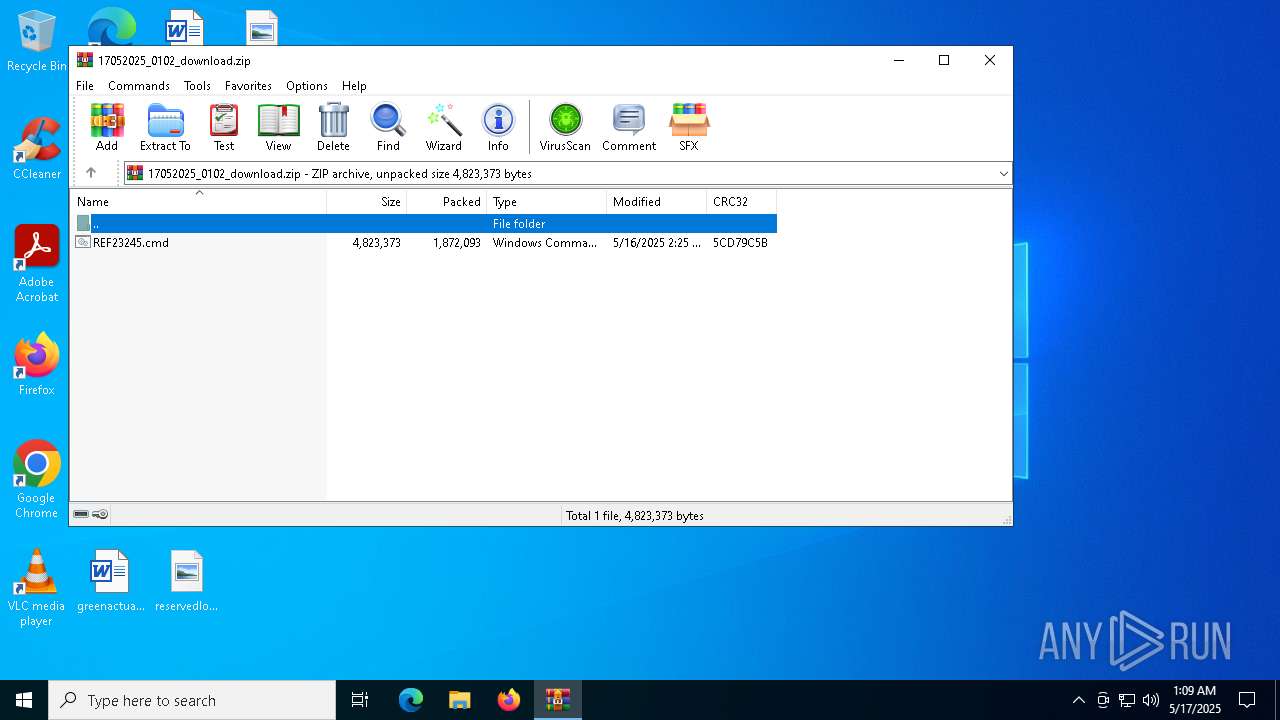
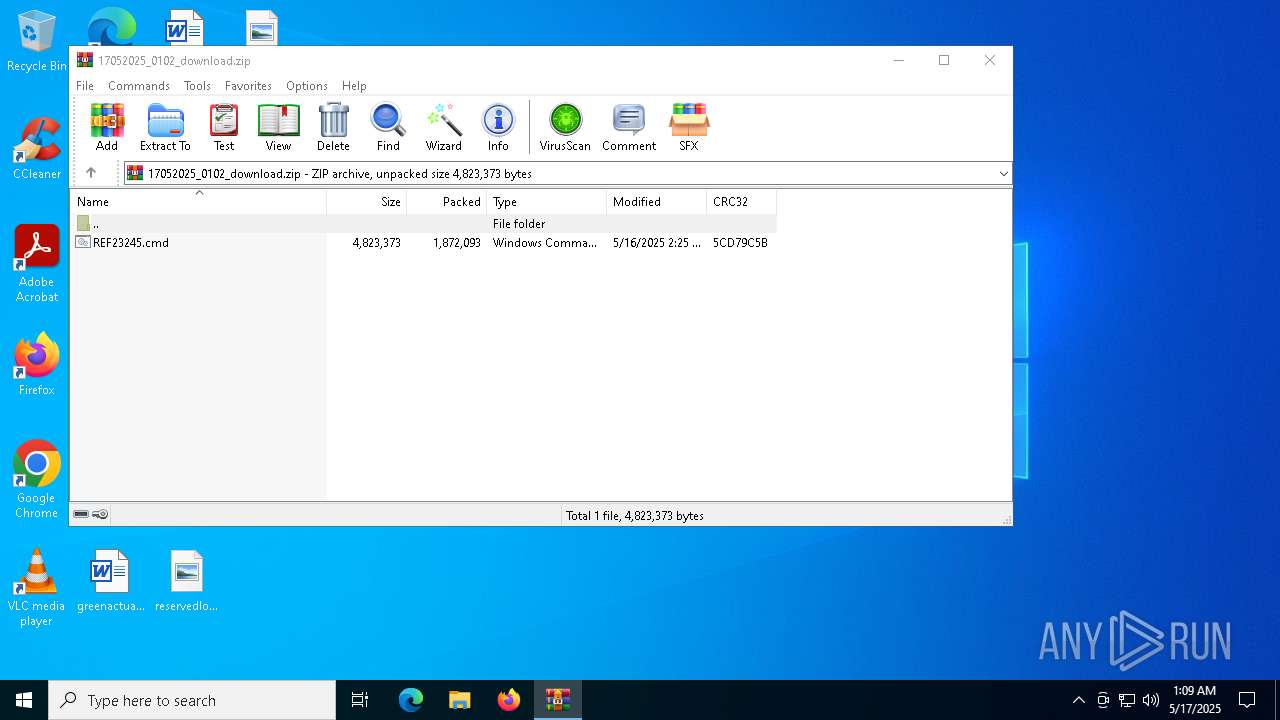
| File name: | 17052025_0102_download.zip |
| Full analysis: | https://app.any.run/tasks/9afa0e29-0b05-49df-aba8-b3fbff0b2472 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | May 17, 2025, 01:09:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A6E4C8792C8457A49F40BF93D9666DA6 |
| SHA1: | 2207310A5F0DBB940081F8CE49A7A5B2F8A75511 |
| SHA256: | 40D8D40E20EA380CE5B72D3AC8DA000DCFDA5B63173219CE20DA28271C3F3792 |
| SSDEEP: | 98304:WLDjVl/zLpKV1r/G7DZ1lLzZFkpJHuZZsgzLIVGdyrAwDzCES7sz1KTCnYa0wt3J:Gze |
MALICIOUS
Generic archive extractor
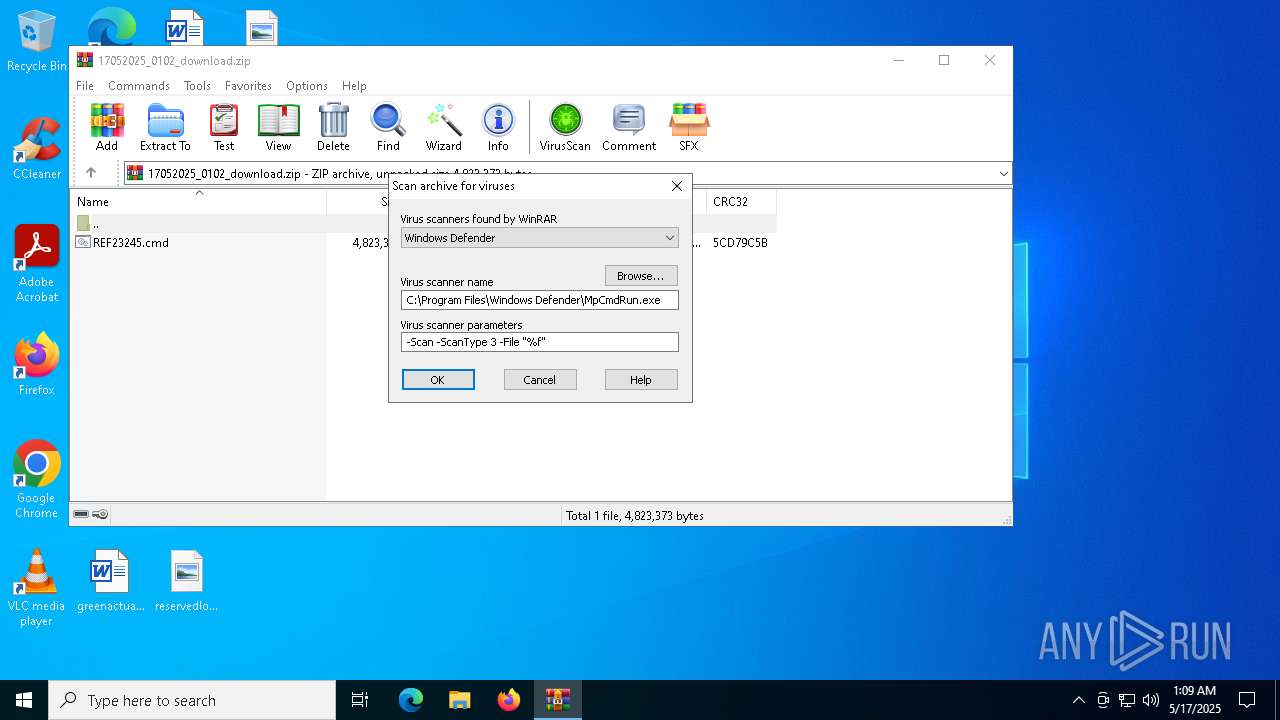
- WinRAR.exe (PID: 2088)
Run PowerShell with an invisible window
- powershell.exe (PID: 2092)
DBATLOADER has been detected (YARA)
- chrome.PIF (PID: 6476)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6668)
REMCOS has been detected (YARA)
- SndVol.exe (PID: 1532)
REMCOS has been detected (SURICATA)
- SndVol.exe (PID: 1532)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 456)
Executable content was dropped or overwritten
- extrac32.exe (PID: 5064)
- expha.pif (PID: 5576)
- expha.pif (PID: 4812)
- expha.pif (PID: 7084)
- ghf.pif (PID: 6964)
- esentutl.exe (PID: 5640)
- chrome.PIF (PID: 6476)
Drops a file with a rarely used extension (PIF)
- extrac32.exe (PID: 5064)
- expha.pif (PID: 5576)
- expha.pif (PID: 4812)
- ghf.pif (PID: 6964)
- expha.pif (PID: 7084)
- esentutl.exe (PID: 5640)
- chrome.PIF (PID: 6476)
Process drops legitimate windows executable
- extrac32.exe (PID: 5064)
- expha.pif (PID: 4812)
- expha.pif (PID: 5576)
The process hide an interactive prompt from the user
- cmd.exe (PID: 456)
Starts application with an unusual extension
- cmd.exe (PID: 456)
- alpha.pif (PID: 1660)
- alpha.pif (PID: 3884)
- rdha.pif (PID: 6644)
- cmd.exe (PID: 5204)
- rundll32.exe (PID: 1132)
- rundll32.exe (PID: 6576)
Process drops legitimate windows executable (CertUtil.exe)
- expha.pif (PID: 7084)
Starts itself from another location
- cmd.exe (PID: 456)
- cmd.exe (PID: 5204)
Runs PING.EXE to delay simulation
- alpha.pif (PID: 6240)
- cmd.exe (PID: 5576)
Reads security settings of Internet Explorer
- rdha.pif (PID: 6644)
- chrome.PIF (PID: 6476)
- Kvmtzzhl.PIF (PID: 5084)
- Kvmtzzhl.PIF (PID: 6808)
- WinRAR.exe (PID: 2088)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 456)
- chrome.PIF (PID: 6476)
- WinRAR.exe (PID: 2088)
Reads the date of Windows installation
- rdha.pif (PID: 6644)
Application launched itself
- cmd.exe (PID: 456)
There is functionality for taking screenshot (YARA)
- chrome.PIF (PID: 6476)
- Kvmtzzhl.PIF (PID: 5084)
- SndVol.exe (PID: 1532)
- Kvmtzzhl.PIF (PID: 6808)
Executing commands from ".cmd" file
- chrome.PIF (PID: 6476)
Starts a Microsoft application from unusual location
- alpha.pif (PID: 6512)
- alpha.pif (PID: 4068)
Created directory related to system
- alpha.pif (PID: 6512)
Likely accesses (executes) a file from the Public directory
- alpha.pif (PID: 6512)
- alpha.pif (PID: 4068)
- esentutl.exe (PID: 5640)
Contacting a server suspected of hosting an CnC
- SndVol.exe (PID: 1532)
Connects to unusual port
- SndVol.exe (PID: 1532)
The process executes via Task Scheduler
- rundll32.exe (PID: 1132)
- rundll32.exe (PID: 6576)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2088)
INFO
Checks supported languages
- extrac32.exe (PID: 5064)
- expha.pif (PID: 4812)
- expha.pif (PID: 5576)
- alpha.pif (PID: 3884)
- ghf.pif (PID: 5244)
- alpha.pif (PID: 1660)
- ghf.pif (PID: 6964)
- expha.pif (PID: 7084)
- rdha.pif (PID: 6644)
- chrome.PIF (PID: 6476)
- alpha.pif (PID: 6240)
- alpha.pif (PID: 6512)
- alpha.pif (PID: 4068)
- Kvmtzzhl.PIF (PID: 5084)
- Kvmtzzhl.PIF (PID: 6808)
- MpCmdRun.exe (PID: 4272)
The sample compiled with english language support
- extrac32.exe (PID: 5064)
- expha.pif (PID: 5576)
- expha.pif (PID: 4812)
- expha.pif (PID: 7084)
- esentutl.exe (PID: 5640)
Creates files in the program directory
- expha.pif (PID: 5576)
- extrac32.exe (PID: 5064)
- expha.pif (PID: 4812)
- ghf.pif (PID: 5244)
- ghf.pif (PID: 6964)
- expha.pif (PID: 7084)
- chrome.PIF (PID: 6476)
Manual execution by a user
- cmd.exe (PID: 456)
Reads the computer name
- extrac32.exe (PID: 5064)
- ghf.pif (PID: 5244)
- ghf.pif (PID: 6964)
- rdha.pif (PID: 6644)
- chrome.PIF (PID: 6476)
- Kvmtzzhl.PIF (PID: 5084)
- Kvmtzzhl.PIF (PID: 6808)
- MpCmdRun.exe (PID: 4272)
Checks proxy server information
- chrome.PIF (PID: 6476)
- Kvmtzzhl.PIF (PID: 5084)
- slui.exe (PID: 5640)
- Kvmtzzhl.PIF (PID: 6808)
Process checks computer location settings
- rdha.pif (PID: 6644)
Compiled with Borland Delphi (YARA)
- chrome.PIF (PID: 6476)
- Kvmtzzhl.PIF (PID: 5084)
- Kvmtzzhl.PIF (PID: 6808)
Reads the machine GUID from the registry
- chrome.PIF (PID: 6476)
- Kvmtzzhl.PIF (PID: 5084)
- Kvmtzzhl.PIF (PID: 6808)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1132)
- rundll32.exe (PID: 6576)
Local mutex for internet shortcut management
- rundll32.exe (PID: 1132)
- rundll32.exe (PID: 6576)
Reads the software policy settings
- slui.exe (PID: 5640)
Create files in a temporary directory
- MpCmdRun.exe (PID: 4272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(1532) SndVol.exe
C2 (3)45.141.233.95:8801
leak-shop.cc:8109
minerasicvalue.com:7501
BotnetTUE07
Options
Connect_interval1
Install_flagFalse
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_fileremcos.exe
Startup_valueFalse
Hide_fileFalse
Mutex_name-49TKCI
Keylog_flag1
Keylog_path%TEMP%
Keylog_file90s.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path1
Audio_dirMicRecords
Connect_delay0
Copy_dirRemcos
Keylog_dirappstore
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:16 10:25:22 |
| ZipCRC: | 0x5cd79c5b |
| ZipCompressedSize: | 1872093 |
| ZipUncompressedSize: | 4823373 |
| ZipFileName: | REF23245.cmd |
Total processes
158
Monitored processes
40
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\REF23245.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2088.11359\Rar$Scan151209.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\system32\rundll32.exe "C:\WINDOWS\system32\ieframe.dll",OpenURL C:\\ProgramData\\Kvmtzzhl.url | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | PING -n 4 127.0.0.1 | C:\Windows\System32\PING.EXE | — | alpha.pif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | cmd /c exit /b 0 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | C:\Windows\System32\SndVol.exe | C:\Windows\SysWOW64\SndVol.exe | chrome.PIF | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Volume Mixer Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
Remcos(PID) Process(1532) SndVol.exe C2 (3)45.141.233.95:8801 leak-shop.cc:8109 minerasicvalue.com:7501 BotnetTUE07 Options Connect_interval1 Install_flagFalse Install_HKCU\RunTrue Install_HKLM\RunTrue Install_HKLM\Explorer\Run1 Install_HKLM\Winlogon\Shell100000 Setup_path%LOCALAPPDATA% Copy_fileremcos.exe Startup_valueFalse Hide_fileFalse Mutex_name-49TKCI Keylog_flag1 Keylog_path%TEMP% Keylog_file90s.dat Keylog_cryptFalse Hide_keylogFalse Screenshot_flagFalse Screenshot_time5 Take_ScreenshotFalse Screenshot_path%APPDATA% Screenshot_fileScreenshots Screenshot_cryptFalse Mouse_optionFalse Delete_fileFalse Audio_record_time5 Audio_path1 Audio_dirMicRecords Connect_delay0 Copy_dirRemcos Keylog_dirappstore | |||||||||||||||
| 1660 | C:\\ProgramData\\alpha.pif /C C:\\ProgramData\\ghf.pif -decodehex -f "C:\\ProgramData\\donex.avi" "C:\\ProgramData\\chrome.PIF" 12 | C:\ProgramData\alpha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\17052025_0102_download.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2092 | PowerShell.exe -WindowStyle hidden -inputformat none -outputformat none -NonInteractive -Command | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294770688 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 108
Read events
14 093
Write events
15
Delete events
0
Modification events
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\17052025_0102_download.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6644) rdha.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (1532) SndVol.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\-49TKCI |
| Operation: | write | Name: | exepath |
Value: 2F4015C4E7834B121A68CC677E3E4BEE575B64CB1DC723DA857635EA14163F7377FAEBAD1A4766EEE163DABD443D6161BFFE905BE26EC6A19CBDC9F2B06B | |||
Executable files
7
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2088.11359\17052025_0102_download.zip\REF23245.cmd | — | |
MD5:— | SHA256:— | |||
| 2092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pckwhfsf.4ze.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5064 | extrac32.exe | C:\ProgramData\expha.pif | executable | |
MD5:41330D97BF17D07CD4308264F3032547 | SHA256:A224559FD6621066347A5BA8F4AEECEEA8A0A7A881A71BD36DE69ACEB52E9DF7 | |||
| 6964 | ghf.pif | C:\ProgramData\chrome.PIF | executable | |
MD5:A0CF1B9028E03C22A335FB67F8CBF1AA | SHA256:977C6363BFBADF16F06A2B30EE0F261944EEABEC40BD64616C81F289108FBF75 | |||
| 5576 | expha.pif | C:\ProgramData\rdha.pif | executable | |
MD5:100F56A73211E0B2BCD076A55E6393FD | SHA256:00BE065F405E93233CC2F0012DEFDCBB1D6817B58969D5FFD9FD72FC4783C6F4 | |||
| 4812 | expha.pif | C:\ProgramData\alpha.pif | executable | |
MD5:CB6CD09F6A25744A8FA6E4B3E4D260C5 | SHA256:265B69033CEA7A9F8214A34CD9B17912909AF46C7A47395DD7BB893A24507E59 | |||
| 1532 | SndVol.exe | C:\Users\admin\AppData\Local\Temp\appstore\90s.dat | binary | |
MD5:1BCECB64333264F39F7F46A47D72C1B2 | SHA256:1EDE51636F7C44419DBC0D3E5234CF9F0914667EDACBFBC047638E65C0CD491A | |||
| 5244 | ghf.pif | C:\ProgramData\donex.avi | text | |
MD5:48D213452D99B06FF3A0569C0E5F6EB1 | SHA256:0E6E3FD7E659AA973E9E969532BC7E63440314B8AD076D64C54F4D66312E0798 | |||
| 7084 | expha.pif | C:\ProgramData\ghf.pif | executable | |
MD5:A7A5B67EC704EAC6D6E6AF0489353F42 | SHA256:BF072F9A6A15B550B13AE86A4FBD3FA809D2A13236847AE9FA9A68F41386106E | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2088.11359\Rar$Scan151209.bat | text | |
MD5:A4DD1125B20A0BDC10834F7F257339E6 | SHA256:8B41B6C6B15C8F12CEFF792A6E166B37D4670EC00175CD43E7675300C5AC6635 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
82
DNS requests
18
Threats
126
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1532 | SndVol.exe | 45.141.233.95:8801 | leak-shop.cc | Euro Crypt EOOD | DE | malicious |
1532 | SndVol.exe | 45.141.233.95:8109 | leak-shop.cc | Euro Crypt EOOD | DE | malicious |
496 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5640 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
leak-shop.cc |
| malicious |
minerasicvalue.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1532 | SndVol.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 5 |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1532 | SndVol.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
1532 | SndVol.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
1532 | SndVol.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
1532 | SndVol.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
1532 | SndVol.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
1532 | SndVol.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
1532 | SndVol.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
1532 | SndVol.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |