| File name: | javaw.exe |
| Full analysis: | https://app.any.run/tasks/016e6390-2280-49fe-be23-8618935c6ad2 |
| Verdict: | Malicious activity |
| Threats: | BlueSky ransomware, first identified in June 2022, shares code similarities with other well-known ransomware families like Conti and Babuk. It primarily spreads via phishing emails and malicious links and can propagate through networks using SMB protocols. BlueSky uses advanced evasion techniques, such as hiding its processes from debuggers via the NtSetInformationThread API, making it difficult for analysts to detect and mitigate its attacks. |
| Analysis date: | May 13, 2024, 13:29:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D8A44D2ED34B5FEE7C8E24D998F805D9 |
| SHA1: | D8369CB0D8CCEC95B2A49BA34AA7749B60998661 |
| SHA256: | 3E035F2D7D30869CE53171EF5A0F761BFB9C14D94D9FE6DA385E20B8D96DC2FB |
| SSDEEP: | 1536:wBrE2D2ZjyKBQs8swOVWCqBTXdXu3+MkNCMm2i9w4:iBD2RfQ/7OVWS3+1rm2i9w4 |
MALICIOUS
Drops the executable file immediately after the start
- javaw.exe (PID: 3964)
Renames files like ransomware
- javaw.exe (PID: 3964)
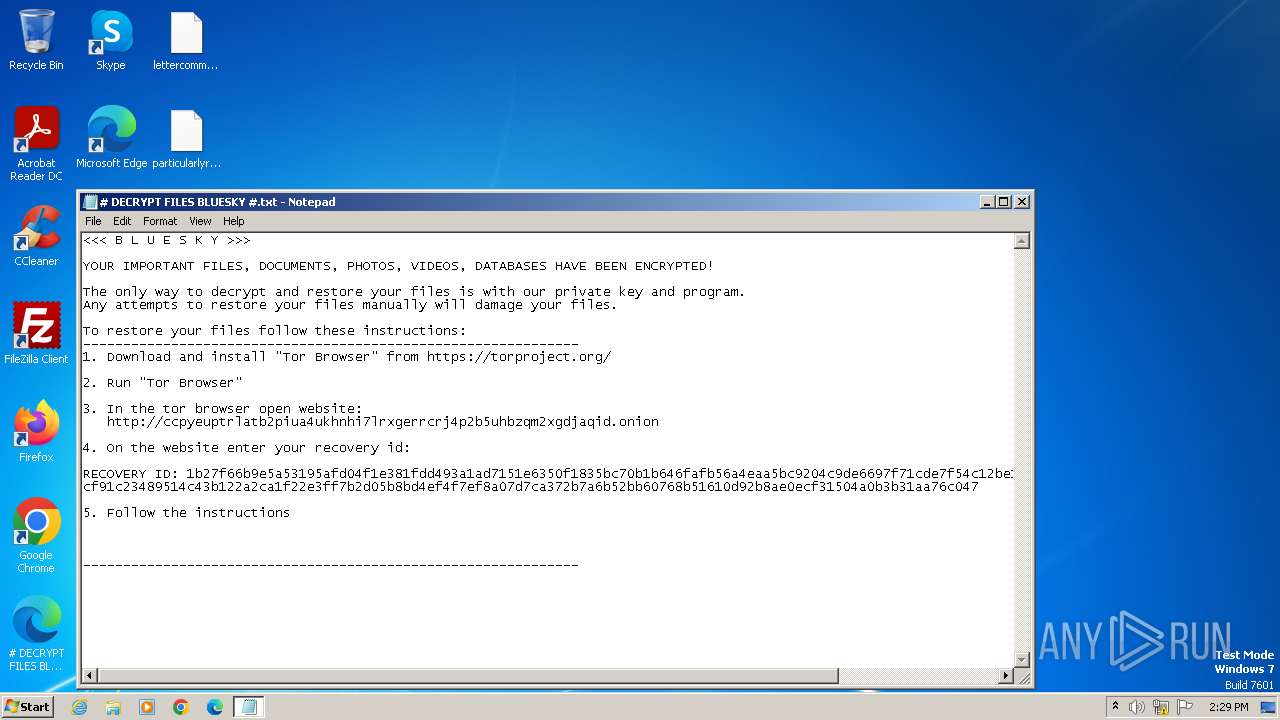
Bluesky note has been found
- javaw.exe (PID: 3964)
SUSPICIOUS
Reads the date of Windows installation
- javaw.exe (PID: 3964)
Creates files like ransomware instruction
- javaw.exe (PID: 3964)
INFO
Checks supported languages
- javaw.exe (PID: 3964)
Reads the machine GUID from the registry
- javaw.exe (PID: 3964)
Reads the computer name
- javaw.exe (PID: 3964)
Creates files or folders in the user directory
- javaw.exe (PID: 3964)
Manual execution by a user
- notepad.exe (PID: 4072)
Dropped object may contain TOR URL's
- javaw.exe (PID: 3964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2085:02:07 16:05:31+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 94.8 |
| CodeSize: | 67584 |
| InitializedDataSize: | 7168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe880 |
| OSVersion: | 5.1 |
| ImageVersion: | 48623.16013 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3964 | "C:\Users\admin\Desktop\javaw.exe" | C:\Users\admin\Desktop\javaw.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4072 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\# DECRYPT FILES BLUESKY #.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 623
Read events
2 619
Write events
4
Delete events
0
Modification events
| (PID) Process: | (3964) javaw.exe | Key: | HKEY_CURRENT_USER\Software\9763CCC75B33F1BA24ABCB533E4CE199 |
| Operation: | write | Name: | RECOVERYBLOB |
Value: 1B27F66B9E5A53195AFD04F1E381FDD493A1AD7151E6350F1835BC70B1B646FAFB56A4EAA5BC9204C9DE6697F71CDE7F54C12BE1BD2E77851776C3E1CC6E79C0CF91C23489514C43B122A2CA1F22E3FF7B2D05B8BD4EF4F7EF8A07D7CA372B7A6B52BB60768B51610D92B8AE0ECF31504A0B3B31AA76C047 | |||
| (PID) Process: | (3964) javaw.exe | Key: | HKEY_CURRENT_USER\Software\9763CCC75B33F1BA24ABCB533E4CE199 |
| Operation: | write | Name: | x25519_public |
Value: 713B5BB8DF4440400C17B3E31F82D16400AC537F52F567EE08BB00A721822526 | |||
| (PID) Process: | (3964) javaw.exe | Key: | HKEY_CURRENT_USER\Software\9763CCC75B33F1BA24ABCB533E4CE199 |
| Operation: | write | Name: | completed |
Value: 0 | |||
| (PID) Process: | (3964) javaw.exe | Key: | HKEY_CURRENT_USER\Software\9763CCC75B33F1BA24ABCB533E4CE199 |
| Operation: | write | Name: | completed |
Value: 1 | |||
Executable files
0
Suspicious files
64
Text files
105
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | javaw.exe | C:\Users\admin\Desktop\employmentlists.rtf.bluesky | — | |
MD5:— | SHA256:— | |||
| 3964 | javaw.exe | C:\users\admin\desktop\evidencearmy.rtf | — | |
MD5:— | SHA256:— | |||
| 3964 | javaw.exe | C:\Users\admin\Contacts\admin.contact.bluesky | — | |
MD5:— | SHA256:— | |||
| 3964 | javaw.exe | C:\users\admin\desktop\particularlyrelationship.jpg | — | |
MD5:— | SHA256:— | |||
| 3964 | javaw.exe | C:\Users\admin\Desktop\fromnetworks.jpg.bluesky | — | |
MD5:— | SHA256:— | |||
| 3964 | javaw.exe | C:\Users\admin\Desktop\tolog.jpg.bluesky | — | |
MD5:— | SHA256:— | |||
| 3964 | javaw.exe | C:\msocache\# DECRYPT FILES BLUESKY #.txt | text | |
MD5:BCA84740C7951AC1747B8D0EE816D935 | SHA256:28FD66E477874F45C88709718357A7868F86CCD6E46CBB3FC8C19B27CD56F66C | |||
| 3964 | javaw.exe | C:\users\admin\# DECRYPT FILES BLUESKY #.html | html | |
MD5:AE804BA85CAFBA46F5A40279217AEEE5 | SHA256:85058418F85E50E0BE6C6071E4353621470AA5657F3E12E1A93544A4CFF7C6B0 | |||
| 3964 | javaw.exe | C:\users\admin\.oracle_jre_usage\# DECRYPT FILES BLUESKY #.html | html | |
MD5:AE804BA85CAFBA46F5A40279217AEEE5 | SHA256:85058418F85E50E0BE6C6071E4353621470AA5657F3E12E1A93544A4CFF7C6B0 | |||
| 3964 | javaw.exe | C:\users\admin\# DECRYPT FILES BLUESKY #.txt | text | |
MD5:BCA84740C7951AC1747B8D0EE816D935 | SHA256:28FD66E477874F45C88709718357A7868F86CCD6E46CBB3FC8C19B27CD56F66C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
266
DNS requests
0
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 192.168.100.202:49422 | — | — | — | unknown |
— | — | 192.168.100.202:49423 | — | — | — | unknown |
3964 | javaw.exe | 192.168.1.2:445 | — | — | — | unknown |
— | — | 192.168.100.202:49425 | — | — | — | unknown |
— | — | 192.168.100.202:49426 | — | — | — | unknown |
— | — | 192.168.100.202:49427 | — | — | — | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3964 | javaw.exe | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |