| File name: | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe |
| Full analysis: | https://app.any.run/tasks/e0ad27b5-a747-4363-866b-4e4979ca7dd0 |
| Verdict: | Malicious activity |
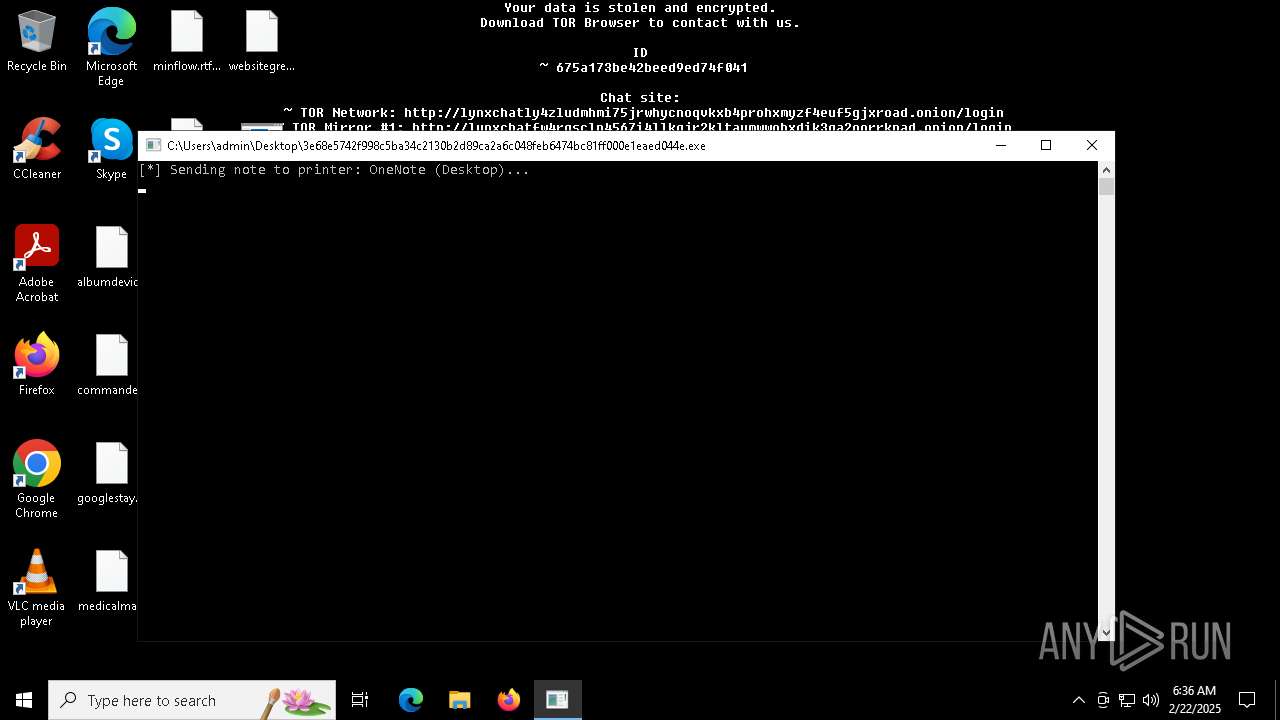
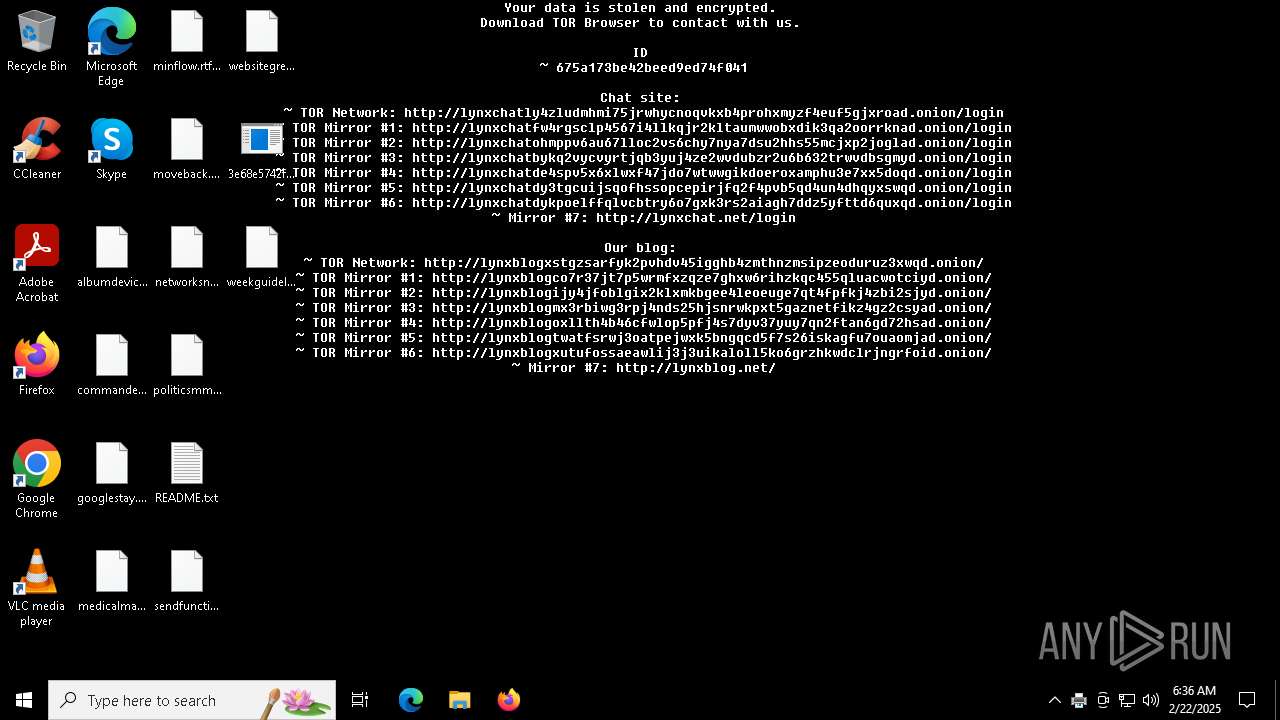
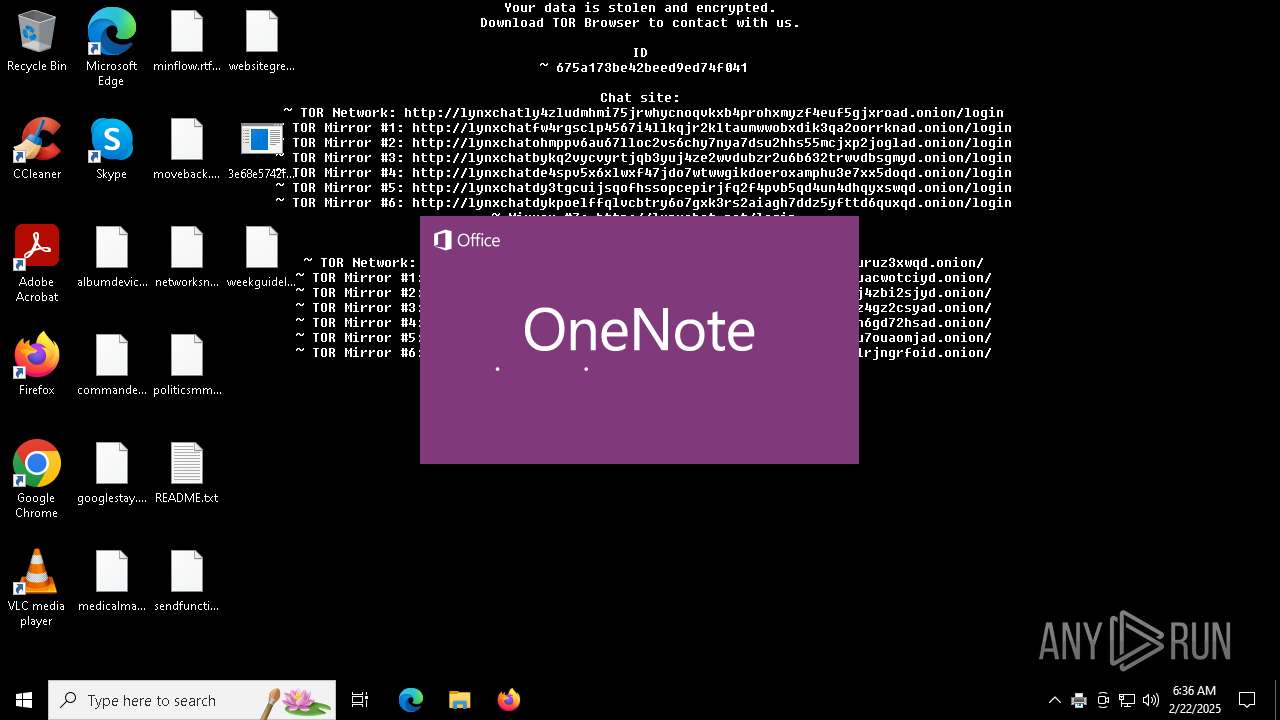
| Threats: | Lynx is a double extortion ransomware: attackers encrypt important and sensitive data and demand a ransom for decryption simultaneously threatening to publish or sell the data. Active since mid-2024. Among techniques are terminating processes and services, privilege escalation, deleting shadow copies. Distribution by phishing, malvertising, exploiting vulnerabilities. |
| Analysis date: | February 22, 2025, 06:35:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | F16238836909D07F86154C5CCBADE96A |
| SHA1: | 558F259459D0ED1B30CBEAEE71AA46EB5E40B090 |
| SHA256: | 3E68E5742F998C5BA34C2130B2D89CA2A6C048FEB6474BC81FF000E1EAED044E |
| SSDEEP: | 3072:rBBDFFFiZhsEzKbLhbJ3zbFli4YU+kIQu42JB3p+frug1swxtMKzO4XYjPHmfP:ahN+RNVlv+8u42z3p+frdbWGfP |
MALICIOUS
LYNX has been detected (YARA)
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
LYNX has been detected
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
RANSOMWARE has been detected
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
Renames files like ransomware
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
Scans artifacts that could help determine the target
- ONENOTE.EXE (PID: 10056)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
Reads security settings of Internet Explorer
- ONENOTE.EXE (PID: 10056)
Changes the desktop background image
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
Executes as Windows Service
- FXSSVC.exe (PID: 9928)
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 10056)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 10056)
Creates file in the systems drive root
- ONENOTE.EXE (PID: 10056)
Reads the date of Windows installation
- ONENOTE.EXE (PID: 10056)
INFO
Creates files in the program directory
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
- FXSSVC.exe (PID: 9928)
Creates files or folders in the user directory
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
- ONENOTE.EXE (PID: 10056)
- printfilterpipelinesvc.exe (PID: 9808)
Checks supported languages
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
- ONENOTE.EXE (PID: 10056)
- ONENOTEM.EXE (PID: 5988)
Reads the machine GUID from the registry
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
- ONENOTE.EXE (PID: 10056)
Reads the computer name
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
- ONENOTE.EXE (PID: 10056)
- ONENOTEM.EXE (PID: 5988)
Create files in a temporary directory
- 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe (PID: 5004)
- ONENOTE.EXE (PID: 10056)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 10056)
- ONENOTEM.EXE (PID: 5988)
Checks proxy server information
- ONENOTE.EXE (PID: 10056)
Reads Environment values
- ONENOTE.EXE (PID: 10056)
Reads product name
- ONENOTE.EXE (PID: 10056)
Reads the software policy settings
- ONENOTE.EXE (PID: 10056)
Reads security settings of Internet Explorer
- printfilterpipelinesvc.exe (PID: 9808)
Disables trace logs
- FXSSVC.exe (PID: 9928)
Reads CPU info
- ONENOTE.EXE (PID: 10056)
Process checks computer location settings
- ONENOTE.EXE (PID: 10056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:11:18 20:55:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 120832 |
| InitializedDataSize: | 49664 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa341 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
125
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5004 | "C:\Users\admin\Desktop\3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe" | C:\Users\admin\Desktop\3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5988 | /tsr | C:\Program Files\Microsoft Office\root\Office16\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Send to OneNote Tool Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 9808 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 9928 | C:\WINDOWS\system32\fxssvc.exe | C:\Windows\System32\FXSSVC.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Fax Service Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 10056 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\{99DFFA54-24DE-4C4C-95F9-84570EA04FD3}.xps" 133846797783000000 | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
14 393
Read events
14 126
Write events
237
Delete events
30
Modification events
| (PID) Process: | (5004) 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\admin\AppData\Local\Temp\\background-image.jpg | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax |
| Operation: | write | Name: | RedirectionGuard |
Value: 1 | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | Password |
Value: 00 | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | delete value | Name: | Password |
Value: | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | Server |
Value: | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | From |
Value: | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | User |
Value: | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Groups\<All devices> |
| Operation: | write | Name: | Devices |
Value: | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Rules\0:0 |
| Operation: | write | Name: | CountryCode |
Value: 0 | |||
| (PID) Process: | (9928) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Rules\0:0 |
| Operation: | write | Name: | AreaCode |
Value: 0 | |||
Executable files
2
Suspicious files
723
Text files
176
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Adobe\ARM\Acrobat_23.001.20093\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Adobe\ARM\{291AA914-A987-4CE9-BD63-0C0A92D435E5}\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Comms\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Adobe\Temp\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Adobe\ARM\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft\ClickToRun\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Adobe\ARM\S\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
| 5004 | 3e68e5742f998c5ba34c2130b2d89ca2a6c048feb6474bc81ff000e1eaed044e.exe | C:\ProgramData\Adobe\ARM\S\388\README.txt | text | |
MD5:88F67C9E434382015362CE2FC3D55DE1 | SHA256:F64DA53E5ED26A192D66A342077DCEF2BD139BF1E7F828E99A85BFDE5F5BBF2E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.42.72.131:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 10 b | whitelisted |
— | — | POST | 200 | 104.208.16.91:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 10 b | whitelisted |
— | — | GET | 200 | 52.123.128.14:443 | https://ecs.office.com/config/v2/Office/onenote/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=onenote&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=onenote.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=OneNoteFreeRetail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bEC34658E-209A-4020-A06B-7790E63F0016%7d&LabMachine=false | unknown | binary | 368 Kb | whitelisted |
— | — | GET | 200 | 52.109.32.97:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 179 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.146:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.21.20.137:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
10056 | ONENOTE.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|