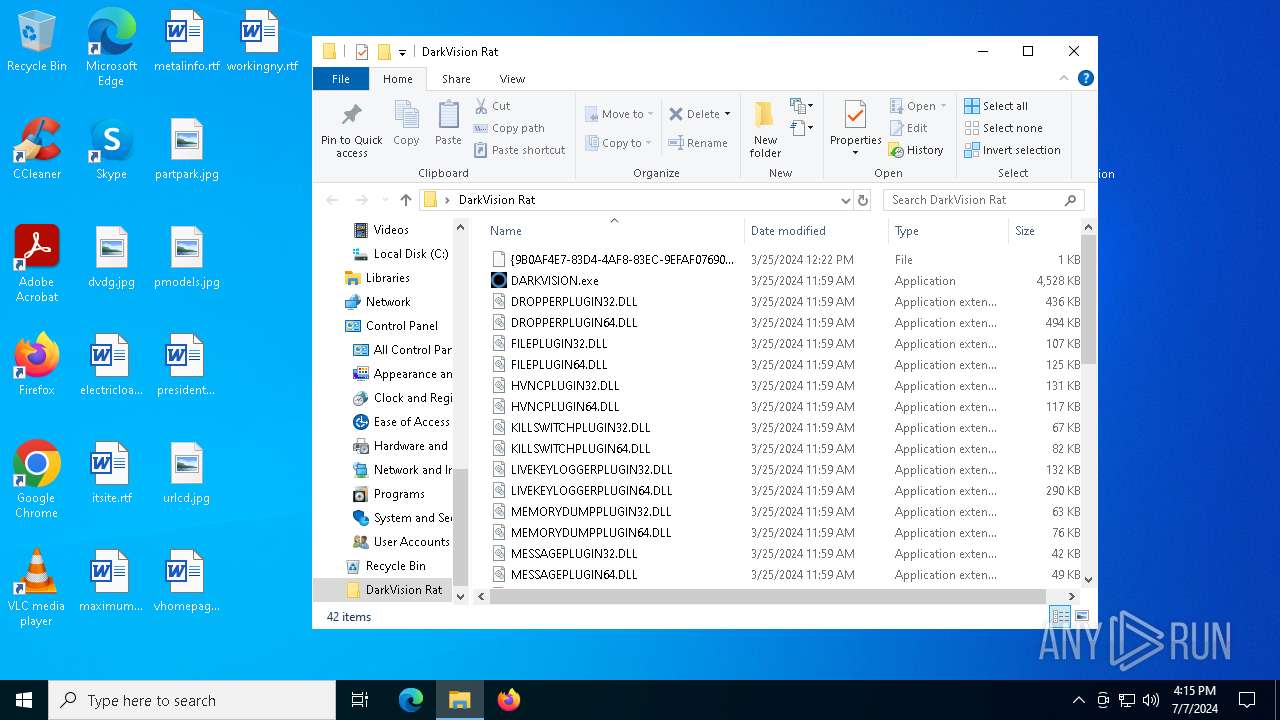
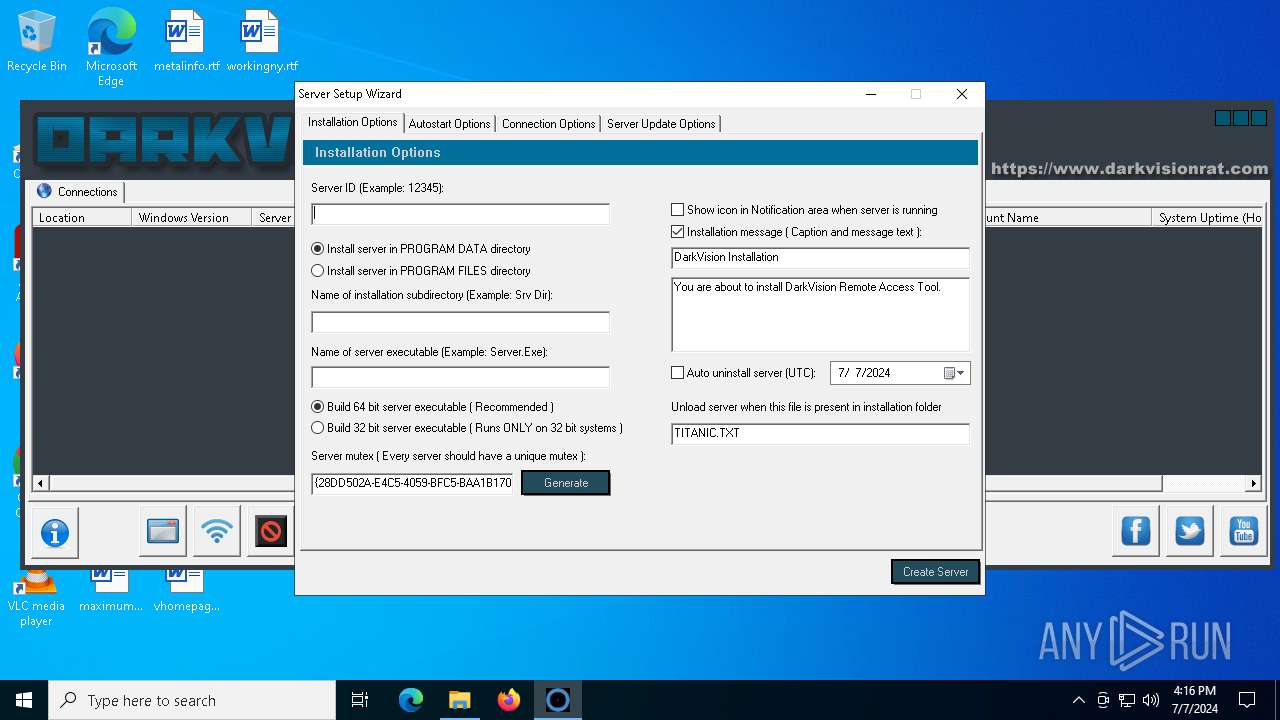
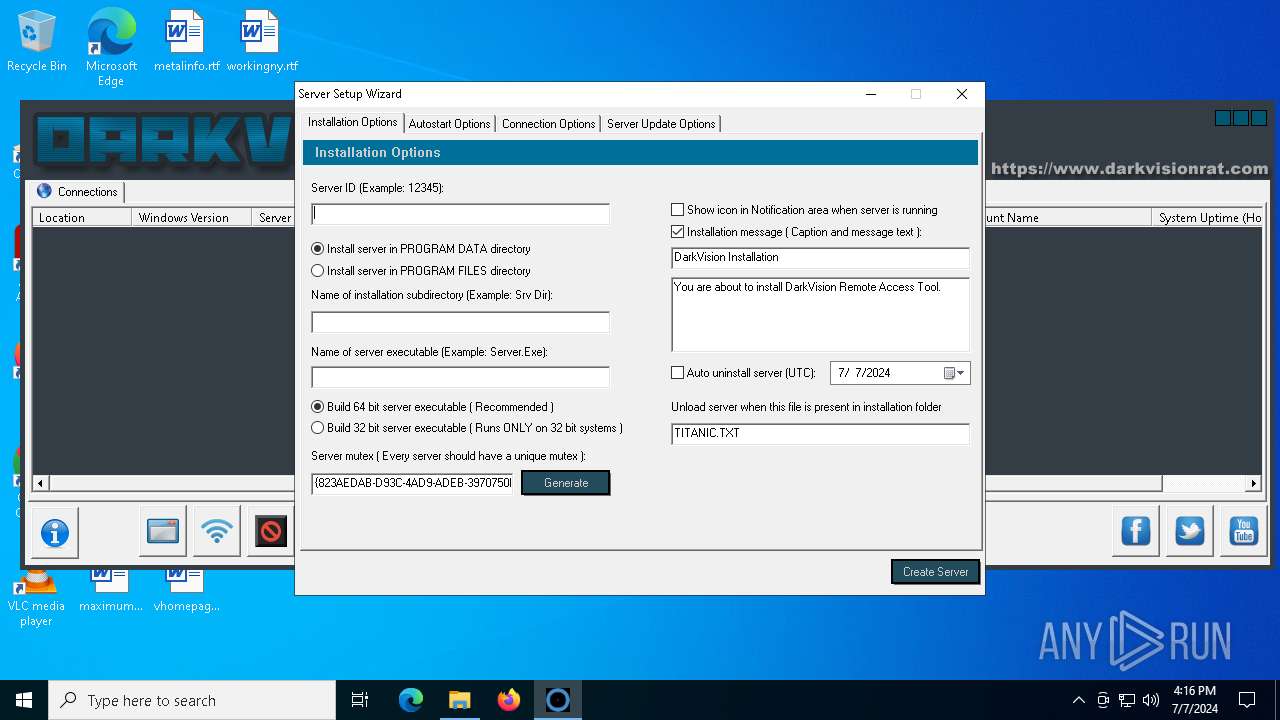
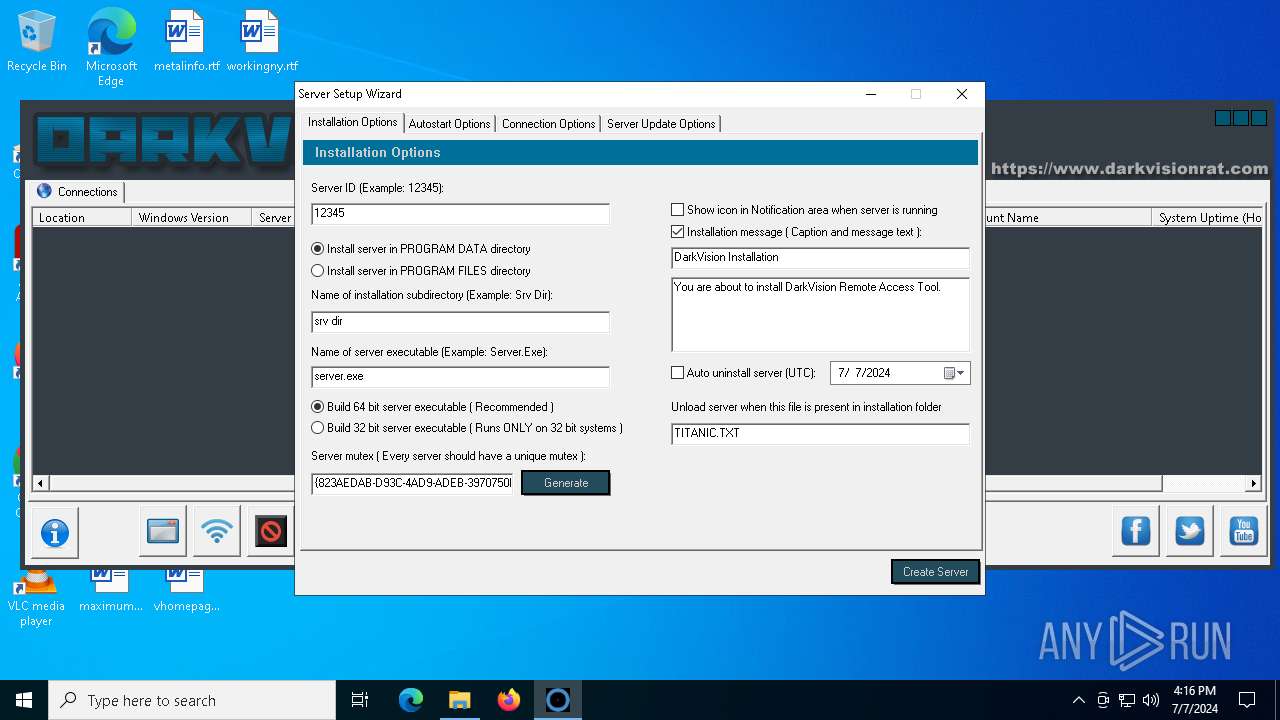
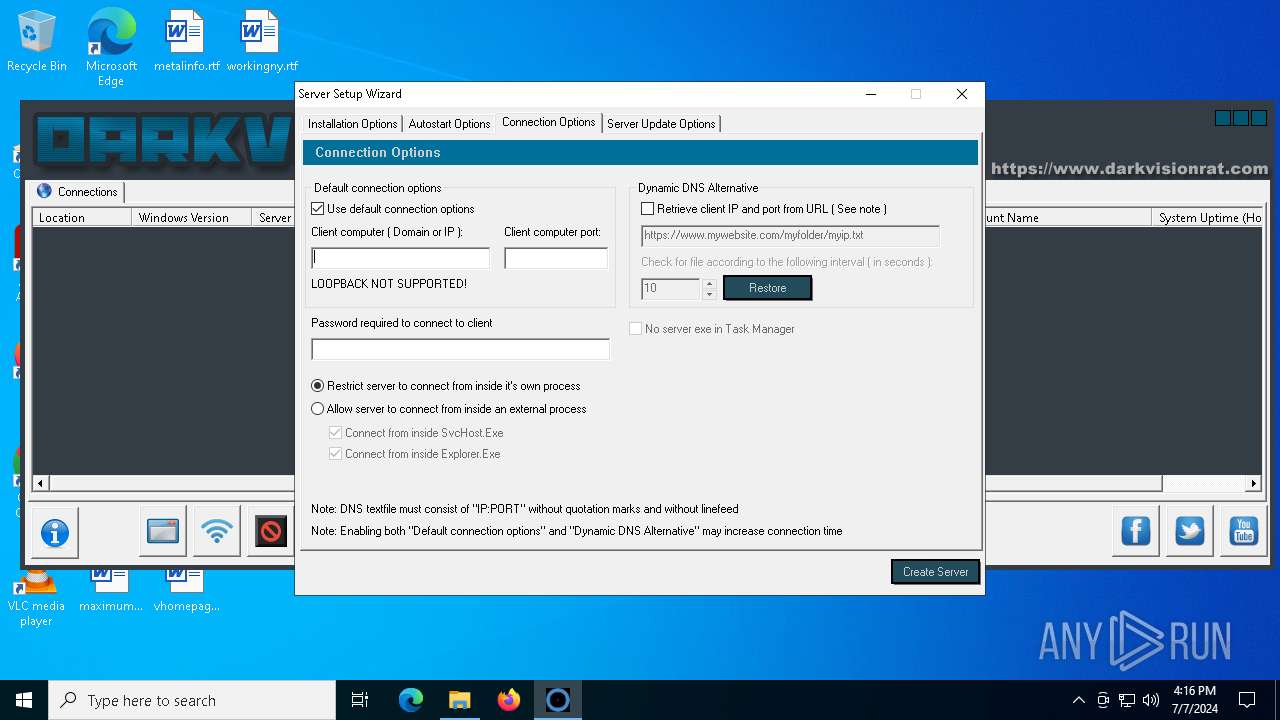
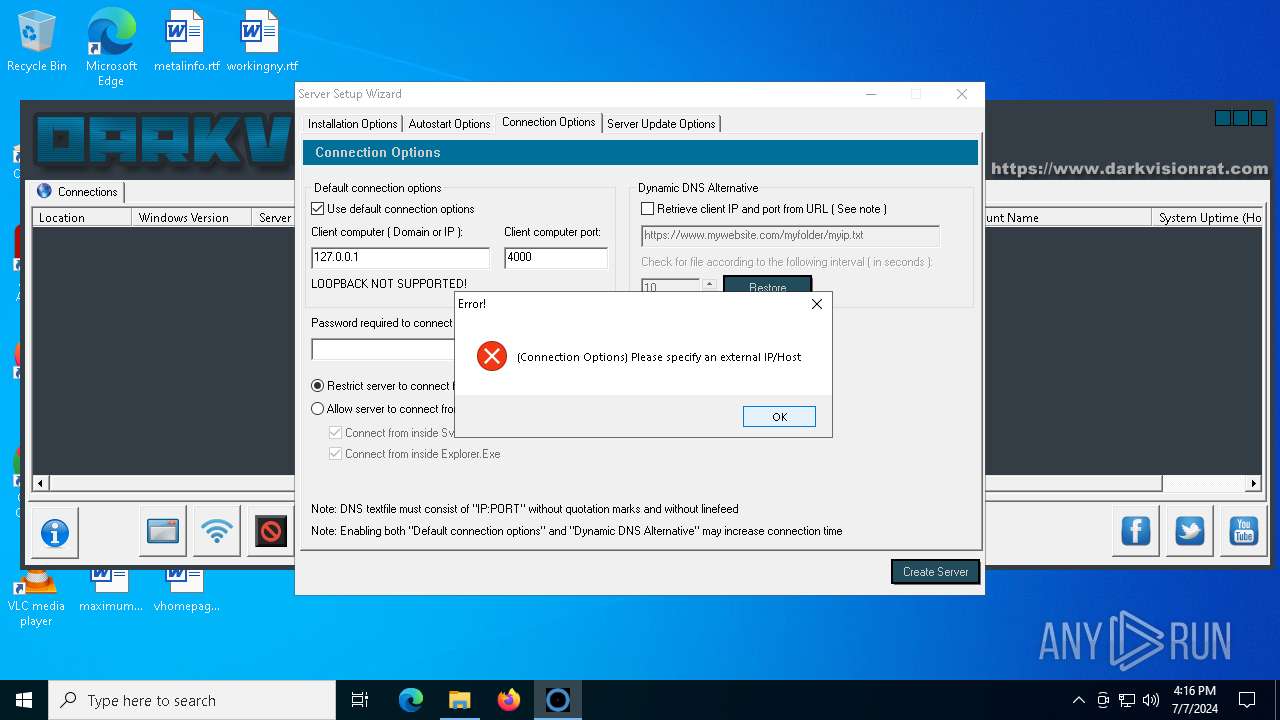
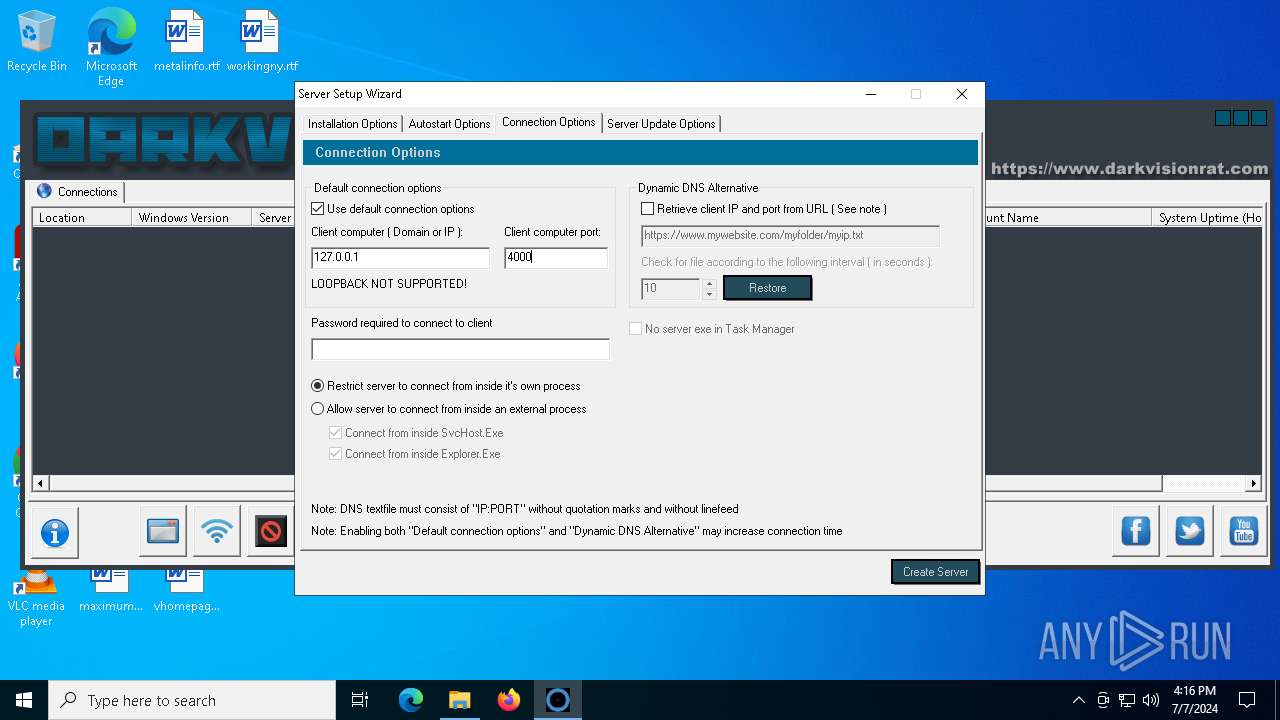
| File name: | DarkVision Rat.7z |
| Full analysis: | https://app.any.run/tasks/043218d7-789a-4271-9673-0b26bceda3cc |
| Verdict: | Malicious activity |
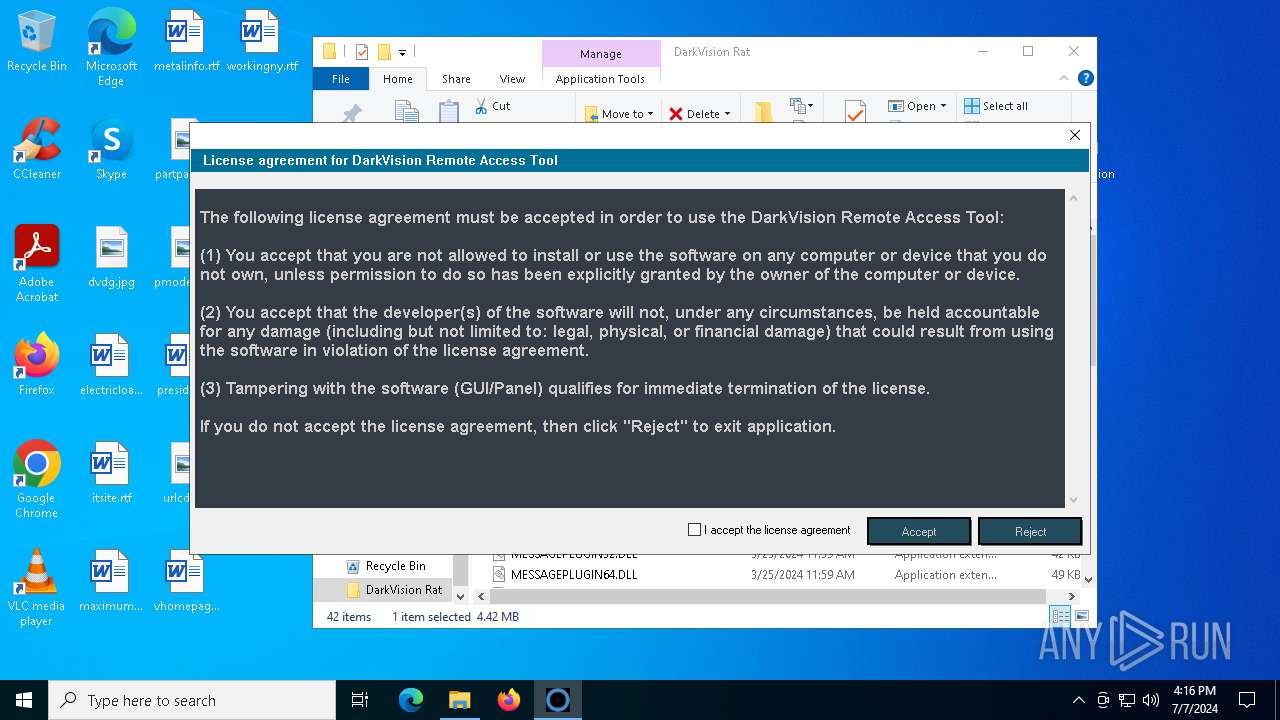
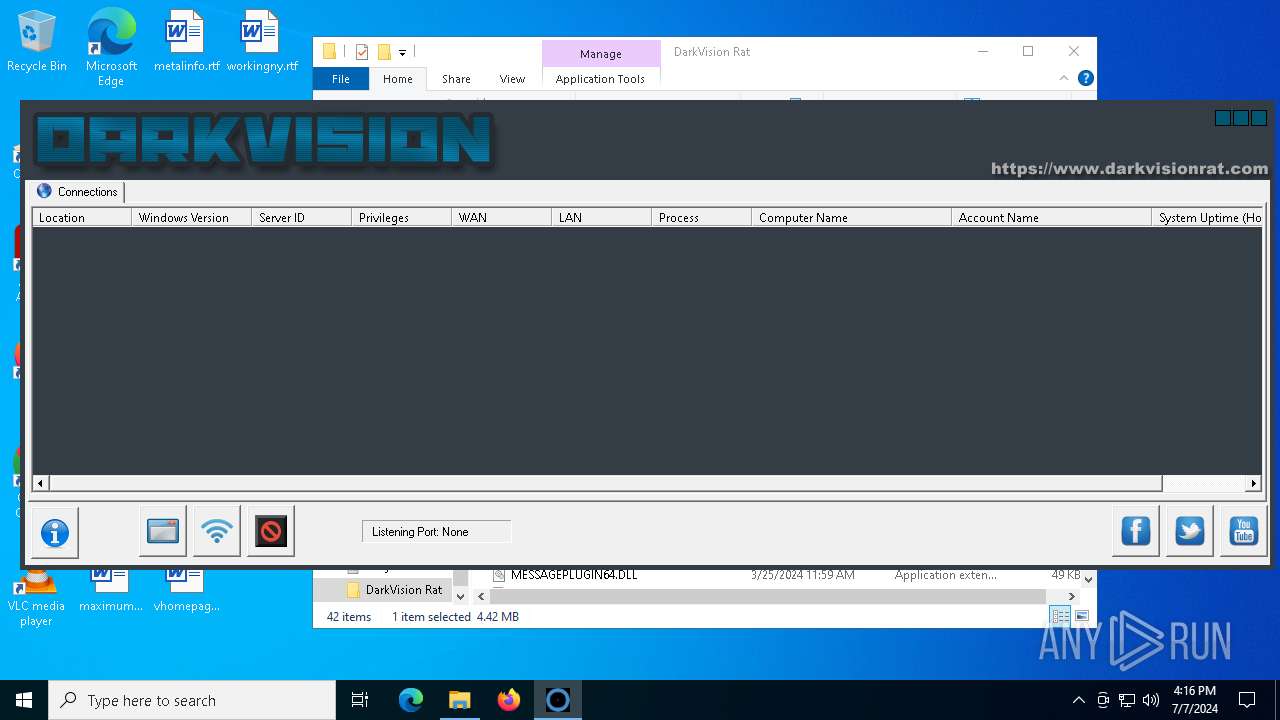
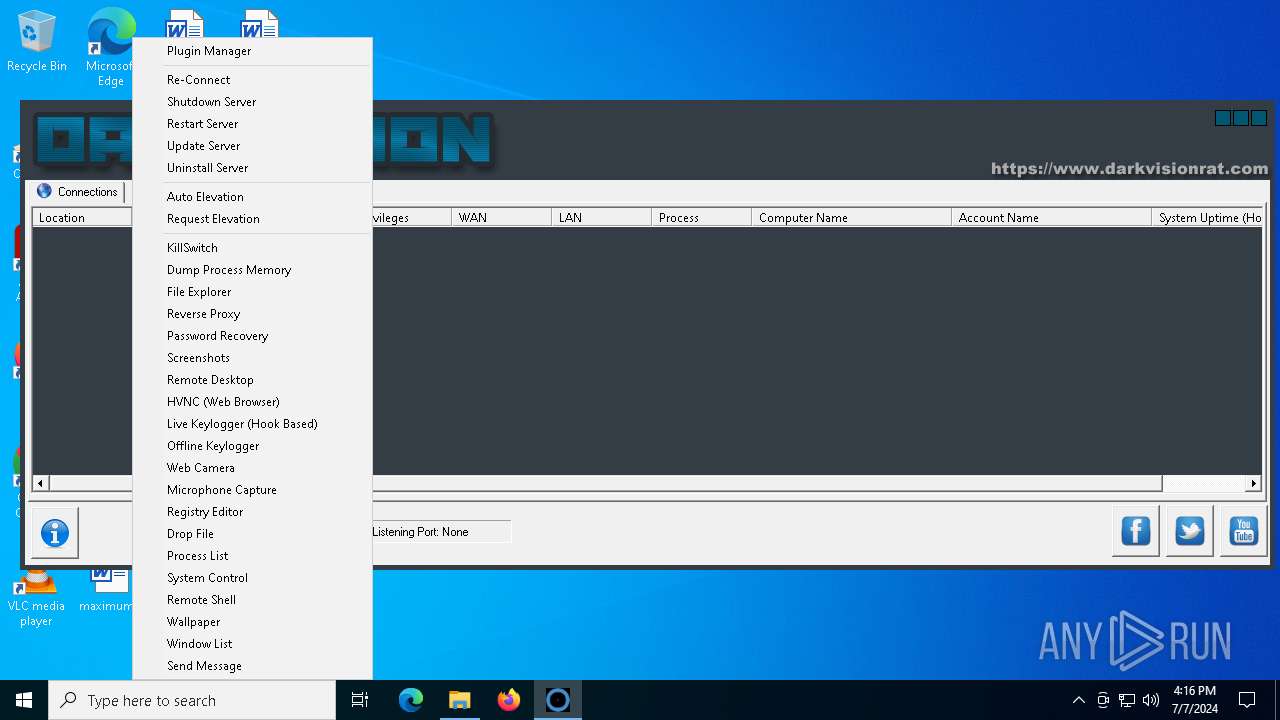
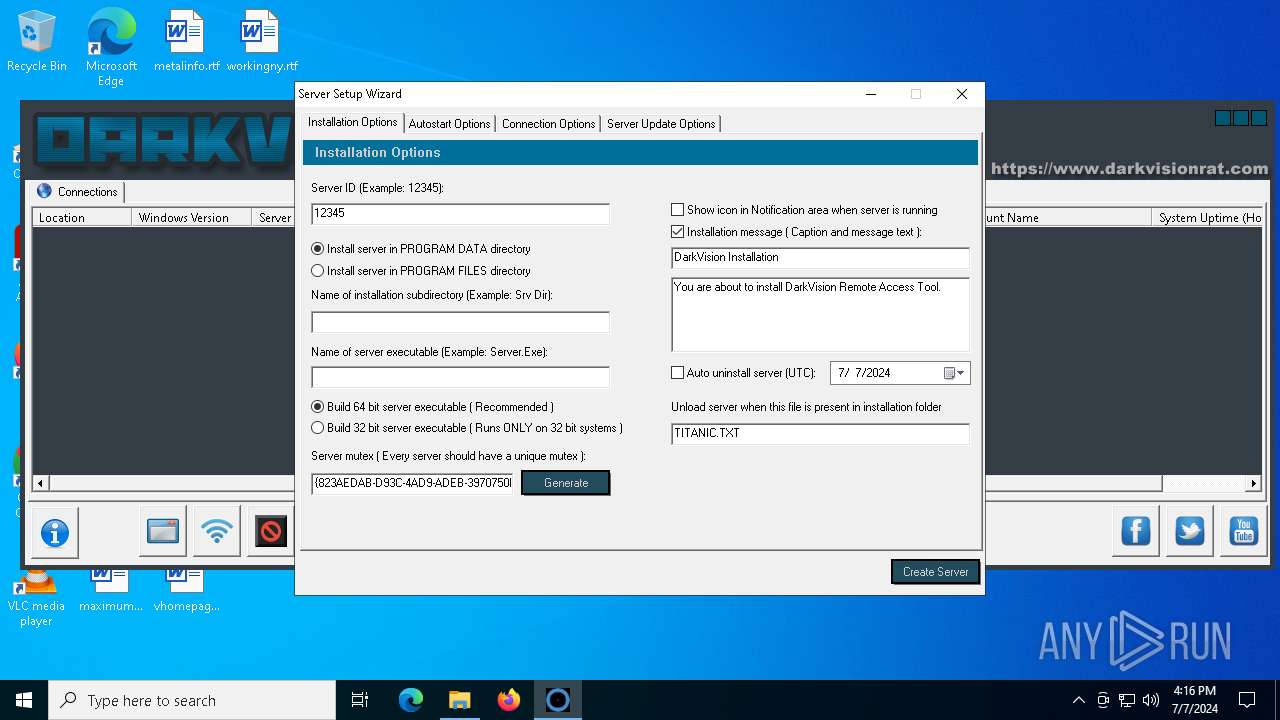
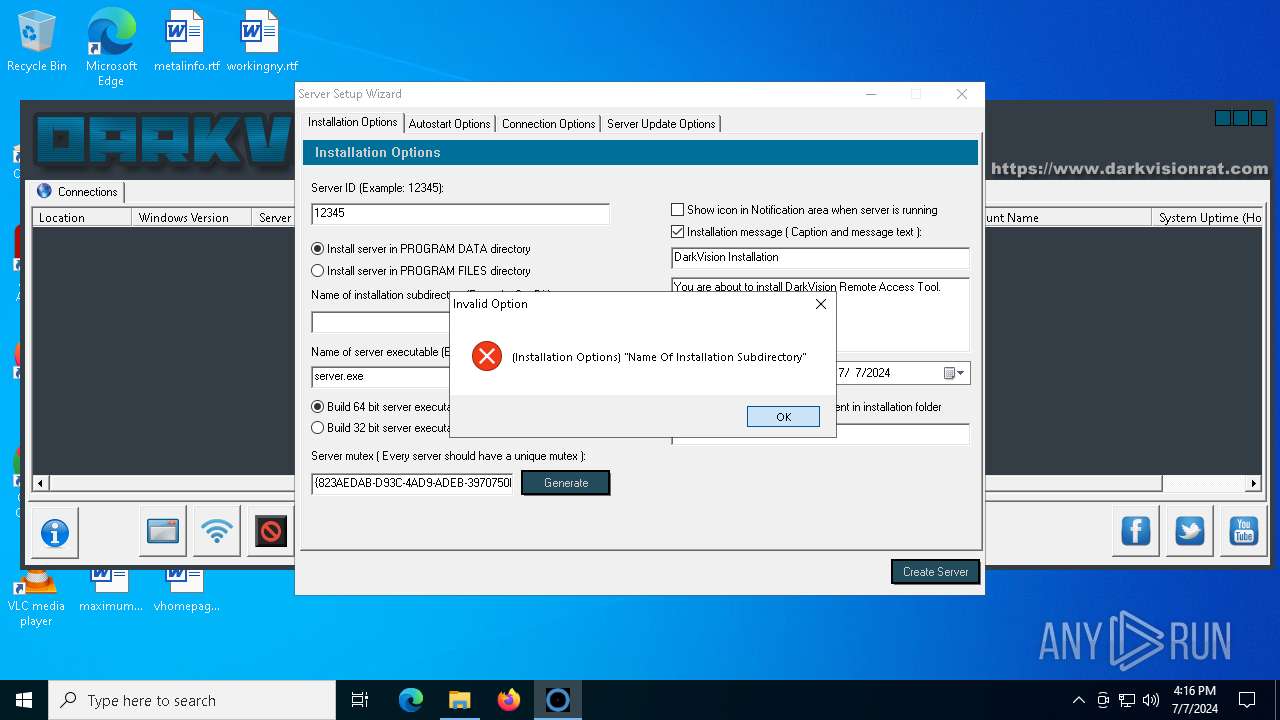
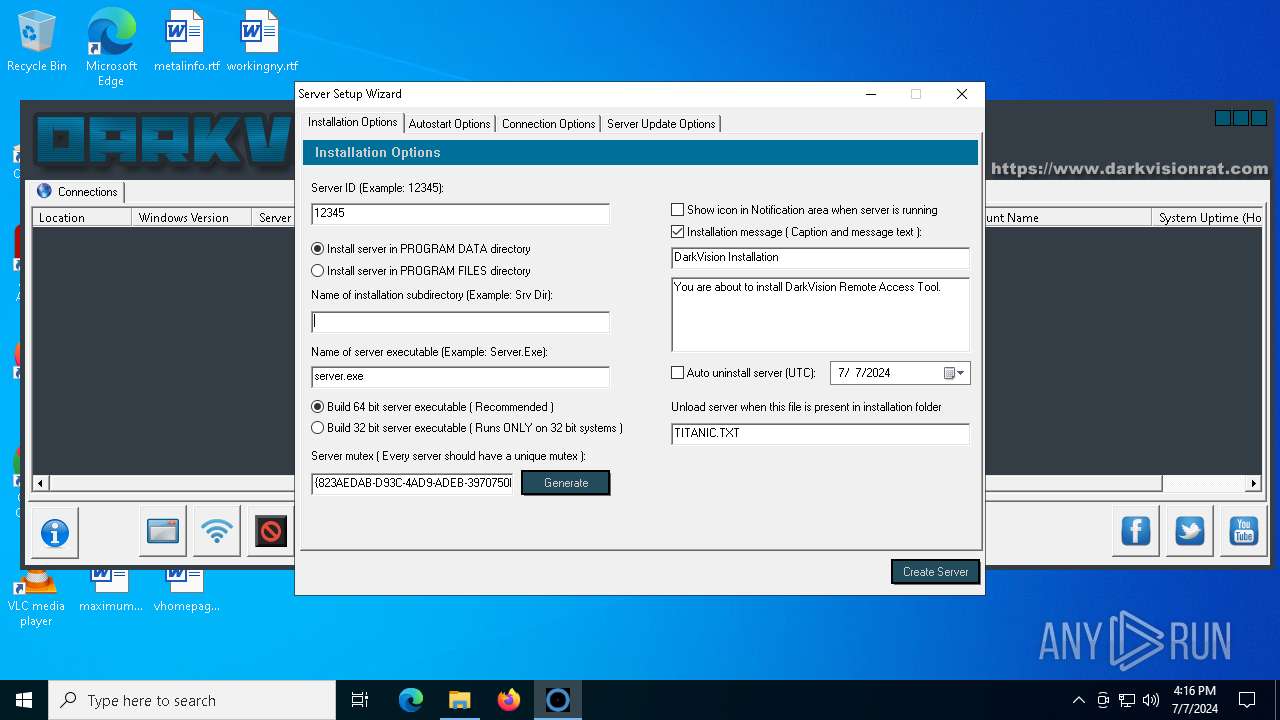
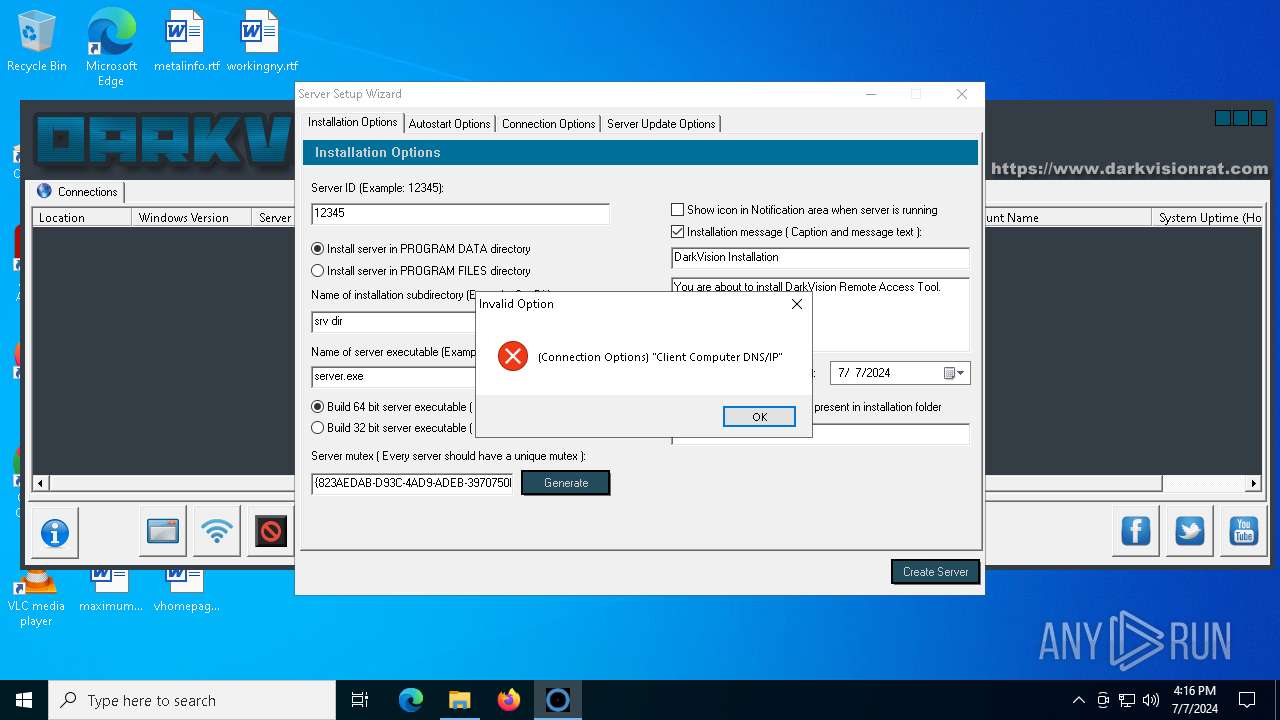
| Threats: | DarkVision RAT is a low-cost, modular Remote Access Trojan that gives attackers remote control of infected Windows hosts. Initially observed around 2020 and sold in underground marketplaces, DarkVision has become notable for its full feature set (keylogging, screen capture, file theft, remote command execution and plugin support) and for being distributed via multi-stage loaders in recent campaigns. |
| Analysis date: | July 07, 2024, 16:14:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3FFE675EBA4CB6AE5D5FF93A600E1635 |
| SHA1: | 8EC8F85F0879D86BBE776ABAFF8AFB3B08C27950 |
| SHA256: | 3F6692D2E43BCFA91FD2D663BC64BAC34D7CBD4EAA009C94010D27822111CBD9 |
| SSDEEP: | 98304:5jjxeUFKYYeg/hFktd9jE85Kl7nlQ8bYD9rBN6E5VKYIkCWRdxQ2pbh5y2DDm+bX:BfVOHyR2Vy |
MALICIOUS
[YARA] DarkVision RAT is detected
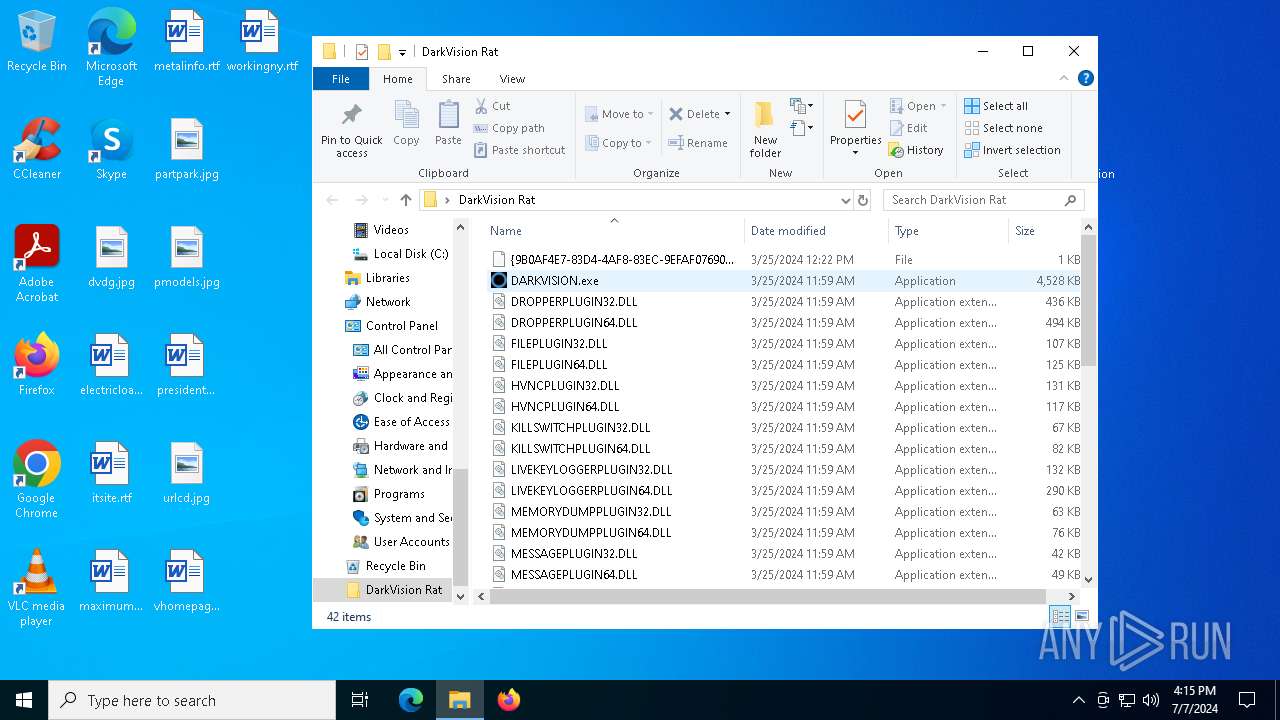
- DARKVISION.exe (PID: 6788)
SUSPICIOUS
Reads security settings of Internet Explorer
- DARKVISION.exe (PID: 6700)
Reads the date of Windows installation
- DARKVISION.exe (PID: 6700)
Application launched itself
- DARKVISION.exe (PID: 6700)
INFO
Reads the computer name
- DARKVISION.exe (PID: 6700)
- DARKVISION.exe (PID: 6788)
Checks supported languages
- DARKVISION.exe (PID: 6700)
- DARKVISION.exe (PID: 6788)
Manual execution by a user
- DARKVISION.exe (PID: 6700)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4928)
Process checks computer location settings
- DARKVISION.exe (PID: 6700)
Reads the machine GUID from the registry
- DARKVISION.exe (PID: 6788)
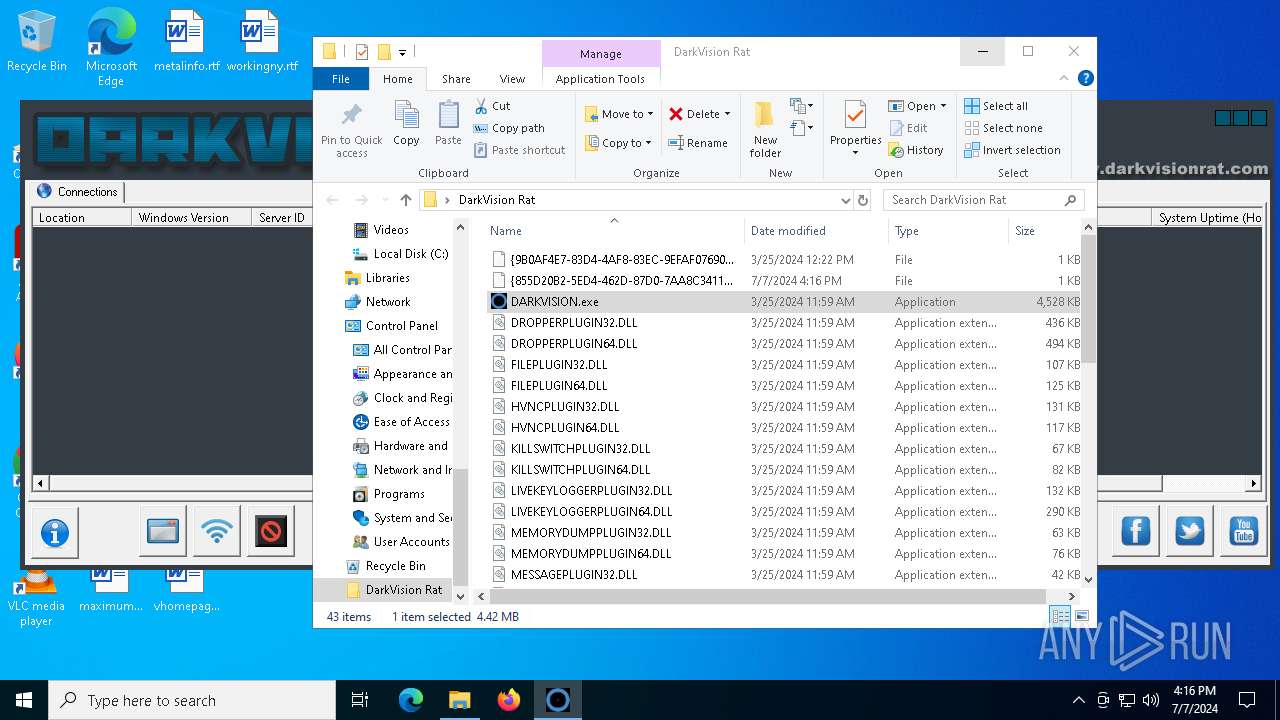
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
143
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4928 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DarkVision Rat.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6652 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6700 | "C:\Users\admin\Desktop\DarkVision Rat\DARKVISION.exe" | C:\Users\admin\Desktop\DarkVision Rat\DARKVISION.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6788 | "C:\Users\admin\Desktop\DarkVision Rat\DARKVISION.exe" | C:\Users\admin\Desktop\DarkVision Rat\DARKVISION.exe | DARKVISION.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
5 848
Read events
5 820
Write events
28
Delete events
0
Modification events
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DarkVision Rat.7z | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (4928) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
41
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\HVNCPLUGIN64.DLL | executable | |
MD5:D8947667CD885C994FCD17D00A357197 | SHA256:55C347FE6766C3D23EF13335C66F22FB84F666DBF0956480BE7A5B95181AE53C | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\DROPPERPLUGIN32.DLL | executable | |
MD5:40CC4932320C65FBB5CF1B07CD6D42AB | SHA256:96454417229C3629BBAE5C909A1A15770F0AEA6BB633C28CE12AA3105E51A1DB | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\KILLSWITCHPLUGIN32.DLL | executable | |
MD5:11136E1D724062472757AA6C01B0A647 | SHA256:A834923FEE51F196F348EF993C584F576D4C7EAFF85EA6D8E1A794121B673D70 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\FILEPLUGIN64.DLL | executable | |
MD5:15F74A7350ED9A19D15BE88E965D77DE | SHA256:3EF8922F7BB2C456CB50B698EBD6B68561D3D74BBBA0CBA5B334F99497A97FF9 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\KILLSWITCHPLUGIN64.DLL | executable | |
MD5:3778830910DA7411F5FCF878F535A52E | SHA256:9F37EBB3F41C58C76700027BBC5B61010B86905841017FEFD51AB0173C651B86 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\MEMORYDUMPPLUGIN64.DLL | executable | |
MD5:C97C8DFC56BE6C9647C696506BB4D868 | SHA256:AB47332BA8A2DECBAC3D1D3EFD44B0B548196C0900EE8DD4858D85DED2C34F35 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\LIVEKEYLOGGERPLUGIN32.DLL | executable | |
MD5:6FABA5D510102796DB1F261817D79DB3 | SHA256:992A8CAFBDBEF8033956774C57200E4CF535DB9E05AF0181650E14AA3C81DD20 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\FILEPLUGIN32.DLL | executable | |
MD5:C35D2454860618AD9CE671A6081E6540 | SHA256:20C66FB1356518CFAEDB95CB3C7F8DD779A7EBA398280DFB916799C545D2DB82 | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\LIVEKEYLOGGERPLUGIN64.DLL | executable | |
MD5:EF5FE080B132E438C2AE6EB347E161D7 | SHA256:7DE2A17B84BC2649F36D94FFE7B6FA30FC278A13105CA1788C194B212556B1CC | |||
| 4928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4928.21466\DarkVision Rat\MESSAGEPLUGIN32.DLL | executable | |
MD5:184460C9F99EB154F7982A8221C6484E | SHA256:FFD57E8C9C6F5AC7C4EF782CABD7D87D5F52F429B2E11B6EF11B644D911CCF78 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
79
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1452 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2064 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2060 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2060 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2064 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1452 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4636 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
5600 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6356 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.139:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2060 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2064 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1452 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2064 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1452 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2060 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |