| File name: | 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744 |
| Full analysis: | https://app.any.run/tasks/b8d2e190-31e2-4950-bc4f-8de994144fb3 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | December 14, 2024, 11:18:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 5D438A4C24C1B5EFAA262D478C5CFCF4 |
| SHA1: | 410EA9660D0C0D09B542E0E5EDB51172F0BDC94F |
| SHA256: | 3E26F0DCB6E7C44C8894BA44074EB2832E84F0973FC2E877087D6D9053C9C744 |
| SSDEEP: | 192:N9sEF7GhLJyhojIrwTFSHDBc6+60ZT208hsyfn8bYFe3Q5tfjJdUCrRQovh:rZh2IQFSOZnyf8bY83Lb |
MALICIOUS
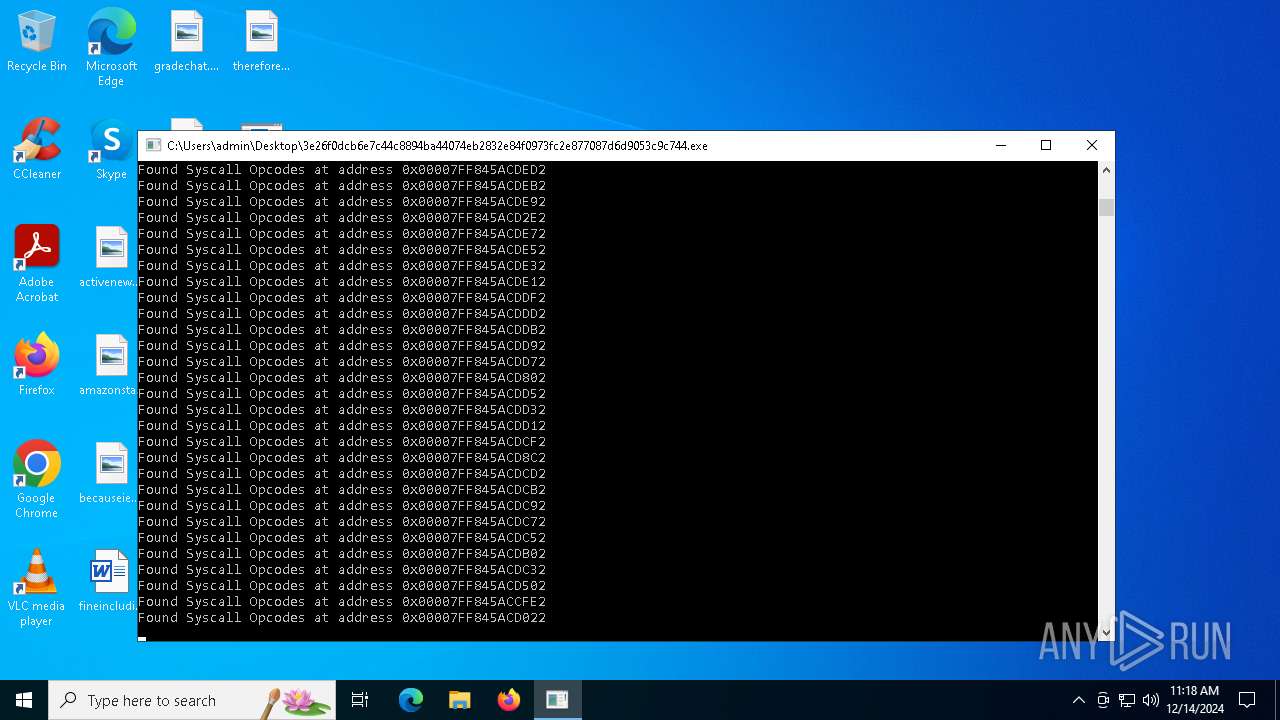
COBALTSTRIKE has been detected (YARA)
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
SUSPICIOUS
Reads security settings of Internet Explorer
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
Checks Windows Trust Settings
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
INFO
Checks supported languages
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
Checks proxy server information
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
Reads the computer name
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
Reads the software policy settings
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
Reads the machine GUID from the registry
- 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe (PID: 6076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CobalStrike
(PID) Process(6076) 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe
C249.232.49.186:443/6vjG
HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; BOIE9;ENUS)
C2 (1)49.232.49.186/www/handle/doc
BeaconTypeHTTPS
Port443
SleepTime3000
MaxGetSize2097167
Jitter0
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDlbDPCv9xTR+KC41Zh1+Ik1uni
7qHDWwMy2kF7kvu89p3TdK5KtjeaJNh6c2EiY55g9gO3ph1LV0x5VkW1I5sTaIzg
USXf092W0twiPmXTnjHrbWi0SDaSEFbr+E8SC0bW8GVGzUapZPNLvpnNX4c4Rrxg
g6TAvQTparu9Kep5vQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86c:\windows\syswow64\rundll32.exe
Spawnto_x64c:\windows\system32\rundll32.exe
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark987654321
bStageCleanupFalse
bCFGCautionFalse
UserAgentMozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; BOIE9;PTBR)
HttpPostUri/IMXo
Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 5 bytes from the beginning, NetBIOS Encode 'a', XOR mask w/ random key
HttpGet_Metadata
SessionId (3)base64url
prepend: SESSIONID=
header: Cookie
HttpPost_Metadata
SessionId (3)mask
netbiosu
parameter: doc
Output (5)mask
base64url
prepend: data=
append: %%
print
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXTrue
bProcInject_UseRWXTrue
bProcInject_MinAllocSize0
ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_Stubae5afcfee8026674dc8f3b4f2da46c7f
ProcInject_AllocationMethodVirtualAllocEx
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:14 09:38:36+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 5632 |
| InitializedDataSize: | 18432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1920 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
119
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6076 | "C:\Users\admin\Desktop\3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe" | C:\Users\admin\Desktop\3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
CobalStrike(PID) Process(6076) 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe C249.232.49.186:443/6vjG HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; BOIE9;ENUS) (PID) Process(6076) 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe C2 (1)49.232.49.186/www/handle/doc BeaconTypeHTTPS Port443 SleepTime3000 MaxGetSize2097167 Jitter0 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDlbDPCv9xTR+KC41Zh1+Ik1uni
7qHDWwMy2kF7kvu89p3TdK5KtjeaJNh6c2EiY55g9gO3ph1LV0x5VkW1I5sTaIzg
USXf092W0twiPmXTnjHrbWi0SDaSEFbr+E8SC0bW8GVGzUapZPNLvpnNX4c4Rrxg
g6TAvQTparu9Kep5vQIDAQAB
-----END PUBLIC KEY----- DNS_strategyround-robin DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86c:\windows\syswow64\rundll32.exe Spawnto_x64c:\windows\system32\rundll32.exe CryptoScheme0 HttpGet_VerbGET HttpPost_VerbPOST HttpPostChunk0 Watermark987654321 bStageCleanupFalse bCFGCautionFalse UserAgentMozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; BOIE9;PTBR) HttpPostUri/IMXo Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 5 bytes from the beginning, NetBIOS Encode 'a', XOR mask w/ random key HttpGet_Metadata SessionId (3)base64url prepend: SESSIONID= header: Cookie HttpPost_Metadata SessionId (3)mask netbiosu parameter: doc Output (5)mask base64url prepend: data= append: %% print bUsesCookies0001 Proxy_BehaviorUse IE settings tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXTrue bProcInject_UseRWXTrue bProcInject_MinAllocSize0 ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000... ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000... ProcInject_Stubae5afcfee8026674dc8f3b4f2da46c7f ProcInject_AllocationMethodVirtualAllocEx | |||||||||||||||
Total events
3 748
Read events
3 748
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
50
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
440 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
440 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 49.232.49.186:443 | https://49.232.49.186/www/handle/doc | unknown | — | — | unknown |
— | — | GET | 200 | 49.232.49.186:443 | https://49.232.49.186/www/handle/doc | unknown | text | 15 b | unknown |
— | — | GET | 200 | 49.232.49.186:443 | https://49.232.49.186/www/handle/doc | unknown | text | 15 b | unknown |
— | — | GET | 200 | 49.232.49.186:443 | https://49.232.49.186/www/handle/doc | unknown | text | 15 b | unknown |
— | — | GET | 200 | 49.232.49.186:443 | https://49.232.49.186/www/handle/doc | unknown | text | 15 b | unknown |
— | — | GET | 200 | 49.232.49.186:443 | https://49.232.49.186/www/handle/doc | unknown | text | 15 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
440 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6076 | 3e26f0dcb6e7c44c8894ba44074eb2832e84f0973fc2e877087d6d9053c9c744.exe | 49.232.49.186:443 | — | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
440 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |