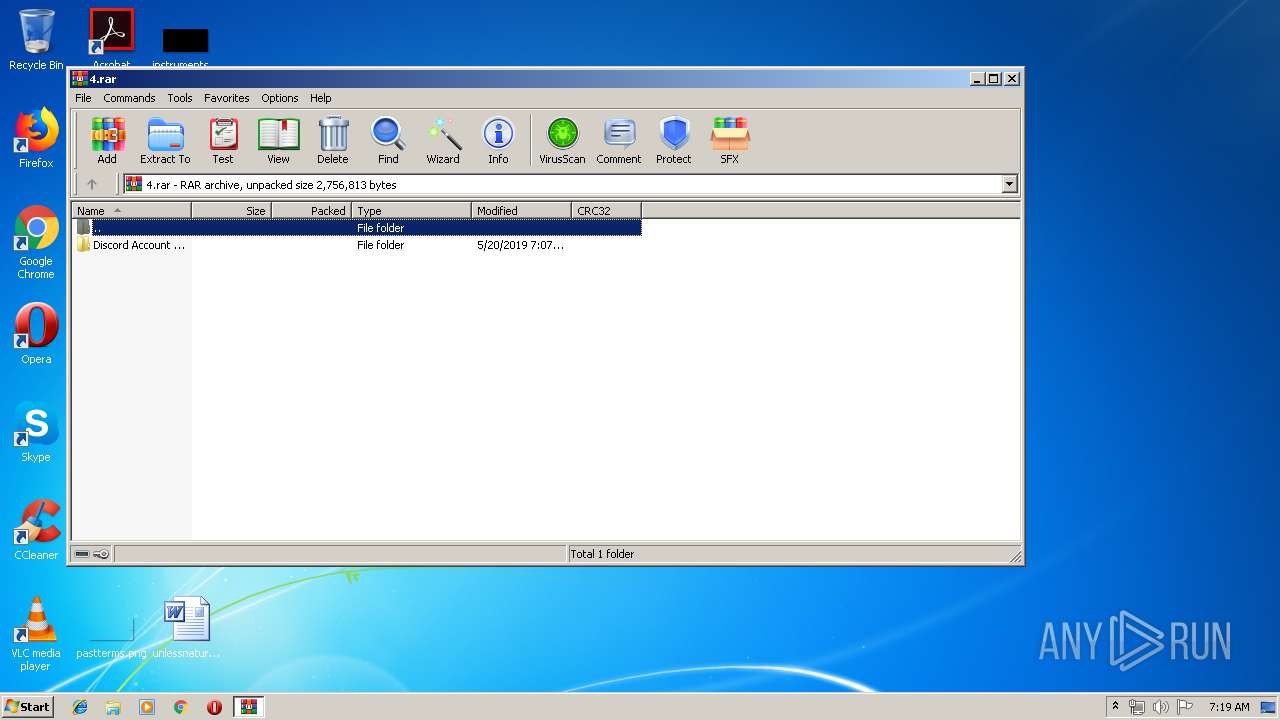
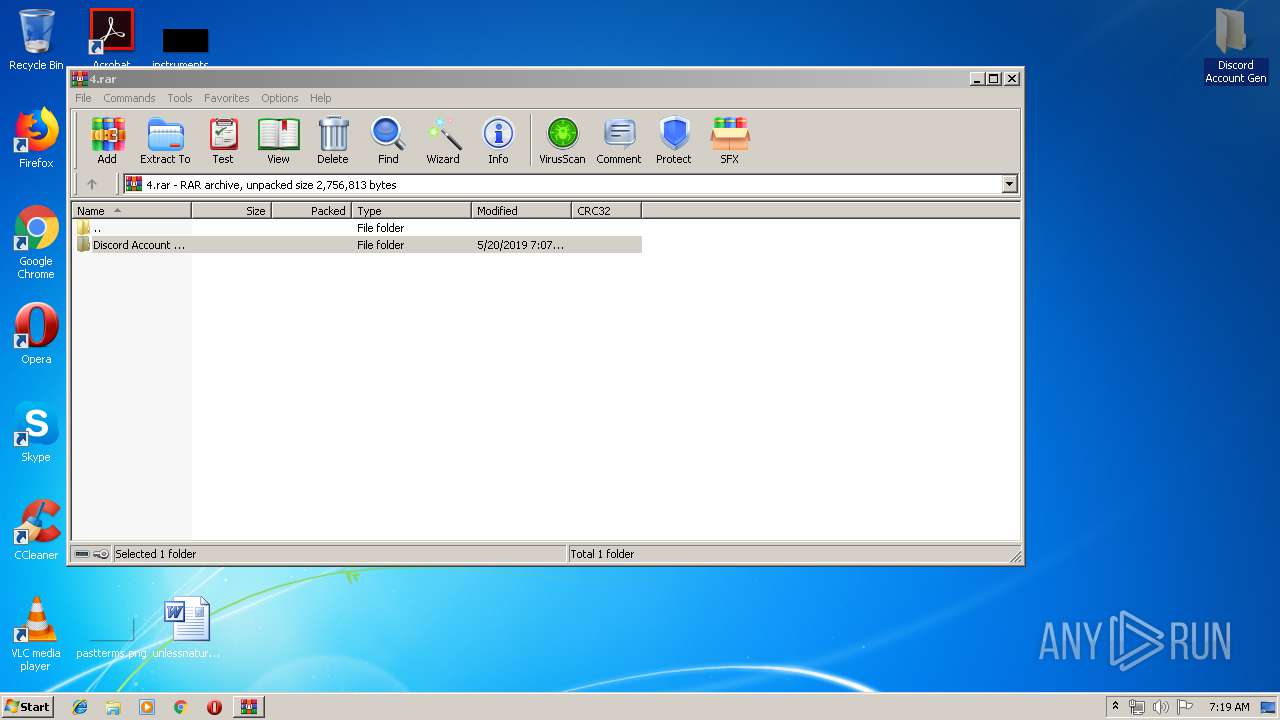
| File name: | 4.rar |
| Full analysis: | https://app.any.run/tasks/c91d301a-9505-4181-9f77-f2411246498f |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | May 20, 2019, 06:19:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 064A8E08DC6803B36424CA6D1C5BBD91 |
| SHA1: | 50C69CA7AAE4ABCDF66372A0C3ED052B64AC64F8 |
| SHA256: | 4011A66E1B61330C672DC128A0B987EB888E2C70DCE9C00F1E952AA15A9CF40A |
| SSDEEP: | 24576:looGNk3p9LjbSsoyfjvXIN3438vzzCgJY3RHK:l93XSqz4N4UzCgC3dK |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3572)
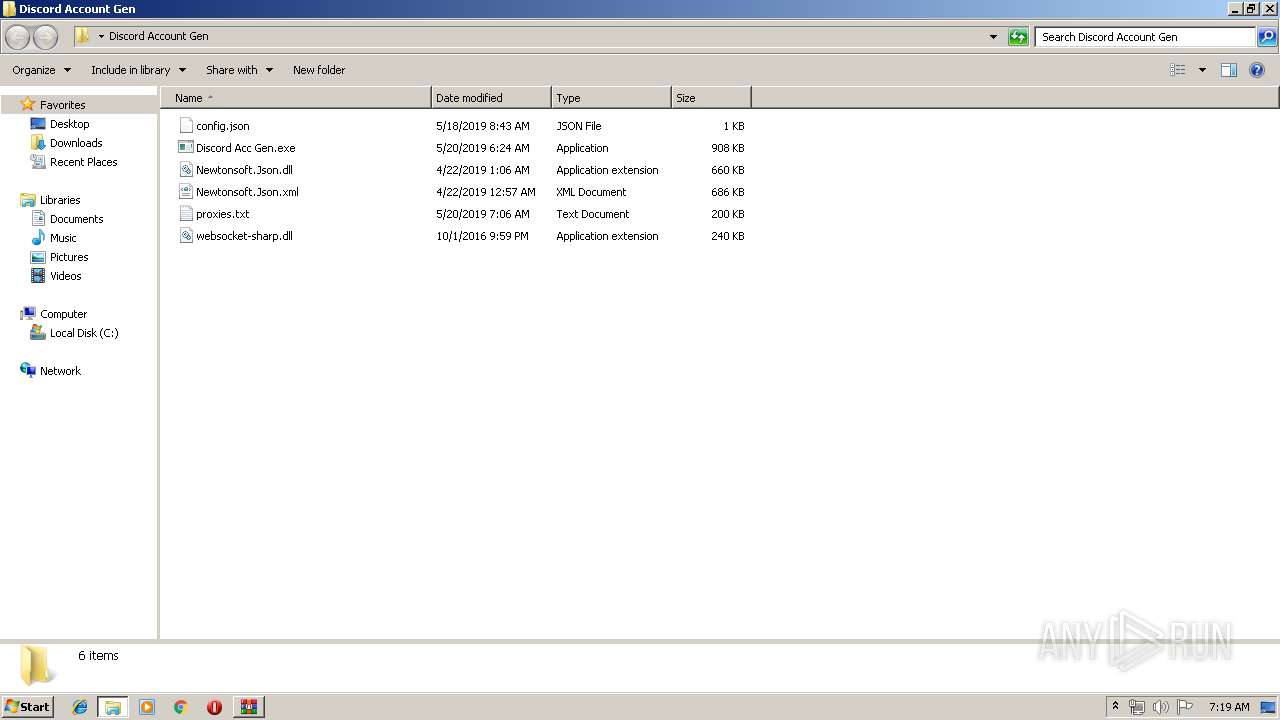
- Discord Acc Gen.exe (PID: 3024)
Orcus was detected
- Discord Acc Gen.exe (PID: 3024)
- Discord Acc Gen.exe (PID: 3560)
Application was dropped or rewritten from another process
- Discord Acc Gen.exe (PID: 3024)
- Discord Acc Gen.exe (PID: 3560)
- ProfileService.exe (PID: 2688)
- ProfileService.exe (PID: 3740)
Changes settings of System certificates
- Discord Acc Gen.exe (PID: 3024)
Loads the Task Scheduler COM API
- Discord Acc Gen.exe (PID: 3024)
Orcus RAT was detected
- ProfileService.exe (PID: 2688)
Actions looks like stealing of personal data
- Discord Acc Gen.exe (PID: 3024)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2088)
- Discord Acc Gen.exe (PID: 3024)
Executed via Task Scheduler
- Discord Acc Gen.exe (PID: 3560)
Application launched itself
- ProfileService.exe (PID: 2688)
Adds / modifies Windows certificates
- Discord Acc Gen.exe (PID: 3024)
Creates files in the user directory
- Discord Acc Gen.exe (PID: 3024)
Reads Internet Cache Settings
- Discord Acc Gen.exe (PID: 3024)
Reads the cookies of Mozilla Firefox
- Discord Acc Gen.exe (PID: 3024)
Starts Internet Explorer
- Discord Acc Gen.exe (PID: 3024)
Reads the cookies of Google Chrome
- Discord Acc Gen.exe (PID: 3024)
INFO
Manual execution by user
- Discord Acc Gen.exe (PID: 3024)
Changes internet zones settings
- iexplore.exe (PID: 3724)
Application launched itself
- iexplore.exe (PID: 3724)
Creates files in the user directory
- iexplore.exe (PID: 1380)
Reads internet explorer settings
- iexplore.exe (PID: 1380)
Reads Internet Cache Settings
- iexplore.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
50
Monitored processes
12
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1380 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3724 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1480 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES5666.tmp" "c:\Users\admin\AppData\Local\Temp\CSC5665.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\4.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2168 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\nvfacbir.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | Discord Acc Gen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2656 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES5ACB.tmp" "c:\Users\admin\AppData\Local\Temp\CSC5ABB.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2688 | "C:\Users\admin\AppData\Local\Temp\ProfileService.exe" /launchSelfAndExit "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" 3024 /protectFile | C:\Users\admin\AppData\Local\Temp\ProfileService.exe | Discord Acc Gen.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3740 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3024 | "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" | C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3560 | "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" | C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3572 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3724 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | Discord Acc Gen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 979
Read events
1 873
Write events
106
Delete events
0
Modification events
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\4.rar | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3572) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3572) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
12
Suspicious files
4
Text files
18
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3024 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\fsggyfwz.0.cs | — | |
MD5:— | SHA256:— | |||
| 3024 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\fsggyfwz.cmdline | — | |
MD5:— | SHA256:— | |||
| 3908 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC5665.tmp | — | |
MD5:— | SHA256:— | |||
| 1480 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES5666.tmp | — | |
MD5:— | SHA256:— | |||
| 3908 | csc.exe | C:\Users\admin\AppData\Local\Temp\fsggyfwz.dll | — | |
MD5:— | SHA256:— | |||
| 3908 | csc.exe | C:\Users\admin\AppData\Local\Temp\fsggyfwz.out | — | |
MD5:— | SHA256:— | |||
| 3024 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\Cab5963.tmp | — | |
MD5:— | SHA256:— | |||
| 3024 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\Tar5964.tmp | — | |
MD5:— | SHA256:— | |||
| 3024 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\Cab5984.tmp | — | |
MD5:— | SHA256:— | |||
| 3024 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\Tar5985.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3724 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3024 | Discord Acc Gen.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3024 | Discord Acc Gen.exe | 35.189.92.148:1337 | — | Google Inc. | US | malicious |
3024 | Discord Acc Gen.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3024 | Discord Acc Gen.exe | 216.18.168.98:443 | www.menofuk.com | Reflected Networks, Inc. | US | unknown |
3724 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
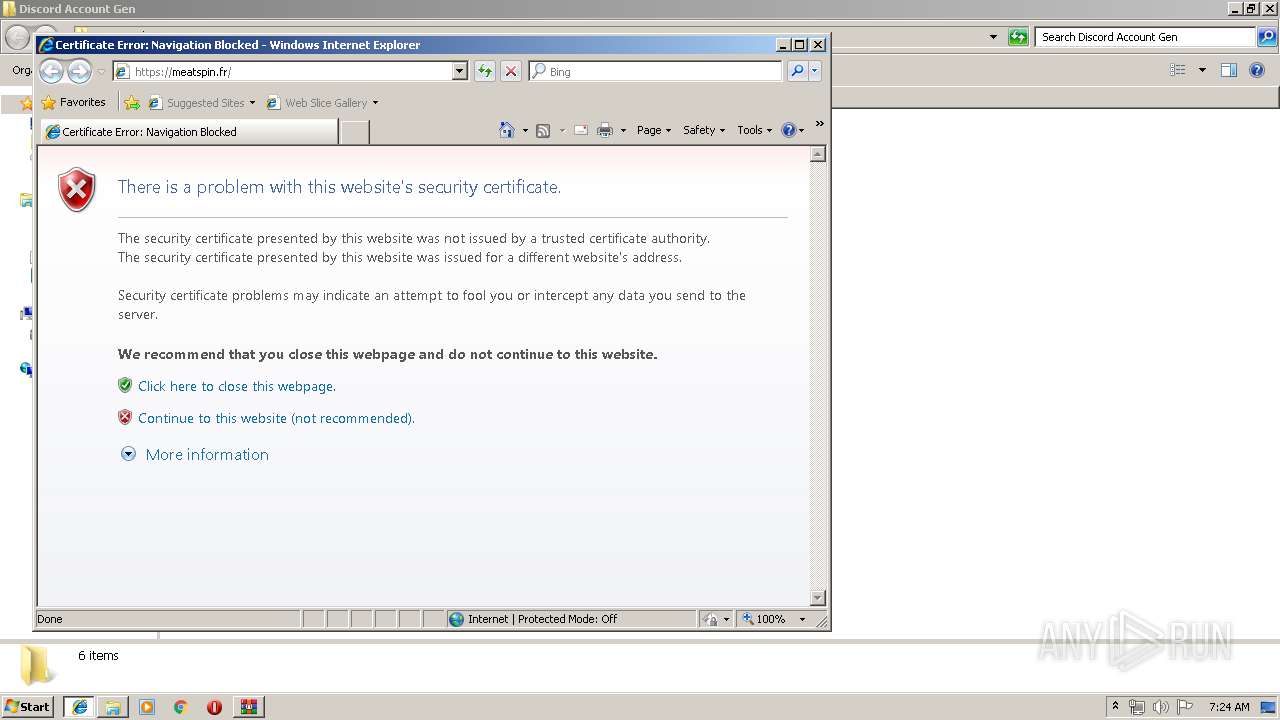
1380 | iexplore.exe | 151.80.37.67:443 | meatspin.fr | OVH SAS | FR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
www.menofuk.com |
| unknown |
meatspin.fr |
| malicious |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3024 | Discord Acc Gen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Malicious SSL Certificate (Orcus RAT) |
3024 | Discord Acc Gen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Malicious SSL Certificate (Orcus RAT) |
3024 | Discord Acc Gen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Malicious SSL connection (Orcus RAT) |
1 ETPRO signatures available at the full report