.exe (PID: 2876)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3988)
- WinRAR.exe (PID: 1056)
- WinRAR.exe (PID: 1644)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 1588)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 1408)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
Create files in a temporary directory
- Ferrecsa_D701163.exe (PID: 1592)
- Ferrecsa_D701163.exe (PID: 1552)
- Ferrecsa_D701163.exe (PID: 1820)
- Ferrecsa_D701163.exe (PID: 1576)
- Ferrecsa_D701163.exe (PID: 856)
- Ferrecsa_D701163.exe (PID: 2420)
- Ferrecsa_D701163.exe (PID: 2876)
- Ferrecsa_D701163.exe (PID: 2860)
Reads Environment values
- RegSvcs.exe (PID: 1588)
- RegSvcs.exe (PID: 2240)
- RegSvcs.exe (PID: 2336)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 1408)
- RegSvcs.exe (PID: 2396)
- RegSvcs.exe (PID: 2552)
- RegSvcs.exe (PID: 2960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1056)
- WinRAR.exe (PID: 1644)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1056)
- WinRAR.exe (PID: 1644)
Manual execution by a user
- wmpnscfg.exe (PID: 1468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(2396) RegSvcs.exe
Protocolftp
Hostftp://ftp.corpsa.net
Usernamevodooooo@corpsa.net
Password-E~O8rekW5UT
(PID) Process(2960) RegSvcs.exe
Protocolftp
Hostftp://ftp.corpsa.net
Usernamevodooooo@corpsa.net
Password-E~O8rekW5UT
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
56
Monitored processes
20
Malicious processes
17
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.25386\Ferrecsa_D701163.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.25386\Ferrecsa_D701163.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6MAXT9QB\Ferrecsa_D701163.uu" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1408 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.25386\Ferrecsa_D701163.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | Ferrecsa_D701163.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1552 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23617\Ferrecsa_D701163.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23617\Ferrecsa_D701163.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1576 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.25439\Ferrecsa_D701163.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.25439\Ferrecsa_D701163.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1588 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23367\Ferrecsa_D701163.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Ferrecsa_D701163.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23367\Ferrecsa_D701163.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23367\Ferrecsa_D701163.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1644 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6MAXT9QB\Ferrecsa_D701163.uu" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.24497\Ferrecsa_D701163.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.24497\Ferrecsa_D701163.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
30 005
Read events
29 411
Write events
564
Delete events
30
Modification events
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3988) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
8
Suspicious files
21
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR3DB7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6MAXT9QB\Ferrecsa_D701163 (2).uu | compressed | |
MD5:0B848B176F5515F876F22694C7ECFC0E | SHA256:609A7A13D60CC5B68709967136FF5C0F99693F634533800FCF56BDBD1787443D | |||
| 1056 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23367\Ferrecsa_D701163.exe | executable | |
MD5:29778E33311B23BCE2A1772F1A9C2A82 | SHA256:98EDEA6F415E600C90FDB035C8530E4912D80303D6A0AD5C167DE55375CC6824 | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6MAXT9QB\Ferrecsa_D701163.uu:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp4103.tmp | binary | |
MD5:EC8694562AA717832D48E1D582ADB54F | SHA256:30EFB7405BDAA06820FAAF66FA62B00A279FF01A0231CDB2A4FC93A667072004 | |||
| 1056 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1056.23617\Ferrecsa_D701163.exe | executable | |
MD5:29778E33311B23BCE2A1772F1A9C2A82 | SHA256:98EDEA6F415E600C90FDB035C8530E4912D80303D6A0AD5C167DE55375CC6824 | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6MAXT9QB\Ferrecsa_D701163.uu | compressed | |
MD5:0B848B176F5515F876F22694C7ECFC0E | SHA256:609A7A13D60CC5B68709967136FF5C0F99693F634533800FCF56BDBD1787443D | |||
| 3988 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6MAXT9QB\Ferrecsa_D701163 (2).uu:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
12
DNS requests
4
Threats
17
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3988 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2240 | RegSvcs.exe | 64.34.65.25:21 | ftp.corpsa.net | COGECO-PEER1 | CA | malicious |
2336 | RegSvcs.exe | 64.34.65.25:21 | ftp.corpsa.net | COGECO-PEER1 | CA | malicious |
2560 | RegSvcs.exe | 64.34.65.25:21 | ftp.corpsa.net | COGECO-PEER1 | CA | malicious |
2396 | RegSvcs.exe | 64.34.65.25:21 | ftp.corpsa.net | COGECO-PEER1 | CA | malicious |
2552 | RegSvcs.exe | 64.34.65.25:21 | ftp.corpsa.net | COGECO-PEER1 | CA | malicious |
2552 | RegSvcs.exe | 64.34.65.25:50074 | ftp.corpsa.net | COGECO-PEER1 | CA | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
ftp.corpsa.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
— | — | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
2552 | RegSvcs.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
— | — | Successful Credential Theft Detected | STEALER [ANY.RUN] Clear Text Password Exfiltration Atempt |
— | — | Successful Credential Theft Detected | STEALER [ANY.RUN] Clear Text Login Exfiltration Atempt |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
— | — | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
— | — | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
4 ETPRO signatures available at the full report