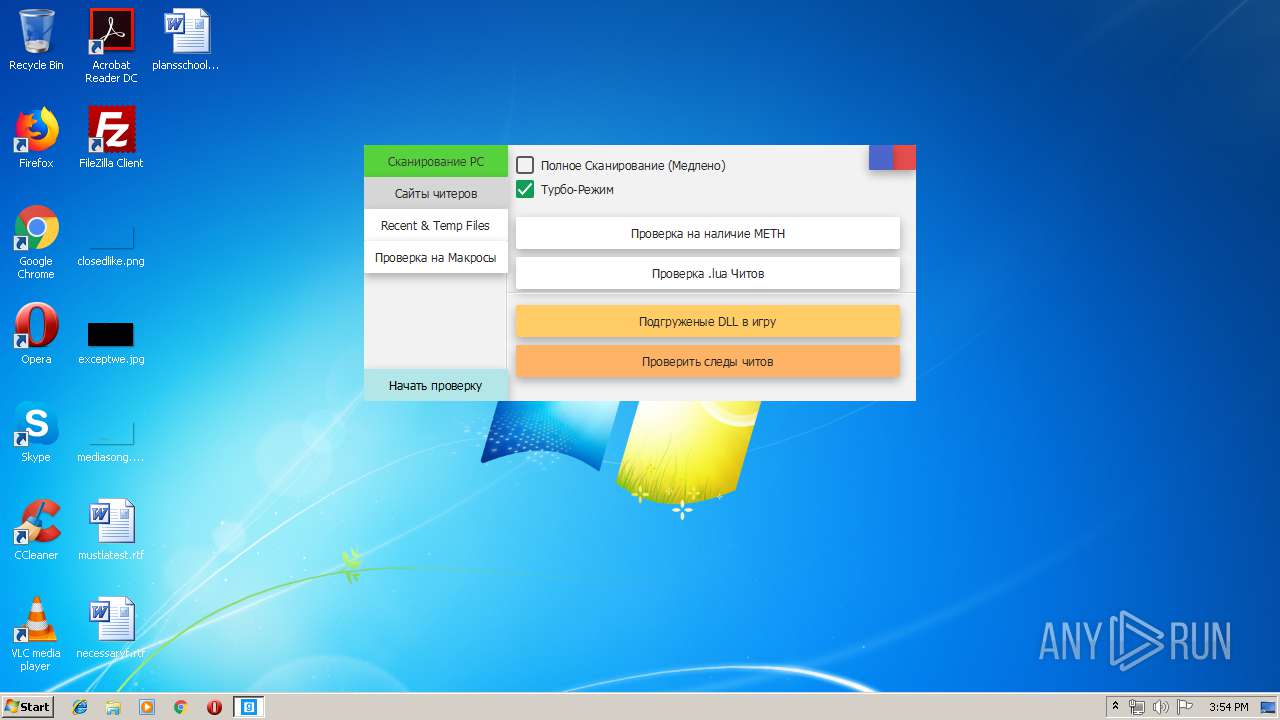
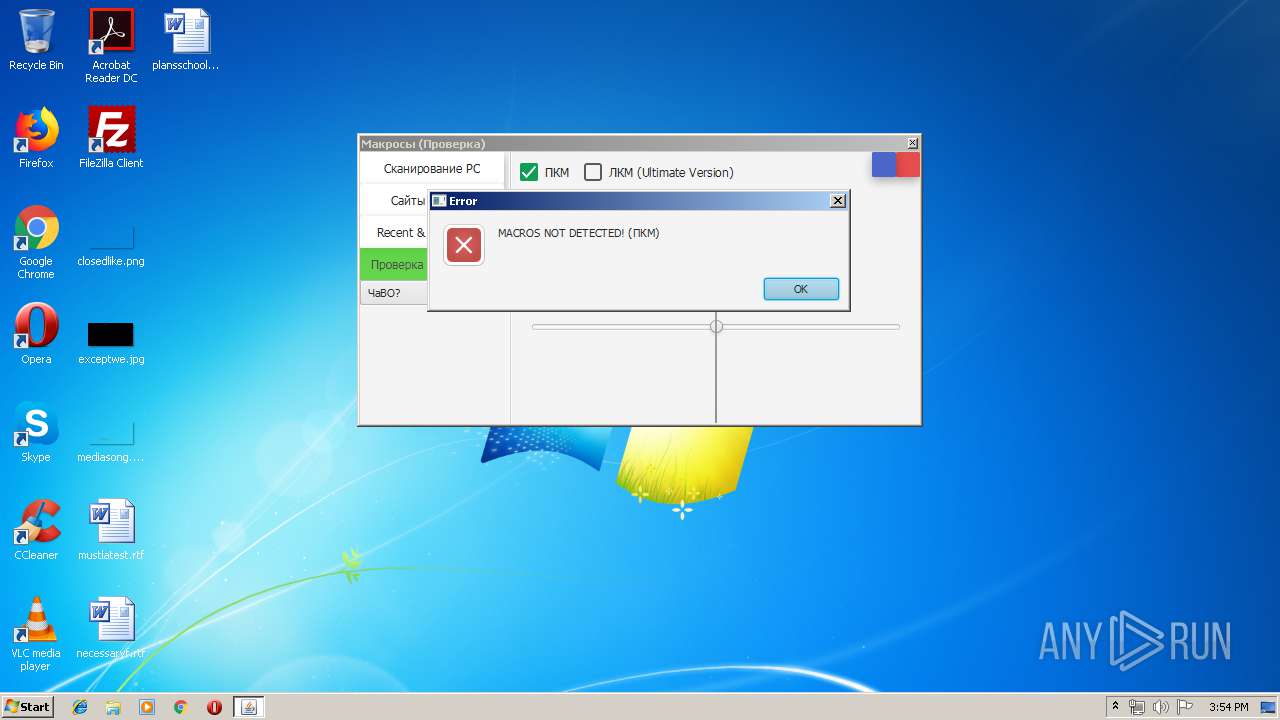
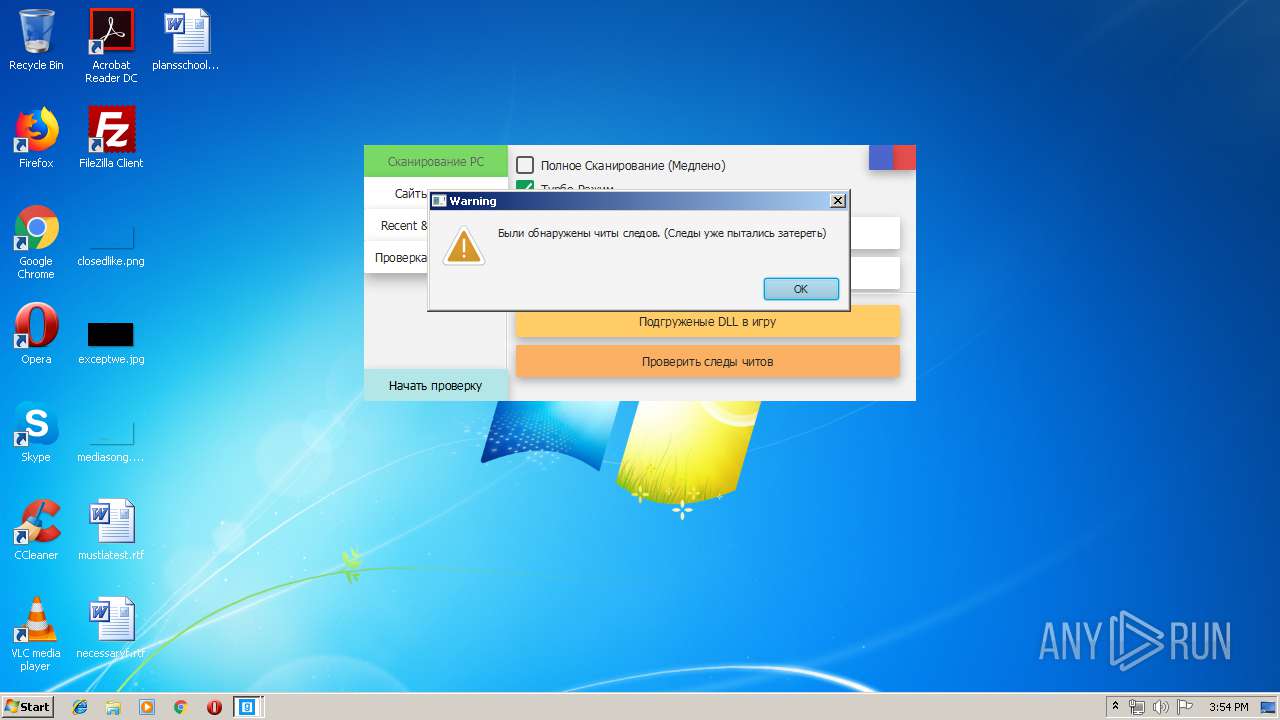
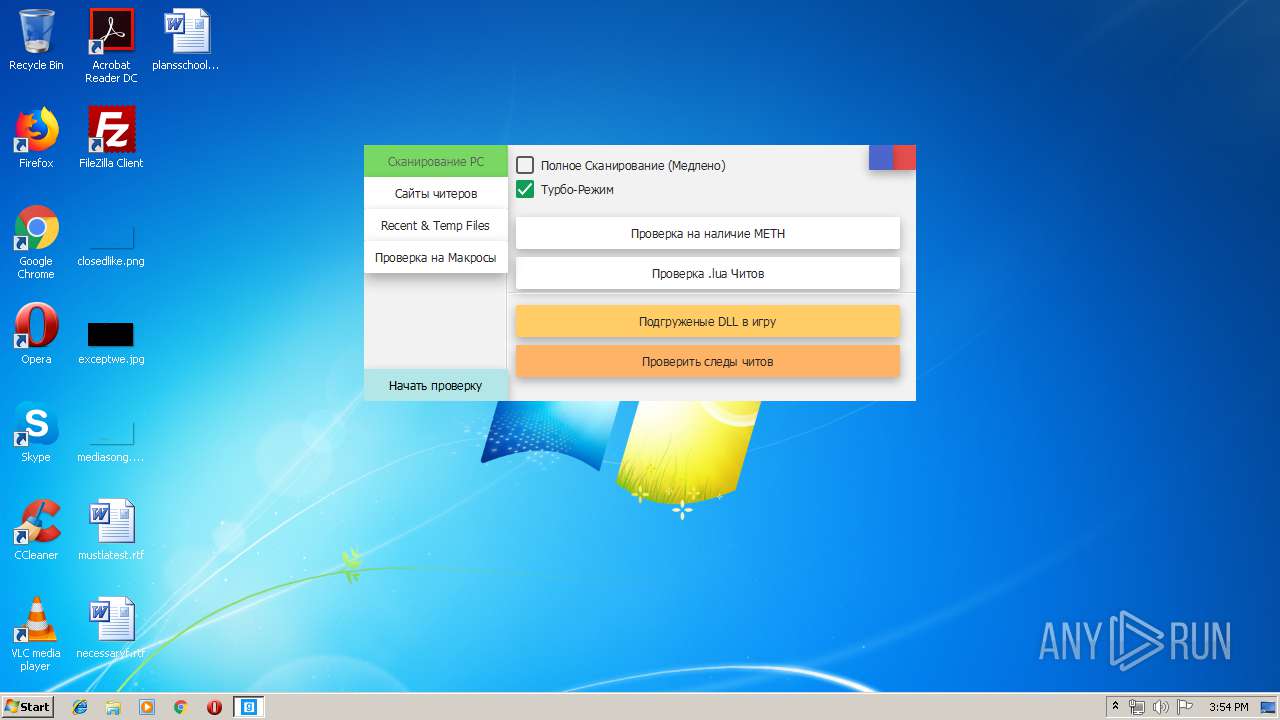
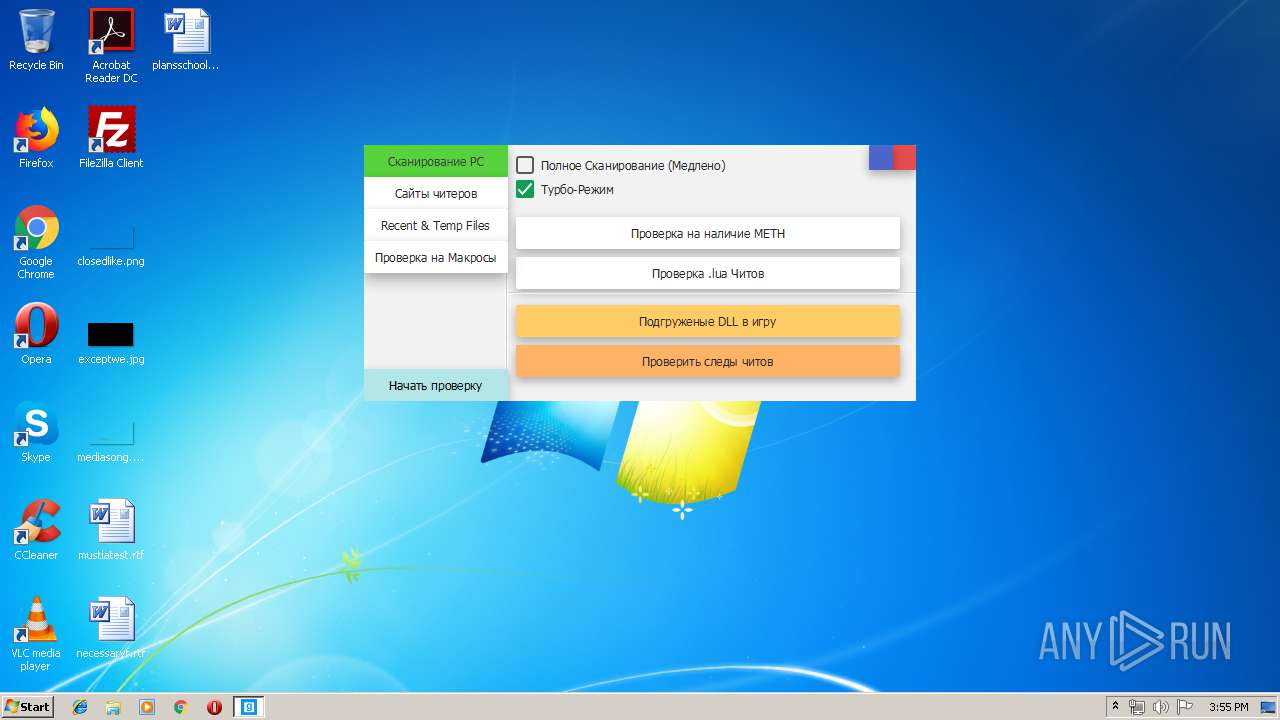
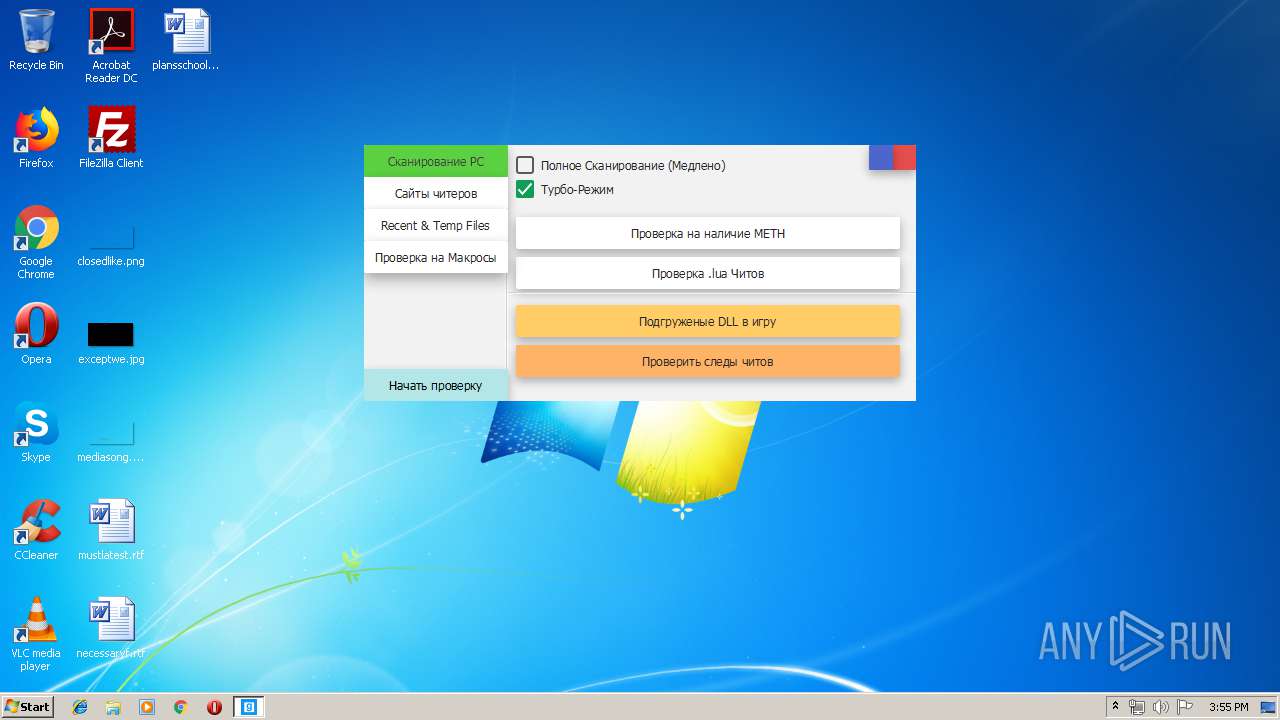
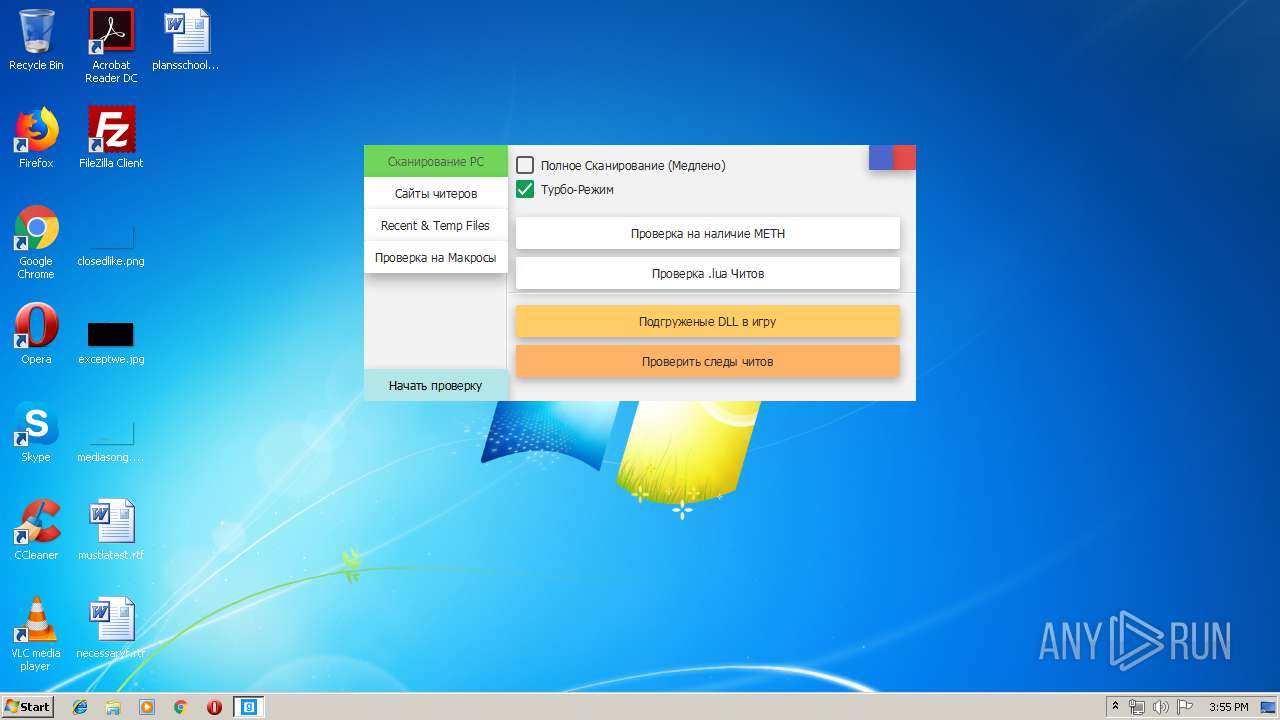
| download: | Cundo_Checker_v2.2.exe |
| Full analysis: | https://app.any.run/tasks/cea9e45f-1730-48bc-ba1c-b62e26b708ae |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 13, 2019, 14:53:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C3C4A5089C481F983512E48F22B2E005 |
| SHA1: | 53150D38B824998378E9D864606110C828161D19 |
| SHA256: | 3EBD52C4E1E3377791831F480A02F380A78A57546D32738E61203AC53530F721 |
| SSDEEP: | 98304:DGG8rVQ5+Y6hl7frcRItLuUeTBrHJWGs2NyqeoNE/7SRYYFilert2KIsWVymGu/b:TTVHJack+eArjIsWlGlSRRbCI |
MALICIOUS
Uses Task Scheduler to run other applications
- Test_Pyhton.exe (PID: 2216)
- auto_updater.exe (PID: 4092)
Application was dropped or rewritten from another process
- Test_Pyhton.exe (PID: 2216)
- WmiPrvSvc.exe (PID: 2720)
- Wmi64Update.exe (PID: 3064)
- auto_updater.exe (PID: 4092)
- CLEAN AntiCheat.exe (PID: 2916)
- taskshell.exe (PID: 3452)
Changes the autorun value in the registry
- Test_Pyhton.exe (PID: 2216)
- auto_updater.exe (PID: 4092)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2116)
- schtasks.exe (PID: 2484)
Connects to CnC server
- taskshell.exe (PID: 3452)
MINER was detected
- taskshell.exe (PID: 3452)
SUSPICIOUS
Executable content was dropped or overwritten
- Cundo_Checker_v2.2.exe (PID: 3340)
- Test_Pyhton.exe (PID: 2216)
- auto_updater.exe (PID: 4092)
Creates files in the program directory
- Test_Pyhton.exe (PID: 2216)
- auto_updater.exe (PID: 4092)
Executes JAVA applets
- CLEAN AntiCheat.exe (PID: 2916)
Connects to unusual port
- taskshell.exe (PID: 3452)
Executed via COM
- explorer.exe (PID: 2312)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2868)
Creates files in the user directory
- javaw.exe (PID: 2572)
Starts Internet Explorer
- javaw.exe (PID: 2572)
INFO
Dropped object may contain Bitcoin addresses
- Cundo_Checker_v2.2.exe (PID: 3340)
- Test_Pyhton.exe (PID: 2216)
Changes internet zones settings
- iexplore.exe (PID: 4088)
Reads Internet Cache Settings
- iexplore.exe (PID: 1496)
Reads internet explorer settings
- iexplore.exe (PID: 1496)
Creates files in the user directory
- iexplore.exe (PID: 1496)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2868)
Application launched itself
- iexplore.exe (PID: 4088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (53.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (17.5) |
| .scr | | | Windows screen saver (16.1) |
| .exe | | | Win32 Executable (generic) (5.5) |
| .exe | | | Win16/32 Executable Delphi generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 5120 |
| InitializedDataSize: | 7793664 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20cc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x000013B8 | 0x00001400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.34099 |
DATA | 0x00003000 | 0x0000007C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.11763 |
BSS | 0x00004000 | 0x00000695 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00005000 | 0x00000302 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.47732 |
.tls | 0x00006000 | 0x00000004 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00007000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.199108 |
.reloc | 0x00008000 | 0x000001C8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 5.7833 |
.rsrc | 0x00009000 | 0x0076E018 | 0x0076E200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 7.94154 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
50 | 7.92554 | 9248 | Latin 1 / Western European | UNKNOWN | RT_ICON |
51 | 2.45606 | 67624 | Latin 1 / Western European | UNKNOWN | RT_ICON |
52 | 2.64323 | 16936 | Latin 1 / Western European | UNKNOWN | RT_ICON |
53 | 2.819 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
54 | 3.02099 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
55 | 3.42526 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
A1 | 5.85121 | 44544 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
A2 | 5.59088 | 40448 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
A3 | 7.95584 | 7595259 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
B1 | 3.32782 | 16 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
kernel32.dll |
shell32.dll |
shfolder.dll |
Total processes
52
Monitored processes
15
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1496 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4088 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2116 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 1 /tn "WMI Services" /tr "C:\ProgramData\WMI Services\\WmiPrvSvc.exe" /f | C:\Windows\System32\schtasks.exe | — | Test_Pyhton.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2216 | "C:\Users\admin\AppData\Local\Temp\Test_Pyhton.exe" | C:\Users\admin\AppData\Local\Temp\Test_Pyhton.exe | Cundo_Checker_v2.2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Build_clipper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2312 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2484 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 1 /tn "WMI Host Updater" /tr "C:\ProgramData\WMI Provider Host\\Wmi64Update.exe" /f | C:\Windows\System32\schtasks.exe | — | auto_updater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2572 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -Dfile.encoding=UTF-8 -classpath "C:\Users\admin\AppData\Local\Temp\CLEAN AntiCheat.exe" org.develnext.jphp.ext.javafx.FXLauncher | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | CLEAN AntiCheat.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2720 | "C:\ProgramData\WMI Services\WmiPrvSvc.exe" | C:\ProgramData\WMI Services\WmiPrvSvc.exe | — | Test_Pyhton.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Clipper 1.1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2848 | explorer execq.gq/cheat | C:\Windows\explorer.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2868 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2916 | "C:\Users\admin\AppData\Local\Temp\CLEAN AntiCheat.exe" | C:\Users\admin\AppData\Local\Temp\CLEAN AntiCheat.exe | — | Cundo_Checker_v2.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 773
Read events
1 606
Write events
166
Delete events
1
Modification events
| (PID) Process: | (3340) Cundo_Checker_v2.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3340) Cundo_Checker_v2.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2216) Test_Pyhton.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2216) Test_Pyhton.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2216) Test_Pyhton.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WMI Update Service |
Value: C:\ProgramData\WMI Services\WmiPrvSvc.exe | |||
| (PID) Process: | (4092) auto_updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\auto_updater_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4092) auto_updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\auto_updater_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4092) auto_updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\auto_updater_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (4092) auto_updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\auto_updater_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (4092) auto_updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\auto_updater_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
8
Suspicious files
3
Text files
57
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4092 | auto_updater.exe | C:\ProgramData\config.json | text | |
MD5:— | SHA256:— | |||
| 3340 | Cundo_Checker_v2.2.exe | C:\Users\admin\AppData\Local\Temp\CLEAN AntiCheat.exe | executable | |
MD5:— | SHA256:— | |||
| 4092 | auto_updater.exe | C:\ProgramData\taskshell.exe | executable | |
MD5:— | SHA256:— | |||
| 4092 | auto_updater.exe | C:\ProgramData\WMI Provider Host\Wmi64Update.exe | executable | |
MD5:— | SHA256:— | |||
| 1496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2216 | Test_Pyhton.exe | C:\ProgramData\WMI Services\WmiPrvSvc.exe | executable | |
MD5:— | SHA256:— | |||
| 4092 | auto_updater.exe | C:\ProgramData\WMI Provider Host\nvrtc64_100_0.dll | executable | |
MD5:— | SHA256:— | |||
| 1496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\I95747OE\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
34
DNS requests
17
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4092 | auto_updater.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
4088 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1496 | iexplore.exe | 104.27.132.174:443 | citizenhack.me | Cloudflare Inc | US | shared |
1496 | iexplore.exe | 205.185.208.52:443 | code.jquery.com | Highwinds Network Group, Inc. | US | unknown |
1496 | iexplore.exe | 172.217.16.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1496 | iexplore.exe | 172.217.18.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1496 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
1496 | iexplore.exe | 151.101.36.193:443 | i.imgur.com | Fastly | US | unknown |
1496 | iexplore.exe | 64.233.184.157:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
1496 | iexplore.exe | 172.217.21.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cwnyfyxugire.000webhostapp.com |
| shared |
iplogger.org |
| shared |
xmr.pool.minergate.com |
| suspicious |
www.bing.com |
| whitelisted |
phizzofficial.wixsite.com |
| malicious |
www.securehosts.us |
| unknown |
citizenhack.me |
| suspicious |
fonts.googleapis.com |
| whitelisted |
code.jquery.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1064 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
4092 | auto_updater.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
4092 | auto_updater.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
4092 | auto_updater.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
1064 | svchost.exe | A Network Trojan was detected | ET POLICY Monero Mining Pool DNS Lookup |
3452 | taskshell.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
3452 | taskshell.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
3452 | taskshell.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3452 | taskshell.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |
3452 | taskshell.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight algo JSON_RPC server Response |
2 ETPRO signatures available at the full report