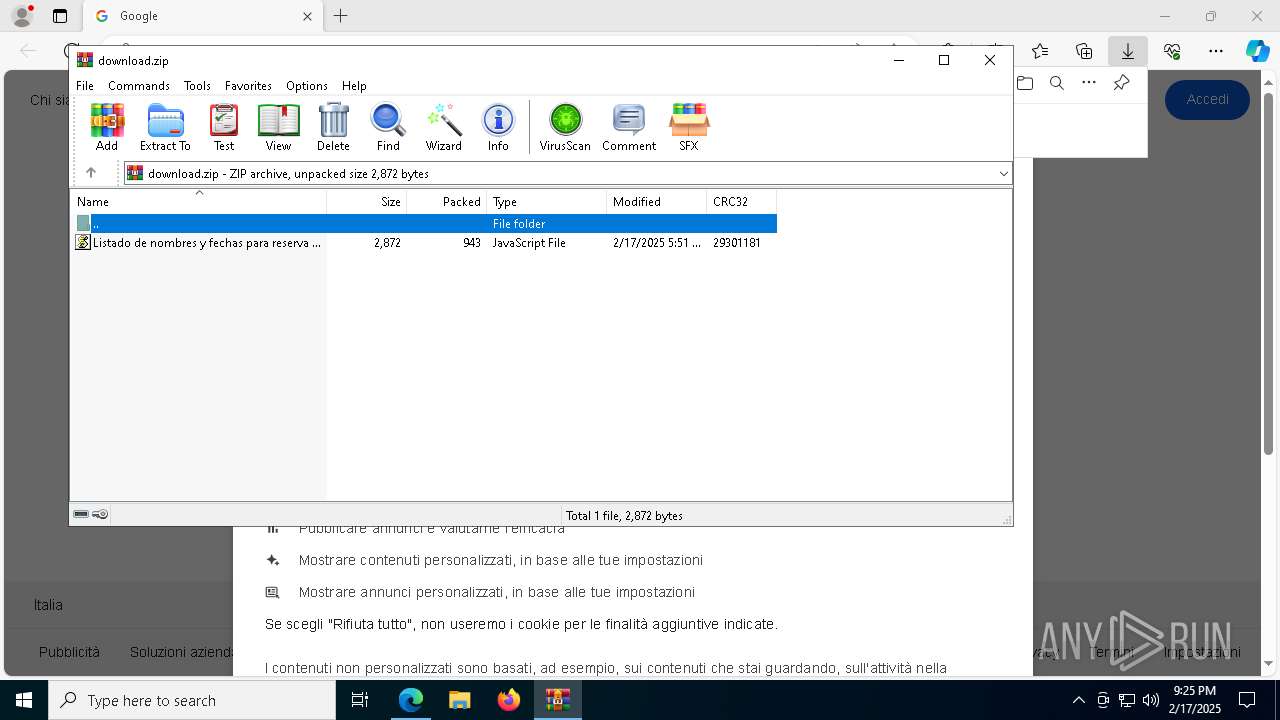
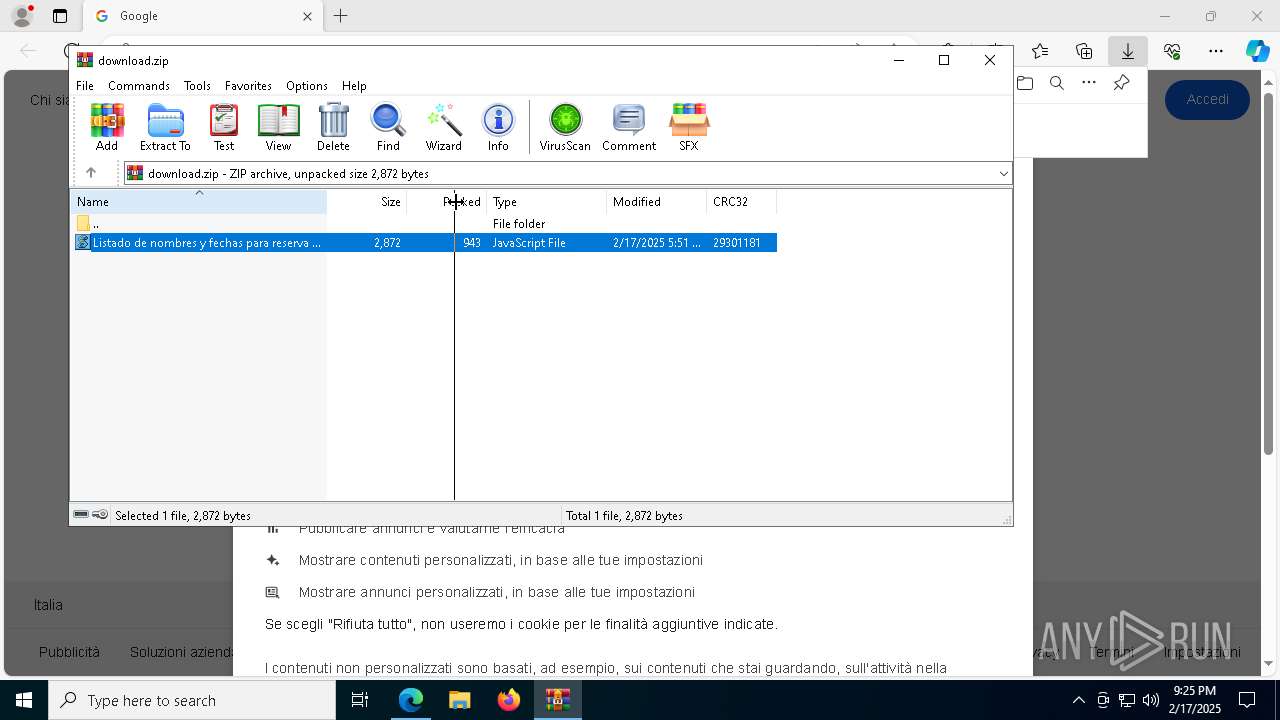
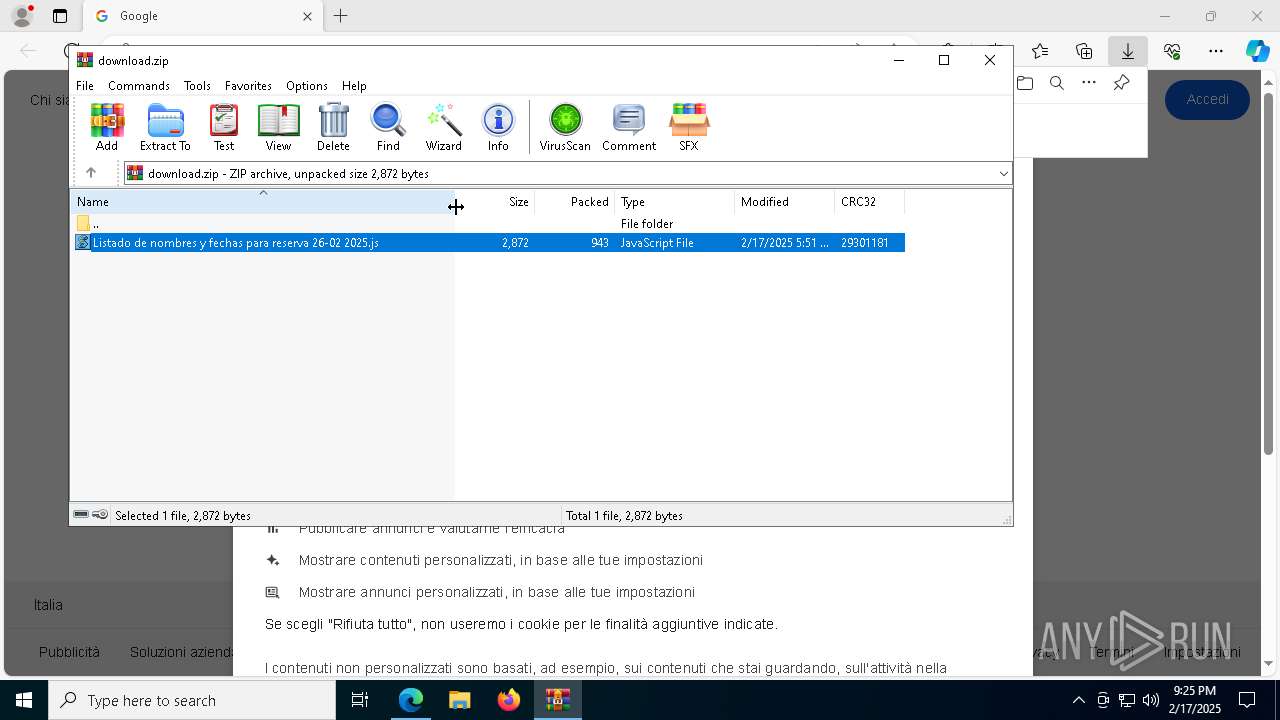
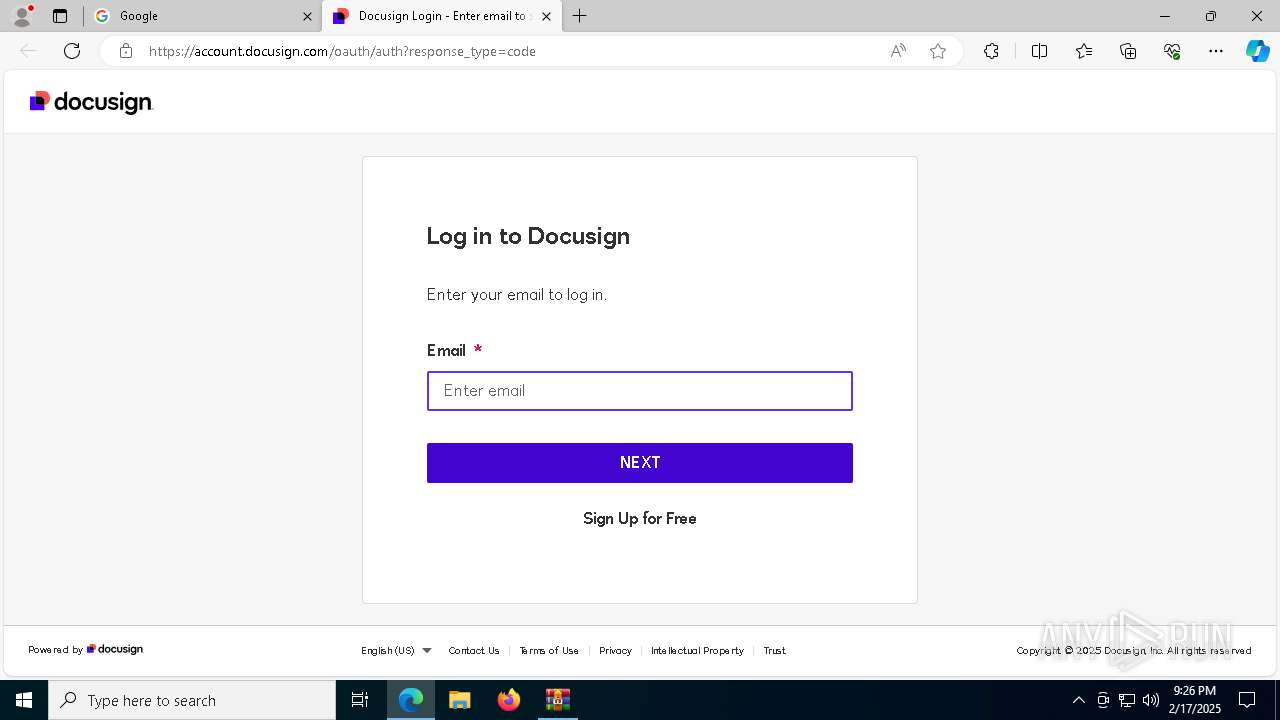
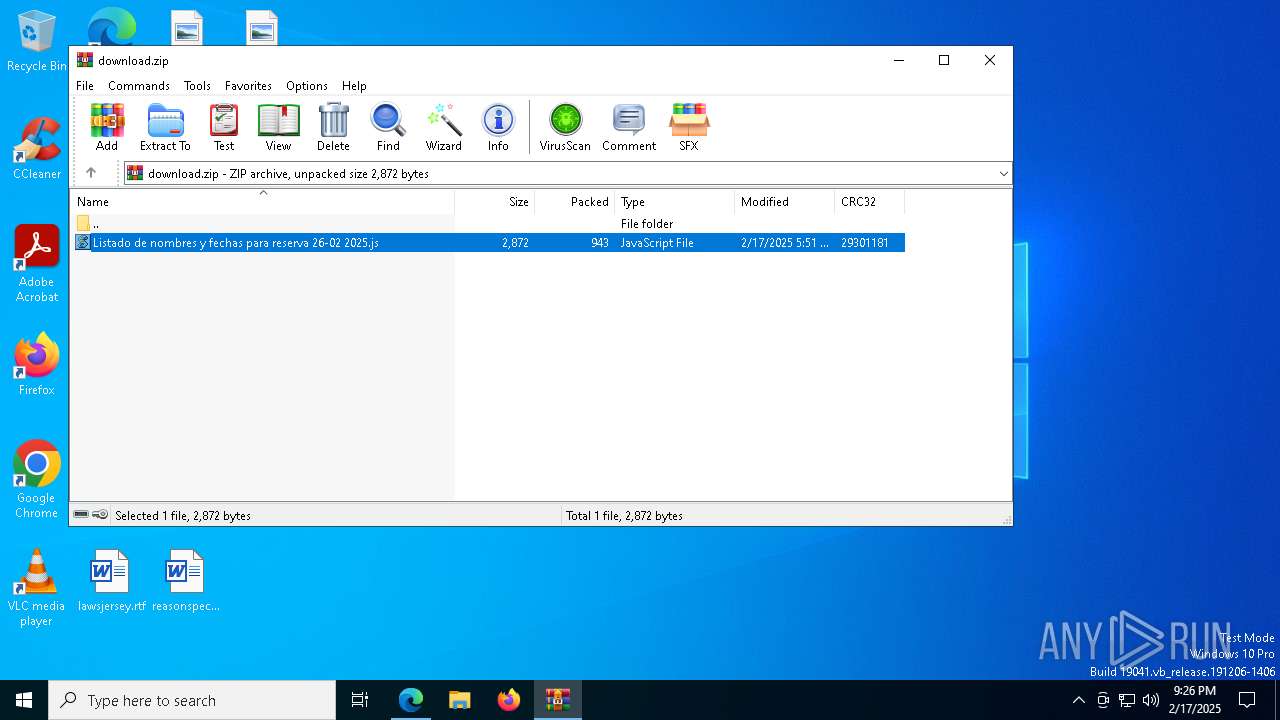
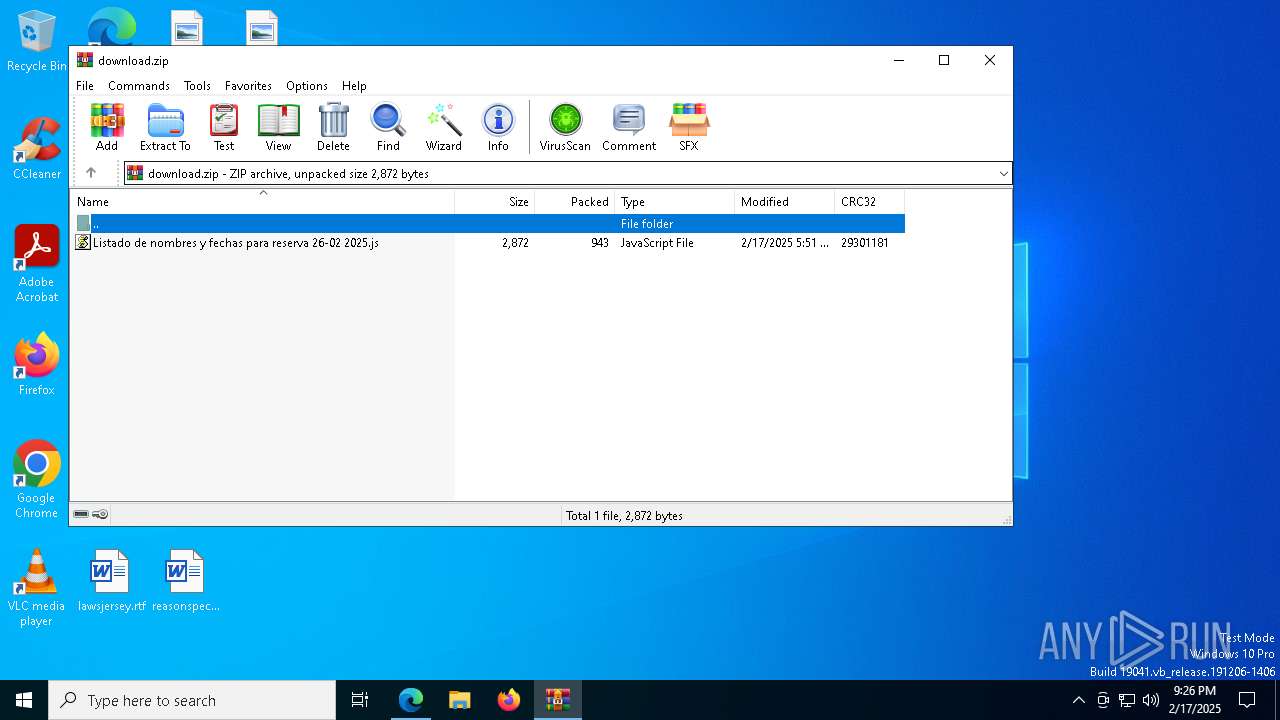
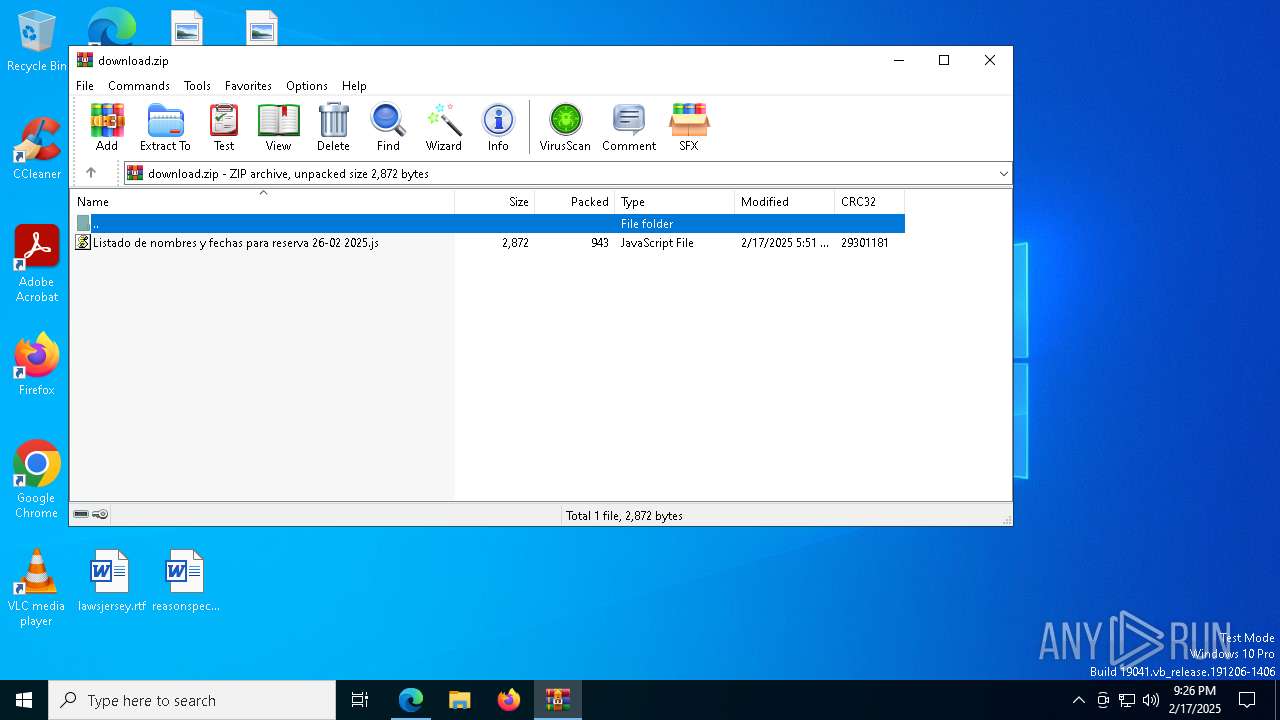
| URL: | https://emailmarketing.locaweb.com.br/accounts/196904/messages/4/clicks/22601/8?envelope_id=4 |
| Full analysis: | https://app.any.run/tasks/d3e4571e-b865-43ac-97b0-66c953adbc79 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 17, 2025, 21:25:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B5305C187A9672E7BFE4FC6617F9DB9E |
| SHA1: | F42551B364030A309D83A28EA1B7C1CF2E864424 |
| SHA256: | 3ECBF13ED6CAB087109718C7F7D8C90B85D5D027A4D9FFEB696FC506E49EA4F1 |
| SSDEEP: | 3:N8k1E4C9FArYGKUic7KcC9bXJRLsKq8:2k1iAcRU/7KhbXJRLu8 |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7320)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 7388)
Run PowerShell with an invisible window
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 4264)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 4704)
- cmd.exe (PID: 4992)
- cmd.exe (PID: 5828)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 5780)
- cmd.exe (PID: 6560)
Bypass execution policy to execute commands
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 4264)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
PSLORAMYRA has been detected
- wscript.exe (PID: 8112)
- wscript.exe (PID: 3152)
- wscript.exe (PID: 1224)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 2392)
- wscript.exe (PID: 6604)
- wscript.exe (PID: 8092)
- wscript.exe (PID: 6012)
- wscript.exe (PID: 6524)
- wscript.exe (PID: 5696)
- wscript.exe (PID: 7500)
- wscript.exe (PID: 4120)
ASYNCRAT has been detected (MUTEX)
- aspnet_regbrowsers.exe (PID: 4624)
- aspnet_regbrowsers.exe (PID: 7448)
- aspnet_regbrowsers.exe (PID: 8088)
- aspnet_regbrowsers.exe (PID: 3920)
- aspnet_regbrowsers.exe (PID: 5404)
- aspnet_regbrowsers.exe (PID: 5856)
- aspnet_regbrowsers.exe (PID: 7852)
Steals credentials from Web Browsers
- aspnet_regbrowsers.exe (PID: 4624)
ASYNCRAT has been detected (SURICATA)
- aspnet_regbrowsers.exe (PID: 4624)
Actions looks like stealing of personal data
- aspnet_regbrowsers.exe (PID: 4624)
ASYNCRAT has been detected (YARA)
- aspnet_regbrowsers.exe (PID: 4624)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7956)
- aspnet_regbrowsers.exe (PID: 4624)
The process executes JS scripts
- WinRAR.exe (PID: 7956)
- aspnet_regbrowsers.exe (PID: 4624)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7320)
- wscript.exe (PID: 8112)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 7388)
- wscript.exe (PID: 3152)
- wscript.exe (PID: 1224)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 2392)
- wscript.exe (PID: 6604)
- wscript.exe (PID: 8092)
- wscript.exe (PID: 6012)
- wscript.exe (PID: 6524)
- wscript.exe (PID: 5696)
- wscript.exe (PID: 7500)
- wscript.exe (PID: 4120)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7320)
- wscript.exe (PID: 8112)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 3152)
- wscript.exe (PID: 7388)
- wscript.exe (PID: 1224)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 2392)
- wscript.exe (PID: 6604)
- wscript.exe (PID: 8092)
- wscript.exe (PID: 6012)
- wscript.exe (PID: 6524)
- wscript.exe (PID: 5696)
- wscript.exe (PID: 7500)
- wscript.exe (PID: 4120)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 4704)
- cmd.exe (PID: 4992)
- cmd.exe (PID: 5828)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 5780)
- cmd.exe (PID: 6560)
Executes script without checking the security policy
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 4264)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 4704)
- cmd.exe (PID: 4992)
- cmd.exe (PID: 5828)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 5780)
- cmd.exe (PID: 6560)
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 8112)
- cmd.exe (PID: 7328)
- powershell.exe (PID: 7448)
- cmd.exe (PID: 4992)
- wscript.exe (PID: 3152)
- powershell.exe (PID: 5980)
- wscript.exe (PID: 1224)
- cmd.exe (PID: 6032)
- wscript.exe (PID: 7848)
- cmd.exe (PID: 6504)
- powershell.exe (PID: 7728)
- wscript.exe (PID: 2392)
- cmd.exe (PID: 7888)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- wscript.exe (PID: 6604)
- cmd.exe (PID: 4120)
- powershell.exe (PID: 1544)
- wscript.exe (PID: 8092)
- cmd.exe (PID: 7104)
- powershell.exe (PID: 132)
- wscript.exe (PID: 6012)
- cmd.exe (PID: 3632)
- powershell.exe (PID: 3364)
- wscript.exe (PID: 6524)
- cmd.exe (PID: 2008)
- powershell.exe (PID: 1328)
- wscript.exe (PID: 5696)
- cmd.exe (PID: 7272)
- powershell.exe (PID: 768)
- wscript.exe (PID: 7500)
- cmd.exe (PID: 5780)
- powershell.exe (PID: 7728)
- wscript.exe (PID: 4120)
- cmd.exe (PID: 6560)
- powershell.exe (PID: 5916)
The process executes VB scripts
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 4264)
Executing commands from a ".bat" file
- wscript.exe (PID: 8112)
- wscript.exe (PID: 3152)
- wscript.exe (PID: 1224)
- wscript.exe (PID: 7848)
- wscript.exe (PID: 2392)
- wscript.exe (PID: 6604)
- wscript.exe (PID: 8092)
- wscript.exe (PID: 6012)
- wscript.exe (PID: 6524)
- wscript.exe (PID: 5696)
- wscript.exe (PID: 7500)
- wscript.exe (PID: 4120)
The process executes Powershell scripts
- cmd.exe (PID: 7328)
- cmd.exe (PID: 4992)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 5780)
- cmd.exe (PID: 6560)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
Connects to unusual port
- aspnet_regbrowsers.exe (PID: 4624)
Contacting a server suspected of hosting an CnC
- aspnet_regbrowsers.exe (PID: 4624)
Executable content was dropped or overwritten
- aspnet_regbrowsers.exe (PID: 4624)
Creates file in the systems drive root
- aspnet_regbrowsers.exe (PID: 4624)
INFO
Checks supported languages
- identity_helper.exe (PID: 7184)
- aspnet_regbrowsers.exe (PID: 4624)
- aspnet_regbrowsers.exe (PID: 7448)
- mhnscj.exe (PID: 7964)
- aspnet_regbrowsers.exe (PID: 8088)
- aspnet_regbrowsers.exe (PID: 3920)
- aspnet_compiler.exe (PID: 6692)
- aspnet_regbrowsers.exe (PID: 5404)
- aspnet_regbrowsers.exe (PID: 5856)
- aspnet_compiler.exe (PID: 2736)
- aspnet_regbrowsers.exe (PID: 7852)
- aspnet_compiler.exe (PID: 1328)
- identity_helper.exe (PID: 3928)
Reads Environment values
- identity_helper.exe (PID: 7184)
- identity_helper.exe (PID: 3928)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6628)
- WinRAR.exe (PID: 7956)
Reads the computer name
- identity_helper.exe (PID: 7184)
- aspnet_regbrowsers.exe (PID: 4624)
- mhnscj.exe (PID: 7964)
- aspnet_regbrowsers.exe (PID: 7448)
- aspnet_regbrowsers.exe (PID: 8088)
- aspnet_regbrowsers.exe (PID: 3920)
- aspnet_compiler.exe (PID: 6692)
- aspnet_regbrowsers.exe (PID: 5404)
- aspnet_regbrowsers.exe (PID: 5856)
- aspnet_compiler.exe (PID: 2736)
- aspnet_regbrowsers.exe (PID: 7852)
- aspnet_compiler.exe (PID: 1328)
- identity_helper.exe (PID: 3928)
Checks transactions between databases Windows and Oracle
- wscript.exe (PID: 7320)
- wscript.exe (PID: 7848)
Checks proxy server information
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 4264)
Disables trace logs
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 4264)
Application launched itself
- msedge.exe (PID: 6628)
- msedge.exe (PID: 3608)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 7996)
- powershell.exe (PID: 4264)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 768)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7996)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 5916)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7448)
- powershell.exe (PID: 5980)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3544)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 132)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 768)
- powershell.exe (PID: 5916)
- powershell.exe (PID: 7728)
Reads the software policy settings
- aspnet_regbrowsers.exe (PID: 4624)
Reads the machine GUID from the registry
- aspnet_regbrowsers.exe (PID: 4624)
- mhnscj.exe (PID: 7964)
- aspnet_regbrowsers.exe (PID: 7448)
- aspnet_regbrowsers.exe (PID: 8088)
- aspnet_regbrowsers.exe (PID: 3920)
- aspnet_compiler.exe (PID: 6692)
- aspnet_regbrowsers.exe (PID: 5404)
- aspnet_regbrowsers.exe (PID: 5856)
- aspnet_compiler.exe (PID: 2736)
- aspnet_regbrowsers.exe (PID: 7852)
- aspnet_compiler.exe (PID: 1328)
Manual execution by a user
- wscript.exe (PID: 7848)
Create files in a temporary directory
- aspnet_regbrowsers.exe (PID: 4624)
Process checks computer location settings
- aspnet_regbrowsers.exe (PID: 4624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(4624) aspnet_regbrowsers.exe
C2 (6)127.0.0.1
cepas2023.duckdns.org
chromedata.accesscam.org
chromedata.webredirect.org
cdt2025.ddns.net
pirulito25.duckdns.org
Ports (18)6606
7707
8808
5551
9999
6666
7777
5555
9001
2023
2021
2020
2019
2018
5000
884
9909
2000
Version| Edit by Vinom Rat
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturepOYNPFuXE0Gj+xiuYmTXu57HosIyK48gXTaZIQAh705Ab/8jAnoDlb1o3f+9d+MBIeNS1dE7vXUSA0NPXUC7Fd6hD2u37pUGz7LL2aWzsvzx/VKKjJaA/o9TO0oY1j+X+HwuREojPsbf7nOkuUHpU6SmiwJ7eCxNXjwRjpdJLIU7eP5VQk/QkepC9DHhC1LSenVoq+OGlNVufqJpGL+7PbOCUbzBJgclqY1nzv/+HjkHBzObFM4U4e+wZgGtsgCkVyxX/uJRlRsZB8JgHYsFFDByKUEYYeXXLf1vRvioG/XN...
Keys
AESe256ea05f48e4b07ee0422455f6fab01e6f509adf3028a404be873373e637ee6
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
290
Monitored processes
158
Malicious processes
43
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | powershell.e"xe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\Public\1tron.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | powershell.e"xe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\Public\Qtron.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\Public\1tron.vbs" | C:\Windows\System32\wscript.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | powershell.e"xe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\Public\1tron.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3764 --field-trial-handle=2372,i,11752748881285922866,127014642916516613,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1544 | powershell.e"xe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\Public\1tron.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
96 628
Read events
96 508
Write events
107
Delete events
13
Modification events
| (PID) Process: | (6384) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6384) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6384) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6384) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (6384) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (6384) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (6628) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6628) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6628) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6628) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
17
Suspicious files
640
Text files
168
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF134f3c.TMP | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF134f7b.TMP | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF134f4c.TMP | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF134f8a.TMP | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF134f9a.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
103
DNS requests
118
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1740134656&P2=404&P3=2&P4=YuuYW%2bB0lDbcvwqTx%2fuj%2fcwKM%2b4mBLPVj2izbTNF%2fbFIRfRrGLi2Kn3DW1pbmTykL6Ypss3%2bTM4%2bXjqtNKN7Yg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | HEAD | 200 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e30939f9-8764-4977-9b5d-f865df373b71?P1=1740138252&P2=404&P3=2&P4=EszSiip0dkjqE9kKMHgHuFbeyxTOVNTTMemmk12beDI5r7jSrTlOukiAsWFDFUA9W4BFBUm%2bFY6bo0rjBYQ6rg%3d%3d | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
440 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6872 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6628 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6872 | msedge.exe | 186.202.135.207:443 | emailmarketing.locaweb.com.br | Locaweb Servicos de Internet SA | BR | whitelisted |
6872 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6872 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6872 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
emailmarketing.locaweb.com.br |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
emktlw.com.br |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6872 | msedge.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
7880 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.webredirect .org Domain |
4624 | aspnet_regbrowsers.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
4624 | aspnet_regbrowsers.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
4624 | aspnet_regbrowsers.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
4624 | aspnet_regbrowsers.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
7996 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
4264 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |