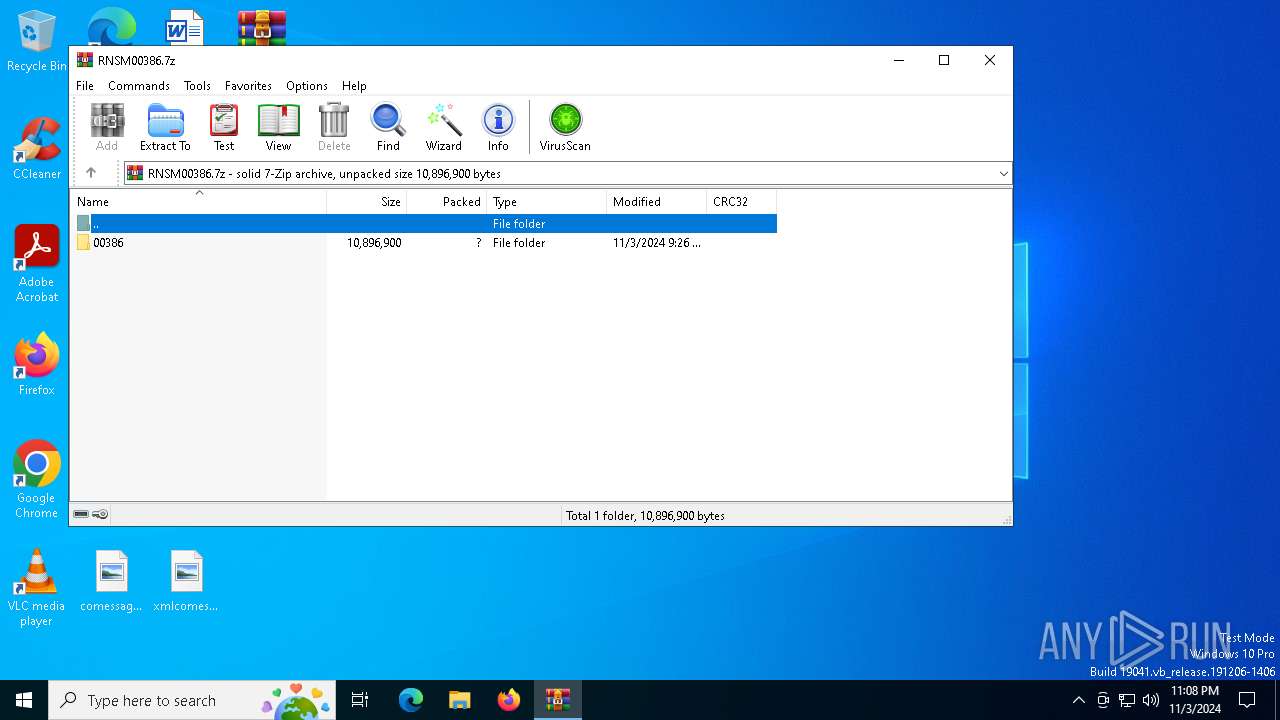
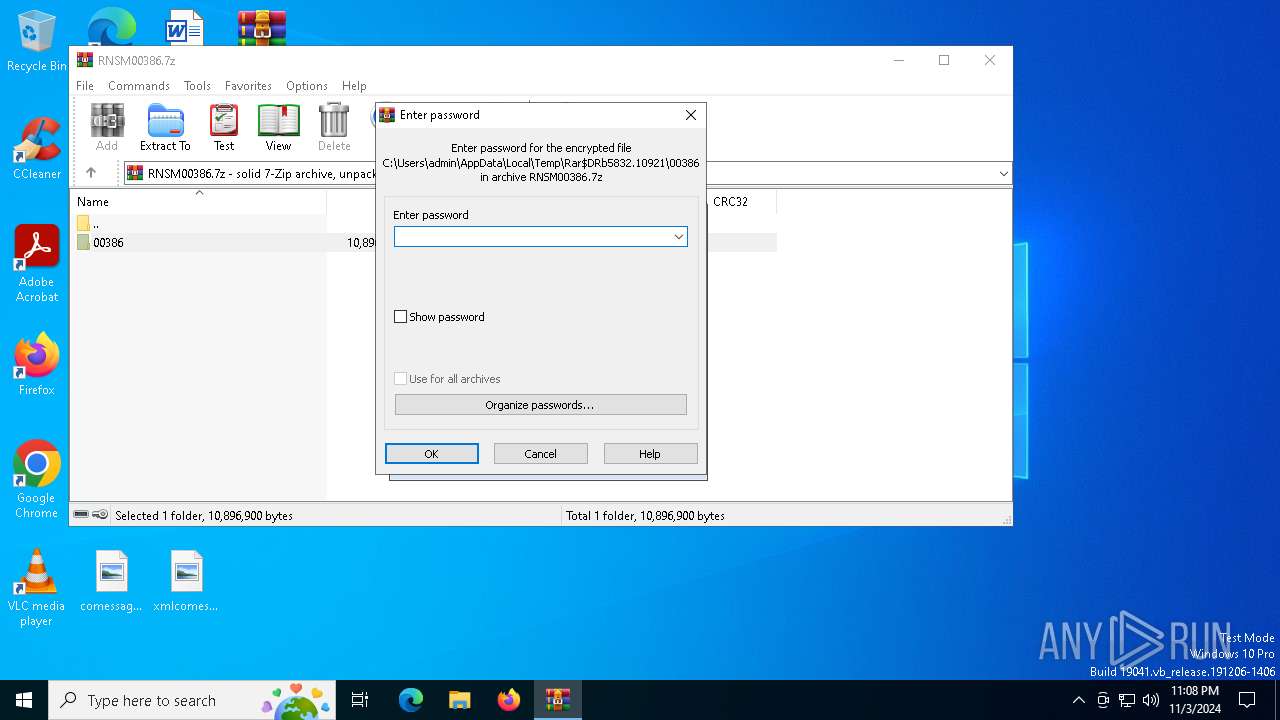
| File name: | RNSM00386.7z |
| Full analysis: | https://app.any.run/tasks/bf9b6ee9-286b-42c1-b79e-7eac1261f1b9 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | November 03, 2024, 23:08:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A31AFB786FD93BE121F890A82BEBDC9C |
| SHA1: | 8528F8F9141EDA1A4940172F0ADEF6E9C05FFBA7 |
| SHA256: | 3DE5223CA74C4B449C7D4DA7E586077E014EE421689F37E2E96505800CCD9F73 |
| SSDEEP: | 98304:CbXp/IUshRBSVtPyo/F3rB7BWKwGinYm9tDfk4Qkfl93f9cOV3wFHjRxQhagMkEY:im9AMc7rN+rcvBqa9w |
MALICIOUS
Changes the autorun value in the registry
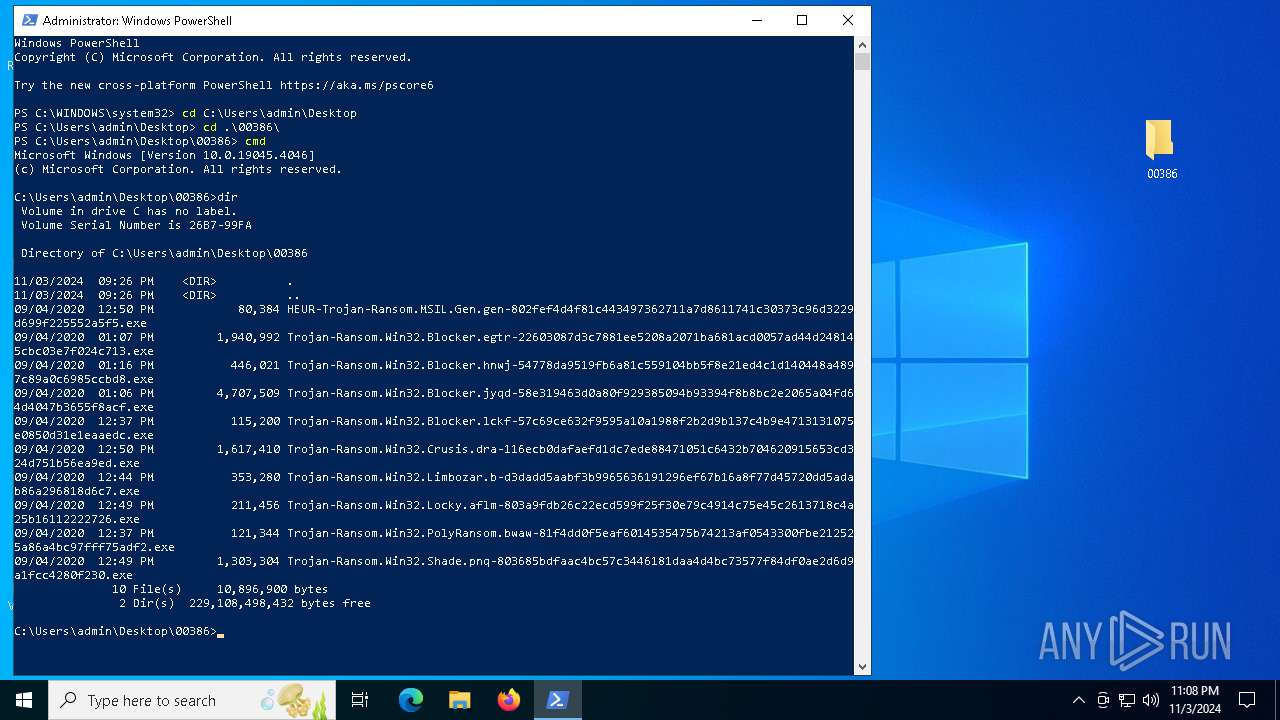
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.Blocker.hnwj-54778da9519fb6a81c559104bb5f8e21ed4c1d140448a4897c89a0c6985ccbd8.exe (PID: 4836)
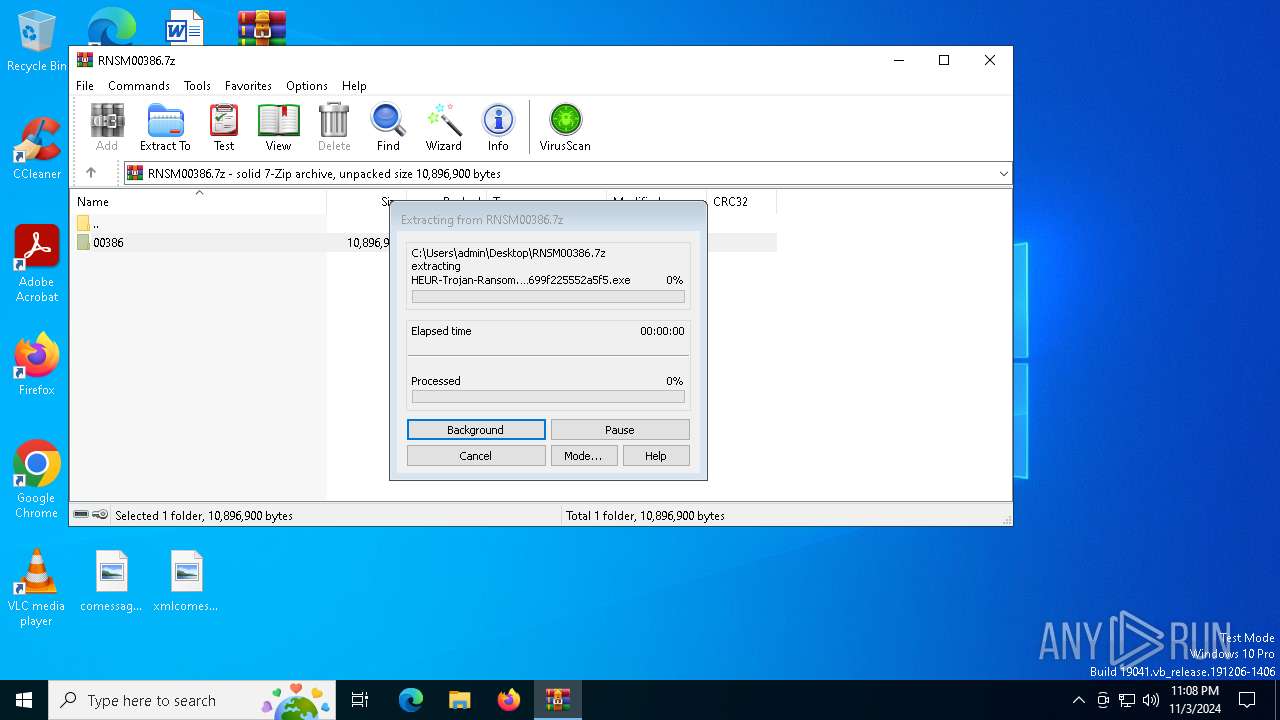
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Connects to the CnC server
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
AZORULT has been detected (SURICATA)
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
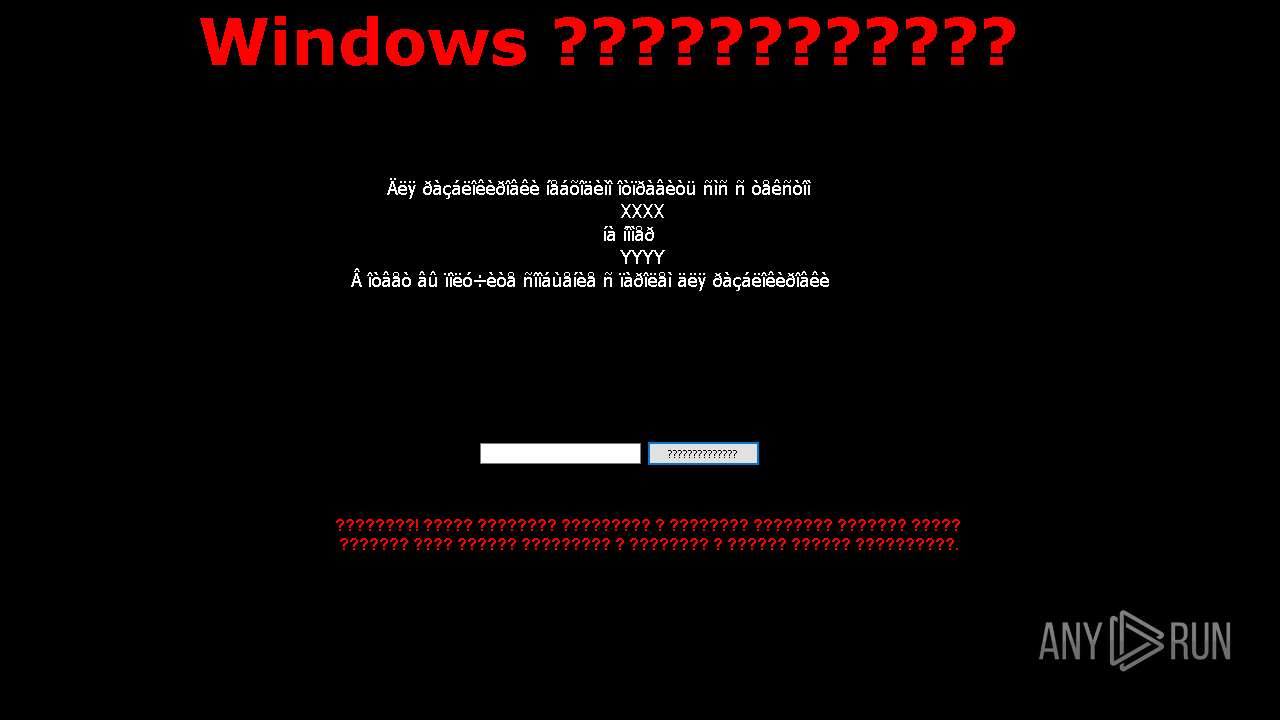
Troldesh is detected
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Stealers network behavior
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
Renames files like ransomware
- Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe (PID: 712)
SUSPICIOUS
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3948)
The process creates files with name similar to system file names
- Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe (PID: 6168)
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Executable content was dropped or overwritten
- Trojan-Ransom.Win32.Blocker.hnwj-54778da9519fb6a81c559104bb5f8e21ed4c1d140448a4897c89a0c6985ccbd8.exe (PID: 4836)
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
- Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe (PID: 6168)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Reads security settings of Internet Explorer
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
Write to the desktop.ini file (may be used to cloak folders)
- Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe (PID: 712)
Creates file in the systems drive root
- Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe (PID: 712)
Checks Windows Trust Settings
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
Malware-specific behavior (creating "System.dll" in Temp)
- Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe (PID: 6168)
Reads the BIOS version
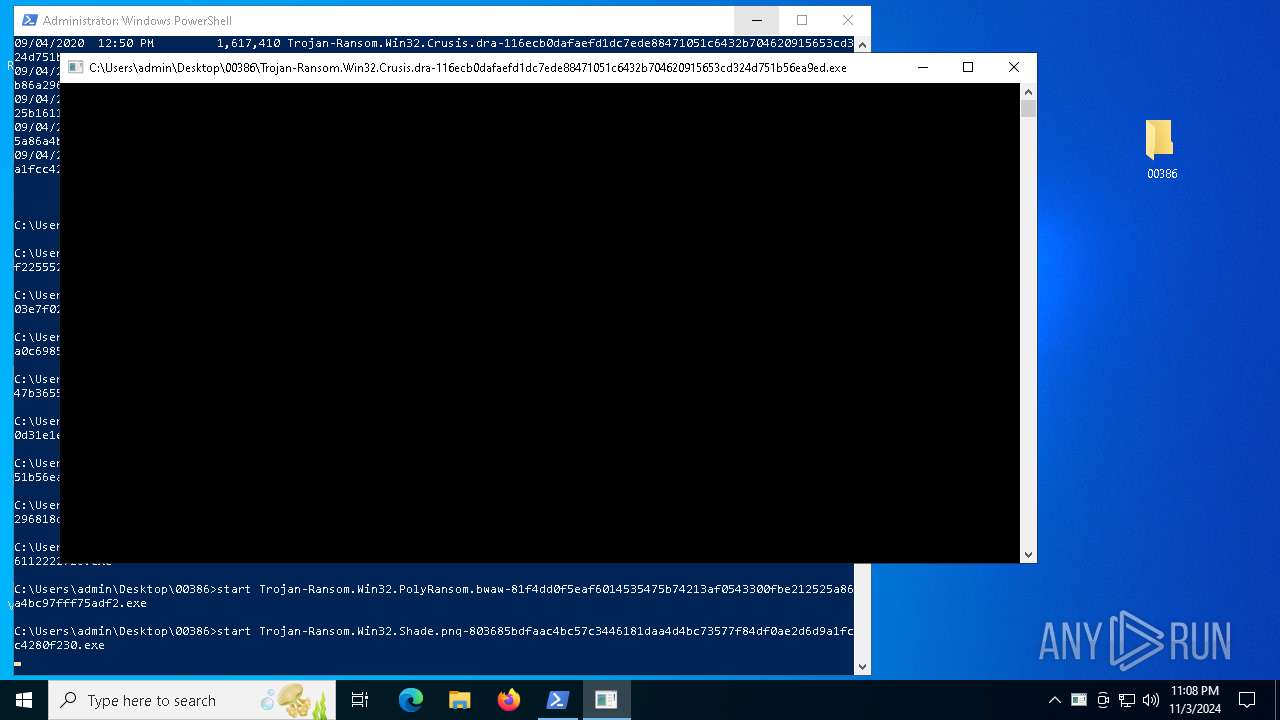
- Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe (PID: 6000)
Starts itself from another location
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
Contacting a server suspected of hosting an CnC
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
Reads the date of Windows installation
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
Potential Corporate Privacy Violation
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
Searches for installed software
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5832)
- powershell.exe (PID: 3948)
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
Manual execution by a user
- powershell.exe (PID: 3948)
Checks supported languages
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
- Trojan-Ransom.Win32.Blocker.hnwj-54778da9519fb6a81c559104bb5f8e21ed4c1d140448a4897c89a0c6985ccbd8.exe (PID: 4836)
- Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe (PID: 6168)
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- Trojan-Ransom.Win32.Locky.aflm-803a9fdb26c22ecd599f25f30e79c4914c75e45c2613718c4a25b16112222726.exe (PID: 4448)
- Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe (PID: 712)
- Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe (PID: 5940)
- Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe (PID: 6000)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
- drpbx.exe (PID: 2236)
Reads mouse settings
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
Reads the computer name
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- Trojan-Ransom.Win32.Locky.aflm-803a9fdb26c22ecd599f25f30e79c4914c75e45c2613718c4a25b16112222726.exe (PID: 4448)
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.Blocker.hnwj-54778da9519fb6a81c559104bb5f8e21ed4c1d140448a4897c89a0c6985ccbd8.exe (PID: 4836)
- Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe (PID: 5940)
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
- Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe (PID: 6168)
- drpbx.exe (PID: 2236)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5832)
Reads the machine GUID from the registry
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe (PID: 5940)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Create files in a temporary directory
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe (PID: 6168)
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Checks current location (POWERSHELL)
- powershell.exe (PID: 3948)
Creates files or folders in the user directory
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
Checks proxy server information
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe (PID: 7160)
- Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe (PID: 5940)
Sends debugging messages
- Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe (PID: 6000)
Reads the software policy settings
- Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe (PID: 6888)
- Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe (PID: 5940)
Disables trace logs
- Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe (PID: 5940)
Creates files in the program directory
- Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe (PID: 5920)
Process checks computer location settings
- HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe (PID: 7156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:11:03 21:26:17+00:00 |
| ArchivedFileName: | 00386 |
Total processes
147
Monitored processes
17
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe | C:\Users\admin\Desktop\00386\Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\Desktop\00386\HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | — | HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Firefox Version: 37.0.2.5583 Modules
| |||||||||||||||
| 3948 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | Trojan-Ransom.Win32.Locky.aflm-803a9fdb26c22ecd599f25f30e79c4914c75e45c2613718c4a25b16112222726.exe | C:\Users\admin\Desktop\00386\Trojan-Ransom.Win32.Locky.aflm-803a9fdb26c22ecd599f25f30e79c4914c75e45c2613718c4a25b16112222726.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4836 | Trojan-Ransom.Win32.Blocker.hnwj-54778da9519fb6a81c559104bb5f8e21ed4c1d140448a4897c89a0c6985ccbd8.exe | C:\Users\admin\Desktop\00386\Trojan-Ransom.Win32.Blocker.hnwj-54778da9519fb6a81c559104bb5f8e21ed4c1d140448a4897c89a0c6985ccbd8.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5832 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\RNSM00386.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5920 | Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe | C:\Users\admin\Desktop\00386\Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe | cmd.exe | ||||||||||||
User: admin Company: Steganos Software GmbH Integrity Level: HIGH Version: 19.1.1.0 Rev 11143 Modules
| |||||||||||||||
| 5940 | Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe | C:\Users\admin\Desktop\00386\Trojan-Ransom.Win32.PolyRansom.bwaw-81f4dd0f5eaf6014535475b74213af0543300fbe212525a86a4bc97fff75adf2.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NetSense Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6000 | Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe | C:\Users\admin\Desktop\00386\Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
9 785
Read events
9 724
Write events
43
Delete events
18
Modification events
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\RNSM00386.7z | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
21
Suspicious files
663
Text files
168
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe | executable | |
MD5:6DE5B2A3DFCFCA470FF68039AD159E38 | SHA256:57C69CE632F9595A10A1988F2B2D9B137C4B9E4713131075E0850D31E1EAAEDC | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe | executable | |
MD5:563A7DDCCF9756B593957C75222E8493 | SHA256:116ECB0DAFAEFD1DC7EDE88471051C6432B704620915653CD324D751B56EA9ED | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe | executable | |
MD5:1D65F334F0B027C0A69A8230F954B24D | SHA256:22603087D3C7881EE5208A2071BA681ACD0057AD44D248145CBC03E7F024C713 | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\Trojan-Ransom.Win32.Locky.aflm-803a9fdb26c22ecd599f25f30e79c4914c75e45c2613718c4a25b16112222726.exe | executable | |
MD5:542751E8E64D10FF82FF68C514486246 | SHA256:803A9FDB26C22ECD599F25F30E79C4914C75E45C2613718C4A25B16112222726 | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\Trojan-Ransom.Win32.Blocker.jyqd-58e319463d0a80f929385094b93394f8b8bc2e2065a04fd64d4047b3655f8acf.exe | executable | |
MD5:1770761262951A27E612B0F35021500B | SHA256:58E319463D0A80F929385094B93394F8B8BC2E2065A04FD64D4047B3655F8ACF | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\Trojan-Ransom.Win32.Limbozar.b-d3dadd5aabf3b9965636191296ef67b16a8f77d45720dd5adab86a296818d6c7.exe | executable | |
MD5:1B8E10CB606B36ABB3EA94169EF8A2C2 | SHA256:D3DADD5AABF3B9965636191296EF67B16A8F77D45720DD5ADAB86A296818D6C7 | |||
| 3948 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sagvsz4z.cs1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3948 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\B9AF724X724CIC73WQUG.temp | binary | |
MD5:74496B1E1A1E544C73D139FFBB559AA7 | SHA256:0AF000020C10B606A4990482FD8215137BF0F5F5D3FCB5D35801F156F8AFC241 | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5832.10921\00386\HEUR-Trojan-Ransom.MSIL.Gen.gen-802fef4d4f81c443497362711a7d8611741c30373c96d3229d699f225552a5f5.exe | executable | |
MD5:C5EFF77DB7EB62C4066247ADFCD64797 | SHA256:802FEF4D4F81C443497362711A7D8611741C30373C96D3229D699F225552A5F5 | |||
| 7160 | Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe | C:\Users\admin\AppData\Local\Temp\aut329E.tmp | binary | |
MD5:87AFB3126B700C6E8BB35F6E918DFC7C | SHA256:50BED156A1A345BF845682E7C6DC27E00C19A0955977AD1BC6610918F759FB15 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
42
DNS requests
24
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2724 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6420 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7160 | Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe | GET | 503 | 69.32.208.221:80 | http://www.downloadnetcat.com/nc11nt.zip | unknown | — | — | malicious |
6420 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6888 | Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe | GET | 200 | 142.250.185.131:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6888 | Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe | GET | 200 | 142.250.185.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6888 | Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe | POST | 301 | 172.67.210.108:80 | http://boec.ubksg.ru/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5640 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.204.134:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 2.19.198.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.16.204.152:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6888 | Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe | Malware Command and Control Activity Detected | ET MALWARE AZORult Variant.4 Checkin M2 |
6888 | Trojan-Ransom.Win32.Blocker.lckf-57c69ce632f9595a10a1988f2b2d9b137c4b9e4713131075e0850d31e1eaaedc.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/AZORult V3.2 Client Checkin M13 |
7160 | Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
7160 | Trojan-Ransom.Win32.Blocker.egtr-22603087d3c7881ee5208a2071ba681acd0057ad44d248145cbc03e7f024c713.exe | Misc activity | ET INFO AutoIt User-Agent Downloading ZIP |
5920 | Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 317 |
5920 | Trojan-Ransom.Win32.Shade.pnq-803685bdfaac4bc57c3446181daa4d4bc73577f84df0ae2d6d9a1fcc4280f230.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Troldesh Ransomware |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
Trojan-Ransom.Win32.Crusis.dra-116ecb0dafaefd1dc7ede88471051c6432b704620915653cd324d751b56ea9ed.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|