| URL: | https://rftloader.com/Files/Oplus_Tool_V5.8.6.44_Version2.2.rar |
| Full analysis: | https://app.any.run/tasks/b68cbb5f-9b3f-4feb-ab19-dc219beda85e |
| Verdict: | Malicious activity |
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | December 23, 2024, 04:06:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 722A785D033EFA130EB1456DF8F9185A |
| SHA1: | 45BFBACC5389019ABD6BD994CE57D0B0F5468D18 |
| SHA256: | 405F2CE7020D14CCE792EA349584E7435E05AC189486E6AB98E6FC781EFC86C9 |
| SSDEEP: | 3:N8FKorKTMJzTizLH362WLjja:2Fpr1JqKxfja |
MALICIOUS
Raccoon mutex has been detected
- FTGUIDev.exe (PID: 5008)
- FTGUIDev.exe (PID: 6792)
Executing a file with an untrusted certificate
- jfrog.exe (PID: 7332)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 7684)
- cmd.exe (PID: 7888)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 8144)
Process drops legitimate windows executable
- WinRAR.exe (PID: 8144)
Reads security settings of Internet Explorer
- FTGUIDev.exe (PID: 5008)
- VcRuntime.Dll.exe (PID: 7080)
- VcRuntime.Dll.exe (PID: 7600)
Executes application which crashes
- RFT2.2.exe (PID: 648)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1172)
- regsvr32.exe (PID: 7628)
Starts CMD.EXE for commands execution
- VcRuntime.Dll.exe (PID: 7080)
- love.exe (PID: 5488)
- love.exe (PID: 7104)
- love.exe (PID: 3584)
- love.exe (PID: 2280)
- love.exe (PID: 308)
- VcRuntime.Dll.exe (PID: 7600)
Executing commands from a ".bat" file
- love.exe (PID: 5488)
- love.exe (PID: 7104)
- love.exe (PID: 3584)
- love.exe (PID: 2280)
- love.exe (PID: 308)
Creates files in the driver directory
- cmd.exe (PID: 6196)
INFO
Checks supported languages
- identity_helper.exe (PID: 7708)
- identity_helper.exe (PID: 5236)
- FTGUIDev.exe (PID: 5008)
- FTForODM.exe (PID: 7812)
- GenChecksum.exe (PID: 396)
- GPWDownloader.exe (PID: 6944)
- jfrog.exe (PID: 7332)
- jfrog.exe (PID: 7836)
- RFT2.2.exe (PID: 648)
- openssl.exe (PID: 6412)
- VcRuntime.Dll.exe (PID: 7080)
- FTGUIDev.exe (PID: 6792)
- RFT2.2.exe (PID: 5556)
- Adb.exe (PID: 7900)
- 7z.exe (PID: 7916)
- jfrog.exe (PID: 6632)
- FTForODM.exe (PID: 904)
- autoedl.exe (PID: 876)
- FTForODM.exe (PID: 5040)
- GenChecksum.exe (PID: 5456)
- love.exe (PID: 5488)
- love.exe (PID: 7104)
- love.exe (PID: 3584)
- openssl.exe (PID: 5004)
- love.exe (PID: 2280)
- love.exe (PID: 308)
- VcRuntime.Dll.exe (PID: 7600)
Application launched itself
- msedge.exe (PID: 6240)
- msedge.exe (PID: 8168)
Reads Environment values
- identity_helper.exe (PID: 7708)
- identity_helper.exe (PID: 5236)
Reads the computer name
- identity_helper.exe (PID: 7708)
- identity_helper.exe (PID: 5236)
- FTGUIDev.exe (PID: 5008)
- GPWDownloader.exe (PID: 6944)
- GenChecksum.exe (PID: 396)
- RFT2.2.exe (PID: 648)
- VcRuntime.Dll.exe (PID: 7080)
- RFT2.2.exe (PID: 5556)
- FTGUIDev.exe (PID: 6792)
- GenChecksum.exe (PID: 5456)
- VcRuntime.Dll.exe (PID: 7600)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6240)
The process uses the downloaded file
- msedge.exe (PID: 7940)
- msedge.exe (PID: 6240)
- WinRAR.exe (PID: 8144)
- VcRuntime.Dll.exe (PID: 7080)
- VcRuntime.Dll.exe (PID: 7600)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8144)
- msedge.exe (PID: 8156)
The sample compiled with english language support
- WinRAR.exe (PID: 8144)
- msedge.exe (PID: 8156)
The sample compiled with chinese language support
- WinRAR.exe (PID: 8144)
Manual execution by a user
- FTGUIDev.exe (PID: 5008)
- FTForODM.exe (PID: 7812)
- GPWDownloader.exe (PID: 6944)
- GenChecksum.exe (PID: 396)
- jfrog.exe (PID: 7332)
- jfrog.exe (PID: 7836)
- openssl.exe (PID: 6412)
- RFT2.2.exe (PID: 648)
- cmd.exe (PID: 5696)
- VcRuntime.Dll.exe (PID: 7080)
- RFT2.2.exe (PID: 5556)
- Adb.exe (PID: 7900)
- 7z.exe (PID: 7916)
- cmd.exe (PID: 2120)
- FTGUIDev.exe (PID: 6792)
- FTForODM.exe (PID: 904)
- love.exe (PID: 7104)
- autoedl.exe (PID: 876)
- GenChecksum.exe (PID: 5456)
- FTForODM.exe (PID: 5040)
- love.exe (PID: 5488)
- love.exe (PID: 3584)
- openssl.exe (PID: 5004)
- love.exe (PID: 2280)
- love.exe (PID: 308)
- VcRuntime.Dll.exe (PID: 7600)
Creates files in the program directory
- FTGUIDev.exe (PID: 5008)
- GPWDownloader.exe (PID: 6944)
Sends debugging messages
- FTGUIDev.exe (PID: 5008)
- FTForODM.exe (PID: 7812)
- GPWDownloader.exe (PID: 6944)
- FTForODM.exe (PID: 5040)
- FTForODM.exe (PID: 904)
Checks proxy server information
- FTGUIDev.exe (PID: 5008)
- WerFault.exe (PID: 1864)
VMProtect protector has been detected
- FTGUIDev.exe (PID: 5008)
- FTGUIDev.exe (PID: 6792)
Reads the software policy settings
- WerFault.exe (PID: 1864)
Reads the machine GUID from the registry
- RFT2.2.exe (PID: 648)
- RFT2.2.exe (PID: 5556)
Reads mouse settings
- VcRuntime.Dll.exe (PID: 7080)
- love.exe (PID: 7104)
- love.exe (PID: 5488)
- love.exe (PID: 3584)
- love.exe (PID: 2280)
- love.exe (PID: 308)
Creates files or folders in the user directory
- WerFault.exe (PID: 1864)
Process checks computer location settings
- VcRuntime.Dll.exe (PID: 7080)
- VcRuntime.Dll.exe (PID: 7600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
267
Monitored processes
126
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1904 --field-trial-handle=2244,i,8202268043591506106,18398030043910586798,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5164 --field-trial-handle=2244,i,8202268043591506106,18398030043910586798,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 308 | "C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\love.exe" | C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\love.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 396 | "C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\GenChecksum.exe" | C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\GenChecksum.exe | — | explorer.exe | |||||||||||
User: admin Company: OPPO Inc. Integrity Level: MEDIUM Description: GenChecksum for MTK Platform Exit code: 1 Version: 1.0.4.0 Modules
| |||||||||||||||
| 648 | "C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\RFT2.2.exe" | C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\RFT2.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RFTvb Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5180 --field-trial-handle=2244,i,8202268043591506106,18398030043910586798,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | "C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\autoedl.exe" | C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\autoedl.exe | — | explorer.exe | |||||||||||
User: admin Company: OPPO Mobile Inc. Integrity Level: MEDIUM Description: Auto EDL Version: 1.0.5.0 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\FTForODM.exe" | C:\Users\admin\Desktop\Oplus_Tool_V5.8.6.44_Version2.2\FTForODM.exe | explorer.exe | ||||||||||||
User: admin Company: Guangdong OPPO Mobile Telecommunications Corp.,Ltd. Integrity Level: MEDIUM Description: OPLUS Flash Tool For ODM Exit code: 0 Version: 5.8.46.0 Modules
| |||||||||||||||
| 936 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2236 --field-trial-handle=2244,i,8202268043591506106,18398030043910586798,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
15 916
Read events
15 867
Write events
43
Delete events
6
Modification events
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459466 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {58414B08-15FB-4AE3-9890-6CAC25B955B9} | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459466 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {19B1BEFC-6D34-4915-BFBC-CC5DF9833F8A} | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8234BE677E882F00 | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2A47C7677E882F00 | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (6240) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: C2BC01687E882F00 | |||
Executable files
163
Suspicious files
633
Text files
161
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13522a.TMP | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13523a.TMP | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13523a.TMP | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13524a.TMP | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13524a.TMP | — | |
MD5:— | SHA256:— | |||
| 6240 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
93
DNS requests
78
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7132 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7132 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4308 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6956 | svchost.exe | HEAD | 200 | 217.20.57.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d50ccf3e-dd06-4e6f-bb20-931c8ce33527?P1=1735351052&P2=404&P3=2&P4=cUkLXNh90TqXjkzUkOyixA2Qn41y0KnSxlCZOtpPjfx0REfy3BOW8V%2bcOyarUusJxne%2bqdnp6A2FapKlrMhV6g%3d%3d | unknown | — | — | whitelisted |
4308 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6956 | svchost.exe | GET | 206 | 217.20.57.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d50ccf3e-dd06-4e6f-bb20-931c8ce33527?P1=1735351052&P2=404&P3=2&P4=cUkLXNh90TqXjkzUkOyixA2Qn41y0KnSxlCZOtpPjfx0REfy3BOW8V%2bcOyarUusJxne%2bqdnp6A2FapKlrMhV6g%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6076 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6588 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6240 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6588 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
rftloader.com |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
Process | Message |
|---|---|
FTGUIDev.exe | [2024/12/23 04:07:56:070][0x1cf4][GetWin32MainNetInfo:57] [System] Selected network interface IP = 192.168.100.178, Address = 52-54-00-C1-3E-3E
|
FTGUIDev.exe | [2024/12/23 04:07:57:805][0x1cf4] [CMsmDownloadToolDlg::OnInitDialog:280] [cmd info]
|
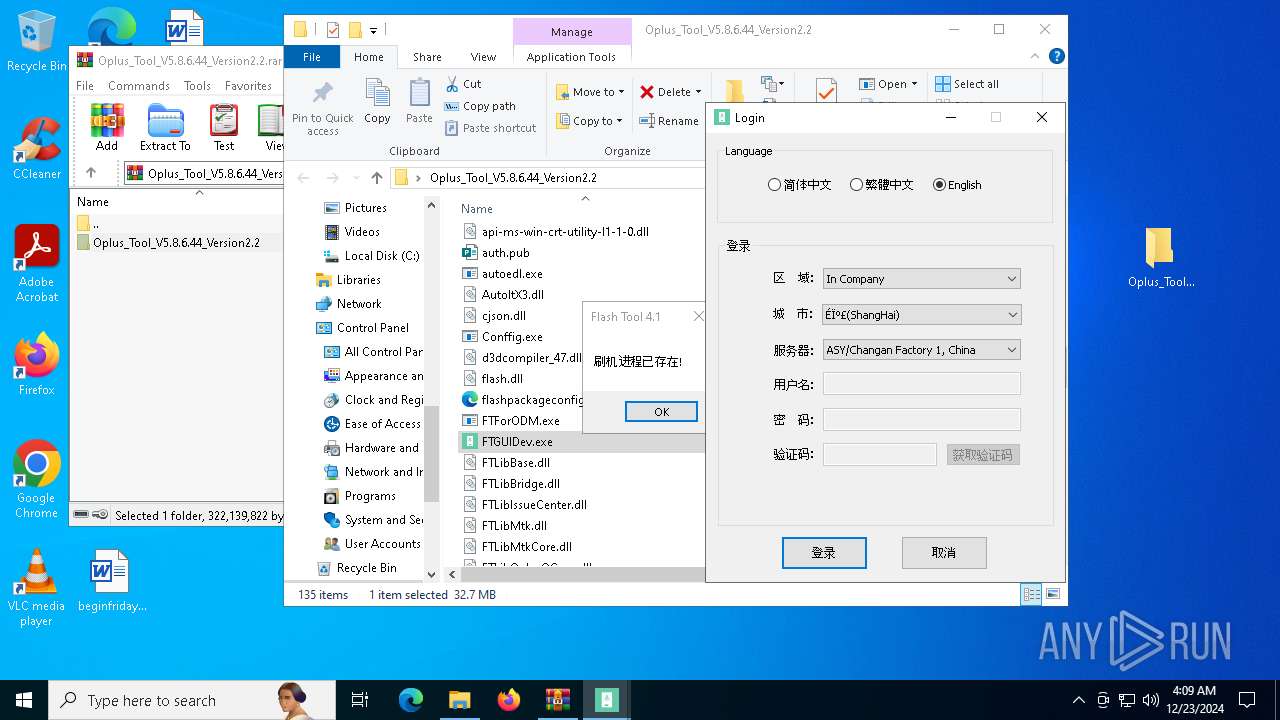
FTGUIDev.exe | [2024/12/23 04:07:57:805][0x1cf4] [CMsmDownloadToolDlg::OnInitDialog:259] OPPO Flash Tool Version V5.8.46.0 For Testing
|
FTGUIDev.exe | [2024/12/23 04:07:57:805][0x1cf4][op_device_manager_set_all_disconnect:989] [opdevice][oplus] set all devices disconnect
|
FTGUIDev.exe | [2024/12/23 04:07:57:805][0x1cf4] [CMsmDownloadToolDlg::OnInitDialog:260] [UI] Login success
|
FTGUIDev.exe | [2024/12/23 04:07:57:821][0x1c18][DeviceDetectThreadImpl:278] [opdevice][FTGUIDev] Start detecting devices...
|
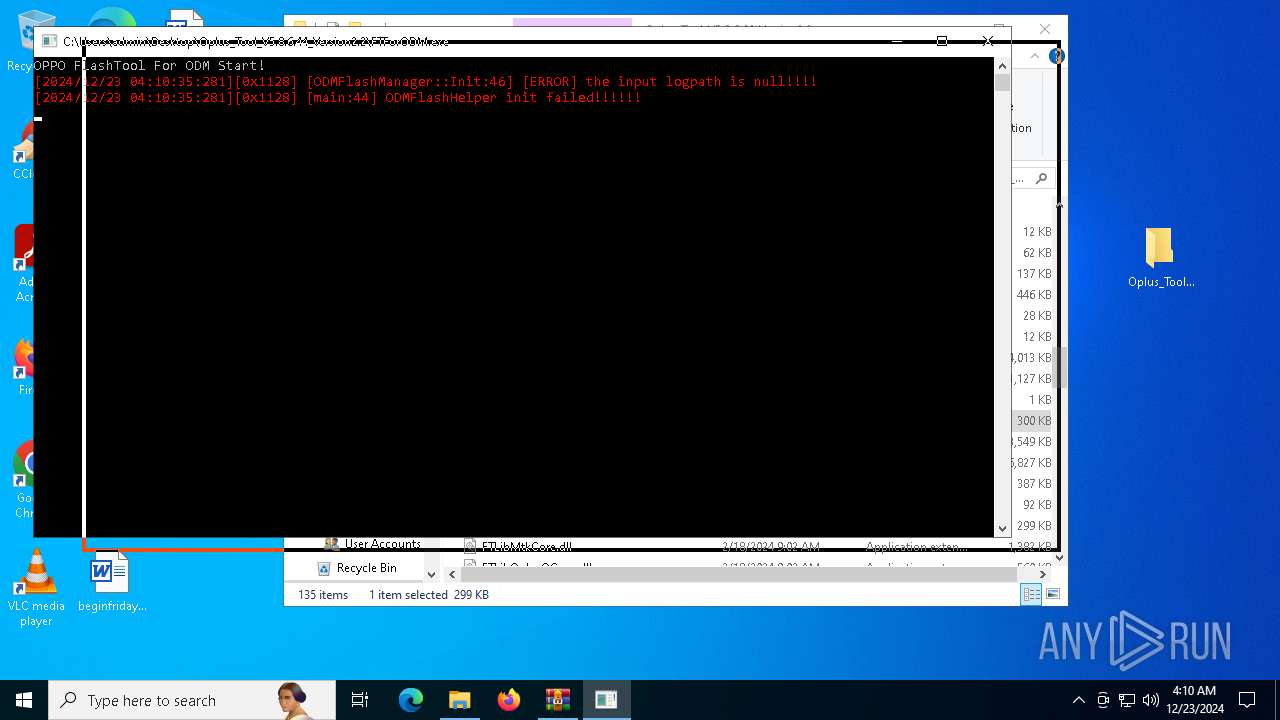
FTForODM.exe | [2024/12/23 04:08:13:930][0x1f44] [main:44] ODMFlashHelper init failed!!!!!!
|
FTForODM.exe | [2024/12/23 04:08:13:930][0x1f44] [ODMFlashManager::Init:46] [ERROR] the input logpath is null!!!!
|
FTForODM.exe | [2024/12/23 04:08:15:946][0x1f44] [main:46] ODMFlashHelper init failed!!!!!!
|
FTGUIDev.exe | [2024/12/23 04:08:20:758][0x1cf4][op_curl_easy_perform:24] [ERROR] curl_easy_perform timeout, Current retry count =1
|