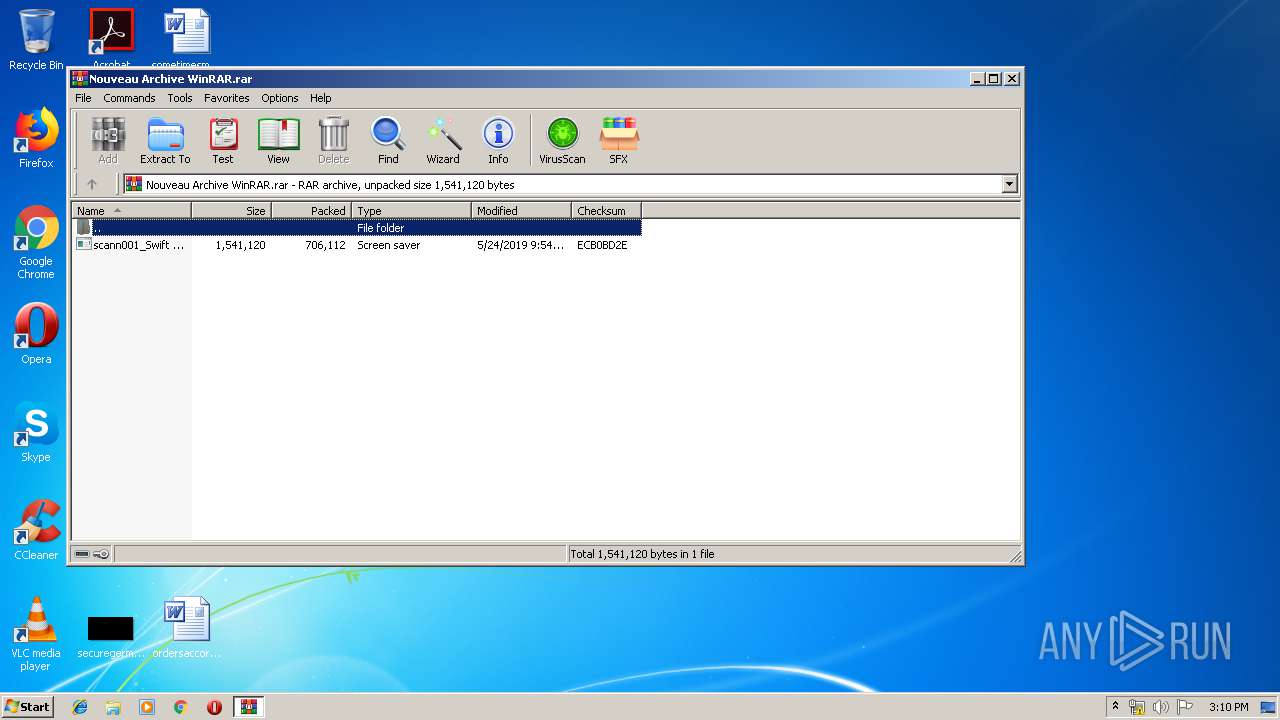
| File name: | Nouveau Archive WinRAR.rar |
| Full analysis: | https://app.any.run/tasks/5e4a59d6-bd9d-4bf9-ac89-09efa350d854 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | May 24, 2019, 14:09:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 82A9D44192044D8CD854C857B255BC0E |
| SHA1: | D7F577A94EE23B0CA3AEBB8763C1EF53349112DE |
| SHA256: | 416A09FC8C80277E2A926CB3DE672366CB3B033F6A5447F2880F778ED27E1BD9 |
| SSDEEP: | 12288:arwMvlrZojKOfjnthtyUIYXu6ZNxuKRuIRUSWRc2ZzzTjWidKWdk:a8MdZoj9tPyOX3uWKtnGirk |
MALICIOUS
Application was dropped or rewritten from another process
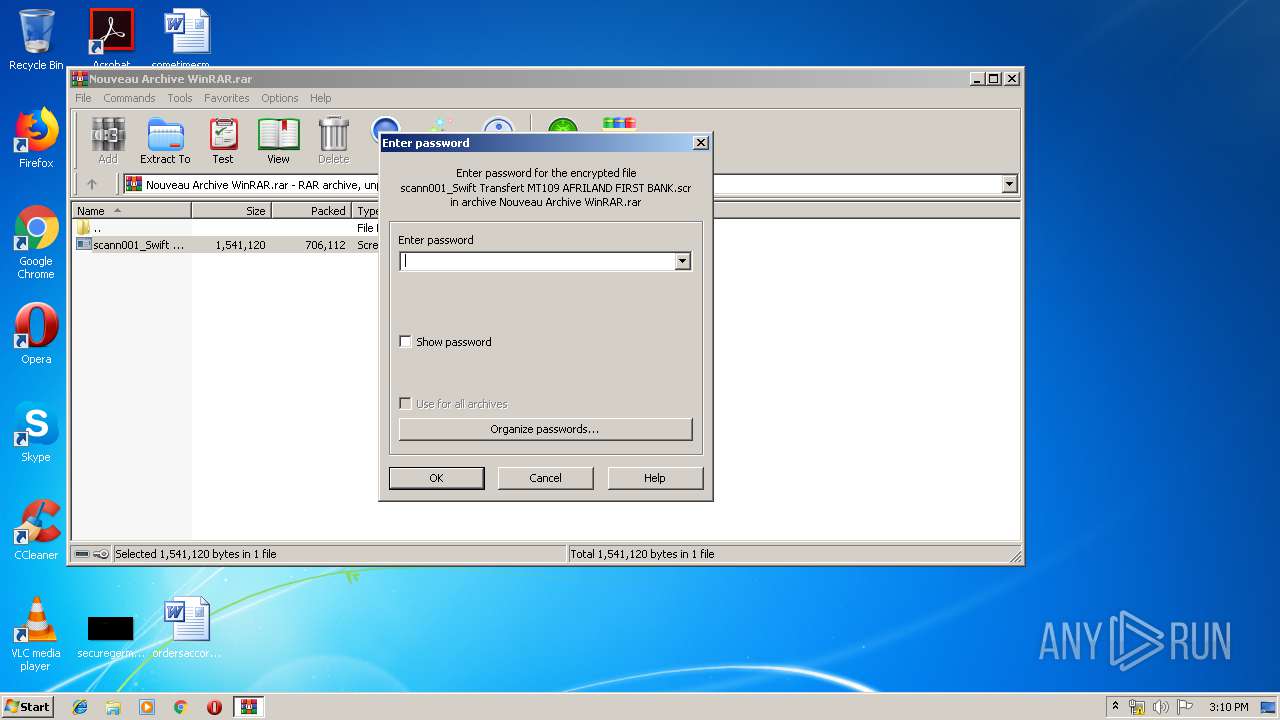
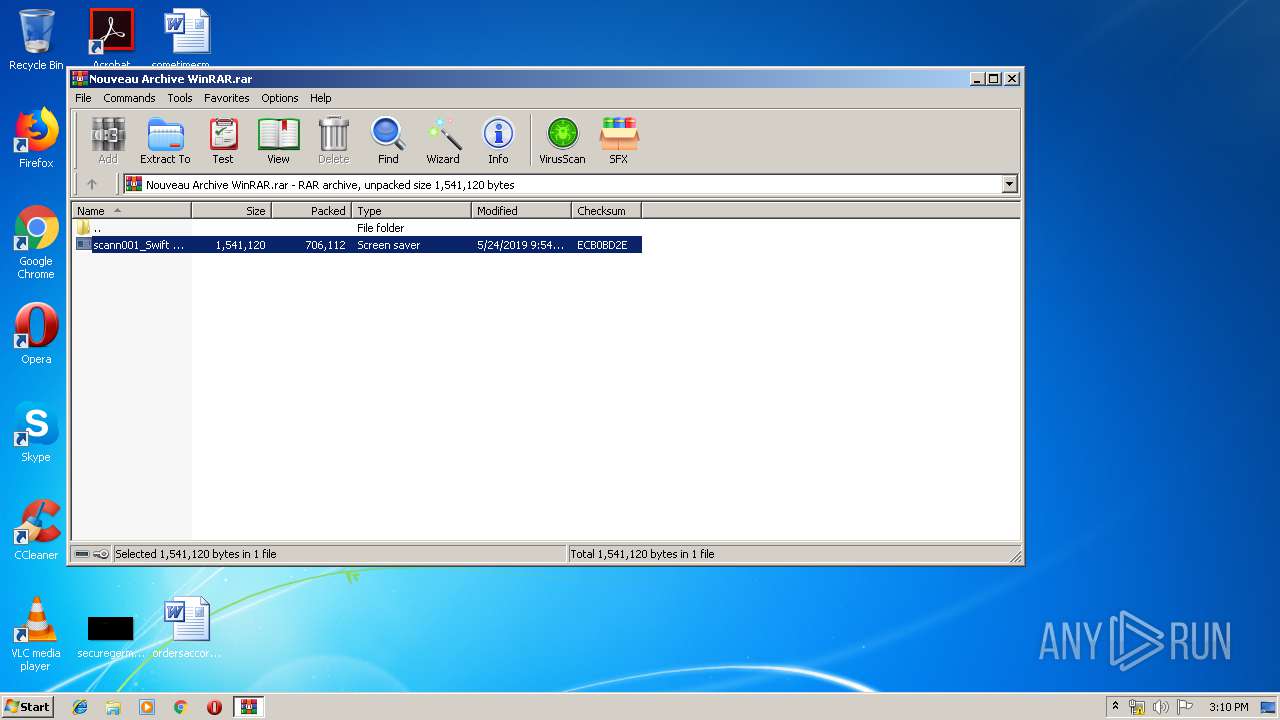
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 2452)
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 3736)
- RegAsm.exe (PID: 2152)
Known privilege escalation attack
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 2452)
Writes to a start menu file
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 3736)
Detected Imminent RAT
- RegAsm.exe (PID: 2152)
Changes the autorun value in the registry
- RegAsm.exe (PID: 2152)
Connects to CnC server
- RegAsm.exe (PID: 2152)
Changes settings of System certificates
- RegAsm.exe (PID: 2152)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3532)
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 3736)
- RegAsm.exe (PID: 2152)
Modifies the open verb of a shell class
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 2452)
Starts application with an unusual extension
- WinRAR.exe (PID: 3532)
- eventvwr.exe (PID: 2432)
Creates files in the user directory
- scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr (PID: 3736)
- RegAsm.exe (PID: 2152)
Adds / modifies Windows certificates
- RegAsm.exe (PID: 2152)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
41
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1900 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | — | scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Event Viewer Snapin Launcher Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2152 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Event Viewer Snapin Launcher Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | "C:\Users\admin\AppData\Local\Temp\Rar$DIb3532.3170\scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIb3532.3170\scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | — | WinRAR.exe | |||||||||||
User: admin Company: Gfxv2_0 Integrity Level: MEDIUM Description: Magnify Exit code: 0 Version: 281.505.910.143 Modules
| |||||||||||||||
| 3532 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Nouveau Archive WinRAR.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3736 | "C:\Users\admin\AppData\Local\Temp\Rar$DIb3532.3170\scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr" | C:\Users\admin\AppData\Local\Temp\Rar$DIb3532.3170\scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | eventvwr.exe | ||||||||||||
User: admin Company: Gfxv2_0 Integrity Level: HIGH Description: Magnify Exit code: 0 Version: 281.505.910.143 Modules
| |||||||||||||||
Total events
668
Read events
576
Write events
92
Delete events
0
Modification events
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Nouveau Archive WinRAR.rar | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
4
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3736 | scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | C:\Users\admin\AppData\Local\Temp\igfxSDK\LicenseManagerShellext.exe | executable | |
MD5:— | SHA256:— | |||
| 3736 | scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\chglogon.url | text | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3532.3170\scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | executable | |
MD5:— | SHA256:— | |||
| 3736 | scann001_Swift Transfert MT109 AFRILAND FIRST BANK.scr | C:\Users\admin\AppData\Local\Temp\igfxSDK\chglogon.vbs | text | |
MD5:— | SHA256:— | |||
| 2152 | RegAsm.exe | C:\Users\admin\AppData\Roaming\Imminent\Path.dat | binary | |
MD5:— | SHA256:— | |||
| 2152 | RegAsm.exe | C:\Users\admin\AppData\Roaming\Imminent\Geo.dat | binary | |
MD5:— | SHA256:— | |||
| 2152 | RegAsm.exe | C:\Users\admin\AppData\Roaming\AppData\UNPUXLauncher.exe | executable | |
MD5:278EDBD499374BF73621F8C1F969D894 | SHA256:C6999B9F79932C3B4F1C461A69D9DC8DC301D6A155ABC33EFE1B6E9E4A038391 | |||
| 2152 | RegAsm.exe | C:\AppData\UNPUXLauncher.exe | executable | |
MD5:278EDBD499374BF73621F8C1F969D894 | SHA256:C6999B9F79932C3B4F1C461A69D9DC8DC301D6A155ABC33EFE1B6E9E4A038391 | |||
| 2152 | RegAsm.exe | C:\Users\admin\AppData\Roaming\Imminent\Logs\24-05-2019 | text | |
MD5:33BE604F8044D5984E8E3E3B694D710A | SHA256:3F785F1CC535B0987139623200C7910B2B28F92DFE3309E8E071C091D0CE7313 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
2
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2152 | RegAsm.exe | GET | 301 | 45.55.57.244:80 | http://www.iptrackeronline.com/ | US | html | 240 b | shared |
2152 | RegAsm.exe | GET | 301 | 45.55.57.244:80 | http://www.iptrackeronline.com/ | US | html | 240 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2152 | RegAsm.exe | 185.244.31.7:47583 | worldcoupe.ddns.net | — | — | malicious |
2152 | RegAsm.exe | 45.55.57.244:80 | www.iptrackeronline.com | Digital Ocean, Inc. | US | malicious |
2152 | RegAsm.exe | 45.55.57.244:443 | www.iptrackeronline.com | Digital Ocean, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
worldcoupe.ddns.net |
| malicious |
www.iptrackeronline.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2152 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Imminent Monitor RAT (outbound) |
2152 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Imminent Monitor RAT (outbound) |
2152 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Imminent Monitor RAT (outbound) |
5 ETPRO signatures available at the full report