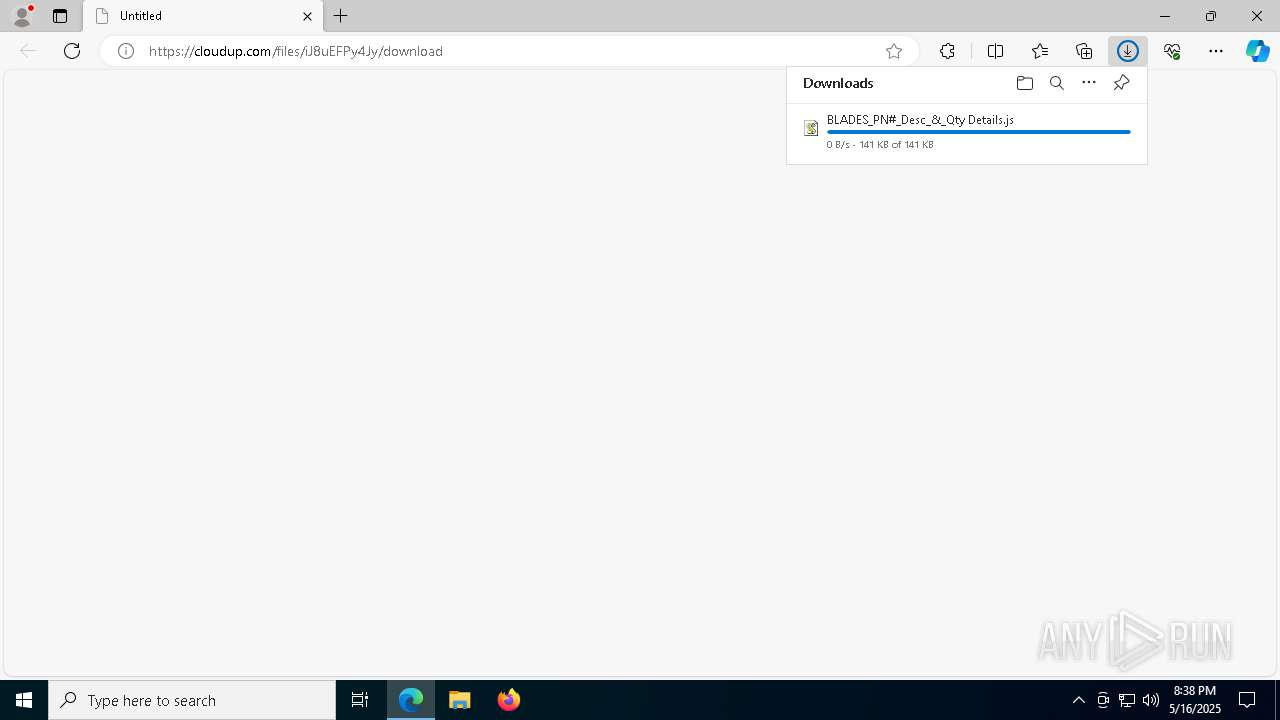
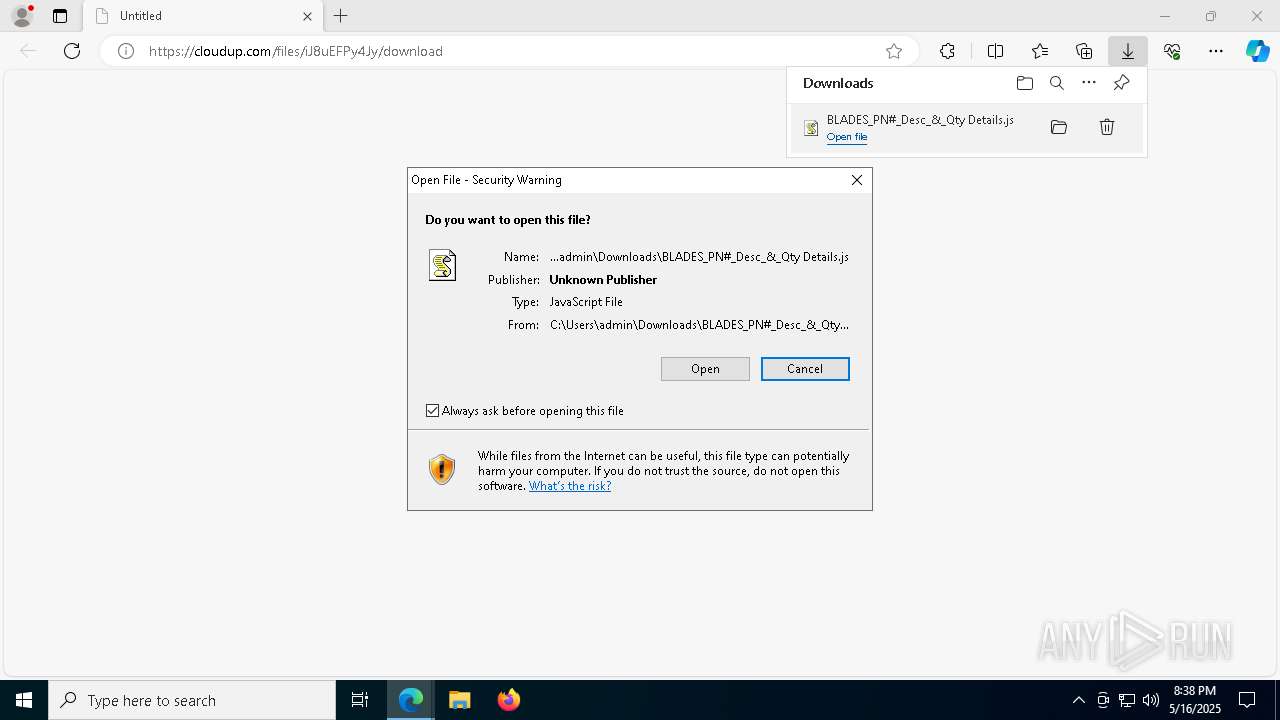
| URL: | https://cloudup.com/files/iJ8uEFPy4Jy/download |
| Full analysis: | https://app.any.run/tasks/77f04d87-99f1-4759-9a71-34d1e9bdee1b |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | May 16, 2025, 20:38:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D6F5E312676B87542C8A591E73471171 |
| SHA1: | 596C11A86E7B9C882A57A69C9153CBEEF7D20D25 |
| SHA256: | 3FFD75EEB796D413B7C4B2AEA4A89A56A527EEE87E899A1C55DD8108A91A61B8 |
| SSDEEP: | 3:N8ULBQVyTLKS1I84z:2UaQTXY |
MALICIOUS
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 8136)
- powershell.exe (PID: 1764)
- cmd.exe (PID: 7872)
- powershell.exe (PID: 5304)
- cmd.exe (PID: 7716)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8120)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 6668)
Bypass execution policy to execute commands
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 8120)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8112)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 6080)
- powershell.exe (PID: 7700)
- powershell.exe (PID: 5680)
- powershell.exe (PID: 2772)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 7884)
- powershell.exe (PID: 516)
- powershell.exe (PID: 1676)
- powershell.exe (PID: 5124)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3956)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 3024)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1764)
Starts CMD.EXE for self-deleting
- powershell.exe (PID: 5304)
Adds path to the Windows Defender exclusion list
- powershell.exe (PID: 5304)
Changes Windows Defender settings
- powershell.exe (PID: 5304)
Run PowerShell with an invisible window
- powershell.exe (PID: 8120)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8112)
- powershell.exe (PID: 7836)
NjRAT is detected
- InstallUtil.exe (PID: 2644)
NJRAT has been detected (SURICATA)
- InstallUtil.exe (PID: 2644)
Connects to the CnC server
- InstallUtil.exe (PID: 2644)
SUSPICIOUS
The process executes JS scripts
- msedge.exe (PID: 2320)
- powershell.exe (PID: 8136)
Base64-obfuscated command line is found
- wscript.exe (PID: 856)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 856)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 856)
- powershell.exe (PID: 8136)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 7716)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8120)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 6668)
Runs shell command (SCRIPT)
- wscript.exe (PID: 856)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 8136)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 8136)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 1128)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 8136)
Application launched itself
- powershell.exe (PID: 8136)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8120)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 6668)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 1764)
Probably obfuscated PowerShell command line is found
- powershell.exe (PID: 8136)
- wscript.exe (PID: 856)
Get information on the list of running processes
- powershell.exe (PID: 8136)
Probably download files using WebClient
- powershell.exe (PID: 8136)
Potential Corporate Privacy Violation
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
The process executes Powershell scripts
- powershell.exe (PID: 1764)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 7716)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8120)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 6668)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 5304)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5576)
- cmd.exe (PID: 4152)
- cmd.exe (PID: 8144)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5304)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 664)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 8120)
Uses NETSH.EXE to add a firewall rule or allowed programs
- InstallUtil.exe (PID: 2644)
Contacting a server suspected of hosting an CnC
- InstallUtil.exe (PID: 2644)
Connects to unusual port
- InstallUtil.exe (PID: 2644)
INFO
Application launched itself
- msedge.exe (PID: 2320)
Reads Environment values
- identity_helper.exe (PID: 5056)
Reads the computer name
- identity_helper.exe (PID: 5056)
- InstallUtil.exe (PID: 2644)
Reads Microsoft Office registry keys
- msedge.exe (PID: 2320)
Checks supported languages
- identity_helper.exe (PID: 5056)
- InstallUtil.exe (PID: 2644)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 8136)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 1128)
Reads the software policy settings
- powershell.exe (PID: 1764)
Create files in a temporary directory
- powershell.exe (PID: 1764)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 8136)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 1764)
Disables trace logs
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
Reads security settings of Internet Explorer
- powershell.exe (PID: 1764)
Checks proxy server information
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5304)
Creates a new folder
- cmd.exe (PID: 6244)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 780)
- powershell.exe (PID: 8056)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 780)
- powershell.exe (PID: 8056)
The sample compiled with english language support
- msedge.exe (PID: 2236)
Executable content was dropped or overwritten
- msedge.exe (PID: 2236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
239
Monitored processes
96
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5376 --field-trial-handle=2312,i,12756668713861725635,16835725267848544613,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 516 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -file "C:\Users\admin\AppData\LocalLow\Daft Sytem (x86)\Program Rules NVIDEO\Program Rules NVIDEO\Program Rules NVIDEO\Program Rules NVIDEO\cmmgc.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7372 --field-trial-handle=2312,i,12756668713861725635,16835725267848544613,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 664 | cmd.exe /k reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7644 --field-trial-handle=2312,i,12756668713861725635,16835725267848544613,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 684 | ping 127.0.0.1 -n 1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=5896 --field-trial-handle=2312,i,12756668713861725635,16835725267848544613,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 780 | powershell $S = 'C:\Windows\Microsoft.NET\Framework\v4.0.30319\' ; Add-MpPreference -ExclusionPath $S -force ; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
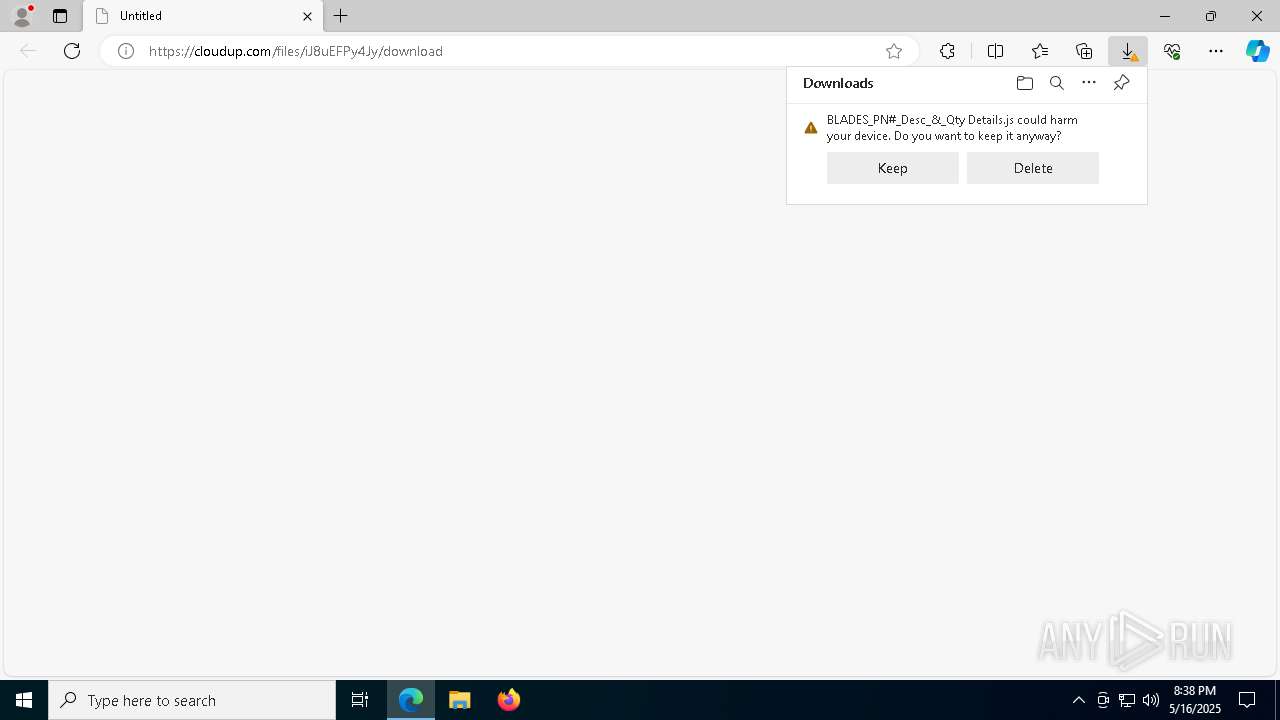
| 856 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\BLADES_PN#_Desc_&_Qty Details.js" | C:\Windows\System32\wscript.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
121 253
Read events
121 195
Write events
57
Delete events
1
Modification events
| (PID) Process: | (2320) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 7328260CDD932F00 | |||
| (PID) Process: | (2320) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: DF392F0CDD932F00 | |||
| (PID) Process: | (2320) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197232 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7D38E2B0-B57B-4144-8159-AB3146A09B1E} | |||
| (PID) Process: | (2320) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197232 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {643FFCE5-7481-409D-A152-21427AA0E4A2} | |||
| (PID) Process: | (6148) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6148) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6148) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6148) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (6148) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (6148) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
Executable files
14
Suspicious files
400
Text files
143
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b855.TMP | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b865.TMP | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b865.TMP | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b874.TMP | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b894.TMP | — | |
MD5:— | SHA256:— | |||
| 2320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
73
DNS requests
81
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5984 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7656 | svchost.exe | HEAD | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1747705080&P2=404&P3=2&P4=FjLaAMrpuIZZYzwDNtl4OuCsfnEy50GTDdTuKBqg7rrQi%2bS0i2cEo6hvvWHZe%2fneKVK8%2bOxaDelZonQSFkZZkg%3d%3d | unknown | — | — | whitelisted |
7656 | svchost.exe | HEAD | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1747705080&P2=404&P3=2&P4=RsAqy%2fnDlSEy8n2HfcJKGx92nIgA8nxkWHAw8dHAqxNZflZvUjFHBIIPsPR96lryURvdmn81asYtenGUX6Pm4A%3d%3d | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7656 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1747705080&P2=404&P3=2&P4=envjuzX7f8u3EWIgufUDCk88B0XgVb7DAlkgqA8Jn%2f%2bWJ%2bm7R%2fdCFUDTYT1%2bA22%2fnhPoqZ%2bx%2b2gaMd9gf5R6ZA%3d%3d | unknown | — | — | whitelisted |
7656 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1747705080&P2=404&P3=2&P4=FjLaAMrpuIZZYzwDNtl4OuCsfnEy50GTDdTuKBqg7rrQi%2bS0i2cEo6hvvWHZe%2fneKVK8%2bOxaDelZonQSFkZZkg%3d%3d | unknown | — | — | whitelisted |
7656 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1747705080&P2=404&P3=2&P4=FjLaAMrpuIZZYzwDNtl4OuCsfnEy50GTDdTuKBqg7rrQi%2bS0i2cEo6hvvWHZe%2fneKVK8%2bOxaDelZonQSFkZZkg%3d%3d | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7656 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1747705080&P2=404&P3=2&P4=envjuzX7f8u3EWIgufUDCk88B0XgVb7DAlkgqA8Jn%2f%2bWJ%2bm7R%2fdCFUDTYT1%2bA22%2fnhPoqZ%2bx%2b2gaMd9gf5R6ZA%3d%3d | unknown | — | — | whitelisted |
7656 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1747705080&P2=404&P3=2&P4=envjuzX7f8u3EWIgufUDCk88B0XgVb7DAlkgqA8Jn%2f%2bWJ%2bm7R%2fdCFUDTYT1%2bA22%2fnhPoqZ%2bx%2b2gaMd9gf5R6ZA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
7324 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2320 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cloudup.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
cldup.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
1764 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
5304 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
2644 | InstallUtil.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 41 |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.bumbleshrimp .com Domain |
2644 | InstallUtil.exe | Misc activity | ET INFO Possible Host Profile Exfiltration In Pipe Delimited Format |
2644 | InstallUtil.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] njRAT Bladabindi CnC Communication command li |
2644 | InstallUtil.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] njRAT Bladabindi CnC Communication command inf |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.sytes.net Domain |