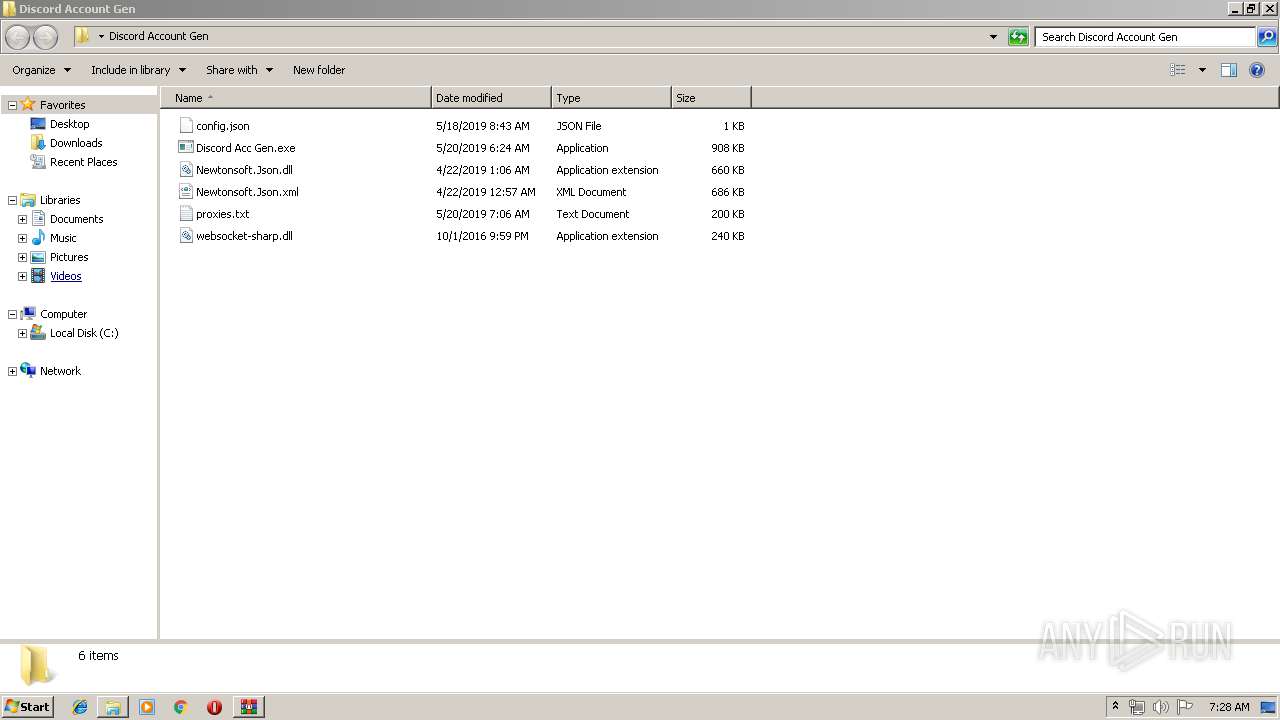
| File name: | 4.rar |
| Full analysis: | https://app.any.run/tasks/24120c51-694f-4912-ae33-2a0df78f1a6c |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | May 20, 2019, 06:26:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 064A8E08DC6803B36424CA6D1C5BBD91 |
| SHA1: | 50C69CA7AAE4ABCDF66372A0C3ED052B64AC64F8 |
| SHA256: | 4011A66E1B61330C672DC128A0B987EB888E2C70DCE9C00F1E952AA15A9CF40A |
| SSDEEP: | 24576:looGNk3p9LjbSsoyfjvXIN3438vzzCgJY3RHK:l93XSqz4N4UzCgC3dK |
MALICIOUS
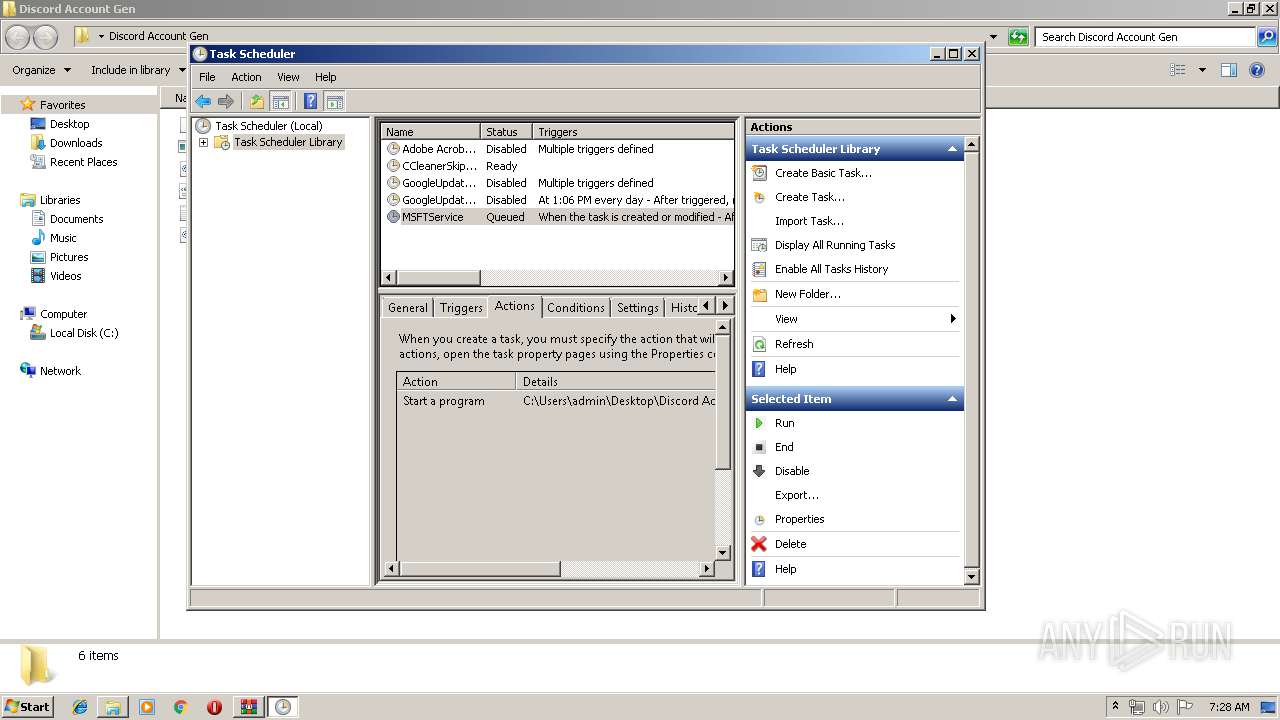
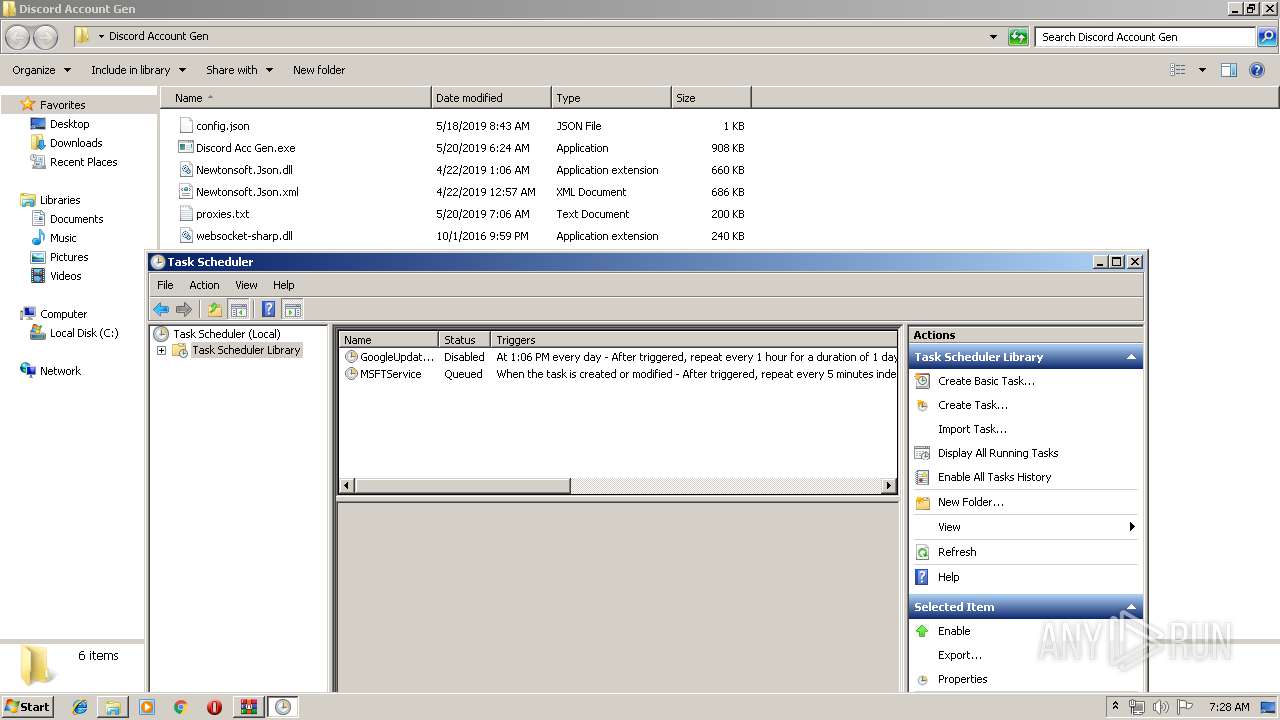
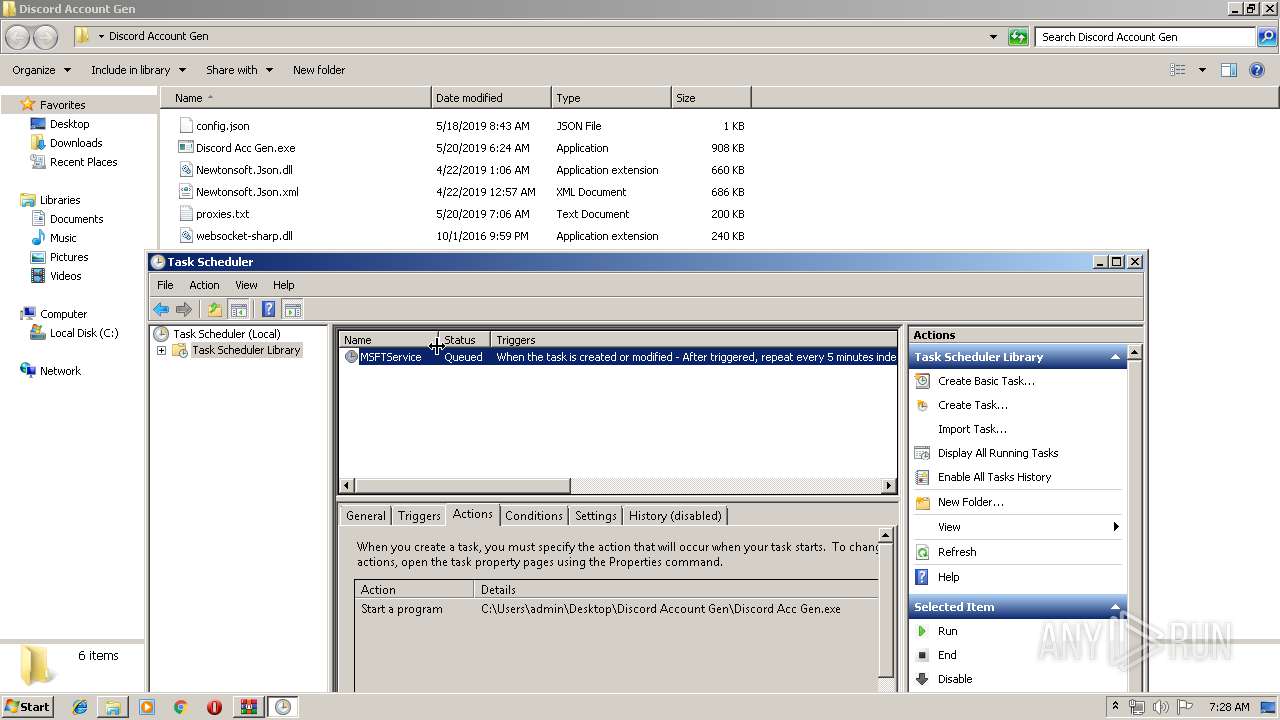
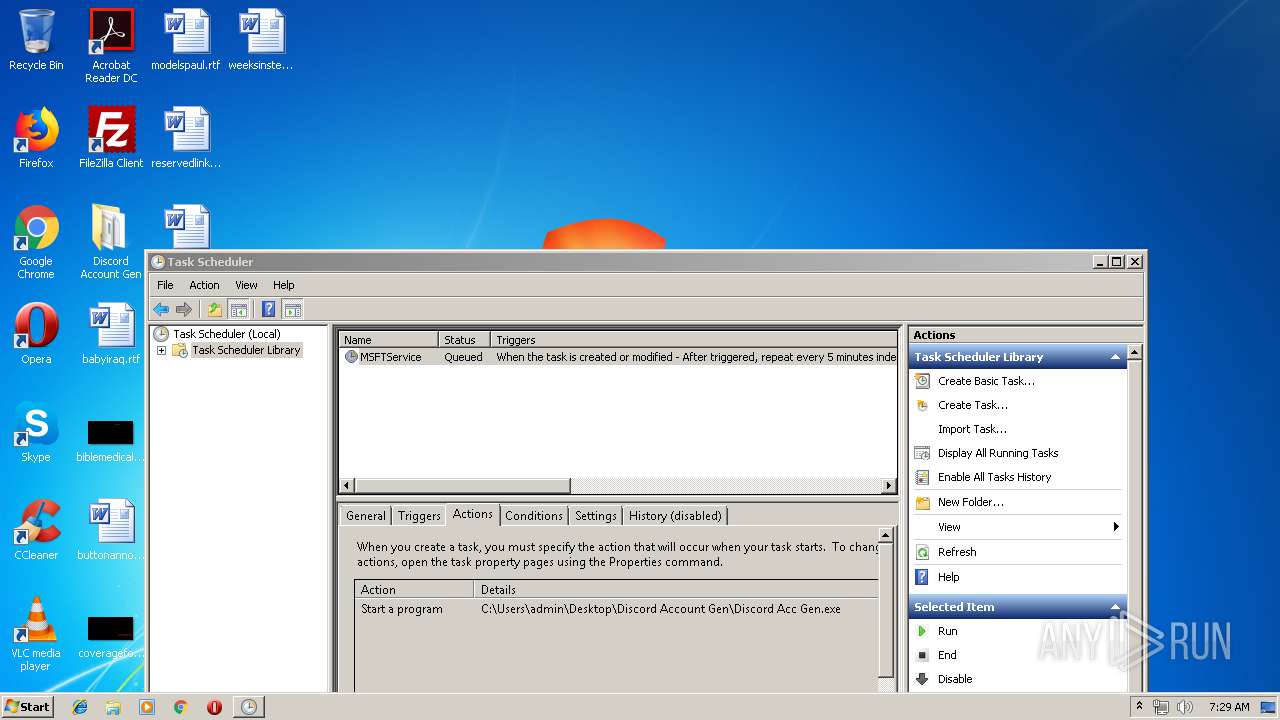
Loads the Task Scheduler COM API
- Discord Acc Gen.exe (PID: 2560)
- mmc.exe (PID: 1684)
Application was dropped or rewritten from another process
- ProfileService.exe (PID: 1664)
- ProfileService.exe (PID: 3212)
Changes settings of System certificates
- Discord Acc Gen.exe (PID: 2560)
Orcus was detected
- Discord Acc Gen.exe (PID: 2560)
- Discord Acc Gen.exe (PID: 2900)
Loads dropped or rewritten executable
- Discord Acc Gen.exe (PID: 2560)
Orcus RAT was detected
- ProfileService.exe (PID: 1664)
SUSPICIOUS
Executed via Task Scheduler
- Discord Acc Gen.exe (PID: 2900)
Adds / modifies Windows certificates
- Discord Acc Gen.exe (PID: 2560)
Application launched itself
- ProfileService.exe (PID: 1664)
Executable content was dropped or overwritten
- Discord Acc Gen.exe (PID: 2560)
Creates files in the user directory
- Discord Acc Gen.exe (PID: 2560)
Searches for installed software
- Discord Acc Gen.exe (PID: 2560)
INFO
Manual execution by user
- Discord Acc Gen.exe (PID: 2560)
- mmc.exe (PID: 1684)
- mmc.exe (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
62
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1520 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES9AEC.tmp" "c:\Users\admin\AppData\Local\Temp\CSC9AEB.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1664 | "C:\Users\admin\AppData\Local\Temp\ProfileService.exe" /launchSelfAndExit "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" 2560 /protectFile | C:\Users\admin\AppData\Local\Temp\ProfileService.exe | Discord Acc Gen.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3212 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1684 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "shutdown.exe" /r /t 0 | C:\Windows\system32\shutdown.exe | — | Discord Acc Gen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" | C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2900 | "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" | C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3092 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | "C:\Users\admin\AppData\Local\Temp\ProfileService.exe" /watchProcess "C:\Users\admin\Desktop\Discord Account Gen\Discord Acc Gen.exe" 2560 "/protectFile" | C:\Users\admin\AppData\Local\Temp\ProfileService.exe | — | ProfileService.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3284 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\m7m2fpni.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | Discord Acc Gen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 3284 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\q5hlt_eq.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | Discord Acc Gen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
Total events
1 337
Read events
1 306
Write events
31
Delete events
0
Modification events
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\4.rar | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2560) Discord Acc Gen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2560) Discord Acc Gen.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE09000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030353000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C01400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748501D00000001000000100000005B3B67000EEB80022E42605B6B3B72400B000000010000000E000000740068006100770074006500000003000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B812000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
Executable files
8
Suspicious files
4
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
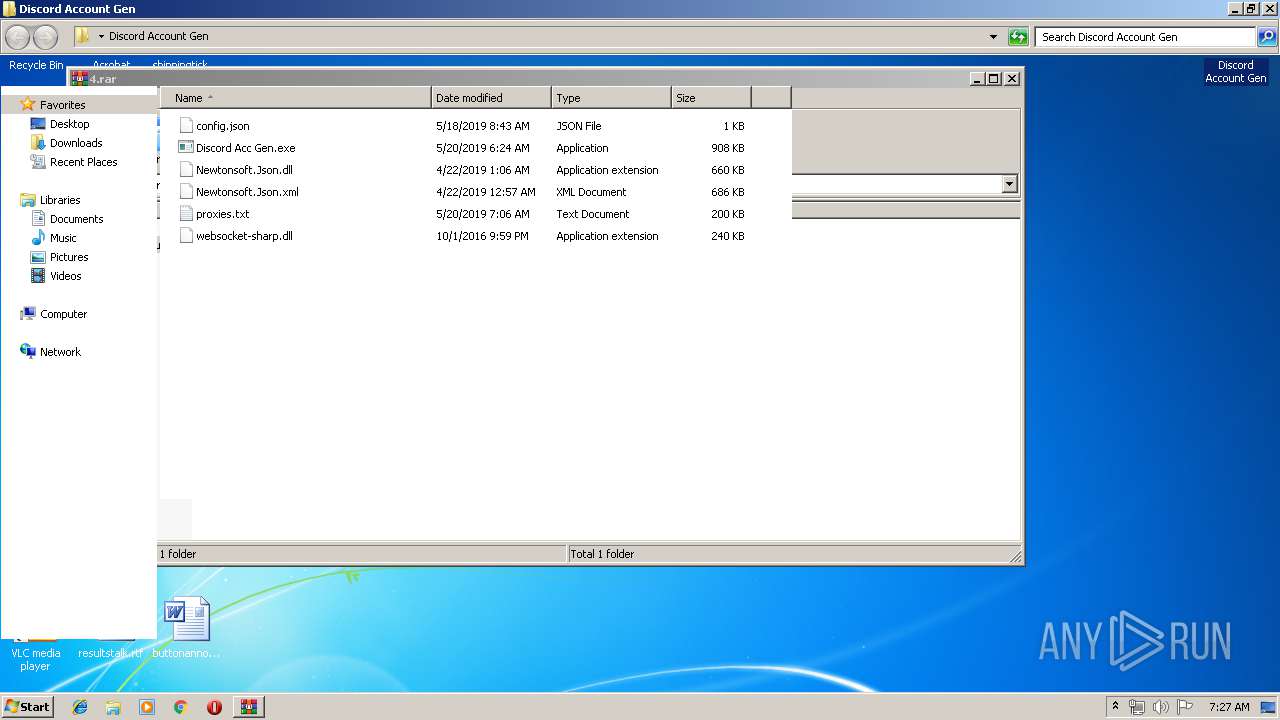
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.15319\Discord Account Gen\config.json | — | |
MD5:— | SHA256:— | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.15319\Discord Account Gen\Discord Acc Gen.exe | — | |
MD5:— | SHA256:— | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.15319\Discord Account Gen\Newtonsoft.Json.dll | — | |
MD5:— | SHA256:— | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.15319\Discord Account Gen\Newtonsoft.Json.xml | — | |
MD5:— | SHA256:— | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.15319\Discord Account Gen\proxies.txt | — | |
MD5:— | SHA256:— | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.15319\Discord Account Gen\websocket-sharp.dll | — | |
MD5:— | SHA256:— | |||
| 2560 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\q5hlt_eq.0.cs | — | |
MD5:— | SHA256:— | |||
| 2560 | Discord Acc Gen.exe | C:\Users\admin\AppData\Local\Temp\q5hlt_eq.cmdline | — | |
MD5:— | SHA256:— | |||
| 3284 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC96B5.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | csc.exe | C:\Users\admin\AppData\Local\Temp\q5hlt_eq.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2560 | Discord Acc Gen.exe | GET | 200 | 67.26.75.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2560 | Discord Acc Gen.exe | 35.189.92.148:1337 | — | Google Inc. | US | malicious |
2560 | Discord Acc Gen.exe | 67.26.75.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2560 | Discord Acc Gen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Malicious SSL Certificate (Orcus RAT) |
2560 | Discord Acc Gen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Malicious SSL Certificate (Orcus RAT) |
2560 | Discord Acc Gen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Malicious SSL connection (Orcus RAT) |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|