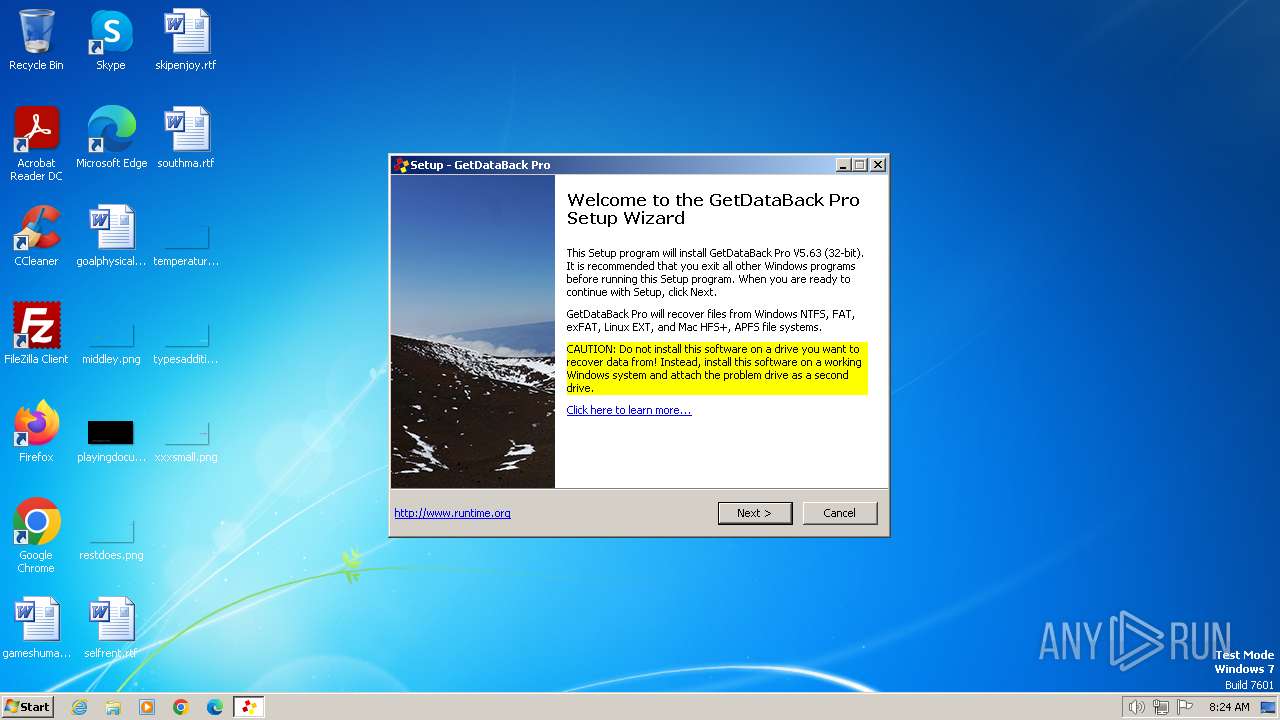
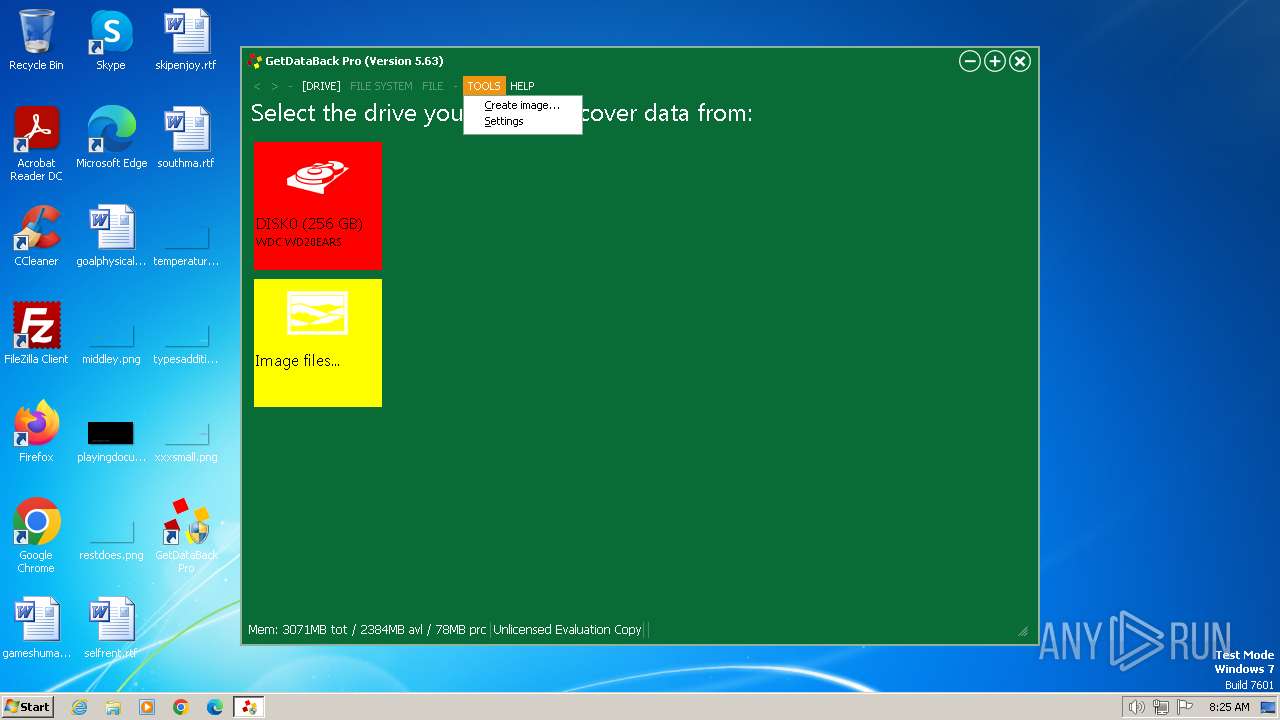
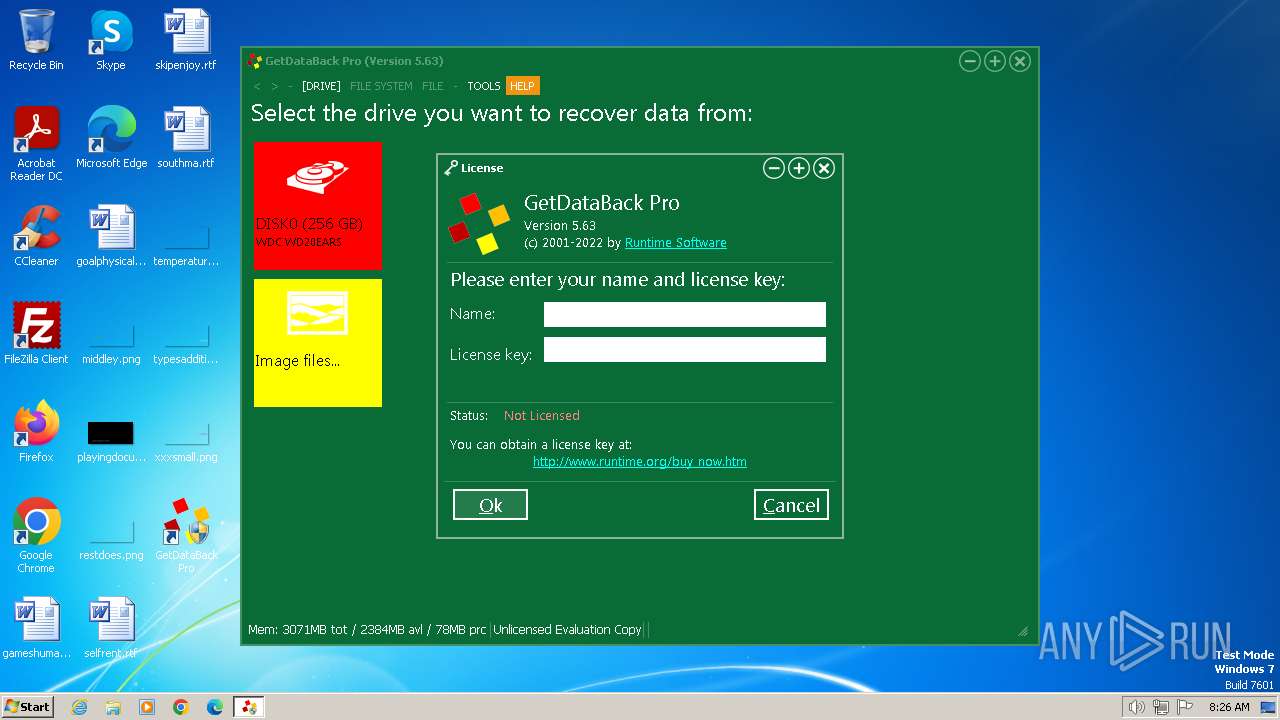
| File name: | gdbprosetup.exe |
| Full analysis: | https://app.any.run/tasks/84f27c53-da09-4aeb-ac70-0656976e5e0b |
| Verdict: | Malicious activity |
| Threats: | Metamorfo is a trojan malware family that has been active since 2018. It remains a top threat, focusing on stealing victims’ financial information, including banking credentials and other data. The malware is known for targeting users in Brazil. |
| Analysis date: | February 29, 2024, 08:24:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DFA1E8EE73787675766B3086EFA1A5F8 |
| SHA1: | E617333CA35292146A31EFEC0C12DE89713BF8A3 |
| SHA256: | 3EBF9ED9EFF9A71EA60B39F0C9AA0693310E65597FC669E44CC9A7E99B37AC84 |
| SSDEEP: | 98304:rJ0riInWOFoi4mN/FnBEYG4wahrLItg+a77y8JryrfTeaT6oNCzhf4uzMzXIipyW:dLBfoyA8uaN0RndVTldfZ9UZR0Rq7v |
MALICIOUS
Drops the executable file immediately after the start
- gdbprosetup.exe (PID: 4052)
- gdbprosetup.exe (PID: 3848)
- gdbprosetup.tmp (PID: 3948)
METAMORFO has been detected (YARA)
- gdbpro.exe (PID: 956)
SUSPICIOUS
Executable content was dropped or overwritten
- gdbprosetup.exe (PID: 3848)
- gdbprosetup.tmp (PID: 3948)
- gdbprosetup.exe (PID: 4052)
Reads the Windows owner or organization settings
- gdbprosetup.tmp (PID: 3948)
INFO
Checks supported languages
- gdbprosetup.exe (PID: 4052)
- gdbprosetup.tmp (PID: 3656)
- gdbprosetup.exe (PID: 3848)
- gdbprosetup.tmp (PID: 3948)
- gdbpro.exe (PID: 956)
Reads the computer name
- gdbprosetup.tmp (PID: 3656)
- gdbprosetup.tmp (PID: 3948)
- gdbpro.exe (PID: 956)
Creates files in the program directory
- gdbprosetup.tmp (PID: 3948)
Create files in a temporary directory
- gdbprosetup.exe (PID: 4052)
- gdbprosetup.exe (PID: 3848)
Creates a software uninstall entry
- gdbprosetup.tmp (PID: 3948)
Manual execution by a user
- gdbpro.exe (PID: 956)
- gdbpro.exe (PID: 2648)
Reads the machine GUID from the registry
- gdbpro.exe (PID: 956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.63.0.0 |
| ProductVersionNumber: | 5.63.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Runtime Software, LLC |
| FileDescription: | Recover Data from NTFS, FAT, exFAT, EXT, HFS+, and APFS |
| FileVersion: | 5.63 |
| LegalCopyright: | Runtime Software, LLC |
| ProductName: | GetDataBack Pro Data Recovery |
| ProductVersion: | 5.63 |
Total processes
48
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Program Files\Runtime Software\GetDataBack Pro\gdbpro.exe" | C:\Program Files\Runtime Software\GetDataBack Pro\gdbpro.exe | explorer.exe | ||||||||||||
User: admin Company: Runtime Software, LLC Integrity Level: HIGH Description: GetDataBack Pro Exit code: 0 Version: 5.6.3.0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Runtime Software\GetDataBack Pro\gdbpro.exe" | C:\Program Files\Runtime Software\GetDataBack Pro\gdbpro.exe | — | explorer.exe | |||||||||||
User: admin Company: Runtime Software, LLC Integrity Level: MEDIUM Description: GetDataBack Pro Exit code: 3221226540 Version: 5.6.3.0 Modules
| |||||||||||||||
| 3656 | "C:\Users\admin\AppData\Local\Temp\is-JRRC5.tmp\gdbprosetup.tmp" /SL5="$E0170,15710126,207360,C:\Users\admin\AppData\Local\Temp\gdbprosetup.exe" | C:\Users\admin\AppData\Local\Temp\is-JRRC5.tmp\gdbprosetup.tmp | — | gdbprosetup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\AppData\Local\Temp\gdbprosetup.exe" /SPAWNWND=$1A01BC /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\gdbprosetup.exe | gdbprosetup.tmp | ||||||||||||
User: admin Company: Runtime Software, LLC Integrity Level: HIGH Description: Recover Data from NTFS, FAT, exFAT, EXT, HFS+, and APFS Exit code: 0 Version: 5.63 Modules
| |||||||||||||||
| 3948 | "C:\Users\admin\AppData\Local\Temp\is-92G9I.tmp\gdbprosetup.tmp" /SL5="$19013E,15710126,207360,C:\Users\admin\AppData\Local\Temp\gdbprosetup.exe" /SPAWNWND=$1A01BC /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\is-92G9I.tmp\gdbprosetup.tmp | gdbprosetup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 4052 | "C:\Users\admin\AppData\Local\Temp\gdbprosetup.exe" | C:\Users\admin\AppData\Local\Temp\gdbprosetup.exe | explorer.exe | ||||||||||||
User: admin Company: Runtime Software, LLC Integrity Level: MEDIUM Description: Recover Data from NTFS, FAT, exFAT, EXT, HFS+, and APFS Exit code: 0 Version: 5.63 Modules
| |||||||||||||||
Total events
3 940
Read events
3 893
Write events
41
Delete events
6
Modification events
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 6C0F0000981120C0E86ADA01 | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 1124D9D5BBBCE6C7D1E6602E63A94DD6774AAEF57C92833069C96D4851BE7260 | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Runtime Software\GetDataBack Pro\gdbpro.exe | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: E744164CEABEEF5A9FE6B3904B092E8F87F1F53ADD6D344E165BC5B210E55AEB | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Runtime Software\GetDataBackPro |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files\Runtime Software\GetDataBack Pro | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Runtime Software\GetDataBackPro |
| Operation: | write | Name: | InstalledBy |
Value: gdbpro | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Runtime Software\GetDataBackPro |
| Operation: | write | Name: | Language |
Value: | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Runtime Software\GetDataBackPro |
| Operation: | write | Name: | Version |
Value: 5.63 | |||
| (PID) Process: | (3948) gdbprosetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Runtime Software\GetDataBackPro\License |
| Operation: | write | Name: | Date |
Value: | |||
Executable files
12
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | gdbprosetup.exe | C:\Users\admin\AppData\Local\Temp\is-JRRC5.tmp\gdbprosetup.tmp | executable | |
MD5:1C14D349E32731381193267BDB30BA16 | SHA256:7A5A1362D7F2A751F392A2A1E5586FC5353D5327C2AB688B3622E84CD2545EBA | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\is-9VAH9.tmp | binary | |
MD5:459574BB542632A9190092F98B1CAD68 | SHA256:D8F5D431D097854567F15C179B528C47BA6C591F2CBEFDF9BEAEC154109A7A4E | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\unins000.exe | executable | |
MD5:677415DB06E76A48A3A539B622C9519B | SHA256:EF7577DD518A9615AC58D43256021ED3BCCEB2CBD86E4FEA5AB7E4E90577DDBD | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\gdbpro.chm | binary | |
MD5:C1B56513AA28CC169B47496C629510C4 | SHA256:0FEDC690FBE6FD0EB3047107ED14FFBAE7628C7DFF8149D332A4335BC6F04E57 | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\wpdecodejp.dll | executable | |
MD5:BF819CCB9774338696CCA1382FC6C533 | SHA256:477D88153935E5C1CAF08D6E1F6C685EEC51398103C6084B21BCF9BCCBD67536 | |||
| 3948 | gdbprosetup.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Runtime Software\GetDataBack Pro.lnk | binary | |
MD5:7CE62DB939F20CD27F06693AD2FF6477 | SHA256:4F1A02FC4374F39F0980D0CF433169EE75E9054CE132674C45F983005E5E2FAA | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\is-JVN1C.tmp | executable | |
MD5:5E83072D724716AB264E8CB562BCF0CF | SHA256:93653749CBCEC9420791B37869C168AC37D1C716795D4BF8EFC64A3D89D401E6 | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\is-GHD5P.tmp | executable | |
MD5:BF819CCB9774338696CCA1382FC6C533 | SHA256:477D88153935E5C1CAF08D6E1F6C685EEC51398103C6084B21BCF9BCCBD67536 | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\is-CUH5H.tmp | binary | |
MD5:C1B56513AA28CC169B47496C629510C4 | SHA256:0FEDC690FBE6FD0EB3047107ED14FFBAE7628C7DFF8149D332A4335BC6F04E57 | |||
| 3948 | gdbprosetup.tmp | C:\Program Files\Runtime Software\GetDataBack Pro\is-DRO1A.tmp | executable | |
MD5:119A4963DD4BEAE7DBF4CF973F3D5ACA | SHA256:ECD68FCB3131FDCC944F13C715BDF8DCDDBFFDF21C32C615A97B4EE8145D9BD3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |